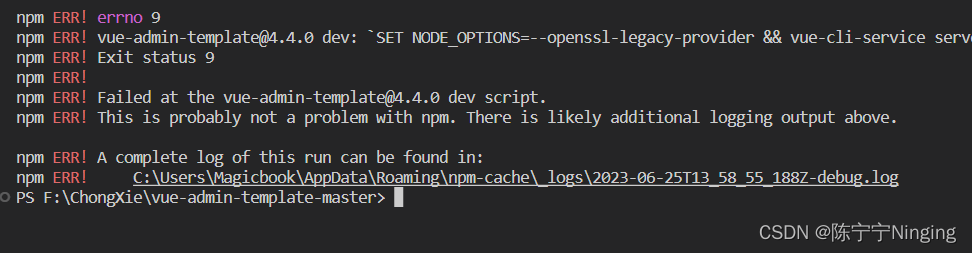
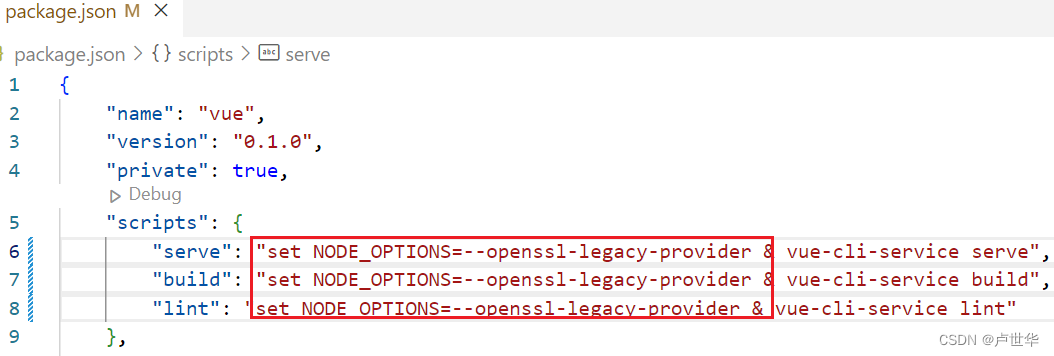
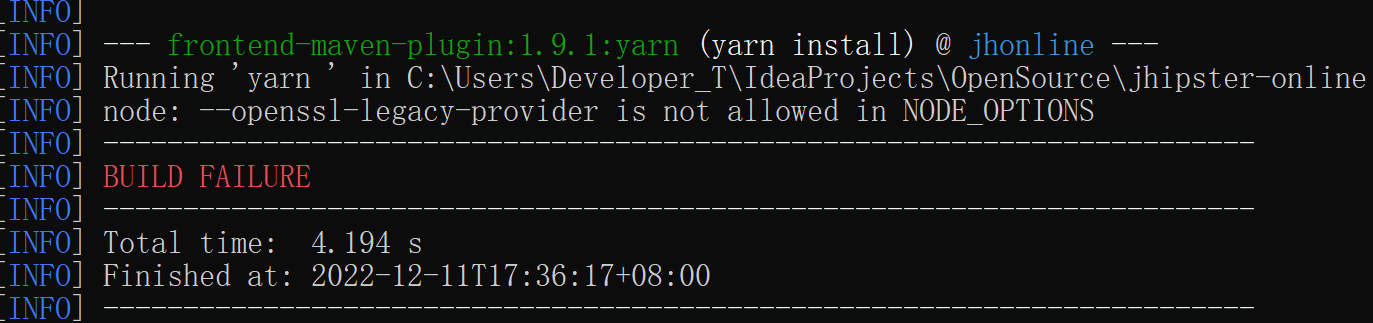
Node: –Openssl-Legacy-Provider Is Not Allowed In Node_Options
Node.js is a popular runtime environment for executing server-side JavaScript applications. It provides a range of features and functionalities to developers, including support for cryptographic operations. One of the options available for cryptographic operations in Node.js is the openssl-legacy-provider.
The openssl-legacy-provider is a cryptographic provider that utilizes the OpenSSL library for handling encryption, decryption, and other cryptographic operations. It is designed to work with older versions of Node.js and provides compatibility with legacy applications that rely on OpenSSL.
In previous versions of Node.js prior to v17, the openssl-legacy-provider was included as a default option for cryptographic operations. This allowed developers to leverage the OpenSSL library without any additional configuration. However, with the introduction of newer versions of Node.js, the inclusion of openssl-legacy-provider in the node_options has been disallowed.
Node_options in Node.js
Node_options in Node.js is a feature that allows developers to customize the runtime environment of their Node.js applications. It enables the modification of various runtime parameters and settings to optimize the performance and behavior of the application.
The node_options feature is significant as it allows developers to fine-tune their Node.js applications according to their specific requirements. It provides flexibility in choosing the runtime options that best suit the application’s needs, including enabling or disabling specific features, setting memory limits, and controlling the behavior of the garbage collector.
Exclusion of openssl-legacy-provider
The decision to disallow the inclusion of openssl-legacy-provider in node_options was driven by several reasons. One of the main concerns was the potential vulnerabilities and security risks associated with the use of OpenSSL in older versions of Node.js.
OpenSSL has had its fair share of security vulnerabilities in the past, and using older versions of the library can expose the application to known vulnerabilities. By removing the openssl-legacy-provider from node_options, Node.js aims to encourage developers to use newer and more secure cryptographic libraries and providers.
Implications for Node.js Developers
The removal of openssl-legacy-provider from node_options can have implications for existing codebases that rely on this cryptographic provider. Developers using Node.js versions prior to v17 will need to update their code to utilize alternative cryptographic providers supported by the newer versions of Node.js.
When upgrading Node.js versions, developers should also consider any dependencies or third-party modules that may still rely on the openssl-legacy-provider. Ensuring compatibility and addressing any potential issues during the migration process is crucial to maintaining the security and functionality of the application.
Alternative Options for Cryptographic Operations
Node.js provides a range of alternative options for cryptographic operations, ensuring that developers can still perform encryption, decryption, and other cryptographic tasks securely. The newer versions of Node.js support alternative cryptographic providers like the built-in Web Crypto API, the NodeJS Crypto module, and third-party libraries such as bcrypt and sodium.
These alternative providers offer modern and secure cryptographic algorithms and techniques, reducing the likelihood of vulnerabilities and ensuring the confidentiality and integrity of sensitive data.
Recommended steps for migrating from openssl-legacy-provider
Migrating from openssl-legacy-provider to alternative cryptographic providers requires careful planning and implementation. Here are some recommended steps for developers:
1. Identify the dependencies: Analyze the codebase and determine all dependencies and third-party modules that rely on the openssl-legacy-provider.
2. Update dependencies: Ensure that all dependencies are updated to versions that support alternative cryptographic providers.
3. Refactor code: Update the codebase to utilize the alternative cryptographic providers. Replace any calls to the openssl-legacy-provider with the appropriate functions or methods from the chosen provider.
4. Test thoroughly: Conduct thorough testing to ensure that the migration process does not introduce any new bugs or vulnerabilities. Pay particular attention to the correctness and security of cryptographic operations.
Ensuring Security in Node.js Applications Post-Migration
Migrating away from openssl-legacy-provider is one step in ensuring the security of Node.js applications. However, maintaining a secure application requires ongoing effort and attention. Here are some best practices to consider:
1. Stay up-to-date: Regularly update Node.js and all dependencies to the latest versions that include security patches and fixes.
2. Implement secure coding practices: Follow secure coding practices and guidelines to minimize the risk of introducing vulnerabilities. This includes validating and sanitizing user input, avoiding known security pitfalls, and properly configuring security-related settings.
3. Regularly assess security posture: Conduct regular security assessments and audits to identify any potential vulnerabilities or weaknesses in the application. This includes conducting penetration testing, code reviews, and vulnerability scanning.
Future Developments and Potential Enhancements
Node.js is continuously evolving, and future versions are likely to introduce improvements and enhancements to cryptographic libraries and providers. The Node.js community is actively working on strengthening the security of cryptographic operations and exploring new options for developers.
Potential developments include the integration of additional cryptographic libraries, the introduction of new algorithms and techniques, and improvements to the overall security posture of Node.js. Developers should stay updated with the latest developments in this area to leverage the most secure and efficient cryptographic options available.
FAQs
1. Can I still use openssl-legacy-provider in Node.js versions after v17?
No, openssl-legacy-provider is not allowed in node_options in Node.js versions after v17.
2. What are the potential security risks of using openssl-legacy-provider?
Using openssl-legacy-provider in older versions of Node.js can expose the application to known vulnerabilities in the OpenSSL library. It is recommended to use alternative cryptographic providers supported by newer versions of Node.js for improved security.
3. How can I migrate my Node.js application from openssl-legacy-provider to alternative providers?
To migrate from openssl-legacy-provider, identify and update dependencies, refactor the code to utilize alternative providers, and thoroughly test the application for correctness and security.
4. What are the recommended cryptographic providers supported by Node.js?
Node.js supports alternative cryptographic providers such as the Web Crypto API, the NodeJS Crypto module, and third-party libraries like bcrypt and sodium.
5. How can I ensure the security of my Node.js application post-migration?
Ensure the security of your Node.js application post-migration by regularly updating Node.js and dependencies, implementing secure coding practices, and conducting regular security assessments.
6. What are the future developments in cryptographic libraries and providers in Node.js?
The Node.js community is continuously working on improving the security of cryptographic operations. This includes integrating additional libraries, introducing new algorithms, and enhancing the overall security posture of Node.js. Stay updated with the latest developments in the Node.js community for the most secure cryptographic options.
Opensslerrorstack:[ Error :Digital Envelope Routines Digital Envelope Routines Reason: Unsupported ]
Keywords searched by users: node: –openssl-legacy-provider is not allowed in node_options export node_options=–openssl-legacy-provider, bad option: –openssl-legacy-provider, Unset NODE_OPTIONS, ‘node_options’ is not recognized as an internal or external command, operable program or batch file., OpenSSL legacy provider failed to load, Export NODE_OPTIONS openssl-legacy-provider vue cli service serve, Node-cmd, FROM node 16
Categories: Top 37 Node: –Openssl-Legacy-Provider Is Not Allowed In Node_Options
See more here: nhanvietluanvan.com
Export Node_Options=–Openssl-Legacy-Provider
In recent times, the open-source JavaScript runtime environment, Node.js, has gained immense popularity due to its ability to build scalable and efficient network applications. To keep up with the ever-evolving technology landscape, Node.js frequently introduces updates and enhancements. One of these updates is the export node_options=–openssl-legacy-provider flag, which has generated considerable interest among developers. In this article, we will explore what this flag entails, its significance, and address some commonly asked questions related to its usage.
Understanding Node.js and OpenSSL
Before diving into the specifics of the export node_options=–openssl-legacy-provider flag, it is essential to comprehend the two primary components involved: Node.js and OpenSSL.
Node.js: As mentioned earlier, Node.js is a runtime environment utilized for executing JavaScript code outside of a browser. It offers developers a powerful platform to build a wide range of applications, including web servers, command-line tools, and even robotics. Known for its high performance and non-blocking I/O capability, developers leverage Node.js to create scalable and event-driven applications.
OpenSSL: OpenSSL is an open-source library that provides cryptographic functionalities, including secure communication over computer networks. It offers protocols such as Transport Layer Security (TLS) and Secure Sockets Layer (SSL), which are crucial for encrypting data during transmission. Additionally, OpenSSL provides various cryptographic algorithms, ensuring data integrity and security.
Introducing the export node_options=–openssl-legacy-provider Flag
The export node_options=–openssl-legacy-provider flag is a configuration option that influences how Node.js interacts with its underlying OpenSSL library. By default, Node.js utilizes the system version of OpenSSL present in its environment. However, with the introduction of this flag, developers can now instruct Node.js to use the legacy OpenSSL provider. This allows developers to have more control over their application’s encryption capabilities and the libraries they rely on.
Significance and Benefits
The export node_options=–openssl-legacy-provider flag holds several benefits for Node.js developers. Let’s take a closer look at its significance:
1. Compatibility: The export node_options=–openssl-legacy-provider flag ensures backward compatibility with earlier versions of OpenSSL. This is especially useful when developers are working with legacy codebases that rely on specific OpenSSL features and may not be compatible with newer versions. By using this flag, developers can ensure their applications continue to function without disruption.
2. Stability: OpenSSL is an integral part of Node.js and plays a vital role in providing secure communication channels. However, newer versions of OpenSSL sometimes introduce breaking changes, which can potentially impact the stability of existing Node.js applications. With the export node_options=–openssl-legacy-provider flag, developers can keep their applications secure while avoiding unexpected issues arising from updated OpenSSL versions.
3. Flexibility: Node.js provides developers with the freedom to choose the cryptographic libraries they prefer. By using the export node_options=–openssl-legacy-provider flag, developers can seamlessly leverage the legacy OpenSSL provider if it better suits their specific application requirements. This flexibility allows developers to fine-tune their applications’ security and performance characteristics.
Frequently Asked Questions (FAQs):
1. How do I enable the export node_options=–openssl-legacy-provider flag in my Node.js application?
To enable the export node_options=–openssl-legacy-provider flag, you simply need to set the environment variable before running your Node.js application. For instance, on Unix-based systems, you can run `export node_options=–openssl-legacy-provider` in your terminal or command prompt. Then, execute your Node.js application as usual.
2. What versions of Node.js support the export node_options=–openssl-legacy-provider flag?
The export node_options=–openssl-legacy-provider flag is available in Node.js versions 12 and above. It is advisable to ensure you are using the latest version of Node.js to take full advantage of this flag’s capabilities.
3. Will using the export node_options=–openssl-legacy-provider flag compromise the security of my Node.js application?
No, using the export node_options=–openssl-legacy-provider flag does not compromise the security of your Node.js application. It allows you to utilize the legacy OpenSSL provider for backward compatibility and stability purposes. However, it is crucial to stay up-to-date with security patches and best practices provided by the Node.js and OpenSSL communities.
4. Are there any performance implications when using the export node_options=–openssl-legacy-provider flag?
The performance implications depend on your specific use case. In some scenarios, the legacy OpenSSL provider may offer better performance compared to newer versions. However, it is recommended to benchmark and assess the performance impact in your particular application before making a final decision.
5. Can I enable the export node_options=–openssl-legacy-provider flag temporarily for specific parts of my code?
Yes, you can selectively enable the export node_options=–openssl-legacy-provider flag within specific parts of your codebase. To do this, create a separate Node.js process with the flag enabled and communicate with it via inter-process communication techniques.
In conclusion, the export node_options=–openssl-legacy-provider flag is a valuable addition to Node.js that offers backward compatibility, stability, and flexibility for developers. By leveraging this flag, developers can ensure their applications continue to function seamlessly with legacy codebases and control their chosen OpenSSL provider. As always, it is essential to stay informed about security best practices and the latest updates from the Node.js and OpenSSL communities to maintain a secure and robust application environment.
Bad Option: –Openssl-Legacy-Provider
Introduction:
When it comes to dealing with cryptographic protocols and securing sensitive data, OpenSSL acts as a widely acclaimed and widely-used toolkit. However, as technology advances, OpenSSL introduced a flag called –openssl-legacy-provider, aimed at providing compatibility with older versions. In this article, we will explore this flag in depth, shedding light on its limitations and why it should be approached with caution.
The –openssl-legacy-provider Flag:
The –openssl-legacy-provider flag is an option offered by OpenSSL, which allows users to select an older provider for cryptographic operations. This flag was introduced to ensure compatibility with outdated versions, offering a temporary solution for transition periods during upgrades. By specifying this flag, users may revert to the older provider, but it comes with its own set of setbacks.
Limitations and Drawbacks:
1. Reduced Security: One of the key concerns when using the –openssl-legacy-provider lies in the compromised security it implies. Older providers may lack the robustness, vulnerability fixes, and overall security enhancements present in the latest releases. Consequently, opting for the legacy provider risks exposing cryptographic processes to vulnerabilities prevalent in the outdated version.
2. Lack of Modern Algorithms: With each iteration of OpenSSL, new and improved cryptographic algorithms are introduced. These algorithms are designed to address the weaknesses or vulnerabilities identified in previous versions. By resorting to the –openssl-legacy-provider flag, users forego the benefits of these advancements, potentially exposing their systems to vulnerabilities that have since been resolved.
3. Depletion of Community Support: As software evolves, it is natural for developers and the entire community to shift their focus towards newer technologies and better practices. By relying on the –openssl-legacy-provider flag, users may find themselves using a provider with limited support and fewer experts available to address any issues that may arise while working with the outdated version.
4. Interoperability Challenges: Transitioning from an older version to a newer one generally requires improved interoperability, ensuring that different systems and software can communicate seamlessly. By using the –openssl-legacy-provider flag, users forfeit the opportunity to explore and capitalize on the advancements made in newer versions, potentially hindering interoperability if other systems have adopted the latest standards.
FAQs:
Q1. Can I use –openssl-legacy-provider to mitigate compatibility issues during an upgrade?
A1. While the –openssl-legacy-provider flag may offer some temporary relief during an upgrade, it is not recommended in the long run. It is better to address compatibility concerns by updating and adapting the software to the latest OpenSSL releases.
Q2. Are there any workarounds to mitigate the security risks associated with the legacy provider?
A2. The best approach is to keep the software up to date, utilizing the latest OpenSSL releases. In cases where compatibility issues are significant, seeking alternative solutions specifically designed for that purpose might be a better option.
Q3. Are there specific circumstances where –openssl-legacy-provider could be considered viable?
A3. In highly specific situations where there is a critical dependency on an outdated version and upgrading is unfeasible in the short term, the –openssl-legacy-provider flag might be temporarily employed with appropriate security measures. However, this should be regarded as a last resort.
Q4. Can I expect any improvements or updates for the –openssl-legacy-provider flag?
A4. Although OpenSSL maintains backward compatibility as much as possible, it is natural to shift the focus towards newer releases. Hence, the –openssl-legacy-provider may not receive significant updates or improvements in the future.
Conclusion:
While the –openssl-legacy-provider flag may seem like a tempting option to maintain compatibility during an upgrade, it comes with its fair share of limitations and drawbacks. To ensure optimal security, staying up to date with the latest OpenSSL releases and migrating away from outdated providers is highly recommended. As technology continues to evolve, keeping cryptographic protocols robust and secure necessitates embracing the advancements offered by newer versions rather than relying on legacy solutions.
Unset Node_Options
Introduction
Node.js is a popular and powerful JavaScript runtime environment known for its scalability, efficiency, and versatility. It offers several handy features and options to optimize and customize its behavior, catering to the specific needs of developers. One such option is the NODE_OPTIONS environment variable, which allows developers to configure various Node.js runtime options. However, in this article, we will explore the concept of unsetting NODE_OPTIONS and delve into its implications and benefits.
Understanding NODE_OPTIONS
Before we discuss unsetting NODE_OPTIONS, let’s take a closer look at what NODE_OPTIONS actually is. NODE_OPTIONS is an environment variable that enables developers to pass command-line options directly to Node.js. It acts as a way to set various runtime flags, such as enabling experimental features, changing the garbage collection behavior, or controlling memory limits.
The NODE_OPTIONS variable follows a specific syntax – it accepts a space-separated string of values, where each value represents a runtime option. For example, to enable Node.js’s experimental modules feature, you would set NODE_OPTIONS as follows:
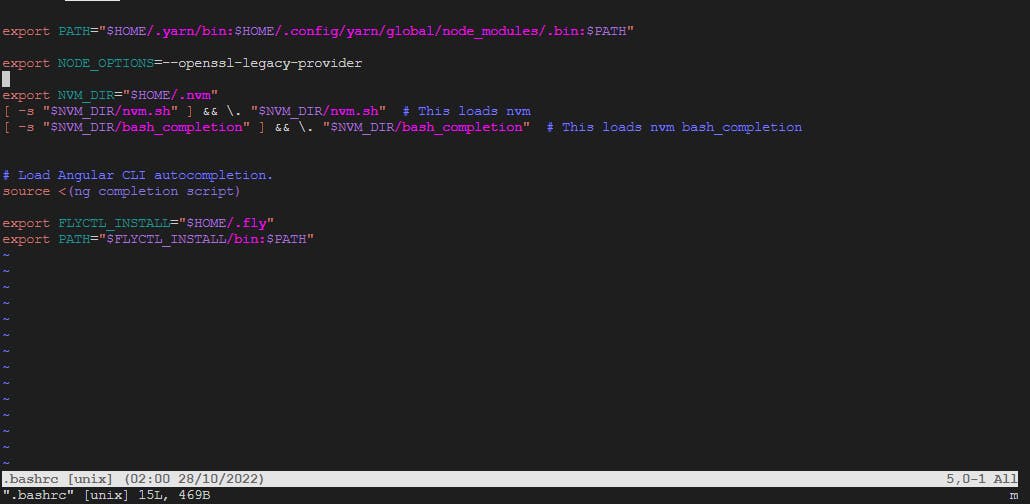
NODE_OPTIONS=”–experimental-modules”
With NODE_OPTIONS, developers have significant control over the Node.js runtime, enabling them to fine-tune the environment to best suit their application’s specific requirements.
Unsetting NODE_OPTIONS
While NODE_OPTIONS offers great flexibility, there may arise situations where unsetting or clearing the environment variable becomes necessary. Unsetting NODE_OPTIONS is done by simply removing or clearing its value. This can be achieved via the command line or by modifying the related configuration files.
Why Would You Unset NODE_OPTIONS?
There are various reasons why unsetting NODE_OPTIONS might be desirable. Let’s explore some common scenarios where developers may choose to do so:
1. Dependency Conflicts: In complex Node.js applications, different dependencies may require specific runtime flags or options. However, conflicts may arise when multiple modules or packages set contradictory options using NODE_OPTIONS. In such cases, unsetting NODE_OPTIONS allows the parent application to define the runtime behavior consistently.
2. Security Considerations: NODE_OPTIONS grants powerful capabilities to alter the runtime behavior, such as overriding security flags or enabling experimental features. In scenarios where security is a top priority, unsetting NODE_OPTIONS ensures that only the desired and secure runtime options are applied, reducing the potential for vulnerabilities.
3. Enhanced Portability: Node.js applications are often deployed across multiple environments. Some environments may not support or allow certain NODE_OPTIONS. By unsetting NODE_OPTIONS, developers can ensure consistent behavior across different deployment platforms.
4. Troubleshooting Performance Issues: NODE_OPTIONS can greatly affect the performance and resource usage of a Node.js application. Temporary unsetting of NODE_OPTIONS can help developers diagnose and identify the impact of specific options on application performance, allowing for better optimization and fine-tuning.
Frequently Asked Questions (FAQs)
Q1. How can I unset NODE_OPTIONS?
A1. To unset NODE_OPTIONS, you can simply remove or clear its value. For example, running `export NODE_OPTIONS=””` in your terminal will unset the variable.
Q2. Does unsetting NODE_OPTIONS affect the default runtime behavior?
A2. No, unsetting NODE_OPTIONS does not change the default runtime behavior of Node.js. It simply ensures that no custom options are applied from the environment variable.
Q3. Can I set NODE_OPTIONS programmatically within my Node.js application?
A3. Yes, NODE_OPTIONS can also be set programmatically within a Node.js application using the `process.env` object. However, unsetting NODE_OPTIONS via this method is not possible as it can only be modified outside the application’s runtime.
Q4. Is there an alternative to unsetting NODE_OPTIONS for managing conflicting options?
A4. Yes, if conflicting options are a concern, an alternative approach is to use individual flags or options directly through the command line or programmatically. This allows for specific control over the desired behavior, bypassing the need for NODE_OPTIONS.
Q5. Can unsetting NODE_OPTIONS impact the stability of my application?
A5. Unsetting NODE_OPTIONS alone does not impact the stability of the application. However, it may affect certain functionalities or behaviors that were dependent on the previous values of NODE_OPTIONS.
Conclusion
NODE_OPTIONS, as an environment variable, provides extensive customization capabilities to Node.js developers. However, the ability to unset or clear NODE_OPTIONS offers several benefits, including resolving dependency conflicts, enhancing security, ensuring portability, and troubleshooting performance issues. Understanding when and why to unset NODE_OPTIONS allows developers to optimize their Node.js applications effectively according to their specific needs.
Images related to the topic node: –openssl-legacy-provider is not allowed in node_options
![opensslErrorStack:[ error :digital envelope routines digital envelope routines reason: unsupported ] opensslErrorStack:[ error :digital envelope routines digital envelope routines reason: unsupported ]](https://nhanvietluanvan.com/wp-content/uploads/2023/07/hqdefault-794.jpg)
Found 49 images related to node: –openssl-legacy-provider is not allowed in node_options theme




Article link: node: –openssl-legacy-provider is not allowed in node_options.
Learn more about the topic node: –openssl-legacy-provider is not allowed in node_options.
- openssl-legacy-provider is not allowed in NODE_OPTIONS …
- openssl-legacy-provider is not allowed in NODE_OPTIONS
- openssl-legacy-provider is not allowed in NODE_OPTIONS
- node –openssl-legacy-provider is not allowed in node_options
- Problem : node: –openssl-legacy-provider is not allowed in …
- How To Fix the ERR_OSSL_EVP_UNSUPPORTED Error in …
- Command-line API | Node.js v20.4.0 Documentation
- How to set environment variables of nodejs? – Google Groups
See more: nhanvietluanvan.com/luat-hoc