Remote Host Identification Has Changed
In today’s digital world, remote host identification plays a crucial role in ensuring secure connections. Remote host identification refers to the process of verifying the identity of a remote host before establishing a connection. This process has evolved over the years, with significant changes in how it is implemented and the associated security considerations.
Understanding Remote Host Identification
Remote host identification is the process of confirming the identity of a remote host before establishing a connection. It is essential for validating the authenticity and integrity of the host, ensuring that the connection is secure. Without proper identification, malicious actors could impersonate legitimate hosts, leading to potential security breaches.
Remote host identification serves as a fundamental component of secure networking protocols such as Secure Shell (SSH). It helps prevent unauthorized access, data breaches, and interception of sensitive information during communication between hosts.
Factors Leading to Remote Host Identification Changes
The dynamic nature of network infrastructure often necessitates changes in remote host identification. One significant factor leading to such changes is the reliance on Internet Protocol (IP) addresses. IP addresses are unique numerical identifiers that allow devices to communicate over the internet. When IP addresses change, remote host identification must be updated to reflect the new address accurately.
Common reasons for remote host identification changes include network reconfigurations, server migrations, domain name changes, and system upgrades. These changes often result in new IP addresses, which require a corresponding adjustment in host identification.
Network configuration changes can have a significant impact on remote host identification. Firewalls, network address translation (NAT), and proxy servers can modify or obscure the true identity of a remote host. It is crucial to carefully manage these configurations to ensure accurate host identification.
Risks Associated with Incorrect Remote Host Identification
Incorrect remote host identification can pose several risks to the security of network connections. One of the primary risks is the potential for man-in-the-middle attacks. These attacks involve intercepting network traffic between two parties while pretending to be the intended recipient. With incorrect host identification, it becomes easier for malicious actors to carry out such attacks undetected.
Moreover, incorrect host identification can lead to data breaches, unauthorized access to resources, and compromised integrity of transmitted data. Without proper authentication of remote hosts, organizations can fall victim to phishing scams, malware attacks, and other malicious activities.
Importance of Verifying Remote Host Identification Before Connecting
Verifying remote host identification before establishing a connection is crucial to ensure the security of network communications. By confirming the identity of the remote host, users can trust that the connection is established with the intended party, reducing the risk of unauthorized access.
Verifying host identification can be done through various methods, including comparing digital certificates, checking key fingerprints, and validating IP addresses. These verification steps provide the necessary assurance that the remote host is who it claims to be, establishing a secure connection.
Key Methods for Identifying Remote Hosts
Several methods exist for identifying remote hosts. One common method is the use of digital certificates issued by trusted third-party certificate authorities (CAs). These certificates contain cryptographic keys that validate a host’s identity. By comparing the digital certificate of the remote host with a trusted root certificate, users can ensure the authenticity of the host’s identity.
Another method involves checking key fingerprints. Key fingerprints are unique cryptographic representations of a host’s public key. By comparing the key fingerprint of the remote host with a trusted source, users can verify its identity before connecting.
It is important to note that each method has its benefits and limitations. Digital certificates offer a high level of trust as they are issued by trusted CAs. However, managing and maintaining a reliable collection of trusted root certificates can be challenging. Key fingerprints, on the other hand, are easily verifiable but can be susceptible to spoofing if not properly validated.
Changing Remote Host Identification and Security Considerations
Handling a changed remote host identification requires specific steps to ensure security. When encountering a changed host identification, it is advisable to update the trusted identification records accordingly. This may involve removing the old host identification and replacing it with the new one.
Changing remote host identification can have implications on existing security protocols. In some cases, systems may raise warnings or errors when trying to connect to a host with changed identification. Users should not ignore these warnings and investigate the changes thoroughly before proceeding. Failure to do so may expose sensitive information or lead to unauthorized access.
To maintain secure connections despite changes in remote host identification, it is crucial to stay vigilant and update identification records regularly. Continuous monitoring and updating procedures should be implemented to ensure that connections remain secure and protected against potential security threats.
Troubleshooting Remote Host Identification Changes
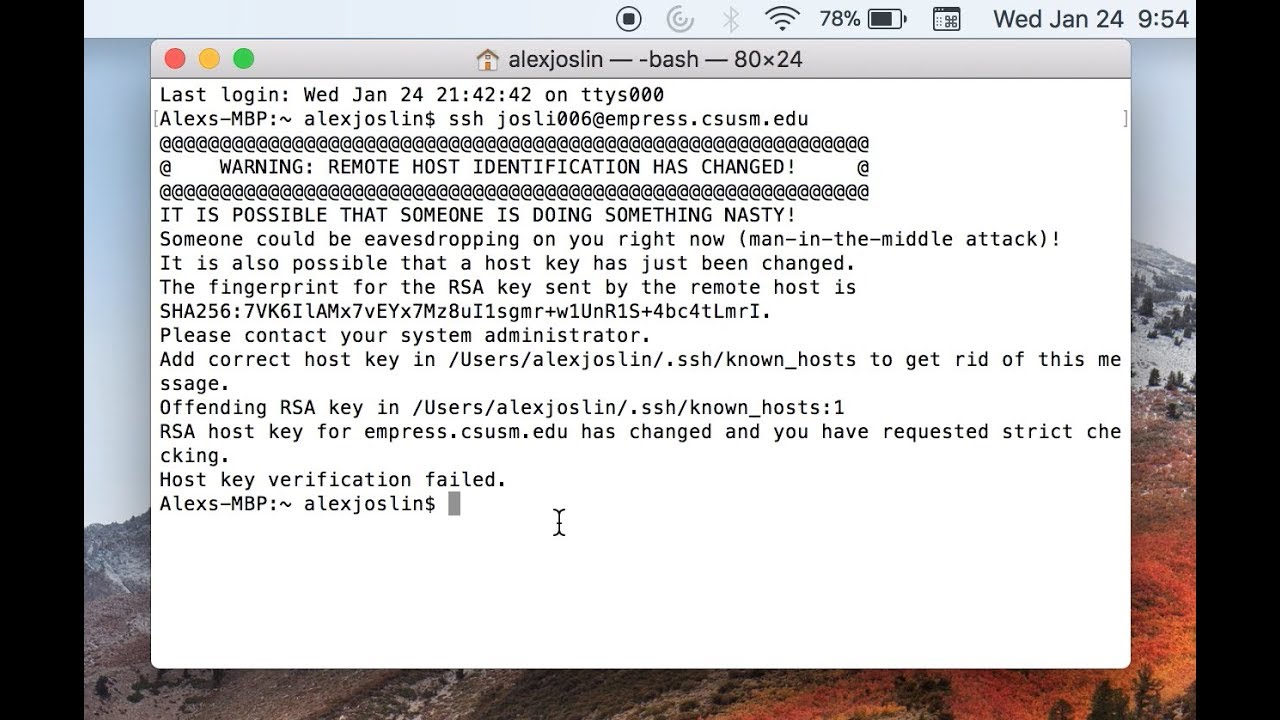
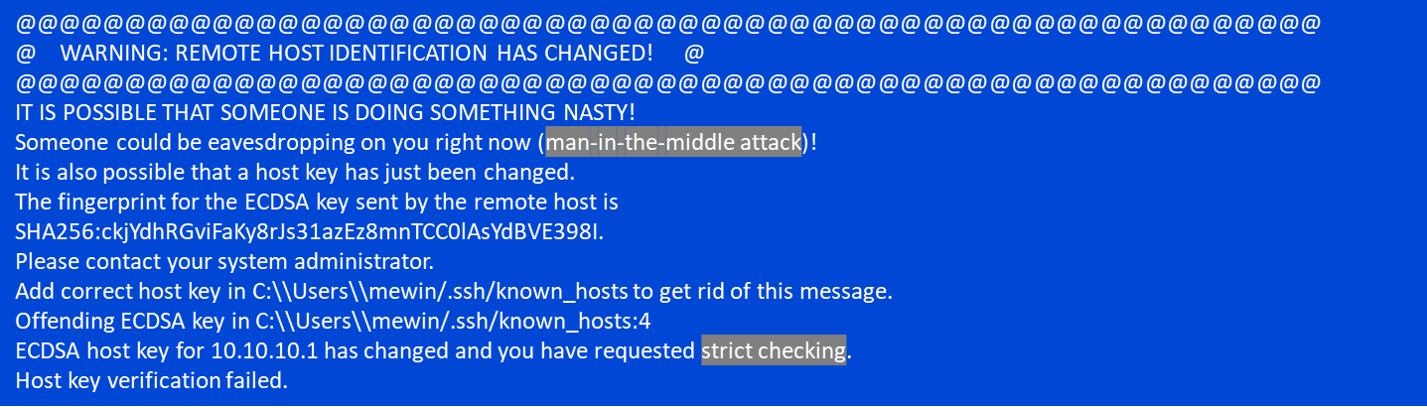
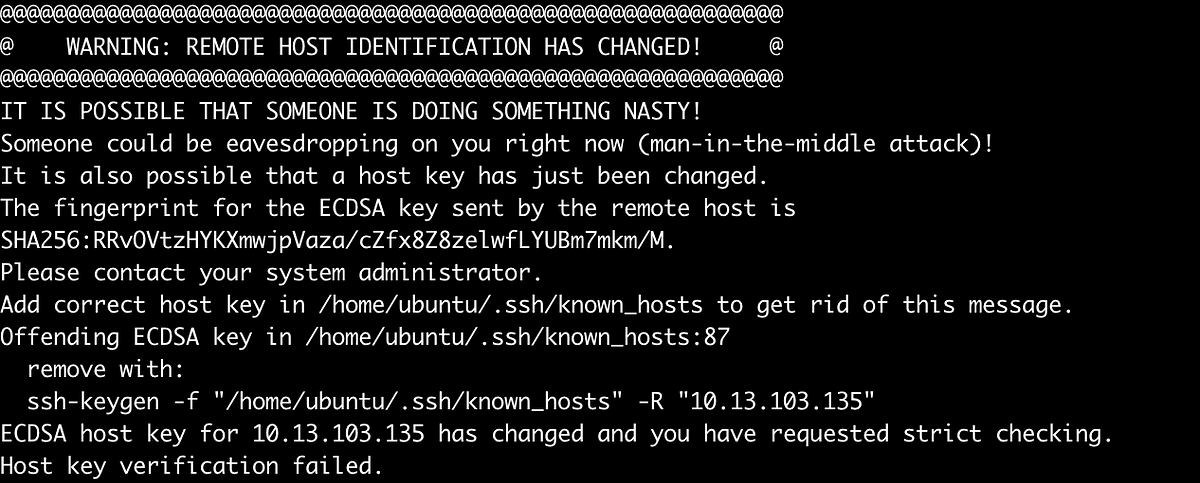
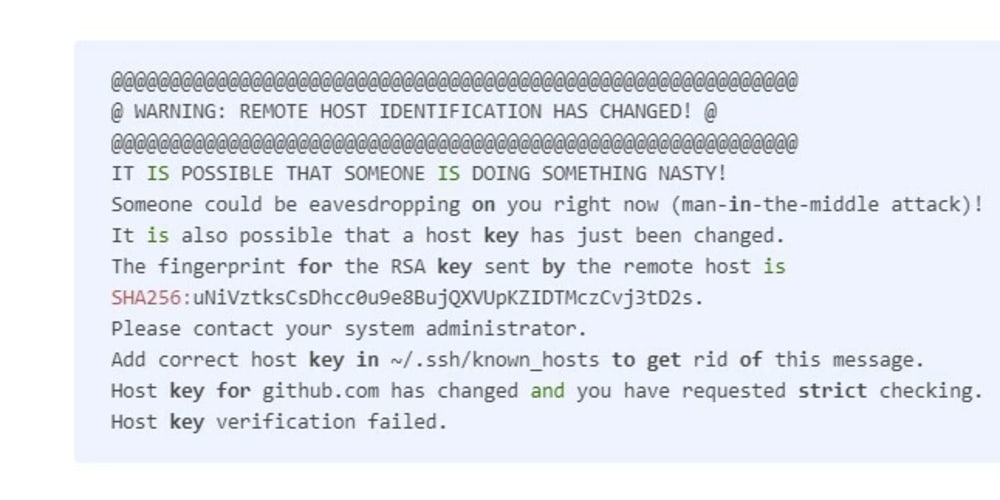
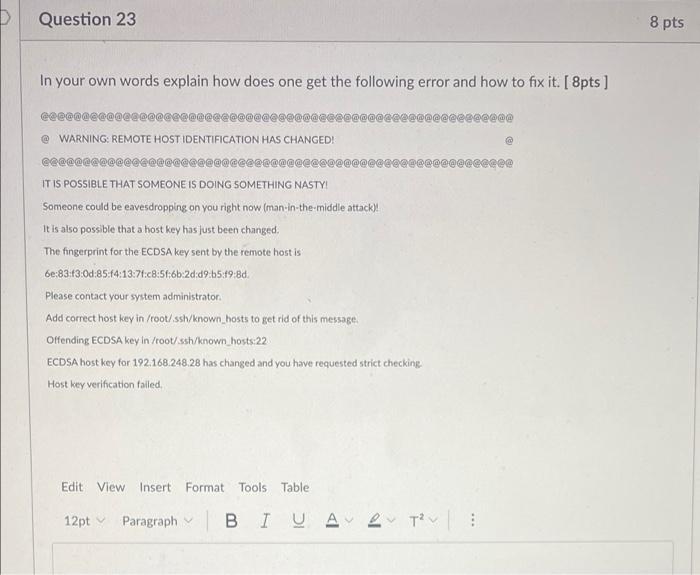
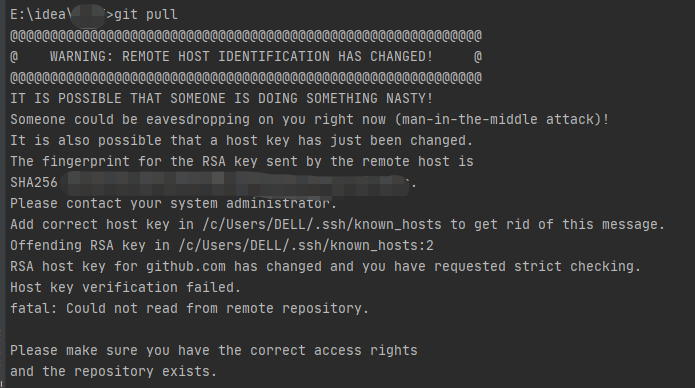
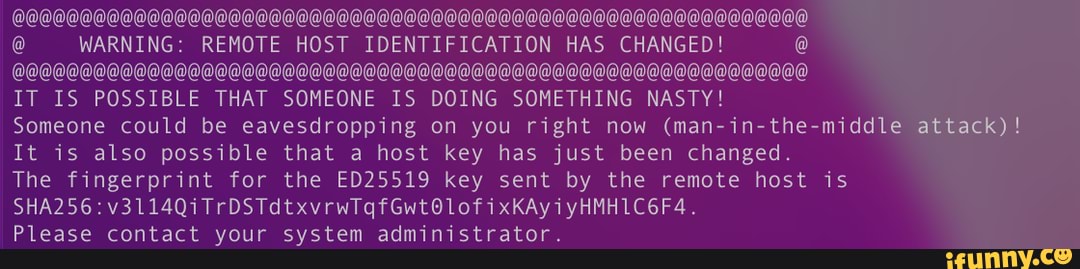
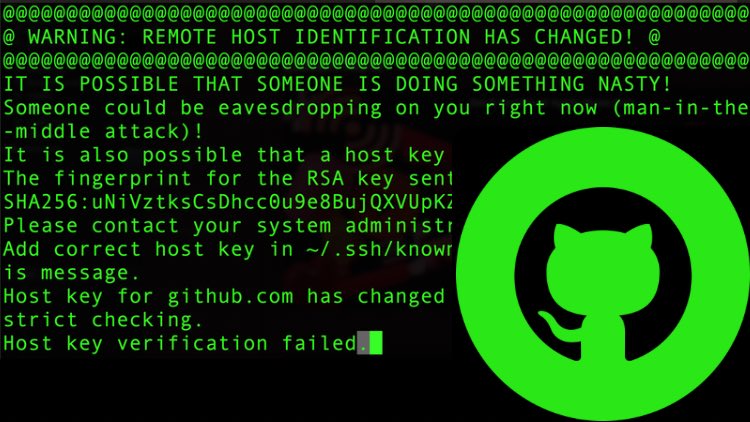
When remote host identification changes occur, users may encounter common errors or warnings during connection attempts. These errors can include messages such as “Warning: remote host identification has changed,” “host key verification failed,” or “The fingerprint for the ECDSA key sent by the remote host is remote host identification has changed.”
To troubleshoot and resolve identification issues, users can utilize tools like Ssh-keygen to regenerate or update host keys. Removing known hosts using the command “Remove known host ssh” may also help address identification discrepancies. It is crucial to follow proper procedures and consult relevant documentation when troubleshooting remote host identification changes.
The Role of SSH in Remote Host Identification
SSH (Secure Shell) plays a critical role in facilitating remote host identification through secure communication protocols. SSH utilizes cryptographic authentication methods, including digital certificates and key fingerprints, to verify the identity of remote hosts.
In addition to authentication, SSH provides features and functionalities that enhance secure connections. These include encryption of data transmission, prevention of eavesdropping, and protection against unauthorized access.
Best Practices for Managing Remote Host Identification Changes
To effectively manage remote host identification changes, organizations should follow best practices. These include:
1. Regularly monitor and update identification records: Maintain an accurate and up-to-date record of trusted host identification information.
2. Continuously assess and update security protocols: Regularly evaluate and update security protocols to ensure compatibility with changing remote host identification.
3. Educate users on identification verification: Train users to verify remote host identification before connecting, and instruct them on appropriate action if identification changes occur.
4. Implement strong access controls: Limit access to remote hosts to authorized individuals only, reducing the risk of unauthorized connections.
5. Use secure communication protocols: Utilize secure protocols such as SSH for remote connections, ensuring encrypted communication channels.
FAQs
1. What does “Warning: remote host identification has changed” mean?
This warning indicates that the identification of the remote host has changed since the last connection attempt. It is crucial to investigate and verify the changes before proceeding to ensure a secure connection.
2. How can I update my trusted host identification records?
To update trusted identification records, you can regenerate or update host keys using tools like Ssh-keygen. Removing known hosts using the command “Remove known host ssh” can also help address identification discrepancies.
3. Why is remote host identification important?
Remote host identification is important for ensuring secure connections and preventing unauthorized access. By verifying the identity of remote hosts, users can trust that their communication is with the intended party and minimize the risk of security breaches.
4. What are the risks associated with incorrect remote host identification?
Incorrect remote host identification can lead to man-in-the-middle attacks, data breaches, unauthorized access, and compromised data integrity. It opens the door for malicious actors to impersonate legitimate hosts, potentially leading to various security threats.
5. How does SSH facilitate remote host identification?
SSH utilizes cryptographic authentication methods, including digital certificates and key fingerprints, to verify the identity of remote hosts. It provides secure communication protocols, encryption, and protection against unauthorized access, enhancing remote host identification and security.
In conclusion, remote host identification plays a critical role in ensuring secure connections in today’s digital landscape. Understanding the factors leading to changes in host identification, the risks associated with incorrect identification, and the best practices for managing these changes are key in maintaining secure network communications. By staying vigilant, regularly updating identification records, and following appropriate security protocols, organizations can establish and maintain secure connections despite changes in remote host identification.
How To Fix Warning Remote Host Identification Has Changed
What Is Remote Host Identification Has Changed?
Remote host identification refers to the process of verifying and validating the identity of a remote computer or server that is attempting to establish a connection with another system. As technology has evolved, the methods and tools used for remote host identification have also changed considerably, offering more secure and efficient ways to ensure the authenticity and integrity of remote connections. In this article, we will explore the concept of remote host identification and discuss how it has transformed over time.
The traditional method of remote host identification was based on using IP addresses. Every computer connected to the internet is assigned a unique IP address, which acts as a virtual identifier for that specific device. Previously, administrators would use these IP addresses to determine whether a remote connection was coming from a trusted source or not. However, relying solely on IP addresses had several drawbacks.
One of the primary limitations of IP-based remote host identification was its vulnerability to IP spoofing attacks. Hackers can manipulate the source IP address of a packet to deceive the receiving system into believing it originates from a trusted source. This practice allows malicious actors to gain unauthorized access to systems or carry out other nefarious activities. These security concerns initiated a need for more robust remote host identification methods.
Public Key Infrastructure (PKI) has played a significant role in the transformation of remote host identification. PKI uses a pair of cryptographic keys, a public key, and a private key, to establish a secure connection between two systems. When a remote computer attempts to establish a connection, it presents its public key for authentication. The receiving system then verifies this key against a trusted certificate authority (CA) to ensure its validity.
This approach offers a much higher level of security by leveraging encryption and authentication mechanisms. PKI eliminates the risks associated with IP spoofing and other malicious activities. Moreover, it enables secure data transfer and prevents unauthorized access.
Another advancement in remote host identification is the use of digital certificates. A digital certificate is an electronic document that binds a public key to an identity, verified by a trusted third-party CA. It contains information such as the certificate holder’s name, the public key, the CA’s signature, and the certificate’s expiration date. When a remote connection is established, the digital certificate is exchanged between the systems to validate the identity of the remote host.
The evolution of remote host identification has also led to the adoption of more advanced protocols and standards. Secure Shell (SSH) is one such protocol widely used for secure remote logins and file transfers. SSH incorporates various cryptographic techniques to establish secure connections and ensure confidentiality, integrity, and authenticity. It relies on public-key cryptography for secure authentication, mitigating the risks associated with password-based authentication.
Nowadays, with the proliferation of cloud computing and remote work, remote host identification has become even more critical. Organizations are increasingly relying on remote access solutions to enable employees to connect to corporate networks securely. Virtual Private Networks (VPNs), for example, authenticate remote hosts by using a username, password, and an additional factor, such as a token or biometric authentication. This multi-factor authentication enhances the security of remote connections and reduces the risks of unauthorized access.
Overall, remote host identification has undergone significant changes to keep up with the evolving security landscape. From relying solely on IP addresses to leveraging PKI, digital certificates, advanced protocols, and multi-factor authentication, the focus has shifted towards strengthening security and ensuring trusted remote connections.
FAQs:
Q: Why is remote host identification important?
A: Remote host identification is crucial to ensure the authenticity and integrity of remote connections, preventing unauthorized access and mitigating the risks of hacking and data breaches.
Q: What are the risks of IP-based remote host identification?
A: Relying solely on IP addresses for remote host identification is vulnerable to IP spoofing attacks, enabling malicious actors to deceive systems into accepting unauthorized connections.
Q: How does Public Key Infrastructure (PKI) enhance remote host identification?
A: PKI uses cryptographic keys and certificates to establish secure connections, eliminating the risks associated with IP spoofing and ensuring secure data transfer.
Q: What role does digital certificates play in remote host identification?
A: Digital certificates bind a public key to an identity, providing a trusted verification of the remote host’s identity during connection establishment.
Q: How have advanced protocols and multi-factor authentication improved remote host identification?
A: Advanced protocols, such as SSH, and multi-factor authentication mechanisms have strengthened remote host identification by incorporating encryption, secure authentication, and additional verification factors.
Why Does Warning Remote Host Identification Has Changed?
When establishing a secure connection with a remote server through SSH (Secure Shell), you may come across a warning message stating, “Warning: Remote Host Identification Has Changed.” This notification is an essential security feature and should not be ignored. It signifies that the remote server’s identity has changed since the last time you connected to it, and there could be a possibility of a security breach. In this article, we will delve into the reasons behind this warning and provide you an in-depth understanding of its implications.
Reasons for the Warning:
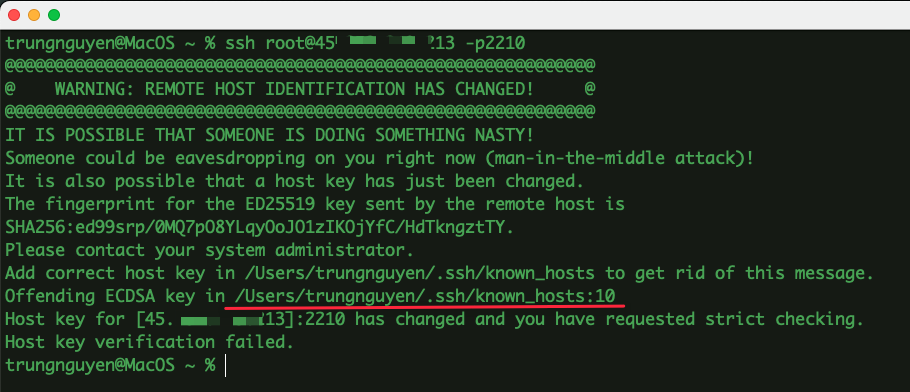
1. Server Reinstallation: In some instances, the server administrator may have reinstalled the operating system or SSH server software, leading to a change in the server’s host keys. Host keys are cryptographic identifiers used to verify a server’s authenticity. When these keys are regenerated, SSH warns users about the change to ensure they are connecting to the correct server.
2. Server Migration or Hardware Changes: If a remote server gets migrated to a new physical machine or its hardware configuration undergoes significant modifications, the host keys might change. This is because the host keys are tied to the underlying server hardware. Consequently, when attempting to establish an SSH connection after such changes, the warning message will be displayed.
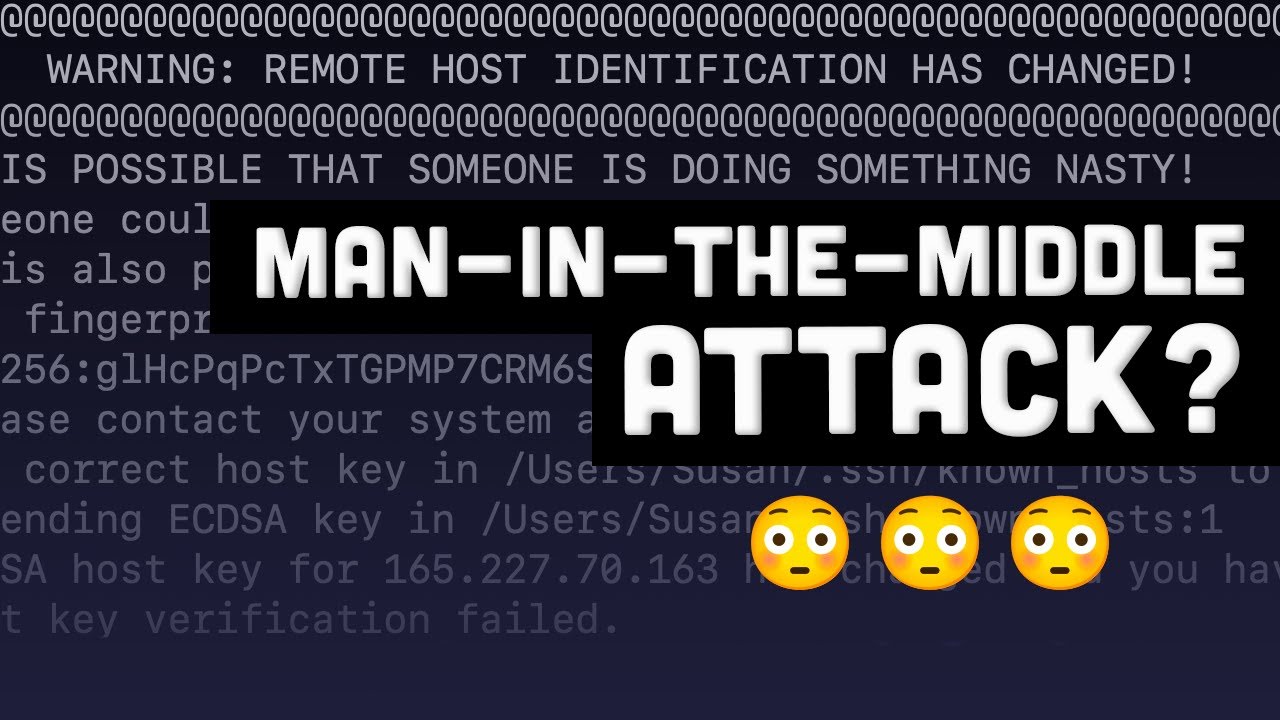
3. Man-in-the-Middle Attack: One of the main reasons this warning should never be ignored is the possibility of a man-in-the-middle (MITM) attack. During an MITM attack, an attacker intercepts the communication between server and client, impersonates the server, and captures sensitive information like usernames, passwords, or any data exchanged. If the warning suddenly appears, it might indicate that someone is tampering with the connection or attempting to carry out an attack.
4. IP Address or DNS Changes: The warning can also arise if the server’s IP address or DNS (Domain Name System) record has changed since the previous connection. DNS records translate the human-readable domain name (e.g., www.example.com) into an IP address. If either the server’s IP address or DNS record has changed without prior notice, SSH will generate a warning to prevent unsuspecting users from connecting to potentially malicious servers.
5. Server Security Breach: In rare cases, the warning could signal a security breach on the remote server. If unauthorized access occurs, attackers might manipulate the host keys or other critical components. SSH will continue to issue the warning until the compromised server is secured and its keys are amended.
Implications of Ignoring the Warning:
Ignoring the “Warning: Remote Host Identification Has Changed” message can have severe consequences. By bypassing this security measure, you risk falling victim to an MITM attack, compromising sensitive data, or connecting to a potentially malicious or unauthorized server. By warning users about the change in host identification, SSH aims to protect against these threats and ensure that connections are made with trusted servers.
What to Do When You See the Warning:
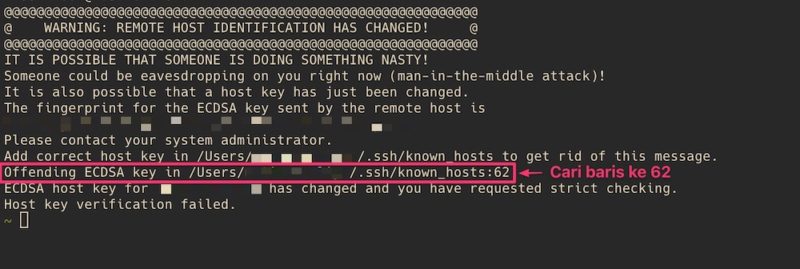
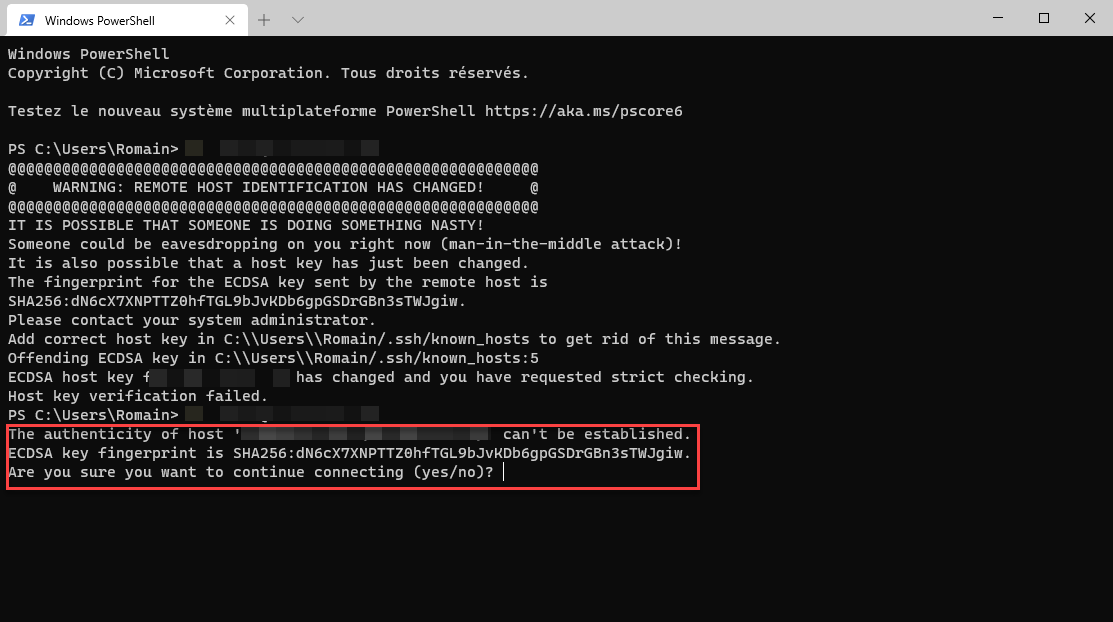
1. Verify the Change: When the warning appears, attentively read the details provided. It will typically include the server’s IP address or hostname, the line in the configuration file where the discrepancy was detected, and the key fingerprint. Compare this information with what you expect to see, based on your previous connection details or any server management communication you might have received. If uncertain, you should contact the server administrator or IT department to verify the changes.
2. Confirm Source Authenticity: If you received the new host key fingerprint through an alternative communication channel, such as a secure email or a trusted messaging platform, verify the authenticity of the source. Ensuring that the provided fingerprint aligns with the server’s identity and the changes you expect will minimize the risk of falling into an attacker’s trap.
3. Re-establish Trust: If you are confident that the server changes are legitimate, SSH allows you to update the host keys stored on your local machine. By accepting and storing the new keys, you re-establish trust with the remote server. The warning should no longer appear when connecting to the same server in the future.
FAQs:
Q: Can I still connect to the server if I ignore the warning?
A: Ignoring the warning is not recommended as it may lead to serious security breaches or data compromise. However, SSH will still allow you to connect to the server after generating the warning. Exercise extreme caution if you choose to proceed without verifying the changes or confirming authenticity.
Q: Does the warning mean the server was hacked?
A: While a changed host identification could indicate a security breach, it could also be a result of legitimate server modifications, hardware changes, or a simple update in administrative settings. Nonetheless, it should always be treated as a potential security issue unless verified otherwise.
Q: How often do host keys change?
A: In most cases, host keys remain unchanged for extended periods. However, specific server maintenance, reinstallation, or hardware changes may necessitate generating new host keys. It is essential to monitor such changes closely.
Q: Can this warning occur during routine server updates?
A: Routine software updates typically do not generate host key changes that trigger the warning. However, major updates or upgrades to the SSH server software could potentially lead to host key changes.
Q: Is it safe to store the new host keys on my local machine?
A: If you have verified the authenticity of the server and are confident that the changes are legitimate, updating and storing the new host keys on your local machine is safe. It ensures secure connections in the future without encountering the warning.
In conclusion, the “Warning: Remote Host Identification Has Changed” message serves as an essential security measure when establishing SSH connections. Understanding the reasons behind this warning and taking appropriate action to verify and validate changes will help ensure secure and trustworthy remote server connections.
Keywords searched by users: remote host identification has changed Warning remote host identification has changed vps, WARNING: remote host IDENTIFICATION has changed ubuntu, Warning remote host identification has changed raspberry pi, host key verification failed., RSA host key for GitHubcom has changed and you have requested strict checking, Ssh-keygen, Remove known host ssh, The fingerprint for the ECDSA key sent by the remote host is
Categories: Top 97 Remote Host Identification Has Changed
See more here: nhanvietluanvan.com
Warning Remote Host Identification Has Changed Vps
As technology continues to advance, more and more businesses are opting for virtual private servers (VPS) to meet their hosting needs. VPS offers flexibility, scalability, and security advantages over traditional shared hosting. However, VPS users might encounter a common warning message that says, “Remote host identification has changed.” It is essential to understand the implications of such a warning to ensure a seamless and secure hosting experience. In this article, we will explore what this warning means, why it occurs, and how users can address it effectively.
Understanding the Warning
The “Remote host identification has changed” warning message typically appears when users attempt to connect to a VPS using secure shell (SSH) protocol. SSH is a popular method for remotely accessing servers. When connecting to a server for the first time, SSH stores the server’s identification information, such as its IP address or host key, in the user’s local system for future reference.
However, if the server’s identification information changes, such as when reinstalling the operating system or transferring the VPS to a different infrastructure, SSH detects the discrepancy and displays the warning message. This is a security feature implemented to prevent man-in-the-middle attacks, where an attacker pretends to be the legitimate server and intercepts or alters the communications between the user and the server.
Why Does This Warning Occur?
Several circumstances can trigger the “Remote host identification has changed” warning on a VPS. The most common reasons include:
1. Server migration: If the VPS undergoes migration to a different physical server due to infrastructure upgrades, the server’s identification information will change, resulting in the warning message.
2. Reinstallation of the operating system: Occasionally, users may choose to reinstall their VPS’s operating system. This will cause the host identity to change, prompting the warning.
3. Security measures: In some cases, the warning can simply be caused by heightened security protocols. System administrators might update the host keys to enhance security, which subsequently triggers the warning on user end.
How to Address the Warning
When encountering the “Remote host identification has changed” warning, it is crucial to assess the situation and determine whether it is a genuine change or a possible security breach. Here are the general steps users can take to address the warning effectively:
1. Verify the change: Before dismissing or accepting the warning, users should verify whether any legitimate changes have occurred on the VPS, such as server migration or operating system reinstallation. Users can consult their VPS provider or system administrator to validate these changes.
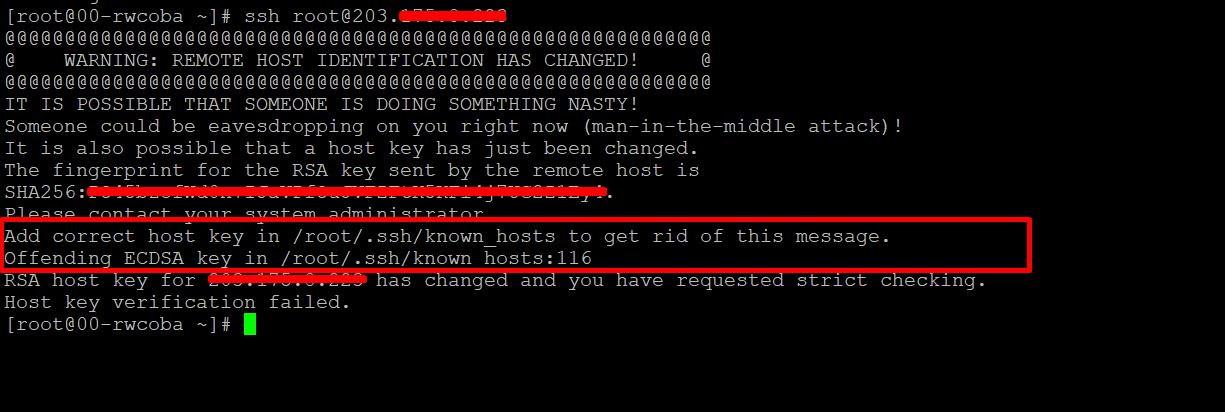
2. Update the known_hosts file: The known_hosts file is where SSH stores the identification information of the servers it has previously connected to. To address the warning, users can open the known_hosts file, locate the line that corresponds to the affected VPS, and remove it. Upon reconnecting, SSH will reestablish a secure connection with the VPS and store the new identification information.
Frequently Asked Questions (FAQs)
1. Can I ignore the “Remote host identification has changed” warning?
It is not recommended to ignore this warning, as it could potentially indicate a security breach. Always investigate the cause of the warning and take necessary actions to address it.
2. What should I do if the warning persists after reconnecting?
If the warning continues to appear even after reconnecting to the VPS, it is advisable to contact your VPS provider or system administrator. They can help identify the source of the warning and provide guidance on resolving it.
3. Should I remove all entries from the known_hosts file?
No, removing all entries from the known_hosts file is not recommended. Doing so can expose users to potential security risks. It is best to remove only the specific line corresponding to the affected VPS.
4. Can I prevent this warning from appearing in the future?
Users can use the SSH option “-o StrictHostKeyChecking=no” to disable strict host key checking temporarily. However, this option should be used with caution, as it sacrifices a layer of security. It is advisable to consult with a system administrator before implementing this option.
In conclusion, the “Remote host identification has changed” warning is an important security feature of SSH that alerts users to potential security breaches regarding their VPS. Understanding the reasons behind this warning and taking appropriate actions, such as updating the known_hosts file, can help users maintain the integrity and security of their VPS. By staying vigilant and promptly addressing any warnings, users can ensure a stable and secure hosting experience on their VPS.
Warning: Remote Host Identification Has Changed Ubuntu
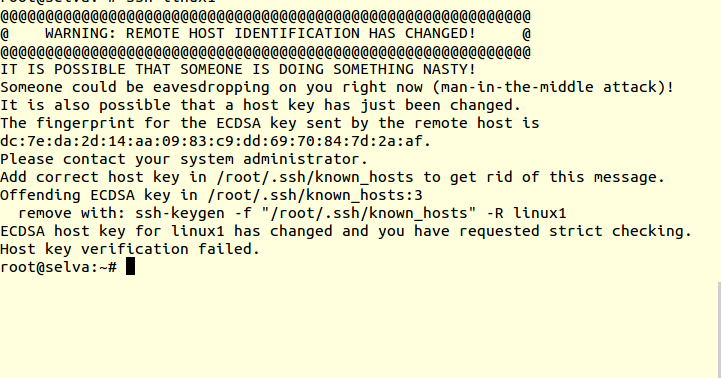
The remote host identification change error may occur when trying to establish a connection to a remote server using SSH protocol on an Ubuntu system. This warning indicates that the server key or host key has been changed since the last time you connected to the remote server. While this message may seem alarming, understanding its cause and how to resolve it can help you ensure the security and integrity of your SSH connections.
When connecting to a remote server for the first time, the SSH client on your Ubuntu system verifies the identity of the remote host by checking its host key. The host key is a cryptographic key assigned to the server in order to validate its authenticity. This key is stored in the ~/.ssh/known_hosts file on your local system. Once verified, the client saves the host key in the known_hosts file to facilitate future connections. This way, any subsequent connection attempt should match the key stored on your system.
However, if the remote server undergoes a change in its keys, such as being reinstalled or updated, the SSH client generates a warning to notify you about this change. This is done to protect users from potential security risks, as server key changes can indicate a possible security breach or a man-in-the-middle attack.
To ensure the security of your SSH connections, the SSH client generates a unique key fingerprint for every server. This fingerprint is a cryptographically generated value that uniquely identifies the server’s key. When the client detects a change in the fingerprint, it alerts you with the “WARNING: remote host identification has changed!” message.
Now that we understand the nature of this warning, let’s delve into the specifics of resolving it:
1. Confirm the change: Verify if the warning is legitimate by cross-checking with the server administrator or another trusted source. Confirming the change helps ensure that you are not connecting to a compromised server.
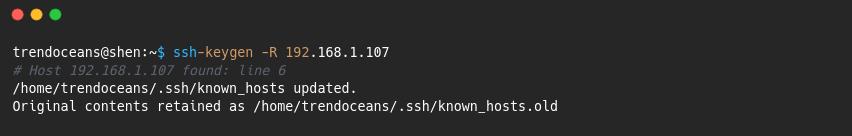
2. Remove the known host entry: If you determine that the change is expected or a mistake, you can remove the corresponding entry from the known_hosts file. Open a terminal and use the following command, replacing “server_ip” with the actual IP address or hostname of the remote server:
“`shell
ssh-keygen -R server_ip
“`
3. Verify the key: If you trust the remote server, you can update the known_hosts file with the new key. You can obtain the new key by connecting to the server via another trusted method (e.g., physical access), or by contacting the server administrator. Once you have the new key, execute the following command, again replacing “server_ip” with the actual IP address or hostname of the remote server:
“`shell
ssh-keyscan server_ip >> ~/.ssh/known_hosts
“`
4. Advanced options: If you frequently encounter this warning due to server changes in your environment, you may consider using strict host key checking. This option enhances security by rejecting connections to servers with changed host keys. To enable this, you can add the following line to your ~/.ssh/config file:
“`shell
StrictHostKeyChecking ask
“`
FAQs:
Q: Can I trust the new server key?
A: If you were not expecting a change in the server key, exercise caution when connecting. Verify the key through trusted sources, such as the server administrator, before proceeding.
Q: What if the remote server key changes frequently due to updates?
A: Consider enabling strict host key checking to enhance security. This way, you will be prompted to verify the key each time it changes, ensuring that you are connecting to the correct server.
Q: Will removing the known host entry compromise the connection?
A: Removing the known host entry will not compromise the connection. However, it will require the client to re-verify the server key the next time you connect.
Q: How can I prevent this warning from appearing?
A: The warning appears to protect users from potential security risks, such as man-in-the-middle attacks. It is recommended to address the warning instead of disabling it completely.
Q: Can this warning appear even without any server changes?
A: Though rare, this warning can occasionally happen without any server changes due to issues with the client or known_hosts file. In such cases, removing the entry and re-establishing the connection can resolve the issue.
In conclusion, the “WARNING: remote host identification has changed!” error in Ubuntu is a vital feature of SSH that alerts users to potential security risks. Understanding the cause and following the appropriate steps to address the warning can help ensure secure and trustworthy connections to remote servers.
Images related to the topic remote host identification has changed

Found 12 images related to remote host identification has changed theme


















![Github] WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! 에러 해결 Github] Warning: Remote Host Identification Has Changed! 에러 해결](https://velog.velcdn.com/images/jeongmin78/post/076f3b89-a89a-46a9-9bf2-a0ac8f5ec9e9/image.png)
![SOLVED] SSH : WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED - YouTube Solved] Ssh : Warning: Remote Host Identification Has Changed - Youtube](https://i.ytimg.com/vi/d0RBXye8qpI/maxresdefault.jpg)








Article link: remote host identification has changed.
Learn more about the topic remote host identification has changed.
- How To Fix “Warning: Remote Host Identification Has … – Kinsta
- ssh remote host identification has changed – Stack Overflow
- How To Fix “Warning: Remote Host Identification Has … – Kinsta
- Error Fix – Warning: Remote Host Identification Has Changed …
- We updated our RSA SSH host key – The GitHub Blog
- SSH Host Key Management Demystified
- How To Deal With the “Remote Host Identification Has …
- WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED!
- 3 Ways to fix remote host identification has changed
- How to fix “Warning: remote host identification has changed”
- How to fix “Remote Host Identification has Changed” error
- Error Fix – Warning: Remote Host Identification Has Changed …
- Fixing SSH Remote Host Identification Has Changed Warnings
- How to fix: “WARNING: REMOTE HOST IDENTIFICATION …
See more: https://nhanvietluanvan.com/luat-hoc