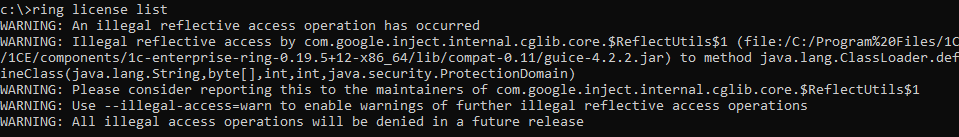
Warning An Illegal Reflective Access Operation Has Occurred
Introduction
Java is one of the most popular programming languages used today, known for its flexibility, performance, and security. However, there are certain scenarios where developers may encounter warning messages regarding illegal reflective access operations. In this article, we will delve into the concept of illegal reflective access, understand why these warnings occur, explore the Java Platform Module System (JPMS), discuss the impact on performance and security, provide troubleshooting steps, and highlight best practices to avoid such warnings. Let’s begin by understanding what an illegal reflective access operation is.
What is an illegal reflective access operation?
In Java, reflection allows developers to examine or modify the runtime behavior of applications. It grants access to methods, fields, constructors, and other elements at runtime, which are otherwise not accessible during compilation. However, sometimes developers perform reflective operations inappropriately or in a way that is not compliant with Java’s access rules. This leads to illegal reflective access operations.
An illegal reflective access operation occurs when the code accesses a member or field of a class using reflection, that is not accessible under normal circumstances. This could be due to a restriction imposed by the Java security manager or mismatches in the visibility modifiers of the class and its member. When such an operation is detected, Java issues a warning message to notify developers and highlight potential risks.
Why does the warning message occur?
Java issues a warning about illegal reflective access operations primarily to alert developers about potentially insecure and risky code practices. These warnings emphasize the fact that the code is accessing members in a way that could compromise the intended encapsulation and security of the application. By highlighting these warnings, Java encourages developers to review and fix their code to ensure best practices and maintain application security.
Understanding the Java Platform Module System (JPMS)
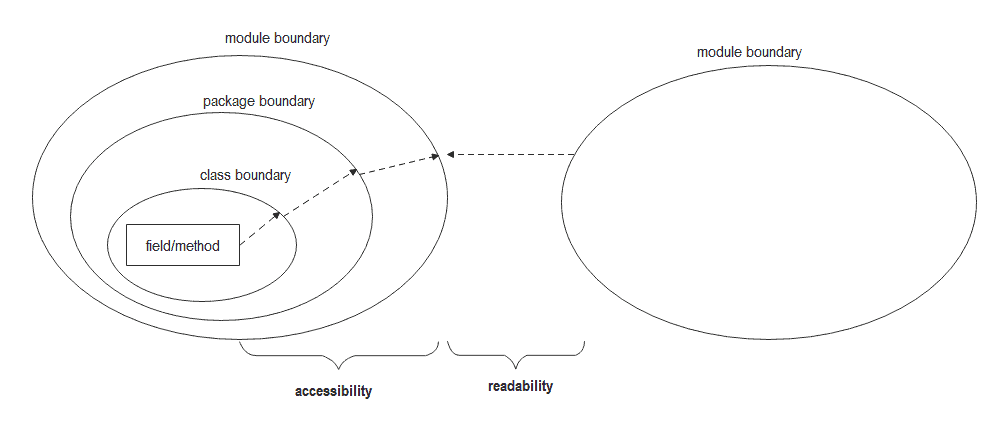
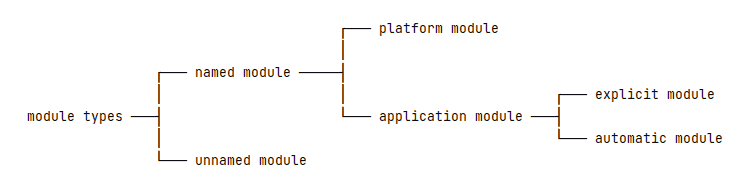
With the release of Java 9, the Java Platform Module System (JPMS) was introduced. JPMS provides a modular architecture for Java applications, allowing developers to encapsulate code into modules, define dependencies explicitly, and specify access rules. It enforces strong encapsulation by default, preventing illegal reflective access to code residing in other modules.
One of the reasons for illegal reflective access warnings could be the mismatch between code that uses modularized libraries and code that doesn’t adhere to modularization rules. If your codebase is modularized, it is essential to ensure that all dependencies comply with JPMS rules to avoid these warnings.
Impact of illegal reflective access on performance and security
Illegal reflective access operations can have a significant impact on the performance and security of Java applications. As these warnings highlight potential violations of encapsulation, it implies that the code is accessing internal or restricted members that are not meant to be accessed directly. This can lead to unexpected behavior, data corruption, or security vulnerabilities. Accessing restricted members using reflection may bypass necessary checks and validations, compromising the security of the application.
Moreover, illegal reflective access can also result in performance degradation. Reflection is more computationally expensive compared to direct access to members. By using reflection in an inappropriate or illegal manner, unnecessary processing overhead can be introduced, resulting in decreased application performance. It is crucial to address illegal reflective access warnings to ensure optimal performance and security.
Steps to troubleshoot and resolve illegal reflective access warnings
When encountering illegal reflective access warnings, it is essential to follow a systematic approach to troubleshoot and resolve the issue. Here are some steps to help you address these warnings effectively:
1. Identify the source: Determine the specific code or library that is causing the warning. Look for the warning message in your development environment console or log files, which will provide details about the class and method involved in the illegal reflective access.
2. Review the code: Carefully analyze the code that triggered the warning. Verify if you are performing any reflective operations that are accessing members not meant to be accessed directly. Check if there are any mismatches in the visibility modifiers or if the code is violating the encapsulation rules.
3. Evaluate JPMS compliance: If your codebase is modularized, inspect the dependencies to ensure they comply with the Java Platform Module System (JPMS) rules. Make sure the module declarations are accurate, and the access controls are appropriately defined.
4. Update libraries and frameworks: If the illegal reflective access is caused by a third-party library or framework, check for any updates or patches provided by the vendor. Updated versions may address these issues and provide a JPMS-compliant solution.
5. Use alternative methods or APIs: Consider using alternative methods or APIs that do not involve reflective access. Relying on direct access, when available, can simplify the code and eliminate the need for reflection.
6. Suppress warnings selectively: If you are confident that the reflective access operation is intentional and does not compromise security, you can suppress the warning using proper annotations or configuration options. However, exercise caution while using this approach, as it should only be considered as a last resort.
Future implications and changes in Java versions
Java has always placed a strong emphasis on security and encapsulation. To enforce these principles more rigorously, Java has announced that all illegal-access operations will be denied in a future release. This decision aims to promote better coding practices, reduce security vulnerabilities, and improve the overall performance of Java applications.
Developers are encouraged to address illegal reflective access warnings promptly and update their code according to the best practices outlined in this article. Planning for future Java releases and adopting JPMS-compliant practices will help avoid disruptions and ensure smooth migration to newer versions.
Best practices to avoid illegal reflective access in your code
To prevent illegal reflective access operations in your code, follow these best practices:
1. Avoid unnecessary reflection: Only use reflection where necessary. Reflection should be used judiciously and sparingly, as it introduces complexities and potential risks. Whenever possible, prefer direct access to members.
2. Review and refactor code: Regularly review your codebase to identify any inappropriate or unnecessary reflective access operations. Refactor the code to eliminate such operations and use direct access or alternative solutions.
3. Update libraries and frameworks: Keep your dependencies up-to-date, as newer versions often address security concerns and provide JPMS-compliant solutions. Regularly check for updates and apply them to keep your codebase secure.
4. Understand JPMS requirements: If you are developing or migrating to a modularized codebase, ensure a thorough understanding of JPMS requirements. Follow the rules of encapsulation and define access controls correctly to avoid illegal reflective access warnings.
5. Conduct thorough testing: Test your code extensively to ensure that reflective operations, where used, work as expected. Perform rigorous testing to identify any potential security or performance issues caused by reflective access.
6. Stay updated with Java releases: Keep yourself informed about the latest Java releases and advancements in JPMS. Stay up-to-date with the latest developments to leverage new features, security enhancements, and performance improvements.
Conclusion
Illegal reflective access warnings in Java serve as warnings against potential security vulnerabilities and performance degradation. By understanding the concept of illegal reflective access, adhering to best practices, and ensuring compliance with the Java Platform Module System, developers can mitigate risks and maintain robust, secure, and high-performing Java applications. Stay alert, address these warnings diligently, and keep your codebase future-proof.
Why Groovy Shows Warning \”An Illegal Reflective Access Operation Has Occurred\” When I Use Jdk11?
How To Avoid Warning An Illegal Reflective Access Operation Has Occurred?
If you have ever encountered the warning message “warning: an illegal reflective access operation has occurred” while running your Java application, you might have wondered what it means and how to avoid it. This article delves into the details of this warning, explains its implications, and presents solutions to prevent it.
Understanding the Warning Message:
The warning is related to the use of reflective access in Java, which allows programs to examine or modify the behavior of classes, methods, fields, etc., at runtime. Reflective access can be a powerful tool, but it can also lead to potential security risks if used incorrectly.
When you encounter the warning “an illegal reflective access operation has occurred,” it implies that your code is accessing internal APIs or methods that are not intended to be used outside of their enclosing classes. This can happen if you are using a library or framework that relies on deprecated or non-public APIs.
Why Is It a Concern?
The warning is not merely aesthetic; it serves as a heads-up that your code may not be future-proof. As Java evolves, certain internal APIs may change or even be removed. By relying on these APIs, you may encounter issues when migrating your application to newer versions of Java.
Additionally, Java provides security measures to prevent unauthorized access to sensitive functionality or data. Using reflective access to bypass these safeguards can compromise the security and integrity of your application.
Ways to Avoid the Warning:
1. Upgrade to Compatible Libraries: If your code is utilizing a library or framework that triggers the reflective access warning, check if there is a newer version available. Keeping your dependencies up to date ensures better compatibility with the latest Java releases.
2. Use Public APIs: Whenever possible, rely on public APIs provided by libraries, frameworks, or the Java standard library. Public APIs are thoroughly tested, documented, and guaranteed to be supported in future releases.
3. Review Deprecated APIs: If you encounter the reflective access warning while using an API, check whether it has been deprecated or replaced with an alternative. Refactoring your code to adopt the recommended approach will help you avoid compatibility issues.
4. Enable Additional Warnings: Java provides options to enable more detailed warnings during compilation. By adding “-Xlint” to your “javac” command, you can enable additional warnings like “-Xlint:deprecation,” which will alert you to the use of deprecated APIs. Fixing these warnings promptly can prevent further issues down the road.
5. Remove Reflective Access: In some cases, the reflective access is used unnecessarily, and an alternative approach exists. Analyze your codebase to find any instances where reflective access is being employed and consider whether it can be replaced with a more straightforward, documented approach.
Frequently Asked Questions:
Q1. What is reflective access?
A1. Reflective access in Java allows programs to inspect and modify the behavior of classes, methods, fields, etc., at runtime. It provides a means to access APIs that are otherwise protected or inaccessible.
Q2. How can reflective access impact my application?
A2. Reflective access can bypass access restrictions, potentially compromising the security and stability of your application. It can also result in compatibility issues, as internal APIs may change or be removed in future Java versions.
Q3. Is reflective access always bad?
A3. No, reflective access can be useful in certain scenarios, such as dynamic instantiation, introspection, or dependency injection. However, it should be used judiciously and confined to situations where other alternatives are not feasible.
Q4. I cannot modify the library/framework code that triggers the warning. What can I do?
A4. In such cases, you can consider contacting the library/framework maintainers and report the issue. If they are responsive, they might address the reflective access warning in future releases. Alternatively, you can search for an alternative library or framework that provides a similar functionality without reflective access.
Q5. Can I ignore the reflective access warning and continue with my code?
A5. It is possible to silence the warning by adding “–add-opens” or “–illegal-access” flags to the JVM arguments. However, doing so is discouraged as it effectively disables the protective mechanisms and increases the likelihood of future compatibility issues.
In conclusion, the warning message “an illegal reflective access operation has occurred” should not be ignored. By understanding the implications and taking proactive measures, such as upgrading libraries, using public APIs, and reducing reflective access, you can ensure the long-term stability and security of your Java application.
What Is Jdk 11 Warning An Illegal Reflective Access Operation Has Occurred?
The release of Java Development Kit (JDK) 11 brought several new features and improvements. However, some developers upgrading to this version have encountered a warning message stating, “Warning: An illegal reflective access operation has occurred.” This warning occurs when an application uses internal APIs (Application Programming Interfaces) or makes use of reflection in a way that goes against the established conventions and security recommendations.
To understand this warning message better, it is important to dive into the concept of reflective access and its role in Java applications.
Reflective Access in Java
Java provides the capability to dynamically inspect and interact with objects at runtime through the use of reflection. Reflection enables developers to access and manipulate classes, methods, fields, and other components that are non-public or inaccessible through normal programmatic means. This can be a powerful tool for frameworks, libraries, or in scenarios where dynamic class loading and introspection are required.
However, reflective access can also be abused if not used carefully. It allows for bypassing encapsulation, violating security restrictions, and potentially breaking application integrity. To mitigate these risks, Oracle, the company behind Java, restricts access to internal APIs by default.
Internal APIs
Internal APIs are classes, methods, or fields that are not part of the public API and are intended solely for internal use by the Java runtime environment. They provide low-level functionality for the core libraries, such as garbage collection, class loading, or thread management. These internal APIs are not subject to the same level of compatibility guarantees as public APIs, and can be subject to changes or removal in future JDK releases.
In JDK 9, Oracle introduced a module system to Java called the Java Platform Module System (JPMS). The module system brings stricter encapsulation and allows explicit control over which packages are accessible from other modules. As part of these efforts, access to internal APIs was further restricted by encapsulating them within specific modules, effectively signaling that they should not be accessed by external code.
Warning Message in JDK 11
Starting from JDK 9, when an application tries to access internal APIs or uses reflection in an unsafe manner, a warning message, “Warning: An illegal reflective access operation has occurred,” is issued by the JVM (Java Virtual Machine).
The purpose of this warning is to notify developers that their code is utilizing Java internals that are not intended for public use. It serves as a reminder to revise and adapt code to comply with the new module system and avoid potential compatibility issues in the future JDK releases.
It is important to note that this warning is purely informative and does not necessarily signify a problem with the functionality of the application or indicate that the application is broken. However, it should not be ignored, as it indicates a possible future incompatibility.
FAQs
Q: How can I fix the warning message in JDK 11?
A: To address the warning, you should modify your code to no longer rely on internal APIs or reflective access that goes against the established conventions. In most cases, there are alternative approaches or workarounds available. It is crucial to analyze the code and identify which parts are triggering the warning, then find a suitable solution specific to your application.
Q: Can I suppress the warning?
A: While it is possible to suppress the warning message using command-line arguments, it is not recommended. Ignoring the warning may lead to compatibility issues in future JDK releases. It is better to understand the root cause of the warning and modify the code accordingly.
Q: Will my application break if I don’t address the warning?
A: In most cases, existing functionality will continue to work without any issues. However, it is strongly advised to fix the code triggering the warning to ensure compatibility with future JDK versions. Future JDK releases may change or remove the internal APIs, which could cause unexpected behavior or break the application altogether.
Q: Is the warning applicable only to JDK 11?
A: The warning was introduced in JDK 9 and still exists in JDK 11. It is likely to persist in future JDK releases as well. It serves as an ongoing reminder to developers to adapt their code to promote clean encapsulation and enhance the overall maintainability and stability of Java applications.
In conclusion, the JDK 11 warning, “Warning: An illegal reflective access operation has occurred,” signifies the usage of internal APIs or unsafe reflection in Java applications. It aims to help developers identify code that needs modification to align with the new module system introduced in JDK 9. By addressing this warning, developers can ensure compatibility with future JDK releases and promote better application integrity.
Keywords searched by users: warning an illegal reflective access operation has occurred All illegal-access operations will be denied in a future release, An illegal reflective access operation has occurred intellij, An illegal reflective access operation has occurred eclipse, Illegal reflective access by retrofit2 platform, Warning illegal reflective access by org apache spark unsafe platform, Illegal reflective access by org apache ibatis reflection reflector, Illegal reflective access by org/springframework CGLIB core reflectutils, Illegal reflective access by net sf jasperreports engine util classutils
Categories: Top 39 Warning An Illegal Reflective Access Operation Has Occurred
See more here: nhanvietluanvan.com
All Illegal-Access Operations Will Be Denied In A Future Release
The world of technology continues to evolve at a rapid pace, bringing forth new innovations and advancements that often augment our lives in countless ways. However, the growth of technology also brings with it an ever-increasing need for enhanced security measures to safeguard our data and privacy. One crucial aspect in achieving this is the prevention of illegal access to sensitive information. In a future release, all illegal-access operations will be denied, ensuring a stronger shield against potential threats.
Illegal-access operations refer to any unauthorized attempt to gain entry or control over a system, network, or data without proper authorization. These operations can vary in nature and severity, ranging from simple hacking attempts to highly sophisticated cyber-attacks. The motivation behind illegal access can also differ, including personal gain, espionage, or simply causing disruption. Regardless of the motives, the consequences of illegal access can be disastrous, resulting in data breaches, financial losses, identity theft, and reputational damage.
To combat this growing threat, developers are consistently working on incorporating robust security measures to prevent illegal access operations. In future software releases, various mechanisms will be employed to safeguard against illegal access attempts. These mechanisms will be designed to identify and block any unauthorized attempts swiftly and efficiently, significantly reducing the risks associated with illegal access.
One such mechanism that will play a vital role in future releases is two-factor authentication (2FA). Traditional username and password protection is often not enough to prevent illegal access, as malicious actors find ways to obtain or bypass these credentials. By implementing 2FA, an additional layer of security is introduced. This method typically involves a second form of verification, such as a fingerprint scan, facial recognition, or a unique code sent to the user’s mobile device. This not only makes it more challenging for unauthorized individuals to gain access but also provides an extra level of assurance for individuals regarding the safety of their information.
Beyond 2FA, future releases will also focus on enhancing encryption techniques. Encryption is the process of encoding information in a way that makes it difficult to be understood or accessed by unauthorized parties. By strengthening encryption methods, data can be transmitted and stored securely, ensuring that even if unauthorized access occurs, the information would remain unreadable. Additionally, stronger encryption algorithms will make it more complex for cybercriminals to crack passwords or encryption keys, making illegal access operations significantly more difficult.
Furthermore, future releases will prioritize continuous monitoring and threat detection. Proactive monitoring involves the real-time tracking of system activities in order to identify any abnormal behavior or potential security threats. Advanced anomaly detection algorithms will be employed to analyze system logs, user behavior, and network traffic patterns to identify any signs of illegal access attempts. Any suspicious activities will be immediately flagged, allowing developers to take prompt action and prevent security breaches before they occur.
Additionally, future releases will integrate machine learning and artificial intelligence (AI) technologies to detect and respond to illegal access operations. These smart systems will learn from past patterns and continuously evolve to identify new threats, making them more adaptive to changing attack methodologies. By leveraging AI capabilities, developers can stay one step ahead of cybercriminals, improving security measures with each software update.
FAQs:
Q: How will the denial of illegal access operations affect user experience?
A: The denial of illegal access operations will have minimal impact on a user’s daily experience. It primarily targets unauthorized actions and focuses on strengthening security measures. Users will notice improved safety and greater peace of mind while using technology and sharing sensitive information.
Q: What can individuals do to protect themselves from illegal access operations in the meantime?
A: While waiting for future releases, individuals can take several steps to enhance their own security. This includes creating strong, unique passwords for each account, regularly updating software and apps, being cautious while clicking on suspicious links or downloading files, and enabling two-factor authentication wherever possible.
Q: Can these security measures guarantee 100% protection against illegal access?
A: While the inclusion of robust security measures significantly reduces the risks associated with illegal access, it is impossible to entirely eliminate the potential for security breaches. However, by staying up to date with the latest software releases and following security best practices, individuals can greatly minimize the likelihood of unauthorized access.
In conclusion, the prevention of illegal-access operations is of utmost importance to ensure the security and privacy of users’ data. In future software releases, developers will implement advanced security mechanisms such as two-factor authentication, enhanced encryption, continuous monitoring, and AI-powered threat detection. By incorporating these measures, the future release will provide a more secure environment, offering individuals greater protection against unauthorized access and fostering trust in the digital world.
An Illegal Reflective Access Operation Has Occurred Intellij
IntelliJ IDEA is a popular integrated development environment (IDE) widely used by developers for software development. However, sometimes users encounter an “Illegal reflective access operation has occurred” error in IntelliJ. This error message can be quite confusing for those who are unfamiliar with the underlying causes. In this article, we will delve into the various aspects of this issue, explore its causes, and provide solutions to overcome it.
Understanding the Error:
When running a Java program in IntelliJ, you might come across an error message similar to “WARNING: Illegal reflective access by [class_name_here] (file:/path/to/project/out/production/classes/) to [package_name_here]”. This indicates that the program is trying to access a declared field, method, or class without the proper permissions. Though it may seem alarming at first, this error is generally benign and can be fixed without causing any major issues.
Causes of Illegal Reflective Access:
1. The Java module system: The introduction of the Java module system, starting from Java 9, enforces strong encapsulation to enhance modularity and security. This error message may occur when code outside the module tries to access internal elements, violating the module boundaries.
2. Reflection API: The Java Reflection API enables the examination and modification of runtime behavior in a class. However, some usage of reflection can lead to illegal reflective access. This commonly occurs while accessing non-public or internal elements of a class.
Solutions to Resolve the Issue:
1. Update IntelliJ and Java versions: Ensure that you are using the latest version of IntelliJ and Java, as newer versions often contain bug fixes and improvements that may resolve the illegal reflective access issue.
2. Check module-info.java: If you are using Java modules, review your module-info.java file. Make sure that the required module declarations are correct, and pay attention to potential exports and opens directives that might be necessary to allow access to specific packages.
3. Enable access to internal elements: If you are confident that the access is safe and necessary, you can explicitly allow illegal reflective access by adding the following command-line argument to your IntelliJ run configuration or VM options: “–illegal-access=warn”. This option will generate a warning instead of an error message, giving you a chance to investigate the issue further. However, it is recommended to use this as a temporary solution and to refactor your code in the long term.
4. Refactor your code to use public APIs: Instead of accessing internal elements reflectively, refactor your code to use public APIs or interfaces. This approach ensures proper encapsulation and eliminates the need for illegal reflective access.
5. Use endorsed standards override mechanism (ESOM): As a last resort, you can use the ESOM to grant a higher level of access to particular packages or classes. However, note that this mechanism is highly discouraged and should only be used if no other alternative exists.
FAQs:
Q1. Why does IntelliJ show this error message even if everything seems to work fine?
IntelliJ follows a strict policy of providing developers with any potential problems that might arise from accessing internal elements. Even if your program runs without apparent issues, the IDE generates this warning to ensure you are aware of any potential consequences and encourage you to address the issue appropriately.
Q2. Can I ignore the illegal reflective access error?
While it is technically possible to ignore the error, it is not recommended to do so. This error warns you about potential future problems and security risks. It is good practice to address it promptly rather than ignoring it, as it might lead to unexpected issues down the line.
Q3. Is it safe to allow illegal reflective access?
Allowing illegal reflective access through the “–illegal-access=warn” option poses potential security risks. You should only use this as a temporary solution and work towards refactoring the code to eliminate the need for illegal reflective access.
Q4. Can I disable the error message in IntelliJ?
To remove the error message, you can go to IntelliJ’s settings, navigate to “Editor -> Inspections -> Java -> Reflection -> Illegal reflective access,” and disable the corresponding inspection. However, this does not resolve the issue; it only hides the error message.
In conclusion, encountering an “Illegal reflective access operation has occurred” error in IntelliJ can be a bit perplexing. However, through understanding the causes and employing the appropriate solutions, developers can overcome this issue without compromising the integrity and security of their software. By following the recommended steps and staying up to date with the latest software versions, you can ensure a smooth development experience with IntelliJ.
An Illegal Reflective Access Operation Has Occurred Eclipse
Eclipse is a widely used Integrated Development Environment (IDE) for Java programming. It provides developers with a seamless environment to write and debug their code. However, sometimes Eclipse can throw an error message that says, “An illegal reflective access operation has occurred.” This error can be confusing and frustrating, especially for beginners.
In this article, we will explore what this error means and why it occurs. We will also provide some possible solutions to help you resolve this issue and continue working with Eclipse without interruption.
What does the error message mean?
When Eclipse encounters an “illegal reflective access operation” error, it means that the Java runtime environment you are using is trying to access a part of the Java API that is restricted and not allowed to be accessed through reflection. Reflection is a powerful mechanism in Java that allows a program to examine or modify the behavior of classes, interfaces, methods, etc., at runtime. However, certain parts of the Java API are intentionally restricted and can only be accessed through non-reflective means. When you encounter this error, it indicates that someone is trying to access such restricted parts using reflection, which is not allowed.
Causes of the error
The “illegal reflective access operation” error can occur due to multiple reasons. Some common causes include:
1. Using an outdated version of Java: It is essential to use the correct version of Java that is compatible with the Eclipse IDE. Sometimes, using an outdated version of Java can lead to this error.
2. Incompatible plugins or libraries: Eclipse supports a vast range of plugins and libraries, which can enhance its functionality. However, using incompatible or outdated plugins/libraries can cause conflicts and result in this error.
3. Incorrect permissions: If the Eclipse installation directory or Java runtime environment lacks the required permissions, it can trigger the “illegal reflective access operation” error.
Solutions to resolve the error
Here are some possible solutions to fix the “illegal reflective access operation” error in Eclipse:
1. Update Java: Ensure that you have the latest version of Java installed on your system. You can download the latest Java Development Kit (JDK) from the official Oracle website. After the installation, update the Java path in your Eclipse IDE by navigating to Preferences > Java > Installed JREs.
2. Check plugin compatibility: If you have recently added new plugins or libraries, try disabling them one by one to identify the incompatible one. Remove the incompatible plugin or check for any available updates. It is recommended to stick with reliable and frequently updated plugins.
3. Grant necessary permissions: Ensure that the Eclipse installation directory and the Java runtime environment have the required read and write permissions. On Windows, right-click on the Eclipse folder, select Properties, and navigate to the Security tab. Here, provide read and write permissions to the appropriate users. On Linux/Unix, use the chmod command to grant permissions.
4. Update Eclipse: Keeping your Eclipse IDE up to date is crucial to benefit from bug fixes and enhancements. Check for the latest updates by navigating to Help > Check for Updates. If there are any available updates, install them and restart Eclipse.
5. Start Eclipse with clean configuration: Sometimes, the error can be caused by a corrupted or misconfigured configuration file. Start Eclipse with a fresh configuration by running it with the -clean parameter. Open the command prompt/terminal, navigate to the Eclipse installation directory, and run the command “eclipse -clean”. This will clear the cached plugins and recreate the configuration files.
Frequently Asked Questions (FAQs)
Q: Can I ignore this error and continue working in Eclipse?
A: It is generally not recommended to ignore this error, as it indicates that some part of your code is trying to access restricted parts of the Java API. Ignoring the error may lead to unexpected behavior or issues in the future. It is better to understand the cause and resolve it.
Q: I have multiple versions of Java installed on my system. Can that be causing this error?
A: Having multiple versions of Java installed on your system should not cause this error. However, it is crucial to ensure that you are using the correct version of Java with your Eclipse IDE. Make sure to update the Java path in Eclipse to point to the desired version.
Q: I have tried all the suggested solutions, but the error still persists. What should I do?
A: If none of the solutions mentioned above resolve the error, there may be an underlying issue with your Eclipse setup. Try reinstalling Eclipse and restoring your projects. Before reinstalling, make sure to take a backup of your projects to avoid any data loss.
In conclusion, encountering an “illegal reflective access operation” error in Eclipse can be frustrating, but with the right troubleshooting steps, you can resolve it and continue working smoothly. Make sure to keep your Java installation, Eclipse, and plugins up to date, grant necessary permissions, and double-check for any incompatible plugins or libraries. Happy coding!
Images related to the topic warning an illegal reflective access operation has occurred

Found 12 images related to warning an illegal reflective access operation has occurred theme



![JAVA] JDK 환경설정 / WARNING: An illegal reflective access operation has occurred 경고 해결 Java] Jdk 환경설정 / Warning: An Illegal Reflective Access Operation Has Occurred 경고 해결](https://img1.daumcdn.net/thumb/R800x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdn%2FbI1EFz%2Fbtrl6QckVIZ%2FmrXcXIWv8m3Y2HEtitkQZk%2Fimg.png)






Article link: warning an illegal reflective access operation has occurred.
Learn more about the topic warning an illegal reflective access operation has occurred.
- What is an illegal reflective access? – java
- Java 9 Illegal Reflective Access Warning
- Getting warnings about “illegal reflective access operation …
- Transition from Java 8 to Java 11 – Azure – Microsoft Learn
- How to fix “an illegal reflective access operation has …
- An Illegal Reflective Access Operation Has Occurred: Fixed
- An illegal reflective access operation has occurred when …
- Getting warnings about “illegal reflective access operation …
- How can I solve “WARNING:An illegal reflective access …
- running under Java 11 gives “illegal reflective access …
- Solved: Getting An illegal reflective access operation has…
- Illegal reflective access in JDK 11 : XD-888 – YouTrack
See more: nhanvietluanvan.com/luat-hoc