Publicly Accessible Google Api Key
In today’s digital landscape, application programming interfaces (APIs) have become a crucial part of software development. They allow developers to easily integrate various functionalities and services into their applications, enhancing user experience and improving data accuracy. Google, being a leader in technology, offers a wide range of APIs that developers can leverage to add powerful features to their applications. However, it is important to understand the importance of securing and managing API keys, as they can expose sensitive data and lead to security vulnerabilities. In this article, we will explore the benefits of using a publicly accessible Google API key and provide best practices on how to store them securely.
Benefits of Using a Publicly Accessible Google API Key:
1. Enhanced User Experience:
By integrating Google APIs into your application, you can provide users with a seamless experience. For example, using the Google Maps API, you can display interactive maps and provide directions to users, making navigation easier and more intuitive.
2. Improved Data Accuracy:
Google APIs provide access to vast amounts of accurate data, such as geolocation information, weather forecasts, and language translations. By leveraging these APIs, you can ensure that your application delivers reliable and up-to-date information to users.
3. Increased Developer Productivity:
Using Google APIs can significantly reduce development time and effort. Instead of building complex functionalities from scratch, developers can rely on pre-existing APIs to handle common tasks, allowing them to focus on other areas of their application.
4. Streamlined Integration with Google Services:
If you already use various Google services, such as Google Cloud Platform or Google Maps, integrating their APIs with your application becomes seamless. This opens up a world of possibilities for developers to leverage the power of Google services in their projects.
5. Cost-Effective Solution:
Google offers a variety of APIs with flexible pricing models, including free tiers for developers starting out or working on small-scale projects. This allows developers to experiment and innovate without incurring significant costs upfront.
6. Accessibility Across Platforms:
Google APIs are designed to be platform-agnostic, meaning they can be easily integrated into web, mobile, or desktop applications. This ensures that users can access the functionality of your application regardless of their preferred device or operating system.
7. Scalability and Flexibility:
Google’s API infrastructure is designed to handle millions of requests per second, ensuring that your application remains performant and responsive even under heavy traffic. Additionally, Google regularly updates and improves its APIs, allowing your application to benefit from new features and enhancements seamlessly.
8. Real-time Updates and Notifications:
Google APIs provide real-time updates and notifications, enabling developers to deliver timely information to users. For example, by using the Google Maps API, you can provide live traffic updates or real-time location tracking for a better user experience.
9. Extensive Documentation and Resources:
Google’s APIs come with comprehensive documentation, guides, and tutorials, making it easy for developers to get started and leverage their full potential. Additionally, Google offers dedicated support for developers, ensuring any issues or concerns can be addressed promptly.
Best Practices for Managing and Securing API Keys:
Publicly accessible Google API keys should be handled with care as they grant access to sensitive data and services. Here are some best practices for managing and securing your API keys:
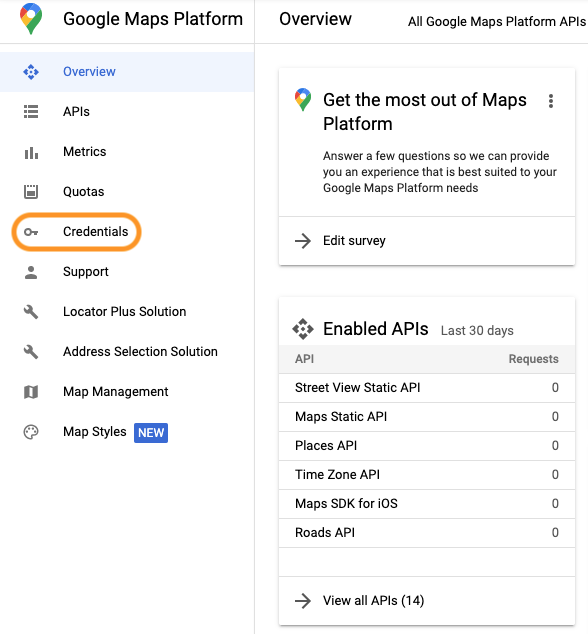
1. Create a Google Cloud Platform (GCP) project:
To obtain a publicly accessible Google API key, you need to create a GCP project. This project acts as a container for your APIs, allowing you to manage and control access securely.
2. Restrict API key usage:
Within your GCP project, you can restrict the usage of your API keys by specifying the allowed referrers or IP addresses. This ensures that only authorized applications or servers can use your API keys, reducing the risk of unauthorized access.
3. Use environment variables:
Instead of hardcoding your API keys into your application’s source code, consider using environment variables. This allows you to store your keys outside of your codebase and provides an extra layer of security. Be cautious when handling environment variables and ensure they are properly secured.
4. Implement rate limiting:
To prevent abuse and unnecessary costs, it is essential to implement rate limiting on your API key usage. By defining limits on the number of requests per second or per user, you can protect your resources and better manage the usage of your key.
5. Regularly rotate your keys:
Periodically rotating your API keys adds an extra layer of security. This practice ensures that even if a key is compromised, the potential impact is minimized. Make sure to update your keys in all applications and services that use them when rotating.
6. Monitor API key usage:
Keep a close eye on your API key usage through the Google Cloud Console or other monitoring tools. Regularly review and analyze the usage patterns to identify any suspicious activities or potential security breaches.
In conclusion, utilizing publicly accessible Google API keys can significantly enhance your application’s user experience, improve data accuracy, and increase developer productivity. However, it is crucial to follow best practices for managing and securing your API keys to ensure the safety and integrity of your application and its users. By implementing proper security measures and staying vigilant, you can leverage the power of Google APIs while keeping your application and data secure.
FAQs:
Q: What is a publicly accessible Google API key for Google Cloud Platform project?
A: A publicly accessible Google API key is a unique identifier provided by Google that allows developers to access and utilize various Google APIs. It is associated with a Google Cloud Platform project and is used to authenticate and authorize access to Google services.
Q: What is Aiza Google API key?
A: “Aiza” is not a recognized term in relation to Google API keys. It is possible that it refers to a specific use case or context, but without further information, it is difficult to provide a comprehensive answer.
Q: How to hide Google Maps API key in JavaScript?
A: To hide your Google Maps API key in JavaScript, you can employ various techniques such as using environment variables, storing the key on a server, or utilizing server-side rendering. These methods help prevent exposing your key in client-side scripts, reducing the risk of unauthorized access.
Q: What are the best practices to manage API keys?
A: Some best practices to manage API keys include restricting key usage to authorized referrers or IP addresses, using environment variables instead of hardcoding keys in source code, implementing rate limiting, regularly rotating keys, and monitoring key usage for suspicious activities.
Q: Can Google API keys be exposed?
A: Yes, Google API keys can be exposed if not properly managed or secured. Exposing an API key can lead to unauthorized access, potentially compromising sensitive data or services. Implementing proper security measures, such as restricting usage and regularly monitoring key usage, helps prevent exposure.
Q: Why should Google API keys not be disclosed?
A: Disclosing Google API keys can pose a security risk as they grant access to sensitive data and services. Unauthorized access can lead to data breaches, compromised applications, or abuse of resources. It is essential to keep API keys confidential and follow security best practices when managing them.
Q: How to store API keys securely?
A: Storing API keys securely involves using techniques like environment variables, secure key management systems, or encrypting keys at rest. It is recommended to avoid hardcoding keys in source code or publicly sharing them. Additionally, following proper access control and rotation practices helps ensure key security.
How To Generate And Restrict Api Keys For Google Maps Platform
Can Google Api Key Be Public?
Google API keys are essential tools for developers who want to integrate Google services into their applications. However, there is often confusion regarding whether these API keys can be made public or should they be kept confidential. In this article, we will explore the implications of making a Google API key public and provide a comprehensive understanding of the topic.
Understanding Google API Keys
To begin, let’s delve into what Google API keys are and their purpose. Google API keys are unique identifiers that authenticate access to Google APIs (Application Programming Interfaces). API keys allow developers to interact with various Google services such as Maps, Calendar, Drive, and more.
When you create a Google API key, it grants access to specific resources and functionalities. For instance, if you are developing a mapping application, your API key would allow access to the Google Maps API, enabling you to display maps and utilize related services. API keys are an essential part of the authentication process, ensuring that only authorized applications can interact with Google’s services.
Public vs. Confidential
The question arises: can Google API keys be made public? The answer is twofold, depending on the type of API key you are using.
Firstly, there are API keys that are intended to be public. These public API keys are usually associated with web-based applications that require access to Google services without any user authentication. In such cases, it is safe and appropriate to distribute the API key publicly. For instance, if you are creating a public website that utilizes Google Maps, you can safely embed the API key in the client-side code.
However, there is another type of API key that should be kept confidential – the private API key. Private API keys are typically used in the context of server-side applications that handle sensitive data or require user authentication. Sharing a private API key publicly can lead to unauthorized access to your application and its associated data. It is crucial to keep these private keys securely stored and not disclose them to avoid any potential security breaches.
Implications of Public API Keys
Public API keys, as mentioned earlier, can be safely distributed. However, it is essential to consider the potential implications and best practices when making a Google API key public. Here are a few key points to keep in mind:
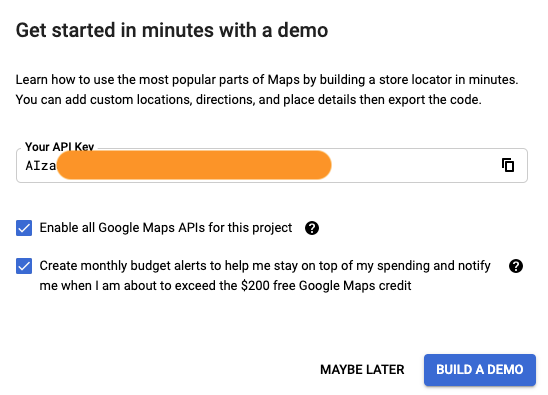
1. Quota Limits: Google sets usage limits for its APIs, including those accessed by public API keys. If your API key is public and widely distributed, it increases the likelihood of hitting these limits. This may result in temporary service disruptions until quota limits reset or your account is upgraded to a higher usage tier.
2. Unauthorized Usage: Although publicly shared API keys can be used by anyone, it is vital to monitor their usage and be cautious of potential misuse or abuse. Unauthorized usage can impact service reliability and may lead to unexpected costs or data discrepancies.
3. Billing Concerns: Some Google APIs have associated costs beyond certain usage thresholds or premium services. If you have a public API key that is widely distributed, keep an eye on potential billing concerns to avoid unexpected expenses.
FAQs
Q1. Can I share my API key with other developers?
A1. Sharing your API key with other developers is generally fine as long as you trust their intentions and make sure they understand the implications of using your key. However, be cautious when sharing private API keys and only provide access to those that require it.
Q2. How can I secure my private API key?
A2. When working with private API keys, it is best to store them securely on your server, rather than embedding them in client-side code, to prevent unauthorized access. Additionally, consider restricting access by IP addresses or implementing other security measures recommended by Google.
Q3. What should I do if my API key is compromised?
A3. If you suspect that your API key has been compromised, it is crucial to take immediate action. Start by revoking the affected key and generating a new one. Update your application with the new key and restrict access to the compromised key as required.
In conclusion, the decision to make a Google API key public or keep it confidential depends on the type of API key and the associated application. Public API keys that do not handle sensitive data can be safely shared, while private API keys must be kept secure to avoid unauthorized access. By following best practices and monitoring usage, developers can effectively leverage Google’s APIs without compromising security or incurring unexpected costs.
Is Google Api Key Private?
In the era of hyper-connectivity, data security has become a paramount concern for businesses and individuals alike. With most operations shifting to the virtual realm, protecting sensitive information from prying eyes has become a necessity. When it comes to Google and its application programming interfaces (APIs), many users question the privacy and security of their API keys. This article aims to delve into the intricacies of Google API keys, analyzing their privacy levels and addressing common concerns.
To begin with, it is important to understand what an API key is and how it functions within the Google ecosystem. An API key is a unique identifier that enables an application to access certain functionalities or data from Google services. These keys play a crucial role in authenticating and authorizing requests made by applications to interact with Google APIs, such as the Google Maps API or the Google Translate API.
One key aspect often overlooked is that an API key is not a secret token or a direct means of accessing confidential data. Instead, it acts as a safeguard to regulate access to Google services, preventing unauthorized usage. This means that while an API key is essential for utilizing certain features of Google APIs, it does not grant direct access to private or sensitive information.
Furthermore, API keys are not inherently private. They are designed to be shared openly with authorized individuals or developers who require access to specific Google services. Sharing an API key in itself does not pose a major threat to security, as long as it remains in the hands of trusted individuals. However, it is essential to limit the distribution of API keys to prevent unauthorized usage, as this can lead to potential security vulnerabilities.
To bolster privacy and security, Google provides various mechanisms to control API key usage. One such mechanism is the option to restrict API key usage by IP addresses or HTTP referrers. With IP restriction, developers can specify a set of IP addresses from which requests are allowed, effectively limiting access to the designated range. On the other hand, HTTP referrer restriction enables developers to specify the URLs from which requests can be made, enhancing control over the origins of API usage.
Moreover, Google API keys can also be secured using various authentication mechanisms, such as OAuth. OAuth allows users to grant limited access to their Google accounts without divulging sensitive credentials. By employing OAuth, developers can ensure that only authorized users are granted access to specific APIs, adding an extra layer of security to the authentication process.
Frequently Asked Questions (FAQs):
Q: Can someone misuse my API key if they obtain it?
A: While it is theoretically possible for someone to misuse your API key, it is highly unlikely if proper precautions are taken. By restricting API key usage and sharing it only with trusted individuals, the risk of misuse can be significantly minimized.
Q: Can sharing API keys compromise the security of my Google account?
A: Sharing API keys in itself does not compromise the security of your Google account. However, unauthorized usage of API keys can potentially lead to security vulnerabilities. It is crucial to manage and restrict API key access to prevent any such risks.
Q: Are there any best practices for securing Google API keys?
A: Yes, there are several best practices for securing Google API keys. These include restricting API key usage, limiting key distribution, using IP or HTTP referrer restrictions, and implementing authentication mechanisms like OAuth. Regularly monitoring API key usage and promptly revoking any compromised keys are also vital precautions.
Q: How can I track and monitor API key usage?
A: Google provides detailed logs and usage reports for API keys. These logs can be accessed through the Google Cloud Platform console, enabling users to track and monitor key usage. By regularly monitoring usage, any suspicious activity or unauthorized usage can be quickly identified and addressed.
Q: Can I delete or change my API key once it has been generated?
A: Yes, API keys can be deleted or regenerated at any time. In case of suspected misuse or security concerns, it is recommended to revoke the existing API key and generate a new one to ensure continued security.
In conclusion, Google API keys are not private in the traditional sense. They are designed to regulate access to Google services rather than provide direct access to confidential data. However, it is crucial to implement necessary precautions like restricting usage, monitoring key access, and employing authentication mechanisms to maintain the privacy and security of API keys. By following best practices and being mindful of key distribution, users can effectively protect their Google API keys and ensure the overall security of their applications.
Keywords searched by users: publicly accessible google api key publicly accessible google api key for google cloud platform project, aiza google api key, how to hide google map api key in javascript, google maps api key usage, how to manage api keys, google api key exposed, google api keys should not be disclosed, how to store api keys securely
Categories: Top 85 Publicly Accessible Google Api Key
See more here: nhanvietluanvan.com
Publicly Accessible Google Api Key For Google Cloud Platform Project
Google Cloud Platform (GCP) is a suite of cloud computing services that offers a range of products and tools for developing, deploying, and managing applications. One of the key components of GCP is the ability to access and utilize a variety of Google APIs through API keys. These API keys allow developers to access Google services and integrate them into their applications easily. However, it is essential to understand the implications of publicly exposing your API key, as this can pose security risks and potentially lead to unauthorized access or abuse of your Google resources.
What is a Google API Key?
A Google API key is a unique identifier that allows access to Google APIs. These keys are generated within the Google Cloud Platform Console and are associated with a specific project. By using an API key, developers can authenticate their applications and authorize them to access specific Google services such as Google Maps, Google Analytics, Google Calendar, and more.
Public vs. Private API Keys
By default, API keys generated in the Google Cloud Platform Console are restricted for use by the creator of the project. This means that only the developer who generates the API key can use it in their applications. This setting is the recommended option for most scenarios as it ensures that your API key is not accessible to others, reducing the risk of unauthorized usage or abuse.
However, there may be situations where you want to make your API key publicly accessible, allowing anyone to use it within their applications. In such cases, enabling public access to your API key can be done by specifying the appropriate settings within the Google Cloud Platform Console. Keep in mind that making your API key publicly accessible exposes it to potential misuse, so it is crucial to understand the risks and take necessary precautions.
Implications of Publicly Accessible Google API Key
Publicly exposing your Google API key can have several implications, including security risks and abuse of resources. Here are some of the main points to consider:
1. Unauthorized Usage: Publicly accessible API keys can be utilized by anyone without any restrictions. This means that anyone who obtains your API key can use it in their own applications, potentially resulting in increased usage and costs for your GCP project.
2. Billing: When your API key is used by other developers, any expenses incurred will be billed directly to your GCP project. Unauthorized usage by others can quickly consume your allocated quotas and lead to unexpected charges.
3. API Abuse: Once an API key is publicly accessible, it can be exploited by malicious actors to abuse your resources. For instance, they might use your API key to launch orchestrated attacks, send spam requests, or scrape data excessively, causing disruptions to your applications or incurring additional costs.
4. Unauthorized Access: In addition to the potential financial consequences, public API keys can expose sensitive data or functionalities to unauthorized individuals. This could include access to personal or business-related information, intellectual property, or any other data managed by Google services linked to the API key.
FAQs
1. Can I change an API key from public to private?
Yes, you can change the accessibility of an API key from public to private at any time within the Google Cloud Platform Console. Simply update the settings to restrict its usage to your own applications.
2. How can I monitor the usage of my publicly accessible API key?
Google provides detailed usage reports and monitoring tools within the GCP Console. You can track the usage of your API key, including the number of requests made, data transferred, and associated costs. By monitoring your API key, you can identify any unusual activity or potential abuse.
3. What are the recommended security practices for handling API keys?
To ensure the security of your API keys, follow these best practices:
– Restrict the permissions of API keys to the specific Google services and actions required by your application.
– Use separate API keys for different applications or projects to granularly control access.
– Regularly rotate and update your API keys to minimize the potential impact of a compromised key.
– Implement security measures such as IP restrictions, request limits, and CAPTCHAs to mitigate abuse and protect your resources.
– Avoid hardcoding API keys within your application’s code, as this can make them vulnerable to unauthorized access or exposure.
Publicly accessible Google API keys can provide convenience and extend the functionality of your applications when used appropriately. However, it is crucial to understand the potential risks and take the necessary steps to secure your API keys and monitor their usage effectively. By following best practices and implementing robust security measures, you can ensure the safe utilization of Google APIs within your Google Cloud Platform projects.
Aiza Google Api Key
In today’s digital age, the power of APIs (Application Programming Interfaces) cannot be understated. APIs enable software applications to connect and interact with each other, allowing for seamless integration and communication between different platforms. When it comes to web development and offering enhanced user experiences, Google’s APIs are among the most powerful and widely used. And Aiza, a leading innovation company, has taken advantage of this by providing developers with their own Aiza Google API Key.
So, what exactly is an API key? In simple terms, an API key is a unique identifier that allows developers to access specific functionalities and data through a particular API. In the case of Aiza’s Google API Key, developers gain access to a plethora of Google’s services, such as Google Maps, Google Drive, Gmail, and much more. With this key, developers can leverage the power of Google’s services to create seamless integrations, advanced functionalities, and improved user experiences.
Aiza’s Google API Key empowers developers by providing them with a secure and reliable way to interact with Google’s APIs. By offering this key, Aiza ensures that developers can make the most of Google’s services without having to worry about the technical complexities or the need to understand all the intricacies of Google’s APIs. This simplifies the development process and allows developers to focus on creating innovative solutions rather than getting lost in the nitty-gritty details.
But why should developers choose Aiza’s Google API Key over other alternatives? One of the key advantages of using Aiza’s API key is the exceptional support and reliability it offers. Aiza’s team of experts ensures that developers receive 24/7 support, making troubleshooting and issue resolution a breeze. Furthermore, with Aiza’s extensive documentation and easy-to-use interface, developers can quickly get up to speed and start building incredible applications with Google’s services.
Additionally, using Aiza’s Google API Key comes with added security benefits. Aiza implements industry-standard security protocols, ensuring that the API key remains secure and protected against unauthorized access or misuse. This level of security is crucial in an era where data breaches and cyberattacks are prevalent. By entrusting their projects to Aiza’s API key, developers can rest assured that their applications and users’ data will remain safe and secure.
Now, let’s address some frequently asked questions regarding Aiza’s Google API Key:
1. How do I obtain an Aiza Google API Key?
Obtaining an Aiza Google API Key is a simple process. Developers can visit Aiza’s official website, sign up for an account, and follow the instructions provided. Once the account is created, developers can generate their unique API key through the Aiza platform.
2. How much does it cost to use Aiza’s Google API Key?
Aiza offers flexible pricing plans to cater to the varying needs of developers. The cost depends on factors such as the number of API requests and the chosen plan. Developers can visit Aiza’s pricing page to get detailed information about the available plans and associated costs.
3. Can I use Aiza’s Google API Key for commercial applications?
Absolutely! Aiza’s Google API Key can be used for both personal and commercial applications. Whether you’re building a small personal project or a large-scale commercial application, Aiza’s API key is designed to meet your needs.
4. What support options are available if I encounter an issue or have questions?
Aiza takes pride in offering excellent customer support. Developers can reach out to Aiza’s support team through various channels, including email and live chat. Additionally, Aiza’s extensive documentation and tutorials serve as valuable self-help resources.
5. Are there any usage limitations for Aiza’s Google API Key?
While Aiza imposes fair usage policies, developers can make a significant number of API requests within their chosen subscription plan. Moreover, Aiza’s team continuously monitors usage patterns to ensure smooth and uninterrupted service provision.
In conclusion, Aiza’s Google API Key provides developers with a powerful tool to integrate Google’s services seamlessly. By simplifying the development process, offering exceptional support and security, and providing flexible pricing plans, Aiza enables developers to unlock the true potential of Google’s APIs. If you’re a developer looking to enhance your applications with Google’s services, Aiza’s API key is undoubtedly worth considering. Empower yourself by joining Aiza’s network of developers and take your applications to new heights.
Images related to the topic publicly accessible google api key

Found 42 images related to publicly accessible google api key theme







.thumb.png.0234369645e7e999c750cead6242c737.png)






![How to Get a YouTube API Key [Tutorial + Examples] How To Get A Youtube Api Key [Tutorial + Examples]](https://blog.hubspot.com/hs-fs/hubfs/youtube-api-credential-options.png?width=650&name=youtube-api-credential-options.png)







Article link: publicly accessible google api key.
Learn more about the topic publicly accessible google api key.
- What to do about this warning email from Google: Publicly …
- API security best practices | Google Maps Platform
- Warning about Publicly accessible Google API key for Google …
- Plugin is publicly exposing my Google API Key – WordPress.org
- Your Publicly Accessible Google API Key Could … – spiderSilk
- Google API Key | GitGuardian documentation
- Pricing & quotas | API Keys API Documentation – Google Cloud
- Use API Keys with Places API – Google for Developers
- Your Publicly Accessible Google API Key Could … – spiderSilk
- Publicly accessible Google API key for Google Cloud Platform…
- Warning from Google: publicly accessible Google API key
- Received email about publicly accessible API key b…
- Publicly accessible Google API key for Google Cloud Platform …
- Publicly accessible Google API key · Issue #581 – GitHub
See more: nhanvietluanvan.com/luat-hoc