Server Certificate Verification Failed. Cafile None Crlfile None
1. Overview of Server Certificate Verification
Server certificate verification is an essential process that ensures the authenticity and integrity of a server’s certificate. When a user connects to a secure website or server, their client software, such as a web browser, verifies the server’s digital certificate to establish a secure communication channel. This verification process helps prevent man-in-the-middle attacks or unauthorized access to sensitive information.
2. Importance of Server Certificate Verification
Server certificate verification is crucial for maintaining the security and trustworthiness of online communications. By verifying the server’s certificate, users can ensure they are connecting to the intended server and not an imposter. This process also validates that the server’s certificate is issued by a trusted certificate authority (CA). Failing to verify the server’s certificate can expose users to various security risks, including data interception and unauthorized access.
3. Causes of Server Certificate Verification Failure
Several factors can lead to server certificate verification failure. Common causes include:
– Expired or invalid certificate: If the server’s certificate has expired or is not properly issued, the verification process will fail.
– Self-signed or untrusted certificate: If the server’s certificate is self-signed or not issued by a trusted CA, clients may reject it, considering it untrustworthy.
– Misconfigured or missing intermediate certificates: Intermediate certificates are necessary to establish the trust chain between the server’s certificate and the root CA. If these intermediates are missing or misconfigured, the verification may fail.
– Issues with the CA’s certificate or revocation status: If the CA’s certificate is not properly installed or the certificate revocation list (CRL) is missing or outdated, the verification process may fail.
4. Understanding CAfile and CRLfile
To perform server certificate verification, client software often relies on a pre-installed set of trusted root CA certificates and a CRL, which contains information about revoked certificates. The CAfile refers to the file that contains the trusted CA certificates, while the CRLfile contains the revocation data. These files play a vital role in the certificate verification process.
5. Significance of CAfile in Certificate Verification
The CAfile contains a list of trusted root CA certificates. When a client connects to a server, it uses the CAfile to validate the server’s certificate chain. If the server’s certificate is issued by a CA listed in the CAfile, and the chain is valid, the server’s certificate is considered trusted.
6. Role of CRLfile in Certificate Verification
The CRLfile contains the revocation data, which helps determine if a certificate has been revoked by the issuing CA. During the certificate verification process, the CRLfile is consulted to check if the server’s certificate has been revoked. If the certificate is found in the CRLfile, the verification fails, as the certificate is considered untrustworthy.
7. Common Error Message: “CAfile None, CRLfile None”
The error message “CAfile None, CRLfile None” typically indicates that the client software is unable to locate the CAfile or CRLfile. This error can occur if the files are missing, misconfigured, or not accessible to the client software. Without these files, the client may not be able to perform server certificate verification successfully.
8. Troubleshooting Server Certificate Verification Failure
When encountering server certificate verification failure, there are a few troubleshooting steps you can follow:
– Verify the date and time settings on the client machine: Inaccurate date and time settings can cause certificate verification failure. Ensure the system clock is correctly configured.
– Check the CAfile and CRLfile locations: Verify the paths to the CAfile and CRLfile in your client software configurations. Ensure the files are present and accessible.
– Update CA certificates: If the CAfile is outdated or missing required root CA certificates, updating it with the latest version may resolve the issue.
– Check for intermediate certificate issues: Ensure that the server’s certificate chain includes all the necessary intermediate certificates. If any intermediates are missing or misconfigured, add or correct them as needed.
– Verify CRL availability: Ensure that the CRLfile is up to date and accessible. If necessary, obtain an updated CRLfile from the CA’s website or authority.
– Contact the server administrator: If the issue persists, it may be necessary to notify the server administrator about the certificate verification failure for further investigation.
9. Configuring CAfile and CRLfile for Successful Verification
To configure CAfile and CRLfile for successful certificate verification, follow these steps:
– Obtain the latest CAfile: Download the latest version of the CAfile, which includes trusted root CA certificates. Ensure the file is in the appropriate format required by your client software.
– Set the CAfile path: Configure your client software to use the correct path to the CAfile. This can usually be done through configuration files, environment variables, or directly in the software settings.
– Obtain the CRLfile: Download the updated CRLfile, which contains the revocation data for certificates. Verify that the file is compatible with your client software.
– Set the CRLfile path: Configure your client software to use the correct path to the CRLfile. Ensure the file is accessible and can be read by the client software.
10. Best Practices for Server Certificate Verification
To ensure secure and reliable server certificate verification, consider these best practices:
– Keep CAfile and CRLfile up to date: Regularly update your CAfile and CRLfile to include the latest trusted root CA certificates and revocation data.
– Enable automatic updates: Configure your client software to automatically update the CAfile and CRLfile when new versions become available.
– Validate server certificates: Enable strict server certificate validation to verify that the server’s certificate is signed by a trusted CA and has not been revoked.
– Implement certificate pinning: Consider implementing certificate pinning, which binds a specific server certificate to your client software, reducing the risk of connecting to a fraudulent server.
– Monitor certificate expiration: Regularly check the expiration dates of server certificates to ensure they are renewed in a timely manner.
– Use reputable CAs: Obtain server certificates from reputable and trusted CAs to ensure the integrity and authenticity of the certificates.
FAQs:
Q: What does the error message “Curl: (60) server certificate verification failed” mean?
A: This error message indicates that the server certificate verification process failed during a Curl request. It could be due to various reasons, such as an expired or untrusted certificate, missing intermediate certificates, or misconfigured CAfile or CRLfile.
Q: How can I disable SSL certificate verification?
A: Disabling SSL certificate verification is not recommended, as it exposes your connection to potential security risks. However, if you have a specific need to disable it temporarily, consult the documentation or settings of your client software for options to disable SSL certificate verification.
Q: How do I resolve the error message “Certificate verification failed: the certificate is not trusted”?
A: This error message usually indicates that the server’s certificate is not issued by a trusted CA or the CA’s certificate is missing or misconfigured. To resolve this issue, ensure that the CAfile is correctly configured and contains the necessary trusted root CA certificates.
Q: What should I do if the certificate verification failed on a Raspberry Pi?
A: If the certificate verification failed on a Raspberry Pi, follow the troubleshooting steps mentioned earlier, such as verifying the date and time settings, checking the CAfile and CRLfile locations, and updating the CA certificates.
Q: How can I disable SSL verification in Jenkins?
A: Disabling SSL verification in Jenkins is not recommended, as it compromises the security of your connections. However, if you have specific requirements, consult the Jenkins documentation or support channels for guidance on how to disable SSL verification.
Github | Ca-Certificate Server Certificate Verification Failed – Fix
What Is Server Certificate Verification Failed?
Server Certificate Verification Failed is an error message that users may encounter while using a web browser or a client application. It occurs when a connection is established with a server that presents an invalid or expired security certificate, making it impossible to establish a secure and encrypted connection. This error message is a result of the server’s failure to prove its identity and may pose serious security risks for users.
When a user accesses a website or an application through a secure connection, such as HTTPS (Hypertext Transfer Protocol Secure), the server presents a digital certificate as proof of its authenticity. This certificate is issued by a trusted Certificate Authority (CA) and includes information about the server’s identity, the CA’s signature, and other essential details. The web browser or client application then verifies the certificate to ensure that the server is indeed who it claims to be.
However, there are various reasons why a server certificate may fail verification. One common issue is an expired certificate. Certificates have a limited validity period, usually ranging from a few months to a few years. When a certificate expires, the server needs to request and install a new valid certificate. Failing to do so will result in a certificate verification failure.
Another reason for a failed verification is an incorrect or mismatched common name or hostname in the certificate. The common name is the fully qualified domain name (FQDN) of the server to which the certificate is issued. If the user tries to access a server with a different hostname, the certificate will not match, resulting in an error.
Furthermore, a certificate may be invalid if the server’s private key is compromised or if the certificate itself is forged or tampered with. In such cases, the server’s identity cannot be reliably established, and the connection is terminated to prevent any potential security breaches.
A server certificate verification failure should never be ignored, as it can leave users vulnerable to various attacks, including man-in-the-middle attacks, where an attacker intercepts and alters the communication between the user and the server. Verifying the server’s certificate is crucial to ensure secure and encrypted communication, keeping sensitive information, such as passwords, credit card data, and personal details, protected.
Frequently Asked Questions (FAQs):
Q: How can I fix a server certificate verification failure?
A: There are several steps you can take to address this issue. First, ensure that your system clock is accurate, as an incorrect system time can cause certificate verification failures. If the clock is correct, try clearing your browser’s cache and cookies. If the problem persists, contact the website or application’s administrator to ensure their server’s certificate is up to date and correctly installed.
Q: Is it safe to bypass a server certificate verification failure?
A: Bypassing the certificate verification may temporarily allow access to the website or application, but it poses significant security risks. Proceeding with an unverified certificate can expose your data to interception or modification by attackers. It is recommended to avoid bypassing the verification and instead address the underlying issue.
Q: Can browser extensions or antivirus software cause certificate verification failures?
A: Yes, certain browser extensions or antivirus programs can interfere with the certificate verification process, leading to failures. Disable any recently installed extensions or temporarily pause antivirus software to see if the issue persists. If it does, you might need to uninstall or update these applications or seek help from their developers.
Q: Why do some websites show a “Not Secure” warning instead of a certificate failure error?
A: If a website does not have a valid SSL/TLS certificate, it will be marked as “Not Secure” in modern web browsers. While this does not necessarily indicate a certificate verification failure, it means that the connection is not encrypted, making it potentially vulnerable to interception. Exercise caution when interacting with such websites, especially when sharing sensitive information.
Q: Does a certificate failure mean the website or application is malicious?
A: Not necessarily. While a failed verification may indicate a problem with the server’s certificate, it does not always mean the website or application is malicious. It could be a result of an expired certificate, misconfiguration, or other technical issues. Nevertheless, it is essential to proceed with caution and assess the situation before sharing any sensitive data.
In conclusion, a server certificate verification failure is a significant concern for users accessing websites or applications over secure connections. It occurs when the server presents an invalid or expired certificate, making it impossible to establish a secure connection. This failure poses potential security risks and requires immediate attention. By understanding the causes and taking appropriate actions, users can mitigate these risks and ensure safe browsing experiences.
How To Validate Server Certificate?
In an age where online security is of paramount importance, validating server certificates is a crucial step in ensuring that your sensitive information remains secure. Server certificates, also known as SSL/TLS certificates, provide encryption and authentication for websites and their servers. When users visit a website with a valid server certificate, they can be confident in the site’s authenticity and the safety of their data.
Certificate validation involves verifying the identity of the server through a trusted third party, known as a Certificate Authority (CA). This process is commonly performed by web browsers and other applications to ensure the authenticity and reliability of a website’s SSL/TLS certificate. Validating server certificates typically begins with a series of checks to confirm the certificate’s integrity and legitimacy.
Here is a comprehensive step-by-step guide on how to validate server certificates:
1. Check the certificate’s expiration date: The first step in validating a server certificate is to verify its expiration date. Certificates have a limited lifespan, typically ranging from one to three years. If a certificate is expired, it may no longer provide reliable security.
2. Confirm the CA’s signature: Each server certificate is digitally signed by its issuing CA. This signature ensures its authenticity and integrity. To validate a certificate, check if the CA’s signature matches the one stored by your system or web browser. If the signatures don’t match, it may indicate tampering or forgery.
3. Verify the certificate’s issuer: Validate the certificate’s issuer by comparing it with the list of trusted CAs stored on your system or web browser. If the issuer is not recognized or listed as untrusted, it could be a warning sign of a potential security risk.
4. Examine the certificate chain: A server certificate is often part of a chain of certificates, also known as the certificate chain or certificate hierarchy. Verify that each certificate in the chain is valid, properly signed, and issued by a trusted CA. Any invalid or untrusted certificates in the chain may compromise the overall security of the connection.
5. Ensure the certificate matches the domain: Check that the server certificate is issued for the correct domain you are visiting. This step is crucial in detecting potential phishing attempts, where malicious actors use certificates for deceptive purposes. If the domain and certificate do not match, it may indicate a security threat.
6. Use Certificate Transparency logs: Certificate Transparency (CT) logs are publicly accessible databases that track issued SSL/TLS certificates. By checking the CT logs, you can confirm that the certificate is properly logged and not revoked by the CA. This additional step helps ensure the certificate’s authenticity and trustworthiness.
Frequently Asked Questions (FAQs):
Q: Can I validate a server certificate manually?
A: Yes, you can manually validate a server certificate using tools like OpenSSL or online certificate validation services. However, most web browsers and applications automatically handle certificate validation to provide seamless security for users.
Q: What happens if a certificate fails validation?
A: If a server certificate fails validation, web browsers and applications typically display a warning message to the user. It is advisable not to proceed with the connection if the certificate cannot be validated, as it may indicate a potential security risk.
Q: Are all server certificates equally secure and trustworthy?
A: No, server certificates vary in terms of security and trustworthiness. Certificates issued by reputable CAs provide a higher level of trust and security compared to self-signed certificates or certificates from less recognized CAs. Always choose certificates from trusted sources.
Q: Can expired certificates be trusted?
A: No, expired certificates should not be trusted. The expiration date indicates the validity period of the certificate, and using an expired certificate compromises the security of the connection.
Q: Why is validating server certificates important for e-commerce websites?
A: Validating server certificates is vital for e-commerce websites as they handle sensitive user data such as credit card information. Without valid certificates, customers’ data could be intercepted or manipulated, leading to severe consequences for both the business and its clients.
By following these steps to validate server certificates, individuals and organizations can ensure secure connections and protect their sensitive information from potential threats. Regularly validating certificates is an essential practice in maintaining a safe and trustworthy online environment.
Keywords searched by users: server certificate verification failed. cafile none crlfile none Curl: (60) server certificate verification failed, Certificate verification failed: the certificate is not trusted, Disable SSL certificate verification, TLS certificate verification has been disabled, Certificate verification failed the certificate is not trusted raspberry, ssl certificate problem: unable to get local issuer certificate, Jenkins disable ssl verification, Etc/ssl/certs
Categories: Top 30 Server Certificate Verification Failed. Cafile None Crlfile None
See more here: nhanvietluanvan.com
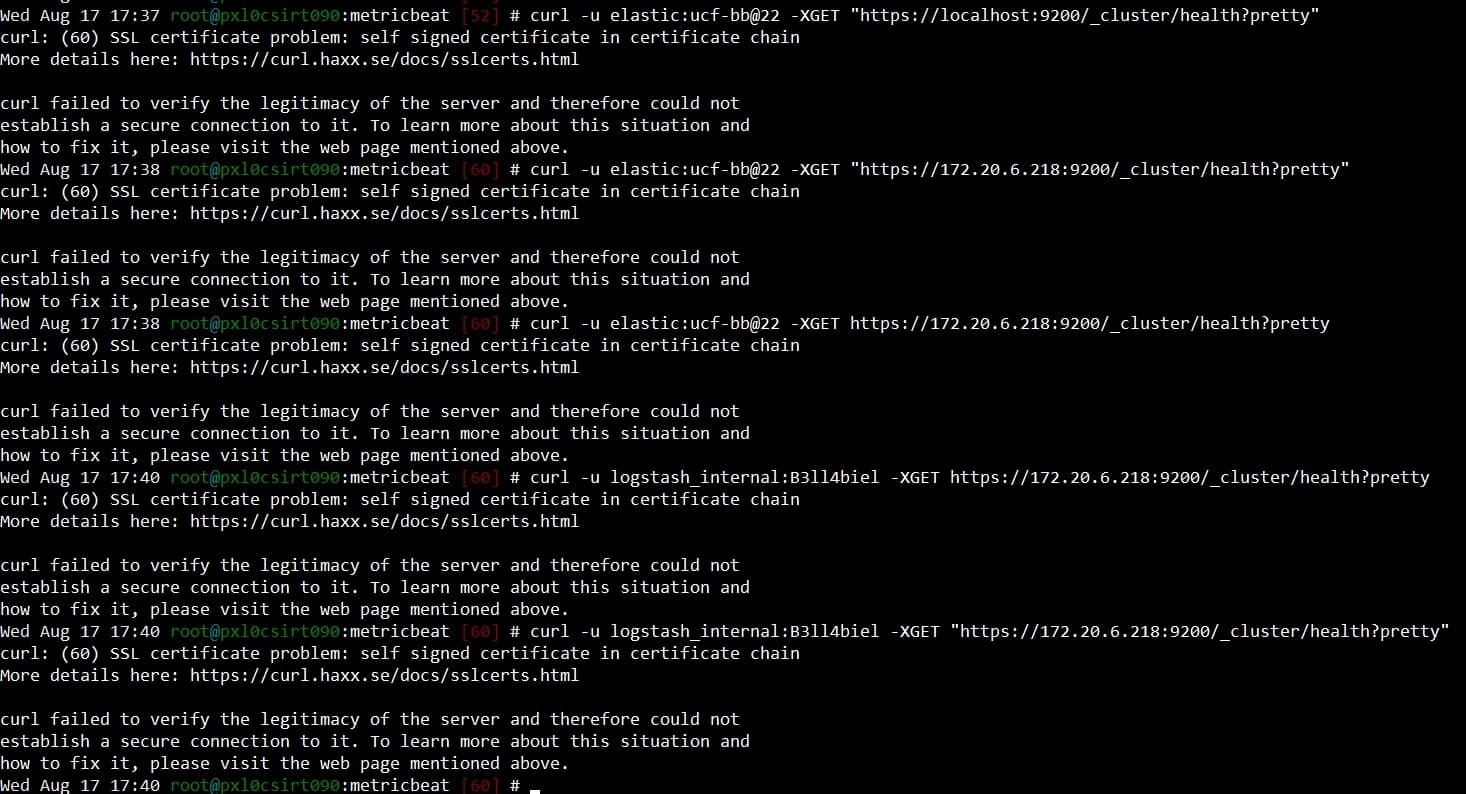
Curl: (60) Server Certificate Verification Failed
When it comes to secure and reliable data transfer over the internet, Curl is a popular choice among developers. Curl, short for “Client URL,” is a command-line tool and library that allows you to transfer data using various network protocols. It supports a wide range of protocols, including HTTP, FTP, SMTP, POP3, IMAP, and more. Curl is widely used for automated testing, web scraping, and even as a data transfer tool in various programming languages.
One of the common challenges developers face when using Curl is dealing with server certificate verification. When you initiate a secure connection to a server using Curl, it verifies the authenticity of the server’s certificate to ensure a secure and encrypted transmission of data. However, there are instances where Curl encounters the error message: “(60) Server Certificate Verification Failed.”
This error occurs when Curl cannot validate the server’s certificate. It may happen due to various reasons, such as an invalid or expired certificate, a mismatch between the server’s hostname and the certificate’s common name, or even due to a missing CA (Certificate Authority) bundle needed for verification. Let’s take a closer look at some of the reasons behind this error and how to address them.
1. Invalid or Expired Certificate:
If the server’s certificate is invalid or has expired, Curl will not be able to verify its authenticity, resulting in the “(60) Server Certificate Verification Failed” error. To resolve this, the server owner/administrator should ensure the certificate is valid and has not expired. They can either renew the certificate or acquire a valid certificate from a trusted CA.
2. Mismatched Hostname and Certificate Common Name:
Curl compares the hostname you are connecting to with the common name in the server’s certificate. If there is a mismatch, such as connecting to “example.com” but the certificate’s common name is “www.example.com,” Curl will raise the certificate verification error. To fix this, either use the correct hostname or obtain a certificate with the correct common name.
3. Missing CA Bundle:
A CA bundle contains trusted root certificates used by Curl to verify the authenticity of a server’s certificate. If it’s missing or not properly configured, Curl will fail to verify the certificate. To resolve this, make sure you have the correct CA bundle installed or specify the path to it using the `–cacert` option in Curl.
Now that we have covered some of the reasons behind the “(60) Server Certificate Verification Failed” error, let’s address some frequently asked questions related to Curl and certificate verification:
FAQs:
Q1. Can I disable server certificate verification in Curl?
A1. Yes, you can disable server certificate verification using the `-k` or `–insecure` option in Curl. However, this is not recommended, as it compromises the security of your data transmission. Disabling verification allows potential man-in-the-middle attacks, where an attacker intercepts your data.
Q2. How can I specify the path to the CA bundle in Curl?
A2. To specify the path to the CA bundle, you can use the `–cacert` option followed by the path to the bundle file. For example, `curl –cacert /path/to/cabundle.crt https://example.com`.
Q3. Is it safe to ignore the certificate verification error?
A3. Ignoring the certificate verification error is not safe, as it puts your data at risk. Server certificate verification is an essential step to ensure a secure and encrypted connection. Disabling or ignoring the error allows attackers to intercept, monitor, or modify your data.
Q4. How can I obtain a valid certificate from a trusted CA?
A4. To obtain a valid certificate from a trusted CA, you can either purchase it from a reputable CA provider or use Let’s Encrypt, which offers free SSL/TLS certificates. Follow the instructions provided by the CA to acquire and install the certificate.
In conclusion, Curl is a powerful tool for data transfer over the internet, with support for various protocols. However, server certificate verification can sometimes result in the “(60) Server Certificate Verification Failed” error. It is crucial to address the underlying causes, such as invalid or expired certificates, mismatched hostname and certificate common names, or missing CA bundles, to ensure secure and reliable data transmission. Disabling or ignoring the error is not recommended, as it compromises your data’s security. Always prioritize proper certificate verification to maintain data integrity and confidentiality.
Certificate Verification Failed: The Certificate Is Not Trusted
In the digital world, security is of utmost importance. Whether you are browsing the internet, accessing an online platform, or sending personal information, you rely on various security measures to ensure the utmost protection. One such security measure is the use of certificates, which authenticate the identity of websites and secure communication channels. However, there are instances where you might encounter a “Certificate verification failed: the certificate is not trusted” error message. In this article, we will delve into the reasons behind this error, its implications, and possible solutions.
Understanding Certificates and Certificate Authorities
Before we delve into the error message itself, it is essential to understand the role of certificates and Certificate Authorities (CAs). Certificates serve as digital passports that verify the identity of websites or individuals in online communication. They are issued by trusted third-party organizations known as Certificate Authorities.
When you access a website secured with a certificate, your device checks the authenticity of the certificate by referring to a list of trusted CAs. If the certificate is verified, the connection is considered secure. However, if the certificate is not trusted, your device may display an error message indicating that the certificate verification has failed.
Why Does the “Certificate Is Not Trusted” Error Occur?
There can be a variety of reasons why you may encounter the “Certificate verification failed: the certificate is not trusted” error message. Let’s explore some common causes:
1. Expired or Invalid Certificate: Certificates come with an expiration date to ensure their continued validity. If the certificate has expired, your device will flag it as untrusted. Similarly, if the certificate is not correctly signed or has invalid information, it may fail to gain trust.
2. Self-Signed Certificates: In certain cases, websites or organizations might create their own certificates instead of obtaining them from trusted CAs. While self-signed certificates can work in some scenarios, most applications and browsers will flag them as untrusted, leading to the certificate verification error.
3. Misconfigured or Outdated Root Certificate Authority: The trustworthiness of certificates depends on the root certificates installed on your device or browser. If the root certificate authority has been misconfigured or is outdated, it may result in certificates not being trusted.
4. Man-in-the-Middle Attacks: When a device connects to a server, any malicious actor positioned between them can intercept the communication, posing as the server. To prevent this, certificates are used to validate the authenticity of the server. If a man-in-the-middle attack occurs and the certificate is not trusted, the verification will fail.
Resolving the “Certificate Is Not Trusted” Error
Encountering the “Certificate verification failed: The certificate is not trusted” error can be frustrating, but there are several ways to resolve the issue:
1. Check Date and Time: Ensure that the date and time settings on your device are accurate. Incorrect date and time can cause certificates to appear expired or not yet valid, resulting in the verification failure.
2. Update Operating System and Software: Keeping your operating system and browser up to date is crucial. Updates often include security patches and the latest trusted root certificates, resolving any known issues.
3. Adjust Firewall or Antivirus Settings: In some cases, overly strict firewall or antivirus settings can interfere with certificate verification. Temporarily disabling these security measures or adjusting their settings can help in troubleshooting the error.
4. Clear Browser Cache: Cached data in your browser might contain outdated or incorrect certificates, leading to verification failures. Clearing the browser cache can refresh the certificate store, allowing it to perform a fresh verification.
5. Import Missing or Outdated Root Certificate Authorities: If the error persists, you can attempt to import missing or outdated root certificate authorities manually. Download the necessary certificates from trusted sources and install them to establish trust with the related websites.
6. Check Certificate Chain: When a certificate is issued by an intermediate CA, its trustworthiness relies on the higher-level root CA. If the intermediate or root CA certificates are absent or misconfigured, it can lead to trust failure. Verify the certificate chain and ensure that each CA in the chain is valid and trusted.
Frequently Asked Questions (FAQs)
Q: Should I proceed if I encounter the “Certificate verification failed: the certificate is not trusted” error while accessing a website?
A: While bypassing the error might allow you to access the website, it is not recommended. Proceeding can expose you to potential security risks, especially if the website handling sensitive information or transactions.
Q: Why are self-signed certificates not trusted?
A: Self-signed certificates are not issued by recognized Certificate Authorities, which leads to their lack of trustworthiness. Browsers and applications consider certificates from trusted CAs as reliable indicators of security.
Q: Why is trust in certificates crucial?
A: Trust in certificates ensures that the communication between your device and a server is secure and that the server’s identity is verified. Without trust, malicious actors can intercept sensitive information or impersonate trusted websites.
Q: Can a trusted certificate become untrusted?
A: Yes, a trusted certificate can become untrusted if it expires, has invalid information, or is not correctly signed. Additionally, if a root certificate authority is compromised or misconfigured, it can result in certificates losing trustworthiness.
Q: Is the “Certificate verification failed” error exclusive to web browsing?
A: No, the error can occur in various scenarios where certificates are used, such as email encryption, Virtual Private Networks (VPNs), and secure connections made through applications.
Conclusion
The “Certificate verification failed: the certificate is not trusted” error message can occur due to various reasons, such as expired or self-signed certificates, misconfigured root CAs, or man-in-the-middle attacks. To ensure secure communication, resolving the error by checking date and time settings, updating software, adjusting security measures, and verifying the certificate chain is crucial. By doing so, you can enhance your online security and protect your sensitive information from potential threats.
Images related to the topic server certificate verification failed. cafile none crlfile none

Found 45 images related to server certificate verification failed. cafile none crlfile none theme














![Ubuntu] Jenkins 업데이트 시 발생하는 에러(server certificate verification failed. CAfile: /etc/ssl/certs/ca-certificates.crt CRLfile: none) 해결 방법 Ubuntu] Jenkins 업데이트 시 발생하는 에러(Server Certificate Verification Failed. Cafile: /Etc/Ssl/Certs/Ca-Certificates.Crt Crlfile: None) 해결 방법](https://img1.daumcdn.net/thumb/C176x176/?fname=https://blog.kakaocdn.net/dn/ppLTU/btrnVayOrkR/90DKVFCObMy9KSpuM4y7M0/img.png)
![Ubuntu] Jenkins 업데이트 시 발생하는 에러(server certificate verification failed. CAfile: /etc/ssl/certs/ca-certificates.crt CRLfile: none) 해결 방법 Ubuntu] Jenkins 업데이트 시 발생하는 에러(Server Certificate Verification Failed. Cafile: /Etc/Ssl/Certs/Ca-Certificates.Crt Crlfile: None) 해결 방법](https://img1.daumcdn.net/thumb/C176x176/?fname=https://blog.kakaocdn.net/dn/dvqt8g/btrn6yAvVKE/iQjVk5sKDrZD86tNzZbRS1/img.png)
![How to fix error “[SSL: CERTIFICATE_ VERIFY_FAILED] certificate verify failed” (_ssl.c:727) – DEVOPS DONE RIGHT How To Fix Error “[Ssl: Certificate_ Verify_Failed] Certificate Verify Failed” (_Ssl.C:727) – Devops Done Right](https://blog2opstree.files.wordpress.com/2021/10/blog-fail-ssl.png)















Article link: server certificate verification failed. cafile none crlfile none.
Learn more about the topic server certificate verification failed. cafile none crlfile none.
- Server certificate verification failed. CAfile: /etc/ssl/certs/ca …
- How to Solve – Certificate Verification Failed | DataOps.live
- Server Certificate Verification Failed. CRLfile: none – Medium
- etc/ssl/certs/ca-certificates.crt CRLfile: none – Computer How To
- Server certificate verification failed … – Unix Stack Exchange
- SSL: server certificate verification failed – n software
- How to Check SSL Certificates (SSL Validation) – Venafi
- How to ignore invalid and self-signed SSL certificate errors in Curl?
- Install CA certificates on Linux systems – Hochschule Schmalkalden
- Error: server certificate verification failed. CAfile: /etc/ssl/certs …
- How to skip SSL certificate verification during git clone
- Git: client error, server certificate verification failed | Fabian Lee
- server certificate verification failed. CAfile: /etc/ssl/certs/ca …
- curl: (60) server certificate verification failed CRLfile: none
See more: https://nhanvietluanvan.com/luat-hoc/