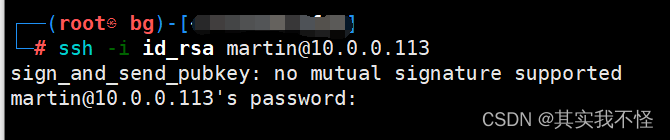
Send_Pubkey_Test: No Mutual Signature Algorithm
In the realm of secure communication, the concept of sending a public key for testing plays a pivotal role. It involves the exchange of cryptographic information between two parties to establish a secure channel for communication. The public key acts as a digital identifier and its transmission allows for authentication and encryption during the communication process. This article aims to delve into the significance of a mutual signature algorithm in secure communication, identify and explain the issue of no mutual signature algorithm, analyze its impact on secure communication, highlight the potential vulnerabilities and risks associated with it, compare different methods and protocols that enable mutual signature algorithm, explore potential alternatives and workarounds, and discuss future prospects and advancements in secure communication protocols to tackle this issue.
1. Explanation of the concept of sending a public key for testing:
When engaging in secure communication, the sender and the recipient need to authenticate each other’s identities to ensure the integrity and confidentiality of the data being transmitted. The concept of sending a public key for testing involves the sender sharing their public key with the recipient. The public key, derived from an asymmetric encryption algorithm, is used to encrypt data that can only be decrypted with the corresponding private key possessed by the recipient. By sharing the public key, the sender enables the recipient to verify their identity and establish a secure communication channel.
2. Overview of the significance of mutual signature algorithm in secure communication:
A mutual signature algorithm plays a crucial role in secure communication by enabling both parties to verify each other’s identities. It ensures that the sender’s public key is trustworthy and belongs to the intended entity. By verifying the signatures of the involved parties, mutual signature algorithms prevent impersonation and man-in-the-middle attacks, enhancing the security of the communication process. It establishes a foundation of trust between the sender and the recipient, enabling secure and confidential data transmission.
3. Identification and explanation of the issue of no mutual signature algorithm:
The issue of no mutual signature algorithm arises when the sender and the recipient do not possess compatible signature algorithms. In this scenario, the two parties cannot mutually authenticate each other, leading to the inability to establish a secure channel for communication. The absence of a mutual signature algorithm hampers the verification process, making it susceptible to malicious attacks and potential security breaches.
4. Impact of the absence of a mutual signature algorithm on secure communication:
The absence of a mutual signature algorithm significantly impacts the security of the communication process. It leaves the channel vulnerable to unauthorized access, data interception, and tampering. Without proper mutual authentication, malicious actors can impersonate one of the parties involved and gain unauthorized access to sensitive information. Furthermore, sensitive data transmitted through such channels can be intercepted, compromising the privacy and confidentiality of the communication.
5. Analysis of the potential vulnerabilities and risks associated with no mutual signature algorithm:
The absence of a mutual signature algorithm introduces several vulnerabilities and risks in secure communication. These include:
a. Sign_and_send_pubkey: signing failed for RSA: This error message indicates a failure in the signing process of the RSA public key. It suggests a potential issue with the generation or configuration of the RSA key.
b. We did not send a packet: This error message signifies a failure to send a necessary packet during the authentication process. It may be caused by misconfiguration or errors in the implemented protocols.
c. Disable method: Disabling a particular method may result in the inability to establish a secure communication channel using that method. This can increase the risk of unauthorized access and compromise the entire communication process.
d. Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth): This error indicates that the public key algorithm specified in the configuration is not accepted. It implies a mismatch between the sender’s and the recipient’s accepted algorithms.
e. Permission denied (publickey): This error message suggests that the public key authentication process failed due to a lack of proper authorization. It can be caused by incorrect key configuration or an unauthorized attempt to access the system.
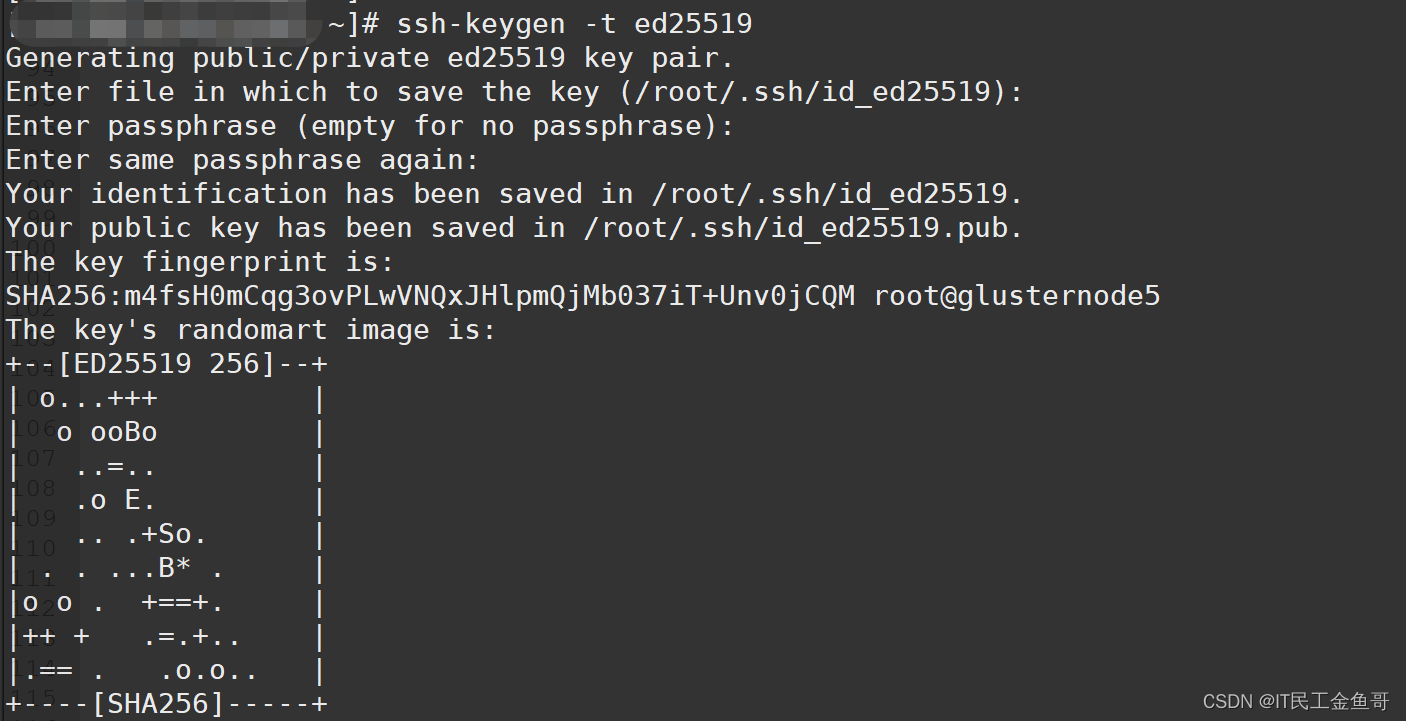
f. Ssh-keygen ed25519: This refers to the use of the Ed25519 algorithm with the ssh-keygen command to generate cryptographic keys. It offers stronger security compared to traditional algorithms like RSA.
g. Create rsa key: This command is used to generate an RSA key pair, consisting of a public and private key, for secure communication.
6. Comparison of different methods and protocols that enable mutual signature algorithm:
Several methods and protocols enable mutual signature algorithm in secure communication. Some examples include:
a. RSA (Rivest-Shamir-Adleman): RSA is one of the most widely used asymmetric encryption algorithms. It enables secure communication by generating a pair of keys—an encrypting public key and a decrypting private key.
b. DSA (Digital Signature Algorithm): DSA is an alternative to RSA and provides secure digital signatures. It offers similar functionality by enabling secure communication through mutual authentication.
c. ECDSA (Elliptic Curve Digital Signature Algorithm): ECDSA is a variant of DSA that uses elliptic curve cryptography. It offers enhanced security and efficiency compared to traditional algorithms.
7. Exploration of potential alternatives and workarounds in the absence of a mutual signature algorithm:
In the absence of a mutual signature algorithm, certain alternatives and workarounds can be implemented to ensure secure communication:
a. Implement alternative mutually supported signature algorithms: Both the sender and the recipient can identify and adopt an alternative signature algorithm that is mutually supported. This ensures compatibility and enables mutual authentication.
b. Upgrade and update cryptographic protocols: Advancements in secure communication protocols can address the issue of no mutual signature algorithm. Regularly updating and upgrading cryptographic protocols enhances security and introduces new features to address emerging threats.
c. Use third-party authentication services: Utilizing third-party authentication services, such as certificate authorities, can provide an additional layer of security and enable mutual authentication even in the absence of a mutual signature algorithm.
8. Discussion of the future prospects and advancements in secure communication protocols to address the issue of no mutual signature algorithm:
To overcome the issue of no mutual signature algorithm, future advancements in secure communication protocols are essential. Focus should be placed on developing standardized protocols that enable secure and mutually authenticated communication between diverse systems. Continuous research and development can lead to the innovation of more robust and efficient cryptographic techniques, ensuring the establishment of secure channels even in challenging scenarios.
In conclusion, the absence of a mutual signature algorithm in secure communication can have severe implications on the confidentiality and integrity of transmitted data. It hampers the establishment of secure channels and introduces vulnerabilities that can compromise the communication process. By understanding the significance of a mutual signature algorithm, identifying the associated issues and risks, and exploring potential alternatives and future advancements, we can strive towards a more secure and reliable communication landscape.
Paramiko Ssh Key-Based Authentication Example: Cisco Ios Using Specific Signature Algorithm Sha-Rsa
Keywords searched by users: send_pubkey_test: no mutual signature algorithm Sign_and_send_pubkey: signing failed for RSA, We did not send a packet, disable method, Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth), Ssh-keygen, Pubkey accepted algorithms, Permission denied (publickey), Ssh-keygen ed25519, Create rsa key
Categories: Top 93 Send_Pubkey_Test: No Mutual Signature Algorithm
See more here: nhanvietluanvan.com
Sign_And_Send_Pubkey: Signing Failed For Rsa
Introduction
When using Secure Shell (SSH) protocol to establish a secure connection between a client and a remote server, users often encounter various error messages. One such error message is “sign_and_send_pubkey: signing failed for RSA.” This article aims to provide a comprehensive understanding of this error message, its potential causes, and possible solutions.
Understanding the Error Message
The error message, “sign_and_send_pubkey: signing failed for RSA,” typically appears when attempting to authenticate with a remote SSH server. It relates specifically to the failure of signing the RSA public key during the authentication process.
RSA (Rivest-Shamir-Adleman) is a widely-used asymmetric encryption algorithm that provides secure data transmission over untrusted networks. The private key is used for signing data, while the corresponding public key verifies the signature. In the context of SSH, RSA authentication involves signing a challenge sent by the server using the client’s private key, with the server verifying it using the associated public key.
However, if the error message “sign_and_send_pubkey: signing failed for RSA” appears, it signifies that the authentication process was unable to correctly sign the challenge using RSA, preventing a successful connection to the SSH server.
Possible Causes and Solutions
To address the “sign_and_send_pubkey: signing failed for RSA” error, it is important to consider potential causes and implement the corresponding solutions. Below are the most common causes and possible solutions to tackle this error message:
1. Invalid or Corrupted Private Key:
– Solution: Verify that the private key used for authentication is valid. Ensure it has not been modified or corrupted. Generate a new private key if necessary.
2. Incorrect Permissions for Private Key:
– Solution: Ensure the private key file has the correct permissions. Restrict read/write access to prevent unauthorized users from tampering with the key. The recommended permissions are 600 (read and write for the owner only).
3. Disabled RSA Authentication on the Server:
– Solution: Check the server configuration to ensure RSA authentication is enabled. If not, consider using an alternative authentication method, such as SSH keys or password authentication.
4. Misconfiguration of SSH Client:
– Solution: Verify the SSH client’s configuration file (usually in ~/.ssh/config) for any misconfigured settings related to RSA authentication. Ensure the correct identity file (private key) is specified, and relevant directives such as “IdentityFile” or “IdentitiesOnly” are properly set.
5. Incompatible Key Formats:
– Solution: Ensure compatibility between the private key format and the SSH client. Different SSH clients might require the private key to be in a specific format, such as OpenSSH or PuTTY. Convert the key format accordingly using relevant tools like ssh-keygen or PuTTYgen.
6. Incorrect Passphrase:
– Solution: If the private key is encrypted with a passphrase, ensure the correct passphrase is provided during authentication. Carefully enter the passphrase character by character, as incorrect input will prevent the authentication process from succeeding.
FAQs:
Q1. Are there alternative authentication methods if RSA fails?
A1. Yes, SSH supports various authentication methods, including but not limited to password authentication, public key authentication, and keyboard-interactive authentication.
Q2. Can an expired RSA key cause the “sign_and_send_pubkey: signing failed for RSA” error?
A2. While an expired RSA key itself may not cause this specific error, it can lead to authentication failures. Make sure your RSA key is not expired and consider generating a new key if needed.
Q3. Can a firewall or network issue lead to RSA signing failure?
A3. It is possible, though rare, for firewalls or network issues to interfere with the RSA authentication process. Ensure that necessary port forwarding rules are in place and that the network is properly configured to allow SSH connections.
Q4. What should I do if none of the solutions mentioned resolve the issue?
A4. If you are still encountering the “sign_and_send_pubkey: signing failed for RSA” error after applying the suggested solutions, it is recommended to seek assistance from your system administrator or the support channels of the SSH client or server you are using.
Conclusion
The “sign_and_send_pubkey: signing failed for RSA” error is a common obstacle faced by SSH users during the authentication process. Understanding the potential causes of this error and implementing the suggested solutions can help overcome the issue. By addressing issues related to invalid or corrupted private keys, permissions, RSA authentication configuration, SSH client misconfiguration, incompatible key formats, and passphrase related problems, users can successfully establish secure connections to SSH servers. Should users face persistent issues, engaging professional support is advisable to ensure a swift resolution.
We Did Not Send A Packet, Disable Method
Introduction:
In the realm of computer networking, the ‘disable’ method plays a crucial role in controlling the flow of information packets. This method, though seemingly straightforward, has often led to confusion and apprehension among network administrators and users. In this article, we delve into the intricacies of the ‘disable’ method, providing an in-depth understanding of its functionality and usage.
Understanding the ‘Disable’ Method:
The ‘disable’ method is commonly used in computer networks to prevent the transmission of data packets. When enabled, it halts the flow of packets between devices, ensuring that no information is exchanged. This feature is particularly valuable in scenarios where network security, maintenance, or troubleshooting is required.
Many networking devices, such as routers, switches, and firewalls, support the ‘disable’ method. By leveraging this functionality, network administrators can effectively control and manage the flow of packets within their network infrastructure.
Key Features and Applications of ‘Disable’ Method:
1. Network Security: One primary application of the ‘disable’ method is in enhancing network security. It enables administrators to temporarily halt data communication, preventing any unauthorized access or potential cyber threats.
2. Maintenance and Upgrades: The ‘disable’ method allows network administrators to effectively perform maintenance tasks on networking devices, such as firmware updates, hardware repairs, or configuration changes, without disrupting normal network operations.
3. Troubleshooting: When network issues arise, the ‘disable’ method proves invaluable. By selectively disabling network connections, administrators can isolate problematic areas, facilitating faster identification and resolution of issues.
4. Load Balancing: In certain scenarios, network congestion or excessive load can affect performance. The ‘disable’ method can be utilized to temporarily disable specific connections or routes, redistributing the workload and improving overall network performance.
FAQs:
Q1. How does the ‘disable’ method differ from physically disconnecting devices?
A1. While physically disconnecting devices may achieve the same result, the ‘disable’ method offers a more convenient and centralized approach. It allows administrators to control network communication remotely, without physically accessing each device.
Q2. Does the ‘disable’ method permanently block packet transmission?
A2. No, the ‘disable’ method temporarily suspends packet transmission. It can be re-enabled when required to resume normal network operations.
Q3. What measures should be taken to ensure the ‘disable’ method does not compromise network productivity?
A3. It is crucial to exercise caution when implementing the ‘disable’ method to avoid unnecessary disruptions. Proper planning, clear communication with users or stakeholders, and coordinated timing can minimize the impact on productivity.
Q4. Are there any risks associated with using the ‘disable’ method?
A4. Although the ‘disable’ method is generally safe when used appropriately, incorrect configuration or accidental disabling of critical network components can temporarily interrupt network connectivity. Adequate testing and proper documentation are strongly advised to mitigate potential risks.
Q5. Can the ‘disable’ method be used in conjunction with other network management methods?
A5. Absolutely. The ‘disable’ method can complement other network management techniques, such as configuring access control lists, implementing port security, or utilizing virtual LANs (VLANs), to enhance the overall security and control of a network infrastructure.
Conclusion:
Understanding the dynamics of the ‘disable’ method is crucial for network administrators seeking to maintain a secure and efficient network infrastructure. By harnessing the power of selectively disabling packet transmission, administrators can safeguard their networks, perform essential maintenance tasks, troubleshoot issues, and optimize network performance. However, it is vital to exercise caution and apply best practices to avoid any unintended disruptions to network connectivity. Embracing the ‘disable’ method as a valuable tool in our networking arsenal, we can confidently address network challenges and ensure the smooth functioning of our digital ecosystems.
Userauth_Pubkey: Key Type Ssh-Rsa Not In Pubkeyacceptedalgorithms (Preauth)
In the world of computer networking and system administration, Secure Shell (SSH) is a widely used protocol for secure remote login and command execution. SSH relies on public-key cryptography to authenticate and establish a secure connection between a client and a server. However, there might be instances where users encounter an error message stating, “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth).” This article aims to explore the reasons behind this error, how to troubleshoot it, and provide some frequently asked questions regarding the issue.
Understanding the Error Message
When attempting to establish an SSH connection to a remote server using a public key, the server checks the received public key against a list of algorithms that it is willing to accept. This list is configured in the SSH server’s configuration file. The error message, “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth),” suggests that the server does not support the SSH-RSA algorithm for public key authentication.
Reasons for the Error
There are a few possible reasons why the SSH server may not accept the SSH-RSA algorithm. One primary cause is the server’s configuration file explicitly excluding the algorithm from the list of accepted algorithms. This might be a security measure to ensure only more secure algorithms are utilized. Alternatively, the server’s SSH software might be outdated and not supporting the SSH-RSA algorithm.
Troubleshooting the Error
Here are some steps you can take to troubleshoot and resolve the “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth)” error:
1. Enable logging: SSH logs can provide valuable information about the error. Enable debugging in your SSH client by adding the “-v” option when attempting to connect. This will generate a more detailed log, allowing you to identify the cause of the issue.
2. Check server configuration: Examine the SSH server’s configuration file (often located at /etc/ssh/sshd_config) for the line “PubkeyAcceptedAlgorithms.” Ensure that the line exists and includes the “ssh-rsa” algorithm. If it does not, add it to the list and restart the SSH service.
3. Update SSH software: If the SSH server’s software is outdated, it may not support certain algorithms. Investigate whether an update is available for your SSH server software and install it if necessary. This should ensure compatibility with the SSH-RSA algorithm.
4. Generate a new key pair: If the above steps do not resolve the issue, consider generating a new key pair using a different algorithm. The RSA algorithm, although widely supported, has been largely phased out in favor of more secure algorithms. Generate a new key pair using the Ed25519 or ECDSA algorithm, for example.
Frequently Asked Questions
Q1. Is the “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth)” error common?
A1. While this error is not uncommon, it highly depends on the server’s configuration. Some servers may exclude the SSH-RSA algorithm for security reasons.
Q2. Can I enable the SSH-RSA algorithm even if the server does not support it by default?
A2. It is generally not recommended to enable unsupported algorithms. However, if you have administrative control over the server’s configuration, you may include the “ssh-rsa” algorithm in the “PubkeyAcceptedAlgorithms” line. Keep in mind that supporting outdated algorithms can introduce security vulnerabilities.
Q3. Why is the SSH-RSA algorithm being phased out?
A3. The RSA algorithm, while widely used and trusted for many years, has certain limitations in terms of key length and its susceptibility to certain attacks. Newer algorithms, such as Ed25519 and ECDSA, offer better security and performance benefits, leading to a gradual shift away from RSA.
Q4. How can I ensure a smooth transition to a different algorithm?
A4. Before switching to a different algorithm, it is vital to ensure that all client systems are compatible with the chosen algorithm. Additionally, communicate the change to all affected users, as they might need to generate new key pairs using the preferred algorithm.
Conclusion
The “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth)” error message can be encountered while attempting to establish an SSH connection. This error suggests that the server does not support the SSH-RSA algorithm for public key authentication. By following the troubleshooting steps outlined in this article, you can resolve the issue and establish a secure SSH connection. Remember to prioritize security by using the recommended algorithms and keeping your SSH software up to date.
Images related to the topic send_pubkey_test: no mutual signature algorithm

Found 34 images related to send_pubkey_test: no mutual signature algorithm theme










Article link: send_pubkey_test: no mutual signature algorithm.
Learn more about the topic send_pubkey_test: no mutual signature algorithm.
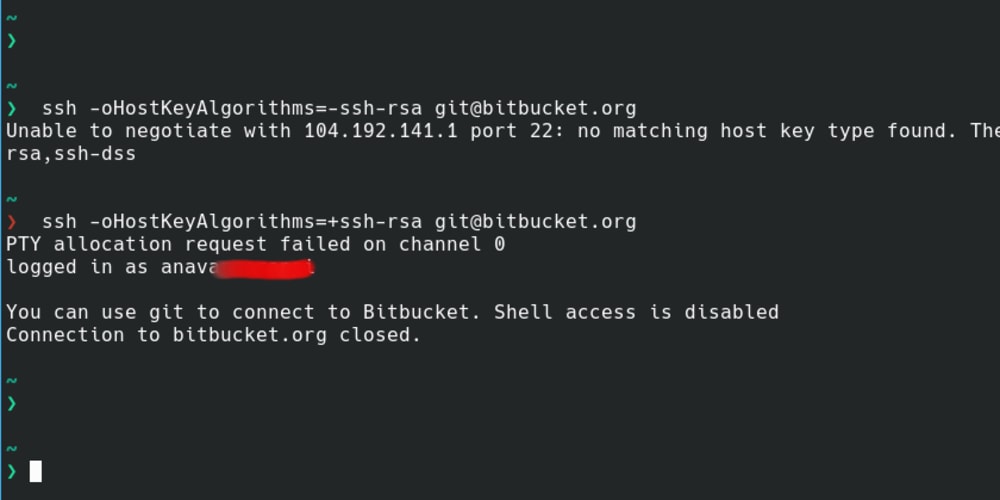
- SSH-RSA key rejected with message “no mutual signature …
- Sign_and_send_pubkey: no mutual signature supported
- SSH-RSA key rejected with message “no … – Virtuozzo Support
- ssh handshake is rejected with ‘no mutual signature algorithm …
- “no mutual signature algorithm” because of disabled ssh-rsa …
- SSH-RSA key rejected with message “no mutual … – Hackolade
- IBM AIX: send_pubkey_test: no mutual signature algorithm
- send_pubkey_test: no mutual signature algorithm – MikroTik
- SSH Key: no mutual signature algorithm : r/linuxquestions
- SSH: Signature Algorithm ssh-rsa Error – John Hanley
See more: nhanvietluanvan.com/luat-hoc