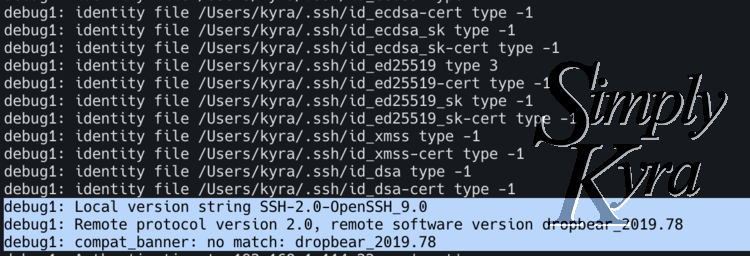
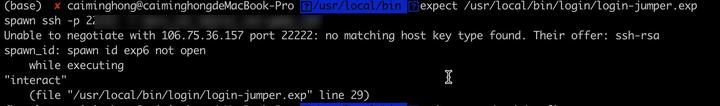
No Matching Host Key Type Found. Their Offer: Ssh-Rsa
Introduction (110 words):
Secure Shell (SSH) is a protocol that provides a secure way to access remote systems. Host key types are a crucial aspect of SSH, serving as unique identifiers for hosts. They ensure the authenticity and integrity of the SSH connections. However, encountering errors like “No Matching Host Key Type Found” can be frustrating, hindering the establishment of these connections. In this article, we will explore the significance of host key types in SSH, particularly focusing on the SSH-RSA key type. We will also discuss common troubleshooting techniques and alternative host key algorithms.
Host Key Types Overview (150 words):
Host key types provide the foundation for SSH connections, ensuring secure communications and protecting against impersonation and tampering. SSH supports various key types, such as RSA, DSA, ECDSA, and ED25519. Each type has its own strengths and weaknesses, making it important for users to understand their characteristics.
Why Host Key Types Matter in SSH (180 words):
Host key types play a critical role in the authentication process of SSH. They establish a secure trust relationship between the client and the server. When a client connects to a server for the first time, it receives the server’s public key. The client then verifies this key against a trusted set of host keys. If the keys match, the client can be confident that it is communicating with the correct server.
Understanding SSH-RSA as a Host Key Type (200 words):
SSH-RSA (Rivest-Shamir-Adleman) is one of the most widely used host key types in SSH. It is based on the RSA asymmetric encryption algorithm. The SSH-RSA key type generates an RSA public and private key pair, ensuring secure authentication and encryption of data during SSH connections. However, recent advancements in cryptographic algorithms have led to the emergence of new, stronger key types.
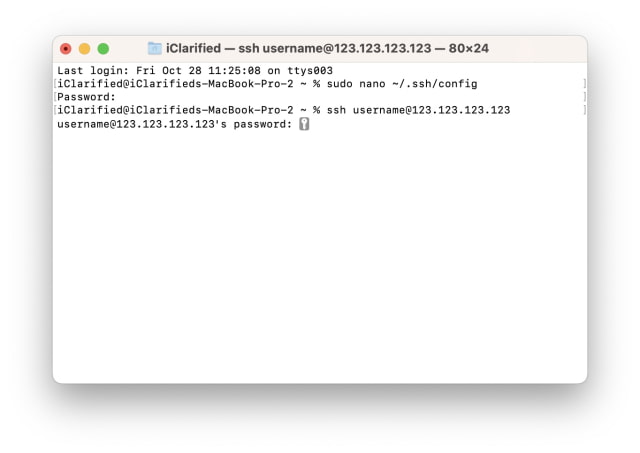
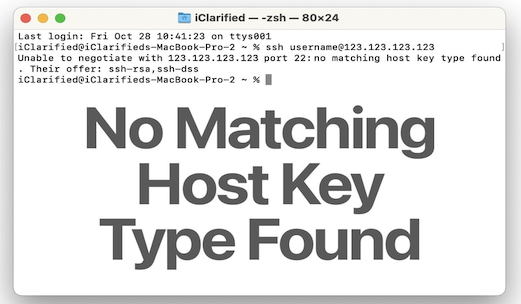
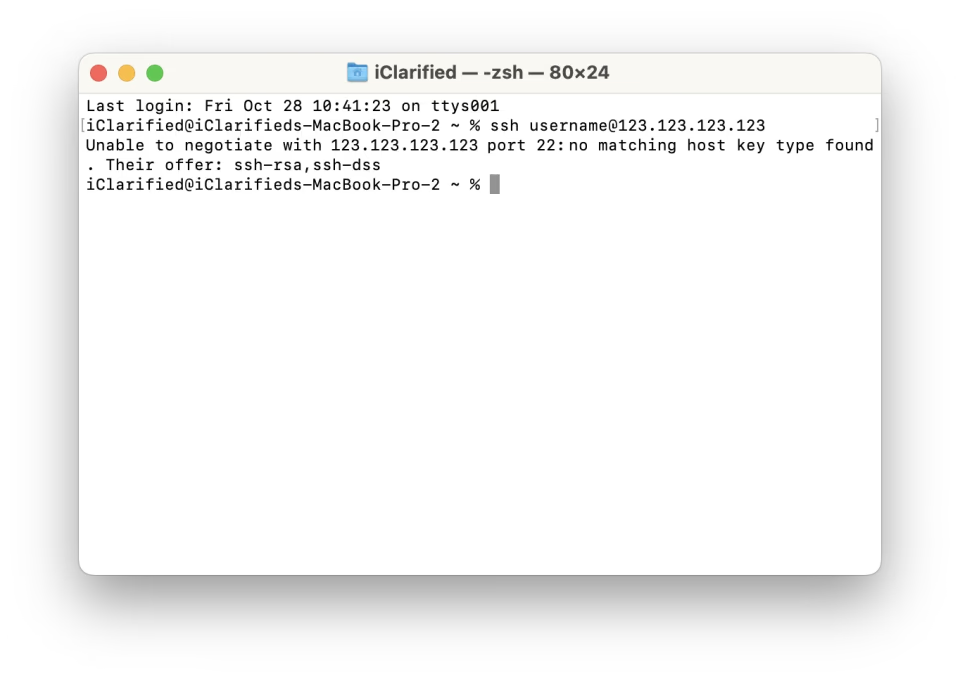
Common Errors: No Matching Host Key Type Found (220 words):
The “No Matching Host Key Type Found” error occurs when a client’s SSH implementation does not support the host key type offered by the server. This can happen if the client’s SSH software is outdated, lacking support for newer key types. It can also occur when the server’s configuration is set to offer key types that the client does not accept.
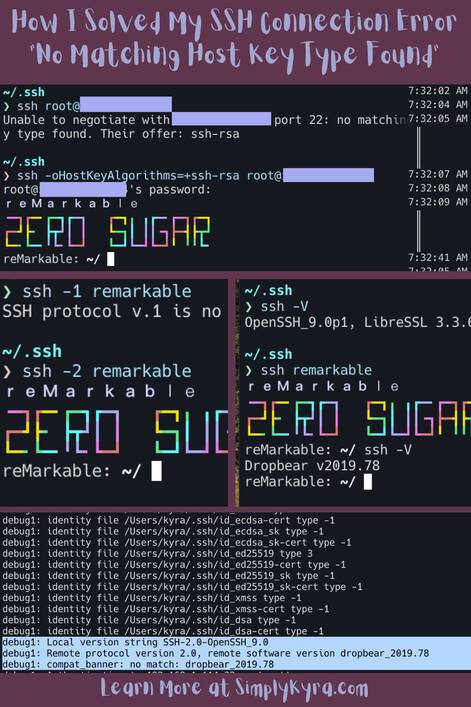
Troubleshooting: Resolving “No Matching Host Key Type Found” Error (240 words):
To resolve this error, a few troubleshooting techniques can be employed. Firstly, one can upgrade the SSH client software to ensure support for the host key type offered by the server. Alternatively, the server’s SSH configuration can be adjusted to use host key types that the client supports.
Alternative Host Key Algorithms (180 words):
If the SSH-RSA key type is not supported or recommended, there are other alternatives worth considering. These include DSA (Digital Signature Algorithm), ECDSA (Elliptic Curve Digital Signature Algorithm), and ED25519. Each algorithm has its strengths and potential compatibility risks, requiring careful consideration when choosing an alternative host key type.
Best Practices for Handling Host Key Types in SSH (220 words):
To ensure smooth and secure SSH connections, it is important to follow best practices with regards to host key types. Regularly updating SSH software, both on the client and server side, is crucial. This ensures compatibility with the latest algorithms and fixes any vulnerabilities. Furthermore, implementing a robust key management system, including rotating and revoking host keys, adds an extra layer of security.
FAQs:
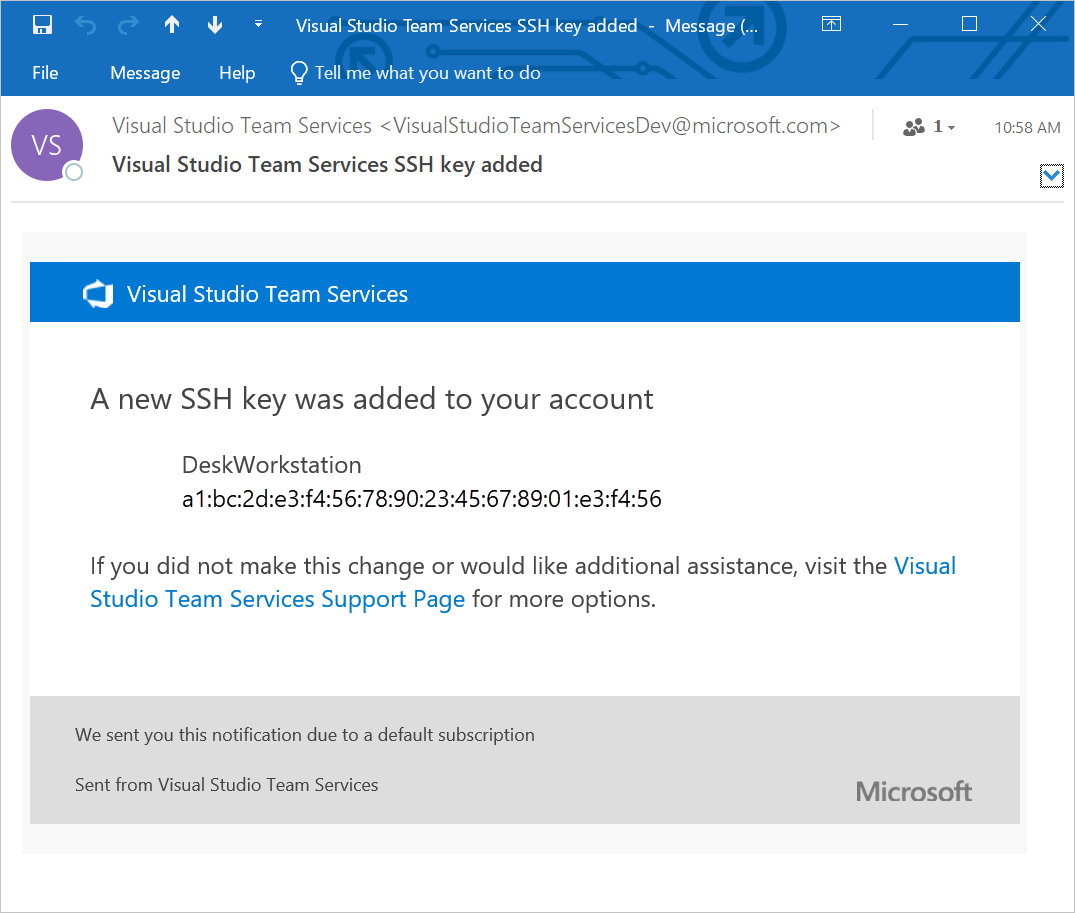
1. What is the “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth)” error?
This error occurs when the SSH server does not accept the SSH-RSA key type for user authentication. It can be resolved by adjusting the server’s SSH configuration to accept the desired key type.
2. How can I generate SSH keys?
To generate SSH keys, you can use the “ssh-keygen” command-line tool. This tool allows you to generate various key types, including RSA, DSA, ECDSA, and ED25519. The generated keys consist of a public key (to be shared with the servers) and a private key (to be kept securely on your local machine).
3. What should I do when I receive a “Host key verification failed” error?
This error usually occurs when the SSH client’s known_hosts file has an outdated or mismatched host key for the server you are connecting to. To resolve this, you can remove the line with the incorrect key from the known_hosts file or simply delete the entire file (if you are certain about the server’s new key).
Conclusion (90 words):
Host key types form an integral part of SSH, ensuring secure and authenticated connections. Understanding SSH-RSA as a host key type can help users troubleshoot errors like “No Matching Host Key Type Found.” By following best practices and staying updated with the latest SSH software, users can establish robust connections and maintain a high level of security in their SSH usage.
Unable To Negotiate With Ip Port 22: No Matching Host Key Type Found. Their Offer: Ssh-Rsa,Ssh-Dss
Keywords searched by users: no matching host key type found. their offer: ssh-rsa Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth), What is host key algorithm, Gen key SSH, WARNING: remote host identification has changed, Host key verification failed, Failed to connect to the host via ssh: Permission denied (publickey,password), Host key for GitHub com has changed and you have requested strict checking, Permission denied (publickey,gssapi-keyex,gssapi-with-mic ssh)
Categories: Top 60 No Matching Host Key Type Found. Their Offer: Ssh-Rsa
See more here: nhanvietluanvan.com
Userauth_Pubkey: Key Type Ssh-Rsa Not In Pubkeyacceptedalgorithms (Preauth)
When it comes to securing remote connections, SSH (Secure Shell) is one of the most popular protocols used in the industry. SSH provides a secure channel over an unsecured network, allowing users to access remote resources securely. However, like any technology, SSH is not without its challenges.
One common issue that SSH users may encounter is the error message “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth).” This error typically occurs when attempting to authenticate using a specific key type, ssh-rsa, which is not supported or allowed by the server’s configuration.
In this article, we will explore the implications of this error message, its possible causes, and potential solutions. By delving into this topic, we hope to provide a comprehensive understanding of the issue and assist SSH users in resolving it effectively.
Understanding the error message:
The error message “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth)” indicates that the server does not support or accept the ssh-rsa key type for public key authentication. It occurs during the authentication process, before the actual user login occurs. The server compares the provided public key algorithm with the list of accepted algorithms specified in the server’s configuration file. If the provided algorithm (in this case, ssh-rsa) is not included in this list, the error message is thrown, preventing authentication.
Possible causes of the error:
1. Server configuration: The most common cause of this error is when the server’s configuration explicitly excludes the ssh-rsa algorithm from the list of accepted key types. Server administrators often limit the accepted key types as a security measure, favoring more modern and secure algorithms like ED25519 or ECDSA.
2. Client configuration: Another possible cause is an outdated or misconfigured SSH client. If the client only supports the ssh-rsa key type but the server configuration no longer accepts it, the error message will occur. Ensuring both the client and server configurations are up to date and compatible is essential.
3. Key type mismatches: The error may also occur due to a mismatch between the key types generated on the server and those provided by the client. If the server-generated keys are of a different type than what the client tries to use for authentication, the error will arise.
Solutions to address the issue:
1. Switch to an accepted key type: The most straightforward solution is to switch to an accepted key type. As mentioned before, modern algorithms like ED25519 or ECDSA are commonly supported and recommended. Both the client and server configurations must be updated accordingly to allow for the new key type. Additionally, it is always advised to generate a new key pair using the accepted algorithm rather than attempting to convert an existing key.
2. Enable support for ssh-rsa: If you prefer to continue using the ssh-rsa algorithm, you can modify the server’s configuration file to include ssh-rsa in the list of accepted algorithms. However, it’s important to note that this algorithm is considered less secure compared to alternatives and should be used with caution.
3. Update or reconfigure the SSH client: Ensure that both the client and server configurations are compatible and up to date. Check for any available updates to the SSH client software and install them. If the issue persists, check the client’s configuration file and make sure it correctly specifies the key type to be used during authentication.
FAQs:
1. Can I use other key types besides ssh-rsa?
Yes, many other key types are supported by SSH. Some widely accepted alternatives include ED25519 and ECDSA. It’s recommended to use these modern algorithms as they offer enhanced security compared to ssh-rsa.
2. Why is ssh-rsa not supported in some server configurations?
As technology evolves, so does the security landscape. The ssh-rsa algorithm, utilizing RSA encryption, has been widely used for many years. However, newer algorithms like ED25519 and ECDSA offer stronger security properties and are preferred in modern server configurations. Excluding ssh-rsa is often a conscious security decision.
3. Why shouldn’t I enable ssh-rsa if it’s not supported by default?
While it is possible to enable ssh-rsa, using outdated algorithms is generally discouraged due to their vulnerability to certain types of attacks. By default, modern SSH server configurations favor more secure algorithms like ED25519 or ECDSA. Enabling ssh-rsa should be a measure carefully evaluated by system administrators, considering the specific security requirements and implications.
4. I’ve updated my server configuration, but the error still persists. What else should I consider?
Ensure that you have restarted the SSH daemon or service after modifying the server configuration file. Changes to the configuration often require a service restart for them to take effect.
In conclusion, the “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth)” error message can be an inconvenience when trying to authenticate via SSH. However, by understanding the causes and solutions discussed in this article, users can address the issue effectively. Whether switching to a more secure key type or modifying the server configuration, resolving this error ensures a safer and smoother remote access experience.
What Is Host Key Algorithm
In the world of secure communication protocols, host key algorithms play a crucial role in ensuring the confidentiality and integrity of data exchanged between a client and a server. These algorithms are an integral component of the widely used Secure Shell (SSH) protocol. The host key algorithm essentially establishes the authenticity and trustworthiness of a remote server during the initial connection process.
When a client connects to a server for the first time using SSH, the client generates a random session key that is used to encrypt the subsequent data transmission. However, before the client can exchange the session key securely, it needs to validate the identity of the server it is connecting to. This is where the host key algorithm comes into play.
The host key algorithm involves three parties: the client, the server, and the trusted third-party certificate authority (CA). The server generates a public-private key pair unique to its identity. The public key is then signed by the CA, ensuring its integrity and authenticity. The signed public key is known as the host key.
When the client attempts to connect to the server, the server presents its host key. The client then checks the authenticity of the host key using the CA’s public key already stored on the client’s system. If the CA’s public key successfully verifies the host key, the client proceeds with establishing a secure connection with the server. However, if the host key does not match the CA’s public key or if the host key is not trusted, the client aborts the connection attempt, preventing any potential security breaches.
Host key algorithms come in various types and are defined by the encryption methods they employ. Some common host key algorithms include RSA, DSA, and more recently, ECDSA and Ed25519. These algorithms differ in terms of key sizes, encryption strengths, and computational efficiency. The choice of host key algorithm depends on the security requirements and the capabilities of the client and server.
Frequently Asked Questions (FAQs):
Q1: Why is the host key algorithm important in SSH connections?
A1: The host key algorithm is crucial in SSH connections as it establishes the authenticity and trustworthiness of a remote server. By validating the host key, clients can ensure they are connecting to the intended server and not falling victim to a malicious imposter.
Q2: How does the host key algorithm prevent man-in-the-middle attacks?
A2: Host key algorithms prevent man-in-the-middle attacks by providing a mechanism to verify the authenticity of a server. Without a trusted host key, an attacker could intercept the connection and impersonate the server, potentially intercepting or modifying sensitive data.
Q3: Can the host key algorithm be compromised?
A3: While no algorithm is entirely immune to compromise, modern host key algorithms, such as ECDSA and Ed25519, are considered highly secure. Regular updates and patches to the system and the use of strong encryption keys are critical in maintaining the security of the host key algorithm.
Q4: How often should host keys be rotated or changed?
A4: Host key rotation frequency depends on the organization’s security policies. In practice, it is recommended to rotate host keys periodically, especially if there is suspicion of compromise or when key sizes become outdated due to advancements in computing power.
Q5: Are there any considerations when selecting a host key algorithm?
A5: When selecting a host key algorithm, factors such as the encryption strength, computational efficiency, and compatibility with the client and server should be considered. It is important to choose a secure algorithm without compromising performance.
In conclusion, the host key algorithm is a vital component of the SSH protocol, ensuring secure and trustworthy connections between clients and servers. By verifying the authenticity of a server’s host key, clients can safeguard their data and protect against potential man-in-the-middle attacks. Adhering to best practices in selecting and regularly rotating host keys can further enhance the security of SSH connections.
Gen Key Ssh
Introduction:
Secure Shell (SSH) is a widely used cryptographic network protocol that provides a secure channel for communication between two computers. It is commonly used for secure remote logins, remote command execution, and secure file transfers. One of the key aspects of SSH is the generation of unique cryptographic keys known as Gen keys SSH. In this article, we will explore the concept of Gen key SSH, its significance in enhancing security, and address some frequently asked questions surrounding this topic.
Understanding Gen key SSH:
Gen key SSH refers to the generation of public and private key pairs used within the SSH protocol. These keys are created through asymmetric encryption algorithms such as RSA, DSA, or ECDSA. The public key is shared with the server while the private key is kept securely on the client-side. These keys play a vital role in ensuring secure communication and authentication.
Importance of Gen key SSH in Security:
1. Stronger Authentication: Gen key SSH provides a higher level of authentication compared to traditional password-based authentication. As the private key remains securely stored on the client-side, it eliminates the risk of passwords being intercepted or compromised.
2. Protection against Password-based Attacks: Password-based authentication can be vulnerable to brute force attacks, dictionary attacks, or keylogger threats. Gen key SSH eliminates these risks by using public-private key pairs, making it more resistant to such attacks.
3. Privacy and Confidentiality: When using Gen key SSH, the client encrypts the data using the public key of the server, ensuring confidentiality during transmission. The private key held by the client is required to decrypt any received data. This prevents unauthorized access to sensitive information.
4. Mitigating Man-in-the-Middle Attacks: Gen key SSH relies on the concept of trust based on key pairs. If the public key received from the server does not match the expected key, the client gets a warning indicating a potential man-in-the-middle attack. This helps users avoid unknowingly connecting to a malicious server.
5. Automated Processes and Secure Transfers: Gen key SSH allows for the automation of processes, such as remote command execution or secure file transfers, using tools like SSH client software. The keys eliminate the need for manual authentication during such operations, making the entire process secure and efficient.
Frequently Asked Questions:
Q1. How are Gen keys SSH generated?
A1. Gen keys SSH are generated using cryptographic algorithms such as RSA, DSA, or ECDSA. Various tools can be used to generate these keys, including OpenSSH, PuTTY, or commercial SSH clients.
Q2. How secure are Gen key SSH?
A2. The security of Gen key SSH depends on the size and strength of the chosen algorithm and the randomness of the generated keys. RSA keys with a length of 2048 or higher are generally considered secure and recommended.
Q3. What should I do if I lose my private key?
A3. It is crucial to keep the private key securely as it is the key to accessing SSH-protected systems. If the private key is lost, it is recommended to generate a new key pair and securely distribute the public key to the relevant server administrators.
Q4. Can Gen keys SSH be used for multiple servers?
A4. Yes, the same Gen keys SSH can be used to authenticate and connect to multiple servers. The public key would need to be placed in the “authorized_keys” file on each server.
Q5. Are Gen keys SSH used only for SSH protocol?
A5. While Gen keys SSH are primarily used for SSH connections, they can also be used in other security protocols and tools, such as SFTP (Secure File Transfer Protocol), SCP (Secure Copy), and Git version control system.
Conclusion:
Gen key SSH is a fundamental aspect of SSH protocol, enhancing security and providing stronger authentication. By using public-private key pairs, it mitigates various security risks associated with password-based authentication. It ensures privacy, protection against attacks, and enables secure automated processes and file transfers. Utilizing Gen key SSH is a practical and reliable approach to maintaining a secure and reliable remote connection.
Images related to the topic no matching host key type found. their offer: ssh-rsa

Found 42 images related to no matching host key type found. their offer: ssh-rsa theme





![SOLUCIÓN] Port 22: no matching host key type found. Their offer: ssh-dss ✓ - YouTube Solución] Port 22: No Matching Host Key Type Found. Their Offer: Ssh-Dss ✓ - Youtube](https://i.ytimg.com/vi/ncCuk3Dm2pA/mqdefault.jpg)










Article link: no matching host key type found. their offer: ssh-rsa.
Learn more about the topic no matching host key type found. their offer: ssh-rsa.
- Git error no matching host key type found. Their offer: ssh-rsa
- I get the error “no matching host key type found. Their offer
- no matching host key type found. Their offer: ssh-dss
- Unable to negotiate with
port 22: no matching … - How to Fix ‘No Matching Host Key Type Found’ on Mac
- [SOLVED] no matching host key type found. Their offer: ssh …
- How to fix OpenWRT SSH Unable to negotiate with … no …
- Fix for ssh authentication failure “no matching host key type …
- How I Solved My SSH Connection Error: No Matching Host …
See more: https://nhanvietluanvan.com/luat-hoc/