Windows Unprotected Private Key File
Overview:
In the digital age, encryption plays a crucial role in safeguarding sensitive information. Private key files, a component of encryption, are used for securing communications, digital signatures, and other cryptographic operations. However, the protection of these files is of utmost importance to prevent unauthorized access, data breaches, and compromise of encryption. In this article, we will explore the risks and consequences of unprotected private key files in Windows, and provide guidance on prevention and security measures, encryption best practices, regular auditing, disaster recovery, and incident response.
Causes of Unprotected Private Key Files:
1. Lack of password protection for private key files: Failure to set strong passwords or implement password policies for private key files leaves them vulnerable to unauthorized access. Without a password, anyone with access to the file could potentially decrypt or use the private key.
2. Failure to properly store private key files: Private key files should be securely stored in encrypted containers or vaults to prevent unauthorized access. Prolonged exposure or storing the files in easily accessible locations increases the risk of compromise.
3. Inadequate access controls and permission settings: In Windows, improper access control mechanisms or permission settings on private key files can lead to unauthorized access. Setting permissions too broadly or granting unnecessary privileges can result in a higher risk of exploitation.
Risks and Consequences:
1. Unauthorized access to sensitive information: When private key files are unprotected, they open the door for unauthorized individuals to gain access to sensitive information. This information could include personal data, financial records, or proprietary business secrets.
2. Potential for data breaches and identity theft: Unprotected private key files can be a gateway for cybercriminals to breach an organization’s network or system. Once inside, attackers can manipulate or steal sensitive data, leading to severe consequences such as identity theft and financial losses.
3. Compromise of encryption and digital signatures: Private key files are critical for encryption and digital signatures. If these files are compromised, adversaries can decrypt encrypted data, forge digital signatures, or impersonate legitimate individuals, undermining the trust in digital security measures.
Prevention and Security Measures:
1. Implementing strong password policies for private key files: It is essential to enforce strong passwords for private key files and regularly update them. Passwords should be complex, unique, and not easily guessable.
2. Secure storage and backup practices for private key files: Private key files should be stored in encrypted containers or secure vaults, with access restricted to authorized individuals only. Regular backups should be created and stored securely to mitigate the risk of file loss or corruption.
3. Effective access control mechanisms and permission settings: Properly configure access control mechanisms and permission settings to limit the exposure of private key files. Grant access and permissions only to individuals who require them, and regularly review access privileges to ensure they are necessary and up-to-date.
Encryption Best Practices:
1. Utilizing robust encryption algorithms for private key files: Choose encryption algorithms that are secure and widely accepted. Stay updated with the latest advancements and best practices in encryption to ensure strong protection for private key files.
2. Regularly updating encryption software and tools: Keep encryption software and tools up-to-date to mitigate potential vulnerabilities or weaknesses. Manufacturers often release updates and patches to address security flaws, so timely installation is critical.
3. Encrypting private key files at rest and in transit: Implement encryption for private key files both when they are stored and when they are transferred over networks. This ensures their confidentiality and integrity, even if intercepted during transmission or accessed without authorization.
Importance of Regular Auditing:
1. Conducting periodic audits to ensure private key file security: Regularly review and audit the security measures implemented for private key files. By conducting periodic assessments, vulnerabilities, weak access controls, or inadequate permissions can be identified and addressed promptly.
2. Monitoring and reviewing access logs for unauthorized activities: Implement logging and monitoring mechanisms to track access to private key files. Regularly review access logs to identify any suspicious activity or unauthorized access attempts, allowing for timely investigation and mitigation.
3. Addressing and mitigating any vulnerabilities or weaknesses: Address identified vulnerabilities or weaknesses promptly, following industry best practices and guidelines. This may involve applying security patches, updating access controls, or modifying permission settings to enhance the security of private key files.
Disaster Recovery and Incident Response:
1. Creating and maintaining backup copies of private key files: Regularly create backups of private key files and ensure they are securely stored. In the event of data loss, hardware failure, or a security incident, backup copies can be used for recovery and restoration purposes.
2. Developing an incident response plan for private key file breaches: Establish an incident response plan specifically tailored to private key file breaches. This plan should outline the steps to be taken in the event of a compromised private key file and ensure a timely and effective response to mitigate potential damage.
3. Performing regular drills and testing of incident response procedures: Regularly conduct drills and exercises to test the incident response plan for private key file breaches. By simulating various scenarios, the organization can identify weaknesses in the plan, improve response times, and enhance the overall readiness of the incident response team.
Training and Education:
1. Importance of educating employees on private key file security practices: Organize training sessions to educate employees about the importance of private key file security and the risks associated with unprotected files. Emphasize the role of employees in maintaining the confidentiality and integrity of private key files.
2. Providing training on encryption technologies and best practices: Train employees on encryption technologies and best practices, including how to properly handle, store, and use private key files. This will empower them to contribute to a secure and resilient digital environment.
3. Promoting a culture of cybersecurity awareness and responsibility: Foster a culture of cybersecurity awareness and responsibility throughout the organization. Encourage employees to be vigilant, report potential security incidents, and contribute to the enhancement of security practices in their day-to-day activities.
FAQs:
Q1: What are the risks of having an unprotected private key file in Windows?
A: Having an unprotected private key file in Windows puts sensitive information at risk of unauthorized access, potential data breaches, identity theft, and compromise of encryption and digital signatures.
Q2: How can I prevent unauthorized access to my private key files?
A: To prevent unauthorized access, implement strong password policies, securely store and backup private key files, and utilize effective access control mechanisms and permission settings.
Q3: What are the best practices for encryption and private key file security?
A: Best practices include using robust encryption algorithms, regularly updating encryption software and tools, and encrypting private key files both at rest and in transit.
Q4: How important is regular auditing for private key file security?
A: Regular auditing helps identify vulnerabilities, weak access controls, and inadequate permissions. It ensures that private key file security measures are effective and up-to-date.
Q5: What should I do in the event of a private key file breach or incident?
A: In the event of a private key file breach, follow an incident response plan that includes steps for recovery, investigation, and mitigation. Regularly conduct drills and testing to improve incident response readiness.
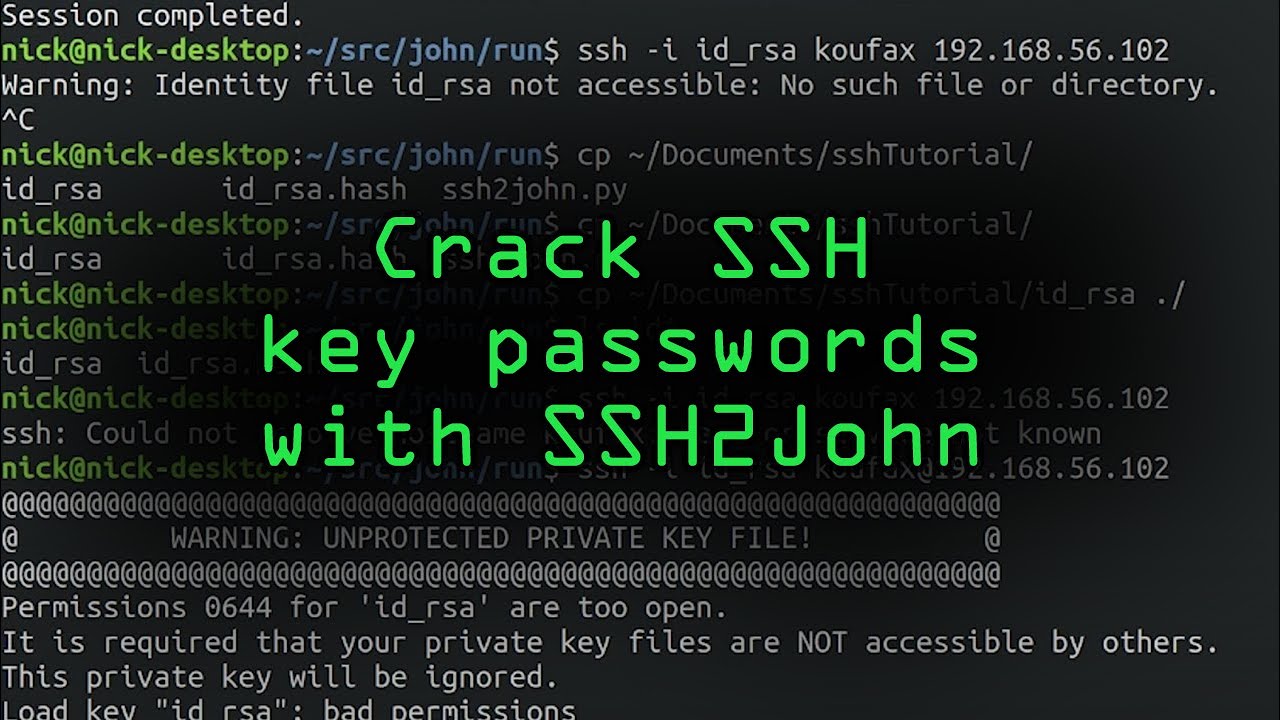
In conclusion, the security of private key files in Windows is paramount to safeguarding sensitive information and maintaining trust in digital security measures. By implementing preventive measures, adhering to encryption best practices, conducting regular audits, preparing for incidents, and promoting employee education, organizations can mitigate the risks associated with unprotected private key files and enhance overall cybersecurity. Remember, “warning: unprotected private key file! It is required that your private key files are NOT accessible by others, Windows, Load key invalid format, Load key bad permissions, it is required that your private key files are not accessible by others, Permissions for are too open, Windows, Aws warning unprotected private key file, Add SSH key to Windows, Windows unprotected private key file.”
How To Solve Warning Unprotected Key File | In Aws Ec2 Instance | In Windows 10
Keywords searched by users: windows unprotected private key file warning: unprotected private key file!, It is required that your private key files are NOT accessible by others Windows, Load key invalid format, Load key bad permissions, it is required that your private key files are not accessible by others., Permissions for are too open Windows, Aws warning unprotected private key file, Add SSH key to Windows
Categories: Top 94 Windows Unprotected Private Key File
See more here: nhanvietluanvan.com
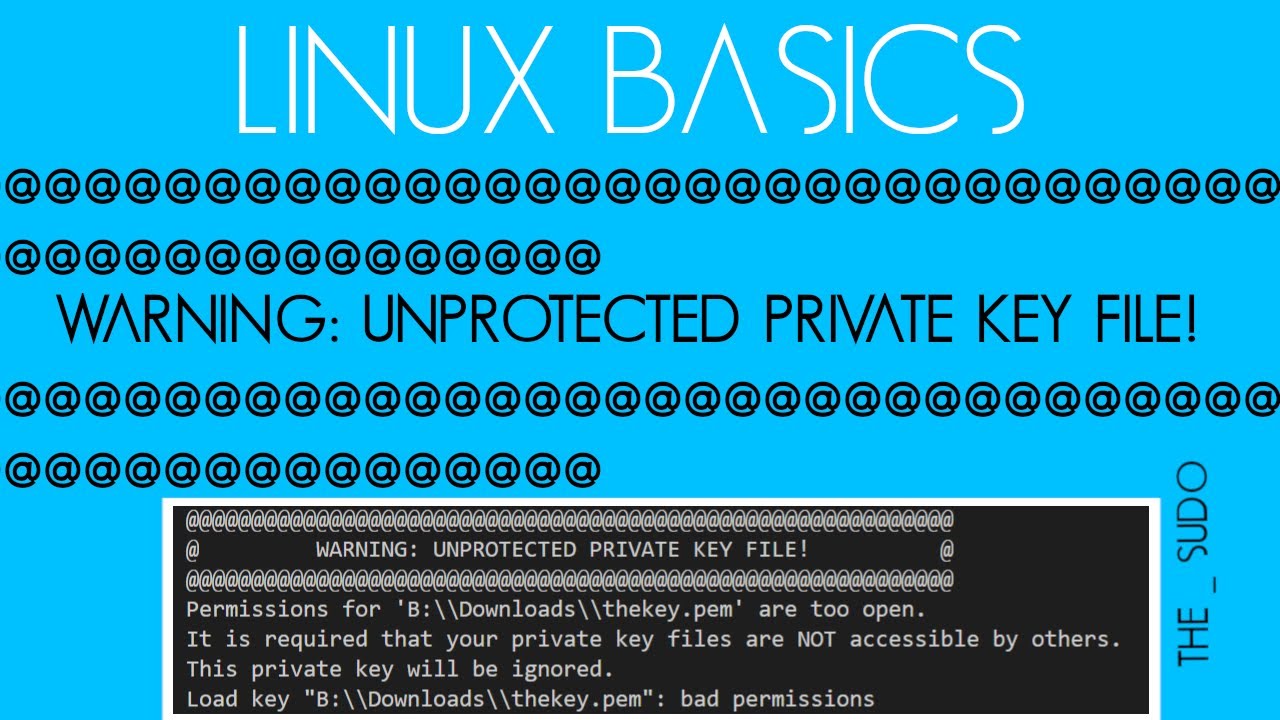
Warning: Unprotected Private Key File!
In today’s digitized world, where cybersecurity threats are continuously on the rise, protecting your digital assets has become increasingly vital. One crucial element of securing such assets is the proper management and protection of private key files. An unprotected private key file can leave your sensitive information vulnerable to hackers, potentially leading to severe consequences. In this article, we will discuss the importance of safeguarding your private key file and provide essential tips for enhanced cybersecurity. Read on to ensure the safety of your digital assets.
Understanding the Private Key File:
A private key file is an integral part of public key cryptography, a cryptographic system that employs a pair of keys, namely public and private keys. These keys work together to establish secure communication and authentication. While the public key is shared with others, the private key must be kept confidential at all times.
Why Is it Critical to Protect Your Private Key File?
Your private key file provides access to your encrypted information, financial records, online accounts, and other valuable digital assets. If an attacker gains access to your private key, they can potentially decipher your sensitive data and misuse it for nefarious purposes. The consequences can range from financial loss to reputational damage or even identity theft.
Common Risks Associated with an Unprotected Private Key File:
1. Unauthorized Access: An unsecured private key file increases the likelihood of unauthorized access. Cybercriminals constantly scan for such vulnerabilities in order to obtain confidential information.
2. Data Breach: Once an attacker gains access to your private key file, your encrypted data is at risk of being stolen or compromised. This can have severe implications, particularly if the encrypted data includes financial transactions or personal information.
3. Insider Threats: Negligence or malicious intent from an insider can also lead to an unprotected private key file falling into the wrong hands. It is crucial to implement strict access controls and security measures within your organization to mitigate such risks.
Tips to Protect Your Private Key File:
1. Encryption: Encrypt your private key file using strong algorithms. This adds an additional layer of security by providing an extra barrier to unauthorized access.
2. Password Protection: Always password-protect your private key file with a strong, unique password. Avoid using easily guessable phrases or reusing passwords across different platforms.
3. Secure Storage: Store your private key file on a secure device or a hardware wallet designed specifically for secure key storage. These physical devices are immune to cyber threats, ensuring an added layer of protection.
4. Regular Backups: Create backups of your private key file and store them securely. Regularly updating backups ensures that you do not lose access to your digital assets in case of theft or hardware failure.
5. Two-Factor Authentication: Enable two-factor authentication (2FA) wherever possible. This adds an extra layer of security by requiring a second form of verification, such as a biometric scan or a unique code sent to your registered mobile device.
6. Secure Communication Channels: Always use secure communication channels, such as encrypted messaging apps or secure email services when sharing your private key file with authorized parties.
FAQs:
Q1. Can I share my private key file with authorized individuals securely?
Yes, you can securely share your private key file with authorized individuals by using encrypted communication channels, such as password-protected zip files or secure file transfer protocols (SFTP).
Q2. What should I do if I suspect my private key file has been compromised?
If you suspect your private key file has been compromised, act swiftly. Immediately generate a new private key file and update it on all relevant platforms and services. Additionally, notify the appropriate authorities or consult with cybersecurity professionals to assess the potential damage and implement further protective measures.
Q3. Can I store my private key file in the cloud?
Storing your private key file in the cloud can be risky, as cloud storage can potentially be accessed by unauthorized individuals. It is recommended to utilize physical devices or hardware wallets for storing your private key file securely.
Q4. How often should I update my private key file?
It is good practice to update your private key file periodically, especially when there are suspected security breaches or changes in your hardware or software environment. Regularly rotating your private key file enhances security and mitigates potential risks.
Conclusion:
Protecting your private key file is paramount in safeguarding your digital assets from unauthorized access and potential misuse. By following the tips outlined above and implementing robust cybersecurity practices, you can ensure the security of your private key file and shield your sensitive information from cyber threats. Remember, the precautions you take today can save you from significant repercussions in the future. Stay diligent and prioritize the safety of your digital world.
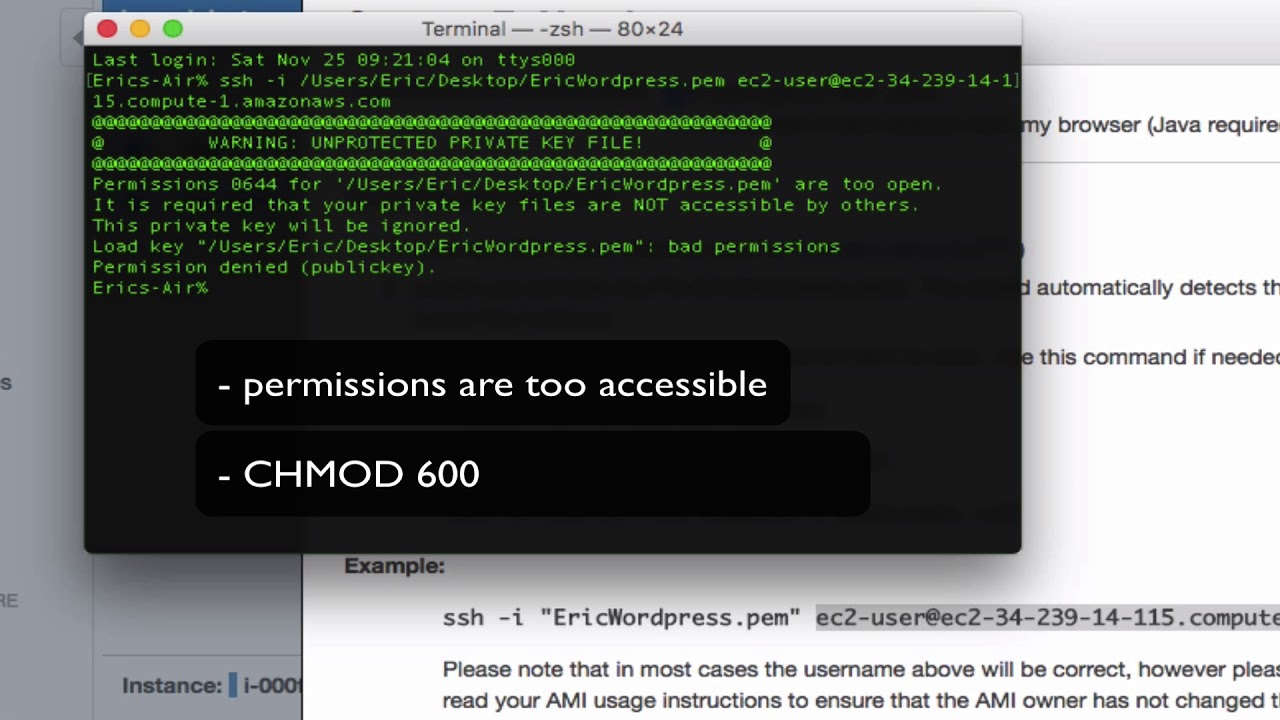
It Is Required That Your Private Key Files Are Not Accessible By Others Windows
Why is it Important?
Private key files play a critical role in securing sensitive information by encrypting data and enabling digital signatures. They are used in asymmetric cryptography, where a public key is freely available without compromising security, while the corresponding private key is kept secure and private. This ensures that only the authorized person with the private key can decrypt the data or create a valid digital signature.
If an attacker gains unauthorized access to your private key files, they can impersonate you, decrypt encrypted data, forge digital signatures, or even create malicious software that appears to be genuine. Additionally, compromising a private key can lead to unauthorized attacks on your online accounts, financial transactions, and other critical systems.
Security Risks and Vulnerabilities
Windows systems are not inherently insecure, but various vulnerabilities can put private key files at risk. Here are some common security risks associated with private key files:
1. Malware: Malicious software, such as keyloggers or spyware, can monitor and capture your keystrokes, including the passwords you use to protect your private key files. Once in possession of the password, an attacker can gain access to the private key and misuse it.
2. Weak Passwords: Weak passwords provide an easy way for attackers to gain unauthorized access to your private key files. Using strong, complex passwords is crucial to protecting your private keys.
3. Insecure Storage: Storing private key files in insecure locations, such as shared network drives or removable storage devices, increases the likelihood of unauthorized access. Physical security measures must be in place to safeguard private key files.
4. Social Engineering: Cybercriminals often resort to social engineering techniques to trick individuals into disclosing their private key file passwords or grant them access through various means. It is crucial to be vigilant and adopt best practices to counter such tactics.
Practical Tips to Secure Private Key Files on Windows
Now that we understand the risks, here are some practical tips to protect your private key files on Windows:
1. Password Protection: Choose a strong, unique password for your private key files. It should be long, include a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using common phrases or dictionary words.
2. Encryption: Encrypt your private key files with a strong encryption algorithm, such as AES (Advanced Encryption Standard). This adds an extra layer of protection, even if an attacker gains access to the files.
3. Two-Factor Authentication: Enable two-factor authentication wherever possible. This adds an additional authentication step apart from the private key, making it harder for attackers to gain unauthorized access.
4. Secure Storage: Store your private key files in a secure location on your machine, such as an encrypted folder or a hardware security module (HSM). Avoid storing them in default or common directories.
5. Regular Backups: Ensure you have secure backups of your private key files in case of system failures or corruption. Store these backups separately from the originals and verify their integrity periodically.
FAQs
Q1. Can I store my private key files in the cloud?
A1. Storing private key files in the cloud can be risky, as it introduces additional security concerns. If you choose to do so, make sure to use a reputable cloud service provider and apply appropriate encryption and access control measures.
Q2. What should I do if I suspect my private key files have been compromised?
A2. If you suspect unauthorized access to your private key files, immediately revoke and regenerate new keys. Inform relevant parties, such as certificate authorities, and assess any potential impact on your systems.
Q3. Are there any additional measures I can take to secure my private key files?
A3. Yes, consider using hardware-based solutions like smart cards or USB tokens to store private keys securely. These devices provide an added layer of protection by isolating the private keys from the host system.
In conclusion, safeguarding your private key files is of paramount importance to maintain the integrity and confidentiality of sensitive data. By following best practices, such as employing strong passwords, encrypting files, and adopting secure storage solutions, you can significantly reduce the risk of unauthorized access and potential security breaches on the Windows platform. Remember, taking proactive security measures goes a long way in safeguarding your digital assets.
Load Key Invalid Format
In the realm of computers and software, error messages can be quite frustrating. They can interrupt our workflow, hinder progress, and leave us feeling exasperated. One such error message that plagues many users is the “Load key invalid format” message. If you’ve encountered this error, fear not, as this article aims to shed light on its causes, suggest potential solutions, and provide a clear understanding of the topic.
Understanding the “Load key invalid format” error:
When you come across the “Load key invalid format” error message, it typically indicates an issue within the cryptographic key infrastructure. This error occurs when the software attempts to load a cryptographic key but is unable to recognize its format. Cryptographic keys play a vital role in maintaining data security, particularly in encryption processes. Therefore, any issues faced in loading these keys could compromise the integrity, confidentiality, and authenticity of your data.
Causes of the “Load key invalid format” error:
1. Incompatible key format: This error message commonly arises when the software requires a specific format for cryptographic keys, and the loaded key does not meet those requirements. This can happen due to using outdated or incompatible key files.
2. Corrupted key file: If the key file itself is corrupted or damaged, the software will fail to recognize its format, leading to the “Load key invalid format” error. Corruption can occur due to various reasons, such as file transfer errors or issues during storage.
3. Incorrect key generation: If the key generation process is not completed correctly, it can result in an invalid key format. This commonly occurs when users attempt to generate custom-made keys but lack the necessary knowledge or experience to do so accurately.
4. Faulty software update or installation: Sometimes, an incompatible software update or improper installation process could lead to changes in key file formats and cause the “Load key invalid format” error.
Solutions for the “Load key invalid format” error:
1. Verify key compatibility: Ensure that the key format matches the requirements of the software. Consult the software documentation or contact the software vendor to obtain information regarding the accepted key formats.
2. Replace the key file: If the key file is corrupted or damaged, the easiest solution is to obtain a new copy of the key file. If the key file had been backed up, restore it from the backup. Otherwise, contact the key issuer or software vendor for assistance in obtaining a valid key file.
3. Regenerate the cryptographic key: If the key generation process was completed incorrectly, it is advisable to regenerate the key. Take care to follow the instructions provided by the software or consult with an expert to ensure the generation process is conducted accurately.
4. Utilize key conversion tools: In some cases, it may be possible to convert the invalid key format into the required format using third-party tools. These tools can assist in transforming the key file so that it becomes compatible with the software.
5. Check software compatibility: If you encounter this error after a software update or installation, double-check that the new version is compatible with your existing key files. Verify if the software vendor provides any migration guides or tools to facilitate the transition to the new version.
FAQs (Frequently Asked Questions):
Q: Can I manually edit the key file to fix the error?
A: It is generally not recommended to manually edit the key file as it can result in further complications and potential security risks. Always seek expert advice before altering any cryptographic key file.
Q: Can I use an online key generator tool?
A: While online key generators are available, it is crucial to exercise caution. Generating keys online poses security risks, as the generated keys could be compromised or used in malicious activities. It is advisable to rely on trusted sources and consult with professionals for proper key generation.
Q: I have multiple key files. How do I identify the correct one?
A: If you possess multiple key files, refer to the documentation or consult the software vendor to determine which key file should be used. Each software may have its own specific naming conventions or file extensions that indicate the correct key file.
Q: Can antivirus software cause this error?
A: While it is unlikely that antivirus software directly causes the “Load key invalid format” error, it is essential to ensure that your antivirus software is not interfering with the key file or associated processes. Temporarily disabling antivirus software and trying to load the key again can help identify any potential conflicts.
Q: What precautions should I take to avoid this error in the future?
A: To prevent encountering the “Load key invalid format” error in the future, regularly update your software and ensure that you have valid and compatible key files. Regular backups of key files are also recommended to mitigate the risks associated with corruption or loss.
In conclusion, the “Load key invalid format” error can be a frustrating obstacle in software operations, but with the right knowledge and troubleshooting steps, it can be resolved. By understanding the causes and implementing the appropriate solutions, users can ensure smooth functioning of their software systems and maintain the integrity of their cryptographic keys.
Images related to the topic windows unprotected private key file

Found 20 images related to windows unprotected private key file theme























Article link: windows unprotected private key file.
Learn more about the topic windows unprotected private key file.
- Windows SSH: Permissions for ‘private-key’ are too open
- OpenSSH using private key on Windows (“Unprotected private …
- Fixed: Cannot SSH in Windows to AWS: UNPROTECTED …
- WARNING: UNPROTECTED PRIVATE KEY FILE! – LinkedIn
- SSH on windows permissions for private key too open error
- Warning Unprotected Private Key File: We Fixed the Bug
- Warning: Unprotected Private Key File! Fixed – Gadgetswright
See more: https://nhanvietluanvan.com/luat-hoc