Sign_And_Send_Pubkey No Mutual Signature Supported
Overview of SSH and Public Key Authentication
Secure Shell (SSH) is a widely used protocol for secure remote access to servers and devices. It provides a secure channel for data communication, authentication, and remote command execution. Public Key Authentication is a method used by SSH to authenticate the client (user) to the server.
With Public Key Authentication, a key pair is generated on the client’s computer. The key pair consists of a private key and a public key. The private key is securely stored on the client’s computer, while the public key is added to the authorized_keys file on the server.
When the client attempts to connect to the server, the server requests the client to prove its identity by signing a challenge with its private key. The server then verifies the signature using the corresponding public key stored in the authorized_keys file. If the signature is valid, the client is granted remote access.
What is sign_and_send_pubkey?
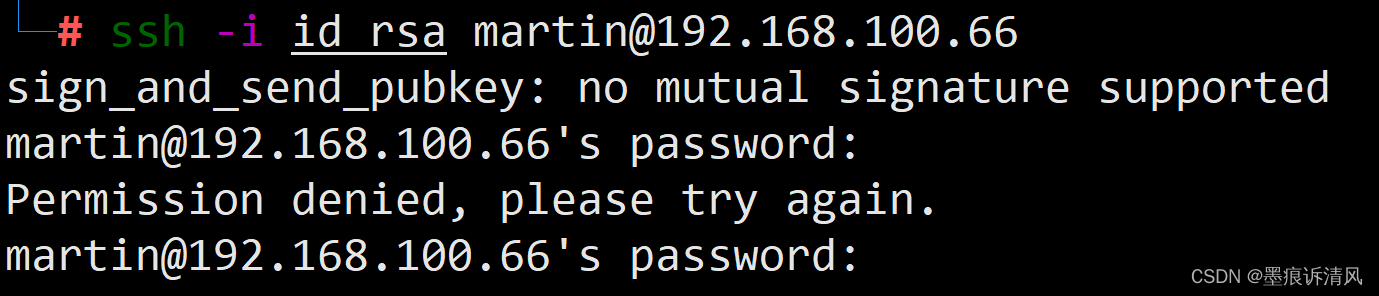
The sign_and_send_pubkey error message is encountered when attempting to establish an SSH connection using Public Key Authentication. It indicates that the client failed to sign the authentication request correctly, resulting in the server rejecting the authentication attempt.
Explanation of the “no mutual signature supported” error
The “no mutual signature supported” error refers to the situation where the client and server cannot agree on a compatible signature algorithm during the authentication process. In other words, the client’s private key and the server’s accepted signature algorithms do not match.
Understanding Public Key Authentication
Public Key Authentication relies on the principle of asymmetric encryption. The private key is kept secret on the client’s computer and is used to sign authentication requests. The public key is exchanged with the server and stored in a file called authorized_keys.
When the client wants to authenticate, the server sends a challenge to the client. The client signs the challenge using its private key, creating a signature. The server then verifies the signature using the client’s public key.
How does Public Key Authentication work?
1. Key Generation: The client generates a key pair (private and public).
2. Public Key Installation: The client installs the public key on the server by adding it to the authorized_keys file.
3. Client Authentication: When the client attempts to connect to the server, the server sends a challenge.
4. Signature Creation: The client signs the challenge using its private key, creating a signature.
5. Signature Verification: The server verifies the signature using the client’s public key.
6. Authentication Result: If the signature is valid, the client is granted access to the server.
Common causes of the “no mutual signature supported” error
1. SSH server configuration: The server may be configured to accept specific signature algorithms. If the client’s private key does not match any of the server’s accepted signature algorithms, the error occurs.
2. Incorrect public key: The public key used by the client may not match the public key stored on the server. This can happen if the public key is not correctly installed in the authorized_keys file.
3. Signature algorithm compatibility: The client may be using a deprecated or unsupported signature algorithm that the server does not accept.
Troubleshooting options for the error
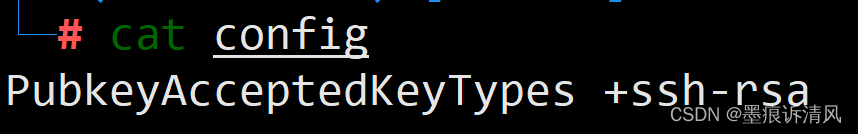
1. Checking the SSH server configuration: Look into the server’s SSH configuration file (typically located at /etc/ssh/sshd_config) and ensure that the accepted signature algorithms are compatible with the client’s private key.
2. Ensuring the correct public key is used: Verify that the public key used by the client matches the public key stored in the authorized_keys file on the server.
3. Verifying the signature algorithm compatibility: Confirm that the client’s private key uses a supported signature algorithm. You can check the algorithm using the ssh-keygen command with the -l option: ssh-keygen -l -f /path/to/private_key.
Additional security measures to enhance SSH authentication
1. Disable password authentication: Password authentication can be disabled in the SSH server configuration to force the use of Public Key Authentication. This reduces the risk of brute-force attacks on user accounts.
2. Generate key pairs with stronger algorithms and key lengths: RSA is a commonly used algorithm for key generation, but it is susceptible to certain vulnerabilities. Consider using stronger algorithms, such as Ed25519 or ECDSA, and longer key lengths for increased security.
3. Regularly rotate keys: Periodically generate new key pairs and update the public keys stored on the server. This practice mitigates the risk of compromised keys.
FAQs
Q: Why am I receiving the “sign_and_send_pubkey: signing failed for RSA” error?
A: This error typically occurs when the SSH client fails to sign an authentication request with the RSA private key. Check that the private key matches the selected signature algorithm and that it is correctly installed on the server.
Q: How do I fix the “PubkeyAcceptedKeyTypes ssh config” error?
A: This error suggests that the SSH server does not accept the specified key types. Ensure that the key types used in the configuration match the key types supported by the server.
Q: What should I do if I receive the “Permission denied (publickey)” error?
A: This error indicates that the server rejected the authentication attempt using Public Key Authentication. Verify that the correct public key is installed on the server and that the client is using the corresponding private key.
Q: How can I generate a new SSH key pair?
A: You can generate a new SSH key pair using the ssh-keygen command. For example, to generate an RSA key pair, execute: ssh-keygen -t rsa.
In conclusion, the “sign_and_send_pubkey: no mutual signature supported” error occurs when there is a mismatch between the client’s private key and the server’s accepted signature algorithms. By ensuring the correct key installation, verifying signature algorithm compatibility, and checking SSH server configurations, this error can be resolved. Implementing additional security measures like disabling password authentication, using stronger algorithms and longer key lengths, and regularly rotating keys enhances SSH authentication security.
How Do I Resolve The Ssh Error “Authentication Failed, Permission Denied” On My Ec2 Instance?
Keywords searched by users: sign_and_send_pubkey no mutual signature supported Sign_and_send_pubkey: signing failed for RSA, PubkeyAcceptedKeyTypes ssh config, Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth), Permission denied (publickey), Ssh-keygen, We did not send a packet, disable method, Gen key SSH, Receive packet: type 51
Categories: Top 89 Sign_And_Send_Pubkey No Mutual Signature Supported
See more here: nhanvietluanvan.com
Sign_And_Send_Pubkey: Signing Failed For Rsa
When it comes to securing data transmission and ensuring confidentiality, encryption plays a vital role. One commonly used encryption method is RSA (Rivest-Shamir-Adleman), which utilizes public-key cryptography. However, during the process of signing and sending a public key, users may occasionally encounter an error message stating “Sign_and_send_pubkey: signing failed for RSA.” In this article, we will explore what this error means, its possible causes, and potential solutions, ensuring that you can overcome this issue and continue using RSA encryption effectively.
Understanding Sign_and_send_pubkey: signing failed for RSA
To comprehend this error message, it’s essential to comprehend the process of signing and sending a public key. In RSA encryption, each user has a pair of keys: a public key and a private key. The private key is kept secret, while the public key is shared freely with others.
To send a message securely, the sender generally encrypts it using the recipient’s public key. Upon receiving the encrypted message, the recipient can decrypt it using their private key. Furthermore, the recipient can identify the message’s sender by verifying the signature attached to the message, which is created using the sender’s private key.
However, when the error message “Sign_and_send_pubkey: signing failed for RSA” occurs, it means that the signing process with the private key has failed. Consequently, the recipient is unable to verify the sender’s authenticity, potentially compromising the overall security of the encrypted communication.
Possible Causes and Troubleshooting
There are several potential causes for the “Sign_and_send_pubkey: signing failed for RSA” error message. Here, we will explore some common causes and offer troubleshooting tips to address them.
1. Incorrect Private Key: One possible cause is that the private key being used to sign the public key does not match the public key being sent. Ensure that you are using the correct private key associated with the public key.
2. Corrupted Key Pair: A corrupted key pair can cause signing failures. Try generating a new key pair and ensure that both the private and public keys work together correctly.
3. Invalid Key Format: The private or public key may be in an invalid format, causing the signing process to fail. Verify that the keys are in the correct format, such as the widely used PEM format.
4. Permission Issues: Insufficient permissions on the key files can also result in signing failures. Ensure that you have proper read and write permissions for the key files involved.
5. Software or Library Compatibility: Sometimes, certain software versions or libraries may have compatibility issues with RSA signing. Make sure you are using the latest software versions and libraries that are known to work well with RSA encryption.
6. Hardware Issues: Rarely, hardware-related problems can interfere with RSA signing. Ensure that your hardware devices, such as a smart card or hardware security module (HSM), are functioning correctly.
FAQs:
Q: I receive the error message “Sign_and_send_pubkey: signing failed for RSA” when using SSH. What could be the reason?
A: This error commonly occurs when attempting to authenticate using SSH. Ensure that you have the correct private key and that it matches the public key registered on the server. Additionally, check for possible permission issues on the key file.
Q: I am using popular encryption software, but the error persists. What shall I do?
A: Ensure that you are using the latest version of the encryption software, as earlier versions may have compatibility issues with RSA signing. Additionally, double-check that the key pair is intact and correctly associated.
Q: Can a firewall or anti-virus software cause this error?
A: While it’s unlikely that a firewall or anti-virus software would directly cause the “Sign_and_send_pubkey: signing failed for RSA” error, they could potentially interfere with the signing process. Temporarily disabling such software and trying again may help identify if they are the underlying cause.
Q: Should I generate a new key pair whenever I encounter this error?
A: Generating a new key pair can help address potential issues with the keys themselves, such as corruption. However, it is advisable to investigate other common causes before generating a new key pair.
Q: What are the implications of this error message for data security?
A: When this error occurs, the recipient is unable to verify the sender’s authenticity, potentially compromising the overall security of the encrypted communication. Consequently, it is crucial to resolve this error promptly to ensure data security.
In conclusion, the “Sign_and_send_pubkey: signing failed for RSA” error message can be concerning when trying to securely transmit data utilizing RSA encryption. By understanding the potential causes and utilizing troubleshooting tips, users can effectively resolve this issue. Remember to ensure the appropriate private key is being used, check for key format issues, address permission problems, and keep software and hardware up to date. By doing so, you can overcome this error and continue to benefit from the security and reliability of RSA encryption.
Pubkeyacceptedkeytypes Ssh Config
Introduction to PubkeyAcceptedKeyTypes
In the realm of secure SSH (Secure Shell) connection, the ability to authenticate using public key cryptography is widely regarded as one of the most secure methods available. SSH, originally designed as a replacement for the less secure Telnet protocol, ensures secure communication between two networked devices. To enforce secure key authentication, SSH config files come with various configuration options, one of which is the “PubkeyAcceptedKeyTypes.”
Understanding SSH Config and PubkeyAcceptedKeyTypes
SSH config files, located in the /etc/ssh/ directory on most Unix-based systems, contain various parameters governing the behavior and configurations of SSH connections. These files provide a convenient way to manage the SSH server and client settings. One such important parameter is the “PubkeyAcceptedKeyTypes,” which determines the acceptable types of public keys for authentication.
By default, SSH allows multiple key types, including RSA (Rivest-Shamir-Adleman), DSA (Digital Signature Algorithm), ECDSA (Elliptic Curve Digital Signature Algorithm), and Ed25519. However, as security threats evolve, new key algorithms are introduced while older, less secure ones are phased out. This is where configuring the “PubkeyAcceptedKeyTypes” option becomes crucial.
The PubkeyAcceptedKeyTypes Parameter Explained
The “PubkeyAcceptedKeyTypes” configuration parameter enables administrators to define the key types that the SSH server will accept for authentication. It lists the allowed key types, ensuring that only secure and preferred key types are accepted for authentication purposes.
To modify the “PubkeyAcceptedKeyTypes” parameter, one must first locate and open the SSH configuration file, typically located at /etc/ssh/sshd_config. Within this file, look for the line containing “PubkeyAcceptedKeyTypes” or add it if it does not exist. Once located, add or modify the parameter to specify the desired key types.
Key Types supported by PubkeyAcceptedKeyTypes
1. RSA (Rivest-Shamir-Adleman): RSA is one of the most widely used key types for SSH authentication. It provides strong security and good performance, making it highly recommended for most cases.
2. DSA (Digital Signature Algorithm): DSA, an older key type, is less common nowadays due to its smaller key sizes and vulnerability to certain types of attacks. It is recommended to refrain from using DSA keys unless compelled by a specific requirement.
3. ECDSA (Elliptic Curve Digital Signature Algorithm): ECDSA is based on elliptic curve mathematics and offers a good balance between security and computational efficiency. It is a recommended key type if RSA is not the desired choice.
4. Ed25519: Ed25519 is a newer key type based on the Edwards-curve Digital Signature Algorithm. It is currently gaining popularity due to its strong security and improved performance over other options.
Recommended Configurations for PubkeyAcceptedKeyTypes
To enhance the security of SSH connections, it is generally recommended to configure the “PubkeyAcceptedKeyTypes” parameter to accept only the most secure key types. The following configuration example demonstrates a secure setup:
PubkeyAcceptedKeyTypes rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp521,ecdsa-sha2-nistp384,ecdsa-sha2-nistp256,ssh-ed25519
In this example, only RSA keys using SHA-2 512 and 256 bit, ECDSA keys using NIST P-521, P-384, P-256 curves, and Ed25519 keys will be accepted for authentication. Other older key types, such as DSA, are explicitly excluded.
FAQs: Frequently Asked Questions
1. How can I check the currently allowed key types on my SSH server?
To check the currently allowed key types, you can examine the SSH server configuration file (/etc/ssh/sshd_config) and look for the “PubkeyAcceptedKeyTypes” parameter. If it is not present, the default configuration of SSH will accept all key types.
2. Can I include multiple key types in the PubkeyAcceptedKeyTypes line?
Yes, it is possible to include multiple key types in the PubkeyAcceptedKeyTypes line. Simply separate them with commas, as shown in the example configuration above.
3. How do I configure PubkeyAcceptedKeyTypes for individual users?
The “PubkeyAcceptedKeyTypes” configuration in the SSH server applies to all users. If you want to configure it differently for individual users, consider using the Match directive in the SSH configuration file to define user-specific rules.
4. What happens if a client attempts to authenticate using a key type not allowed by PubkeyAcceptedKeyTypes?
When a client attempts to authenticate using a key type that is not allowed by the PubkeyAcceptedKeyTypes configuration, the authentication will fail. The client will receive an error message indicating that the key type is not accepted and the SSH connection will be terminated.
Conclusion
The “PubkeyAcceptedKeyTypes” SSH config parameter allows administrators to define the allowed key types for secure key authentication. By carefully configuring this parameter, SSH connections can be made more secure by ensuring that only the most secure key types are accepted. To enhance overall system security, regularly update SSH configuration files, staying informed about the latest developments in key authentication algorithms, and follow recommended practices.
Images related to the topic sign_and_send_pubkey no mutual signature supported

Found 22 images related to sign_and_send_pubkey no mutual signature supported theme



![RHEL] Permissions 0644 for '/etc/ssh/ssh_host_ed25519_key' ทำให้ไม่สามารถ Start sshd.service ได้ | naiwaen@DebuggingSoft Rhel] Permissions 0644 For '/Etc/Ssh/Ssh_Host_Ed25519_Key' ทำให้ไม่สามารถ Start Sshd.Service ได้ | Naiwaen@Debuggingsoft](https://naiwaen.debuggingsoft.com/blog/wp-content/uploads/2021/03/2021-03-27_141414_ds.jpg)
Article link: sign_and_send_pubkey no mutual signature supported.
Learn more about the topic sign_and_send_pubkey no mutual signature supported.
- Sign_and_send_pubkey: no mutual signature supported
- SSH-RSA key rejected with message “no mutual signature …
- SSH no mutual signature supported – Coder v1 Docs
- ssh handshake is rejected with ‘no mutual signature algorithm …
- sign_and_send_pubkey: no mutual signature supported
- “no mutual signature algorithm” because of disabled ssh-rsa …
- SSH-RSA key rejected with message “no … – Virtuozzo Support
- No Mutual Signature Supported – SFTP Gateway Support ·
- ssh in fedora 33 error sign_and_send_pubkey: no mutual …
- SFTP connection error (sign_and_send_pubkey: no mutual …
See more: nhanvietluanvan.com/luat-hoc