Terraform Lifecycle Ignore_Changes All
Definition of Terraform Lifecycle
Terraform is an open-source infrastructure as code (IaC) tool that enables users to define and provision infrastructure resources through declarative configuration files. It automates the creation, modification, and management of cloud resources across various providers, ensuring consistent and reproducible infrastructure deployments.
The lifecycle of Terraform refers to the different stages that an infrastructure resource goes through, including initialization, planning, applying changes, and destroying resources. Each stage has a specific set of tasks and operations associated with it, allowing users to manage and maintain their infrastructure efficiently.
Introduction to the concept of “ignore_changes all”
Terraform provides a “lifecycle” block that allows users to define certain behaviors for their resources during different stages of the infrastructure lifecycle. One important attribute within this block is “ignore_changes,” which allows users to specify the resource attributes or properties that Terraform should ignore when determining whether to update or recreate a resource.
The “ignore_changes” attribute is useful in situations where specific attributes of a resource should not trigger resource recreation or updates. By using the “ignore_changes” attribute, users can instruct Terraform to disregard specified attribute changes and prevent unnecessary modifications to existing resources.
Importance and benefits of utilizing this feature
The “ignore_changes” attribute provides several benefits for managing infrastructure resources effectively:
1. Preventing unnecessary resource modifications: By specifying certain changes to be ignored, users can avoid unnecessary resource recreation or updates, saving time and resources.
2. Enhancing control over infrastructure changes: The ability to define which attribute changes Terraform should ignore gives users greater control over the evolution of their infrastructure resources.
3. Ensuring stability: By ignoring certain changes, users can maintain a stable infrastructure by preventing inadvertent modifications that could cause downtime or other disruptions.
4. Improving deployment speed: Ignoring changes that do not affect the desired state of a resource allows for faster deployments and reduces the time required for Terraform operations.
Understanding “ignore_changes all”
The “ignore_changes” attribute in Terraform allows users to specify individual attributes or provide the value “all” to ignore all changes to a resource. When “all” is used, Terraform will consider the resource as unchanged if any attribute changes, effectively bypassing updates or recreations for that resource.
Insights into the usage of “ignore_changes all” command
The “ignore_changes all” command is particularly useful in situations where all changes to a specific resource should be disregarded. For example, if a particular resource’s properties are managed externally or require manual intervention, using “ignore_changes all” ensures Terraform does not modify or recreate the resource based on attribute changes.
Scenarios and use cases where this command is applicable
1. Third-party-managed resources: When integrating with existing infrastructure or services managed by other tools or platforms, using “ignore_changes all” allows users to control the updates without interfering with external management.
2. Manual modifications: When a resource requires manual changes or custom configuration that should not be overridden by Terraform, “ignore_changes all” ensures that resource properties are not modified by Terraform.
3. Sensitive data: In situations where sensitive or security-related attributes must not be modified by Terraform, specifying “ignore_changes all” prevents accidental modifications.
Implementing “ignore_changes all” in Terraform
Implementing “ignore_changes all” in Terraform involves specifying the “ignore_changes” attribute within the “lifecycle” block of a resource. The following steps outline the process:
1. Identify the resource requiring the “ignore_changes all” behavior.
2. Define the resource block in the Terraform configuration file.
3. Add a “lifecycle” block within the resource block.
4. Set the “ignore_changes” attribute to “all” within the “lifecycle” block.
5. Save the Terraform configuration file.
Example configuration:
“`
resource “aws_instance” “example” {
instance_type = “t2.micro”
ami = “ami-0c94855ba95c71c99”
lifecycle {
ignore_changes = [“all”]
}
}
“`
Best practices and recommendations for effective utilization
To effectively utilize the “ignore_changes all” feature, consider the following best practices:
1. Limit its usage: Use “ignore_changes all” sparingly and only apply it to the resources that genuinely require the behavior. Overusing this feature can lead to a lack of control and potential issues.
2. Clearly document the rationale: Comment the configuration file or provide supporting documentation explaining why “ignore_changes all” is being used for specific resources. This ensures the purpose and intention behind the attribute changes are well-documented.
3. Regularly review and update configurations: Periodically review the use of “ignore_changes all” within the Terraform configuration to ensure it aligns with the evolving requirements of the infrastructure.
Potential implications and considerations
While “ignore_changes all” provides flexibility and control, there are potential implications to be aware of:
1. Oversight of important changes: Using “ignore_changes all” can lead to overlooking crucial changes that should trigger updates or recreations in the infrastructure. Care should be taken to avoid unintended consequences.
2. Limited granularity: When using “ignore_changes all,” all changes to a resource are ignored, which may not be desirable in some cases. Ensure that the benefits outweigh any limitations before applying this command.
3. Dependencies and cascading changes: Ignoring changes to specific attributes may have cascading effects on dependent resources. Consider these dependencies carefully to ensure that changes are managed appropriately and avoid potential discrepancies.
Alternatives and limitations
There are alternative methods for managing changes in Terraform:
1. Using lifecycle hooks: Terraform supports other lifecycle hooks, such as “create_before_destroy,” “prevent_destroy,” and “delete_before_create,” which can be utilized based on specific requirements.
2. Dynamically conditionally applying changes: Leveraging Terraform’s conditional expressions allows for more granular control over when changes should be applied.
Real-world examples and case studies
To illustrate the practical applications of “ignore_changes all,” consider the following real-world examples:
1. Managing DNS records: When managing DNS records with Terraform, “ignore_changes all” can be used to prevent Terraform from modifying any external DNS changes that occur outside of its control.
2. Custom security group rules: If security group rules are modified manually to accommodate specific configurations, “ignore_changes all” can be used to avoid unintentional changes by Terraform.
Lessons learned and insights gained from these examples
From these examples, it is evident that “ignore_changes all” is particularly valuable in situations where resources require external or manual management. It allows for seamless integration with existing infrastructure and empowers users to maintain control over specific attributes without compromising the stability and consistency of the overall infrastructure.
FAQs
1. Can I use “ignore_changes all” with any Terraform resource?
Yes, “ignore_changes all” can be used with any Terraform resource.
2. Can I ignore changes to only specific attributes using “ignore_changes”?
Yes, it is possible to provide a list of attribute names to ignore instead of using “all” to ignore all attribute changes.
3. How do I handle necessary changes that should not be ignored?
For necessary changes, it is recommended to explicitly define the attribute names that should trigger updates or recreations in the Terraform configuration.
4. Are there any restrictions on where the “lifecycle” block should be placed in the Terraform configuration?
The “lifecycle” block should be placed within the respective resource block where the desired behavior needs to be applied.
5. Can I combine “ignore_changes all” with other lifecycle hooks?
Yes, it is possible to combine “ignore_changes all” with other lifecycle hooks based on the specific requirements of the resource.
In conclusion, the “ignore_changes all” feature in Terraform’s lifecycle provides users with granular control over attribute changes to resources. By utilizing this feature effectively, users can enhance stability, maintain control over resource evolution, and save time in managing their infrastructure. However, it is important to consider the potential implications, document the rationale, and regularly review configurations to ensure the best use of this feature in Terraform.
39. Terraform Lifecycle Meta Argument Ignore Changes Implement And Test
How And When To Ignore Lifecycle Changes In Terraform?
Terraform is a well-known infrastructure-as-code (IaC) tool that enables the provisioning and management of cloud infrastructure resources. With its declarative syntax, it allows users to define the desired state of infrastructure and automate its creation and updates. One key feature in Terraform is the lifecycle block, which provides fine-grained control over resource management during updates. However, there are situations where ignoring lifecycle changes becomes necessary. In this article, we will explore how and when to ignore lifecycle changes in Terraform, focusing on scenarios where it can be beneficial.
Understanding the Lifecycle Block
The lifecycle block in Terraform allows users to manage resource lifecycles, specifically defining behaviors during creation, update, and deletion. By specifying lifecycle settings, users can control resource replacement, prevent accidental configuration drift, and apply specific actions when updates occur.
Ignoring lifecycle changes can be achieved by defining the “ignore_changes” attribute within the lifecycle block. This attribute allows specific resource attributes to be ignored during updates, even if they have changed in the Terraform state or execution plan.
Use Cases for Ignoring Lifecycle Changes
Ignoring lifecycle changes in Terraform can be beneficial in several scenarios:
1. External Management: In certain cases, resources might be managed externally to Terraform. For example, you may have a database that is managed separately and not part of Terraform’s provisioning process. In such cases, it is important to ignore lifecycle changes related to that specific resource, preventing Terraform from trying to modify or delete it.
2. Immutable Resources: Some resources, such as immutable AMIs or network security groups, may change frequently outside of Terraform’s control. Ignoring lifecycle changes for these resources ensures that Terraform does not unnecessarily attempt to update them, avoiding conflict with external modifications.
3. Delayed Configuration Drift: In a large-scale infrastructure, it is common for certain attributes to drift due to external modifications. However, addressing these changes immediately might not always be feasible or desirable. By ignoring lifecycle changes temporarily, you can postpone syncing Terraform state with resource state until it is more convenient, reducing the risk of unintended consequences during critical periods.
4. Resource Placement: When using Terraform to provision resources across multiple availability zones or regions, resource placement decisions may vary over time. In such cases, ignoring lifecycle changes for the attributes related to resource placement helps to prevent unnecessary replacement of resources, as it avoids constant re-creation of resources in different locations.
FAQs
1. How can I ignore lifecycle changes in Terraform?
To ignore lifecycle changes, you need to define the “ignore_changes” attribute within the lifecycle block for the specific resource. This attribute takes an array of resource attributes that should be ignored during updates.
2. Can I ignore all lifecycle changes for a resource?
Yes, with the “ignore_changes” attribute, you can ignore all changes for a specific resource. Simply define the attribute and set its value to [“*”], indicating that all attributes should be ignored during updates.
3. How should I decide which changes to ignore?
Deciding which changes to ignore depends on the specific requirements of your infrastructure and the resources being managed. Reviewing resource types, their lifecycles, and external management processes will help you identify the attributes that should be ignored.
4. What happens if I ignore a necessary change by mistake?
If you mistakenly ignore a necessary change, it may lead to configuration drift and potential inconsistencies between the Terraform state and the deployed resources. In such cases, it is essential to review and correct the ignored changes to ensure the infrastructure remains in the desired state.
5. Can I ignore lifecycle changes for multiple resources at once?
Yes, you can ignore lifecycle changes for multiple resources simultaneously. Simply define the “ignore_changes” attribute within the lifecycle block for each resource, specifying the attributes that should be ignored.
Conclusion
Terraform’s lifecycle block provides powerful capabilities for managing resource lifecycles during updates. However, there are situations where ignoring lifecycle changes becomes necessary, such as when resources are managed externally, configurations drift temporarily, or resource placement decisions evolve over time. Understanding how and when to ignore lifecycle changes in Terraform allows users to achieve a more flexible and robust infrastructure management workflow. Always carefully evaluate each scenario and implement changes cautiously to avoid unintended consequences.
What Is The Terraform Lifecycle For All Resources?
Introduction:
Terraform is an Infrastructure as Code (IaC) tool that allows you to manage your infrastructure resources using code. With Terraform, you can define, create, modify, and delete infrastructure resources across various cloud providers, including Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure. When working with Terraform, it is crucial to understand the Terraform lifecycle for all resources. In this article, we will explore the Terraform lifecycle in detail, covering its stages and explaining how each stage works.
Terraform Lifecycle:
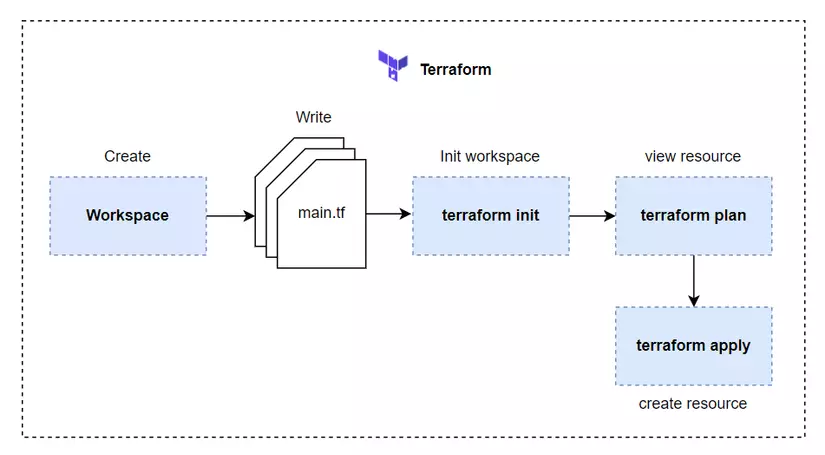
The Terraform lifecycle consists of three stages: create, update, and destroy. These stages determine how Terraform manages the resources defined in your configuration files.
Create:
During the create stage, Terraform initializes and plans the infrastructure resources before creating them. Below are the steps involved in the create stage:
1. Initialize:
Initializing is the first step in the create stage. During this step, Terraform downloads the required provider plugins and sets up the environment for your configuration. To initialize, run the following command in your Terraform project directory:
“`
terraform init
“`
2. Plan:
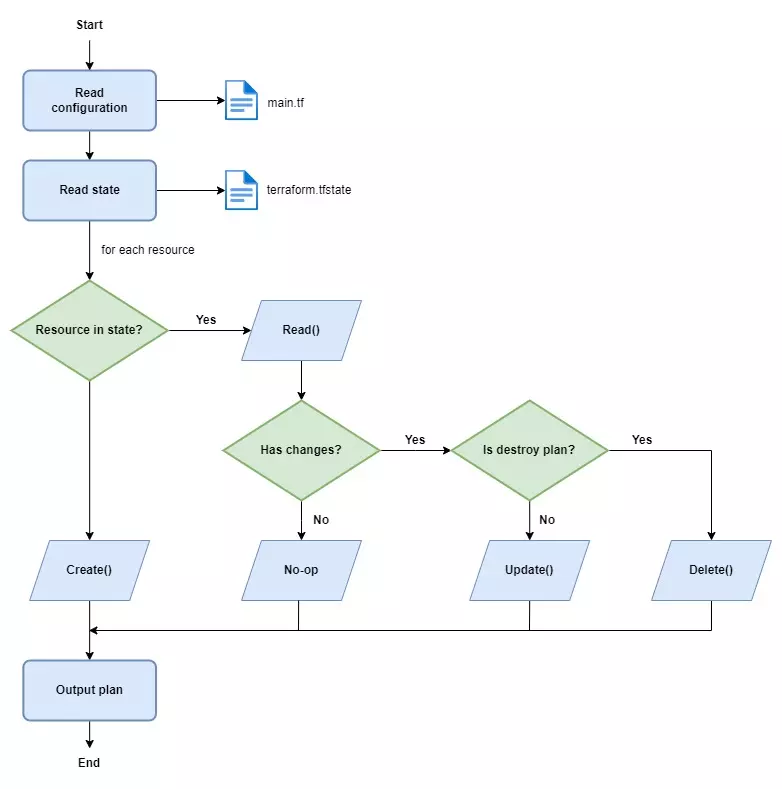
After initializing, you need to generate an execution plan using the `terraform plan` command. The plan stage analyzes your configuration files and evaluates any changes or additions needed to create the desired resources. It shows you the actions Terraform will perform without actually executing them. This allows you to verify the expected changes before proceeding.
3. Apply:
Once you are satisfied with the execution plan, you can proceed to the apply stage. Running the `terraform apply` command will create the defined infrastructure resources and store their state in a state file. This state file contains information about the resources managed by Terraform and is used to determine changes during future updates.
Update:
The update stage comes into play when you modify the infrastructure described in your configuration files. It helps you make changes to your resources without causing any downtime or loss of data. The update stage consists of the following steps:
1. Change:
When you modify your configuration files, Terraform detects the changes during the `terraform plan` command. It analyzes the differences between the current state and the desired state, highlighting the resources that need either creation, modification, or deletion.
2. Plan:
Similar to the create stage, you must generate a plan using `terraform plan` to review the proposed changes before applying them. The plan shows you what Terraform will create, modify, or delete based on your configuration changes.
3. Apply:
Once you are comfortable with the proposed changes, you can proceed to the apply stage using `terraform apply`. This command will modify your existing resources to match the updated configuration. Terraform intelligently determines the changes needed, minimizing disruptions to your infrastructure. It will create, update, or delete resources as necessary.
Destroy:
The destroy stage allows you to remove the infrastructure resources managed by Terraform. This stage is useful when you want to tear down your infrastructure or when you no longer need specific resources. Below are the steps involved in the destroy stage:
1. Plan:
Before removing resources, it is crucial to generate a destroy plan using `terraform plan -destroy`. This command will highlight the resources that will be deleted. Reviewing the destroy plan helps ensure you are aware of the impact on your existing infrastructure.
2. Apply:
After reviewing the destroy plan, you can run `terraform apply` to proceed with the deletion of resources. Terraform will remove the resources defined in your configuration, ensuring that you no longer have any traces of them in your infrastructure.
FAQs:
1. Can I skip the plan stage and directly apply changes?
No, it is not recommended to skip the plan stage. Running `terraform plan` allows you to preview the changes and understand what Terraform will do. Skipping this step might lead to unexpected behavior or unintended consequences.
2. How does Terraform handle dependencies between resources?
Terraform handles resource dependencies automatically. By analyzing your configuration and resource interdependencies, Terraform determines the correct order to create, update, or delete resources to maintain consistency.
3. Can I revert changes made by Terraform?
Terraform is not designed to directly rollback changes. However, you can use version control systems like Git to track changes and roll back to a previous version of your configuration files.
4. How does Terraform ensure the idempotency of operations?
Terraform follows the principle of idempotency, which means that applying a Terraform configuration multiple times will result in the same end-state. Terraform compares the desired state with the current state to determine if any actions are required.
In conclusion, understanding the Terraform lifecycle is essential for effectively managing infrastructure resources. By following the create, update, and destroy stages, you can ensure predictable and reliable infrastructure management with Terraform. With the ability to plan and apply changes, Terraform enables you to automate resource provisioning, modification, and tear down with ease.
Keywords searched by users: terraform lifecycle ignore_changes all Terraform lifecycle ignore_changes, terraform ignore_changes, terraform lifecycle ignore_changes example, terraform lifecycle ( ignore_changes nested), terraform lifecycle ( ignore_changes dynamic block), terraform ignore changes module, terraform ignore changes to property, terraform ignore changes to resource
Categories: Top 21 Terraform Lifecycle Ignore_Changes All
See more here: nhanvietluanvan.com
Terraform Lifecycle Ignore_Changes
In the world of infrastructure as code (IaC), Terraform has become one of the most widely adopted tools for provisioning and managing infrastructure resources across multiple cloud platforms. With its declarative language and powerful orchestration capabilities, Terraform makes it easy for developers and operators to define and manage their infrastructure as code. One crucial aspect of managing infrastructure resources with Terraform is understanding the concept of the Terraform lifecycle and how it handles changes to resources. In this article, we will dive deep into the Terraform lifecycle and take a closer look at the `ignore_changes` argument, which allows users to selectively ignore certain changes to resources.
## The Terraform Lifecycle
Before we discuss the `ignore_changes` argument, let’s start by understanding the Terraform lifecycle. When you run `terraform apply`, Terraform performs a series of steps to determine what changes need to be made to your infrastructure to achieve the desired state defined in your code. These steps are as follows:
– **Init**: Initializing the Terraform working directory by downloading provider plugins and other dependencies.
– **Validate**: Checking the syntax and validating the structure of the Terraform code.
– **Plan**: Creating an execution plan that outlines the changes Terraform will make to achieve the desired infrastructure state.
– **Apply**: Applying the changes to create, modify, or delete the necessary resources.
– **Destroy**: Destroying all resources defined in the Terraform code.
Terraform uses a state file to track the state of resources managed by Terraform. This state file is crucial in understanding what resources Terraform is managing and helps Terraform generate an accurate plan when applying changes.
## The Ignore Changes Argument
Now that we have a good understanding of the Terraform lifecycle, let’s explore the `ignore_changes` argument. Often, there are situations where certain attributes of a resource should not trigger changes when a Terraform plan is applied, even though the attribute values have been modified. This could be due to external factors or because the resources are managed by other processes outside of Terraform.
For example, let’s consider an AWS EC2 instance resource managed by Terraform. The EC2 instance’s user data may be dynamically generated by an external process, making it change every time Terraform is applied. However, you may want Terraform to ignore changes to the user data attribute and prevent unnecessary recreation of the EC2 instance.
In such cases, the `ignore_changes` argument comes into play. By specifying `ignore_changes` in a resource block, you can instruct Terraform to ignore specific attribute changes when determining if a resource needs to be replaced.
The syntax for using `ignore_changes` is straightforward. It accepts a list of attribute names you want to ignore changes for, as shown below:
“`
resource “aws_instance” “example_instance” {
instance_type = “t3.medium”
ami = “ami-0c94855ba95c71c99”
ignore_changes = [
user_data,
]
}
“`
In the example above, the `user_data` attribute will be ignored when Terraform compares the desired state to the current state of the resource.
## Impact of Ignore Changes
It is essential to understand the impact of using `ignore_changes` in your Terraform code. When an attribute is specified in `ignore_changes`, Terraform will no longer detect changes to that attribute and will not attempt to recreate the resource if the attribute changes.
While this can be very useful in certain scenarios, it also means that changes to ignored attributes will not be applied automatically. As a result, any resource changes requiring those attributes to be updated must be handled manually outside of Terraform through other means.
For example, suppose you use `ignore_changes` on the user data attribute of an EC2 instance. If the user data changes outside of Terraform, it will not be automatically updated on the instance during future Terraform runs. You would need to handle these updates using other mechanisms, such as a script or automation tool.
Additionally, be cautious when using `ignore_changes` with sensitive attributes. If you ignore changes to sensitive attributes, Terraform will not recreate or modify resources containing those attributes even if they are changed externally. This could open up a security risk if you don’t have proper controls in place to handle sensitive changes.
## FAQs
**Q: Can I use `ignore_changes` with all resource types?**
A: Yes, `ignore_changes` can be used on any resource type in Terraform.
**Q: How do I determine which attributes to ignore?**
A: This depends on the specifics of your infrastructure and how resources are managed. It’s important to understand the implications of ignoring changes and carefully consider which attributes should be ignored.
**Q: Are there any alternatives to `ignore_changes` for managing dynamic attributes?**
A: Yes, there are alternative approaches like using external data sources or Terraform data blocks to fetch dynamically generated attributes.
**Q: Can I specify multiple attributes to ignore using `ignore_changes`?**
A: Yes, you can specify multiple attributes by adding them to the `ignore_changes` list.
**Q: Is `ignore_changes` supported in all versions of Terraform?**
A: Yes, `ignore_changes` is a native feature in Terraform and is supported in all recent versions.
In conclusion, the `ignore_changes` argument in Terraform provides a powerful mechanism to selectively ignore changes to certain attributes of resources. While it can be a valuable tool for managing dynamic infrastructure, it’s important to carefully consider its implications and use it judiciously in your Terraform code. With a clear understanding of the Terraform lifecycle and how `ignore_changes` works, you can confidently manage and evolve your infrastructure resources using Terraform.
Terraform Ignore_Changes
In today’s world of rapidly changing technology and infrastructure requirements, it is crucial to have a system in place to manage these changes efficiently. Terraform, an infrastructure as code (IaC) tool developed by HashiCorp, has gained significant popularity due to its ability to automate the deployment and management of cloud infrastructure resources. Terraform tracks the state of your deployed infrastructure and allows you to make updates or modifications to it through code. However, there are instances where you may want to exclude specific changes from being applied during updates. This is where the terraform ignore_changes feature proves invaluable.
Understanding Terraform Ignore_changes
Terraform’s ignore_changes attribute allows you to specify certain resource attributes that should not trigger a new resource if they change. It provides a way to maintain control over which changes are propagated to your deployed infrastructure resources. By specifying ignore_changes for particular attributes, you can ensure that Terraform focuses only on the necessary updates, reducing the chances of unintended side effects.
Ignoring Changes in Terraform: Syntax and Usage
The syntax for using ignore_changes in Terraform is straightforward. Within a resource block, you include the ignore_changes argument followed by a list of attributes to be ignored. For example:
resource “aws_instance” “example” {
ami = “ami-0c94855ba95c71c99”
instance_type = “t2.micro”
ignore_changes = [
tags,
ebs_optimized,
]
}
In this example, we have specified that changes to the tags and ebs_optimized attributes should be ignored. Consequently, when applying updates to this resource, Terraform will not create a new instance if only these specified attributes change. Instead, it will leave the existing instance untouched.
It’s important to note that ignore_changes can only be defined within a resource block and cannot be defined in a provider or module block.
Key Use Cases for Terraform Ignore_changes
Let’s explore some real-world scenarios where Terraform’s ignore_changes feature proves incredibly useful:
1. Working with auto-generated attributes: Some resource attributes are automatically generated by the provider and can change between runs. By using ignore_changes, you can avoid unnecessary changes and resource recreation. For example, if the public IP address of an EC2 instance changes due to instance replacement or scaling, ignoring this attribute will prevent Terraform from recreating the instance.
2. Preventing drift in monitored resource attributes: Attributes like compliance rules or monitored infrastructure parameters might be modified externally and should not be changed or reverted by Terraform. By specifying these attributes in the ignore_changes list, you can ensure they are not modified during resource updates.
3. Protecting sensitive information: Certain resource attributes, such as user passwords, access keys, or secrets, should never be updated by Terraform. By explicitly ignoring these attributes, you can mitigate the risk of accidental exposure.
Frequently Asked Questions (FAQs)
Q1: Can I use ignore_changes with all resource types?
A: Yes, the ignore_changes attribute can be used with any Terraform resource.
Q2: Does ignore_changes affect the plan or destroy command?
A: No, ignore_changes only affects the apply command. Both plan and destroy commands are not impacted by the ignore_changes setting.
Q3: Can ignore_changes be used within a module?
A: No, ignore_changes cannot be specified within a module block. It is only allowed within a resource block.
Q4: What happens if I modify an ignored attribute manually?
A: If an attribute that is listed in the ignore_changes setting is modified outside of Terraform, the subsequent apply command will assume that the resource has changed and attempt to apply the changes, potentially causing conflicts.
Q5: Can I use wildcards in ignore_changes?
A: No, ignore_changes only accepts explicit attribute names. Wildcards or regular expressions are not supported.
Q6: How can I override an ignored attribute when necessary?
A: To apply a change to an ignored attribute, you can temporarily remove it from the ignore_changes list. However, exercise caution when doing so, as it may lead to unintended consequences.
In summary, Terraform ignore_changes is a powerful feature that allows you to selectively control which changes are applied during updates to your infrastructure. It plays a crucial role in maintaining infrastructure as code, ensuring consistency, and preventing unnecessary resource recreation. By understanding its usage and exploring various scenarios, you can make the most out of Terraform’s capabilities and streamline your infrastructure management processes.
Terraform Lifecycle Ignore_Changes Example
Introduction to Terraform
Terraform, an open-source infrastructure as code (IaC) tool, enables users to describe infrastructure resources in a declarative manner. With its ability to manage infrastructure across various cloud providers, Terraform has gained significant popularity in the DevOps community. One of the key features of Terraform is its lifecycle management, allowing users to define how resources are created, updated, or destroyed. In this article, we will explore an important aspect of Terraform’s lifecycle management, specifically the “ignore_changes” configuration option, which provides granular control over resource updates.
Understanding Terraform Lifecycle
The Terraform lifecycle defines how resources are managed and maintained by Terraform during its lifecycle. It consists of three major stages, namely creation, update, and destruction. By default, Terraform manages resource updates by comparing the desired state (as declared in Terraform configuration) with the current state (as tracked by Terraform during previous runs). However, there are scenarios where certain changes to resources should be ignored.
Use Case: Ignoring Specific Changes
Consider a scenario where a user wants to create an Amazon Web Services (AWS) Elastic Compute Cloud (EC2) instance using Terraform. During the initial setup, the user configures the operating system and installs various software packages. If the user later wants to update the instance’s attributes, such as its tags or security groups, they do not want to reapply the initial configuration. Here, Terraform’s “ignore_changes” configuration can be incredibly useful.
The “ignore_changes” configuration option enables users to specify which resource attributes should be ignored during updates. This means that Terraform will not take any action if changes are detected in the specified attributes. It allows users to selectively exclude certain attributes from being managed by Terraform during updates, preserving any manual modifications made on those attributes.
Example Usage of “ignore_changes”
Let’s explore a practical example to better understand the usage of “ignore_changes.” Consider the following Terraform configuration for an AWS EC2 instance:
“`hcl
resource “aws_instance” “example” {
ami = “ami-0c94855ba95c71c99”
instance_type = “t2.micro”
tags = {
Name = “example-instance”
Env = “production”
}
}
“`
In this example, we have an EC2 instance with a predefined Amazon Machine Image (AMI) ID and an instance type. Additionally, there is a “tags” attribute with two key-value pairs defining the instance’s name and environment.
Now, let’s say we don’t want Terraform to manage any changes made to the “Env” tag. We can achieve this by using the “ignore_changes” configuration option as shown below:
“`hcl
resource “aws_instance” “example” {
ami = “ami-0c94855ba95c71c99”
instance_type = “t2.micro”
tags = {
Name = “example-instance”
Env = “production”
}
lifecycle {
ignore_changes = [
tags.Env
]
}
}
“`
By specifying “tags.Env” within the “ignore_changes” block, we instruct Terraform to ignore any modifications made to the “Env” tag. This means that if the “Env” tag is modified outside of Terraform, for example, through the AWS Management Console, Terraform will not attempt to bring it back to the desired state.
FAQs
Q1. When should I use the “ignore_changes” configuration option?
A1. The “ignore_changes” configuration option is useful when you want to exclude certain resource attributes from Terraform’s management during updates. This is particularly valuable when you want to preserve any manual modifications made to those attributes.
Q2. Can I use “ignore_changes” for all resource attributes?
A2. Yes, you can use “ignore_changes” for any resource attribute that you want to exclude from Terraform’s management. However, it is important to use it judiciously and only for attributes that require manual modifications.
Q3. Can I dynamically evaluate which attributes to ignore?
A4. Yes, the “ignore_changes” configuration option supports referencing variables and expressions. This allows you to dynamically evaluate which attributes to ignore based on the desired logic or conditions.
Q4. How does “ignore_changes” affect resource updates?
A4. When a resource is updated, Terraform compares the current state with the desired state. Any attributes specified in the “ignore_changes” configuration block are excluded from this comparison. Therefore, Terraform will not attempt to bring those attributes back to the desired state if any changes are detected.
Q5. Is “ignore_changes” applicable only to AWS resources?
A5. No, the “ignore_changes” configuration option is applicable to all resources managed by Terraform, regardless of the cloud provider or technology.
Conclusion
In this article, we explored Terraform’s “ignore_changes” configuration option, an essential feature of its lifecycle management. We learned how to selectively exclude certain resource attributes from Terraform’s management during updates, preserving any manual modifications made to those attributes. By providing granular control over resource updates, “ignore_changes” enables users to better manage their infrastructure as code setups.
Images related to the topic terraform lifecycle ignore_changes all

Found 12 images related to terraform lifecycle ignore_changes all theme

![Terraform] 誤解されがちなignore_changesの動き・機密情報はstateに保持されるのか? | DevelopersIO Terraform] 誤解されがちなIgnore_Changesの動き・機密情報はStateに保持されるのか? | Developersio](https://d1tlzifd8jdoy4.cloudfront.net/wp-content/uploads/2022/09/ignore_changes_1-960x281.png)


Article link: terraform lifecycle ignore_changes all.
Learn more about the topic terraform lifecycle ignore_changes all.
- The lifecycle Meta-Argument – Terraform – HashiCorp Developer
- Terraform Lifecycle Ignore changes – Stack Overflow
- How and when to ignore lifecycle changes in Terraform
- Terraform Ignore changes using ignore_changes – FreeKB
- The Three Stages of Terraform’s Lifecycle Meta Argument – Why Scalr?
- Day 69 – Meta-Arguments in Terraform – LinkedIn
- Terraform – Understanding the Lifecycle Block – DEV Community
- The Lifecycle of a Terraform Resource – Spacelift
- Terraform lifecycle Meta-Argument Explained – AWS Tip
- Terrafrom: Ignore changes on some of the managed resources
- Hashicorp Terraform – Setup – Mike Polinowski
See more: nhanvietluanvan.com/luat-hoc