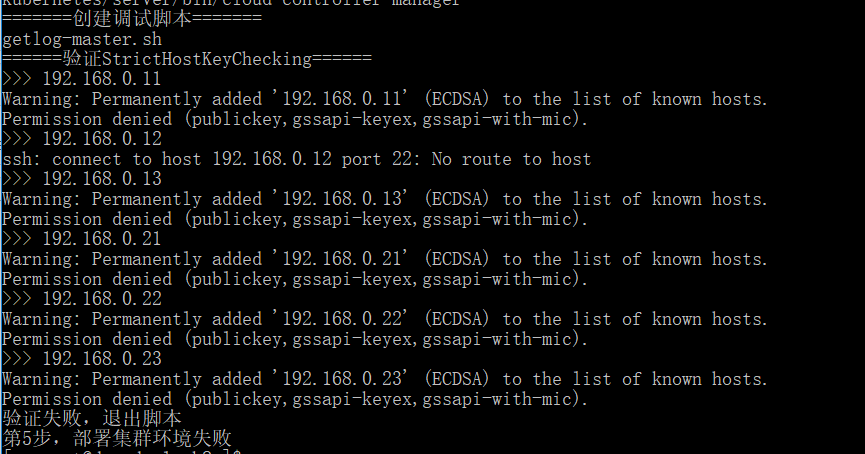
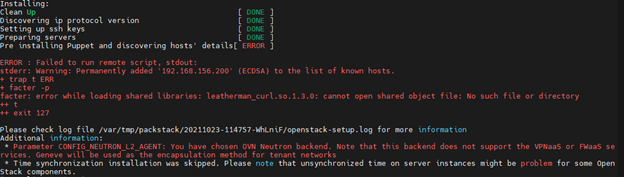
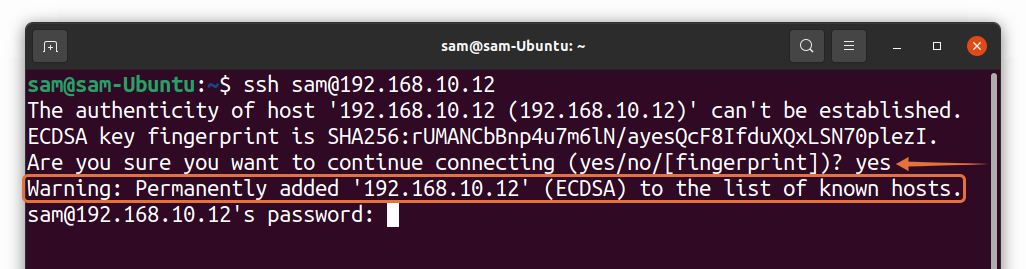
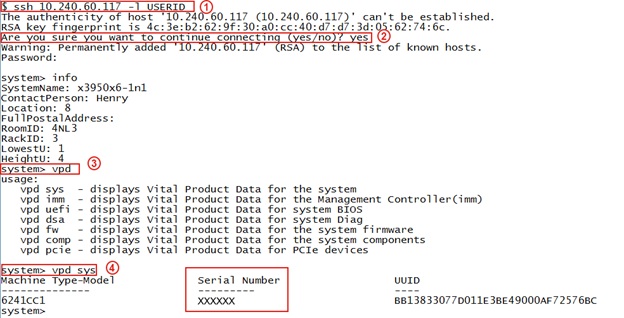
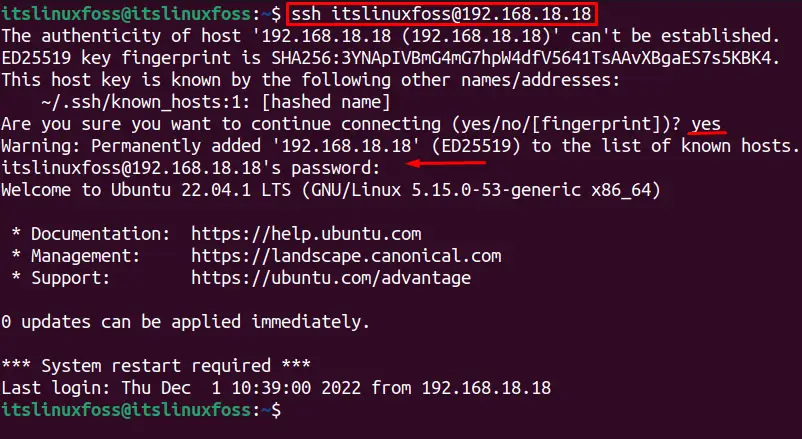
Permanently Added To The List Of Known Hosts.
Introduction
In the realm of computer security, SSH (Secure Shell) plays a vital role in authenticating and establishing secure connections. When connecting to remote systems or servers via SSH, you may encounter the message “Permanently added to the list of known hosts.” This article will delve into the concept of known hosts, the process of adding a host to the known hosts list, the associated benefits and risks, and how to manage the list effectively. We will also discuss alternatives to permanently adding a host to the known hosts list.
Understanding the Concept of Known Hosts
Known hosts are a fundamental aspect of SSH security. When SSH clients connect to a remote server, they exchange public key fingerprints to verify the authenticity of the connection. These fingerprints are stored in the known hosts file on the client machine. The known hosts file contains a list of trusted, previously connected server hostnames and their public key fingerprints.
Each time an SSH client connects to a server, it compares the received fingerprint with the ones stored in the known hosts file. If the fingerprints match, the client considers the connection secure. However, if the fingerprint is different or not found in the known hosts file, the client displays a warning to the user.
Adding a Host to the Known Hosts List
When connecting to a new server for the first time, the SSH client prompts you to confirm the authenticity of the host’s public key fingerprint. This is typically done by displaying the message “Warning: Permanently added ECDSA to the list of known hosts.” By responding affirmatively, you are adding the host and its fingerprint to the known hosts list.
The process of adding a host to the known hosts list is automatic and requires no manual configuration. The client retrieves the server’s fingerprint and saves it in the known hosts file, ensuring future connections can be reliably authenticated.
Benefits of Permanently Adding a Host to the Known Hosts List
1. Enhanced Security: By permanently adding a host to the known hosts list, SSH connections become more secure. The client can detect if the fingerprint changes, indicating a potential security breach or a man-in-the-middle attack.
2. Convenience: Once a host is added to the known hosts list, future connections to the same host will not prompt you to confirm the fingerprint. This eliminates the need for manual intervention during subsequent connections, enhancing user convenience.
Risks and Considerations When Permanently Adding a Host
While permanently adding a host to the known hosts list offers benefits, it is crucial to consider the associated risks:
1. Man-in-the-Middle Attacks: If an attacker manages to intercept the SSH connection during the initial connection to a new host, they can present their own fingerprint and trick the client into adding it to the known hosts list. Therefore, it is essential to ensure secure connections during the first connection.
2. Authenticity of the Fingerprint: In some cases, the fingerprint displayed during the first connection may not be the expected one. This could be due to system administrator changes or migrating to a new server. It is important to verify the fingerprint through alternative channels (e.g., in-person, secure messaging) to ensure it is legitimate.
Managing the Known Hosts List
To effectively manage the known hosts list, consider the following:
1. Regular Updates: The known hosts list should be periodically reviewed and updated to remove entries that are no longer required or trusted. Regularly inspecting the list helps ensure that it remains accurate and secure.
2. Clearing Known Hosts: If you encounter the error message “Failed to add the host to the list of known hosts,” it may indicate a corruption or incorrect configuration of the known hosts file. In such cases, clearing the known hosts file (e.g., using the command “Git clear known_hosts”) will resolve the issue.
Alternatives to Permanently Adding a Host
In certain situations, you may prefer not to permanently add a host to the known hosts list. Alternatives include:
1. SSH List Known Hosts: The “ssh-keygen” command can be utilized to list the known hosts on a machine. This allows you to review and manage the list accordingly.
2. Temporary Trust: When connecting to a new server, you can temporarily trust the host fingerprint for the current session only instead of permanently adding it. This offers a more cautious approach, particularly when connecting to unfamiliar servers.
3. Removing Known Hosts: If a host in the known hosts list becomes compromised or its fingerprint changes unexpectedly, it is advisable to remove it from the list to prevent potential security risks. This can be done manually or by using the appropriate command (e.g., “Remove known host sshpermanently added to the list of known hosts”).
Conclusion
Understanding the concept of known hosts and effectively managing the list is essential for maintaining secure SSH connections. By permanently adding a trusted host to the known hosts list, you enhance both security and convenience. However, it is crucial to remain vigilant about potential risks and consider the alternatives available for managing and securing your SSH connections effectively.
Is It Dangerous To Clone,Warning About Permanently Added ” To List Of Known Hosts?
What Is The Known Hosts Entry?
When it comes to secure communication networks, the “known hosts entry” plays a critical role. Specifically, it refers to a file used in the implementation of Secure Shell (SSH), a widely-used cryptographic network protocol. This entry ensures the authenticity of remote services and hosts, allowing users to verify their identities and secure their data transmission.
The known hosts entry is typically found in an SSH client’s configuration directory. This file, named “known_hosts,”contains a record of public keys associated with servers or hosts a user has previously connected to. Each entry in this file consists of the host name, IP address, and the public key of the remote server or host. When establishing a connection, the SSH client checks this file to compare the presented public key with the stored one. If these keys match, the client confirms the authenticity of the remote host, enabling secure communication.
Importance of the known hosts entry
The known hosts entry provides several essential benefits for secure communication networks:
1. Identity Verification: By checking the remote server or host’s public key, the known hosts entry helps users ensure they are connecting to the intended destination. This mechanism prevents Man-in-the-Middle attacks, where unauthorized actors intercept and manipulate data transmissions.
2. Protection from Spoofing: The known hosts entry guards against malicious users attempting to impersonate a host. If the presented public key does not match the stored key, SSH warns the user about a potential impersonation attempt. This prompts users to exercise caution and take necessary security measures.
3. Simplified Authentication: Once a remote server or host has been authenticated, the known hosts entry eliminates the need for repeated verification on subsequent connections. This streamlines the process, saving time and effort for users accessing frequently visited services.
4. Trust Management: The known hosts entry enables users to manage the trust level of remote hosts. By examining the stored public keys, users can identify any changes or discrepancies, informing their decisions about whether to establish a connection or investigate further.
Frequently Asked Questions (FAQs):
Q1. Can the known hosts entry be modified or updated?
A1. Yes, the known hosts entry can be modified manually. If a server’s public key changes or if a new server is added, the corresponding entry in the file should be updated accordingly. However, it is important to exercise caution when editing this file to avoid any accidental changes or deletions, which may lead to authentication issues.
Q2. What happens if a public key in the known hosts entry doesn’t match the one presented by the remote host?
A2. If the public key presented by the remote host differs from the one stored in the known hosts entry, SSH issues a warning message indicating a potential security threat. The user must then decide whether to proceed with the connection, investigate further, or terminate the connection.
Q3. Can the known hosts entry become a security vulnerability?
A3. While the known hosts entry is crucial for secure communication, it can potentially become a vulnerability if not managed carefully. Attackers can exploit this file to trick users into connecting to malicious hosts. Users should regularly review their known hosts entries, verify the authenticity of hosts, and promptly remove unrecognized or suspicious entries.
Q4. Are there any tools available to manage the known hosts entry?
A4. Various tools exist to simplify the management of known hosts entries. SSH clients often include built-in functionality to add, remove, or verify entries. Additionally, there are external tools that provide more advanced features and facilitate large-scale management of known hosts entries in enterprise environments.
Q5. Can the known hosts entry be shared between different SSH clients?
A5. Yes, the known hosts entry is portable and can be shared between different SSH clients. This allows users to maintain consistency across different devices or platforms, ensuring a streamlined and secure user experience.
In conclusion, the known hosts entry serves as a linchpin for establishing secure communication through SSH. By verifying the authenticity of remote hosts, users can confidently transmit data without the risk of interception or impersonation. Understanding the importance of this entry and effectively managing it is vital to safeguarding networks and maintaining secure connections.
What Is Known Hosts In Ssh?
Secure Shell (SSH) is a cryptographic network protocol used for secure communication between two devices, typically a client and a server. It provides a secure channel over an unsecured network by employing encryption techniques. The known hosts in SSH play a vital role in maintaining the security and integrity of SSH connections.
When a client attempts to connect to a remote server using SSH for the first time, a session key is established to encrypt the subsequent communication. However, it’s essential to verify the authenticity of the server to prevent man-in-the-middle attacks, where an attacker intercepts the communication and poses as the intended server.
SSH incorporates a mechanism known as known hosts to ensure the server’s identity can be authenticated securely. The known hosts file, usually named “known_hosts,” stores the fingerprints of the remote SSH server’s public key. As the clients connect to various servers, the SSH client software automatically adds the server’s public key fingerprint to the known hosts file.
The public key fingerprint is a cryptographic hash generated from the server’s public key. It uniquely identifies the server and ensures that any future connections to the same server can be verified against the stored fingerprint. If the fingerprint doesn’t match or is missing from the known hosts file, SSH will issue a warning to the user, indicating a potential security compromise.
SSH clients store the known hosts file in the user’s home directory, typically located at ~/.ssh/known_hosts. This file may contain multiple entries representing various SSH servers the client has connected to in the past. The entries include the server’s IP address or hostname, the encryption algorithm used, the public key fingerprint, and any additional comments.
When a client connects to a server, the SSH client software retrieves the server’s public key from the remote server. It then follows a series of steps to verify if the public key matches the one stored in the known hosts file. If the fingerprint matches, the client proceeds with the connection, establishing a secure and encrypted channel. However, if the fingerprint doesn’t match or is not found in the known hosts file, the client warns the user of a potential security risk and gives the option to proceed or abort the connection.
FAQs about Known Hosts in SSH:
Q: Can the known hosts files be edited manually?
A: Yes, the known hosts file can be edited manually using a text editor. However, it is recommended to use SSH utilities or commands to add or delete entries to avoid any syntax errors.
Q: Can known hosts prevent all types of man-in-the-middle attacks?
A: Known hosts provide protection against server identity spoofing, which is a common type of man-in-the-middle attack. However, other attacks like DNS spoofing or compromised client systems can still pose threats.
Q: Can I just ignore the warnings and proceed with the connection?
A: While it is possible to proceed with the connection after the warning, it is strongly advised not to ignore the warnings unless you are absolutely certain about the server’s identity. Ignoring the warnings can potentially expose your communication to eavesdropping or other security risks.
Q: What should I do if the known hosts file gets too large or cluttered?
A: The known hosts file can become cluttered over time, especially if you connect to numerous servers. You can remove specific entries manually or use SSH commands to clean up or manage the known hosts file.
Q: Can I disable the known hosts check to simplify the connection process?
A: Yes, it is possible to disable the known hosts check, but it is not recommended. Disabling it can leave your SSH connections vulnerable to man-in-the-middle attacks.
In conclusion, known hosts in SSH provide an essential security measure to verify the authenticity of remote SSH servers. By storing and comparing public key fingerprints, SSH clients ensure that subsequent connections to the same server are secure and legitimate. Users should always pay attention to the warnings issued by SSH clients and take necessary precautions to prevent unauthorized access and potential security compromises.
Keywords searched by users: permanently added to the list of known hosts. Ssh list known hosts, Warning: Permanently added ECDSA to the list of known hosts Permission denied (publickey), Failed to add the host to the list of known hosts, [email protected]: permission denied (publickey)., This key is not known by any other names, Git clear known_hosts, host key verification failed., Remove known host ssh
Categories: Top 80 Permanently Added To The List Of Known Hosts.
See more here: nhanvietluanvan.com
Ssh List Known Hosts
The known_hosts file serves as a trust inventory for SSH clients, ensuring the authenticity and integrity of remote systems. When connecting to a previously accessed server, the client compares the server’s host key fingerprint to the one stored in known_hosts. If they match, the connection is established without any security warnings or prompts. However, if the fingerprint has changed, a security warning is displayed, indicating a potential security risk.
By storing the server’s public key in known_hosts, SSH prevents “man-in-the-middle” attacks, where an adversary intercepts your traffic and poses as the remote server. Checking the host key fingerprint helps guarantee that you are connecting to the correct server without any tampering. This security feature is crucial to protect sensitive data and ensure the integrity of remote systems.
The known_hosts file is typically located in the user’s home directory, specifically at ~/.ssh/known_hosts. The tilde (~) symbol represents the home directory. However, it should be noted that some systems may use a different location based on their configuration. It’s essential to consult your system’s documentation or administrator to confirm the location if it differs from the default.
To view the content of known_hosts, you can use the command-line tool “ssh-keygen” with the “-F” flag followed by the server’s hostname or IP address. For example:
“`bash
ssh-keygen -F example.com
“`
This command will display the key fingerprint and other details related to the specified server. Alternatively, you can open the known_hosts file in a text editor to view its contents directly.
While the known_hosts file plays a critical role in SSH security, it can sometimes pose challenges. For example, in certain scenarios like server reconfiguration or IP address changes, the server’s host key fingerprint may change. Consequently, if you attempt to connect to the modified server, SSH will display a warning because the fingerprint in known_hosts no longer matches.
To overcome this issue, you have a few options. The simplest approach would be to delete the entry related to the modified server from known_hosts. However, this may leave your connection vulnerable to a man-in-the-middle attack. To maintain security while removing the warning, you can update known_hosts with the new host key fingerprint. The updated fingerprint can typically be obtained from the system administrator or the server’s documentation.
To remove a specific entry from known_hosts, you can use the following command:
“`bash
ssh-keygen -R example.com
“`
This command removes the entry matching the specified server hostname or IP address from the known_hosts file. Once the entry is removed, the next connection attempt will prompt a security warning, allowing you to update the host key fingerprint.
In case you want to remove all entries from known_hosts and start fresh, you can either delete the file manually or use the following command:
“`bash
> ~/.ssh/known_hosts
“`
This command truncates the known_hosts file, effectively deleting all entries within it.
Now let’s address some frequently asked questions related to the SSH known_hosts file:
**Q: Can I automate the management of the known_hosts file?**
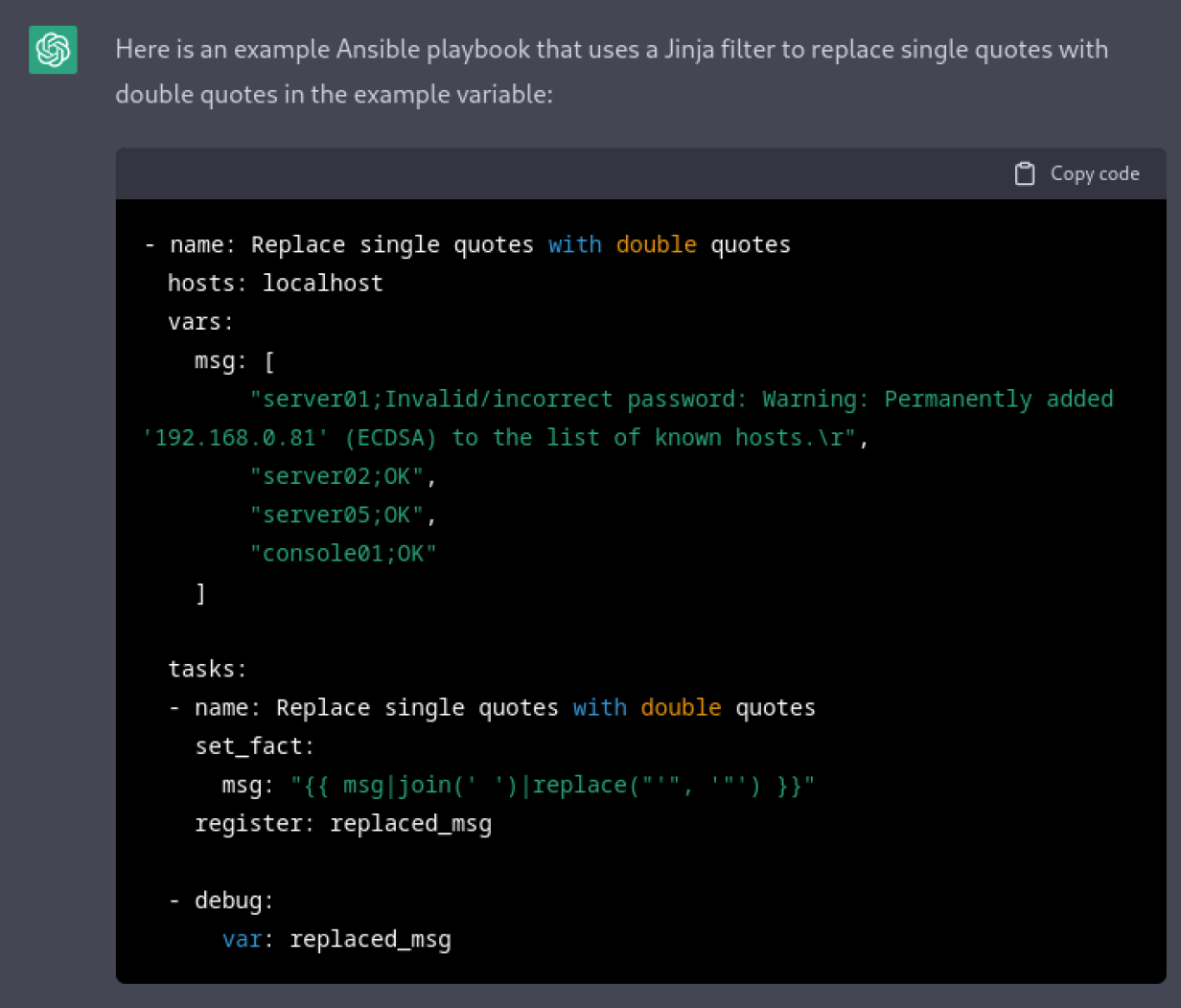
A: Yes, you can automate the management of the known_hosts file using configuration management tools like Ansible, Puppet, or Chef. These tools can help you update the known_hosts file across multiple systems, ensuring consistency and security.
**Q: Are there any security risks associated with the known_hosts file?**
A: Generally, the known_hosts file enhances security by protecting against forged or tampered connections. However, it’s important to ensure the security of the file itself. Make sure the permissions on the known_hosts file and its parent directory are properly set to prevent unauthorized access.
**Q: Can I disable host key checking for SSH connections?**
A: Disabling host key checking eliminates the security benefits provided by the known_hosts file. It is not recommended unless you are entirely confident about the authenticity of the remote systems you’re connecting to. Incorrectly configured SSH connections can leave you vulnerable to attacks. It is advisable to review the server’s key fingerprint manually before disabling host key checking.
**Q: How often should I update the known_hosts file?**
A: Ideally, you should update the known_hosts file whenever the host key fingerprint of a server changes. This could occur when the server undergoes significant changes, such as reconfiguration, relocation, or an IP address change. Regularly reviewing and updating the file will help maintain the security and integrity of your SSH connections.
In conclusion, the known_hosts file is a critical component of SSH security, ensuring the authenticity and integrity of remote systems. By storing the server’s public key fingerprint, SSH protects users against man-in-the-middle attacks and guarantees secure connections. Managing the known_hosts file effectively requires updating entries when server configurations change while maintaining security precautions. Understanding the purpose and proper management of the known_hosts file is essential for secure and reliable SSH connections.
Warning: Permanently Added Ecdsa To The List Of Known Hosts Permission Denied (Publickey)
Have you ever come across the error message “Warning: Permanently added ECDSA to the list of known hosts Permission denied (publickey)” while trying to connect via SSH or use Git? If so, you’re not alone. This error can be frustrating to deal with, especially if you’re not familiar with the underlying causes and potential solutions. In this article, we will delve into the details of this error, its possible causes, and provide a comprehensive guide to resolving the issue.
What does the error message mean?
When you attempt to connect to a remote server via SSH or use Git to interact with a remote repository, your local machine verifies the authenticity of the server’s identity using known host keys. These known host keys are stored in a file, typically located in the ~/.ssh directory, on your local machine.
The error message “Warning: Permanently added ECDSA to the list of known hosts Permission denied (publickey)” typically appears when your local machine is unable to establish a secure, authenticated connection with the remote server. It indicates that your public key, which is used to verify your identity, has been denied permission to access the server.
Causes of the error
1. Incorrect permissions: One of the most common causes of this error is incorrect permissions on the server’s side. If the permissions for the authorized_keys file or the ~/.ssh directory are not set correctly, the server will deny the public key access, resulting in the error message.
2. Incorrect public key: Another possible cause is an incorrect or mismatched public key. If the public key on the server does not match the private key on the client’s machine, authentication will fail, and the error message will appear.
3. Invalid or expired host key: Host keys can become invalid or expire over time, especially when servers undergo maintenance or upgrades. If the host key on the server has changed but your local machine still has the old key stored, authentication will be denied, triggering the error.
4. Firewall or port restrictions: In some cases, firewalls or port restrictions on either the client or server side can prevent a successful SSH or Git connection. If the required ports are blocked or the necessary firewall rules are not in place, the connection will fail, resulting in the error message.
5. Server misconfiguration: Improper server configuration, such as disabled SSH access or incorrect SSH server settings, can also lead to this error. If the server is not properly set up to handle connections, the access will be denied.
Resolving the error message
Now that we understand the possible causes of the error, let’s explore some solutions to resolve it:
1. Verify file permissions: Ensure that the permissions for the authorized_keys file and the ~/.ssh directory on the server are set correctly. The authorized_keys file should have restricted permissions (600) and the ~/.ssh directory should have permissions set to 700.
2. Check public key: Verify that your public key on the server matches the private key on your local machine. If they don’t match, you may need to regenerate your keys and update them on both the client and server sides.
3. Update known_hosts file: If the warning persists even after verifying the file permissions and key matching, it may be necessary to remove the outdated host key from the known_hosts file on your local machine. You can do this by editing the file manually or using SSH commands like ssh-keygen -R
4. Check firewall and port restrictions: Ensure that port 22, which is the default SSH port, is open and accessible on both the client and server sides. Additionally, check for any firewall rules or restrictions that could be blocking the connection and modify them accordingly.
5. Troubleshoot server configuration: Double-check SSH server settings and ensure that SSH access is enabled. Consult server documentation or reach out to the server administrator or hosting provider for assistance in identifying and rectifying any misconfigurations.
FAQs:
Q: I’ve verified the file permissions and key matching, but the error persists. What should I do?
A: In this case, try removing the outdated host key from the known_hosts file on your local machine. Additionally, restarting the SSH service on both the client and server sides can also help.
Q: Can this error occur even with valid credentials?
A: Yes, even with valid credentials, this error can still occur due to issues like incorrect file permissions, expired host keys, or misconfigured servers.
Q: Is it safe to remove the outdated host key from the known_hosts file?
A: Removing the outdated host key from the known_hosts file merely removes the stored record of the old key. It does not compromise security, as the next connection attempt will prompt for the new key to be added, ensuring secure verification.
Q: Why did the error suddenly appear even though I was previously able to connect without any issues?
A: The sudden appearance of the error can be attributed to changes on the server’s side, such as key rotation, server upgrades, or modifications to the SSH configuration.
In conclusion, the error message “Warning: Permanently added ECDSA to the list of known hosts Permission denied (publickey)” is often encountered while attempting SSH or Git connections. Understanding the potential causes, from incorrect permissions to server misconfigurations, is crucial in troubleshooting and resolving the error. By following the suggested solutions and consulting additional resources as needed, users can successfully establish secure connections and regain access to remote servers or repositories.
Images related to the topic permanently added to the list of known hosts.

Found 42 images related to permanently added to the list of known hosts. theme




![Linux] ssh No route to host 에러 Linux] Ssh No Route To Host 에러](https://velog.velcdn.com/images/xeomina/post/a5537d07-5a97-432e-8806-a9e869325380/image.png)



![I've done something daft (TM) [and hosed my network connection] - General - Rocky Linux Forum I'Ve Done Something Daft (Tm) [And Hosed My Network Connection] - General - Rocky Linux Forum](https://global.discourse-cdn.com/business7/uploads/rockylinux/original/2X/3/396a9593380736c29f025bcb4efb176ccd2ebd80.jpeg)








![Ansible] 2. Cách xác thực SSH đối với Server Linux - Đỗ Trung Quân Ansible] 2. Cách Xác Thực Ssh Đối Với Server Linux - Đỗ Trung Quân](https://dotrungquan.info/wp-content/uploads/2021/12/CleanShot-2021-12-19-at-13.06.48.png)




![EPC-R7200]About building an environment on the host - Software - Advantech AIM-Linux Community Epc-R7200]About Building An Environment On The Host - Software - Advantech Aim-Linux Community](https://global.discourse-cdn.com/standard11/uploads/aim_linux/original/1X/4780b33288f58f4e88ad375651da0c590a258256.png)



Article link: permanently added to the list of known hosts..
Learn more about the topic permanently added to the list of known hosts..
- Git says “Warning: Permanently added to the list of known hosts”
- Permanently add host to the list of known hosts (SSH)
- Permanently added ‘github.com,140.82.x.x’ (ECDSA) to the list …
- What is known_hosts File in Linux [Everything to Know]
- Known Hosts File – Glossary | CSRC
- Updating host keys – DreamHost Knowledge Base
- Managing Your SSH known_hosts Using Git – JamieWeb.net
- “Permanently added the RSA host key” what does it mean?
- How to fix warning about ECDSA host key – Super User
- Permanently added host key” Message When Opening SSH …
- 1.2 SSH Host Keys
- Warning: Permanently added ‘111.222.33.40’ (ECDSA) to the …
See more: nhanvietluanvan.com/luat-hoc