How To Access /Etc/Shadow File Without Root
Before diving into accessing the /etc/shadow file without root, it is crucial to understand its purpose and the restrictions surrounding it. The /etc/shadow file is a crucial component of Linux operating systems, specifically designed to store user account information, specifically the hashed passwords. It acts as the primary source for authentication and is protected by strict permissions to ensure the security and integrity of user data.
Understanding the /etc/shadow File:
1. The Purpose of the /etc/shadow File:
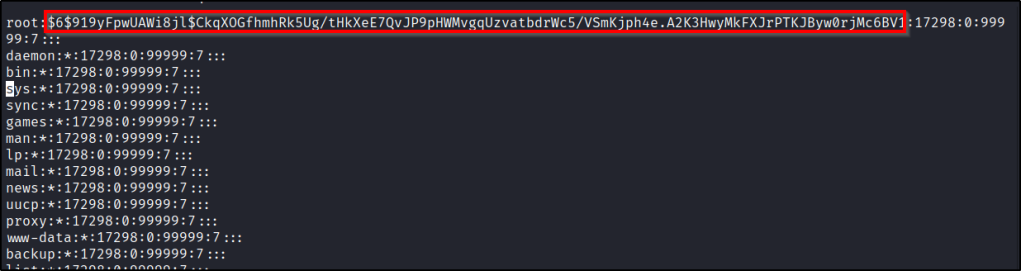
The /etc/shadow file serves as a secure repository for storing encrypted versions of user passwords, ensuring that they remain confidential and protected from unauthorized access. It acts as a replacement for the original /etc/passwd file, which used to store user passwords in a less secure manner.
2. Restrictions and Permissions of the /etc/shadow File:
To ensure the utmost security, the /etc/shadow file is only accessible by the root user or users with similar privileges. The file is typically readable only by the root user and has strict permissions set to prevent any unauthorized viewing or modifications. This makes it inherently difficult to access the /etc/shadow file without root privileges.
Exploring Access Methods:
3. Limitations of Accessing /etc/shadow without Root:
Attempting to access the /etc/shadow file without root privileges is highly challenging due to the stringent restrictions in place. The fundamental purpose of these restrictions is to protect sensitive user information and prevent unauthorized access. Therefore, accessing the /etc/shadow file without root poses significant limitations and often requires alternative approaches.
4. Utilizing the Read Access to /etc/shadow:
Although the /etc/shadow file may not be accessed directly without root privileges, some limited information can still be gathered by users with read access to the file. This includes details about the account’s expiration date, the minimum and maximum password age, and other configuration settings. However, the actual hashed passwords are not accessible without proper privileges.
Working with Privileges:
5. Characteristics of the Root User:
The root user, also known as the superuser, possesses the highest level of privileges in a Linux system. Root access allows complete control over the system, including the ability to access critical files such as the /etc/shadow file. This level of access is vital for system administration tasks but must be used responsibly to ensure the security of user data.
6. Gaining Root Access:
Gaining root access can be achieved through various means such as using the “su” command with the root password or the “sudo” command that authorizes specific users to execute commands as the root user. However, it is essential to exercise caution when accessing root privileges, ensuring that only trusted individuals are granted such access.
Alternative Approaches:
7. Utilizing Vulnerabilities and Exploits:
Although circumventing root privileges is not recommended, it is worth noting that certain vulnerabilities and exploits may allow for unauthorized access to the /etc/shadow file. Exploiting such weaknesses can lead to severe security breaches and is highly unethical and potentially illegal. It is crucial to prioritize the security and integrity of user data above all else.
8. Employing Process Substitution:
Another potential method involves employing process substitution, a technique that allows users to execute commands with elevated privileges without root access. It involves creating temporary files or named pipes to pass data between processes, effectively enabling access to files like /etc/shadow. However, this approach requires a thorough understanding of system internals and must be approached with caution.
9. Utilizing a Group Membership:
One alternative method to access the /etc/shadow file without root is by utilizing group membership. By adding a user to a specific group with read permission to the /etc/shadow file, they can gain access to its contents. However, this approach requires prior knowledge of the system’s group settings and careful consideration of potential security implications.
FAQs:
Q1: How can I edit the /etc/shadow file in Linux?
To edit the /etc/shadow file, you need root privileges. After obtaining root access, you can use text editors like Nano or Vim to modify the file’s contents. However, exercise caution when making changes to ensure the integrity of user passwords.
Q2: Is there an exploit for the /etc/shadow file?
Exploiting the /etc/shadow file is considered illegal and unethical. While certain vulnerabilities may exist that could potentially allow unauthorized access, it is essential to prioritize the security and privacy of user data.
Q3: Can I decrypt passwords stored in the /etc/shadow file?
The passwords stored in the /etc/shadow file are hashed, which means they cannot be decrypted. Hashing algorithms such as SHA-512 are designed to be irreversible, providing an additional layer of security for user passwords.
Q4: What is the relationship between the shadow and passwd files in Linux?
The /etc/shadow file is a secure replacement for the original /etc/passwd file, storing user account information, including hashed passwords, while the /etc/passwd file contains user account details in an older, less secure format. Both files work in conjunction to facilitate user authentication.
Q5: Can I set the /etc/shadow file to read-only?
Setting the /etc/shadow file to read-only is not recommended as it may disrupt system functionality and prevent legitimate processes from modifying the file as required. Instead, it is advisable to maintain strict permissions and ensure proper access controls to protect sensitive user information.
Q6: How does the /etc/shadow file use the SHA-512 algorithm?
The SHA-512 algorithm is commonly used to secure passwords stored in the /etc/shadow file. It performs a one-way hashing process on the original password, creating a fixed-length hash value that is stored in the file. This hash value cannot be reversed to obtain the original password.
Q7: How can I copy the /etc/shadow file on Linux?
To copy the /etc/shadow file, you need root privileges. Using commands like “cp” or tools like “rsync,” you can create a backup or make a copy of the file. However, ensure that the copied file is stored securely to prevent unauthorized access.
Q8: What permissions should be set for the /etc/shadow file?
The /etc/shadow file should have strict permissions to ensure its security. On most Linux systems, it is accessible only by the root user (owner) with read and write permissions (mode 600). Additionally, the file is typically owned by the root user or the “shadow” group.
Common Linux Privilege Escalation: Cracking Hashes In /Etc/Shadow File
Keywords searched by users: how to access /etc/shadow file without root how to edit /etc/shadow file in linux, etc/shadow exploit, etc/shadow password decrypt, shadow and passwd file in linux, etc/shadow read only, etc/shadow sha512, copy shadow file linux, etc/shadow permissions
Categories: Top 65 How To Access /Etc/Shadow File Without Root
See more here: nhanvietluanvan.com
How To Edit /Etc/Shadow File In Linux
The /etc/shadow file is a key component of Linux systems, storing essential user account information related to user authentication and password security. With proper knowledge and caution, editing this file can be useful in managing user accounts and strengthening the overall security of your Linux system. In this article, we will delve into the details of editing the /etc/shadow file, providing step-by-step instructions, useful tips, and addressing frequently asked questions (FAQs) to ensure a comprehensive understanding.
Editing the /etc/shadow file entails altering the password hash, changing the password expiration dates, or modifying other attributes associated with user accounts. Before proceeding with any modifications, it is essential to exercise caution, as improper alterations may render the system inoperable or compromise its security.
Step 1: Understanding /etc/shadow File Structure
The /etc/shadow file, usually stored in the /etc directory, consists of several fields delimited by colons. Each field represents different attributes associated with a user account. Understanding these fields is crucial to grasp the procedure of editing the file.
Step 2: Backing Up /etc/shadow File
As a precautionary measure before making any modifications, create a backup of the original /etc/shadow file. This ensures the ability to restore if any errors or issues arise during the editing process. To create a backup, open a terminal and run the following command:
sudo cp /etc/shadow /etc/shadow.bak
Step 3: Editing /etc/shadow File
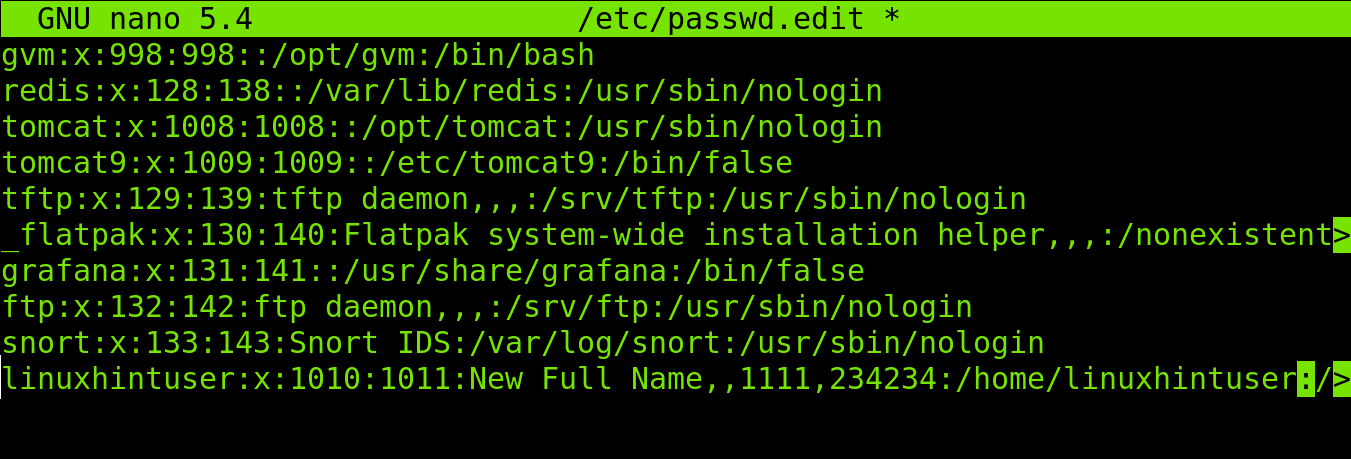
To edit the /etc/shadow file, open it with a text editor. However, it is crucial to use a text editor that preserves the file’s permissions and ownership while saving changes. For instance, the “vi” or “nano” editors are popular choices. Open a terminal and run the following command to start editing with “vi”:
sudo vi /etc/shadow
Step 4: Modifying User Attributes
Within the /etc/shadow file, each user account is represented by a single line. Each line contains several fields, including the username, password hash, password change dates, and more. By modifying the respective fields, various user attributes can be altered. Be sure to follow the correct syntax and refer to the official documentation for the specific format of each field.
For example, to change a user’s password, locate the line corresponding to the desired user and replace the current password hash with the new one. Password hashes can be generated using a tool like “mkpasswd” or “openssl.”
Other possible modifications include resetting password expiration dates, enforcing password aging policies, or disabling a user’s account by adding an exclamation mark (“!”) as the password hash.
Step 5: Saving and Exiting
After making the necessary modifications, save the changes and exit the text editor. In “vi”, press the “ESC” key, then type “:wq” and hit “Enter” to save and quit. If using “nano”, press “Ctrl+O” to save and “Ctrl+X” to exit.
Step 6: Verifying Changes
To ensure that the changes were applied correctly, it is essential to verify the modifications. Run the following command in a terminal, replacing “username” with the desired user’s name:
sudo chage -l username
This command displays the current password expiration dates and other relevant information related to the edited user account.
FAQs:
Q1: Can I directly edit the /etc/shadow file without using a text editor?
A: No, it is not recommended to edit the /etc/shadow file without using a text editor that preserves permissions and ownership. Using a proper text editor ensures the file remains intact and consistent.
Q2: What are some common mistakes to avoid while editing /etc/shadow?
A: Some common mistakes include modifying fields incorrectly, deleting lines, or using incorrect user names. Any errors may cause login issues or permanent damage to the user accounts. Always double-check modifications before saving and exiting.
Q3: Are there alternative methods to edit /etc/shadow?
A: Yes, there are various graphical tools and command-line utilities available that provide a more user-friendly method to edit user accounts, such as “usermod” or “passwd.” These tools handle the modifications internally and update the /etc/shadow file correctly.
Q4: What recourse do I have in case of mistakes or issues after editing /etc/shadow?
A: If issues arise after modifying /etc/shadow, those with a backup can restore the original file using the following command:
sudo cp /etc/shadow.bak /etc/shadow
Alternatively, booting into recovery mode or using a live USB may provide access to the system to reverse the changes.
In conclusion, editing the /etc/shadow file in Linux can be a powerful tool in managing user accounts and enhancing security, but it requires careful attention and knowledge of the file structure. By following the step-by-step instructions provided, referring to official documentation, and exercising caution, you can confidently make necessary modifications while ensuring the integrity and stability of your Linux system.
Etc/Shadow Exploit
Introduction (100 words)
In the realm of cybersecurity, staying informed about the latest exploits is crucial to safeguarding sensitive data and preventing unauthorized access. One such exploit that has attracted attention is the etc/shadow exploit. This article aims to provide a comprehensive understanding of this exploit, shedding light on the vulnerabilities it exploits, potential consequences, and ways to mitigate the risks.
Understanding the etc/shadow Exploit (500 words)
1. What is the etc/shadow exploit?
The etc/shadow exploit refers to a vulnerability that occurs in Unix-like operating systems. This exploit targets the /etc/shadow file which stores user password information in a hashed format. By gaining unauthorized access to this file, attackers can extract hashed passwords and attempt to crack them using password cracking techniques.
2. How does the etc/shadow exploit work?
The exploit takes advantage of insecure file permission settings on the /etc/shadow file. Normally, this file should only be accessible by the system’s root user, but misconfigurations or vulnerabilities can allow other users or processes to gain unauthorized access to the file. Once the attacker has access, they can either attempt to crack passwords offline or use the hashed passwords as entry points for further system infiltration.
3. What are the consequences of the etc/shadow exploit?
The exploitation of the etc/shadow file poses significant security risks to a system. If an attacker successfully gains access to the hashed passwords, they can use powerful password cracking tools to uncover users’ plaintext passwords. This, in turn, grants them access to various user accounts, potentially allowing them to assume control over critical system resources and escalate privileges. Additionally, if users reuse passwords across different platforms, the attacker may gain access to other services as well.
4. How can the etc/shadow exploit be mitigated?
To mitigate the risks associated with the etc/shadow exploit, various preventive measures can be implemented:
a. Restrict File Permissions: Restrict access to the /etc/shadow file to the root user only, ensuring that other users or processes cannot read or modify it.
b. Regularly Update and Patch: Keep the system and its dependencies up-to-date with the latest releases and security patches. This helps address vulnerabilities that could potentially be exploited.
c. Monitor Log Files: Implement log monitoring tools to detect any abnormal activities related to user behavior, file access, or system changes. These tools can raise flags and alert administrators to potential unauthorized access attempts.
d. Implement Strong Password Policies: Enforce policies that mandate strong passwords, encourage regular password changes, and prohibit password reuse across different platforms.
e. Implement Multi-Factor Authentication: By implementing multi-factor authentication methods, such as biometrics or one-time passwords, an additional layer of security is added, making it significantly harder for attackers to gain unauthorized access.
f. Regular Security Audits: Conduct regular security audits to identify vulnerabilities and ensure that proper security measures are in place to protect sensitive information.
g. Adoption of Security Solutions: Deploying firewall systems, Intrusion Detection Systems (IDS), and Intrusion Prevention Systems (IPS) can help detect and prevent unauthorized access attempts or limit the impact if a breach occurs.
FAQs (233 words)
1. Is the etc/shadow exploit limited to Unix-like operating systems?
Yes, the etc/shadow exploit specifically targets Unix-like systems, including Linux distributions, FreeBSD, OpenBSD, and others.
2. Can the etc/shadow exploit be remotely exploited?
While remote exploitation of the etc/shadow exploit is possible, it typically requires prior access to the target system. Attackers often gain initial access through various means, such as social engineering, phishing attacks, or exploiting other vulnerabilities before attempting to exploit the etc/shadow file.
3. Can changing file permissions on the /etc/shadow file fix the vulnerability?
Merely changing the file permissions is not sufficient to fix the vulnerability. Permissions should be set to restrict access to the root user, but other preventive measures, as mentioned earlier, should also be implemented.
4. Can the etc/shadow exploit be detected by antivirus software?
Antivirus software is primarily designed to detect and mitigate malware threats, whereas the etc/shadow exploit is not categorized as malware. However, integrating IDS or IPS solutions can help identify suspicious activities indicating a potential etc/shadow exploit attempt.
Conclusion (100 words)
Understanding the etc/shadow exploit is crucial in today’s cybersecurity landscape. By knowing how this exploit works, its potential consequences, and implementing relevant preventive measures, system administrators can strengthen their defenses against unauthorized access attempts. Staying vigilant, keeping systems up-to-date, and maintaining strong password policies are vital practices in safeguarding system integrity and sensitive data.
Etc/Shadow Password Decrypt
Introduction (50 words):
In modern computing environments, safeguarding user authentication details is of utmost importance. The ETC/Shadow password decryption process provides an additional layer of security by encrypting and storing user passwords separately. In this article, we will delve into the intricacies of ETC/Shadow password decryption, shedding light on its functionality and significance in preserving data integrity.
Understanding the ETC/Shadow Encryption System (200 words):
The ETC/Shadow encryption system, also referred to as /etc/shadow, is a widely employed mechanism primarily found in Unix-based operating systems. Its robust nature protects user passwords by storing them in an encrypted format, distinct from the /etc/passwd file, accessible only to privileged users.
To maintain data integrity, sensitive user information such as passwords, encryption keys, and expiration dates are securely concealed within the /etc/shadow file. In contrast to the easily accessible /etc/passwd file, /etc/shadow hashes passwords using a strong algorithm like MD5, SHA-256, or Blowfish. This cryptographic transformation ensures that even if an unauthorized user breaches the system, they will struggle to extract meaningful password information.
The Strengths of ETC/Shadow Password Decryption (200 words):
ETC/Shadow password decryption strengthens overall system security by employing several key strategies, including:
1. Limited accessibility: Access to the /etc/shadow file is exclusively granted to privileged users, making it highly challenging for unauthorized entities to gain access. This restriction prevents malicious actors from obtaining password hashes, thus increasing system resilience.
2. Salted password hashes: To further enhance security, ETC/Shadow password decryption utilizes a technique called password salting. This process adds a random string of characters (salt) to each password before hashing, rendering precomputed tables (rainbow tables) ineffective, as every password’s hash differs from a simple dictionary lookup.
3. Strong hashing algorithms: The choice of strong and computationally expensive hashing algorithms makes it substantially more difficult for potential attackers to reverse-engineer passwords. By using widely-used algorithms like SHA-256 or bcrypt, the system remains resilient to brute-force and dictionary attacks.
Frequently Asked Questions (394 words):
Q1. Can ETC/Shadow passwords be decrypted?
No, ETC/Shadow passwords cannot be decrypted directly. Instead, the system compares user-provided passwords by encrypting them and checking if the resulting hash matches the one stored in the /etc/shadow file. This approach ensures that user passwords remain secure, even if unauthorized access to /etc/shadow occurs.
Q2. What happens if the /etc/shadow file is breached?
If the /etc/shadow file is compromised, it is crucial to take immediate action. The breach should be reported to the appropriate security personnel and the system administrator. Meanwhile, users should update their passwords to mitigate risks associated with unauthorized access.
Q3. How does password salting contribute to security?
Password salting adds an extra layer of security by appending a unique string to each password before hashing. This renders precomputed tables of hashed passwords ineffective, making it incredibly difficult for attackers to crack passwords using rainbow tables or dictionary attacks.
Q4. How often should /etc/shadow passwords be changed?
To maintain optimal security, it is advisable to enforce regular password changes for all users. Implementing a password expiration policy, periodically prompting users to update their passwords, significantly reduces the risk of password compromise.
Q5. Is ETC/Shadow password encryption flawless?
While ETC/Shadow password encryption is widely regarded as secure, no system is entirely resilient to attacks. However, by employing strong encryption algorithms, regular updates, and following best practices, the risks associated with password breaches can be minimized.
Conclusion (50 words):
The ETC/Shadow password decryption process plays a significant role in securing user credentials in Unix-based operating systems. By utilizing strong encryption algorithms, password salting techniques, and limited accessibility, the system ensures that password hashes remain resilient against unauthorized decryption attempts, thus contributing to overall data integrity and security.
Images related to the topic how to access /etc/shadow file without root

Found 43 images related to how to access /etc/shadow file without root theme






Article link: how to access /etc/shadow file without root.
Learn more about the topic how to access /etc/shadow file without root.
- How could a hacker access the /etc/shadow file if it is only …
- non-root permission to the /etc/shadow? – LinuxQuestions.org
- Running a script that reads /etc/shadow without having to log …
- Understanding /etc/shadow file format on Linux – nixCraft
- What is a shadow password file? – TechTarget
- /etc/shadow File in Linux – CyberSophia
- /etc/shadow file in Linux Explained with Examples
- su root (without asking for password) – LinuxQuestions.org
- How to create a user and give it read permission to /etc …
- Privilege Escalation: Exploiting write access to /etc/shadow
- How To Edit The /etc/shadow File In Linux – Systran Box
- linux – What prevents me from just editing the /etc/shadow file …
- Does getpwuid work with /etc/shadow without root priviledge
- Day 65: Change Linux Root Password with Shadow File …
See more: nhanvietluanvan.com/luat-hoc