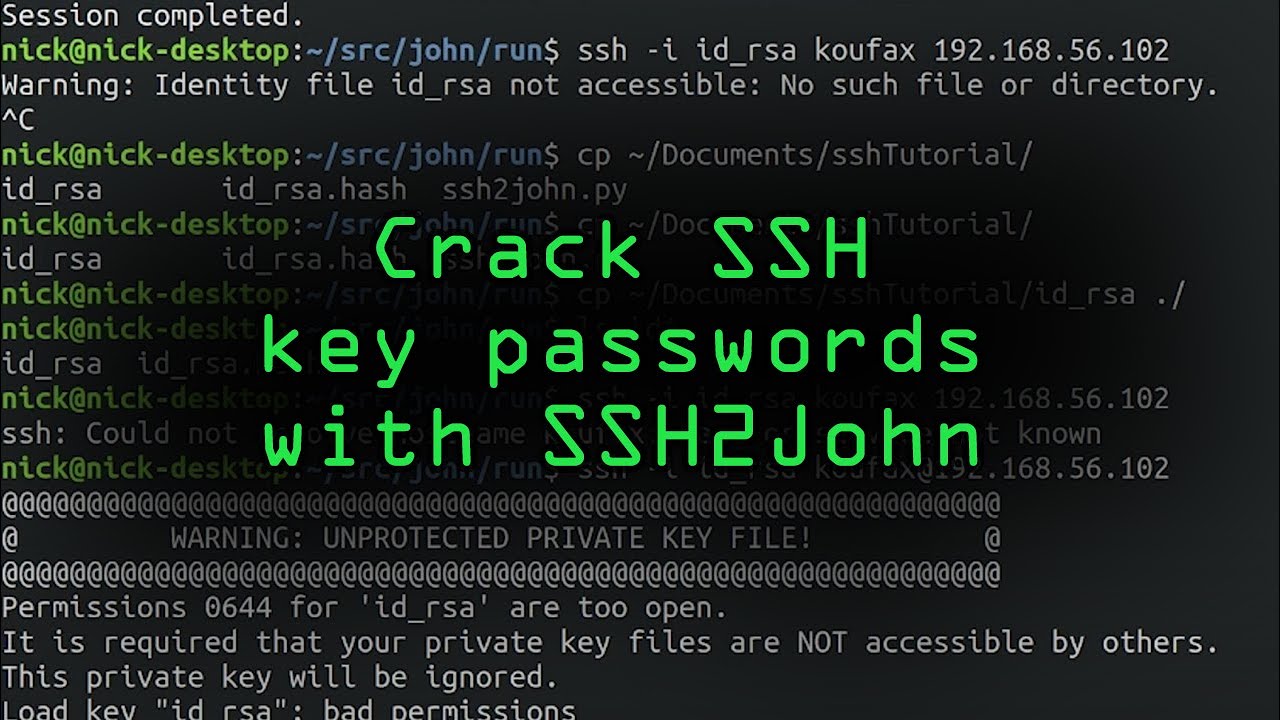
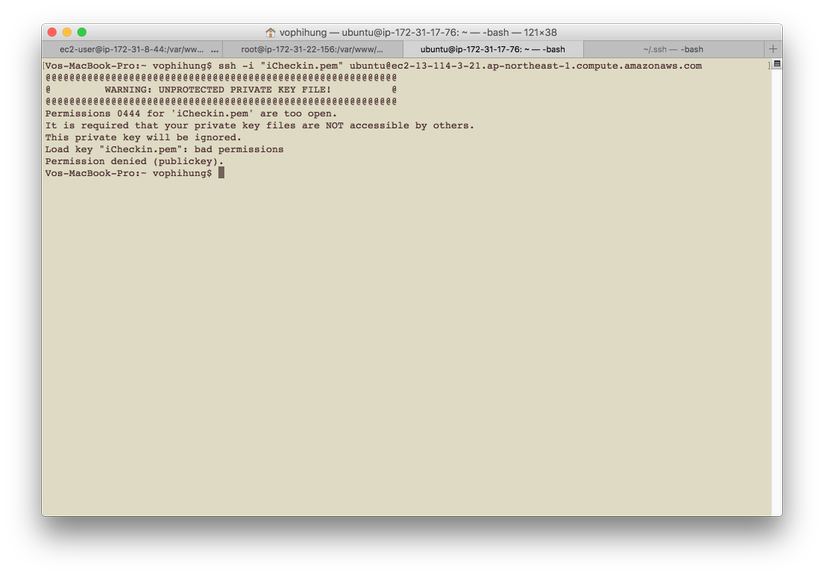
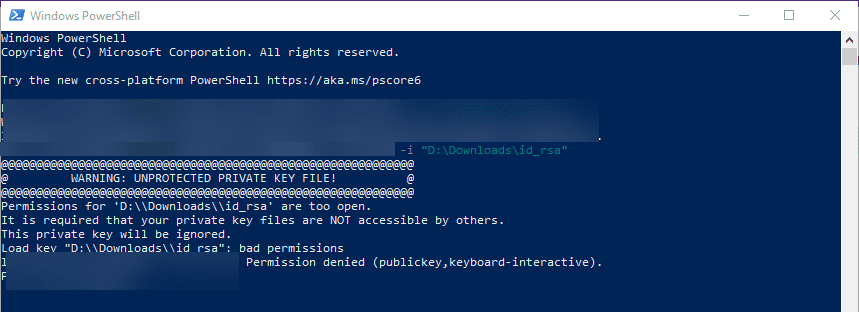
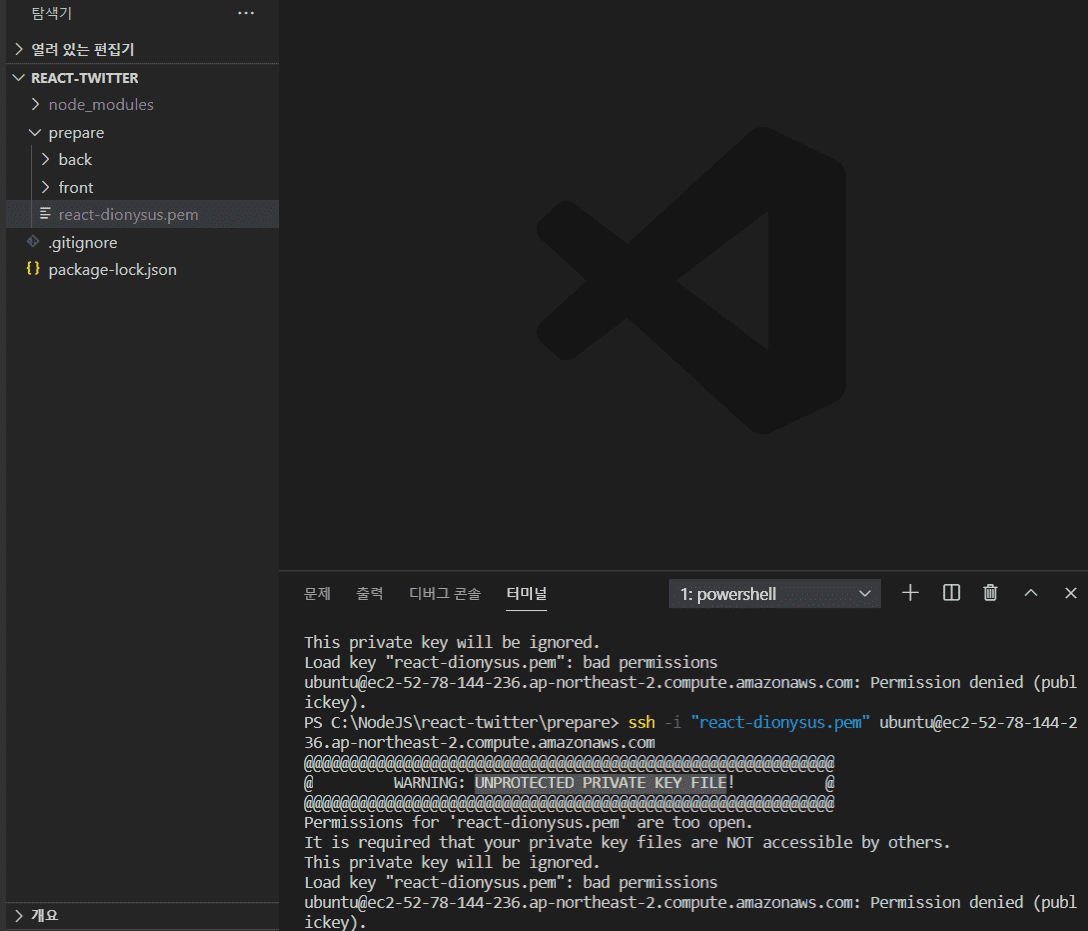
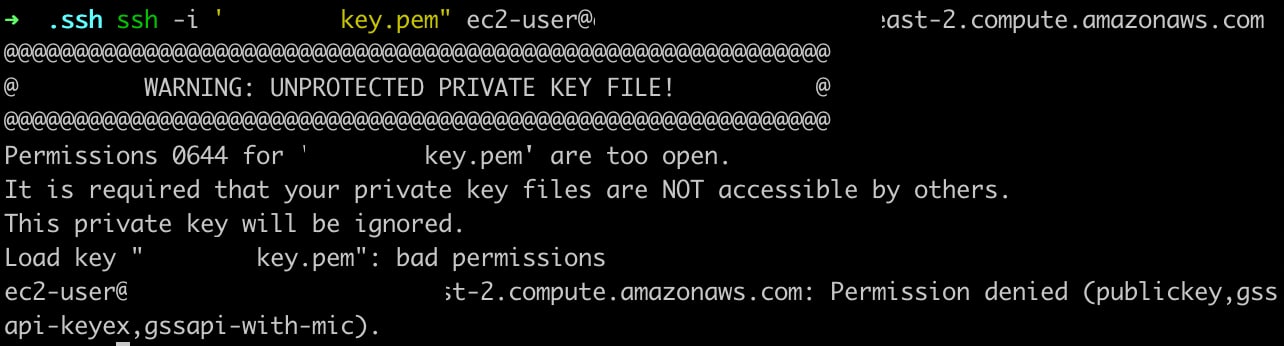
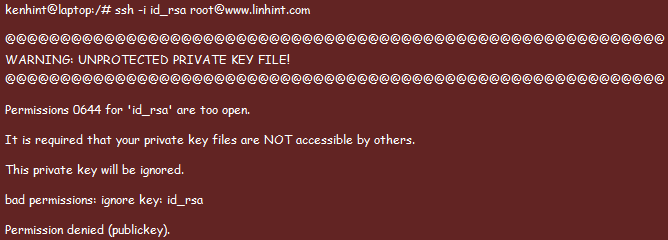
Warning Unprotected Private Key File
Introduction:
In the digital age, where data security is paramount, the protection of private key files is of utmost importance. Unprotected private key files can lead to severe consequences, including unauthorized access, data breaches, and financial losses. This article will explore the risks associated with unprotected private key files and provide security measures, encryption techniques, and best practices to safeguard them. Additionally, we will discuss the consequences of mishandling or losing a private key file and steps to take in case of a compromise.
1. Understanding the Role of a Private Key File:
A private key file is a crucial component in public-key cryptography, enabling secure communication and data transmission. It is paired with a public key file, and together they form a cryptographic key. While the public key is shared openly, the private key must be kept confidential, as it allows the owner to decrypt data, sign digital signatures, and authenticate their identity.
2. Common Risks Associated with Unprotected Private Key Files:
Unprotected private key files pose several potential risks, including:
2.1 Unauthorized Access: If a malicious actor gains access to an unprotected private key file, they can impersonate the owner, decrypt sensitive data, and perform unauthorized actions.
2.2 Data Breaches: A compromised private key file can result in the exposure of sensitive information, leading to significant reputational damage, legal liabilities, and financial implications.
2.3 Financial Losses: Attackers who gain access to private key files can initiate unauthorized transactions, resulting in monetary losses for individuals or organizations.
3. Security Measures to Safeguard your Private Key File:
To ensure the protection of your private key file, consider implementing the following security measures:
3.1 Strong Password Protection: Encrypt your private key file with a strong password that is unique and not easily guessable.
3.2 Two-Factor Authentication (2FA): Enable 2FA to add an extra layer of security to your private key file by requiring an additional authentication factor.
3.3 Secure Storage: Store your private key file in an encrypted and password-protected location, ensuring it is not accessible to unauthorized individuals.
4. Encryption Techniques for Protecting Private Key Files:
Utilizing encryption techniques is vital for safeguarding private key files. Two commonly used encryption methods include:
4.1 Symmetric Encryption: Symmetric encryption uses a single key to both encrypt and decrypt your private key file. Ensure the key used for encryption is stored securely.
4.2 Asymmetric Encryption: Asymmetric encryption involves two keys – a public key for encrypting data and a private key for decrypting it. Protect the private key file with strong encryption methods and restrict access to it.
5. Best Practices for Storing and Managing Private Key Files:
Follow these best practices to maintain the security of your private key files:
5.1 Regular Backups: Create secure backups of your private key files and store them separately from the originals.
5.2 Secure Transmission: When transmitting private key files, use secure channels such as SSH or VPN protocols to prevent interception or tampering.
5.3 Controlled Access: Limit and carefully manage access to private key files, granting permissions only to trusted individuals or systems.
6. Regular Monitoring and Auditing of Private Key File Security:
Regularly monitoring and auditing your private key files is crucial to maintaining their security. Implement the following practices:
6.1 Log Monitoring: Monitor activities related to private key file access, modifications, and usage. Any suspicious or unauthorized activities should be immediately addressed.
6.2 Periodic Auditing: Conduct routine audits to ensure adherence to security policies and identify any vulnerabilities or weaknesses.
7. Consequences of Mishandling or Losing the Private Key File:
Mishandling or losing a private key file can have severe repercussions:
7.1 Unauthorized Access and Data Breach: An unprotected or lost private key file provides unauthorized individuals with the means to access sensitive data and compromise confidentiality.
7.2 Financial Losses and Legal Liabilities: The misappropriation of private key files can lead to financial losses, legal issues, and damage to an individual or organization’s reputation.
8. Steps to Take in Case of Private Key File Compromise:
If you suspect your private key file has been compromised, take immediate action:
8.1 Disable and Replace: Disable the compromised key and generate a new one. Update all systems and services that rely on the key.
8.2 Inform Relevant Parties: Notify relevant individuals or organizations that had access to the compromised key to prevent further unauthorized access.
FAQs:
Q1. What is the “Aws warning unprotected private key file” error message?
A1. The “Aws warning unprotected private key file” error message indicates that your private key file is not properly protected and can be accessed by others. It is essential to secure your private key file to prevent unauthorized access.
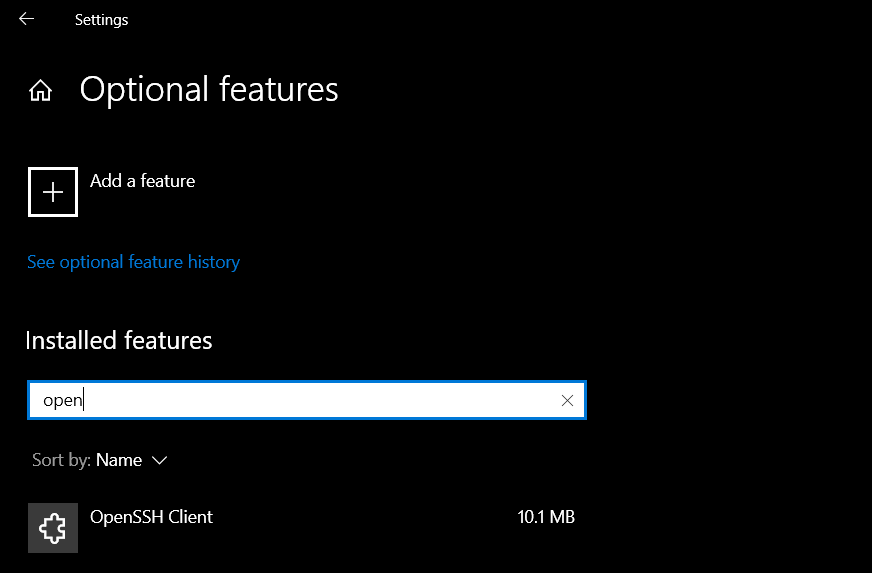
Q2. How can I remove an SSH key from Windows 10?
A2. To remove an SSH key from Windows 10, navigate to the directory where the key is stored and delete the corresponding key file.
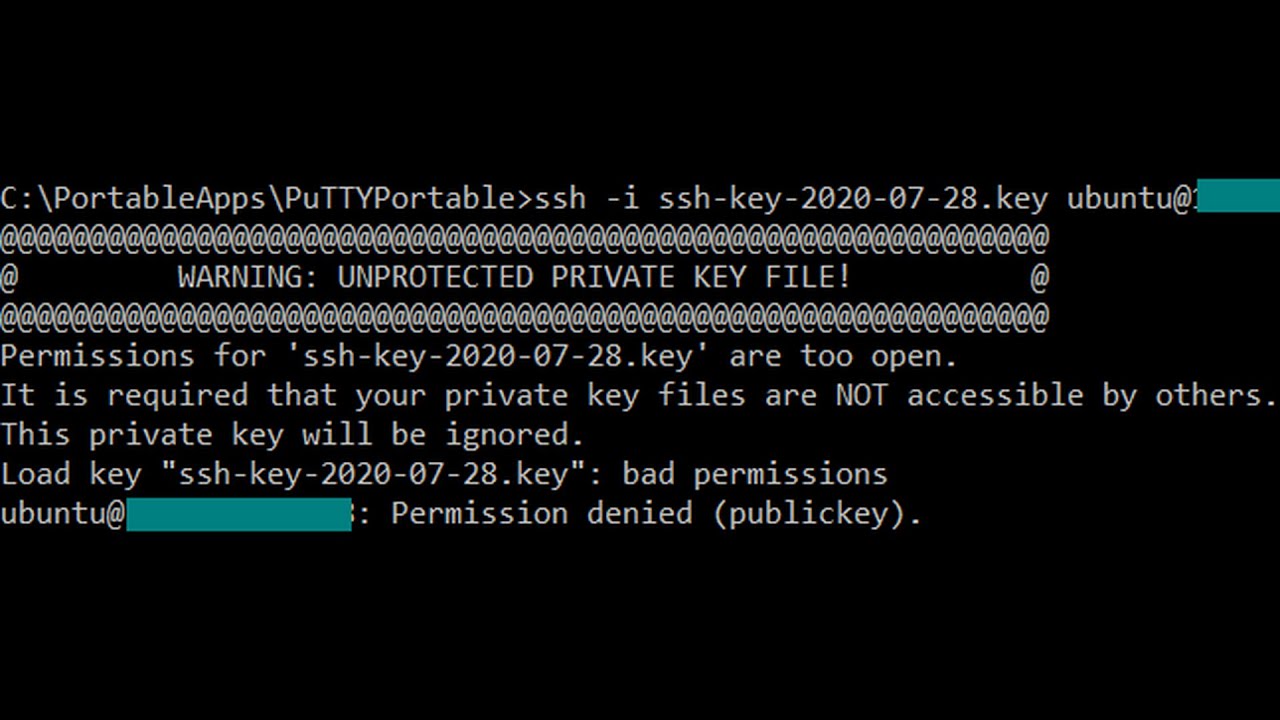
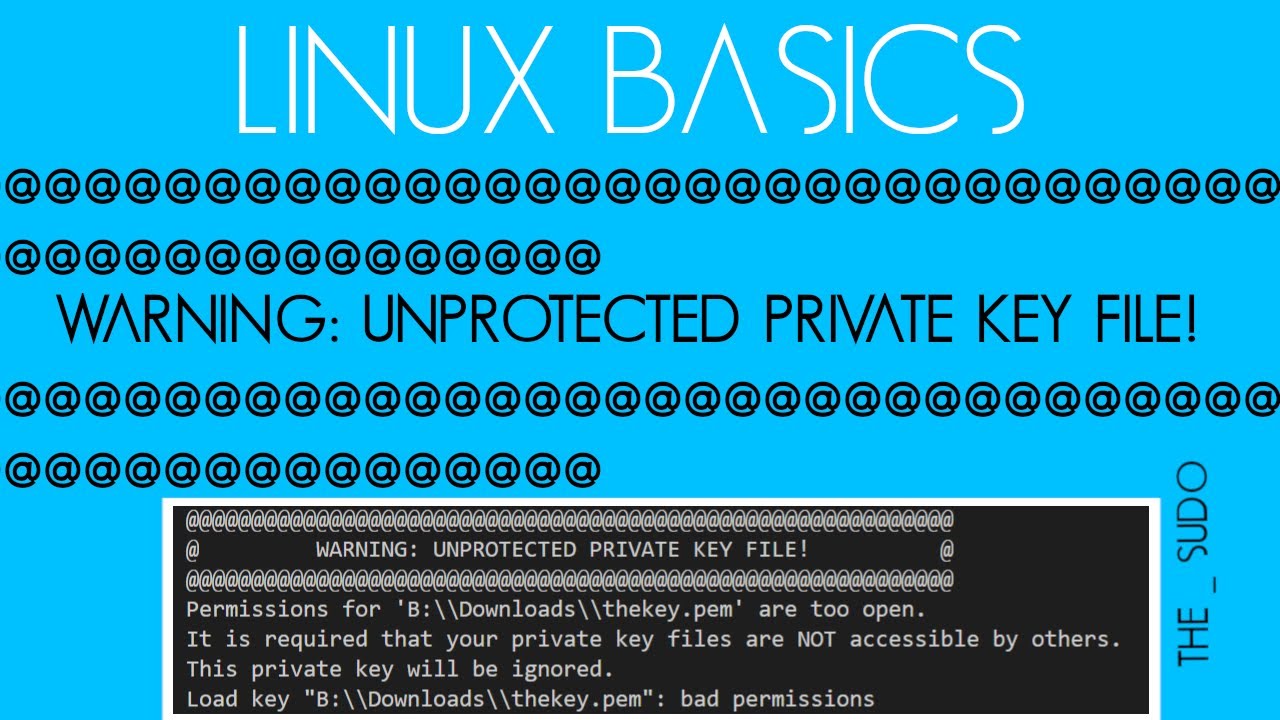
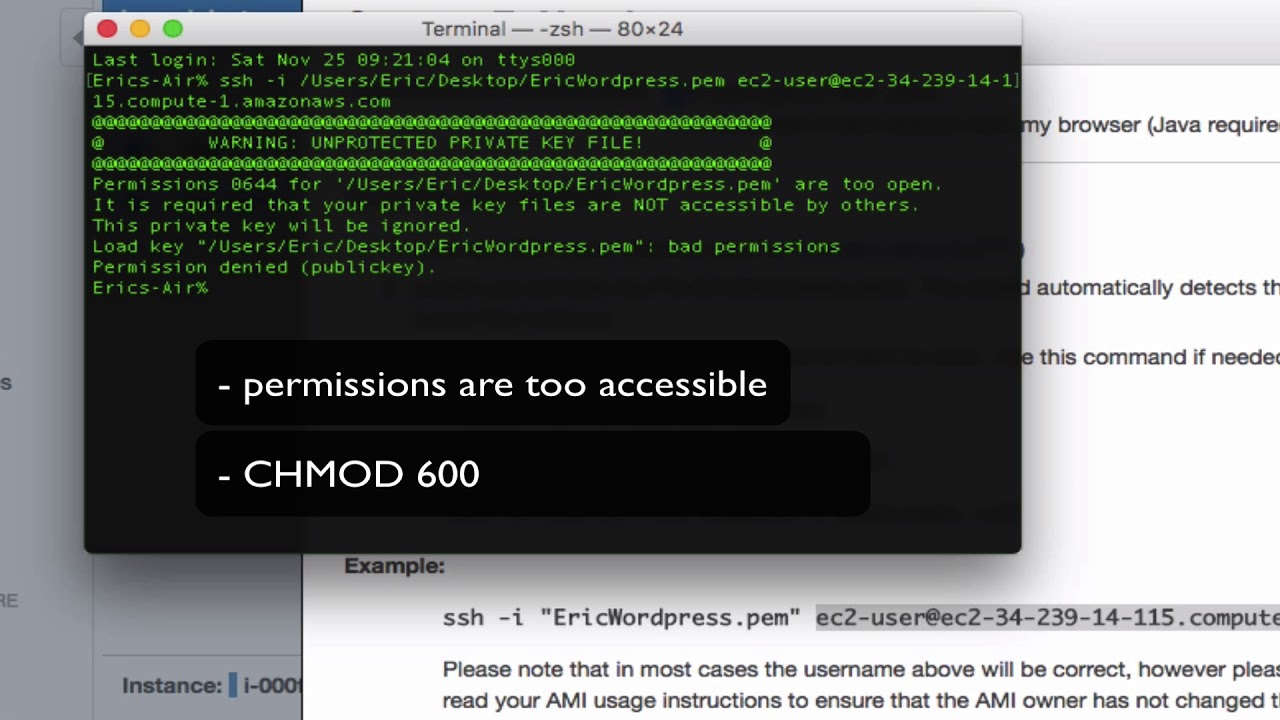
Q3. What does “Load key bad permissions, it is required that your private key files are not accessible by others” mean?
A3. The “Load key bad permissions” error message signifies that the permissions on your private key file are not properly set, and it is accessible by others. Ensure that the correct permissions are in place to restrict access to your private key file.
Q4. What should I do if my private key file is in an invalid format?
A4. If your private key file is in an invalid format, you may need to regenerate a new key file or convert it into the appropriate format using tools or software designed for key conversion.
In conclusion, protecting your private key file is crucial to maintaining data security and preventing unauthorized access. By implementing strong security measures, encryption techniques, and best practices, you can greatly reduce the risks associated with unprotected private key files. Regular monitoring, auditing, and swift response to compromises are essential to maintaining the integrity of your private key files and ensuring a secure digital environment.
How To Resolve \”Warning: Unprotected Private Key File\” Error In Aws Ec2.
Keywords searched by users: warning unprotected private key file Aws warning unprotected private key file, Load key bad permissions, it is required that your private key files are not accessible by others., Load key invalid format, permission denied (publickey,gssapi-keyex,gssapi-with-mic)., Remove ssh key, Remove SSH key Windows 10, Key is invalid you must supply a key in OpenSSH public key format
Categories: Top 78 Warning Unprotected Private Key File
See more here: nhanvietluanvan.com
Aws Warning Unprotected Private Key File
As businesses increasingly move their operations to the cloud, Amazon Web Services (AWS) has emerged as a leading provider of secure and scalable cloud computing solutions. However, it’s important to note that even the most robust systems can fall victim to security vulnerabilities if not properly maintained and protected. One such vulnerability that AWS users should be aware of is the warning regarding unprotected private key files.
Private key files, often referred to as SSH keys, are a critical component of securing remote access to AWS instances. These keys help authenticate remote connections and establish secure communication between a user’s computer and the AWS infrastructure. If a private key file falls into the wrong hands, it can provide unauthorized access to sensitive data and lead to potential security breaches.
AWS takes security seriously and provides users with stern warnings if they identify any unprotected private key files within their infrastructure. Such warnings are typically generated when AWS discovers that the private key files associated with an account are publicly accessible or stored in an insecure location. Users must address these warnings promptly to prevent potential security lapses.
There are several reasons why private key files might be left unprotected. Sometimes, administrators accidentally leave these files in publicly accessible directories or share them with unauthorized parties. Other times, key pairs might be compromised through various cyber-attacks. Regardless of the reason, it’s crucial to rectify the situation quickly to minimize the risk of unauthorized access.
To address the issue of unprotected private key files, AWS suggests taking a series of preventive measures. Firstly, users must avoid storing keys in publicly accessible locations such as websites or GitHub repositories. Secondly, it is highly recommended to regularly rotate key pairs and delete any unnecessary key files. Additionally, implementing multi-factor authentication adds an extra layer of security and reduces the chances of unauthorized access.
FAQs:
1. What should I do if I receive a warning regarding unprotected private key files from AWS?
Upon receiving a warning, take immediate action to secure your private key files. Start by locating the unprotected files and ensure they are no longer publicly accessible. Consider rotating key pairs to ensure old keys are no longer used. Finally, implement additional security measures like multi-factor authentication.
2. How can I prevent my private key files from being exposed?
To prevent exposure, avoid storing private key files in publicly accessible locations or sharing them with unauthorized parties. Store keys securely and consider using a password manager or encrypted storage methods. Regularly review access permissions and remove any unnecessary keys to further reduce the risk.
3. Are there any tools or services provided by AWS to help with managing private key files?
AWS provides various tools and services to assist with the management of private key files. AWS Systems Manager Parameter Store and AWS Secrets Manager are two services that offer secure storage and retrieval of secrets, including private key files. These services help keep your keys protected and offer additional features like access control and auditing.
4. Can I recover a compromised private key?
If a private key file is compromised, it is crucial to take immediate action. Contact AWS support and alert them about the security breach. They will guide you through the steps required to mitigate the risk, which may include rotating key pairs, revoking the compromised key, and investigating the cause of the breach.
5. Is protecting private key files the sole responsibility of the user?
The responsibility for protecting private key files lies with both AWS and the user. AWS ensures the security of its infrastructure, while users must take necessary precautions to secure their own data. AWS provides warnings and best practices to help users maintain an effective security posture, but it is the user’s responsibility to implement and follow these guidelines.
In conclusion, the warning from AWS regarding unprotected private key files underscores the importance of maintaining robust security practices within the cloud computing environment. Storing private key files securely, regularly rotating keys, implementing multi-factor authentication, and promptly addressing any warnings are essential steps in strengthening the security of AWS instances. By adopting these practices, businesses can enhance their overall security posture and safeguard against potential breaches.
Load Key Bad Permissions
SSH Key-Based Authentication:
SSH key-based authentication is a more secure alternative to traditional password-based authentication. It involves the use of key pairs – a public key and a private key. The public key is placed on the server, while the private key is stored on the client-side machine. When a connection to the server is initiated, the client presents its private key as proof of identity, and the server verifies it against the corresponding public key. If the keys match, the server allows access without the need for a password.
Importance of File Permissions:
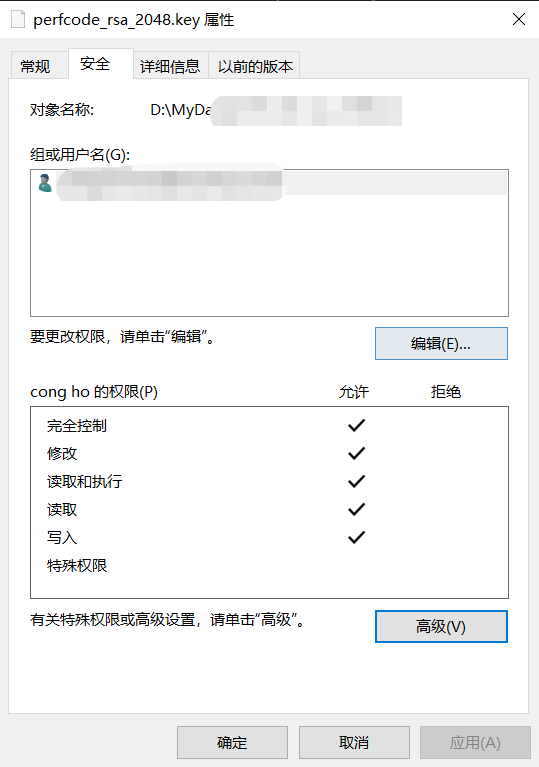
In the context of SSH key-based authentication, file permissions play a crucial role in maintaining the security of the private key. If the permissions are set incorrectly, it could potentially allow unauthorized access to the private key, compromising the entire authentication process.
The permissions on the private key file should be restrictive, and it should be accessible only by the owner. Typically, the recommended permission setting is 400 or 600, which ensures that only the owner can read and write to the file, while everyone else is denied access. Setting insecure permissions, such as 777, allows anyone on the system to access the private key, defeating the purpose of using SSH key-based authentication.
Causes of Load Key Bad Permissions Error:
There can be several causes for the load key bad permissions error. Here are some common scenarios:
1. Incorrect permission settings: As mentioned earlier, incorrect file permissions can trigger this error. If the private key file’s permissions are not set to a secure value, the SSH client will refuse to load the key.
2. Ownership issues: The private key file should be owned by the user who intends to use it. If the file is owned by a different user or root, the SSH client will consider it insecure and prevent loading the key.
3. Incorrect file location: SSH expects the private key file to be located in the .ssh directory in the user’s home directory. If the file is placed in a different location or has an incorrect filename, the SSH client will fail to load the key.
Solutions to Load Key Bad Permissions Error:
To resolve the load key bad permissions error, follow these steps:
1. Verify file permissions: Ensure that the private key file’s permissions are correctly set. Use the chmod command to adjust the permissions if necessary. For example, to set the recommended permission of 400, use: `chmod 400 /path/to/private_key`.
2. Adjust file ownership: Ensure that the private key file is owned by the correct user. You can use the chown command to change the ownership. For example, to change ownership to the user “john,” use: `chown john /path/to/private_key`.
3. Confirm file location and filename: Make sure that the private key file is located in the .ssh directory in the user’s home directory. Additionally, verify that the file name matches the default naming convention (id_rsa for RSA keys).
Frequently Asked Questions:
Q1. Can load key bad permissions error occur if I specify the private key location using the -i flag?
A1. No, the load key bad permissions error typically occurs when the SSH client tries to use the default private key file located in the .ssh directory. However, if you explicitly specify the private key location using the -i flag, make sure to check the permissions and ownership of that file.
Q2. I have verified the file permissions, ownership, and location, yet the error still persists. What could be the issue?
A2. In some cases, the issue could be related to the file system’s security context. Use the `ls -Z` command to view the SELinux context of the private key file. If it differs from the expected context, use the `chcon` command to set the correct context.
Q3. I am using a passphrase-protected private key. Could that be causing the error?
A3. No, the load key bad permissions error is unrelated to passphrase protection. It specifically refers to incorrect file permissions.
Q4. Are there any other common SSH key authentication errors I should be aware of?
A4. Yes, apart from the load key bad permissions error, you may also encounter errors like “Permission denied (publickey)” or “Too many authentication failures.” These errors have different causes and solutions.
In conclusion, load key bad permissions error can be resolved by ensuring the correct file permissions, ownership, and location of the private key file. By adhering to secure practices and being mindful of file permissions, you can enhance the security and effectiveness of SSH key-based authentication.
It Is Required That Your Private Key Files Are Not Accessible By Others.
Introduction:
In the world of digital security, protecting our valuable information is of utmost importance. One key component of secure communication is the use of private key files. These files play a crucial role in many encryption algorithms and are essential for maintaining confidentiality and authenticity. However, it is equally vital to ensure that these private key files remain secure and inaccessible to any unauthorized individuals. In this article, we will delve into the significance of keeping your private key files out of reach and explore different methods to achieve optimal security.
Understanding Private Key Files:
Private key files are a vital element in asymmetric encryption algorithms such as RSA. They are generated as a pair with a corresponding public key that is openly shared. These key pairs are used to encrypt and decrypt sensitive data. The private key file, as the name suggests, should be kept private and confidential to maintain the integrity of the encryption system. If compromised, unauthorized individuals can gain access to encrypted data, compromising its security.
The Dangers of Unauthorized Access:
1. Breach of Confidentiality: Private key files grant access to encrypted data. If obtained by malicious entities, these files can be used to decrypt sensitive information, jeopardizing confidentiality.
2. Impersonation Attacks: If someone gains unauthorized access to your private key files, they can potentially impersonate you or your organization. This can lead to serious consequences, such as unauthorized actions, compromised accounts, or reputation damage.
3. Tampering with Data Integrity: When utilizing private key files, data integrity is ensured through digital signatures. If unauthorized individuals gain access, they can modify the data and re-sign it with the stolen private key, making the falsified data appear legitimate.
Securing Your Private Key Files:
1. Password Protection: The simplest and most widely used method is to assign strong, complex passwords to your private key files. These passwords should be kept confidential and not shared with anyone. Implementing two-factor authentication adds an extra layer of security.
2. Encryption: Encrypting your private key files provides an additional level of protection. Utilize strong encryption algorithms like AES (Advanced Encryption Standard) with long, random passwords. Make sure to store your encrypted private keys in secure storage.
3. Secure File Permissions: Restrict file access by assigning appropriate permissions. Only grant read and write access to trusted users or applications, while denying access to any other entities. Regularly review and update these permissions to prevent unauthorized access.
4. Secure Storage: Store your private key files in hardware security modules (HSMs) or dedicated hardware devices designed specifically for secure key storage. These physical devices protect your private keys from unauthorized access and tampering.
5. Regular Backups: Maintain secure backups of your private key files in encrypted form. Store these backups in multiple locations, preferably with offline or cloud-based backup solutions. Regularly test the restoration process to ensure their integrity.
FAQs:
1. What happens if my private key files are compromised?
If your private key files are compromised, unauthorized individuals may gain access to encrypted data, potentially leading to data breaches and privacy violations. It is crucial to immediately revoke compromised keys, generate new ones, and take appropriate measures to safeguard the affected systems.
2. Should I share my private key files?
No, private key files should never be shared. Remember, the public key is intended for sharing, while the private key must remain exclusively in your possession.
3. Can I recover my private key files if lost?
Generally, private key files cannot be recovered if lost or accidentally deleted. Losing these files would mean losing access to any encrypted data associated with the key pair. It is therefore advisable to keep multiple secure backups and consider key escrow services to prevent permanent loss.
4. Are longer private keys more secure?
Yes, longer private keys provide increased security against cryptographic attacks. Modern encryption algorithms typically recommend a key length of 2048 bits or more. Longer keys require significantly more computational power to be compromised, thus enhancing security.
Conclusion:
Securing your private key files is paramount in maintaining the confidentiality, authenticity, and integrity of your encrypted communication. By implementing the aforementioned measures, such as strong passwords, encryption, secure storage, and restricted access, you can significantly mitigate the risks associated with unauthorized access. Regularly reviewing and reinforcing your security measures will ensure that your private key files remain inaccessible to malicious entities, providing peace of mind in the digital realm.
Images related to the topic warning unprotected private key file

Found 9 images related to warning unprotected private key file theme
![Warning Unprotected Private Key File AWS EC2 Error [Solved] | bobbyhadz Warning Unprotected Private Key File Aws Ec2 Error [Solved] | Bobbyhadz](https://bobbyhadz.com/images/blog/aws-ec2-warning-unprotected-private-key-file/unprotected-private-key-file-error.webp)


![Warning Unprotected Private Key File AWS EC2 Error [Solved] | bobbyhadz Warning Unprotected Private Key File Aws Ec2 Error [Solved] | Bobbyhadz](https://bobbyhadz.com/images/blog/aws-ec2-warning-unprotected-private-key-file/banner.webp)









![SOLVED] WARNING Unprotected Private RSA Pem Key File Ansible EC2 Windows Ubuntu Debian - YouTube Solved] Warning Unprotected Private Rsa Pem Key File Ansible Ec2 Windows Ubuntu Debian - Youtube](https://i.ytimg.com/vi/CLaz2DmXtuI/maxresdefault.jpg)




















Article link: warning unprotected private key file.
Learn more about the topic warning unprotected private key file.
- Getting “Warning: unprotected private key file!” error message …
- Sửa lỗi WARNING: UNPROTECTED PRIVATE KEY FILE!
- How to resolve the “SSH Unprotected Private Key File” warning
- Fixing UNPROTECTED PRIVATE KEY FILE.md – GitHub Gist
- WARNING: UNPROTECTED PRIVATE KEY FILE! – LinkedIn
- How to Fix “WARNING: UNPROTECTED PRIVATE KEY FILE …
- Warning Unprotected Private Key File AWS EC2 Error [Solved]
- SSH error: permissions are too open – Educative.io
- Unprotected Private Key File” on Windows 10 – Super User
See more: https://nhanvietluanvan.com/luat-hoc