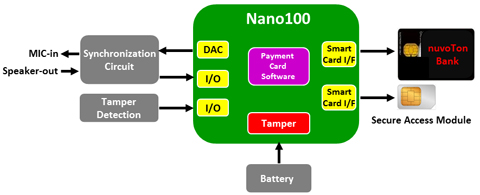
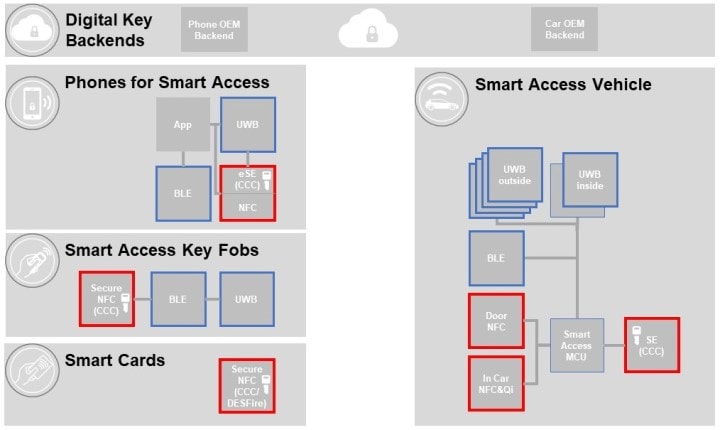
Secure Access Module Reader
In today’s digital age, where security breaches and identity thefts are becoming increasingly common, organizations are prioritizing the protection of sensitive data more than ever before. One way to ensure data security is by implementing secure access module (SAM) readers. These devices play a crucial role in securely accessing and managing data, providing an added layer of protection against unauthorized access. In this article, we will explore the different types of secure access module readers, their features, advantages, functioning, installation process, common applications, and the importance of security and encryption in SAM card readers.
Types of Secure Access Module Reader
Secure Access Module Readers come in various types, each with its own unique features and capabilities. Let’s take a closer look at some of the most common types of SAM card readers:
1. Smart Card Readers: These readers are designed to read and process smart cards, which contain an embedded chip capable of securely storing and transmitting data. They are widely used for secure authentication and identification purposes.
2. Magnetic Stripe Readers: Magnetic stripe readers are used to read information encoded on the magnetic stripe of a card. While they are not as secure as smart card readers, they are commonly used for various applications, such as access control systems and loyalty programs.
3. Proximity Card Readers: These readers use radio frequency technology to communicate with proximity cards. By simply waving the card in front of the reader, the information can be read securely, making them ideal for applications where convenience is key, such as building access control.
Features of Secure Access Module Reader
Secure Access Module Readers come equipped with a range of features designed to enhance security and ease of use. Some notable features include:
1. Secure Data Transfer: SAM card readers allow for secure data transfer between the reader and the card, ensuring that sensitive information is encrypted and protected throughout the process.
2. Multi-Factor Authentication: Many SAM card readers support multi-factor authentication, requiring users to present more than one form of identification before granting access. This adds an extra layer of security, making it more difficult for unauthorized users to gain access.
3. Remote Management: Some SAM card readers offer remote management capabilities, allowing administrators to easily monitor and manage the devices from a centralized location. This simplifies the management process and ensures that all readers are up to date with the latest security measures.
Key Advantages of Secure Access Module Reader
Implementing a Secure Access Module Reader in your organization can offer several advantages. Some key advantages include:
1. Enhanced Security: SAM card readers provide an additional layer of security, ensuring that only authorized individuals can access sensitive data or restricted areas. This helps prevent unauthorized access and potential security breaches.
2. Greater Data Protection: With secure data transfer and encryption features, SAM card readers help protect valuable information from being intercepted or tampered with during the transfer process.
3. Improved Compliance: Many industries, such as healthcare and finance, have strict regulatory requirements for data protection. By using SAM card readers, organizations can ensure compliance with these regulations, avoiding costly penalties and reputational damage.
4. Ease of Use: SAM card readers are designed to be user-friendly, allowing for quick and convenient access to authorized individuals. This eliminates the need for complex authentication processes and enhances the overall user experience.
How Secure Access Module Reader Works
SAM card readers work by establishing a secure connection between the reader and the card, ensuring that only authorized individuals can access the data or functionality provided by the card. The reader authenticates the card by verifying its unique identifier or a digital signature embedded within it. Once the card is authenticated, the reader can securely access the desired data or functionality, such as granting access to a restricted area or retrieving encrypted information.
Important Considerations When Choosing a Secure Access Module Reader
When selecting a Secure Access Module Reader, there are several factors to consider to ensure that it meets the specific requirements of your organization. Here are some important considerations to keep in mind:
1. Compatibility: Ensure that the reader is compatible with the type of cards you plan to use. Different types of cards require different reader technologies.
2. Security Features: Assess the security features offered by the reader, such as encryption protocols, authentication methods, and support for multi-factor authentication. Choose a reader that aligns with your organization’s security needs.
3. Integration: Consider how easily the reader can be integrated into your existing infrastructure. Look for readers that are compatible with the systems or applications you already use.
4. Scalability: If your organization anticipates growth in the future, choose a reader that can easily accommodate an increasing number of users or cards without sacrificing security.
Installation and Integration of Secure Access Module Reader
The installation and integration process of a Secure Access Module Reader can vary depending on the type and model of the reader. However, the general steps involved include:
1. Connect the Reader: Begin by connecting the reader to a compatible computer or an access control system using the provided interface cable.
2. Install the Driver: Install the necessary driver software to ensure proper communication between the reader, the card, and the operating system.
3. Testing and Configuration: Test the reader to ensure that it is functioning correctly. Configure the reader according to your organization’s specific requirements, such as setting up encryption protocols or authentication methods.
4. Integration with Existing Systems: If required, integrate the reader with your existing access control system or any other relevant systems to enable seamless operation.
Common Applications of Secure Access Module Reader
Secure Access Module Readers find applications in various industries and sectors. Some common applications include:
1. Physical Access Control: SAM card readers are commonly used for building access control systems, allowing authorized individuals to enter restricted areas securely.
2. Computer Logins: Many organizations use SAM card readers for secure user authentication when logging into computers or accessing networks, providing an added layer of protection against unauthorized access.
3. Transaction Authorization: SAM card readers play a pivotal role in secure financial transactions, ensuring that only authorized individuals can access and perform transactions using their smart cards.
4. Electronic Identification: SAM card readers are utilized for electronic identification and digital signature verification, allowing for secure online transactions and document signing.
Security and Encryption in Secure Access Module Reader
Security and encryption are crucial aspects of Secure Access Module Readers, as they provide the necessary protection against unauthorized access and data breaches. SAM card readers employ various security measures, such as:
1. Encryption Protocols: SAM card readers utilize advanced encryption protocols to secure data during the communication between the reader and the card. Common encryption algorithms include RSA, AES, and DES.
2. Secure Authentication: The reader verifies the authenticity of the card through secure authentication processes, such as mutual authentication or challenge-response authentication, ensuring that only authorized cards can be accessed.
3. Tamper Resistance: SAM card readers are designed to resist physical tampering and attacks, ensuring that unauthorized individuals cannot extract sensitive information from the reader.
FAQs:
Q1. What is a Secure Access Module (SAM) reader?
A Secure Access Module (SAM) reader is a device used to securely access and manage data stored on smart cards, magnetic stripe cards, or proximity cards. It provides an additional layer of security, ensuring that only authorized individuals can access the data or functionality provided by the card.
Q2. Are all SAM card readers the same?
No, SAM card readers come in various types, each designed to cater to different card technologies. The most common types include smart card readers, magnetic stripe readers, and proximity card readers.
Q3. How does a SAM card reader enhance security?
A SAM card reader enhances security by establishing a secure connection between the reader and the card, ensuring that only authorized individuals can access the data or functionality provided by the card. Additionally, they often employ encryption protocols, secure authentication methods, and support multi-factor authentication, adding multiple layers of security to the overall system.
Q4. Can a SAM card reader be integrated into an existing access control system?
Yes, SAM card readers can be integrated into existing access control systems or any other relevant systems. However, it is important to choose a reader that is compatible with the systems or applications already in use to ensure smooth integration.
Q5. What are some common applications of SAM card readers?
SAM card readers find applications in various industries and sectors, including physical access control, computer logins, transaction authorization, and electronic identification. These devices are used where secure authentication and access management are crucial.
In conclusion, Secure Access Module Readers are essential devices for ensuring data security and access management in today’s digital world. With different types, each catering to specific card technologies, these readers provide enhanced security, greater data protection, improved compliance, and ease of use. By employing secure data transfer, multi-factor authentication, and other advanced features, SAM card readers play a pivotal role in securing sensitive information and preventing unauthorized access.
Glossary: Dr. Peter Klein, Security Access Module (Sam)
What Is The Use Of Sam Card?
A Subscriber Identity Module (SIM) is a small, integrated circuit that securely stores the International Mobile Subscriber Identity (IMSI) and is essential for the functioning of a mobile phone. However, there is another type of smart card that holds even more significant importance when it comes to data security and identity verification – the Security Access Module Card or SAM card.
A SAM card is a specialized smart card that is used to enhance the security of various devices and systems. It provides secure access to sensitive information and ensures the integrity of data transfers. SAM cards are widely used in industries such as telecommunications, banking, transportation, and even vending machines.
The primary use of a SAM card is to store encryption keys and algorithms that are required to secure data transmission. It acts as a secure repository for cryptographic information, protecting it from unauthorized access or tampering. SAM cards are extensively used in mobile phones, allowing secure communication between the user’s SIM card and the mobile network.
Major telecommunication companies utilize SAM cards in their network infrastructure to prevent unauthorized access to their networks and protect against fraud. By securely storing and managing encryption keys, SAM cards ensure that only authorized SIM cards can access the network, thus protecting user privacy and preventing illegal activities.
In the banking sector, SAM cards are used to secure financial transactions and ensure the confidentiality of sensitive customer information. When you use a payment card at an ATM or a point-of-sale terminal, a SAM card may be used to encrypt the data transmitted between the card and the processing system, protecting against potential eavesdropping or data manipulation.
Transportation systems such as electronic toll collection and public transportation payment systems also benefit from the use of SAM cards. These cards store authentication information for vehicles or passengers and enable secure and efficient transactions. The data transmitted over the communication network between the terminals and the backend systems are protected by the encryption keys stored in the SAM card, ensuring the integrity and confidentiality of the information.
In addition to mobile networks, banking, and transportation, SAM cards find application in various industries where secure data transfer is critical. For example, vending machines that accept electronic payments require SAM cards to encrypt data sent between the machine and the payment system, minimizing the risk of fraud or unauthorized access.
FAQs:
Q: How is a SAM card different from a SIM card?
A: While both SAM cards and SIM cards are smart cards, they serve different purposes. A SIM card is primarily used to identify and authenticate the user in a mobile network, whereas a SAM card stores encryption keys and algorithms to secure data transmissions between devices.
Q: Can SAM cards be hacked?
A: SAM cards are designed with robust security features to minimize the risk of hacking or unauthorized access. However, like any technology, they are not completely immune to attacks. Manufacturers employ various layers of security measures to protect the information stored on SAM cards, making them significantly more secure than other storage mediums.
Q: Are SAM cards only used in high-security applications?
A: While SAM cards are commonly used in high-security applications, they are not limited to them. Their versatility allows them to be implemented in various systems that require secure data transfers, such as vending machines, gaming devices, and digital rights management systems.
Q: Can SAM cards be easily replaced or upgraded?
A: Generally, SAM cards can be replaced or upgraded. However, the process may vary depending on the specific system or device where they are used. In some cases, replacement or upgrade may require special tools or configurations.
Q: Can SAM cards be used to track users?
A: SAM cards themselves do not track users. They store encryption keys and algorithms to ensure secure data transmission. However, the network operators or service providers utilizing the SAM cards may have systems in place to track the usage patterns for purposes such as network optimization or security monitoring.
In conclusion, SAM cards play a crucial role in securing data transfers and ensuring the integrity of sensitive information in various industries. From telecommunications to banking and transportation systems, SAM cards protect against unauthorized access, fraud, and data tampering. While they may seem relatively small in size, the importance and impact of these smart cards on modern technology and data security are significant.
What Is Sam In Card Machine?
In the modern age of digital transactions, businesses rely heavily on card machines to process payments seamlessly and conveniently. One name that has gained considerable recognition in the industry is “Sam.” But what exactly is Sam in a card machine? In this article, we will delve into the details of Sam, exploring its functionalities, benefits, and frequently asked questions.
Sam, short for Security Access Module, is a crucial component found within card machines. As the name suggests, Sam is primarily responsible for ensuring the security of transactions by encrypting and decrypting sensitive data. It acts as a safeguard against fraud, thus protecting both businesses and customers in their financial endeavors.
Functionally, Sam plays a pivotal role in the authentication process during card transactions. When a customer inserts their card into a card machine, Sam securely communicates with the customer’s bank or financial institution, verifying the validity of the transaction. This authentication process involves the exchange of cryptographic keys and ensures that the transaction is conducted between authorized parties only.
Moreover, Sam is designed to protect the cardholder’s data, including personal information and card details, from being compromised. By utilizing advanced encryption techniques, it ensures that the sensitive data remains confidential during transmission and storage. This is particularly crucial in mitigating risks associated with identity theft and unauthorized access to financial information.
Benefits of Sam in Card Machines:
1. Enhanced Security: Sam employs advanced encryption methods, significantly reducing the risk of data breaches and fraudulent activities.
2. Compliance with Security Standards: Card machines equipped with Sam adhere to industry standards such as the Payment Card Industry Data Security Standard (PCI DSS), ensuring businesses meet security requirements.
3. Efficient Transaction Processing: Sam expedites the process of authenticating transactions, allowing for quick and hassle-free payments.
4. Cost-effective Solution: By minimizing the potential financial losses caused by fraudulent activities, Sam serves as a cost-effective security measure for businesses.
FAQs:
Q1: Are all card machines equipped with Sam?
A1: No, not all card machines have Sam. However, most modern card machines incorporate Sam to ensure secure and reliable transactions.
Q2: Can Sam prevent all types of fraud?
A2: While Sam significantly reduces the risk of fraud, it cannot eliminate it entirely. It is always recommended to implement additional security measures and stay vigilant against evolving fraudulent techniques.
Q3: How does Sam protect customer data?
A3: Sam protects customer data by encrypting it during transmission and storage. This ensures that even if the data is intercepted, it remains unreadable and unusable to unauthorized individuals.
Q4: Can Sam be hacked?
A4: Sam is designed with robust security measures to deter unauthorized access. While no system is entirely immune to hacking, the encryption and security protocols implemented in Sam make it highly resistant to attacks.
Q5: Do businesses need to pay for Sam separately?
A5: In most cases, businesses do not need to separately pay for Sam. The cost of incorporating Sam is often included in the overall cost of the card machine or the service provided by the payment solution provider.
In conclusion, Sam plays a critical role in ensuring the security and integrity of card transactions. As businesses increasingly rely on cashless payment methods, having Sam in a card machine becomes vital for protecting both customers and businesses from the risks associated with fraudulent activities. With its enhanced security features and compliance with industry standards, Sam acts as a trustworthy guardian of sensitive financial data, allowing for seamless and worry-free payment experiences.
Keywords searched by users: secure access module reader SAM card
Categories: Top 33 Secure Access Module Reader
See more here: nhanvietluanvan.com
Sam Card
Introduction (85 words)
The Subscriber Identity Module (SIM) card has become an integral part of our daily lives, powering our smartphones and enabling seamless connectivity. However, there’s a lesser-known sibling in the telecommunications world called the Security Access Module (SAM) card. In this article, we will delve into the fascinating world of SAM cards, exploring their purpose, functionalities, advantages, and compatibility. By the end, you’ll have a clear understanding of SAM cards and how they contribute to the security and efficiency of our modern communication networks.
What is a SAM Card? (135 words)
Unlike a SIM card that is used in mobile devices, a Security Access Module (SAM) card is primarily utilized in secure applications or devices. It is a smart card containing a powerful microprocessor, memory, and cryptographic algorithms. SAM cards act as a secure element, providing robust security features to prevent unauthorized access or manipulation of sensitive data.
Purpose and Functionality of SAM Cards (200 words)
SAM cards are employed in various sectors, such as payment processing systems, identification and access control, public transportation, and more. Their primary purpose is to enhance the security of dedicated devices or applications by storing encryption keys, authentication data, and confidential information within a tamper-proof environment. This prevents cybercriminals from exploiting vulnerabilities in less secure software-based solutions.
Furthermore, the functionality of SAM cards extends to ensuring secure transactions, safeguarding digital signatures, performing cryptographic computations, and validating digital certificates. By offloading these security processes to the SAM card, it reduces the computational burden on the device itself, increasing overall efficiency and speed.
SAM Cards vs. SIM Cards (160 words)
The key difference between a SAM card and a SIM card lies in their intended usage. While SIM cards are designed for cellular communication, SAM cards are focused on enhancing security in specific applications or devices. SAM cards are primarily used in proprietary systems, such as point-of-sale terminals, smart lock systems, or industrial control systems, where security is paramount.
Advantages of SAM Cards (160 words)
The utilization of SAM cards offers several advantages in terms of security, flexibility, and convenience. As a secure element, SAM cards provide tamper-proof storage for cryptographic keys, ensuring the integrity and confidentiality of sensitive data. This makes them an excellent choice for applications that handle financial transactions, access control, or digital signatures.
Additionally, SAM cards can be easily updated and managed remotely, reducing maintenance costs and diminishing the need for physical upkeep. Their plug-and-play nature allows for effortless integration into existing systems, making them a versatile solution for both new and legacy devices.
FAQs (149 words)
Q1. Are SAM cards interchangeable with SIM cards?
No, SAM cards and SIM cards are not interchangeable. Their functionalities and physical form factors differ, serving distinct purposes. SIM cards are used for cellular communication and are associated with mobile networks, while SAM cards are primarily employed in secure applications or systems.
Q2. Can SAM cards be reused?
Yes, SAM cards can be reused multiple times, allowing for cost-effectiveness and long-term use in compatible devices or applications. They are commonly designed for durability and can withstand extended periods of use.
Q3. Can I use a SIM card in place of a SAM card?
Using a SIM card in place of a SAM card is not recommended unless explicitly stated by the device manufacturer. While both cards share similarities, such as a microprocessor and memory, the security features and functionalities of SAM cards make them essential for specific secure applications.
Q4. How does a SAM card ensure data security?
A SAM card incorporates advanced cryptographic algorithms, secure storage for encryption keys, and secure communication protocols, making it virtually impossible for unauthorized parties to access or manipulate encrypted data.
Q5. Can a SAM card be hacked?
While no system is completely impervious to hacking, SAM cards are designed with multiple layers of security to minimize the risk of unauthorized access. Their tamper-proof design and strong encryption algorithms make them highly resistant to various hacking techniques.
Conclusion (40 words)
SAM cards play a pivotal role in securing various applications and devices by providing a robust and tamper-proof storage solution for sensitive information. Their versatility and security features make them an indispensable asset in today’s evolving digital landscape.
Images related to the topic secure access module reader

Found 11 images related to secure access module reader theme
















Article link: secure access module reader.
Learn more about the topic secure access module reader.
- Secure access module – Wikipedia
- SAM Card (Secure Application Module) Development Tool
- Secure access module – Wikipedia
- What is the difference between SAM card and SIM card?
- Secure Access Module – Paragon ID
- SAM Card (Secure Application Module) Development Tool
- What are Secure Access Modules (SAM) needed for?
- MIFARE SAM
- Security Access Module – Made-in-China.com
- Fare Collection Systems – Secure application modules – SSATP
See more: https://nhanvietluanvan.com/luat-hoc/