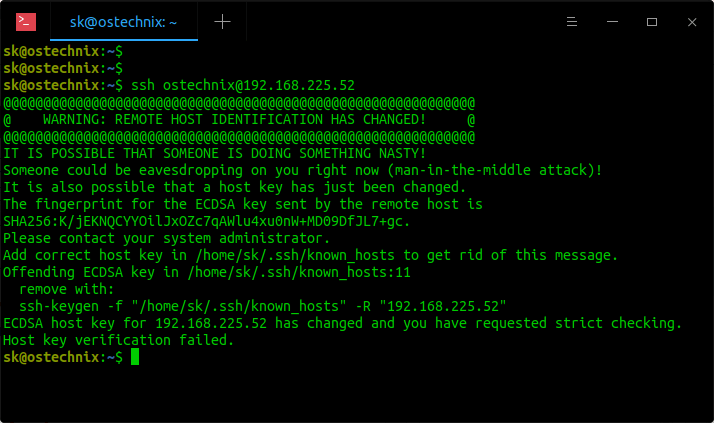
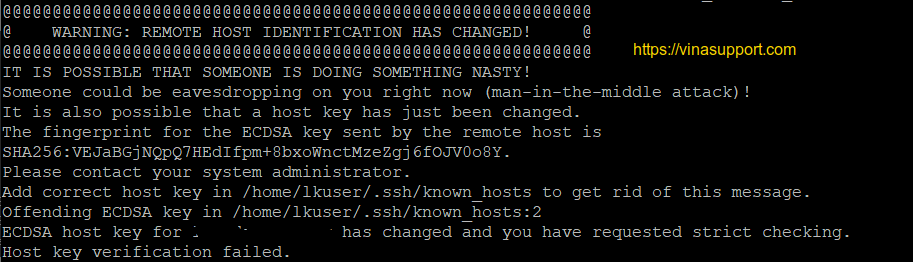
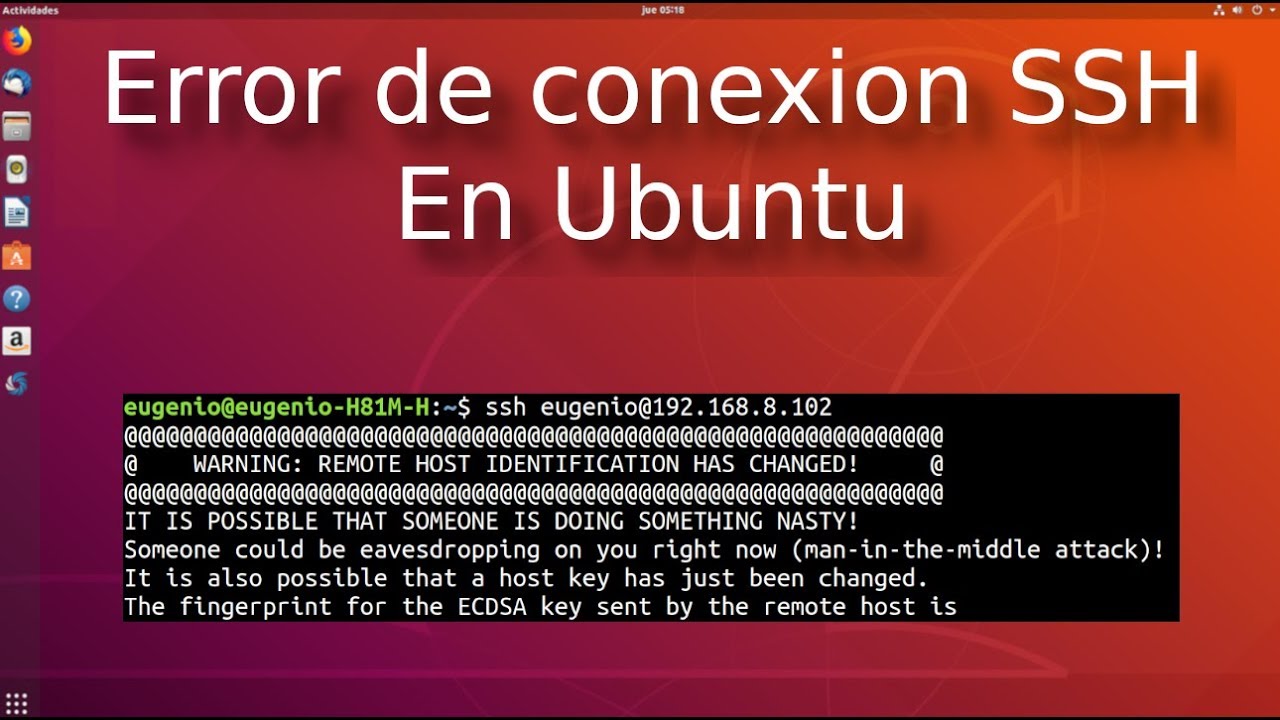
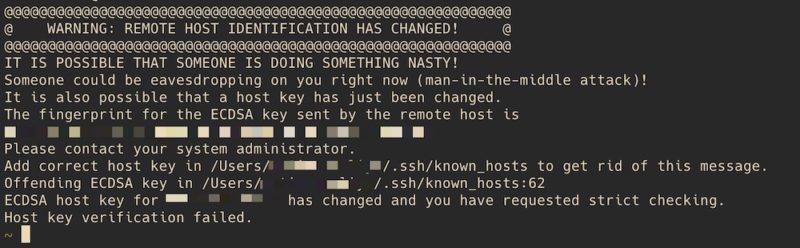
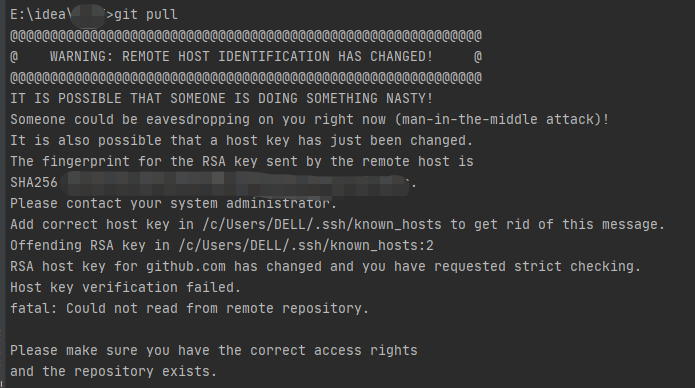
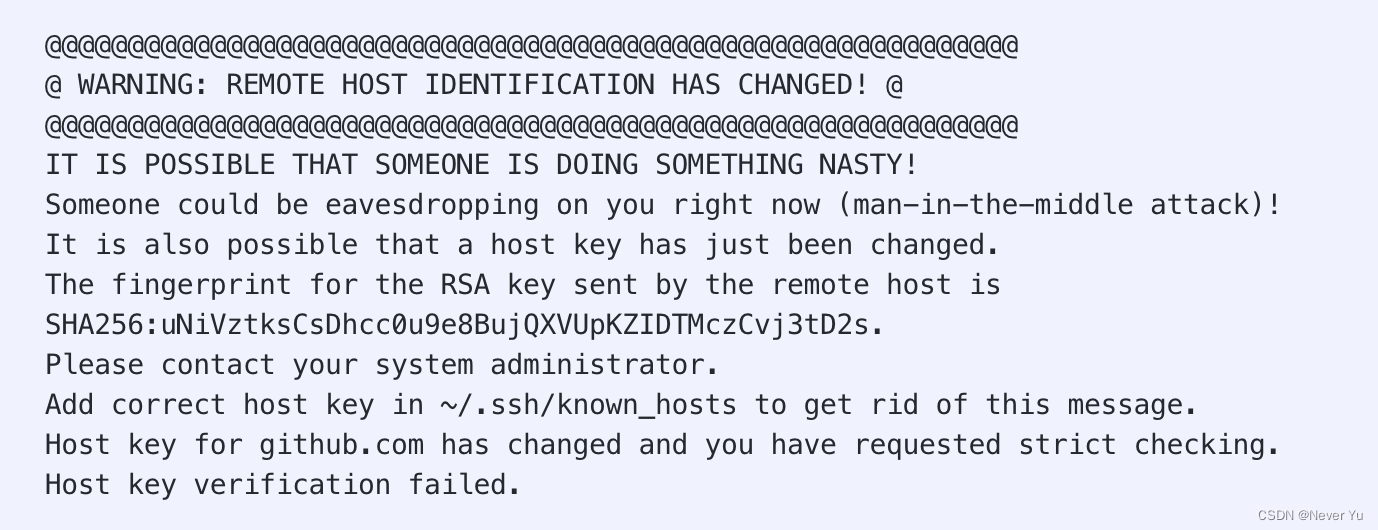
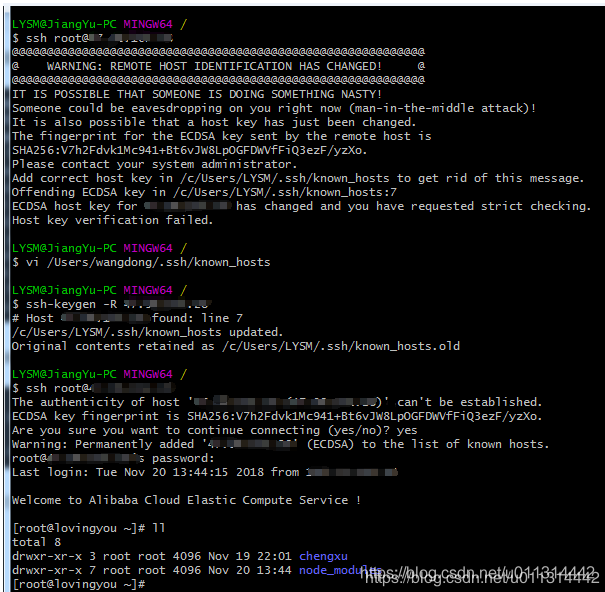
Warning: Remote Host Identification Has Changed
When working with remote hosts, you may encounter a warning message stating “Warning: Remote Host Identification Has Changed.” This warning indicates that the identity or configuration of the remote host has changed since your last connection. It is crucial to understand the causes, implications, and appropriate responses to this warning in order to maintain the security and integrity of your system.
Causes of the “Warning: Remote Host Identification Has Changed” message:
1. IP address change: If the remote host has acquired a new IP address, it can trigger the warning. This could happen due to network reconfigurations or a change in the host’s network connection.
2. Reinstallation or reconfiguration of the remote host: If the remote host has undergone a reinstallation or reconfiguration process, it can result in a change in its identification. This can occur when the host’s operating system is updated or modified.
3. DNS changes: Any modifications made to the Domain Name System (DNS) configuration, such as changes in hostname or IP mapping, can cause the warning. It is important to ensure that your DNS settings are up to date and accurate.
4. Network configuration changes: Altering network configurations, such as network interfaces or routing tables, can lead to changes in the remote host’s identification. This can occur when there are modifications to the networking infrastructure or when there is a change in the host’s network settings.
Implications of the warning:
1. Security risks associated with ignoring the warning: Ignoring the warning can potentially expose your system to security risks. The change in host identification may be a result of unauthorized access or a compromise of the remote host’s security. It is essential to take precautions and investigate the warning to ensure the safety of your system.
2. Possibility of a man-in-the-middle attack: The warning may indicate the presence of a man-in-the-middle attack, where an attacker intercepts and alters the communication between you and the remote host. Ignoring the warning may allow the attacker to intercept sensitive information or gain unauthorized access to your system.
3. Potential disruption of communication and data integrity: Disregarding the warning can result in communication disruptions or potential data integrity issues. The warning serves as a precaution to ensure that the remote host’s identity is trusted and that the data transmitted between parties remains intact.
4. Impact on system performance and availability: A change in the remote host’s identification can impact the performance and availability of your system. Ignoring the warning without investigating and resolving the underlying cause may lead to further complications and may disrupt your workflow.
How to interpret and respond to the warning:
1. Understanding the meaning behind the warning: It is important to comprehend the implications of the warning and the potential risks associated with it. This understanding will help you respond effectively and mitigate any security concerns.
2. Verifying the authenticity of the remote host: Before proceeding, it is crucial to verify the authenticity and integrity of the remote host. You can do this by contacting the host administrator or utilizing secure communication channels, such as phone verification, to confirm the changes in the host’s identification.
3. Encryption and secure communication protocols: Ensure that your communication with the remote host is encrypted using secure protocols such as SSH (Secure Shell). Encryption adds an extra layer of security and protects the confidentiality of the data transmitted.
4. Implementing security measures to prevent future warnings: To prevent future occurrences of the warning, implement security measures such as regularly updating and maintaining the known_hosts file. This file contains a record of trusted host keys and can be useful in ensuring that the remote host’s identity is accurately identified during future connections.
Troubleshooting steps for resolving the warning:
1. Checking the known_hosts file for incorrect entries: Inspect the known_hosts file on your local system for any outdated or incorrect entries. These entries may be associated with the previous identification of the remote host. Removing these entries can help resolve the warning.
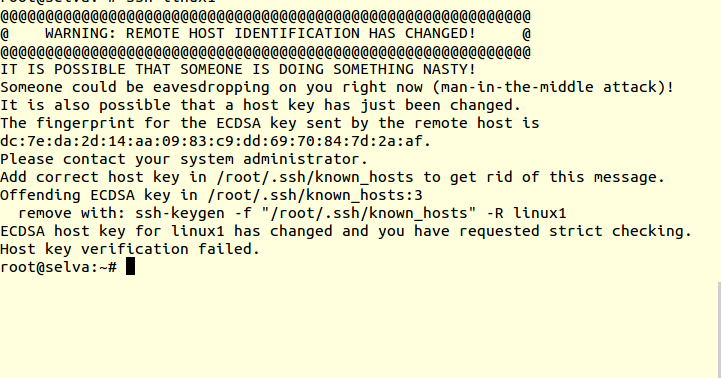
2. Updating the known_hosts file with the new host identification: If the change in the remote host’s identification is legitimate, update the known_hosts file with the new host key or fingerprint. This ensures that future connections will recognize the updated identification.
3. Verifying the remote host’s fingerprint: Compare the fingerprint provided by the remote host with the one stored in the known_hosts file. If they match, it indicates that the remote host’s identification is unchanged, and it is safe to proceed with the connection.
4. Reconnecting and testing the connection after resolving the warning: Once you have resolved the warning, reconnect to the remote host and test the connection. Ensure that the warning no longer appears and that the connection is secure and reliable.
Preventive measures to avoid future warnings:
1. Regularly updating and maintaining known_hosts file: Regularly update and maintain the known_hosts file to ensure it reflects the current identification of remote hosts. Remove outdated entries and verify the authenticity of new entries.
2. Implementing secure connection methods, such as SSH keys: Utilize secure connection methods, such as SSH keys, to establish trust between your system and the remote host. SSH keys provide enhanced security and eliminate the need to rely solely on host identification.
3. Monitoring and managing changes in IP addresses or configurations: Monitor and manage any changes in IP addresses or configurations of remote hosts. Keep track of these changes and update your system accordingly to avoid triggering unwanted warnings.
4. Keeping track of DNS changes and updating accordingly: Stay informed about DNS changes that may affect the identification of remote hosts. Regularly update your DNS settings or configurations to match the current information.
Additional considerations and advanced configurations:
1. Configuring secure connection through firewall rules: Implement firewall rules to restrict access and ensure secure connections between your system and remote hosts. This adds an extra layer of protection against unauthorized access and potential security threats.
2. Implementing multi-factor authentication for added security: Enable multi-factor authentication for stronger authentication and increased security. This can involve requiring additional authentication factors, such as biometrics or unique tokens, to establish a connection with remote hosts.
3. Using SSH wrappers or utilities to enhance security measures: Explore the use of SSH wrappers or utilities that provide additional security measures. These tools can help automate security measures, simplify authentication processes, and provide better control over remote host identification.
4. Periodically auditing and reviewing remote host identification process: Conduct regular audits and reviews of your remote host identification process. This ensures that your systems and practices are up to date and compliant with the latest security standards.
In conclusion, receiving the “Warning: Remote Host Identification Has Changed” message should not be taken lightly. It indicates potential security risks and requires immediate attention. By understanding the causes, implications, and appropriate responses to this warning, you can effectively address the issue, maintain the security and integrity of your system, and prevent future occurrences. Stay vigilant, keep your systems updated and secured, and adhere to best practices when connecting to remote hosts.
FAQs:
Q: What should I do if I encounter the warning message?
A: It is important to investigate the warning and ensure the authenticity of the remote host before proceeding. Update the known_hosts file with the new host identification, verify the fingerprints, and establish a secure connection. If in doubt, contact the host administrator for verification.
Q: Can ignoring the warning lead to security vulnerabilities?
A: Yes, ignoring the warning can expose your system to security risks. It may indicate unauthorized access or a compromise of the remote host’s security. Take necessary precautions to investigate and address the warning promptly.
Q: How can I avoid future warnings?
A: Regularly update and maintain the known_hosts file, implement secure connection methods like SSH keys, monitor and manage changes in IP addresses or configurations, and keep track of DNS changes. These preventive measures can help avoid future warnings.
Q: What should I do if the warning persists after troubleshooting?
A: If the warning persists after following the troubleshooting steps, it is advisable to seek help from a system administrator or IT professional. They can provide further assistance and ensure that your system is secure and functioning correctly.
How To Fix Warning Remote Host Identification Has Changed
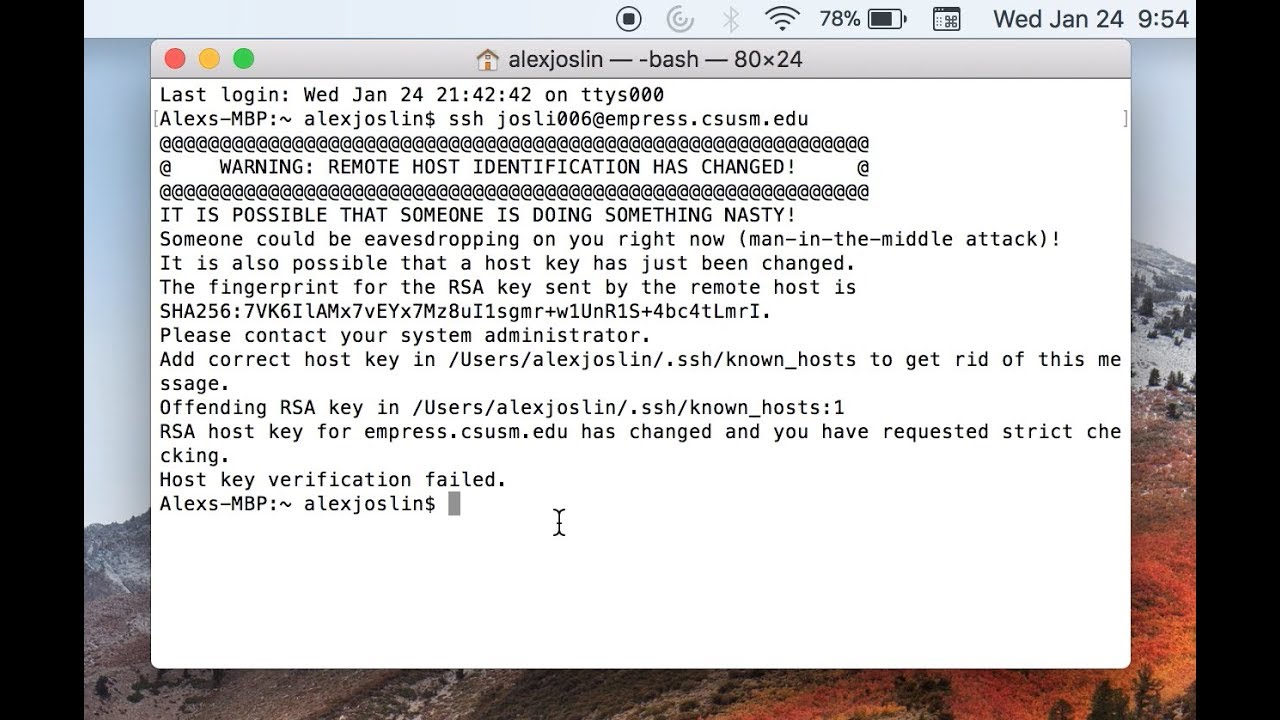
What Is Warning Remote Host Identification Changed On Mac?
If you frequently use remote login or SSH (Secure Shell) to access remote servers or other systems from your Mac, you may have come across a message saying “warning remote host identification changed.” This warning pops up when the SSH client on your Mac detects that the host identification, or the fingerprint of the remote server, has changed since the last time you connected to it.
In simpler terms, the warning is alerting you that the server you are trying to access has undergone some changes, which may indicate a potential security risk. SSH uses a fingerprint to verify the identity of the server and protect the connection from potential hackers or unauthorized access. When the fingerprint changes unexpectedly, it suggests that the server’s identity might have been compromised, and thus, you are being cautioned before proceeding with the connection.
Many factors can result in a changed host identification. Some common scenarios include:
1. Reinstallation or migration of the remote server: If the server has been reinstalled or migrated to a new host, its fingerprint will naturally change. This can occur during system upgrades, hardware replacements, or restoration from backups.
2. Renewal of SSH keys: SSH keys are used for authentication between the client and the server. When the server’s SSH keys are renewed, changed, or regenerated, the old fingerprint becomes invalid, causing the “warning remote host identification changed” message to appear.
3. Security breach or tampering: In more severe cases, the changed host identification might indicate a security breach or an attempt to tamper with the server’s identity. This could occur due to a hacker gaining unauthorized access or an attack targeting the server’s security infrastructure.
It is important to take the “warning remote host identification changed” message seriously, especially if it randomly appears without any apparent cause. Ignoring or blindly accepting the warning can expose you to risks such as man-in-the-middle attacks, where malicious entities intercept your connection to gather sensitive information or imitate the server to gain access to your credentials.
FAQs:
1. Should I always be concerned when I see the “warning remote host identification changed” message?
While the warning is an indication that the server’s fingerprint has changed, it is not always a cause for immediate concern. If you are aware of any recent changes or updates to the server, such as a system upgrade or SSH key renewal, you can safely ignore the warning. However, if the message appears unexpectedly or you have reasons to suspect a security breach, it is recommended to investigate further before proceeding with the connection.
2. How can I verify if the changed host identification is legitimate or a security risk?
To verify the legitimacy of the changed host identification, you can contact the system administrator or server owner and inquire about any recent changes. They can confirm if the identified changes were intentional or if any security breaches have occurred. Additionally, you can compare the new fingerprint provided by the warning message with a trusted source, such as the server owner’s records, to ensure consistency.
3. What actions should I take if I suspect a security breach or unauthorized access?
If you suspect a security breach or unauthorized access due to the changed host identification, it is crucial to refrain from connecting to the server and immediately contact the server administrator or system owner. They can guide you on further steps, such as disabling SSH access or investigating the incident. It is also advisable to review any log files or security measures in place to identify potential vulnerabilities or evidence of unauthorized access.
4. Can I manually update the server’s fingerprint to avoid future warnings?
Yes, it is possible to manually update the server’s fingerprint to avoid future warnings. You can achieve this by accessing the known_hosts file on your Mac, which contains records of the fingerprints of previously connected servers. Locate the entry for the server in question and remove it from the file. Upon reconnecting, your SSH client will generate a new entry for the server with the updated fingerprint, eliminating the warning for subsequent connections.
In conclusion, the “warning remote host identification changed” message on your Mac serves as an important security measure to protect your SSH connections from potential threats. While it can be triggered by legitimate changes to the remote server, it is essential to remain vigilant and investigate any unexpected or suspicious warnings. By verifying the changes with trusted sources and taking appropriate actions when necessary, you can ensure the integrity and security of your remote connections.
What Is Warning Remote Host Identification Has Changed?
When connecting to a remote host or server using SSH (Secure Shell), you may encounter a warning message that says, “Warning: Remote Host Identification Has Changed.” This warning indicates that the identification of the remote host you are trying to connect to has changed, which could be a potential security concern. In this article, we will delve into the details of this warning, its causes, and what actions you should take when encountering it.
Understanding the Warning Message:
The warning message, “Warning: Remote Host Identification Has Changed,” is displayed by the SSH client program, which is commonly used to establish secure shell connections. SSH uses cryptographic keys to verify the authenticity of the remote host, and any changes in these keys trigger the warning message.
Causes of Remote Host Identification Change:
1. Reinstallation or Recommissioning: If the remote host’s operating system is reinstalled or its SSH server is recommissioned, the new installation generates new cryptographic keys. As a result, the host identification changes, triggering the warning.
2. IP Address Changes: In some cases, the remote host may change its IP address due to network reconfigurations. A change in IP address alters the host identification, leading to the warning message.
3. Man-in-the-Middle (MITM) Attack: Probably the most concerning cause, a MITM attack occurs when a malicious person intercepts the connection between you and the remote host. This interceptor then poses as the remote host and presents its own cryptographic keys, leading to a changed host identification. Such attacks are rare, but they can severely compromise the security of your connection.
Actions to Take:
1. Confirm the Cause: When encountering the warning message, it is essential to determine the cause before proceeding. If you have not made any major changes to the remote host or network recently, a MITM attack is less likely. However, if you suspect foul play or are unsure about the cause, proceed with caution.
2. Verify Host Fingerprints: SSH provides a fingerprint or hash of the remote host’s public key, enabling users to verify its authenticity. You can check this fingerprint against the one you have previously recorded to verify the identity of the remote host. For example, the command `ssh-keygen -F
3. Update Known Hosts File: The known_hosts file, usually located in the “.ssh” directory under your home folder, keeps records of the fingerprints of the remote hosts you have connected to. If you have verified and trust the new host identification, you can update this file to reflect the change. The command `ssh-keygen -R hostname` removes the old fingerprint, allowing the new one to be saved upon reconnection.
4. Exercise Caution: If you suspect a MITM attack and are unable to verify the authenticity of the host, it is advisable to avoid connecting to the remote host. Proceeding with a questionable connection can put your data and privacy at risk.
FAQs:
Q1. Why is a changed host identification a security concern?
A1. The SSH protocol relies on cryptographic keys to ensure secure connections. When the host identification changes unexpectedly, it implies that either the remote host has changed or someone is intercepting your connection. This can potentially expose your data and communication to unauthorized access, leading to security breaches.
Q2. How do I verify the host’s fingerprint?
A2. To verify the host’s fingerprint, use the command `ssh-keygen -F
Q3. Can I ignore the warning and proceed with the connection?
A3. While it is possible to ignore the warning and proceed, it is generally not recommended. Ignoring the warning, especially without confirming the cause or verifying the host’s identity, can leave your connection vulnerable to interception or man-in-the-middle attacks.
Q4. How can I prevent encountering this warning?
A4. To prevent encountering this warning, make sure to keep your known_hosts file up to date. Whenever you connect to a remote host for the first time, SSH prompts you to save its fingerprint in the known_hosts file. By updating and maintaining this file, you reduce the likelihood of encountering the warning message.
In conclusion, the warning message “Warning: Remote Host Identification Has Changed” should not be taken lightly. It indicates a change in the remote host’s identification, potentially compromising the security of your connection. By understanding the causes, verifying host fingerprints, and taking appropriate actions, you can ensure secure and authentic SSH connections. Remember, always exercise caution and prioritize security.
Keywords searched by users: warning: remote host identification has changed Warning remote host identification has changed vps, RSA host key for GitHubcom has changed and you have requested strict checking, host key verification failed., Ssh-keygen, Warning remote host identification has changed raspberry pi, Remove known host ssh, The fingerprint for the ECDSA key sent by the remote host is, GitHub SSH key
Categories: Top 29 Warning: Remote Host Identification Has Changed
See more here: nhanvietluanvan.com
Warning Remote Host Identification Has Changed Vps
When working with a Virtual Private Server (VPS), it is not uncommon to come across the warning message “remote host identification has changed.” This warning can sometimes raise concerns for VPS users, particularly if they are not familiar with the implications and potential causes of this message. In this article, we will delve deeper into what this warning means, why it occurs, and how to address it.
What does the warning mean?
The warning “remote host identification has changed” typically appears when you try to connect to a VPS through SSH (Secure Shell), a secure network protocol used for remote access to servers. SSH is designed to verify the identity of the server you are connecting to, ensuring the connection is secure and not compromised.
When SSH compares a server’s identity with the previously stored identity, it checks the key fingerprint of the server. If the key fingerprint has changed, SSH notifies you with the warning message. Essentially, this message indicates that the server’s identity has been modified, and the previous fingerprint no longer matches the current one.
Why does it happen?
There are a few common scenarios that can lead to the warning “remote host identification has changed” when connecting to a VPS. Understanding these scenarios can help you identify the cause and potential risks involved:
1. Server reinstallation: If the VPS provider reinstalls or reconfigures the server, it will generate a new SSH key fingerprint. This process will alter the server’s identity and trigger the warning.
2. Server migration: In cases where you are migrating your VPS to a different provider or server, the new server will have a different key fingerprint. Consequently, SSH will detect the change in identity and issue the warning.
3. Security breach or attack: A change in the server’s SSH key fingerprint can also indicate a compromised server. If you didn’t initiate any modifications, this warning could be a cause for concern, indicating a potential security breach or attack.
How to address the warning?
When the warning “remote host identification has changed” appears, it is crucial to take appropriate action to ensure the security of your connection. Here are the steps you can follow to address the warning effectively:
1. Verify the server’s identity: Before proceeding, confirm the new fingerprint’s legitimacy. This can often be done by contacting your VPS provider directly and comparing the fingerprints provided.
2. Update your known_hosts file: On your local machine, navigate to the directory where your SSH known_hosts file is located. This file stores the fingerprints of remote servers you have connected to before. Open the known_hosts file and delete the line corresponding to the affected server. Save the changes.
3. Reestablish trust: Once the known_hosts file is updated, reconnect to the VPS. SSH will prompt you to verify the server’s new fingerprint. Carefully compare the displayed fingerprint with the one confirmed by your VPS provider. If they match, you can confirm and proceed. If not, abort the connection and contact your provider for assistance.
FAQs
Q: Is it safe to ignore the warning “remote host identification has changed”?
A: It is generally not recommended to ignore this warning, as it can indicate a security risk. Contact your VPS provider to investigate the nature of the change before deciding the appropriate action.
Q: Can server updates trigger this warning?
A: Yes, server updates or reconfigurations can generate new SSH key fingerprints and result in the warning message. Make sure you have verified the changes before updating your known_hosts file.
Q: What if the warning persists even after updating the known_hosts file?
A: If the warning continues to appear despite updating the file, it is advisable to contact your VPS provider immediately. They will help investigate the issue and ensure the integrity and security of your VPS.
Q: Are there any tools to automate the process of updating known_hosts file?
A: Various tools, such as ssh-keyscan or sshfp, can help automate the process of validating and updating SSH key fingerprints. These tools can be useful for managing multiple servers or when performing frequent server migrations.
In conclusion, encountering the warning “remote host identification has changed” when connecting to a VPS is not uncommon. By understanding the reasons behind this warning and following the recommended steps to address it, you can ensure a secure and reliable connection to your VPS. Remember to verify any changes with your VPS provider and take prompt action in case of any suspicion of compromised security.
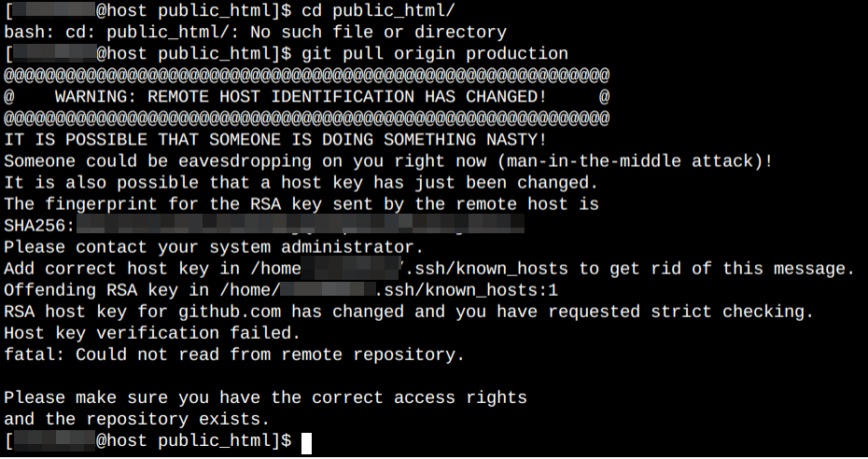
Rsa Host Key For Githubcom Has Changed And You Have Requested Strict Checking
GitHub.com is a widely popular platform that hosts millions of software projects, facilitating collaboration and development. As a user, you trust the platform to provide a secure and reliable environment for your code. To ensure this security, GitHub.com uses RSA host keys, which are crucial for authenticating and encrypting data transmissions between your local machine and the GitHub servers. Recently, you may have received a notification stating that the RSA host key for GitHub.com has changed and that you have requested strict checking. In this article, we will delve into the details of RSA host keys, the reasons behind their change, and what this means for you as a user.
Understanding RSA Host Keys:
RSA (Rivest-Shamir-Adleman) is a widely adopted encryption algorithm that plays an essential role in securing communication over insecure networks, such as the internet. RSA works on the principle of public-key cryptography, where two mathematically related keys—a public key and a private key—are used for encryption and decryption.
In the context of GitHub.com, RSA host keys are used to secure the connection between your local machine and the platform’s servers. When you connect to GitHub.com via SSH (Secure Shell), your local machine verifies the authenticity of the server by checking its RSA host key. If the key matches the expected value, the connection proceeds securely. However, if the key has changed, it raises a security alert, as it might indicate a potential man-in-the-middle attack.
Reasons for Changing RSA Host Key:
Changing an RSA host key is not a routine occurrence and is only done in specific situations. The most common reasons for changing an RSA host key include:
1. Key Expiration: RSA host keys have an expiration date, typically after one year. To ensure continued security, GitHub.com regularly rotates these keys and generates new ones.
2. Security Breach: If there is a suspicion or evidence of a security breach, it becomes necessary to change the RSA host key to protect users’ data.
3. Server Migration or Upgrade: When GitHub.com undergoes server migrations or upgrades, including changing hosting providers or data centers, RSA host keys are regenerated as a precautionary measure.
4. Preemptive Measures: In some cases, RSA host key changes might occur as a pre-emptive measure to enhance security or to implement new cryptographic algorithms for improved protection.
Requesting Strict Checking:
Alongside the notification about the RSA host key change, you may have noticed a mention that you have requested strict checking. Strict checking is an additional layer of security where your SSH client verifies the RSA host key every time you connect to GitHub.com, even if the key has not changed. By enabling strict checking, you are adding an extra level of assurance that the connection remains secure throughout all your interactions with the platform.
It is important to note that strict checking may lead to more frequent RSA host key change notifications. This occurs because even the slightest change in the host key, such as during a server reboot, will trigger an alert. While it might seem bothersome, strict checking is a recommended practice to maintain the highest standards of security when utilizing GitHub.com.
Frequently Asked Questions (FAQs):
Q1: Should I be concerned if the RSA host key has changed on GitHub.com?
A1: Not necessarily. Sometimes, the RSA host key change is a routine procedure to ensure the continued security of the platform. However, if you have any doubts or concerns about the change, you can reach out to GitHub support for clarification.
Q2: How can I verify the authenticity of the new RSA host key?
A2: GitHub provides documentation on how to verify its RSA host key using your SSH client. Following those guidelines will help ensure that you are connecting securely to GitHub.com.
Q3: What are the implications of requesting strict checking?
A3: Requesting strict checking adds an additional layer of security to your connection with GitHub.com. It helps prevent potential man-in-the-middle attacks by thoroughly verifying the RSA host key every time you connect. However, it might result in more frequent notifications about host key changes.
Q4: What can I do to stay informed about RSA host key changes?
A4: GitHub actively communicates RSA host key changes to its users via email notifications. Make sure your email address associated with your GitHub account is up-to-date to ensure you receive these important notifications promptly.
Q5: Can I disable strict checking if I find it to be too bothersome?
A5: While you can disable strict checking, it is generally recommended to keep it enabled, as it provides an extra layer of protection against potential security threats. It is better to ensure your connection’s integrity by verifying the RSA host key rather than compromising your security.
Conclusion:
The RSA host key change on GitHub.com, along with the strict checking request, underscores the platform’s commitment to security and data integrity. Understanding RSA host keys, the reasons behind their changes, and the implications of strict checking ensures that you can confidently continue your work on GitHub.com, knowing that your code and data are protected. Stay vigilant, keep yourself informed about any future changes, and embrace the security measures put in place to safeguard your projects on GitHub.com.
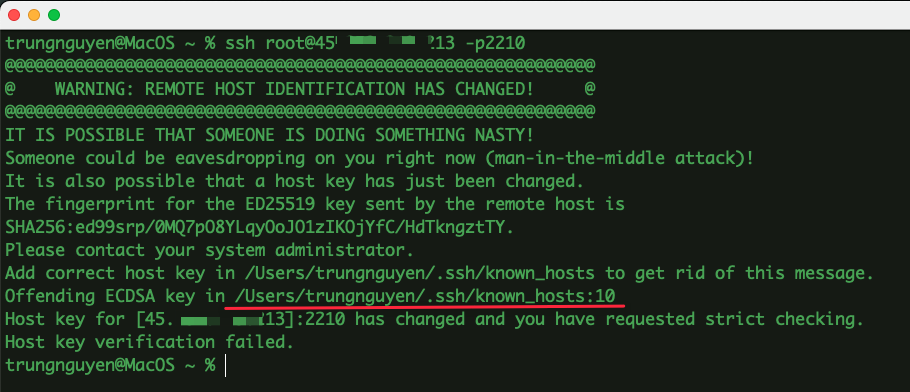
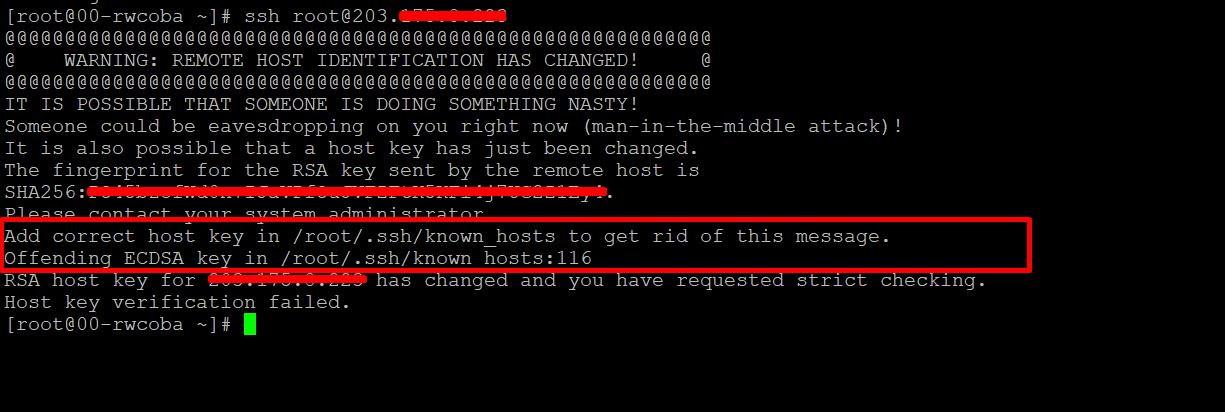
Host Key Verification Failed.
Introduction:
When connecting to a remote server using SSH (Secure Shell) protocol, it is crucial to ensure a secure and trustworthy connection. One of the security mechanisms involved in this process is host key verification. However, at times, users may encounter the “Host Key Verification Failed” error, which can be perplexing and lead to concerns about the integrity of the connection. In this article, we will delve into this error, its causes, and explore various troubleshooting techniques to resolve it.
Understanding Host Key Verification:
SSH uses host keys to authenticate the identity of the server before establishing a connection. These keys help prevent man-in-the-middle attacks, ensuring that you are connecting to the intended server and not a malicious entity. When you make a connection to a remote server, your SSH client checks the server’s key against a known set of host keys stored on your computer, typically in the known_hosts file.
Reasons for Host Key Verification Failed Error:
There are several potential reasons why the “Host Key Verification Failed” error occurs:
1. Change in Host Key: If the server’s host key has changed, your SSH client will raise the verification error. This often happens when the server’s software or hardware has been modified, reinstalled, or reconfigured.
2. Host Key Mismatch: If an attacker tries to impersonate the server or conduct a man-in-the-middle attack, your SSH client will detect the mismatched host key and display this error. Proceeding with the connection could compromise your security.
3. Known Hosts File Issues: If your known_hosts file is incomplete, corrupted, or incorrect due to manual modifications, it may prevent proper host key verification.
4. Untrusted Network: When connecting to a server from an untrusted network, such as public Wi-Fi, your SSH client may display the verification error as a cautionary measure.
Resolving the Host Key Verification Failed Error:
Resolving this error requires careful verification and manual intervention. Consider the following steps:
1. Verify the Host Key: Double-check the host key displayed in the error message with the expected host key. Contact the server administrator to confirm any discrepancies. The server may have changed its host key for a genuine reason, such as security updates.
2. Update the Known Hosts File: If the host key has changed legitimately, you should remove the outdated entry from your known_hosts file. You can do this manually or by utilizing the command line tools available for your SSH client.
3. Trust the New Host Key: Once you have validated the new host key, update your known_hosts file accordingly to trust the new key. This ensures that subsequent connections to the same server will not trigger the verification error.
4. Verify Connection Security: If connecting from an untrusted network, consider using a VPN (Virtual Private Network) service to establish a secure connection before attempting to connect to the server via SSH.
Host Key Verification Failed Error FAQs:
Q1. How can I manually remove an incorrect entry from the known_hosts file?
A1. Open your known_hosts file in a text editor, locate the incorrect entry corresponding to the server’s IP address or hostname, and delete that line. Save the file and retry the connection.
Q2. Can I disable host key verification to bypass this error?
A2. Disabling host key verification is strongly discouraged as it compromises SSH’s security. Instead, resolve the underlying issue causing the error by manually verifying and updating host keys.
Q3. Is this error message relevant for every SSH client?
A3. Yes, the “Host Key Verification Failed” error is a standard message across SSH clients. If faced with this error, the troubleshooting steps mentioned above can be applied irrespective of the client you are using.
Q4. Should I be worried if I encounter this error?
A4. While the error can be unsettling, addressing it diligently will ensure a secure connection. Verify the host key, update the known_hosts file, and establish a trusted connection.
Conclusion:
The “Host Key Verification Failed” error is a security mechanism that protects SSH connections from potential threats. Maintaining the integrity of host keys is crucial to securely connect to remote servers. With the troubleshooting steps outlined in this article, you can effectively address this error and ensure a safe and risk-free SSH connection. Always remember to validate and update host keys to maintain the highest level of security.
Images related to the topic warning: remote host identification has changed

Found 50 images related to warning: remote host identification has changed theme



























Article link: warning: remote host identification has changed.
Learn more about the topic warning: remote host identification has changed.
- How To Fix “Warning: Remote Host Identification Has … – Kinsta
- ssh remote host identification has changed – Stack Overflow
- Error Fix – Warning: Remote Host Identification Has Changed …
- How To Fix “Warning: Remote Host Identification Has … – Kinsta
- We updated our RSA SSH host key – The GitHub Blog
- SSH Host Key Management Demystified
- How To Deal With the “Remote Host Identification Has …
- WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED!
- How to fix “Warning: remote host identification has changed”
- 3 Ways to fix remote host identification has changed
- How to fix “Remote Host Identification has Changed” error
- Fixing SSH Remote Host Identification Has Changed Warnings
- Error Fix – Warning: Remote Host Identification Has Changed …
See more: https://nhanvietluanvan.com/luat-hoc