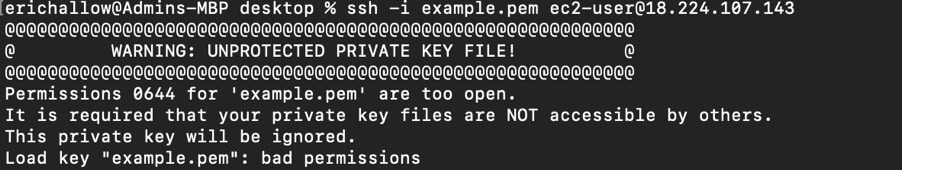
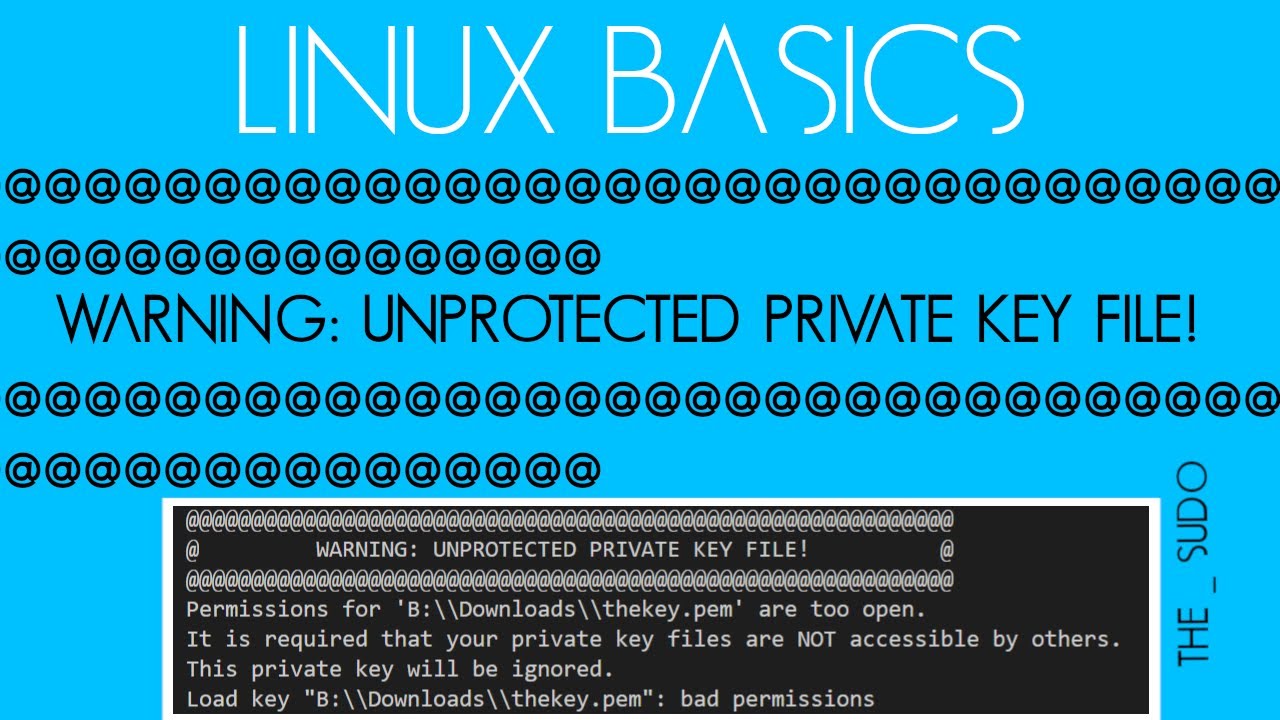
Permissions 0644 For Are Too Open
Overview of File Permissions
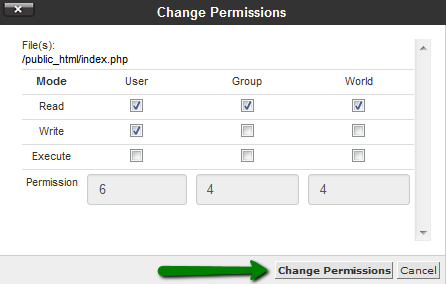
File permissions control access to files and directories on a computer system. They determine who can read, write, and execute files or directories. In the context of Windows, file permissions are represented by a set of three-digit numbers, denoting the permissions for the owner, group, and others.
Each permission digit can have a value of 0 to 7, with each value representing a different level of access. The digits correspond to the following permissions: 0 – no permission, 1 – execute permission, 2 – write permission, and 4 – read permission. Therefore, the common permission values are 0, 1, 2, 3, 4, 5, 6, and 7.
Understanding the Importance of Permissions 0644
Permissions 0644 indicate that the owner of the file or directory has read and write access, while the group and others have only read access. This is considered a relatively open permission setting, often used for files that are meant to be shared or accessed by multiple users. However, it is crucial to ensure that this permission setting is used appropriately and does not pose any security risks.
Risks and Consequences of Having Permissions 0644 Too Open
Having permissions 0644 set too open can lead to several security risks and consequences. Firstly, it can allow unauthorized users or attackers to view and potentially modify sensitive files, leading to data breaches or unauthorized access to critical information. Additionally, malware and other malicious software can exploit open permissions to manipulate or delete files, causing disruption or loss of data.
Moreover, open permissions can also result in accidental changes or deletions by users who may not have the necessary knowledge or intentions to make such modifications, leading to data loss or system instability. It is essential to strike a balance between accessibility and security by setting appropriate permissions.
Examples of Vulnerabilities with Permissions 0644
To better understand the risks associated with permissions 0644 that are too open, let’s consider a few examples:
1. A user accidentally sets permissions 0644 on a configuration file containing sensitive information, such as database credentials. This would allow anyone with read access, including unauthorized individuals, to view the contents of the file and potentially gain access to the database.
2. Malware infects a system and gains read and write access to all files with permissions 0644. The malware can then modify critical system files, install additional malware, or exfiltrate sensitive data.
3. An employee accidentally deletes important files from a shared folder due to the open write access granted by permissions 0644. This can lead to the loss of valuable data and disrupt business operations.
Best Practices for Setting Secure Permissions 0644
To ensure the security and integrity of your files, it is essential to follow best practices when setting permissions 0644. Here are some guidelines to consider:
1. Limit access to sensitive files and directories by granting permissions only to those who need them.
2. Regularly review and audit file permissions to ensure they remain appropriate and up-to-date.
3. Avoid setting permissions 0644 for files that contain sensitive or critical information, and instead, restrict access to trusted individuals or groups.
4. Consider implementing access control lists (ACLs) to provide more granular control over permissions for specific users or groups.
5. Regularly backup important files to mitigate the potential impact of accidental changes or deletions.
Tools and Techniques for Auditing and Adjusting Permissions 0644
Auditing and adjusting file permissions is a crucial aspect of maintaining security. Fortunately, Windows provides several built-in tools and commands to help with this process. Here are a few commonly used tools and techniques:
1. Windows Security -> Permissions tab: Right-click on a file or folder and select Properties. Navigate to the Permissions tab to view and manage file permissions easily.
2. Command Line: The `icacls` command can be used to view and modify file permissions from the command prompt or PowerShell.
3. Third-Party Tools: Various third-party tools, such as AccessEnum and NTFS Permissions Reporter, offer more advanced features and capabilities for auditing and adjusting file permissions.
Conclusion: Maintaining Secure Permissions 0644
Permissions 0644 for are too open? Maintaining secure file permissions is crucial for protecting your sensitive data and maintaining the integrity of your system. Understanding the risks and consequences of having permissions 0644 that are too open is vital for implementing proper security measures. By following best practices, regularly auditing permissions, and using the appropriate tools, you can strike a balance between accessibility and security, ensuring that your files remain safe and protected.
Ssh: \”Permissions 0644 For ‘My_Key.Pub’ Are Too Open.\” (4 Solutions!!)
Keywords searched by users: permissions 0644 for are too open Permissions for are too open Windows, permission denied (publickey,gssapi-keyex,gssapi-with-mic), Load key bad permissions, It is required that your private key files are NOT accessible by others Windows, Permissions 0555 are too open, Load key invalid format, Bad permissions SSH key Windows, Permissions 0644 for
Categories: Top 17 Permissions 0644 For Are Too Open
See more here: nhanvietluanvan.com
Permissions For Are Too Open Windows
In today’s digital age, where privacy and security are of utmost importance, it is crucial to ensure that our computers and data are protected. One aspect of maintaining a secure system is managing permissions in the Windows operating system. Permissions allow users to access and manipulate files and folders on a computer, but when these permissions are too open, they can pose a significant risk to our privacy and data integrity. In this article, we will explore the potential dangers associated with overly permissive permissions in Windows and discuss ways to mitigate these risks effectively.
Understanding Permissions in Windows:
Before delving into the risks, let’s first understand how permissions work in Windows. Windows uses an Access Control List (ACL) to determine who can access and modify files and folders. The ACL includes individual permissions, such as Read, Write, and Execute, that can be assigned to different user accounts or groups. These permissions are hierarchical, with inheritance allowing permissions to be propagated from parent folders to child folders and files.
The Risks of Overly Permissive Permissions:
When permissions are set too loosely or assigned without proper consideration, several risks arise that can compromise the security of our systems and data. Here are some key risks associated with overly permissive permissions in Windows:
1. Unauthorized Access: Open permissions can allow unauthorized users or malware to access sensitive files or folders. This can result in data breaches, unauthorized modifications, or theft of valuable information.
2. Accidental Deletion or Modification: When permissions are too open, any user can accidentally delete or modify critical files, leading to data loss or system instability. This risk is particularly high in shared environments, such as business networks or public computers.
3. Malicious Actions: Permissive permissions pave the way for potential cyber-attacks, including the execution of malicious scripts or the installation of unauthorized software. Malware can exploit open permissions to spread across systems or manipulate sensitive data undetected.
4. Compliance and Legal Issues: Organizations that handle sensitive data, like customer information or intellectual property, must comply with various data protection regulations. Failure to implement strict permissions can result in legal consequences and damage the organization’s reputation.
Mitigating the Risks:
To ensure a secure computing environment and safeguard our data, it is essential to address overly permissive permissions effectively. Consider the following best practices for managing Windows permissions:
1. Principle of Least Privilege: Follow the principle of least privilege by granting users only the minimum permissions necessary to perform their tasks. Avoid providing administrative privileges to standard users to limit their ability to modify system components.
2. Regular Permission Audits: Regularly review and audit permissions on files, folders, and network shares. Remove unnecessary permissions and ensure that access is granted based on user roles or necessary tasks. Tools like Microsoft’s AccessEnum can assist in auditing permissions effectively.
3. Limit Inherited Permissions: When assigning permissions, avoid excessive inheritance. Instead, grant permissions directly to individual files or folders, reducing the risk of granting broader access inadvertently.
4. Strong Password Policies: Enforce strong password policies to prevent unauthorized access. Passwords should be complex, regularly updated, and not shared among users. Utilizing multi-factor authentication adds an extra layer of security.
5. File and Folder Encryption: Consider encrypting sensitive files and folders using tools like BitLocker or third-party solutions. Encryption protects data even if permissions are compromised, ensuring confidentiality.
6. Regular Software Updates and Patches: Keep your operating system and software up-to-date with the latest security patches. These updates often address vulnerabilities that could be exploited due to overly permissive permissions.
FAQs:
Q1. How can I check permissions on a file or folder in Windows?
A1. Right-click on the file or folder, select “Properties,” and navigate to the “Security” tab. Here, you can view the permissions assigned to individual users or groups.
Q2. What should I do if I suspect I have overly permissive permissions?
A2. Conduct a thorough permissions audit using tools like AccessEnum or PowerShell commands. Correct any unnecessary permissions and ensure access is limited to only necessary users.
Q3. Are there any built-in tools in Windows to help manage permissions effectively?
A3. Yes, Windows provides tools like Active Directory (for domain environments), Group Policy Management, and Access Control Lists (ACLs) to manage and enforce permissions across networks and systems.
Q4. Are there any automated solutions to manage Windows permissions?
A4. Yes, various software and solutions are available to assist in managing permissions efficiently. Some popular options include SolarWinds Access Rights Manager, Varonis DataPrivilege, and ManageEngine ADAudit Plus.
Q5. How often should I review and update permissions?
A5. It is recommended to conduct regular permission audits, at least annually or whenever significant changes occur, such as personnel changes or system upgrades.
In conclusion, permissions that are too open in Windows pose a severe security risk. By implementing best practices such as the principle of least privilege, regular audits, and strong password policies, we can mitigate these risks effectively. Ongoing vigilance and staying up-to-date with the latest security practices are key to maintaining a secure computing environment and protecting our valuable data.
Permission Denied (Publickey,Gssapi-Keyex,Gssapi-With-Mic)
Introduction (100 words)
SSH (Secure Shell) is a widely used network protocol that allows secure remote access to servers and systems. However, when establishing an SSH connection, users may encounter various errors, such as “Permission Denied” with the extensions “publickey,” “gssapi-keyex,” and “gssapi-with-mic.” In this article, we will delve into the causes, troubleshooting steps, and potential solutions for addressing these errors, ensuring a successful SSH connection.
Understanding the “Permission Denied” Errors (250 words)
1. Publickey Extension:
The “Permission Denied (publickey)” error occurs when the server rejects the authentication attempt from the client using public key-based authentication. Public key-based authentication relies on generating a key pair, consisting of a public and private key, where the private key remains on the client, and the public key gets stored on the SSH server. The server verifies the client’s authenticity by decrypting a challenge with the public key.
2. GSSAPI-Keyex Extension:
GSSAPI (Generic Security Services Application Programming Interface) provides a framework for user authentication and secure communication between clients and servers. The “Permission Denied (gssapi-keyex)” error emerges when the server fails to negotiate the GSSAPI’s key exchange mechanism.
3. GSSAPI-with-Mic Extension:
GSSAPI-with-Mic is another GSSAPI extension that deals with message integrity checking. The “Permission Denied (gssapi-with-mic)” error occurs when the client fails to authenticate itself with the server during the GSSAPI-with-Mic mechanism.
Troubleshooting Steps (450 words)
1. Permission denied errors may arise due to incorrect file or directory permissions. Ensure that the SSH files, such as the ~/.ssh directory and authorized_keys file, have the correct permissions. Typically, the directory permissions should be set to 700 (drwx——), while the authorized_keys file should have permissions of 600 (-rw——-).
2. Verify that the correct public and private key pair is being used. Check that the public key is correctly placed on the server and linked to the appropriate user account.
3. In case of the “Permission Denied (publickey)” error, ensure the public key is properly formatted and saved in the authorized_keys file. It should be one key per line, without any line breaks or additional characters.
4. Disable password-based authentication and enable public key-based authentication in the SSH server configuration. This ensures that the server does not attempt password-based authentication, eliminating potential conflicts with public key authentication.
5. If the “Permission Denied (gssapi-keyex)” error occurs, first ensure that GSSAPI authentication is enabled on the server. Adjust the SSH server’s configuration file and enable the ‘GSSAPIAuthentication’ option.
6. Additionally, for the “Permission Denied (gssapi-keyex)” error, check the client’s GSSAPI libraries and verify if they are properly installed and up-to-date. Outdated or incompatible libraries can cause authentication failures.
7. If encountering the “Permission Denied (gssapi-with-mic)” error, ensure that the client’s GSSAPI libraries are correctly configured and that both the server and the client support the desired authentication method.
8. To debug and obtain more detailed error messages, increase the verbosity level of the SSH client by appending the “-v” option. This provides insights into the authentication process, aiding in troubleshooting.
Frequently Asked Questions (230 words)
Q1) Why am I receiving a “Permission Denied (publickey)” error when trying to SSH into my server?
A1) This error indicates that the server rejected your authentication attempt using the public key. Possible causes include incorrect file permissions, improper placement of the public key, or incorrect formatting of the authorized_keys file.
Q2) How can I resolve the “Permission Denied (gssapi-keyex)” error I’m encountering?
A2) The “Permission Denied (gssapi-keyex)” error appears when the server cannot negotiate the GSSAPI’s key exchange mechanism. Ensure GSSAPI authentication is enabled on the server and check the client’s GSSAPI libraries for compatibility and updates.
Q3) What should I do if I encounter the “Permission Denied (gssapi-with-mic)” error?
A3) The “Permission Denied (gssapi-with-mic)” error occurs when the client fails to authenticate during the GSSAPI-with-Mic mechanism. Make sure the server and the client support the desired authentication method and verify the configuration of the client’s GSSAPI libraries.
Q4) What are the risks of disabling password-based authentication?
A4) Disabling password-based authentication improves security by relying solely on public key authentication. However, it is crucial to ensure strong passphrase protection for the private key to prevent unauthorized access.
Conclusion (100 words)
“Permission Denied” errors in SSH, such as “publickey,” “gssapi-keyex,” and “gssapi-with-mic,” can be resolved by following systematic troubleshooting steps. Understanding the potential causes behind these errors and implementing appropriate solutions will ensure a successful SSH connection, providing secure remote access to systems and servers. Remember to double-check file permissions, verify key pairs, enable/disable required authentication methods, and keep GSSAPI libraries up-to-date to troubleshoot and resolve these errors effectively.
Load Key Bad Permissions
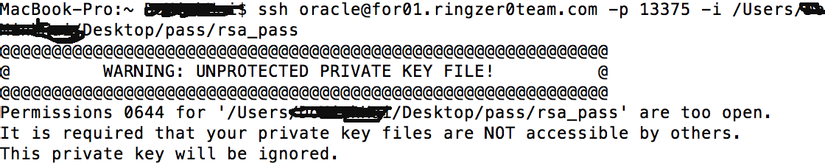
Load key bad permissions occur when an SSH client, such as OpenSSH, attempts to connect to a remote server using a private key for authentication. SSH private keys are encrypted files that serve as a secure means of authentication between the client and the server. However, the private key file must have appropriate permissions in order for the SSH client to read and load it successfully.
When the permissions on the private key file are incorrect, either too permissive or too restrictive, the SSH client fails to load the key and displays the “Load key bad permissions” error message. Improper file permissions can expose the private key to unauthorized access or prevent the SSH client from accessing it.
There are several possible causes for this error. The most common one is incorrect file permissions set on the private key file. The ideal permissions for a private key file are 600, meaning that only the owner of the file can read and write to it. If the permissions are set to 644 or higher, allowing read access for other users, the SSH client will refuse to load the key, resulting in the error message.
Another cause of this error is when the private key file is owned by a different user than the one running the SSH client. Since the private key file contains sensitive information, it should only be accessible by the user it belongs to. If the file ownership is incorrect, the SSH client will be unable to load the key, resulting in the error.
It’s worth noting that file permissions can be set differently based on the operating system used. While the standard permissions on Unix-like systems are denoted using octal notation (e.g., 600, 644), Windows systems utilize a different system to assign access permissions. Regardless of the specific operating system, it’s important to ensure that the private key file has the appropriate permissions and ownership to prevent the “Load key bad permissions” error.
To troubleshoot and resolve the “Load key bad permissions” error, follow these steps:
1. Verify the file permissions: Use the command `ls -l` (on Unix-like systems) or check the file properties (on Windows) to inspect the permissions of the private key file. Make sure the permissions are set to 600 for Unix-like systems or a similar appropriate setting on Windows.
2. Adjust the file permissions: If the permissions are incorrect, use the command `chmod 600
3. Check the file ownership: Verify that the private key file is owned by the same user running the SSH client. If the ownership is incorrect, use the command `chown
4. Ensure correct file location: Double-check that the SSH client is looking for the private key file in the correct location. If not, provide the correct path to the private key file in the SSH client configuration.
By following these troubleshooting steps, you should be able to resolve the “Load key bad permissions” error and successfully authenticate with the remote server using SSH.
FAQs:
Q: Why does the SSH client require specific file permissions for the private key file?
A: SSH client enforces strict file permissions to protect the private key’s confidentiality. Correct permissions ensure that only the owner of the key file can read or modify it, preventing unauthorized access.
Q: Can I change the permissions of the private key file to a less secure setting?
A: It is strongly discouraged to weaken the file permissions of the private key file. Doing so compromises the security of your SSH connection and increases the risk of unauthorized access to the remote server.
Q: I’ve changed the file permissions and ownership, but I still encounter the error. What should I do?
A: If the issue persists after adjusting the file permissions and ownership, double-check that the private key file is not corrupt or modified. Try generating a new private key and repeating the troubleshooting steps.
Q: Can this error occur if I’m using password authentication instead of private key authentication?
A: No, this error specifically pertains to the private key authentication method. If you are using password authentication, this issue should not arise.
In conclusion, the “Load key bad permissions” error occurs when the SSH client is unable to load the private key file due to incorrect file permissions. By ensuring the private key has the appropriate permissions and ownership, users can troubleshoot and resolve this error, successfully connecting to remote servers using SSH. Remember to adhere to specific file permission guidelines for your operating system and maintain the security of your private key to protect your SSH connections.
Images related to the topic permissions 0644 for are too open

Found 19 images related to permissions 0644 for are too open theme
























Article link: permissions 0644 for are too open.
Learn more about the topic permissions 0644 for are too open.
- ssh “permissions are too open” – Stack Overflow
- SSH: “Permissions 0644 for ‘my_key.pub’ are too open.”
- SSH Error “permissions are too open” for Private Key File
- SSH error: permissions are too open – Educative.io
- How to Fix “WARNING: UNPROTECTED PRIVATE KEY FILE …
- Unable to SSH with “Permissions for key are too open …
- Adding SSH private key gives error that 0644 permissions are …
- SSH: permissions 0644 for xxx are too open – Lixiang随笔
- Permissions 0644 for ‘devops.pem’ are too open. – How did I fix
- SSH Keys and their permissions – Chrysanthium
See more: nhanvietluanvan.com/luat-hoc