Unprotected Private Key File
In the world of cybersecurity, protecting sensitive information is of utmost importance. One such crucial component of securing systems is the private key file. A private key file, also known as an SSH key, is a cryptographic key used for secure communication and authentication. It plays a vital role in establishing a secure connection between two parties, preventing unauthorized access and data breaches. However, an unprotected private key file can expose a system to significant security risks, potentially leading to severe consequences. In this article, we will delve into the various aspects of unprotected private key files, including their generation, storage, access, risks, preventive measures, and best practices.
Generation of Private Key:
The private key is typically generated using encryption algorithms such as RSA or DSA. During the key generation process, a pair of keys, namely the private key and its corresponding public key, is created. The private key is retained by the owner, while the public key is shared with others to establish trusted connections. It is crucial to undertake this key generation process securely and with well-established cryptographic practices to ensure the integrity of the private key.
Storage of Private Key:
Storing the private key file securely is key to maintaining its confidentiality. It is recommended to store the private key file in an encrypted format, using strong and complex passphrase protection. Additionally, it is advisable to keep multiple backups of the private key file in secure locations, such as encrypted external storage devices or secure cloud storage services. By ensuring secure storage, the risk of unauthorized access to the private key file can be mitigated.
Access to Private Key:
Access to the private key file should be strictly controlled and limited to authorized individuals. Only individuals who genuinely require access for the intended purposes, such as system administrators or automated scripts, should be granted permission. Implementing a robust access control mechanism, such as role-based access control (RBAC), helps ensure that only authorized users can read or modify the private key file.
Security Risks of Unprotected Private Key Files:
An unprotected private key file poses various security risks that can potentially compromise the confidentiality and integrity of systems and sensitive data. Some prominent risks include:
1. Unauthorized Access: If an attacker gains access to an unprotected private key file, they can impersonate the legitimate owner and gain unauthorized access to systems, services, or data.
2. Credential Theft: A compromised private key file could lead to credential theft, enabling attackers to access other systems or escalate their privileges within the compromised environment.
3. Data Breach: An attacker with access to a private key file can intercept and decrypt sensitive data transmitted between systems, leading to a data breach.
4. Key Validation Errors: Improper file permissions or invalid key formats can cause key validation errors, leading to failures in establishing secure connections and potentially disrupting critical services.
Preventive Measures for Protecting Private Key Files:
To mitigate the security risks associated with unprotected private key files, certain preventive measures should be implemented. These include:
1. Encryption: Encrypt the private key file using strong algorithms and protect it with a complex passphrase to prevent unauthorized access.
2. Secure Storage: Store the private key file in encrypted formats, such as password-protected or encrypted external storage devices or secure cloud storage services.
3. Access Control: Limit access to the private key file to only authorized individuals or processes. Employ mechanisms like RBAC to control and manage user permissions effectively.
4. Regular Key Rotation: Periodically rotate private keys to ensure their freshness and invalidate any compromised or outdated keys.
Consequences of Unprotected Private Key Files:
The consequences of leaving private key files unprotected can be severe and far-reaching. Some potential outcomes include:
1. System Compromise: Attackers can gain unauthorized access to systems, leading to data breaches, service disruption, or even complete system compromise.
2. Financial Loss: A security breach resulting from an unprotected private key file could lead to significant financial losses associated with incident response, recovery, and potential legal liabilities.
3. Damage to Reputation: Data breaches or unauthorized access incidents can tarnish an organization’s reputation, eroding customer trust and confidence.
Best Practices for Handling Private Key Files:
To ensure optimal security when handling private key files, it is essential to adhere to best practices. Some recommended practices include:
1. Secure Key Generation: Follow established cryptographic practices and use well-vetted algorithms and key lengths during private key generation.
2. Regular Auditing: Periodically review access logs and audit trails to identify any unauthorized or suspicious activities related to private key file access.
3. Revoke Access: Immediately revoke access to the private key file in the event of personnel changes or specific requirements.
4. Regular Updates: Stay updated with the latest security patches and updates for the software or systems utilizing the private key file.
5. Training and Awareness: Conduct regular training and awareness programs to educate employees and stakeholders about the importance of securing private key files and the potential risks associated with mishandling them.
In conclusion, an unprotected private key file can expose systems to significant security risks, potentially leading to severe consequences. By following best practices, implementing preventive measures, and prioritizing the security of private key files, organizations can minimize the likelihood of unauthorized access, data breaches, and system compromises. Protecting private key files is a critical step towards maintaining the confidentiality, integrity, and availability of sensitive information.
How To Resolve \”Warning: Unprotected Private Key File\” Error In Aws Ec2.
What Does Warning Unprotected Private Key File Mean?
When dealing with computer security, the concept of private key files is commonly encountered. These files play a vital role in encryption, authentication, and secure communication. However, occasionally users may come across a warning message stating, “Warning: Unprotected Private Key File”. This article will delve into the meaning behind this warning, its implications, and how to address the issue.
Understanding Private Key Files:
A private key file is a critical component in asymmetric encryption algorithms such as RSA and Elliptic Curve Cryptography. It acts as the counterpart to a public key, allowing users to encrypt or decrypt data securely. Private keys are typically stored in files, often with a .pem or .key extension. These files contain sensitive information and should be handled with utmost care.
The Warning Message:
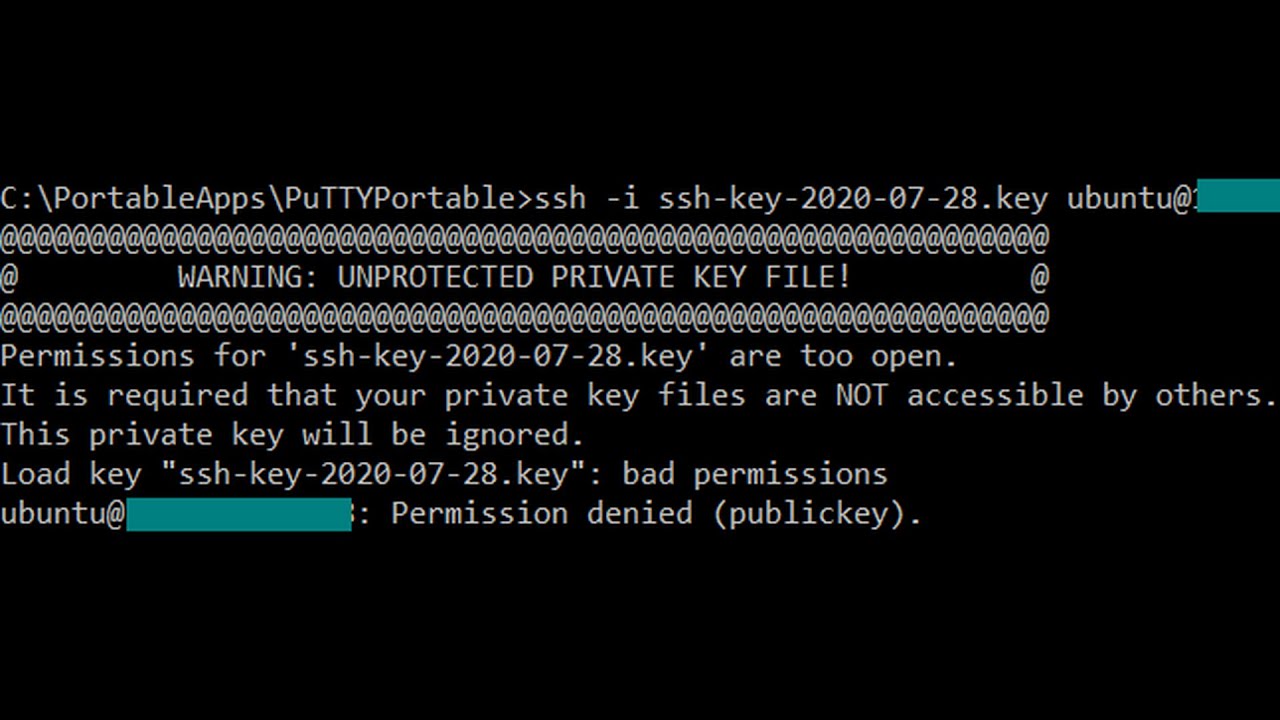
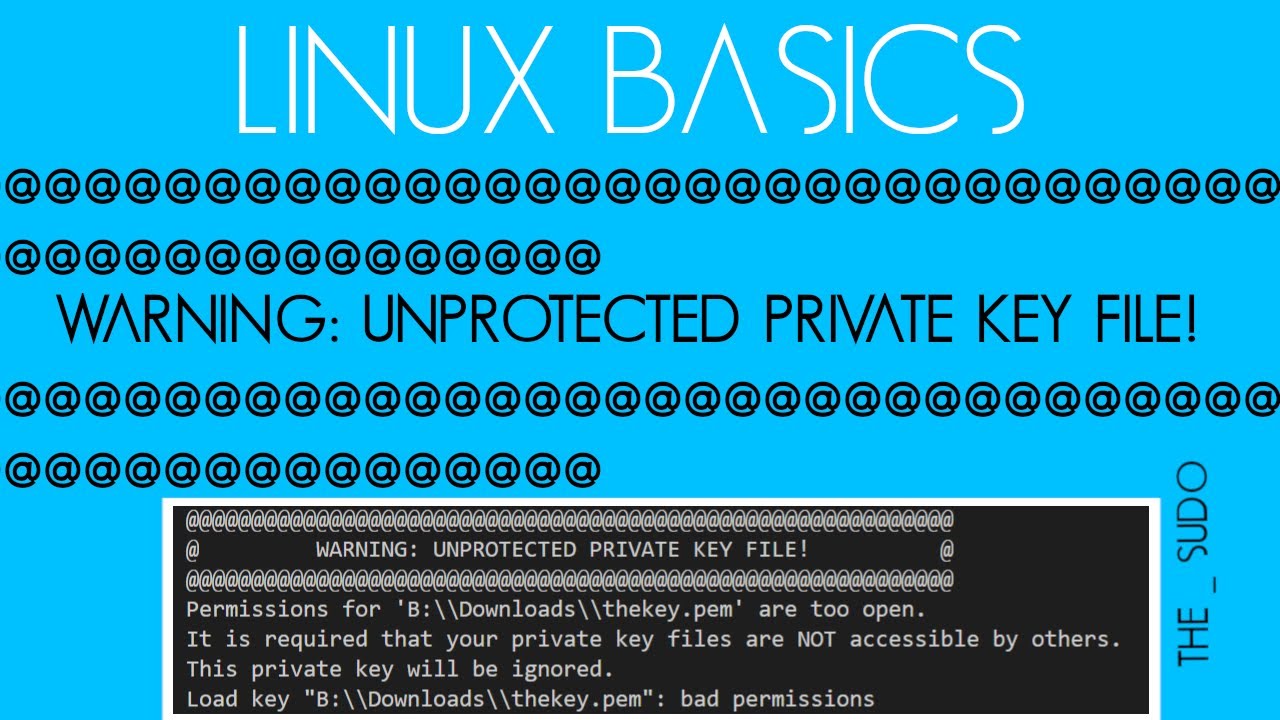
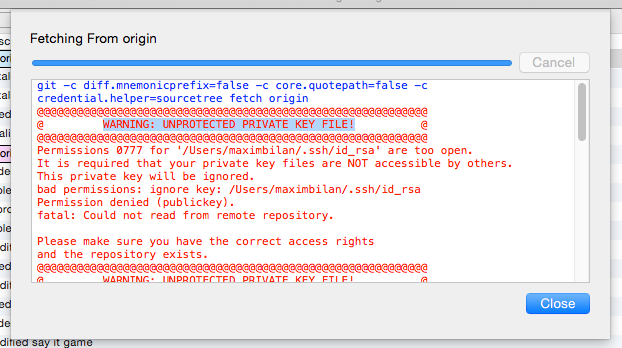
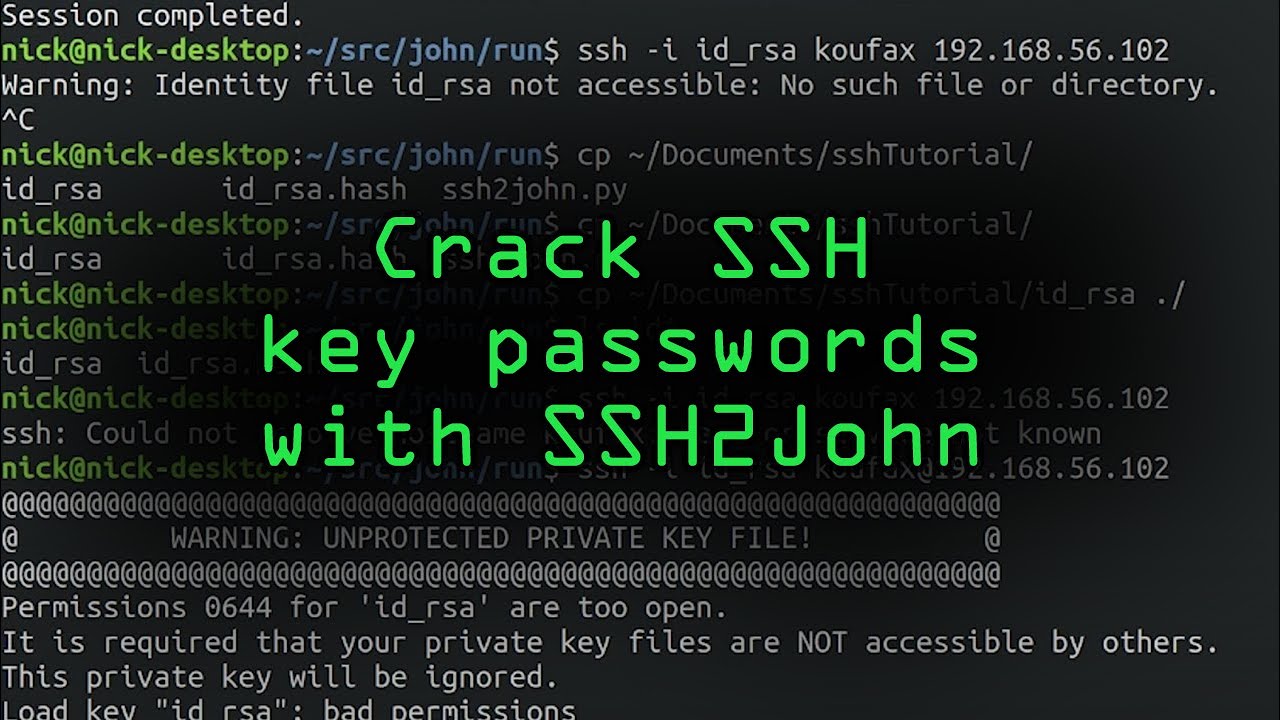
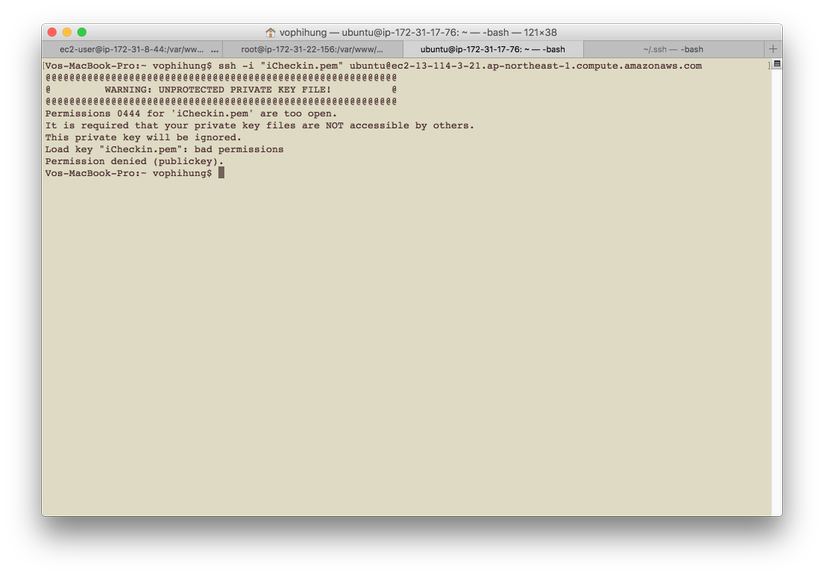
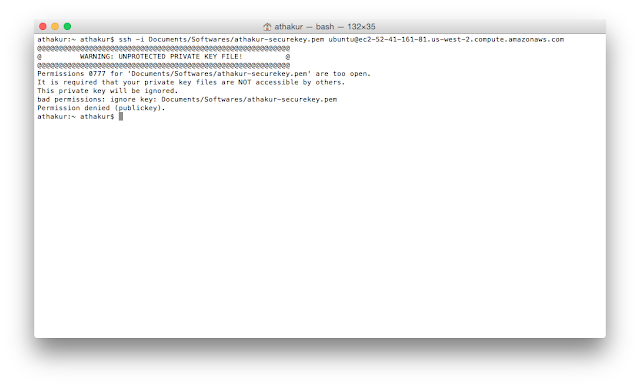
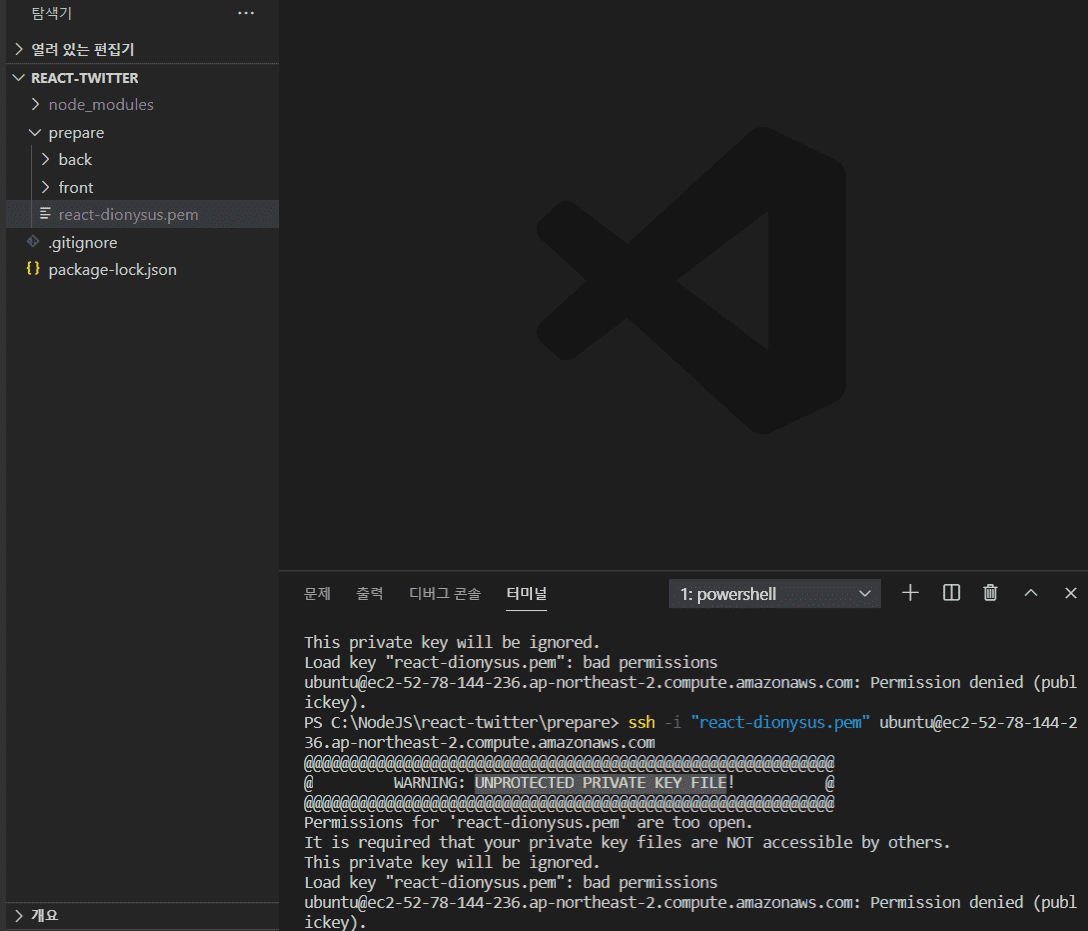
Encountering the warning message “Warning: Unprotected Private Key File” indicates that the private key file is not adequately protected. This means that the file has incorrect permissions or is accessible to unauthorized individuals or processes. The warning should not be taken lightly, as an unprotected private key file could result in severe security breaches.
Reasons for an Unprotected Private Key File:
There are several reasons why a private key file may be left unprotected:
1. Insufficient Permissions: The file may have incorrect permissions set, allowing unauthorized access. In some cases, the file may be accessible by a group or user who should not have permission to access it.
2. Accidental Exposure: Unintentional actions, such as sharing the private key file in an unsecured manner or placing it in a public directory, can lead to its exposure.
3. Insecure Storage: If the private key file is stored on an inadequately secured device or server, it is susceptible to unauthorized access.
Implications of an Unprotected Private Key File:
If an unprotected private key file falls into the wrong hands, the consequences can be dire. Attackers could potentially decrypt sensitive data, impersonate legitimate users, or launch man-in-the-middle attacks. Furthermore, this could compromise the integrity and confidentiality of communication channels, jeopardizing the security of individuals and organizations.
Addressing the Issue:
To mitigate the risks associated with an unprotected private key file, various measures can be taken:
1. Review File Permissions: Ensure that the private key file has appropriate permissions set. It should be accessible only to authorized users or processes. Regularly monitor and restrict access to such files.
2. Secure Storage: Store private key files in secure locations, such as encrypted directories or hardware security modules. Avoid keeping them on easily accessible devices or servers.
3. Encryption: If the private key file contains particularly sensitive information or you require an extra layer of security, consider encrypting the file itself. This adds an additional barrier to unauthorized access.
4. Regular Auditing: Conduct periodic audits of systems and devices to identify any potential vulnerabilities or unprotected private key files. This helps in promptly addressing any security gaps and reducing exposure.
FAQs:
Q: Is it safe to ignore the warning message about an unprotected private key file?
A: No, it is not safe to ignore the warning message. It indicates that the private key file is at risk of unauthorized access and potential security breaches.
Q: What are the possible consequences of an unprotected private key file?
A: An unprotected private key file can lead to unauthorized decryption of sensitive data, impersonation attacks, and compromised communication channels.
Q: How can I protect my private key files?
A: Ensure appropriate file permissions, store them securely, consider encryption, and conduct regular audits of systems to minimize exposure.
Q: Are private key files only used in the context of encryption?
A: Private key files are indeed crucial for encryption, but they also play a significant role in authentication and secure communication protocols.
Q: What actions should be taken if an unprotected private key file is discovered?
A: If an unprotected private key file is found, it is crucial to immediately review file permissions, move it to a secure location, and notify relevant stakeholders about the security breach.
In conclusion, encountering a warning message stating “Warning: Unprotected Private Key File” highlights a potential security vulnerability. Users must understand the importance of protecting private key files, address any issues promptly, and implement security measures to safeguard sensitive information and ensure secure communication.
How To Protect Ssh Key File?
SSH (Secure Shell) is a widely used cryptographic network protocol that provides secure remote access to systems and data over an unsecured network. SSH key pairs are an integral part of SSH authentication and are used to establish a secure connection between the client and the server. Ensuring the security and confidentiality of your SSH key files is crucial, as they grant access to sensitive information and systems. In this article, we will delve into various techniques to protect your SSH key file and minimize the risk of unauthorized access.
1. Generate SSH Keys with Strong Passphrases:
The first step towards protecting your SSH key file is to generate a strong passphrase during key creation. A strong passphrase is a combination of upper and lower case letters, numbers, and special characters that are unique and not easily guessable. A complex passphrase adds an additional layer of security by protecting the private key stored locally.
2. Store SSH Keys in a Secure Location:
Once the SSH keys are generated, it is essential to store them in a secure location. Restrict access to these files, allowing only authorized users to view and modify them. It is advisable to store SSH key files on removable media (like USB drives) that are encrypted and password protected. This way, even if the device is lost or stolen, the keys remain secure.
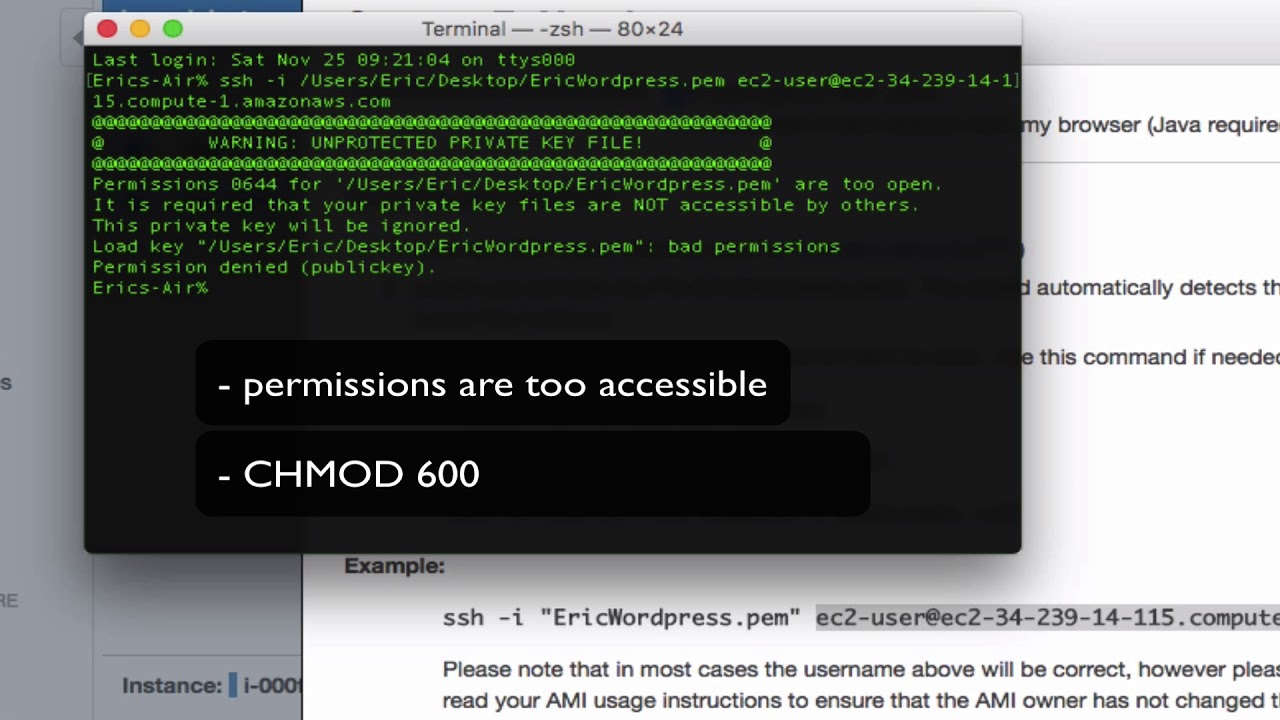
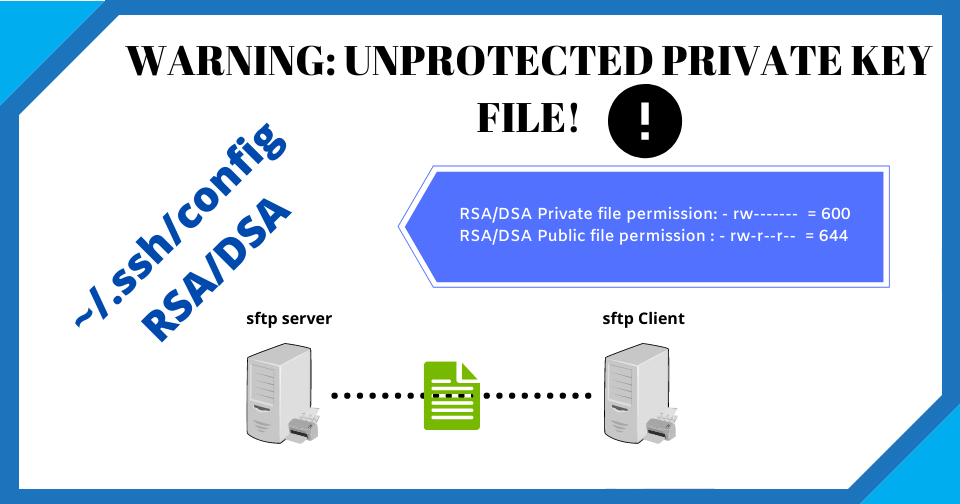
3. Protect SSH Key Files with File Permissions:
Setting appropriate file permissions for SSH key files is crucial to prevent unauthorized access. On Unix-like systems, SSH key files should be readable only by the owner (chmod 600) and, if necessary, group (chmod 640). By limiting the permissions, you reduce the risk of malicious users gaining access to your SSH key files.
4. Utilize Secure Passwords for System User Accounts:
One common way for attackers to gain unauthorized access to SSH keys is by compromising system user accounts. Ensuring that strong, unique passwords are used for system user accounts reduces the probability of brute-force attacks and unauthorized access to SSH key files.
5. Enable Two-Factor Authentication:
Enabling two-factor authentication (2FA) for SSH adds an extra layer of security, requiring not only the SSH key file but also a second form of authentication, such as a password or a time-based one-time password (TOTP). Various 2FA solutions can be implemented, including Google Authenticator or hardware tokens like YubiKey.
6. Limit SSH Access:
One effective way to protect SSH key files is to restrict access to only authorized users. By limiting SSH access to specific IP addresses or user groups, you reduce the risk of unauthorized individuals attempting to access your SSH key files.
7. Regularly Rotate SSH Keys:
Regularly changing SSH keys is a good security practice. Implementing a key rotation policy ensures that compromised or outdated keys do not pose a threat to your system’s security. Whenever a key is rotated, make sure to revoke access for the old key to prevent any unauthorized access attempts.
8. Monitor and Audit SSH Connections:
Monitoring and logging SSH connections are essential to identify any malicious activities or potential security breaches. By logging SSH sessions and monitoring key-based authentication attempts, you can detect any unauthorized use and take immediate action.
FAQs:
Q1. Can I share my SSH key file with others?
While sharing SSH key files may be necessary for specific cases, it is generally not recommended. Sharing SSH key files increases the risk of unauthorized access and compromises the confidentiality of your system. If sharing is unavoidable, consider creating separate key pairs for each user and applying restrictive access controls.
Q2. What should I do if my SSH key file is compromised?
If you suspect that your SSH key file has been compromised, the first step is to immediately revoke access using that key. Generate a new SSH key pair with a strong passphrase and update it on all the necessary servers. Additionally, investigate the source of the compromise and take appropriate action to prevent future incidents.
Q3. Can I recover my SSH key file if it is lost?
If your SSH key file is lost or deleted, recovery is not possible. It is essential to have a backup of your SSH key file in a secure location. Without a backup, you will need to generate a new SSH key pair and update it accordingly on all systems where the old key was in use.
Q4. Should I use password authentication with SSH key authentication?
Using password authentication alongside SSH key authentication (2FA) is generally considered best practice. It provides an added layer of security, reducing the risk of compromising the SSH key file itself. Additionally, enforcing strong password policies adds an extra level of protection. However, it is essential to consider the specific requirements and limitations of your environment when determining the authentication methods to use.
In conclusion, protecting your SSH key file is of utmost importance in maintaining the security of your systems and data. By following the guidelines mentioned above, you can significantly minimize the risk of unauthorized access and potential security breaches associated with SSH keys. Remaining vigilant, keeping your systems up to date, and educating users about the best practices surrounding SSH key file protection are vital aspects of ensuring robust security.
Keywords searched by users: unprotected private key file Load key bad permissions, Load key invalid format, Remove ssh key, Ssh with pem file, Chmod 400 Windows, Key is invalid you must supply a key in OpenSSH public key format, Remove SSH key Windows 10, it is required that your private key files are not accessible by others.
Categories: Top 98 Unprotected Private Key File
See more here: nhanvietluanvan.com
Load Key Bad Permissions
In the vast realm of computer science, one of the prevalent issues that users frequently encounter is related to bad permissions when loading a key. This problem, commonly referred to as “Load Key Bad Permissions,” can be frustrating and confusing for the average user. To address the issue comprehensively, this article aims to explain what Load Key Bad Permissions entail, explore its causes, and provide potential solutions to overcome it.
Understanding Load Key Bad Permissions
Load Key Bad Permissions is an error message that can be encountered when attempting to load a cryptographic key, typically within the context of encryption or digital signatures. This error arises due to inadequate or improper access permissions for the key file, preventing the system from loading it successfully. When the operating system or a specific application tries to access the key, it realizes that the necessary permissions are missing or wrong, leading to the error message.
Causes of Load Key Bad Permissions
1. Insufficient User Privileges: The most common cause of Load Key Bad Permissions is inadequate user privileges. If the user attempting to load the key does not have the necessary permissions, the system will prevent the action, resulting in the error message. This typically occurs when non-administrative users attempt to access certain files requiring elevated privileges.
2. Incorrect File Permissions: Another cause of this error is incorrect file permissions. If the key file is set to read-only or lacks the necessary read and write permissions, the system will fail to load the key. Incorrect permissions can arise due to improper configuration during key generation or when transferring the key between systems.
3. File Location: The location of the key file can also lead to Load Key Bad Permissions. If the key file is located in a restricted system directory or a location that requires elevated permissions, it may trigger the error message. This generally occurs when attempting to load a key from a system-protected folder.
Resolving Load Key Bad Permissions
To overcome Load Key Bad Permissions, several potential solutions can be tried depending on the underlying cause:
1. Run as Administrator: If insufficient user privileges are the culprit, try running the program or command prompt as an administrator. Alternatively, grant the necessary permissions to the user account to access the key file. Ensure that you possess administrative rights or consult with the system administrator if required.
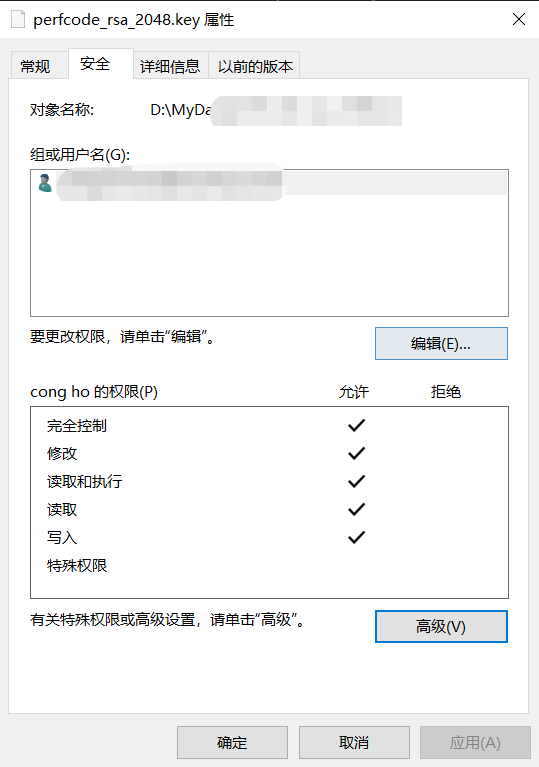
2. Modify File Permissions: If the issue is incorrect file permissions, modify the permissions of the key file accordingly. Right-click on the file, choose Properties, navigate to the Security tab, and grant read and write permissions to the relevant user accounts. It is crucial to apply these changes to both the file and any parent directories if required.
3. Change File Location: If the key file is stored in a restricted folder, move it to a different location with more relaxed permissions. Preferably, store it in a newly created folder outside of system-protected directories. Ensure you have appropriate read and write access to the new location.
4. Generate a New Key: On rare occasions, the key file itself may be corrupt or have incorrect permissions embedded within it. In such cases, consider generating a new key and ensuring its permissions are properly configured from the beginning. This approach may require updating relevant configurations in applications or systems relying on the key.
Frequently Asked Questions (FAQs)
Q: Are Load Key Bad Permissions limited to a specific operating system?
A: No, Load Key Bad Permissions can occur across various operating systems, including Windows, macOS, and Linux.
Q: Can these permissions impact the functionality of applications relying on the key?
A: Yes, incorrect permissions can prevent applications from loading or accessing the key, impairing their functionality or rendering them completely non-functional.
Q: How can I identify if Load Key Bad Permissions are the issue?
A: Usually, an error message explicitly stating “Load Key Bad Permissions” or a related variant will appear. Additionally, checking the key file’s permissions and the user account attempting to load it can provide valuable insights.
Q: Is it recommended to share the key file with others to resolve this issue?
A: No, sharing the key file is not recommended unless required for collaboration. Sharing cryptographic keys should be done securely and with utmost caution.
Q: Is there a universal solution for Load Key Bad Permissions?
A: Due to various causes, there isn’t a universal solution to this issue. The appropriate solution depends on the underlying cause of the error.
In conclusion, Load Key Bad Permissions can be a troublesome obstacle when dealing with cryptographic keys. Understanding the causes and appropriate solutions can help users navigate and resolve this error effectively. Ensure you possess the necessary permissions, modify file permissions if required, and consider relocating the key file to a suitable location. By following these guidelines, users can overcome Load Key Bad Permissions and continue leveraging secure encryption and digital signature functionality.
Load Key Invalid Format
When working with various electronic devices or software applications, encountering errors is not an uncommon occurrence. One of the frequently encountered errors is “Load Key Invalid Format.” This error message often leaves users puzzled, as it can hinder the functionality of the device or application. In this article, we will delve into the depths of this error, understand its causes, and explore solutions to resolve it effectively.
Understanding the Error:
The “Load Key Invalid Format” error usually occurs during encryption or decryption processes. This error message is commonly seen when dealing with cryptographic software, such as encryption tools, secure connection establishment protocols, or digital certificates. It may also appear when working with devices that utilize encryption algorithms like USB drives, external hard drives, or even some smart cards.
Causes of “Load Key Invalid Format” Error:
1. Corrupted Key File: One of the main reasons for encountering this error is a corrupted key file. If the encryption or decryption software cannot interpret the key file’s format, it will result in the “Load Key Invalid Format” error. This corruption may happen due to improper transfer or storage of the key file, software bugs, or data transmission errors.
2. Incompatible Key File Format: Different software applications or devices may use different key formats. If a key file generated by one software or device is used in another software or device that does not support that particular format, the “Load Key Invalid Format” error may arise. It is essential to ensure compatibility between the key file and the software or device being used.
3. Version Incompatibility: Using an outdated version of the encryption software or device’s firmware can also lead to encountering this error. Developers regularly release updates to enhance security and fix known issues. Therefore, keeping software and firmware up to date is crucial to avoiding compatibility issues and error messages like “Load Key Invalid Format.”
Solutions to Resolve the Error:
1. Confirm Key File Integrity: To ensure that the key file is not corrupted, verify its integrity by comparing the file’s checksum or hash value with the original. Additionally, if the key file was transferred, try transferring it again using a different method, such as using a different USB cable or sending it through a different file transfer protocol.
2. Generate a New Key File: If the key file is indeed corrupted, generating a new key file from scratch might resolve the issue. By doing so, you eliminate the possibility of using an incompatible or corrupted key file. However, make sure to use software or devices that are known to be compatible with your encryption or decryption process.
3. Update Software/Firmware: If you suspect that the error arises due to version incompatibility, update the software or firmware to the latest stable version available. Visit the official website of the software or device manufacturer to check for any available updates. Be cautious while updating, as any interruption during the update process might exacerbate the error or cause further system issues.
Frequently Asked Questions:
1. Is the “Load Key Invalid Format” error reversible?
Yes, this error is reversible, and there are several solutions that can be employed to resolve it. By following the steps mentioned above, users can often overcome the error and restore the encryption or decryption functionality of their software or devices.
2. Can antivirus software interfere with key files, leading to this error?
Although it is rare, certain antivirus software with strict security measures can sometimes interfere with key files, resulting in the “Load Key Invalid Format” error. Temporarily disabling the antivirus software or adding an exception for the encryption or decryption process might resolve the issue.
3. What are the best practices to prevent encountering this error?
To prevent encountering the “Load Key Invalid Format” error, it’s essential to follow some best practices:
– Regularly update software and firmware to the latest versions.
– Store key files securely, ensuring there is no risk of corruption or accidental deletion.
– Utilize reputable encryption tools and devices that are known for their compatibility and reliability.
– Backup key files regularly to avoid potential loss or corruption.
In conclusion, the “Load Key Invalid Format” error is a common issue faced by users dealing with encryption or decryption processes. Understanding its causes, such as corrupted or incompatible key files, and following the suggested solutions will assist users in successfully resolving the error. By employing preventive measures and maintaining up-to-date software and firmware, users can minimize the occurrence of such errors and ensure the smooth functioning of their encrypted files and devices.
Remove Ssh Key
Introduction:
SSH (Secure Shell) keys are essential tools that provide secure and encrypted access to remote systems. They serve as a more secure alternative to passwords, making them an integral part of modern cybersecurity practices. However, there may come a time when you need to remove an SSH key from your system or revoke access for various reasons. In this article, we will explore the effective methods to remove SSH keys and address some common questions regarding this process.
I. Understanding SSH Keys and Their Importance:
Before delving into SSH key removal, it is crucial to understand the significance of SSH keys and why they are used. SSH keys are cryptographic key pairs that consist of a public and private key. The public key is stored on the remote server, while the private key remains on the user’s local machine. This unique verification system ensures secure authentication and protects against unauthorized access.
Benefits of Using SSH Keys:
1. Enhanced Security: SSH keys add an extra layer of security by eliminating the need for passwords, which can be compromised or guessed.
2. Simplified Authentication: SSH keys provide a seamless authentication process, enabling quick and automated access to remote systems.
3. Increased Productivity: By eliminating the hassle of remembering and entering passwords, SSH keys save time and streamline workflow.
II. How to Remove SSH Keys:
1. Removing SSH Keys from Remote Servers:
To revoke access to a specific server, you must remove the corresponding SSH key from the server. The process may vary depending on the operating system. Here are the general steps:
– Log in to the remote server and navigate to the user’s home directory.
– Look for a file named “.ssh/authorized_keys” or similar. Open the file in a text editor.
– Locate the line containing the public key you wish to remove and delete it.
– Save the changes and exit the editor. The SSH key is now removed from the remote server.
2. Removing SSH Keys from Local Machines:
If you wish to remove an SSH key from your local machine, you can do so by following these steps:
– Navigate to the directory where your SSH keys are stored (typically “~/.ssh/”).
– Look for the public key file associated with the key pair you wish to remove.
– Delete the corresponding public key file from the directory.
– If using an SSH agent, remove the key from the agent using the “ssh-add -d” command.
– Restart the SSH agent to ensure the changes take effect.
III. FAQs:
1. Can I remove an SSH key without root access?
Yes, it is possible to remove SSH keys from remote servers without root access. As long as you have access to the user’s home directory and the “.ssh/authorized_keys” file, you can edit the file and remove the desired key without administrative privileges.
2. Can removing an SSH key cause disruptions?
Removing an SSH key from either the remote server or the local machine should not cause any disruptions to existing connections or services. However, it is essential to ensure that the key you intend to remove is not actively being used for critical operations.
3. How do I replace an SSH key while removing an old one?
To replace an existing SSH key while removing the old one, follow these steps:
– Generate a new SSH key pair using tools like ssh-keygen.
– Remove the old SSH key from both the local machine and the remote server.
– Add the new SSH key to the desired locations, including authorized_keys on remote servers and the local SSH configuration file.
4. Are there any security concerns when removing SSH keys?
When removing unused or compromised SSH keys, security concerns are minimal. However, it is crucial to ensure that the key you remove is not inadvertently being used by any ongoing processes or services. Additionally, should you suspect malicious activity, promptly remove the SSH key and investigate any potential security breaches.
Conclusion:
By understanding how to remove SSH keys, you can maintain a streamlined and secure remote access system. Whether you need to revoke access or replace an existing key, the process is relatively straightforward. Just remember to exercise caution during the removal process and follow best security practices to keep your system safe from unauthorized access.
Images related to the topic unprotected private key file

Found 25 images related to unprotected private key file theme



















![Git] WARNING: UNPROTECTED PRIVATE KEY FILE! | 卡螺絲 Git] Warning: Unprotected Private Key File! | 卡螺絲](https://d33wubrfki0l68.cloudfront.net/971ef90f4ede575b157b643a5c2dfce9c0d68694/86f63/images/2013/12/git-warning-unprotected-private-key-file.png)

![SOLVED] WARNING Unprotected Private RSA Pem Key File Ansible EC2 Windows Ubuntu Debian - YouTube Solved] Warning Unprotected Private Rsa Pem Key File Ansible Ec2 Windows Ubuntu Debian - Youtube](https://i.ytimg.com/vi/CLaz2DmXtuI/maxresdefault.jpg)












Article link: unprotected private key file.
Learn more about the topic unprotected private key file.
- Getting “Warning: unprotected private key file!” error message …
- Sửa lỗi WARNING: UNPROTECTED PRIVATE KEY FILE!
- How to resolve the “SSH Unprotected Private Key File” warning
- UNPROTECTED PRIVATE KEY FILE!” on Linux – How-To Geek
- UNPROTECTED PRIVATE KEY FILE!” on Linux – How-To Geek
- SSH Key Management Overview & 10 Best Practices – BeyondTrust
- 4.1.3 Ensure private key permissions are restricted – Tenable
- Enabling RSA key-based authentication on UNIX and Linux …
- Warning Unprotected Private Key File AWS EC2 Error [Solved]
- How to Fix “WARNING: UNPROTECTED PRIVATE KEY FILE …
- Fixing UNPROTECTED PRIVATE KEY FILE.md – GitHub Gist
- WARNING: UNPROTECTED PRIVATE KEY FILE! – LinkedIn
- Unable to SSH with “Permissions for key are too open …
See more: https://nhanvietluanvan.com/luat-hoc