What Is An Endpoint
In the world of technology and networking, the term “endpoint” refers to a device or a piece of hardware that serves as a communication point. It is the point where data originates or is received within a network. Endpoints are crucial components of networking infrastructure, enabling devices to connect and exchange information with each other. In this article, we will delve deeper into the concept of endpoints, discussing their definition, characteristics, types, importance, functions, security measures, and future trends. Additionally, we will address frequently asked questions about endpoints to provide a comprehensive understanding of this vital networking element.
Endpoint Definition:
An endpoint, in terms of networking, can be defined as a device or a specific hardware component that acts as a source or destination of communication in a network. It can be a computer, mobile device, server, IoT (Internet of Things) device, or any other network-enabled device. Endpoints are essential for any network to function properly as they facilitate the transmission and reception of data across the network.
Characteristics of an Endpoint:
There are several key characteristics that define an endpoint:
1. Connectivity: An endpoint must have the ability to connect and communicate with other devices or systems within a network.
2. Data Source/Sink: Endpoints serve as points where data is either generated or consumed within a network. They can send data to other devices or receive data from them.
3. Network Address: Every endpoint is assigned a unique network address (such as an IP address) that distinguishes it from other devices in the network.
Types of Endpoints:
Endpoints can vary in their form and function, depending on the specific network and purpose. Here are some common types of endpoints:
1. Workstations: Computers used by individuals for various tasks, including data entry, document processing, and web browsing, are considered endpoints.
2. Mobile Devices: Smartphones, tablets, and other portable devices that connect to a network fall under the category of endpoints. These devices have become increasingly prevalent in recent years due to the rise of mobile technology.
3. Servers: In a network, servers act as both endpoints and intermediaries. They serve as endpoints when they receive requests from clients and as intermediaries when they route or process data to be sent to other endpoints.
4. IoT Devices: Internet of Things devices, such as smart home appliances, sensors, and wearable gadgets, are endpoints that collect and send data to other devices or systems. These endpoints play a significant role in the growing ecosystem of interconnected devices.
Importance of Endpoints in Networking:
Endpoints are crucial for networking infrastructure due to their various functions and contributions to network connectivity. Below are some reasons why endpoints are important:
1. Data Transmission: Endpoints allow the transmission of data across networks by sending or receiving information from other devices. Without endpoints, networks would be unable to exchange data efficiently.
2. Connectivity: Endpoints enable multiple devices to connect and communicate with each other, facilitating collaboration, resource sharing, and information exchange.
3. User Access: Endpoints provide users with access to network resources, applications, and services. Users can utilize endpoints to connect to servers, access files, and interact with different devices and services.
4. Network Management: Endpoints play a crucial role in network management, as they provide administrators with control and monitoring capabilities. Through endpoints, network administrators can enforce security measures, manage user permissions, and track network usage.
Functions of Endpoints:
The functions of endpoints can vary depending on their specific purpose and context within a network. Here are some common functions performed by endpoints:
1. Data Transmission: Endpoints act as sources or recipients of data, transmitting information between devices or systems.
2. Data Processing: Some endpoints, such as servers, can process or manipulate data before transmitting it to other endpoints.
3. Access Control: Endpoints can enforce access control mechanisms, determining which users or devices are granted access to network resources.
4. Security Measures: Endpoints play a critical role in implementing security measures, such as firewalls, antivirus software, and encryption protocols, to protect networks from threats and unauthorized access.
Endpoint Security Measures:
As endpoints are crucial components of network infrastructure, ensuring their security is vital to safeguarding the entire network. Here are some essential security measures for endpoints:
1. Antivirus and Anti-Malware Software: Installing and regularly updating antivirus and anti-malware software on endpoints helps detect and prevent malicious software from compromising the network.
2. Firewall: Configuring firewalls on endpoints can provide an additional layer of security by monitoring incoming and outgoing network traffic and blocking suspicious or unauthorized connections.
3. Encryption: Encrypting data transmitted between endpoints can protect sensitive information from being intercepted or accessed by unauthorized entities.
4. Patches and Updates: Keeping endpoints up to date with the latest security patches and software updates is crucial to address vulnerabilities and protect against emerging threats.
Future Trends in Endpoint Technology:
Endpoint technology continues to evolve and adapt to the advancements in networking and computing. Here are some future trends to watch out for:
1. Internet of Things: The growing prevalence of IoT devices is expected to expand the number of endpoints in networks, leading to increased complexity and data transmission requirements.
2. Artificial Intelligence and Machine Learning: The integration of AI and machine learning algorithms in endpoints can enhance their security capabilities by identifying and responding to threats in real-time.
3. Endpoint Detection and Response: Endpoint detection and response (EDR) solutions are becoming increasingly important for proactive threat detection and incident response on endpoints.
4. Edge Computing: With the rise of edge computing, endpoints are expected to play a crucial role in processing and analyzing data closer to the source, reducing latency and improving network efficiency.
Frequently Asked Questions (FAQs):
Q1. What is an endpoint in API?
A1. In API (Application Programming Interface) terminology, an endpoint refers to a specific URL (Uniform Resource Locator) or route to which API calls are made to access a particular functionality or resource provided by the API.
Q2. What are endpoints in cyber security?
A2. In cyber security, endpoints are the devices or systems that are most vulnerable to attacks, as they are often the points of entry for hackers. Endpoint security focuses on protecting these devices and preventing unauthorized access or data breaches.
Q3. What is the function of an endpoint on a network?
A3. The function of an endpoint on a network is to enable communication and data exchange between devices or systems. Endpoints act as the source or destination of data transmission within a network.
Q4. What intermediate network device is usually used as an endpoint in the data center?
A4. In a data center, switches are commonly used as intermediate network devices that act as endpoints. They facilitate connections between different devices and networks within the data center environment.
Q5. What is a web service endpoint?
A5. A web service endpoint refers to a URL or URI (Uniform Resource Identifier) that exposes the functionality of a web service. It represents the location where clients can access and interact with the web service.
Q6. What is a REST API endpoint?
A6. REST (Representational State Transfer) is an architectural style used in API design. A REST API endpoint is a specific URL that represents a resource or a specific operation provided by the API. Clients can make HTTP requests to these endpoints to interact with the API.
Q7. What is an Endpoint API?
A7. An Endpoint API refers to a set of rules, protocols, and tools that enable the creation, deployment, and management of endpoints in a network or system. It allows developers to define, configure, and control these endpoints programmatically.
Q8. What is the endpoint of a titration?
A8. In chemistry, the endpoint of a titration is the point at which the reaction between the titrant (solution of known concentration) and the analyte (solution of unknown concentration) is complete. It is typically indicated by a color change or other measurable change.
In conclusion, endpoints are critical components of networking infrastructure that enable the transmission and reception of data within a network. They vary in their form and function, serving as sources, recipients, or intermediaries of data. Endpoints play a vital role in network connectivity, user access, and network management. Ensuring endpoint security is paramount to protect against threats and unauthorized access. As technology progresses, endpoints are expected to continue evolving, integrating advanced security measures and becoming integral to emerging trends such as AI and edge computing. Understanding the concept of endpoints is essential for anyone involved in networking or system architecture, allowing for more efficient and secure network design and implementation.
What Is An Endpoint?
What Is An Endpoint In An Api?
In the world of technology and software development, APIs (Application Programming Interfaces) play a vital role in connecting different applications and systems. APIs act as a communication bridge, allowing different software components to interact with each other, exchange data, and execute functions. Central to the concept of APIs are endpoints, which serve as gateways to access specific functionalities or resources within an application.
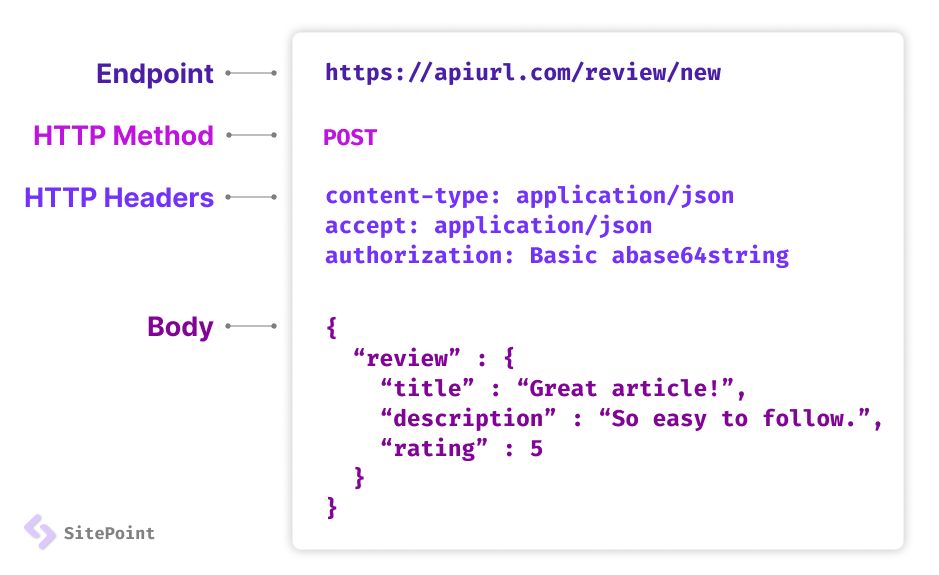
An endpoint in an API refers to a specific URL (Uniform Resource Locator) or URI (Uniform Resource Identifier) through which an API can be accessed. It acts as a reference point that defines where the API resources or functionalities can be accessed or manipulated. In simpler terms, an endpoint represents a specific destination within an API that developers can send requests to, fetching or modifying data according to their needs.
Understanding the Role of Endpoints:
Endpoints are designed to provide a structured and organized way of accessing and interacting with an API. Each endpoint represents a specific functionality or resource within the API, enabling developers to perform certain operations. These operations can include fetching data, modifying or deleting existing data, creating new data, authenticating users, and more.
Endpoints are essentially the interface that exposes the available operations within an API. Developers can make HTTP (Hypertext Transfer Protocol) requests to these endpoints, specifying the desired operation (such as GET, POST, PUT, DELETE), and provide any required parameters or data. The API then processes the request and returns the appropriate response.
Endpoint Structure and URL Format:
Endpoints are typically structured in a hierarchical manner, following a specific URL format. The format can vary depending on the API design or implementation, but it generally consists of a base URL followed by a path that identifies the specific functionality or resource.
For instance, consider an API for managing a user database. The base URL might be something like “https://exampleapi.com/”. To access the users’ information, the endpoint URL could be “https://exampleapi.com/users”. To retrieve information about a specific user, the endpoint URL could be “https://exampleapi.com/users/{user_id}”, where “{user_id}” is a placeholder representing the actual user ID.
In many cases, endpoints may also accept query parameters, allowing developers to refine the results or specify additional details. For example, an endpoint like “https://exampleapi.com/users?name=John” could be used to retrieve a list of users with the name “John”.
FAQs:
1. How do I find the endpoints for an API?
Endpoint information is usually provided in the API documentation. The documentation should outline the available endpoints, their purpose, required parameters, and expected responses.
2. Can an API have multiple endpoints?
Yes, APIs can have multiple endpoints to represent different functionalities or resources. An API may consist of dozens or even hundreds of endpoints, depending on its complexity.
3. What HTTP methods can be used with API endpoints?
API endpoints can support various HTTP methods, but the most commonly used ones are GET, POST, PUT, and DELETE. GET is used to retrieve data, POST to create new data, PUT to update existing data, and DELETE to remove data.
4. Are endpoints the same as URLs?
While endpoints are represented by URLs, they are not the same. Endpoints are specific paths within an API that can be accessed through URLs. URLs, on the other hand, can refer to any web resource, including websites, images, or other files.
5. Is it possible to secure API endpoints?
Yes, API endpoints can be secured by implementing various authentication and authorization mechanisms. This ensures that only authorized users or applications can access and manipulate the API resources.
In conclusion, endpoints are an essential component of an API as they define the accessible functionalities or resources. Developers can use endpoints to send requests, retrieve or modify data, and perform various operations within an API. Understanding endpoints and their structure enables developers to effectively utilize APIs and build robust applications.
What Is An Endpoint In A Network?
In the world of computer networks, the term “endpoint” refers to a device or a node that is connected to a network and is capable of sending or receiving data. Essentially, an endpoint is a point of entry or exit for data in a network infrastructure. It can be a computer, a smartphone, a server, a printer, or any other device that connects to a network.
Endpoints play a vital role in the functioning of a network, as they enable communication and data transfer between network users and resources. They act as both sources and destinations of data packets, facilitating the exchange of information across the network. Without endpoints, networks would be inaccessible, rendering them useless for connectivity and collaboration purposes.
Characteristics of Endpoints:
1. IP Addresses: Every endpoint connected to a network is assigned a unique IP (Internet Protocol) address. This address acts as an identifier, allowing other devices to locate and establish connections with each endpoint. IP addresses can be either static or dynamic, depending on the network configuration.
2. Protocols: Endpoints use network protocols to communicate and exchange data. These protocols define the rules and procedures for communication, ensuring seamless connectivity and standardization across different devices and networks. Common protocols include TCP/IP, HTTP, FTP, and SMTP.
3. Operating Systems: Endpoints are usually equipped with an operating system (OS) that enables them to manage different software and hardware components. Examples of popular operating systems include Windows, macOS, Linux, Android, and iOS. The OS facilitates the interpretation and execution of instructions, making the endpoints functional and user-friendly.
4. Network Interfaces: Endpoints possess network interfaces, such as Ethernet, Wi-Fi, or Bluetooth, which allow them to connect and interact with other devices within a network. These interfaces provide the physical connection required for data transfer and communication.
Endpoint Security:
Apart from their connectivity benefits, endpoints also present security challenges. Given the continuous growth of cyber threats and attacks, securing endpoints has become a top priority for network administrators and users. Endpoint security involves protecting endpoints from unauthorized access, malware, data breaches, and other potential risks that can compromise the network’s integrity.
Endpoint security measures commonly include antivirus software, firewalls, encryption, and regular software updates. These tools and practices aim to prevent, detect, and respond to security breaches, ensuring that endpoints remain secure and data remains confidential.
FAQs:
1. Why are endpoints important in a network?
Endpoints are crucial in networks as they enable communication and data transfer between network users and resources. They act as sources and destinations for data packets, allowing connectivity and collaboration within the network.
2. Can an endpoint refer to a network switch or router?
While network switches and routers are integral components of a network, they are not typically referred to as endpoints. Endpoints are devices or nodes that connect to a network and possess IP addresses, allowing them to send or receive data. Switches and routers, on the other hand, are responsible for managing and directing network traffic.
3. How can I secure my endpoints?
Securing endpoints involves implementing various security measures such as antivirus software, firewalls, encryption, and regular software updates. Additionally, user education and awareness, strong passwords, and multi-factor authentication can greatly enhance endpoint security.
4. Can an endpoint be a virtual machine?
Yes, virtual machines (VMs) can also function as endpoints. A VM is a software emulation of a computer system, running on a physical host machine. VMs can be used as endpoints to connect to networks, just like physical devices, and communicate with other devices within the network.
5. Is mobile computing a type of endpoint?
Yes, mobile devices such as smartphones and tablets are considered endpoints. They can connect to networks using various wireless technologies, offering users mobility and access to network resources from anywhere.
In conclusion, endpoints are the devices, both physical and virtual, that connect to a network and enable communication and data transfer. They play a critical role in network infrastructure and require adequate security measures to safeguard against potential threats. Understanding endpoints and their characteristics is essential for maintaining a functional and secure network environment.
Keywords searched by users: what is an endpoint What is endpoint in API, what are endpoints in cyber security, What is a function of an endpoint on a network, What intermediate network device is usually used as an endpoint in the data center, What is a web service endpoint, REST API endpoint, Endpoint API, What is the endpoint of a titration
Categories: Top 93 What Is An Endpoint
See more here: nhanvietluanvan.com
What Is Endpoint In Api
In the world of software development, an API (Application Programming Interface) serves as a medium for different software applications to communicate with each other. It allows developers to access functionalities and services provided by other software in a standardized and efficient manner. An essential component of an API is the endpoint, which acts as a gateway to access specific resources or data within the software system.
An endpoint is essentially a unique URL (Uniform Resource Locator) that an API exposes, allowing developers to interact with the API and perform various operations. It serves as the access point from where API clients can send requests and receive responses. Each endpoint corresponds to a specific function or feature of the API and defines what actions can be performed on it.
Endpoints typically follow a predefined syntax structure, making it easier for developers to understand and use them. They consist of the root URL of the API, followed by a path that specifies the specific resource or operation being accessed. For example, consider an API that provides weather information. An endpoint to retrieve the current weather for a given location could be:
“`
https://api.weather.io/weather/current
“`
In this example, “https://api.weather.io” is the root URL, and “/weather/current” is the path that represents the specific endpoint.
Endpoints can vary in their functionality based on the HTTP methods they support. The most common methods are:
1. GET: Retrieves information or data from the API.
2. POST: Sends data to the API to create a new resource.
3. PUT: Updates an existing resource within the API.
4. DELETE: Removes a specific resource from the API.
These HTTP methods allow developers to perform various operations on the data exposed by the API. For instance, using the weather API mentioned earlier, a GET request to the endpoint could return the current weather details, while a POST request to the same endpoint with relevant data could create a new weather record.
Endpoints can also have additional parameters appended to the URL to further refine the request. These parameters can be used to filter results, specify formatting options, or provide authentication credentials. For example, adding a “city” parameter to the weather API endpoint could return weather information specifically for the given city:
“`
https://api.weather.io/weather/current?city=London
“`
Endpoints play a crucial role in the security and scalability of APIs. It’s common practice to protect endpoints with authentication mechanisms, such as API keys or access tokens, to ensure that only authorized clients can access sensitive data or perform certain actions. Additionally, APIs often provide rate limiting measures on endpoints to prevent excessive requests, ensuring fair usage in a shared infrastructure.
Frequently Asked Questions (FAQs):
Q: How do endpoints differ from URLs?
A: While endpoints are essentially URLs, they represent a specific functionality or resource within an API. URLs, on the other hand, refer to any web addresses used to access resources on the internet.
Q: Can an API have multiple endpoints?
A: Yes, APIs can have multiple endpoints. Each endpoint corresponds to a specific functionality or resource within the API.
Q: Are endpoints specific to RESTful APIs only?
A: No, endpoints can be used in various API architectures, including RESTful APIs. They provide a way to interact with resources or services regardless of the underlying architecture.
Q: How can I determine the available endpoints in an API?
A: API documentation typically provides a comprehensive list of available endpoints and their functionalities. Developers can refer to this documentation to understand how to interact with an API.
Q: Is it possible to create custom endpoints in an API?
A: While most API endpoints are predefined by the API developers, some APIs allow users to create custom endpoints based on their specific requirements or use cases.
Q: Are endpoints always accessible to the public?
A: Access to endpoints depends on the API’s design and intended usage. Some endpoints may require authentication or have restricted access, while others might be open to the public.
Q: Can one API have different versions of endpoints?
A: Yes, APIs can have different versions of endpoints to provide backward compatibility and support incremental updates. These versions allow developers to migrate to new functionalities at their own pace.
In conclusion, an endpoint is a crucial element in API development that enables API clients to interact with specific resources and services. It acts as a gateway by providing a unique URL where developers can send requests and receive responses. Understanding how endpoints work is essential for effectively utilizing APIs and integrating them into various software applications.
What Are Endpoints In Cyber Security
In today’s digital landscape, where cyber threats are constantly evolving and becoming more sophisticated, implementing effective cybersecurity measures is of the utmost importance for individuals and businesses alike. One aspect of cybersecurity that often gets overlooked is the concept of endpoints. In this article, we will delve into what endpoints are in cybersecurity, why they play a crucial role in defending against cyber threats, and how to secure them effectively.
Defining Endpoints
Endpoints refer to any device or application that has access to a network. This includes computers, laptops, smartphones, tablets, servers, printers, Internet of Things (IoT) devices, and even virtual machines or cloud instances. Essentially, any device or software that can connect to a network is considered an endpoint.
Endpoints as Vulnerabilities
Endpoints are highly attractive targets for cybercriminals because they provide direct entry points into networks. Their popularity as targets is due to a variety of reasons. Firstly, endpoints often have a large attack surface, meaning they have multiple potential vulnerabilities that can be exploited. For example, outdated operating systems or unpatched software on endpoints can create significant weaknesses.
Moreover, endpoints frequently interact with external networks and receive and transmit data, making them more susceptible to malware infiltration, data breaches, and other cyber attacks. Cybercriminals exploit these weaknesses to gain unauthorized access to networks, steal sensitive information, or even launch more complex attacks like ransomware.
Endpoints and the Zero Trust Model
Traditionally, cybersecurity strategies have focused on perimeter defenses to keep threats out of the network. However, with the rise of remote work and the increasing use of cloud-based services, the concept of the perimeter has become less defined. This is where the Zero Trust model comes into play.
Zero Trust is a security framework that assumes no trust, even for devices within the network perimeter. It emphasizes verifying every user and device attempting to access network resources, regardless of their location or whether they are internally or externally connected.
Endpoints are critical components of the Zero Trust model. Organizations need to adopt a holistic approach to endpoint security by implementing measures such as device identity verification, strict access controls, continuous monitoring, and encryption to ensure the security of endpoints and the entire network.
Effective Endpoint Security Measures
To strengthen endpoint security, organizations should consider implementing the following measures:
1. Regular Software Updates and Patch Management: Keeping endpoints up to date with the latest security patches and software updates is crucial. These updates often contain essential security fixes that protect against known vulnerabilities.
2. Endpoint Protection Platforms (EPPs) and Endpoint Detection and Response (EDR): EPPs provide real-time protection against viruses, malware, and other threats. EDR solutions, on the other hand, are proactive systems that monitor and respond to suspicious activities on endpoints.
3. Multi-factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to provide multiple pieces of evidence, such as a password and a unique code sent to their mobile device, before gaining access to the network.
4. Data Encryption: Encrypting sensitive data both at rest and in transit ensures that even if it falls into the wrong hands, it remains unreadable and unusable.
5. User Education and Awareness: Regularly training users to recognize potential threats, identify phishing attempts, and follow best security practices can significantly reduce the risk of successful attacks.
FAQs
1. Why are endpoints vulnerable to cyber attacks?
Endpoints often have multiple potential vulnerabilities, such as outdated software or misconfigurations. Additionally, they frequently interact with external networks and transmit data, making them attractive targets for cybercriminals.
2. What is the Zero Trust model?
The Zero Trust model assumes no trust, even for internal devices. It emphasizes verifying every user and device attempting to access network resources, regardless of their location or connectivity.
3. What are the critical components of endpoint security?
Endpoint security should include regular software updates, endpoint protection platforms, multi-factor authentication, data encryption, and user education and awareness.
4. Why are software updates and patches important for endpoint security?
Software updates and patches often include essential security fixes that protect against known vulnerabilities. By keeping endpoints updated, organizations reduce the risk of successful attacks.
5. How can user education and awareness contribute to endpoint security?
Regularly training users to identify potential threats, such as phishing attempts, and teaching them best security practices can significantly reduce the risk of successful attacks, as users become more cautious and vigilant.
What Is A Function Of An Endpoint On A Network
In the world of computer networks, an endpoint refers to a device or a node that is connected to a network, either physically or wirelessly. Endpoints are crucial components of networks as they enable communication between users or devices and the network itself. They play a vital role in facilitating the flow of data and ensuring seamless connectivity. This article aims to delve into the functions of endpoints on a network, providing a comprehensive understanding of their importance and operation.
Functions of Endpoints:
1. Data Transmission:
The primary function of an endpoint is to transmit and receive data over a network. By establishing a connection to the network, endpoints become capable of sending and receiving information, allowing users or devices to communicate and share data with one another. This enables the transfer of files, messages, images, and various types of media, contributing to efficient collaboration and information exchange.
2. Network Access Control:
Endpoints act as gateways that regulate access to the network. They control who can join or leave the network, ensuring security and privacy. Network administrators can implement protocols and authentication mechanisms on endpoints to verify the identity and credentials of users or devices trying to connect. This helps protect the network from unauthorized access, preventing potential security breaches.
3. Addressing and Routing:
Endpoints are assigned unique network addresses, such as Internet Protocol (IP) addresses, which serve as identifiers for their location on the network. These addresses enable the routing of data packets to the appropriate endpoint, ensuring that information is sent to the intended recipient. Routing algorithms determine the optimal path for data transmission, allowing endpoints to receive incoming data packets efficiently.
4. Network Monitoring and Management:
Endpoints play a crucial role in network monitoring and management. They provide valuable information about network performance, usage patterns, and potential issues. Monitoring software installed on endpoints allows network administrators to track network traffic, identify bottlenecks, and detect any anomalies or suspicious activities. This data aids in maintaining network reliability, optimizing performance, and addressing any network-related problems promptly.
5. Service Access and Provision:
Certain endpoints function as gateways to network services and resources. For example, servers and routers are endpoints that provide specific services to other devices connected to the network. Servers store and deliver files or web pages, while routers direct network traffic. These endpoints act as intermediaries, facilitating access to network services by forwarding requests and delivering responses.
6. Collaboration and Communication:
Endpoints enable collaboration and communication within a network. Through endpoints like computers, laptops, smartphones, or IP telephones, users can participate in online meetings, video conferences, or instant messaging. Such endpoints offer various communication tools and applications, enhancing productivity and fostering effective collaboration between individuals or teams.
FAQs:
Q: Are endpoints only limited to devices used by individuals?
A: No, endpoints can also include machines or devices connected to the network for specific purposes, such as Internet of Things (IoT) devices used in smart homes or industrial systems.
Q: How does endpoint security work?
A: Endpoint security involves implementing measures to protect endpoints from external threats, such as malware or unauthorized access. This can be achieved through antivirus software, firewalls, encryption, intrusion detection systems, and network access controls.
Q: Can an endpoint connect to multiple networks simultaneously?
A: Yes, some endpoints have the capability to connect to multiple networks. For instance, a modern laptop can connect to both a wired Ethernet network and a wireless network simultaneously.
Q: How do endpoints contribute to network scalability?
A: Endpoints play a vital role in network scalability as they can be easily added or removed from the network. This facilitates the expansion or contraction of network capacity to accommodate changing requirements.
Q: What is the difference between endpoints and network infrastructure?
A: Endpoints are typically user-facing devices that facilitate communication, data transmission, and accessing network services. On the other hand, network infrastructure consists of routers, switches, servers, and other devices that provide the underlying framework for network connectivity and operations.
In conclusion, endpoints are fundamental components of any computer network, serving various essential functions. They facilitate data transmission, control network access, address and route traffic, enable network monitoring, provide access to services, and foster collaboration and communication. Understanding the role and significance of endpoints is crucial for building and managing efficient and secure networks.
Images related to the topic what is an endpoint

Found 40 images related to what is an endpoint theme
.png?width=650&name=api%20endpoint%20(update%20722).png)





















Article link: what is an endpoint.
Learn more about the topic what is an endpoint.
- What is an API Endpoint? | SmartBear Software Resources
- What Is an Endpoint? | Microsoft Security
- What is an Endpoint & How Endpoint Security Works – Webroot
- What is Web Endpoint and how it can be monitored? | BizTalk360 Blogs
- What Is an Endpoint? | Microsoft Security
- What is an Endpoint? – Palo Alto Networks
- What is an endpoint? | Endpoint definition – Cloudflare
- What is an API Endpoint? | SmartBear Software Resources
- What is an Endpoint & How Endpoint Security Works – Webroot
- What Is an Endpoint? Definition & Examples – CrowdStrike
- A simple definition: what is an endpoint? – Druva
- What is an Endpoint Security and its Definition? – Xcitium
- What is an Endpoint? | Security Encyclopedia – HYPR
- What is an Endpoint? – Mitigo Cyber Security
See more: https://nhanvietluanvan.com/luat-hoc