Sudo A Terminal Is Required To Read The Password
Sudo, short for “superuser do,” is a command-line utility in Unix-like operating systems that allows users to run programs or perform tasks with the privileges of another user, typically the superuser or root. It provides a way for regular users to execute specific commands as an administrator without needing to log in as the superuser permanently.
Sudo is essential for system administration tasks as it helps in maintaining security and control over the system. It allows administrators to grant certain users or groups the ability to execute specific commands with elevated privileges while restricting them from becoming the superuser permanently, reducing the risk of accidental damage or misuse.
Exploring the need for a password when using sudo in the terminal
The requirement for entering a password when using sudo is a critical security measure. It ensures that only authorized users can gain superuser privileges and execute privileged commands. The password acts as a safeguard to prevent unauthorized access and restrict potential misuse or accidental damage to the system.
Requiring a password for sudo provides an additional layer of security, making it harder for unauthorized users to gain root access, even if they manage to compromise a regular user’s credentials. It also enforces accountability by logging sudo commands and the user who executed them, aiding in the identification of any potential security breaches.
Different ways to use sudo in the terminal for various tasks
Sudo can be used in different ways to execute various tasks in the terminal. Here are some common examples:
1. Running a single command with elevated privileges:
“`
sudo command
“`
This allows users to execute a specific command with superuser privileges once they enter their password.
2. Running a shell session with elevated privileges:
“`
sudo -s
“`
This command opens a new shell session as the superuser, providing users with a terminal where they can execute multiple commands with elevated privileges. They will need to enter their password to authenticate.
3. Executing a command as another user:
“`
sudo -u username command
“`
This allows users to run a command with the privileges of a specified user other than the root.
The process of initiating sudo and providing the password in the terminal
To initiate sudo and provide the password in the terminal, follow these steps:
1. Open a terminal on your system.
2. Type the `sudo` command followed by the command you want to execute with elevated privileges. For example, `sudo apt-get update` to update packages in Ubuntu.
3. Press Enter.
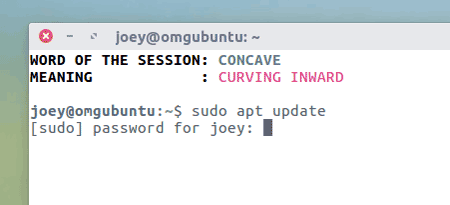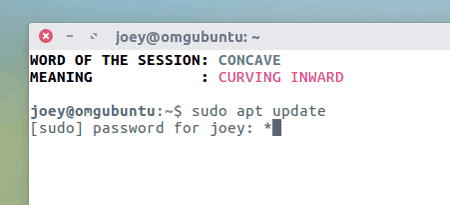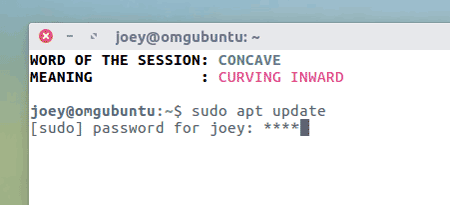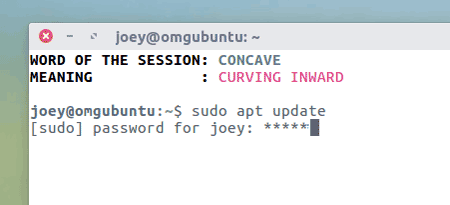
4. The terminal will prompt you to enter your password.
5. Type your password, and press Enter. Note that the password won’t appear on the screen while typing for security reasons.
6. If the password entered is correct, the command will execute with superuser privileges. Otherwise, an error message will be displayed.
Taking precautions when entering the password for sudo in the terminal
When entering the password for sudo in the terminal, it is essential to take certain precautions to ensure security:
1. Be cautious of shoulder surfing: Make sure no one is around or able to observe your password while you enter it.
2. Verify the terminal authenticity: Always ensure that you are entering the sudo password in a legitimate terminal window and not in a potentially malicious application.
3. Use strong and unique passwords: Avoid using easily guessable passwords and consider using a password manager to generate and manage strong, unique passwords.
4. Regularly update your passwords: Change your sudo password periodically to maintain security.
5. Enable Two-Factor Authentication (2FA): If available, consider enabling 2FA for your account to add an extra layer of security.
Troubleshooting common issues with sudo password authentication in the terminal
Sometimes users may encounter issues while authenticating their password with sudo in the terminal. Here are some common troubleshooting steps:
1. Verify the password: Ensure that you are entering the correct password. Remember that the password won’t be displayed on the screen while typing.
2. Check sudo configuration: Verify that the required sudo configuration allows your user account to use sudo. This can be done by checking the `/etc/sudoers` file or using the `sudo -l` command.
3. Temporarily disable password caching: If you are repeatedly asked for the password within a short interval, it might be due to password caching settings. Temporarily disabling password caching may resolve the issue.
4. Check for password expiry: If your system enforces password expiry, check if your password has expired and needs to be updated.
5. Reset the sudo password: If all else fails, you can reset the sudo password by booting into a recovery mode or by using a live CD.
Exploring the security implications of using sudo in the terminal
Using sudo in the terminal has both security benefits and risks. Some of the security implications are:
1. Enhanced security: Sudo helps ensure that users only gain elevated privileges temporarily and for specific tasks, reducing the risk of accidental damage or misuse.
2. Auditing and accountability: Logged sudo commands provide an audit trail, allowing administrators to review actions performed by users and identify any potential security breaches.
3. Granular access control: Sudo allows fine-grained control over user permissions, enabling administrators to grant certain users or groups access to specific commands while restricting others.
4. Password protection: Requiring a password for sudo adds an extra layer of security, preventing unauthorized users from gaining root access or executing privileged commands.
5. Privilege escalation vulnerabilities: Misconfigured sudo rules or software vulnerabilities may lead to privilege escalation attacks, where unauthorized users exploit sudo to gain unintended privileges.
6. Password security risks: Weak or compromised passwords can undermine the security of sudo. Users should maintain strong and unique passwords to mitigate the risk of unauthorized access.
Understanding the benefits of using sudo in the terminal for system administration tasks
Using sudo in the terminal offers several benefits for system administration tasks:
1. Improved access control: Sudo allows administrators to delegate specific administrative tasks to non-root users, reducing the amount of time spent as the superuser and minimizing the risk of accidental damage.
2. Reduced reliance on the root account: With sudo, users can execute privileged commands without needing to log in as the root user, improving security by limiting the exposure of the root account.
3. Enhanced accountability: Sudo logs provide an audit trail of all executed commands with superuser privileges, enabling administrators to monitor and review actions performed by users.
4. Simplified command execution: Sudo eliminates the need for users to switch to the root account, providing a seamless way to execute privileged commands from their own user environment.
5. Increased security awareness: By requiring users to enter their password for each sudo command, it promotes security-conscious behavior and reduces the likelihood of accidental misuse.
Exploring alternatives to providing a password for sudo in the terminal
While it is generally recommended to require a password for sudo in the terminal, there are alternative approaches that can be used based on specific requirements and security considerations. Some alternatives include:
1. Passwordless sudo: With appropriate configurations, it is possible to allow specific users or commands to execute sudo without entering a password. However, this alternative should only be used in situations where the security risks are understood and carefully managed.
2. Time-based password caching: Sudo can be configured to cache the entered password for a specific duration, allowing users to execute multiple sudo commands without re-entering their password within that time frame. This balances security and convenience, but caution should be exercised when defining the duration.
3. Two-Factor Authentication (2FA) for sudo: Implementing 2FA for sudo adds an extra layer of security by requiring users to provide a second form of authentication, such as a mobile app or a hardware token, in addition to their password.
4. Role-based access control: Instead of relying solely on passwords for authentication, implementing a role-based access control system (RBAC) can provide a more granular level of access control based on users’ roles and responsibilities.
Tips and best practices for effectively and securely using sudo in the terminal
To effectively and securely use sudo in the terminal, consider following these tips and best practices:
1. Use sudo sparingly: Only execute commands with sudo when necessary and ensure that the command you are about to run has been reviewed and validated as safe.
2. Limit sudo access: Grant sudo privileges only to users or groups that require them. Avoid granting blanket sudo access to all users.
3. Regularly review sudo configurations: Periodically review and update sudo configurations to ensure they align with the current security requirements and user responsibilities.
4. Enable auditing: Ensure that sudo logs are enabled, and review them periodically to identify any unauthorized or suspicious activity.
5. Update sudo and the operating system: Keep your system and sudo package up to date with the latest security patches and updates to protect against known vulnerabilities.
6. Educate users: Provide training and resources to users, explaining the proper usage of sudo, the importance of password security, and the potential risks and implications.
7. Implement a strong password policy: Enforce the use of strong and unique passwords for sudo authentication. Consider policies such as password complexity requirements and regular password updates.
8. Monitor for unusual sudo activity: Implement monitoring systems to detect any abnormal or unauthorized sudo activity, helping to identify potential security breaches promptly.
FAQs
Q1. Will I always need to enter my password when using sudo in the terminal?
A1. By default, sudo requires users to enter their password when executing commands with elevated privileges. However, with proper configuration, it is possible to enable passwordless sudo or implement time-based password caching.
Q2. How can I check if my user has sudo access?
A2. You can check if your user has sudo access by running the `sudo -l` command. This command displays the allowed commands and sudo privileges for the current user.
Q3. Can I configure sudo to require a password for every command?
A3. Yes, it is possible to configure sudo to require a password for every command execution. This is the default behavior in most configurations.
Q4. Is it safe to run commands as root without using sudo?
A4. Running commands as the root user without using sudo is generally discouraged because it presents a higher risk of accidental damage or misuse. Using sudo helps ensure that privileged commands are executed deliberately and with accountability.
Q5. Are there any graphical user interfaces available for sudo?
A5. Yes, there are options like gksu and kdesudo for graphical interfaces, which incorporate the use of sudo to execute privileged tasks.
Q6. Can I use sudo remotely over SSH?
A6. Yes, you can use sudo remotely over SSH to execute privileged commands on a remote system. However, ensure that proper security measures, such as key-based authentication and secure SSH configurations, are in place to prevent unauthorized access.
In conclusion, sudo is a powerful utility that allows users to perform privileged tasks in a controlled and secure manner in Unix-like operating systems. By understanding its concept, usage, and best practices, users can effectively leverage sudo to enhance system administration and ensure the security of their systems. Remember to always follow security precautions, use strong passwords, and regularly update the system to stay protected.
How To Use Sudo Command Without Entering Password In Ubuntu
Keywords searched by users: sudo a terminal is required to read the password Sudo a terminal is required to read the password either use the option, Jenkins sudo a password is required, Sudo without password, Sudo ask for password, Sudo with password, Su without password, SSH with sudo, Checking for sudo access which may request your password don t run this as root
Categories: Top 80 Sudo A Terminal Is Required To Read The Password
See more here: nhanvietluanvan.com
Sudo A Terminal Is Required To Read The Password Either Use The Option
In the world of computer programming, the terminal—a text-based interface for interacting with a computer’s operating system—holds considerable importance. It allows developers and system administrators to execute various commands and configure their systems efficiently. One essential tool for managing access and improving security in the terminal is Sudo. This article will delve into the depths of Sudo, detailing its uses, benefits, and providing answers to common questions.
What is Sudo?
Sudo, short for “superuser do,” is a command-line utility found in Unix-like operating systems, including Linux and macOS. It enables users to execute commands with the privileges of another user, typically the superuser or root. By default, the root user possesses the highest level of administrative control. However, granting unrestricted access to the root account may pose significant security risks. Sudo mitigates these concerns by allowing users to execute specific commands with escalated privileges while maintaining accountability.
How does Sudo work?
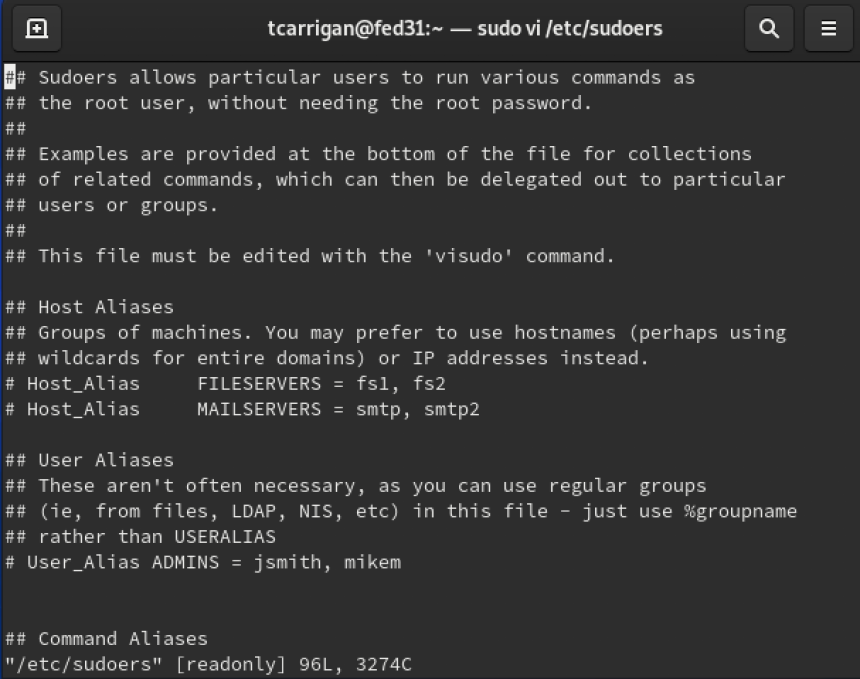
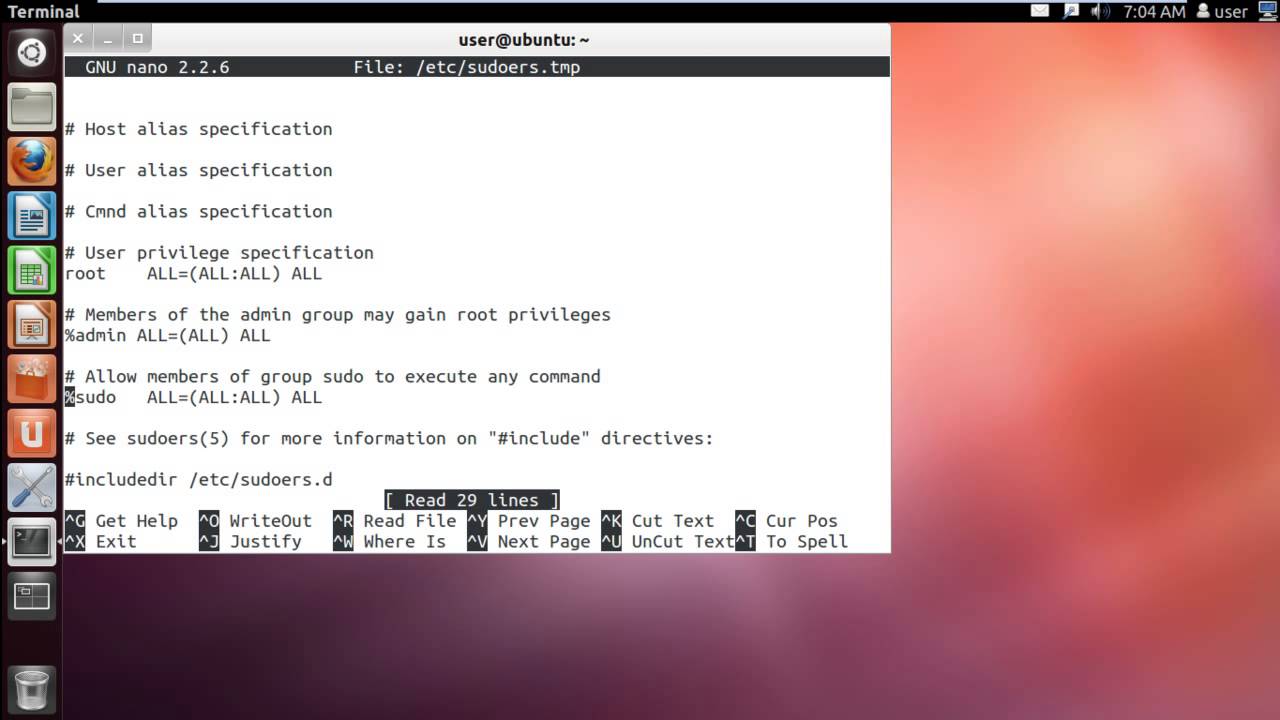
Sudo operates by referencing a configuration file, usually located at ‘/etc/sudoers,’ which contains rules and specifications for user privileges. These rules define which users can execute specific commands, as well as the conditions attached to their execution. When a user runs a command with Sudo, they are prompted to authenticate using their own password. Once authenticated, Sudo ensures that the user has the necessary privileges to run the command. If authorized, the command is executed with the privileges determined by the configuration file.
What are the benefits of using Sudo?
1. Enhanced Security: Sudo helps minimize the risks associated with unrestricted root access. By limiting which users have elevated privileges and defining specific command access, potential security vulnerabilities are significantly reduced. Sudo ensures accountability by tracking user actions, aiding in auditing and addressing any unauthorized system modifications.
2. Granular Control: Sudo’s configuration file allows administrators to fine-tune access permissions, permitting users to execute a specific set of commands while blocking access to others. This granular control minimizes the potential for users to unintentionally execute dangerous or system-altering commands, ensuring system stability.
3. Improved Collaboration: Sudo is particularly useful in multi-user environments where different individuals require varying levels of access. It allows administrators to delegate specific administrative tasks to trusted users, rather than sharing the root account credentials. This improves collaboration, as multiple users can manage the system simultaneously without compromising security.
Frequently Asked Questions (FAQs):
Q1. Can I install Sudo on any operating system?
Sudo is primarily available for Unix-like operating systems such as Linux and macOS. While Windows does not have native Sudo, alternative solutions like ‘RunAs’ or third-party utilities can provide similar functionality.
Q2. Is Sudo limited to the terminal?
Yes, Sudo is predominantly used within the terminal due to its command-line nature. It is primarily utilized for administrative tasks and requires a terminal interface to execute privileged commands.
Q3. Can I customize the Sudo configuration file?
Yes, the Sudo configuration file can be customized to suit specific requirements. However, it is important to exercise caution while modifying this file as incorrect changes can render Sudo unusable, leading to potential system access issues.
Q4. How do I check if Sudo is installed on my system?
To check if Sudo is installed, open a terminal and type ‘sudo -v’ or ‘sudo -h’ (without quotes) and press enter. If Sudo is installed, it will display the version and usage information; otherwise, it will prompt you to install it.
Q5. Are there any alternatives to Sudo?
While Sudo is the most widely used tool for elevated privileges, alternatives such as ‘su’ (substitute user) and ‘pkexec’ (PolicyKit Authorization) are also available. However, these alternatives lack some of the advanced features and customizability offered by Sudo.
In conclusion, Sudo is an invaluable utility that provides enhanced security and efficient user management within the terminal environment. By limiting access to privileged commands and enforcing accountability, Sudo helps protect systems from unauthorized modifications. Its granular control and collaborative capabilities make it an indispensable tool for effectively managing user privileges.
Jenkins Sudo A Password Is Required
Introduction
Jenkins is a popular open-source continuous integration/continuous deployment (CI/CD) tool that automates the build, test, and deployment processes of software development. It allows developers to integrate changes into a shared repository frequently, thereby facilitating faster and more reliable software releases. However, when working with Jenkins and executing certain commands, users may come across the message “sudo: a password is required.” In this article, we will delve into what this message means, explore the reasons behind it, and discuss potential solutions.
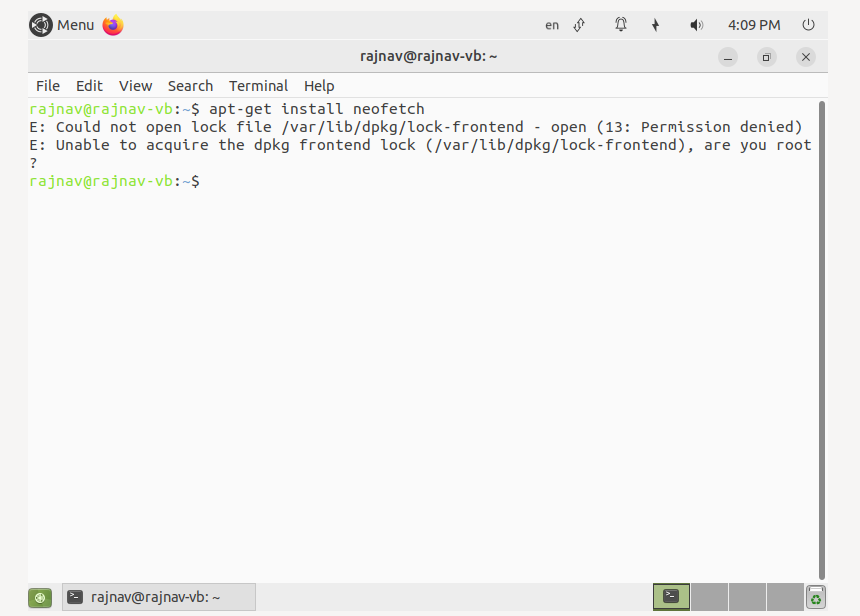
Understanding the “sudo: a password is required” message
The “sudo: a password is required” message is a result of the sudo command, which stands for “superuser do.” Sudo allows users to execute commands with the privileges of another user, typically the root user. This command is a crucial aspect of administrating Unix-like operating systems, enabling individuals to perform tasks that require elevated privileges without granting them perpetual root access.
When Jenkins users encounter this message, it typically means that the command they are attempting to run with sudo requires authentication via a user’s password. This password requirement ensures that only authorized personnel can execute privileged commands, thereby enhancing security on the system.
Reasons for the password requirement
1. Security and Privilege Separation:
Requiring a password when using sudo ensures that only authorized users can execute privileged operations. It prevents unauthorized individuals from gaining access to critical system components, files, and software. This security measure helps to mitigate the risk of unauthorized changes or malicious activities.
2. Auditing and Accountability:
The password requirement helps create an audit trail by associating actions performed with sudo with individual user accounts. This audit trail enables system administrators to track and identify who executed specific commands, promoting accountability and assisting in troubleshooting or identifying potential security breaches.
3. Avoiding Accidental Misconfiguration:
Requiring a password before executing sudo commands serves to prevent accidental misconfiguration. It forces users to actively authenticate their elevated access, reducing the risk of unintended commands or changes that could have irreversible consequences.
Solutions to resolve the “sudo: a password is required” message
1. Providing the Password:
The simplest solution to overcome the “sudo: a password is required” message is to provide the user password when prompted. This method is useful when the command requires immediate execution and user authentication is appropriate for the specific task at hand. However, this might not be an ideal approach for automated tasks or when continuous execution is necessary.
2. Configuring sudoers file:
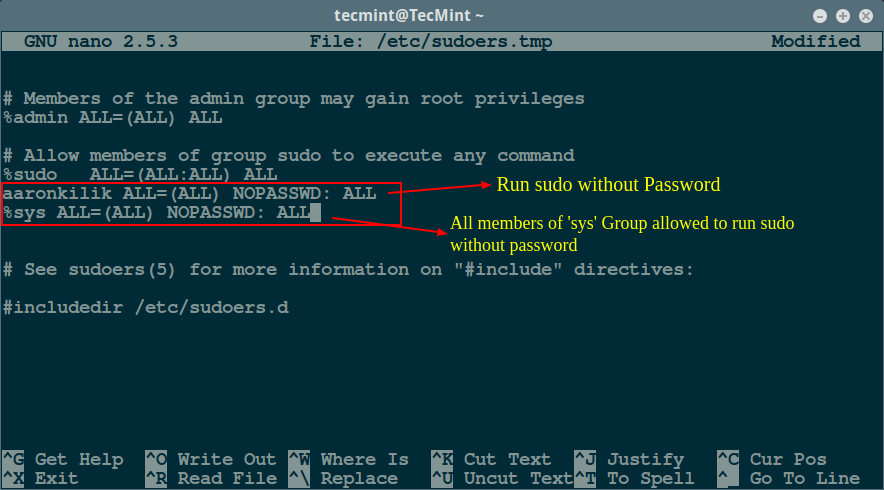
The sudoers file configures the sudo command and defines which users or groups have permission to execute commands with elevated privileges without requiring a password. By modifying the sudoers file, users can grant specific permissions to Jenkins or other users, allowing them to execute specific commands without password authentication. However, modifying the sudoers file requires caution, as incorrect changes can lead to system vulnerabilities or lockouts.
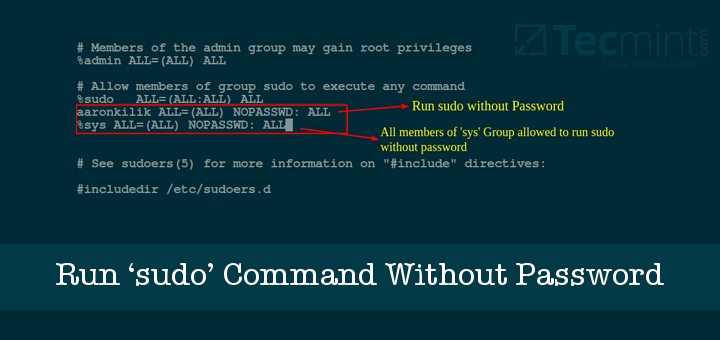
To edit the sudoers file, run the command “sudo visudo” to open in a safe editor. Then, add a line specifying the command and user or group. For example, to grant Jenkins access to execute the “apt-get update” command without password authentication, add the following line to the sudoers file:
jenkins ALL=(ALL) NOPASSWD: /usr/bin/apt-get update
Save the file, and Jenkins will now be able to execute the specified command without providing a password.
FAQs
Q1. Can I remove the password requirement altogether?
A1. While technically possible, it is strongly advised not to remove the password requirement entirely. Doing so would compromise the system’s security, as anyone with access to the user account could execute privileged commands. It is essential to strike a balance between convenience and security by carefully managing user privileges.
Q2. How can I check if I have sudo privileges?
A2. Running the command “sudo -v” will prompt you to enter your password if you have sudo privileges. If you can successfully execute the command without errors, it means you have the necessary privileges.
Q3. What if the password prompt is not shown when running sudo commands?
A3. If the password prompt is not displayed when running sudo commands, it indicates that the user has already entered their password recently. By default, sudo caches the password for a certain duration (usually 15 minutes) to avoid repeatedly asking for authentication. However, this behavior can be customized in the sudoers file.
Conclusion
Encountering the “sudo: a password is required” message in Jenkins is a security mechanism designed to ensure that only authorized users can execute privileged commands. By requiring a password, Jenkins enforces security, accountability, and responsible system administration practices. While it is possible to configure sudoers file to bypass the need for authentication in specific cases, it is important to approach such modifications with caution to maintain system integrity and security.
Images related to the topic sudo a terminal is required to read the password

Found 16 images related to sudo a terminal is required to read the password theme











![How to Reset Ubuntu Linux Password on WSL [In 3 Easy Steps] How To Reset Ubuntu Linux Password On Wsl [In 3 Easy Steps]](https://itsfoss.com/content/images/wordpress/2021/06/reset-wsl-password.png)



Article link: sudo a terminal is required to read the password.
Learn more about the topic sudo a terminal is required to read the password.
- sudo: a terminal is required to read the password; either use the
- Jenkins fails: a terminal is required to read the password …
- sudo: a terminal is required to read the password [SOLVED]
- How to run sudo command without a password on a Linux or …
- Deployment Script suddenly failing with “a terminal is required …
- Sudo: a terminal is required to read the password; – Cloudmin
- How to Fix the “sudo Password Not Working” Error on Linux
- How to fix the “sudo: no tty present and no askpass program …
- Sudo ask me a password – Notes from a data witch
- Pass the Password to su/sudo/SSH Without Overriding the TTY
See more: nhanvietluanvan.com/luat-hoc