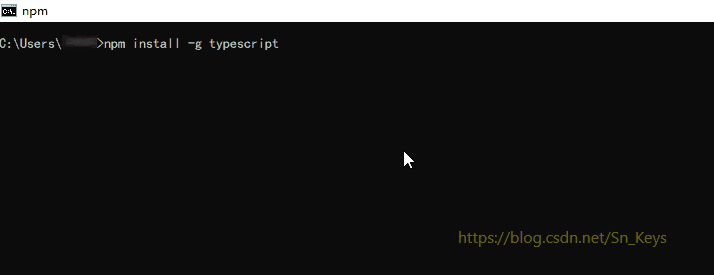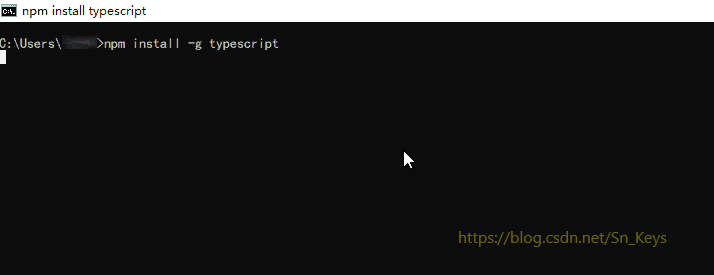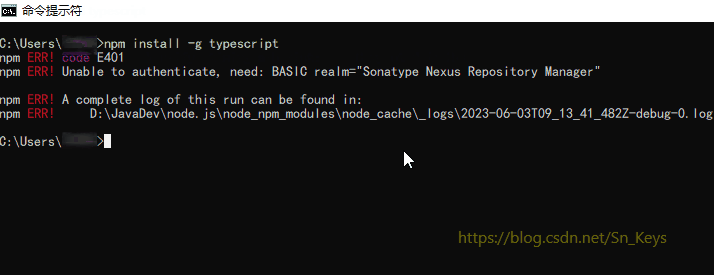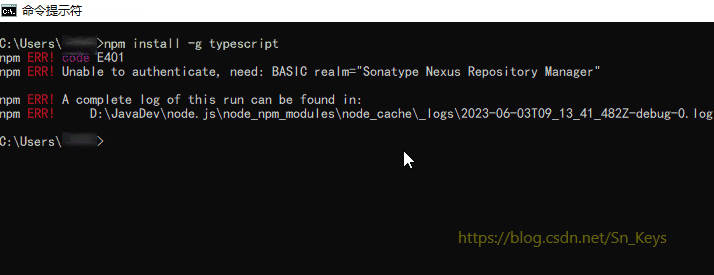
Unable To Authenticate Need Basic Realm Sonatype Nexus Repository Manager
Overview of Sonatype Nexus Repository Manager
Sonatype Nexus Repository Manager is a highly popular and widely used open-source repository manager tool that allows developers to store, manage, and distribute software components. It provides a robust and scalable solution for managing dependencies, artifacts, containers, and other software components in an organized and efficient manner.
Importance of Authentication in Sonatype Nexus Repository Manager
Authentication plays a crucial role in Sonatype Nexus Repository Manager as it ensures that only authorized users have access to the repositories. With proper authentication mechanisms in place, organizations can prevent unauthorized access, data breaches, and the distribution of malicious components. It helps maintain the integrity and security of the software components stored in the repository manager.
Common Authentication Issues in Sonatype Nexus Repository Manager
1. “Unable to authenticate” error message: This error occurs when a user attempts to access a repository without providing valid login credentials. It indicates that the authentication process has failed, and the user is denied access to the repository.
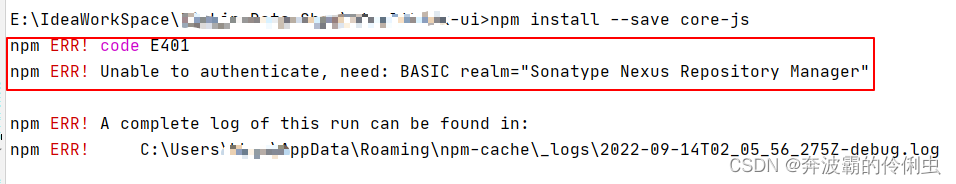
2. “Npm ERR code E401”: This error typically occurs when trying to publish or install packages using npm (Node Package Manager). It signifies that the authentication credentials provided are either incorrect or missing.
3. “Npm Nexus repository”: This issue arises when the npm client is unable to authenticate with a Nexus repository. It may be caused by incorrect configuration settings or a misconfigured authentication realm.
Understanding the “unable to authenticate” Error Message
The “unable to authenticate” error message indicates that the authentication process in Sonatype Nexus Repository Manager has failed. It means that the user’s credentials were either not provided or were invalid. This error prevents users from accessing the repositories and performing operations such as publishing, installing, or downloading artifacts.
Troubleshooting Steps for Resolving the Authentication Issue
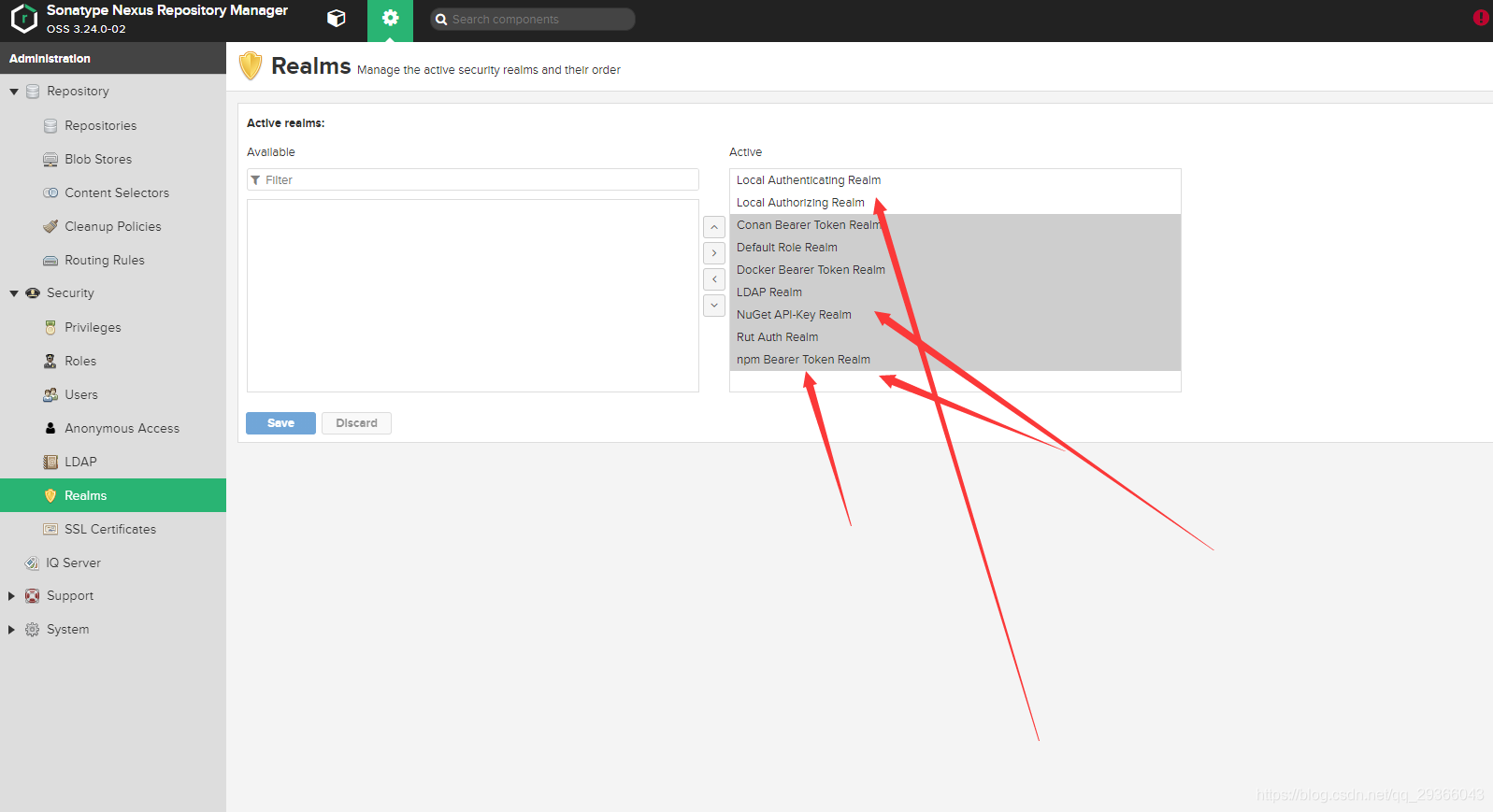
1. Checking the Basic Realm Configuration in Sonatype Nexus:
– Ensure that the Basic Realm authentication method is enabled in the Nexus configuration settings.
– Confirm that the realm is properly configured to authenticate users against the desired authentication source, such as an LDAP server or a local user database.
2. Verifying User Credentials for Authentication:
– Double-check the username and password entered during the authentication process.
– Ensure that the credentials are correct and match the user’s account in the authentication source.
– Consider using password managers to avoid typos or mistakes in credentials.
3. Resetting the User Password in Sonatype Nexus:
– If the user has forgotten their password or suspects it to be incorrect, resetting the password can be a solution.
– Utilize the appropriate methods provided by Sonatype Nexus to reset the password, such as using the administrative console or contacting the system administrator.
Additional Tips and Best Practices for Authentication in Sonatype Nexus
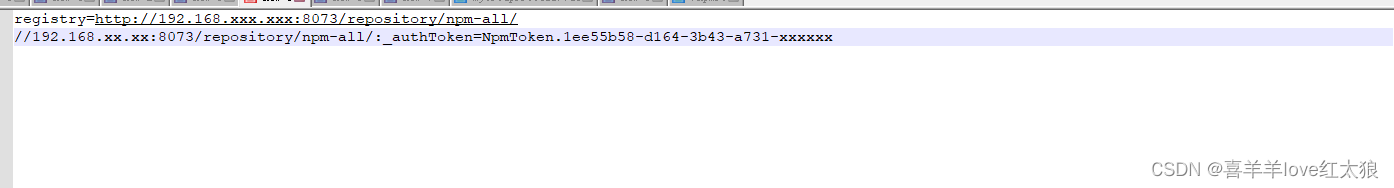
1. Config auth _authToken Username and Password must be Scoped to a Registry:
– When authenticating with private registries, ensure that the username and password are properly scoped to the specific registry. This is critical for successful authentication.
2. Make Sure the Artifact Exists in the npm Registry:
– Verify that the artifact you are trying to access or install is available in the npm registry. If it is not present, authentication issues may occur.
3. Web Login Not Supported:
– It’s important to note that Sonatype Nexus does not support web login by default. Users must authenticate using tools or clients that support the authentication methods employed by the repository manager.
FAQs
1. What does “Basic realm” mean in the “unable to authenticate” error message?
– The “Basic realm” refers to the specific authentication realm configured in Sonatype Nexus Repository Manager. It is used to identify and authenticate users against a given authentication source.
2. How can I resolve the “Npm ERR code E401” error in Sonatype Nexus?
– To resolve this error, ensure that the npm configuration and authentication settings are correctly configured in your Nexus repository. Verify that the provided authentication credentials are valid and have the necessary access rights.
3. Can Sonatype Nexus support authentication against external authentication sources like LDAP?
– Yes, Sonatype Nexus supports authentication against external sources like LDAP, Active Directory, and other user databases. You can configure these authentication realms within Nexus to authenticate users from these sources.
4. What should I do if I forget my password in Sonatype Nexus?
– If you forget your password, reach out to your system administrator or follow the appropriate password reset procedures as defined by your organization. Sonatype Nexus provides methods to reset passwords either through its administrative console or by contacting the administrator.
Nodejs : Npm Error E401: Unable To Authenticate, Need: Basic Realm=\”Sonatype Nexus Repository Manage
What Are The Default Credentials For Sonatype Nexus Repository Manager?
Sonatype Nexus repository manager is a widely used tool for managing artifacts and repositories in the software development life cycle. It provides a secure and efficient way to store, organize, and distribute software components. When deploying Sonatype Nexus for the first time, it is essential to understand the default credentials and their implications on the security of the platform.
By default, the Sonatype Nexus repository manager does not have any predefined credentials. This means that there are no out-of-the-box username and password combinations that grant access to the system. When the Sonatype Nexus is installed, it is necessary to set up an initial administrative user account with appropriate privileges.
During the installation process, Sonatype Nexus will prompt the user to create a new administrative user and specify a password. This user will have full access to all the functionalities and configurations of the Nexus repository manager. It is crucial to ensure that the password is strong and unique to prevent unauthorized access to the system.
It is recommended to follow best practices for password management, such as using a combination of uppercase and lowercase letters, numbers, and special characters. Additionally, it is advisable to regularly update the administrative user’s password and avoid using common or easily guessable passwords.
FAQs:
Q: What happens if I forget the administrative user’s password?
A: If you forget the password for the administrative user, it is still possible to regain access to the system. The Sonatype Nexus provides a password reset functionality that allows you to reset the password for the administrative user. This process typically involves executing a command or running a script provided by Sonatype. By following the instructions, you can reset the password and regain access to the Sonatype Nexus repository manager.
Q: Can I create additional user accounts with different access permissions?
A: Yes, Sonatype Nexus allows the creation of multiple user accounts with different access permissions. These accounts can have varying degrees of access to repositories and functionalities based on the user’s role and responsibilities. By creating separate user accounts, it is possible to enforce granular access control and ensure that each user has access only to the necessary resources.
Q: What are some recommended security measures for Sonatype Nexus repository manager?
A: Apart from setting up strong passwords for administrative and user accounts, there are several other security measures to consider. It is crucial to regularly update Sonatype Nexus to the latest version, as these updates often contain security patches and bug fixes. Configuring firewall rules to limit access to the Nexus repository manager is another recommended practice. Additionally, enabling HTTPS for secure communication and implementing secure network configurations provide an extra layer of protection.
Q: Can I integrate Sonatype Nexus repository manager with my existing authentication system?
A: Yes, Sonatype Nexus supports integration with external authentication systems such as LDAP (Lightweight Directory Access Protocol) or Active Directory. This integration allows users to authenticate using their existing credentials within the organization, simplifying the user management process and ensuring consistent authentication mechanisms across systems.
Q: Are there any additional security features in Sonatype Nexus?
A: Sonatype Nexus offers several security features to enhance the protection of your repositories. These include role-based access control (RBAC), which allows administrators to define roles and assign permissions to specific user accounts. Moreover, Nexus can enforce password policies, such as password complexity requirements and expiration intervals. Additionally, Sonatype Nexus provides support for two-factor authentication (2FA), adding an extra layer of security for user authentication.
In conclusion, the Sonatype Nexus repository manager does not have default credentials. During installation, it is necessary to set up an administrative user with a strong password. Following best practices for password security and regularly updating the administrative user’s password help ensure the security of the system. By taking advantage of additional security measures and features provided by Sonatype Nexus, organizations can enhance the protection of their repositories and mitigate potential security risks.
What Is The Root Password For Sonatype Nexus?
Sonatype Nexus is an open-source repository manager used by developers to efficiently manage software components and their dependencies. It is a widely popular tool in the software development industry, providing a central repository for storing and distributing software artifacts. However, one common question that arises among users is the root password for Sonatype Nexus. Let’s explore this topic in-depth and answer some frequently asked questions related to it.
Sonatype Nexus is designed with security in mind, and by default, the root user account does not have a hard-coded password assigned to it. During the initial setup, the user who installs Nexus becomes the system administrator. This user is granted full administrative privileges and is considered the root user for all practical purposes.
When you install Sonatype Nexus, it creates a default admin user with administrative privileges and provides a web-based user interface to manage the repository. It is crucial to change the default password for the admin user to ensure the security of your Nexus instance.
To change the admin user’s password, follow these steps:
1. Access the Sonatype Nexus web interface by typing the URL in your web browser, typically http://localhost:8081/.
2. Log in using the default administrator credentials (username: admin and password: admin123).
3. Once logged in, click on the “Administration” tab, usually found on the top-right corner of the page.
4. In the administration panel, select “Security” located in the left navigation menu.
5. Under the “Users” section, click on the “admin” user.
6. Now, you can change the password by clicking on the “Change Password” button and following the on-screen instructions.
After successfully changing the admin password, you can securely manage your Sonatype Nexus instance with a password of your choice. It is important to periodically change passwords to enhance security and prevent unauthorized access.
FAQs
Q: Can I reset the password if I forget it?
A: Yes, you can reset the admin password if you forget it. To do so, you need to have access to the email address associated with the admin user. On the Sonatype Nexus login page, click on the “Forgot your password?” link. Enter the email address associated with the admin user and follow the instructions provided in the email received to reset the password.
Q: How do I add additional users to Sonatype Nexus?
A: To add additional users with specific access privileges, follow these steps:
1. Log in to Sonatype Nexus using the admin user credentials.
2. Go to the “Administration” tab and select “Security” from the left navigation menu.
3. Under the “Roles” section, you can create custom roles with specific privileges.
4. After creating the roles, go to the “Users” section and click on “New User.”
5. Fill in the required information, assign the appropriate roles, and set a password for the user.
Q: Is it possible to integrate Sonatype Nexus with an external user database or authentication system?
A: Yes, Sonatype Nexus supports integration with external user databases and authentication systems such as LDAP (Lightweight Directory Access Protocol) or Active Directory. This allows you to centralize user management and authentication processes.
Q: How can I enhance security further in Sonatype Nexus?
A: Apart from changing default passwords and using strong, unique passwords, here are some additional steps to enhance security:
1. Enable SSL/TLS encryption for secure communication between Sonatype Nexus and client applications.
2. Regularly update Sonatype Nexus to the latest version to benefit from the latest security patches and improvements.
3. Regularly monitor and audit access logs to identify any suspicious activities.
4. Implement strong firewall rules to restrict access to the Nexus server to trusted networks or IP addresses.
5. Create and enforce security policies, such as password complexity requirements or multi-factor authentication, if supported by your Sonatype Nexus version.
In conclusion, while there is no root password for Sonatype Nexus, it is crucial to change the default admin user’s password to secure your repository manager. Sonatype Nexus offers a user-friendly web interface to manage users, roles, and security configurations. By following best practices in password management and enhancing security measures, you can effectively safeguard your software artifacts and ensure a robust repository management solution.
Keywords searched by users: unable to authenticate need basic realm sonatype nexus repository manager Unable to authenticate, need: Basic realm https pkgsprodcus1 pkgs visualstudio com, Npm ERR code E401, Npm Nexus repository, Nexus repository doc, Incorrect or missing password, Config auth _authToken username and password must be scoped to a registry, Is not in the npm registry, Web login not supported
Categories: Top 67 Unable To Authenticate Need Basic Realm Sonatype Nexus Repository Manager
See more here: nhanvietluanvan.com
Unable To Authenticate, Need: Basic Realm Https Pkgsprodcus1 Pkgs Visualstudio Com
In the digital era, online authentication is an essential component of accessing various services, including software packages and development tools. However, there are times when users encounter difficulties in authenticating themselves, resulting in frustration and delays in their workflow. One common issue that users face is the “Unable to authenticate” error message when trying to access the Basic realm https://pkgsprodcus1.pkgs.visualstudio.com. In this article, we will delve into the reasons behind this error and provide helpful solutions to address the problem.
Understanding the Basic Realm
To comprehend the root of the issue, it is crucial to understand what the Basic realm is. In the context of web services, the Basic realm is a form of authentication that provides a simple and straightforward means of verifying users’ identities. This method requires users to provide a username and password combination to access the desired service or resource.
Causes of the “Unable to Authenticate” Error
There can be several reasons behind the “Unable to authenticate” error message when attempting to access the Basic realm of https://pkgsprodcus1.pkgs.visualstudio.com. Let’s explore some of the common causes:
1. Incorrect Username or Password: The most common cause of this error is an incorrect username or password. Ensure that you are entering the valid credentials associated with your account. Double-check for any typos or case sensitivity issues that might be causing authentication failure.
2. Expired Password: If you haven’t changed your password in a while, it could have expired. In such cases, you need to reset your password following the Forgot Password or Reset Password option provided by the service.
3. Network Issues: Sometimes, network connectivity problems can disrupt the authentication process. Ensure that you have a stable internet connection, and there are no firewall or proxy settings hindering your access.
4. Server Issues: Occasionally, the issue might lie on the server-side. The authentication server could be experiencing maintenance or technical difficulties temporarily. In such cases, you can try accessing the service again after some time.
Troubleshooting the Issue
Now that we have explored the potential causes of the “Unable to authenticate” error, let’s dive into the solutions to resolve this issue:
1. Verify Credentials: Begin by double-checking your username and password combination. Pay attention to letter case and ensure there are no typos. If needed, use the password reset option to create a new password.
2. Clear Browser Cache: Temporarily stored login credentials or cached data in your browser might be interfering with the authentication process. Clear your browser cache and try signing in again.
3. Disable VPN or Proxy: Virtual Private Network (VPN) or proxy settings can sometimes hinder authentication due to conflicting network configurations. Temporarily disable your VPN or proxy before attempting to log in.
4. Check Network Connectivity: Verify that you have a stable internet connection by checking other websites or services. If necessary, restart your router or contact your internet service provider for assistance.
5. Contact Support: If none of the above solutions work, reach out to the support team of the service you are trying to access. They will be able to provide specific guidance and troubleshoot the issue further.
Frequently Asked Questions (FAQs):
Q1. Can I use my Microsoft account to authenticate on Basic Realm https://pkgsprodcus1.pkgs.visualstudio.com?
A1. No, Basic Realm authentication typically requires a separate set of credentials specific to the service you are accessing. Your Microsoft account credentials may not work unless they are explicitly linked with the Basic Realm service.
Q2. I am sure that my credentials are correct, but I still cannot authenticate. What should I do?
A2. In such cases, consider following the troubleshooting steps mentioned in this article. If the problem persists, reach out to the support team of the service you are trying to access for further assistance.
Q3. Does the “Unable to authenticate” error indicate a security breach?
A3. Not necessarily. This error message indicates a failure in authentication rather than a security breach. However, it is always recommended to follow best security practices, such as keeping your passwords safe and using unique combinations for different services.
Q4. How can I prevent the “Unable to authenticate” error in the future?
A4. To avoid this error, ensure that you maintain a record of your correct credentials. Regularly update your password and periodically check for notifications or updates from the service provider. Additionally, stay updated on any maintenance schedules or server downtime to plan your work accordingly.
In conclusion, encountering the “Unable to authenticate” error can be frustrating, especially when you are trying to access important resources within the Basic realm https://pkgsprodcus1.pkgs.visualstudio.com. By understanding the causes and following the troubleshooting steps mentioned above, you can effectively resolve the issue and continue your work smoothly.
Npm Err Code E401
When using npm, the package manager for the Node.js runtime, encountering an E401 error typically means that you are trying to access a package from a private registry without proper authentication. However, it’s important to note that this error can also occur when trying to download packages from public registries due to various factors. Let’s delve into the causes of this error and the steps you can take to resolve it.
Causes of the Npm ERR code E401:
1. Invalid or Missing Authentication Tokens:
One primary cause of this error is invalid or missing authentication tokens. These tokens are used to authenticate your access to private package registries. If you do not have the correct tokens or have not set them up correctly, npm will return the E401 error. Double-checking your authentication tokens and ensuring they are correct is the initial step towards resolving this issue.
2. Incorrect or Incomplete Registry Configuration:
Another cause of the E401 error can be the incorrect or incomplete configuration of the package registry in your npm configuration file. It’s essential to verify that you have correctly set up the registry you intend to access.
3. Residual Caching Issues:
Sometimes, a cached authentication token can cause conflicts resulting in the E401 error. Clearing the cache can potentially resolve this issue.
4. Network Connectivity or Firewall Restrictions:
Network connectivity issues or firewall restrictions can also be factors that contribute to the E401 error. Ensure that you have a stable internet connection and that your firewall settings are not blocking the required access.
Solutions to the Npm ERR code E401:
1. Verify Authentication Tokens:
To resolve the E401 error, first, ensure that your authentication tokens are correct and up to date. If you are accessing a private package registry, make sure you have obtained the correct tokens from the registry provider and have set them up correctly in your npm configuration.
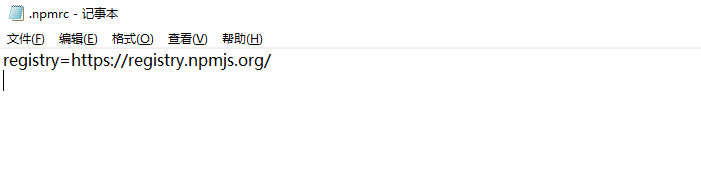
2. Review the npm Configuration:
Double-check your npm configuration file (typically `.npmrc` or `.yarnrc`) to ensure the registry configuration is accurate. If you are using multiple registries, verify that the correct registry is being used for the package causing the E401 error.
3. Clear the npm Cache:
If you suspect caching issues, it may be helpful to clear the npm cache. You can use the `npm cache clean –force` command to remove any potentially problematic cached data. Once cleared, try installing the package again.
4. Check Network Connectivity and Firewall Restrictions:
Ensure that your network connection is stable and that there are no issues with accessing the required package registry. Additionally, check your firewall settings to confirm that they are not blocking npm’s access to the registry.
Frequently Asked Questions:
Q1: I am receiving an E401 error on a public registry. How can I resolve this issue?
A1: Although E401 errors are commonly associated with private registry access, they can also occur when downloading packages from public registries. To troubleshoot this, try running `npm config set registry https://registry.npmjs.org/` to reset the registry to the default public one.
Q2: Can I manually authenticate with a private registry to resolve the E401 error?
A2: Yes, you can manually authenticate with a private registry by running `npm login` and providing the required authentication details. This will ensure that you have the necessary tokens for accessing the registry.
Q3: How can I avoid E401 errors when using multiple package registries?
A3: If you are using multiple package registries, ensure that you have set up the authentication tokens and registry configurations correctly for each specific registry. Review your npm configuration file to confirm no conflicts or misconfigurations exist.
Q4: What should I do if I still encounter the E401 error after trying the suggested solutions?
A4: If the issue persists, it’s recommended to reach out to the package registry provider’s support team for further assistance. They can help troubleshoot any specific issues or provide guidance tailored to their registry.
In conclusion, the Npm ERR code E401 can be resolved by carefully verifying authentication tokens and registry configurations, clearing the npm cache, ensuring network connectivity, or reviewing firewall restrictions. By following the solutions provided and addressing any specific concerns, developers can overcome this error and continue working with npm smoothly.
Npm Nexus Repository
Introduction to Npm Nexus Repository
As software development and release cycles have become more intricate, managing dependencies has become increasingly important. This is where a repository manager comes in handy. The Npm Nexus Repository is a popular choice for managing packages and dependencies in an efficient and organized manner.
In this comprehensive article, we will delve into the intricacies of the Npm Nexus Repository. We will explore its features, benefits, and the process of setting it up. Furthermore, we will address common questions and concerns through a detailed FAQ section.
Understanding Npm Nexus Repository
The Npm Nexus Repository is a robust and extensible repository manager designed to facilitate the management of software components, artefacts, and their dependencies. It acts as a central hub for teams to store, organize, and distribute Npm packages securely. By caching remote repositories, the Npm Nexus Repository provides faster access to packages and mitigates external dependencies.
Key Features and Benefits
1. Proxying: The Npm Nexus Repository allows developers to securely proxy remote repositories like the official Npm registry. This ensures faster downloads and reduces external dependency risks by providing a local mirror.
2. Caching: By caching downloaded packages, the Npm Nexus Repository minimizes download times for recurring dependencies. This boosts build efficiency and reduces network usage.
3. Hosting: Developers can publish and host their Npm packages internally. This ensures control over the release cycle and provides a centralized and reliable source for other teams and projects.
4. Access control: With the Npm Nexus Repository, organizations can implement access control policies, ensuring that only authorized personnel can manage, access, and publish packages. This greatly enhances security and compliance.
5. Build integration: Seamless integration with build tools, such as Jenkins or GitLab CI/CD, enables developers to automate deploying, testing, and building packages, reducing manual effort and enhancing DevOps practices.
Setting Up Npm Nexus Repository
1. Installation: To begin using the Npm Nexus Repository, download the appropriate package for your operating system from the official website. Follow the installation instructions provided to complete the setup.
2. Configuration: After installation, configure the repository manager by accessing the web-based admin interface. Customize settings such as security, remote repositories, caching, and proxying according to your organization’s requirements.
3. Proxy configuration: To proxy the official Npm registry, add the remote repository URL in the Npm Nexus Repository’s configuration. This will ensure that packages are fetched from the local cache for improved performance.
4. Access control: Implementing user management and access control policies within the Npm Nexus Repository ensures that packages are restricted to authorized personnel. This prevents unauthorized access and enhances security.
5. Publish and distribute packages: Use the Npm Nexus Repository to host and distribute your internally developed packages. This allows for control over the release cycle, enabling teams to iterate, test, and deploy more efficiently.
FAQs
Q1. Can the Npm Nexus Repository be used with other package managers?
Yes, the Npm Nexus Repository is not limited to Npm packages; it can also be used with other popular package managers such as Maven, Docker, and Gradle.
Q2. Is the Npm Nexus Repository compatible with different operating systems?
Absolutely! The Npm Nexus Repository is compatible with various operating systems including Windows, macOS, and Linux. This makes it accessible and functional across different environments.
Q3. How does the Npm Nexus Repository handle security vulnerabilities?
The Npm Nexus Repository provides security scanning capabilities to detect vulnerabilities within hosted packages. It also integrates with security tools like Sonatype OSS Index to proactively identify and address vulnerabilities.
Q4. Can the Npm Nexus Repository be integrated with CI/CD pipelines?
Yes, the Npm Nexus Repository seamlessly integrates with popular CI/CD tools like Jenkins, GitLab CI/CD, and TeamCity. This allows for automated package deployment, testing, and building, ensuring efficient and streamlined workflows.
Q5. Is the Npm Nexus Repository suitable for both small and large organizations?
Absolutely! The Npm Nexus Repository caters to the needs of both small and large organizations. Its scalability, access control features, and build integration capabilities make it suitable for teams of any size.
Conclusion
The Npm Nexus Repository is a powerful tool for managing Npm packages and their dependencies. By providing caching, proxying, and access control features, it enhances efficiency, security, and control over the software release cycle. With its seamless integration capabilities and cross-platform compatibility, the Npm Nexus Repository is an excellent choice for organizations of all sizes.
Images related to the topic unable to authenticate need basic realm sonatype nexus repository manager

Found 13 images related to unable to authenticate need basic realm sonatype nexus repository manager theme








Article link: unable to authenticate need basic realm sonatype nexus repository manager.
Learn more about the topic unable to authenticate need basic realm sonatype nexus repository manager.
- npm error E401: Unable to authenticate, need: BASIC realm …
- Unable to authenticate agains Nexus hosted NPM Repository
- Users – Sonatype Help
- Post-Install Checklist – Sonatype Help
- User Management – Sonatype Help
- Creating a new user account on the public registry – npm Docs
- Solidjs deploy from git – npm ERR! Unable to authenticate …
- Unable to authenticate, need: Basic realm=”Artifactory Realm”
- Authenticate bitbucket with Nexus Sonar Type.
- Getting “npm ERR! Unable to authenticate, need: Basic realm …
See more: nhanvietluanvan.com/luat-hoc