The Authenticity Of Host Cant Be Established
The Difficulty in Verifying the Identity of a Host:
One of the main challenges in establishing the authenticity of a host is the lack of a standardized system for verifying their identity. Unlike hotels, where guests can rely on established brands and professional management, the sharing economy relies on individuals to provide accommodations. As a result, it becomes crucial to ensure the legitimacy of these hosts.
Various platforms have implemented measures like ID verification, background checks, and social media profiles to mitigate these risks. However, these procedures are not foolproof and rely heavily on self-reporting and user-submitted information.
The Risks of Booking with an Unverified Host:
Booking with an unverified host can expose guests to several risks. First and foremost, there is a risk of falling victim to scams and fraudulent listings. Fake listings can be created to mislead guests, resulting in disappointing or even dangerous accommodation experiences. It is not uncommon to hear stories of travelers arriving at their destination only to find that the listed property doesn’t exist or is significantly different from its description.
Another risk is the potential breach of privacy and security. By staying in someone’s home, guests are essentially placing their trust in the host. However, without a proper verification process, it becomes challenging to determine if the host can be trusted. There have been instances where hidden cameras or other invasive surveillance devices were discovered in accommodations, placing guests at risk.
Consumer Protection Measures in the Sharing Economy:
Recognizing the risks associated with booking accommodations with unverified hosts, many sharing economy platforms have implemented consumer protection measures. For example, Airbnb offers a Host Guarantee program that provides compensation for damages to the property caused by guests, although it does not cover personal injuries or stolen items.
Additionally, most reputable platforms have a dispute resolution process where guests can report issues and seek resolution. However, these measures do not fully eliminate the risks; they merely provide some level of recourse if something goes wrong.
The Role of Reviews and Ratings in Determining Authenticity:
One of the most significant factors in determining the authenticity and trustworthiness of a host is the reviews and ratings left by previous guests. Platforms like Airbnb, Couchsurfing, and HomeAway heavily rely on guest feedback to establish trust within their communities.
Reviews and ratings allow guests to evaluate the quality of the host’s hospitality, accuracy of the listing description, and overall guest experience. Positive reviews can be an indication of a genuine host, while negative reviews may raise red flags.
However, it is worth noting that reviews can also be manipulated or fake. Some hosts may incentivize guests to leave positive reviews, while others may resort to fraudulent practices. Platforms continuously monitor and moderate reviews to detect and remove suspicious or dishonest feedback.
Different Approaches to Authenticating Hosts:
Sharing economy platforms employ various strategies to authenticate hosts. Some platforms rely on a combination of ID verification, background checks, and social media integration. Others may require hosts to provide additional documentation, such as proof of address or utility bills, to establish their authenticity.
It is essential for platforms to strike a balance between ensuring host authenticity and maintaining user privacy. While robust verification processes can help build trust, they should not infringe on hosts’ rights or deter potential participants from engaging in the sharing economy.
The Importance of Trust and Safety in the Sharing Economy:
Trust is the foundation of the sharing economy. Without trust between hosts and guests, the entire system would collapse. Guests must feel confident that the hosts they choose are genuine, and hosts need to trust that their guests will be respectful and responsible.
Safety is another critical aspect that cannot be overlooked. Accommodation-sharing platforms must prioritize the safety of their users by implementing security protocols and educating hosts and guests on best practices. It is crucial that platforms stay responsive to user concerns and adapt their safety measures accordingly.
Steps Taken by Platforms to Verify Hosts:
To address the challenges associated with host authenticity, sharing economy platforms are continuously refining their verification processes. For example, Airbnb introduced a Verified ID system, requiring hosts to provide government-issued identification. Additionally, hosts can link their social media profiles to establish further credibility.
Platforms may also collaborate with third-party verification services to strengthen their processes. These services use advanced algorithms and data analysis to identify inconsistencies, screen for fraudulent activity, and detect if a host’s identity has been compromised.
Ultimately, while platforms strive to provide more robust host verification systems, it is crucial for guests to remain vigilant and use their best judgment when booking accommodations. Pay attention to reviews, engage in open communication with hosts, and report any suspicious activity or concerns to the platform.
FAQs:
Q: Why is it challenging to establish the authenticity of a host?
A: Unlike hotels, individual hosts in the sharing economy don’t have established brands or professional management. This lack of a standardized system for verifying identities poses difficulties in ensuring the authenticity of hosts.
Q: What risks are associated with booking with an unverified host?
A: Booking with an unverified host can result in falling victim to scams, encountering fraudulent listings, breach of privacy and security, and other potentially unsafe situations.
Q: Do sharing economy platforms have consumer protection measures in place?
A: Yes, most reputable platforms have implemented consumer protection measures such as compensation for damages caused by guests and dispute resolution processes.
Q: How can reviews and ratings help determine the authenticity of a host?
A: Reviews and ratings left by previous guests play a significant role in establishing trust in the sharing economy. Positive reviews can indicate a genuine host, while negative reviews may raise concerns.
Q: What steps are sharing economy platforms taking to verify hosts?
A: Platforms employ various strategies such as ID verification, background checks, social media integration, and collaborating with third-party verification services.
In conclusion, the authenticity of a host in the sharing economy remains a complex issue. While platforms and hosts strive to establish trust and safety measures, there are inherent challenges in verifying identities. Guests must be vigilant and rely on reviews, ratings, and their own judgment when booking accommodations to mitigate risks.
The Authenticity Of Host Can’T Be Established. Key Fingerprint Key Is Not Known By Any Other Name
How Does Known_Hosts Work?
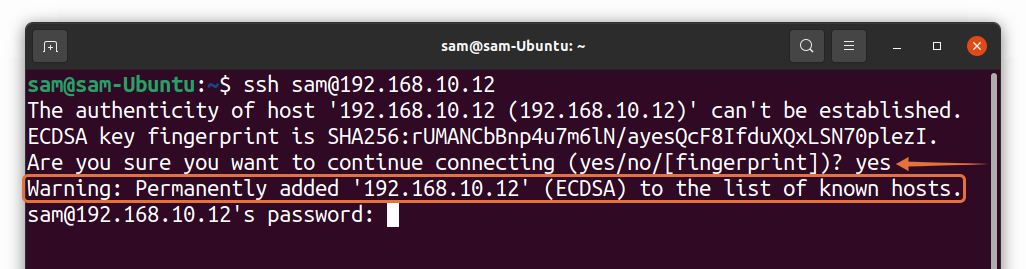
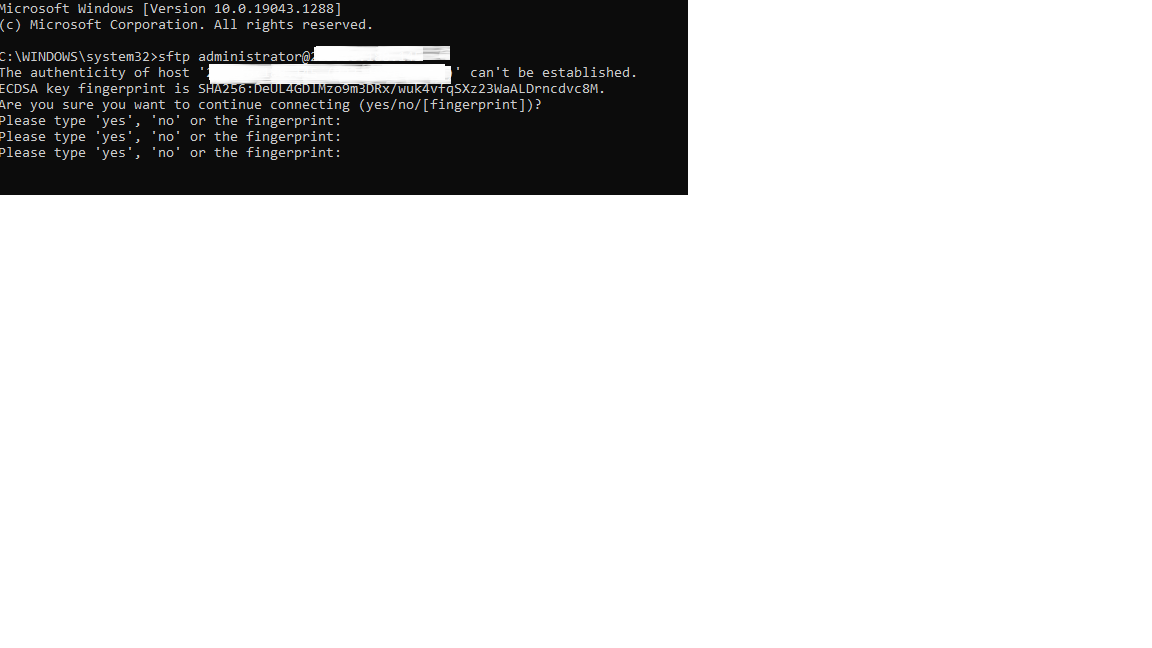
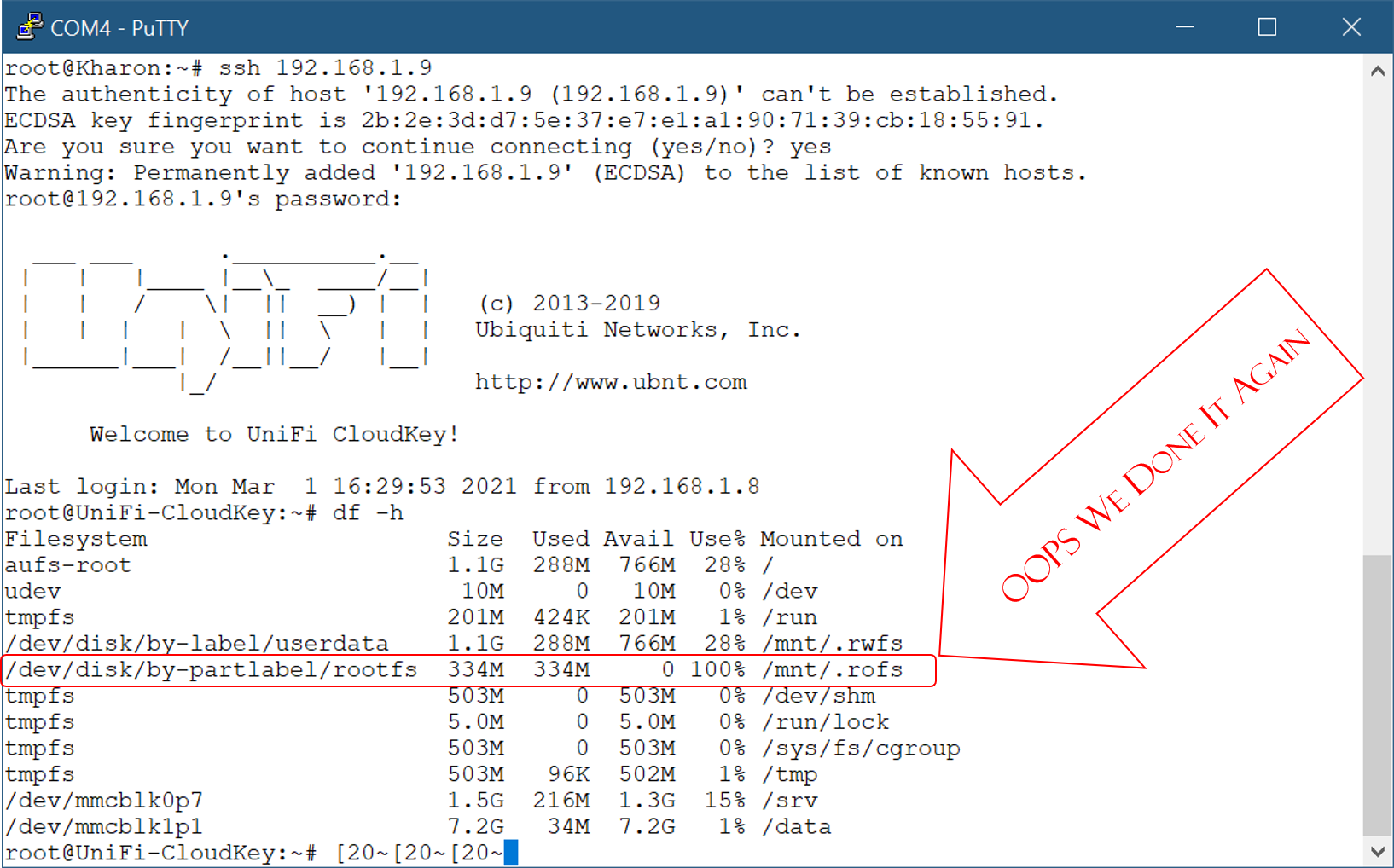
When connecting to a remote server using SSH (Secure Shell), you may have encountered the message: “The authenticity of host ‘xxx.xxx.xxx.xxx’ can’t be established… Are you sure you want to continue connecting?”. This message is related to the known_hosts file, a vital component of the SSH authentication process. In this article, we will explore how known_hosts works and its importance in securing SSH connections.
What is known_hosts?
The known_hosts file is a text file that stores the public keys of known remote hosts. It resides on the client-side that initiates an SSH connection. The file’s purpose is to verify the authenticity of a remote server during the connection process. When attempting to connect to a new remote server, SSH compares the server’s public key with the ones stored in the known_hosts file. If there is a match, the connection is established. If there is no match or there is a change in the public key, SSH raises a warning.
How is the known_hosts file created?
The known_hosts file is automatically created the first time you connect to a remote server. When you connect to a server for the first time, SSH displays the fingerprint of the server’s public key and asks for confirmation. If you decide to proceed with the connection, SSH adds the server’s public key to the known_hosts file. From that point forward, SSH will compare any future connection attempts against this file.
Why is the known_hosts file important?
The known_hosts file plays a crucial role in ensuring secure SSH connections. It helps to prevent man-in-the-middle (MITM) attacks, where a malicious third party intercepts and alters the communication between two parties. By verifying the authenticity of a remote server, the known_hosts file ensures that the client is connecting to the intended server and not to an impostor. This authentication mechanism forms a cornerstone of SSH’s security architecture.
What happens if the public key has changed?
If the public key of a remote server has changed, SSH raises a warning during the connection attempt. This can occur for legitimate reasons, such as a server being reinstalled or a network administrator replacing the server’s SSH keys. However, it can also indicate a potential security threat such as a MITM attack.
When the public key has changed, SSH notifies the user, typically displaying a warning message that includes the fingerprint of the new key. The user must then make an informed decision about whether to trust the new key or abort the connection. If the user decides to proceed, the known_hosts file is updated with the new public key.
How does SSH know which known_hosts file to use?
SSH first checks the user’s home directory for a known_hosts file. By default, this file is located at ~/.ssh/known_hosts. If no known_hosts file is found in the user’s home directory, SSH searches for a system-wide known_hosts file located in the /etc/ssh/ directory. In some cases, the known_hosts file may be stored in a different location depending on the configuration.
FAQs
Q: Can I remove entries from the known_hosts file?
A: Yes, you can remove entries from the known_hosts file. This can become necessary if a server has changed its public key or if you no longer need to establish connections to a particular server. However, exercise caution when modifying the known_hosts file to avoid inadvertently removing valid entries.
Q: Can the known_hosts file be manually edited?
A: Yes, the known_hosts file can be manually edited. You can open the file with a text editor and delete or modify entries as needed. However, remember that incorrect modifications can lead to connection issues or security vulnerabilities, so it is essential to be careful when making changes.
Q: Can the known_hosts file be shared between different users on the same system?
A: No, the known_hosts file cannot be shared between different users. Each user has their own known_hosts file in their respective home directory, and SSH checks the file specific to the user initiating the connection.
Q: Can the known_hosts file be copied between different systems?
A: Yes, the known_hosts file can be copied between different systems. This can be useful when transferring your known hosts list to a new machine or when setting up connections on multiple systems. However, note that copying the known_hosts file will transfer all trusted keys, so it is crucial to ensure the security of the copied file.
In conclusion, the known_hosts file is an essential component of the SSH authentication process. It helps to establish secure connections by verifying the authenticity of remote servers. By storing known public keys and comparing them during connection attempts, the known_hosts file acts as a defense against potential security threats. Understanding how known_hosts works is vital in safeguarding the integrity and security of your SSH connections.
Where Is The Known_Hosts File?
The known_hosts file is an essential part of secure communication protocols used in Linux and Unix-based systems. It is a simple text file that keeps a record of the public keys of remote servers that a user has previously connected to via SSH (Secure Shell) or similar protocols. This article aims to shed light on the location and significance of the known_hosts file, as well as address some frequently asked questions surrounding its usage.
Location of the known_hosts file:
By default, the known_hosts file is located in the user’s home directory. More specifically, it resides in the .ssh subdirectory, which is hidden by default as its name begins with a dot. The precise location can be represented as ~/.ssh/known_hosts, where the tilde (~) denotes the user’s home directory.
It is important to note that each user on a system has their own known_hosts file. Therefore, if multiple users exist, the file for each user will be located in their respective home directories.
Significance and purpose:
The known_hosts file plays a vital role in securing SSH connections. When a user connects to a remote server for the first time, the server’s public key is stored in this file. Upon subsequent connections, SSH clients will compare the server’s public key presented during the connection process with the stored key in the known_hosts file. If the keys match, the client proceeds with the connection; otherwise, a warning is issued, suggesting a possible security breach or server impersonation.
This mechanism ensures that users are connecting to the correct server and mitigates the risk of man-in-the-middle attacks. It provides a level of assurance about the authenticity and integrity of the remote server before establishing a secure connection.
FAQs:
1. Can the known_hosts file be modified manually?
Yes, the known_hosts file can be modified manually. However, this action is generally discouraged unless you fully understand the implications. Removing a line from the file will cause the client to prompt again for the server’s key the next time a connection is attempted. Adding or modifying lines should be done with caution as it can potentially compromise the security of the connection.
2. What if the known_hosts file becomes too large?
Over time, the known_hosts file may accumulate a significant number of entries, especially for users who frequently connect to multiple servers. If the file becomes too large, it can slow down SSH connections and create unnecessary overhead. In such cases, it is advisable to consider removing or archiving older entries that are no longer required.
3. Can the known_hosts file be shared among multiple users?
While it is technically possible for multiple users to share the same known_hosts file, it is not recommended for security reasons. Each user should maintain their own individual known_hosts file to ensure that the authenticity of remote servers is independently verified for each user.
4. Can the known_hosts file be used to track server changes or detect compromise?
Since the known_hosts file only contains the public keys of remote servers, it is primarily designed to ensure the integrity of the server-to-client connection. It does not serve as a comprehensive tracking or monitoring tool. Monitoring server changes or detecting compromises requires additional security measures and tools.
5. How can I quickly find the known_hosts file?
If you are unsure about the exact location of your known_hosts file, you can use the command `ssh-keygen -F
In conclusion, the known_hosts file serves as a crucial element in maintaining secure SSH connections. Its location in the user’s home directory and its role of storing and verifying server public keys underscore its significance in establishing trusted connections. Navigating the known_hosts file carefully and understanding its purpose is key to enhancing the security of remote server communications.
Keywords searched by users: the authenticity of host cant be established The authenticity of host GitHub com 20.205 243.166 can T be established, The authenticity of host can t be established MySQL Workbench, The authenticity of host ec2 can t be established, permission denied (publickey), The authenticity of host gitlab com 172.65 251.78 can t be established, The authenticity of host Bitbucket org 104.192 141.1 can T be established, This key is not known by any other names, host key verification failed.
Categories: Top 61 The Authenticity Of Host Cant Be Established
See more here: nhanvietluanvan.com
The Authenticity Of Host Github Com 20.205 243.166 Can T Be Established
In today’s digital age, online security and the ability to trust the authenticity of websites and hosts have become paramount concerns. One such concern revolves around the authenticity of host GitHub.com with its IP address being 20.205.243.166. Establishing the authenticity of a host is crucial to ensuring the security of the data and information exchanged with it. In this article, we will delve into the topic of the authenticity of the host GitHub.com and analyze why it cannot be established. We will also address frequently asked questions surrounding this issue.
Before diving into the specifics, it is important to understand the concept of authenticity in the context of online hosts. Authenticity relates to the assurance that the entity being communicated with is indeed the entity it claims to be. This assurance is typically provided through digital certificates and secure communication protocols, such as Transport Layer Security (TLS).
GitHub.com is a widely popular web-based hosting service primarily used for version control of software projects. With millions of users and numerous high-profile open-source projects, it becomes crucial to ensure the authenticity and integrity of the GitHub.com domain.
However, when we examine the IP address associated with GitHub.com, which is 20.205.243.166, we encounter a problem. Establishing the authenticity of this IP address is not feasible because it does not belong to GitHub.com itself. As IP addresses can be easily changed and reassigned, relying solely on the IP address is not a secure way to authenticate a host.
To establish the authenticity of a website or host, one must rely on other mechanisms, such as digital certificates and secure communication protocols like TLS. GitHub.com uses TLS to secure the communication between users and their servers. TLS, formerly known as SSL, provides encryption and authentication, ensuring that the data exchanged between users and GitHub.com remains confidential and trustworthy.
When accessing GitHub.com, a user’s browser checks the digital certificate presented by the server, which is issued by a trusted Certificate Authority (CA). The certificate contains information about the domain name for which it was issued, such as github.com, and is signed by the CA to establish its authenticity. This validation process ensures that users are indeed connecting to the genuine GitHub.com.
However, it is important to note that the digital certificate does not authenticate the IP address associated with the host. It solely verifies the authenticity of the domain name, which in this case is github.com. Therefore, the IP address 20.205.243.166 itself cannot be considered conclusive evidence of authenticity.
To provide additional assurance, users should also ensure that they are connecting to GitHub.com over a secure connection. This can be verified by checking for the presence of “https://” in the URL and a padlock icon in the browser’s address bar. This indicates that the communication between the user’s browser and GitHub.com is encrypted and securely established.
It is also worth mentioning that trusting the authenticity of GitHub.com is not limited to IP addresses and digital certificates alone. Users should exercise caution regarding phishing attacks, where malicious actors may attempt to mimic the appearance of GitHub.com to deceive unsuspecting users. Common practices to mitigate phishing risks include verifying the website URL, avoiding clicking on suspicious links, and enabling two-factor authentication (2FA).
While the authenticity of the host IP address 20.205.243.166 cannot be established, relying on the established authentication mechanisms, such as digital certificates and secure communication protocols, is crucial for ensuring the trustworthiness of GitHub.com.
FAQs:
Q1: Is it safe to access GitHub.com using the IP address 20.205.243.166?
A1: It is not recommended to access GitHub.com using solely its IP address. To ensure the authenticity and security of your connection, it is advised to use the domain name (github.com) instead.
Q2: Can I trust the digital certificate presented by GitHub.com?
A2: Yes, the digital certificate issued by a trusted Certificate Authority (CA) ensures the authenticity of GitHub.com. However, it does not authenticate the IP address associated with the host.
Q3: How can I verify if my connection to GitHub.com is secure?
A3: Ensure that the URL begins with “https://” and look for the padlock icon in your browser’s address bar. These indicate that your connection is encrypted and established securely.
Q4: What precautions should I take to protect myself from phishing attacks on GitHub.com?
A4: Verify the website URL, avoid clicking on suspicious links, and consider enabling two-factor authentication (2FA) to mitigate the risk of phishing attacks.
The Authenticity Of Host Can T Be Established Mysql Workbench
MySQL Workbench is a powerful tool used by database administrators and developers to manage and manipulate MySQL databases. It provides a graphical user interface (GUI) that simplifies the process of creating, editing, and managing databases. However, when connecting to a remote MySQL server using MySQL Workbench, users may sometimes encounter a warning message stating, “The authenticity of host cannot be established.”
This warning message is primarily displayed to ensure the security of the connection. It indicates that MySQL Workbench is unable to verify the identity of the remote server it is attempting to connect to. When this message appears, users are presented with two options: to either continue with the connection or to cancel it.
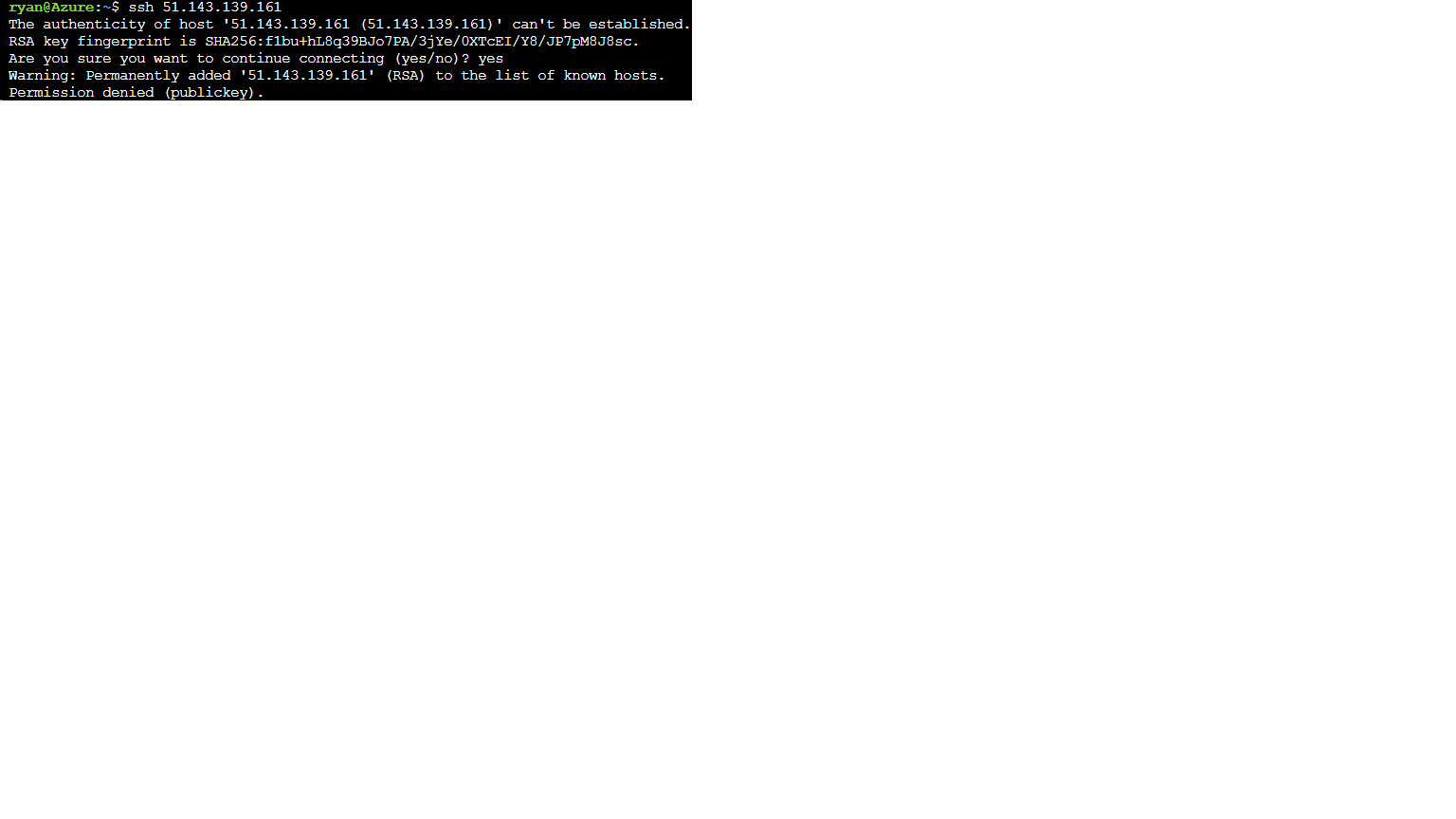
While the warning message may initially seem alarming, it is essential to understand its significance. This authentication process is known as the host key verification, which is a security feature employed by SSH (Secure Shell) protocols. SSH is responsible for securely connecting to remote servers and authenticating their identities.
When a user connects to a remote MySQL server, the server’s SSH host key is used to verify its authenticity. The host key is a cryptographic key that uniquely identifies the server and ensures the integrity of the connection. If the host key presented by the server matches the stored key on the client-side, the connection proceeds, and data can be safely transmitted. However, if the keys do not match, it could indicate potential security risks, such as a man-in-the-middle attack, where an unauthorized entity intercepts the communication.
In some cases, the warning message may appear due to a legitimate reason, such as when connecting to a server for the first time or if the server’s key has been changed or reinstalled. However, it is crucial to exercise caution and consider the potential risks before proceeding.
To address the warning message and establish the authenticity of the host, there are a few steps that can be taken:
1. Verify the server’s identity manually: Before making a decision, users can verify the fingerprint and key information manually. The fingerprint represents a unique identifier generated based on the server’s host key. By contacting the server administrator or referring to the server documentation, users can cross-reference the displayed fingerprint to ensure its authenticity. If the fingerprint matches, it can provide reassurance about the server’s identity.
2. Consult with the server administrator: If uncertain about the warning message, users can contact the server administrator to verify its authenticity. The administrator will be able to assist in confirming whether any changes have been made to the server or if the warning can be disregarded.
FAQs:
Q: What should I do if I encounter the “The authenticity of host cannot be established” warning?
A: Firstly, it is essential not to panic. Understand that this warning message exists to ensure the security of your connection. To proceed, you have two options: either manually verify the server’s identity or consult with the server administrator for confirmation.
Q: How can I verify the server’s identity manually?
A: By contacting the server administrator or referring to the server documentation, you can cross-reference the fingerprint displayed in the warning message with the server’s actual fingerprint. If they match, it indicates that the server is authentic and can be trusted.
Q: Can I always proceed with the connection if the fingerprints match?
A: While matching fingerprints provide reassurance about the server’s authenticity, it is still essential to exercise caution. If you are connecting to the server for the first time or if you suspect any potential security risks, it may be advisable to consult with the server administrator before proceeding.
Q: What if the fingerprints do not match?
A: If the fingerprints do not match, it could indicate that the server’s host key has been changed, reinstalled, or tampered with. In such cases, it is strongly recommended to abort the connection and contact the server administrator to ensure the security of your connection.
Q: Are there any other security measures I should be aware of when using MySQL Workbench?
A: Alongside host key verification, it is crucial to employ other security measures when using MySQL Workbench, such as strong passwords, encrypted connections, and restricted access privileges. Regularly updating MySQL Workbench to the latest version is also recommended to ensure any security vulnerabilities are patched.
In conclusion, the “The authenticity of host cannot be established” warning in MySQL Workbench is a crucial security measure to ensure the integrity of your connection to remote servers. While it may cause initial concern, taking the necessary steps to verify the server’s identity and consult with the server administrator can help establish the authenticity of the host. By following these precautions, users can confidently manage and manipulate their MySQL databases while prioritizing security.
Images related to the topic the authenticity of host cant be established

Found 14 images related to the authenticity of host cant be established theme













![I've done something daft (TM) [and hosed my network connection] - General - Rocky Linux Forum I'Ve Done Something Daft (Tm) [And Hosed My Network Connection] - General - Rocky Linux Forum](https://global.discourse-cdn.com/business7/uploads/rockylinux/original/2X/3/396a9593380736c29f025bcb4efb176ccd2ebd80.jpeg)











Article link: the authenticity of host cant be established.
Learn more about the topic the authenticity of host cant be established.
- How To Fix the Authenticity of Host Can’t Be Established (8 …
- ssh: The authenticity of host ‘hostname’ can’t be established
- SSH: The authenticity of host
can’t be established - Known Hosts File – Glossary | CSRC
- Updating host keys – DreamHost Knowledge Base
- Description – IBM
- Verifying the Authenticity of Remote Host (SSH Key …
- The authenticity of host ‘bitbucket.org (104.192.143.1)’ can’t …
- Authenticity of host can’t be established · SFTP Gateway Support
- The authenticity of host can’t be established but that …
- FIX: The authenticity of host github.com can’t be established.
- How to resolve the authenticity of host ‘hostname’ that can’t …
See more: nhanvietluanvan.com/luat-hoc