Ssh Key Environment Variable
In the fast-paced world of technology, security is a paramount concern. As more and more businesses rely on remote access and secure connections, the need for robust security solutions is on the rise. One such solution that has gained popularity is the SSH (Secure Shell) protocol. SSH allows users to securely connect to a remote server and perform various tasks. Within the SSH framework, there is a lesser-known yet vital component called the SSH Key Environment Variable. In this article, we will explore what the SSH Key Environment Variable is, how it works, why it is significant, how to set it up, and best practices for its usage. We will also touch on common troubleshooting issues.
What is an SSH Key Environment Variable?
An SSH Key Environment Variable is a configuration setting that enables the SSH protocol to retrieve and use SSH keys. SSH keys are cryptographic keys used for authentication in SSH sessions. They consist of a public key, which is stored on the remote server, and a corresponding private key, which is stored securely on the client machine. The SSH Key Environment Variable allows the SSH client to locate and use the private key for authentication.
How does SSH Key Environment Variable Work?
When an SSH session is established, the SSH client checks the SSH Key Environment Variable to determine the location of the private key associated with the session. It then uses this information to authenticate the user to the remote server. This mechanism eliminates the need to manually specify the private key for each connection, streamlining the authentication process.
Why is the SSH Key Environment Variable Important?
The SSH Key Environment Variable is crucial for ensuring a seamless and secure authentication process. By allowing the SSH client to automatically locate the private key, it eliminates the possibility of human error in specifying the correct key manually. Moreover, it saves time and effort by removing the need to repeatedly enter the private key for each SSH connection. This becomes especially significant in environments where numerous SSH connections are made frequently.
How to Set up the SSH Key Environment Variable?
Setting up the SSH Key Environment Variable requires a few simple steps:
1. Generate an SSH key pair: If you don’t already have an SSH key pair, you need to generate one. This can be done using the `ssh-keygen` command on Unix-based systems or using tools like PuTTYgen on Windows.
2. Store the private key securely: Save the private key file in a secure location on your client machine. It is crucial to protect the private key with strong encryption and restrict access to authorized users only.
3. Set the SSH Key Environment Variable: To set the SSH Key Environment Variable, you need to add the location of the private key as an environment variable. This can typically be done through the SSH client’s configuration file.
Storing SSH Keys in the SSH Key Environment Variable
It is essential to store SSH keys securely. One common practice is to encrypt the private key using a passphrase. This adds an additional layer of protection to the key, as it cannot be used without entering the passphrase. Another best practice is to regularly rotate and update SSH keys to minimize the risk of compromise.
Retrieving SSH Keys from the SSH Key Environment Variable
To retrieve the SSH key from the SSH Key Environment Variable, the SSH client uses the `ssh-add` command. This command adds the private key to the SSH agent, which is responsible for managing SSH keys. Once added to the agent, the key can be used for authentication without explicitly specifying it for each connection.
Managing SSH Keys in the SSH Key Environment Variable
To manage SSH keys in the SSH Key Environment Variable effectively, it is recommended to use key management tools. These tools provide centralized management and control over SSH keys, simplifying the process of adding, removing, and rotating keys.
Best Practices for Using the SSH Key Environment Variable
To ensure the secure and efficient usage of the SSH Key Environment Variable, consider the following best practices:
1. Protect the private key with a strong passphrase.
2. Regularly rotate SSH keys to mitigate the risk of compromise.
3. Use a key management system to simplify the management of SSH keys.
4. Restrict access to SSH keys to authorized individuals only.
5. Implement multi-factor authentication for additional security.
Troubleshooting Common Issues with the SSH Key Environment Variable
Despite its benefits, some users may encounter issues when working with the SSH Key Environment Variable. Here are some common troubleshooting tips:
– Ensure that the SSH environment variables are correctly set.
– Double-check that the RSA key is correctly specified in the environment file.
– Verify that the SSH set environment variable points to the correct private key file.
– If using a passphrase, ensure that it is entered correctly.
– Make sure the SSH Agent is running and properly configured.
– Check if SSH Agent forwarding is required for your specific use case.
In conclusion, the SSH Key Environment Variable is a crucial component of the SSH protocol that simplifies and secures the authentication process for remote connections. By liberating users from the need to manually specify the private key, it saves time and eliminates human error. By following best practices and adhering to security principles, organizations can fully harness the advantages of the SSH Key Environment Variable while maintaining a robust security posture.
Python Quick Tip: Hiding Passwords And Secret Keys In Environment Variables (Mac \U0026 Linux)
How To Pass Environment Variable In Ssh?
Introduction:
SSH (Secure Shell) is a widely used network protocol that allows secure remote access to a computer or server. It provides a secure channel over an unsecured network by encrypting the data sent between the client and the server. Environment variables are values that can be set within an operating system or session to affect the behavior of processes and programs. In this article, we will explore different methods to pass environment variables in SSH and discuss their usage.
Methods of Passing Environment Variables in SSH:
1. Inline Environment Variable Declaration:
The simplest and most straightforward method is to declare the environment variable inline when executing an SSH command. Here’s an example:
“`
ssh user@hostname ‘VAR=value sheLLcommand’
“`
In this example, we set the value of VAR as “value” and execute the sheLLcommand within the SSH session. This method is useful when you need to pass a specific value for a single command.
2. SSH Config File:
Another approach is to define environment variables in the SSH configuration file. The SSH configuration file is typically located at /etc/ssh/sshd_config. To define environment variables globally, open the configuration file and add the following line:
“`
AcceptEnv VAR
“`
Replace “VAR” with the name of the environment variable you want to pass. Multiple variables can be specified by separating them with spaces. After making the change, restart the SSH service for the changes to take effect.
3. SSH Environment File:
SSH also allows the usage of environment files, which are specific files that contain environment variable declarations. Follow these steps to use an environment file:
a. Create an environment file, e.g., ssh_env_vars, and add your environment variable declarations. For example:
“`
VAR1=value1
VAR2=value2
“`
b. Copy the environment file to the remote server:
“`
scp ssh_env_vars user@hostname:~/
“`
c. On the remote server, add the following line to your ~/.bashrc or ~/.bash_profile file:
“`
source ~/ssh_env_vars
“`
This will load the environment file and set the specified variables whenever you log in via SSH.
Frequently Asked Questions (FAQs):
Q1. Why would I need to pass environment variables in SSH?
A1. There are several scenarios where passing environment variables in SSH can be useful. For example:
– Specifying specific configurations or settings for an SSH session
– Setting environment variables required by programs or scripts on the remote server
– Managing different environments (e.g., development, staging, production) with distinct configurations
Q2. Are all environment variables passed automatically when using SSH?
A2. No, by default, SSH does not automatically pass environment variables. You need to employ one of the methods mentioned above to pass them explicitly.
Q3. Can I pass environment variables only to specific SSH sessions?
A3. Yes, you can pass environment variables only to specific SSH sessions using the -o option. For example:
“`
ssh -o SendEnv=VAR user@hostname
“`
Replace “VAR” with the name of the environment variable. Add multiple -o options to pass multiple variables.
Q4. Will the environment variables passed with SSH be available to all processes on the remote server?
A4. No, the availability of environment variables depends on how the remote server is configured. Some servers may restrict access to specific environment variables for security reasons.
Q5. Is there a limit to the number of environment variables that can be passed using SSH?
A5. There is no specific limit to the number of environment variables that can be passed using SSH. However, it is suggested to limit the number of variables and use them judiciously to maintain simplicity and avoid potential conflicts.
Conclusion:
Passing environment variables in SSH sessions can greatly enhance flexibility and customizability. Whether you need to set configurations, execute specific commands, or manage different environments, the methods discussed in this article provide you with means to accomplish these tasks. Understanding these approaches empowers you to utilize SSH efficiently and effectively.
How To Get Ssh Key Value?
SSH (Secure Shell) keys are cryptographic keys used for secure communication between two computers. In the context of connecting remotely to servers or transferring files securely, SSH keys play a crucial role in encrypting data and authenticating users. Obtaining an SSH key value requires a few steps, which we will discuss in depth in this article.
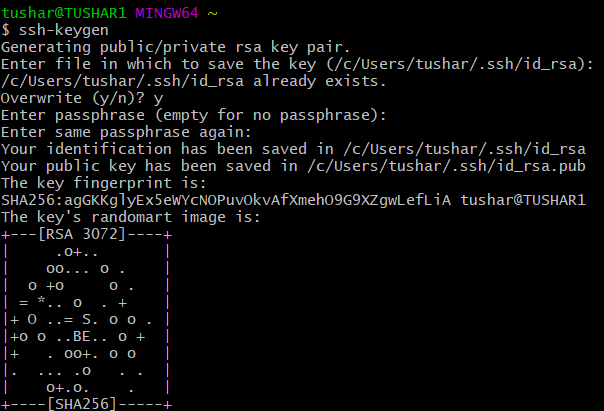
Generating an SSH Key Pair:
Before obtaining the SSH key value, you first need to generate a key pair. The key pair consists of a public key and a private key. The private key must be kept secure and should never be shared, while the public key can be freely distributed.
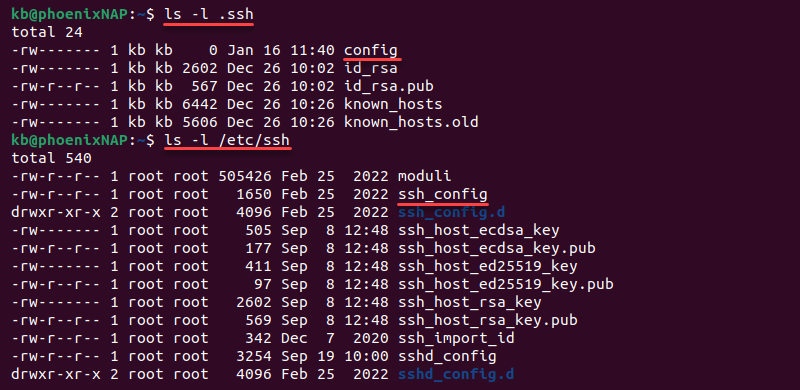
Step 1: Check for Existing SSH Keys: To ensure you don’t generate a new key pair if one already exists, check for existing SSH keys on your machine. Open your terminal and run the command:
“`
ls -al ~/.ssh
“`
This command will list any existing SSH keys present in the .ssh directory.
Step 2: Generate a New SSH Key Pair: If there are no existing keys or you wish to generate a new one, execute the following command in your terminal:
“`
ssh-keygen -t rsa -b 4096 -C “[email protected]”
“`
The `-t` flag specifies the type of key, and here we use RSA. The `-b` flag sets the number of bits in the key, with 4096 being a commonly-used value. Finally, `-C` allows you to add an optional comment about the key.
Step 3: Provide a Secure Passphrase (Optional): Setting a passphrase adds an extra layer of security to your SSH key. However, it is not mandatory. If you choose to set a passphrase, enter it when prompted. A strong passphrase contains a combination of uppercase and lowercase letters, numbers, and symbols.
Step 4: Generating the Key Pair: After setting a passphrase or leaving it blank, the SSH key pair will be generated. By default, the keys are saved in the .ssh directory located in your home folder. The public key will be saved with a .pub extension and the private key without any extension.
Obtaining the SSH Key Value:
Once you have generated the SSH key pair, obtaining the key value is a straightforward process.
Step 1: Use the `cat` Command: In your terminal, run the following command to display the public key value:
“`
cat ~/.ssh/id_rsa.pub
“`
This command will output the public key value directly in your terminal.
Step 2: Copy the SSH Key: Select the entire SSH key value and copy it to the clipboard. The key is a long string of characters starting with `ssh-rsa` and ending with your email address.
Using the SSH Key Value:
With the SSH key value obtained, it can now be used in various scenarios:
1. Server Authentication: When setting up a remote server, you can add the SSH key value to the server’s authorized_keys file to allow secure authentication without the need for passwords.
2. Git Repositories: Many code hosting platforms, such as GitHub, GitLab, and Bitbucket, provide SSH as a secure way to interact with repositories. You can add your SSH key value to your account settings to authenticate and push commits securely.
3. File Transfers: SSH keys can also be used for secure file transfers using protocols like SCP (Secure Copy) or SFTP (SSH File Transfer Protocol). Simply specify the SSH key value when connecting to the remote server.
FAQs about SSH Key Values:
Q1. Can I use the same SSH key pair for multiple servers?
Yes, you can use the same SSH key pair across multiple servers and platforms. Distribute the public key to all the servers while keeping the private key secure on your local machine.
Q2. How do I change the passphrase for my SSH key?
To change the passphrase for an existing SSH key, run the following command:
“`
ssh-keygen -p -f ~/.ssh/id_rsa
“`
You will then be prompted to enter the old passphrase and set a new passphrase.
Q3. I lost my private key. What should I do?
If you lose your private key, it’s essential to revoke access to any services linked with that key. You will need to generate a new SSH key pair, distribute the new public key, and update any affected accounts or servers accordingly.
Q4. Should I share my SSH key value with anyone?
No, you should never share your private key with anyone. The private key should remain secure on your machine. The public key can be shared freely as it is used for authentication purposes.
In conclusion, obtaining the SSH key value involves generating a key pair and extracting the public key. With the key value in hand, you can securely authenticate with servers, interact with Git repositories, and transfer files. Remember to keep your private key secure, change your passphrase periodically, and replace your keys if they are compromised.
Keywords searched by users: ssh key environment variable SSH environment variables, Ssh-add, RSA key in env file, ssh set environment variable, set private key as environment variable, Ssh add string, Docker SSH key, Ssh-agent forwarding
Categories: Top 31 Ssh Key Environment Variable
See more here: nhanvietluanvan.com
Ssh Environment Variables
Introduction:
Secure Shell (SSH) is a widely used cryptographic network protocol for secure remote login from one computer to another. It enables users to securely access and control remote servers and machines over an unsecured network. SSH provides a highly secure and encrypted connection, ensuring data integrity and privacy during transmission. In addition to its strong security features, SSH also supports environment variables that allow users to customize and enhance their remote SSH sessions. In this article, we will explore SSH environment variables and their significance in depth.
Understanding SSH Environment Variables:
Environment variables are dynamic values that affect the behavior of software programs and system processes. They provide a mechanism for configuring and controlling specific features within an application. SSH environment variables, specifically, influence the behavior and settings related to SSH connections.
When an SSH client establishes a connection with an SSH server, it passes several environment variables to the server. These variables help set up the remote session according to the user’s requirements. The SSH server then utilizes these variables to determine how the session should be configured. The variables can control a wide range of settings, such as the user’s preferred language, terminal type, proxy configuration, and more.
Common SSH Environment Variables:
1. SSH_CLIENT: This variable contains information about the client’s IP address, port, and the specific user that initiated the SSH connection.
2. SSH_CONNECTION: Similar to SSH_CLIENT, SSH_CONNECTION provides details about the client’s IP address, port, and also includes the server’s IP address and port.
3. SSH_TTY: This variable holds the name of the TTY (terminal) associated with the SSH session. It is useful for determining whether the session is interactive or non-interactive.
4. SSH_AUTH_SOCK: It specifies the location of the SSH authentication agent socket. This variable is used to manage SSH keys, allowing seamless authentication without re-entering passwords for every connection.
5. LANG and LC_*: These variables determine the user’s preferred language for the session. They influence the localization settings and enable SSH servers to present outputs in the user’s language.
6. TERM: TERM defines the terminal type used by the SSH client. It assists in providing an appropriate environment for the SSH session based on the terminal capabilities.
7. SSH_ORIGINAL_COMMAND: This variable contains the command provided by the client when the SSH session is initiated. It can help to restrict the allowed commands or trigger specific scripts as per the custom configuration.
Utilizing SSH Environment Variables:
SSH environment variables can be leveraged to customize and optimize SSH sessions to suit individual needs. Here are some real-world use cases where SSH environment variables play a significant role:
1. Localization and internationalization: By defining the LANG and LC_* variables, users can set the desired language for the SSH session. This ensures that the server presents the output in a language the user understands, improving usability and accessibility.
2. Proxy configuration: SSH environment variables allow users to specify a SOCKS proxy for secure tunneling of network traffic. The variables HTTP_PROXY, HTTPS_PROXY, and FTP_PROXY can be used to configure the proxy settings.
3. Automating tasks with SSH keys: The SSH_AUTH_SOCK variable facilitates seamless authentication using SSH keys. This removes the need for repetitive password input and enables users to automate remote tasks securely.
FAQs (Frequently Asked Questions):
Q1. Can SSH environment variables be modified during an ongoing session?
A1. No, SSH environment variables cannot be modified once a session is established. They are set during the initial connection setup and remain unchanged throughout the session.
Q2. How can I view the current SSH environment variables on the server-side?
A2. To view the SSH environment variables on the server, you can use the “env” command. Simply type “env” in the terminal, and it will display all the currently set environment variables.
Q3. Are SSH environment variables only applicable for the SSH client-side or server-side as well?
A3. SSH environment variables are relevant to both the client and server sides. The client sets the variables and sends them to the server during the connection establishment. The server then uses these variables to configure the session.
Q4. Can I create custom SSH environment variables?
A4. Yes, you can create custom SSH environment variables to suit your specific requirements. However, it is essential to ensure that the variables are supported and recognized by both the SSH client and server.
Conclusion:
SSH environment variables play a crucial role in customizing and controlling SSH sessions. They enable users to tailor their remote connections based on individual preferences and needs. Understanding and effectively utilizing SSH environment variables empowers users to maximize the benefits of SSH and enhances the overall remote access experience.
Ssh-Add
Introduction:
Secure Shell (SSH) is a cryptographic network protocol widely used for secure remote login, file transfer, and command execution in a secure manner. SSH relies on public-key cryptography to authenticate users and establish a secure connection with remote servers. To manage these cryptographic keys effectively, SSH offers several tools, and one such tool is ssh-add. This article will delve into the intricacies of ssh-add and provide an in-depth guide on its usage and features.
Understanding ssh-add:
ssh-add is a command-line utility that allows users to add their private SSH keys to the SSH authentication agent. The authentication agent acts as a mediator between the user and remote servers, facilitating the authentication process while keeping the private keys secure. Through ssh-add, users can add their private keys to the agent’s cache, enabling them to authenticate with remote servers without entering the passphrase each time.
Key Features and Usage:
1. Adding Private Keys:
The primary function of ssh-add is to add private keys to the agent. By using the command “ssh-add [keyfile]”, users can load their private keys into the authentication agent. The keyfile parameter specifies the path to the private key file to be added. This process prompts users to enter the passphrase associated with the key, decrypting it and making it available for subsequent connections.
2. Unlocking Private Keys:
When a private key is added to the agent, users can unlock it by entering the associated passphrase. Once unlocked, the key remains available in the agent’s cache until explicitly removed or until the agent process is terminated. This allows users to establish secure connections without re-entering the passphrase for every session.
3. Listing Loaded Keys:
Users can list the keys currently loaded into the authentication agent by running the command “ssh-add -l”. This command provides a convenient way to verify the loaded keys, ensuring that the correct keys are available for authentication.
4. Removing Private Keys:
To remove a specific key from the agent’s cache, users can utilize the “ssh-add -d [keyfile]” command. This command removes the specified private key from the agent, requiring the passphrase to be re-entered when the key is needed again. Additionally, the “ssh-add -D” command can be used to remove all loaded keys from the agent, effectively clearing the key cache.
Frequently Asked Questions (FAQs):
Q1. Why should I use ssh-add?
A1. Using ssh-add eliminates the need to repeatedly enter the passphrases associated with private keys during SSH sessions. It offers convenience without compromising security.
Q2. Can I add multiple private keys to the agent?
A2. Yes, ssh-add allows users to add multiple private keys to the agent, making them available for authentication.
Q3. How can I avoid entering the passphrase every time the agent starts?
A3. Users can utilize the “-K” option while adding the key (e.g., ssh-add -K [keyfile]) to store the passphrase in the macOS keychain. This allows the agent to automatically unlock the key whenever it’s required.
Q4. Can I use ssh-add with agent forwarding?
A4. Yes, ssh-add can be used in conjunction with agent forwarding. This feature allows the agent on your local machine to forward the authentication request to a remote server, enabling passwordless authentication on the remote machine.
Q5. Is it safe to keep private keys loaded in the agent?
A5. While it is generally safe to keep the private keys loaded in the agent, it is recommended to remove keys that are no longer required or periodically restart the agent. This mitigates the risk of unauthorized access to private keys if the machine is compromised.
Conclusion:
Ssh-add is a powerful utility that simplifies SSH key management, providing a convenient and secure way to handle private keys. By understanding ssh-add’s features and usage, users can streamline their SSH connections and enhance the overall security of their workflow. Whether you’re a system administrator or a regular SSH user, ssh-add proves to be an invaluable tool for managing your cryptographic keys effectively.
Rsa Key In Env File
In the world of cybersecurity, encryption plays a pivotal role in safeguarding sensitive information. One popular encryption algorithm is RSA (Rivest-Shamir-Adleman), widely used for secure data transmission and authentication. In this article, we will delve into the concept of RSA key stored in an env file, discussing its significance, implementation, and addressing common FAQs related to its usage.
What is an RSA Key?
An RSA key pair consists of a public key and a private key. The public key is used for encrypting data, while the private key is employed to decrypt the encrypted data. Asymmetry is the central characteristic of RSA encryption, wherein the public key can encrypt data, but it is nearly impossible to decipher it without the corresponding private key. This makes RSA encryption a secure and reliable method for securing sensitive information.
Why Store RSA Key in Env File?
An env file, short for environment file, is a text file used to store environment variables. These variables are essential configuration settings that enable software applications to function properly. Storing an RSA key in an env file offers several advantages.
Firstly, env files are simple and easy-to-use. They can be easily edited and updated, making it convenient to manage RSA keys. Additionally, env files can be securely stored, aiding in the protection of sensitive data.
Implementing RSA Key in Env File
To store RSA keys in an env file, one must follow a systematic process. Let’s take a step-by-step look at the implementation procedure:
1. Generate RSA Key Pair: Begin by generating an RSA key pair using tools like OpenSSL or libraries available in programming languages like Python or Java.
2. Convert RSA Key to String Format: RSA keys are usually generated in binary or PEM format. To store them in an env file, they need to be converted to string format.
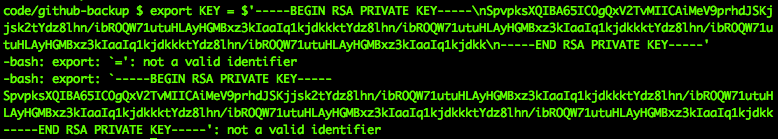
3. Define Environment Variable: Create a new line in the env file and assign it a meaningful name. For instance, RSA_PRIVATE_KEY=<
4. Save and Reference: Save the updated env file and reference the environment variable in your software application code.
It is important to follow security best practices when handling RSA keys in env files. The env file should be stored in a secure location and access to it should be restricted to authorized individuals only.
FAQs
Q1. Is it secure to store RSA keys in an env file?
Yes, when implemented correctly, storing RSA keys in an env file can be secure. However, it is crucial to ensure that the env file is kept in a secure location and access to it is restricted to authorized individuals. Additionally, the server hosting the env file should have robust security measures in place to prevent unauthorized access.
Q2. Can I encrypt the RSA key stored in an env file?
Yes, it is possible to encrypt the RSA key stored in an env file. One approach is to use a passphrase, known only to authorized individuals, to encrypt the env file. This adds an extra layer of security and ensures that even if the env file is compromised, the encrypted RSA key remains protected.
Q3. Should I include the env file in version control?
Including the env file in version control systems like Git is generally not recommended. Since env files often contain sensitive information, such as RSA keys and other credentials, it is advisable to keep them out of version control repositories. Instead, utilize secure methods to share and distribute env files among authorized individuals.
Q4. Can I rotate RSA keys stored in an env file?
Yes, periodically rotating RSA keys is considered a good security practice. When rotating keys, generate a new RSA key pair, update the env file with the new keys, and ensure the necessary updates are made in the corresponding software application. Proper documentation and communication about key rotation procedures should be established to avoid any disruptions.
Q5. Are there any alternatives to storing RSA keys in env files?
Yes, there are alternatives to storing RSA keys in env files. Some organizations choose to store RSA keys in secure key management systems designed specifically for cryptographic materials. These systems offer additional features like key rotation, access control, and centralized management, enhancing the overall security of RSA keys.
In conclusion, storing RSA keys in an env file provides a convenient and secure method for managing encryption keys in software applications. By understanding the implementation process and adhering to security best practices, organizations can ensure the confidentiality and integrity of their sensitive information. Remember to regularly review and update the state of RSA keys, keeping security at the forefront of all operations.
Images related to the topic ssh key environment variable

Found 5 images related to ssh key environment variable theme
















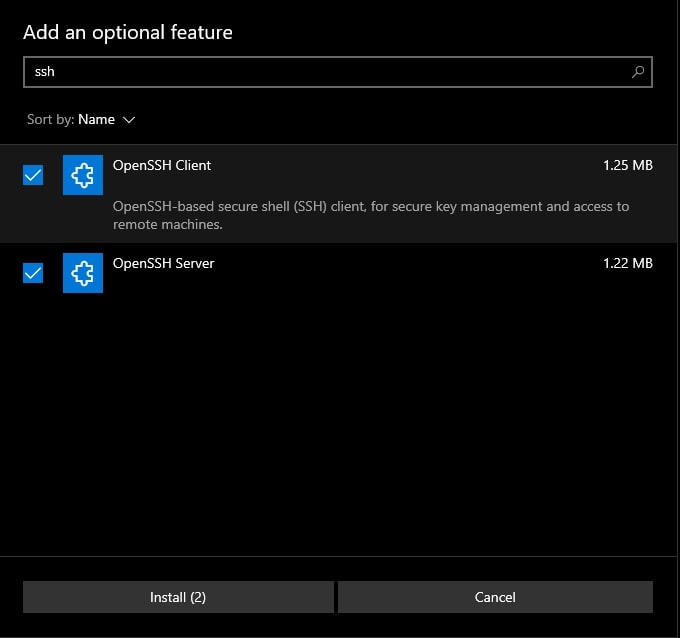

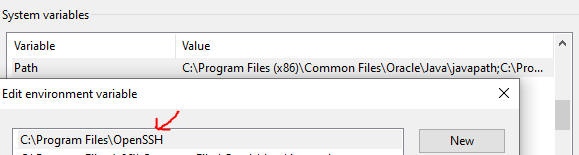




Article link: ssh key environment variable.
Learn more about the topic ssh key environment variable.
- How to pass to ssh the key stored in a shell environment …
- [Support Guide] Using an SSH key via environment variable …
- Add SSH key from variable – bash – Stack Overflow
- WTH is Environment Variables and wait, who are you SSH?
- Passing env variables to a ssh connection – Unix Stack Exchange
- Create SSH Key-Value Pair with Bash – Platform9 Docs
- Shell Environment (System Administration Guide, Volume 1)
- Git SSH Keys: A Complete Tutorial – Atlassian
- SSH private keys in an environment variable – GitLab Forum
- Environment Variables & SSH – Linux – DevPress – CSDN
- Using an Environment Variable inside of add_ssh_keys step
- Is it possible to use ssh key which contents is specified in …
See more: https://nhanvietluanvan.com/luat-hoc/