Github Rsa Key Changed
Introduction
In today’s world, where cybersecurity is a top concern, organizations must take necessary measures to ensure the protection of their sensitive data and maintain trust with their users. GitHub, the popular code collaboration platform, understands the significance of security, especially in managing access to repositories. One essential aspect of securing access is through the use of RSA (Rivest-Shamir-Adleman) keys. In this article, we will discuss the importance of RSA keys in GitHub, explain how they work, delve into the reasons for changing them, outline the benefits, discuss the process, potential challenges, and cover best practices for managing RSA keys in GitHub.
I. Importance of RSA Keys in GitHub
RSA keys play a crucial role in GitHub’s security infrastructure as they ensure the authenticity, integrity, and confidentiality of data transmitted between clients and servers. These keys are used for both authentication and encryption purposes. Without RSA keys, GitHub’s security mechanisms would be compromised, allowing malicious entities to gain unauthorized access, manipulate data, or intercept sensitive information.
II. How RSA Keys Work in GitHub
In GitHub, RSA keys function using a public-key encryption scheme. Each user is assigned a pair of keys: a public key and a corresponding private key. The public key is made available to GitHub, while the private key is securely stored on the user’s local machine, ensuring confidentiality.
When a user attempts to access a repository or perform an action on GitHub, their public key is used to encrypt the data. This encrypted data can only be decrypted using the corresponding private key, which is kept exclusively by the user. GitHub verifies the authenticity of the user by decrypting the data with the corresponding public key on file, ensuring the user’s identity and facilitating secure communication between the client and server.
III. Reasons for Changing RSA Keys in GitHub
The GitHub RSA key needs to be changed on occasion due to various reasons:
1. Compromised Keys: If there is any suspicion or evidence of a security breach, such as unauthorized access or an attack, it becomes crucial to change the RSA keys immediately to prevent further misuse.
2. Key Expiration: RSA keys have a limited lifespan; hence, they need to be refreshed periodically to maintain the effectiveness of encryption and authentication mechanisms.
3. Employee Departure or Privilege Changes: When an employee leaves an organization or experiences a significant change in roles, it is necessary to change the associated RSA keys to revoke access and mitigate potential security risks.
IV. Benefits of Changing RSA Keys in GitHub
Changing RSA keys in GitHub brings several benefits to both the organization and its users:
1. Enhanced Security: By regularly changing RSA keys, GitHub can bolster security and prevent any security breaches or unauthorized access attempts.
2. Future-Proofing: Refreshing RSA keys ensures GitHub stays aligned with the industry’s evolving security standards and best practices.
3. Trust and Confidence: Frequent RSA key changes demonstrate the platform’s commitment to security, instilling confidence in users regarding the safety of their repositories and personal information.
V. Process of Changing RSA Keys in GitHub
Changing RSA keys in GitHub involves a few essential steps:
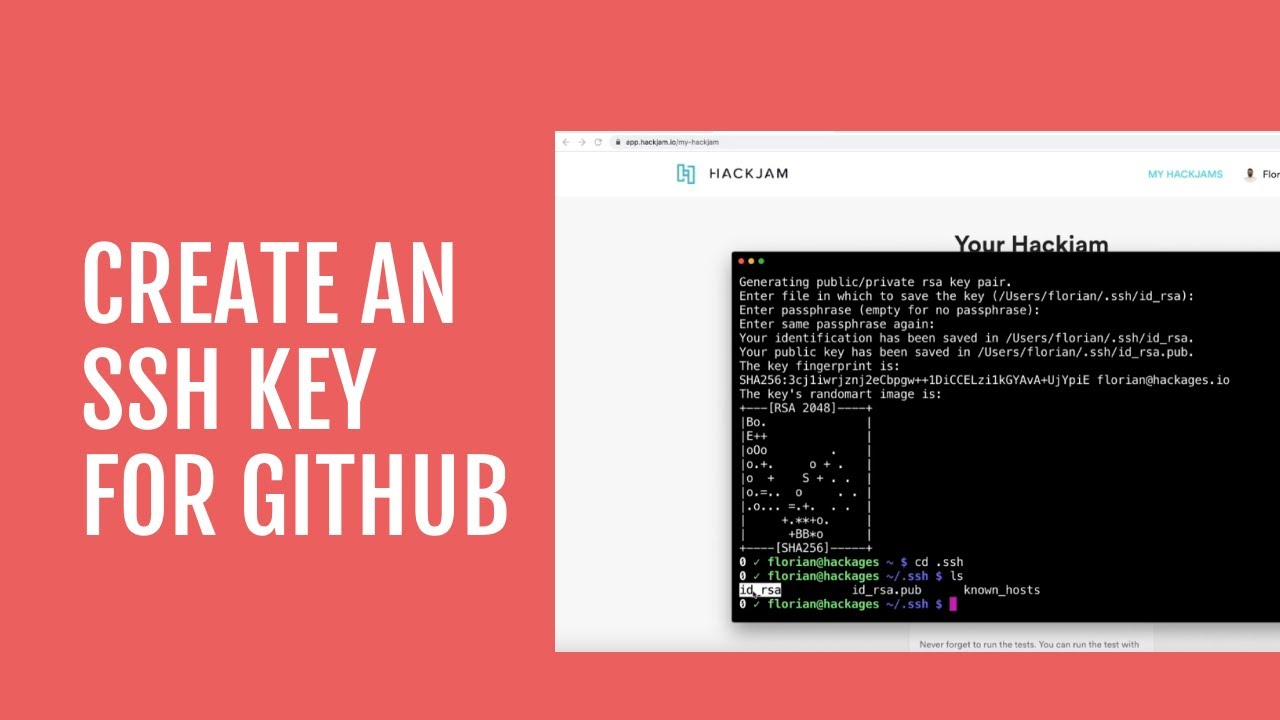
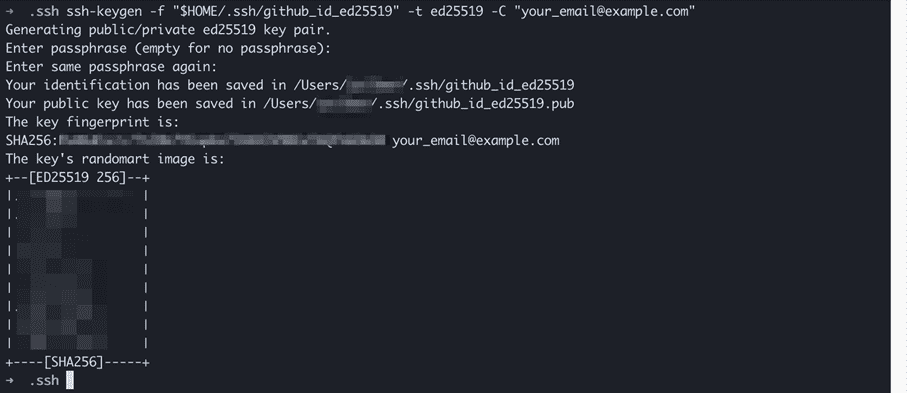
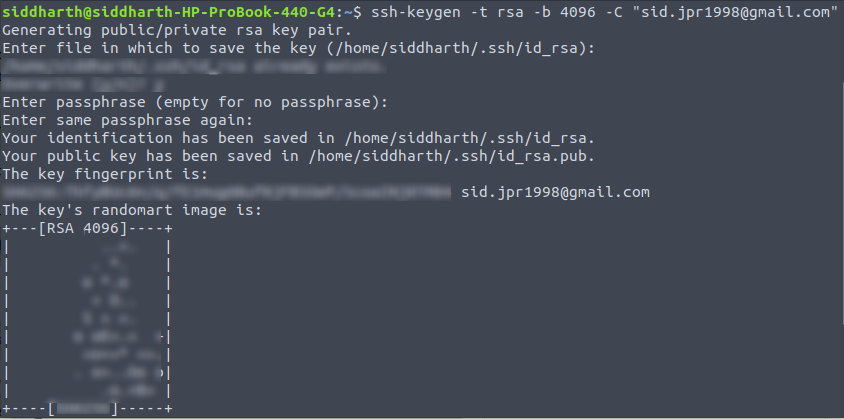
1. Generate New RSA Keys: Generate a new RSA key pair (public and private keys) using trusted key generation tools or libraries.
2. Update the Public Key: Add the new public key to the user’s GitHub account. This allows GitHub to validate the user’s identity when performing operations.
3. Remove Old Public Key: As a best practice, remove the outdated public key from the user’s GitHub account to avoid confusion and ensure proper key management.
VI. Steps to Change RSA Keys in GitHub
Below is a summarized guide on how to change RSA keys in GitHub:
1. Generate a new RSA key pair using a trusted tool or library.
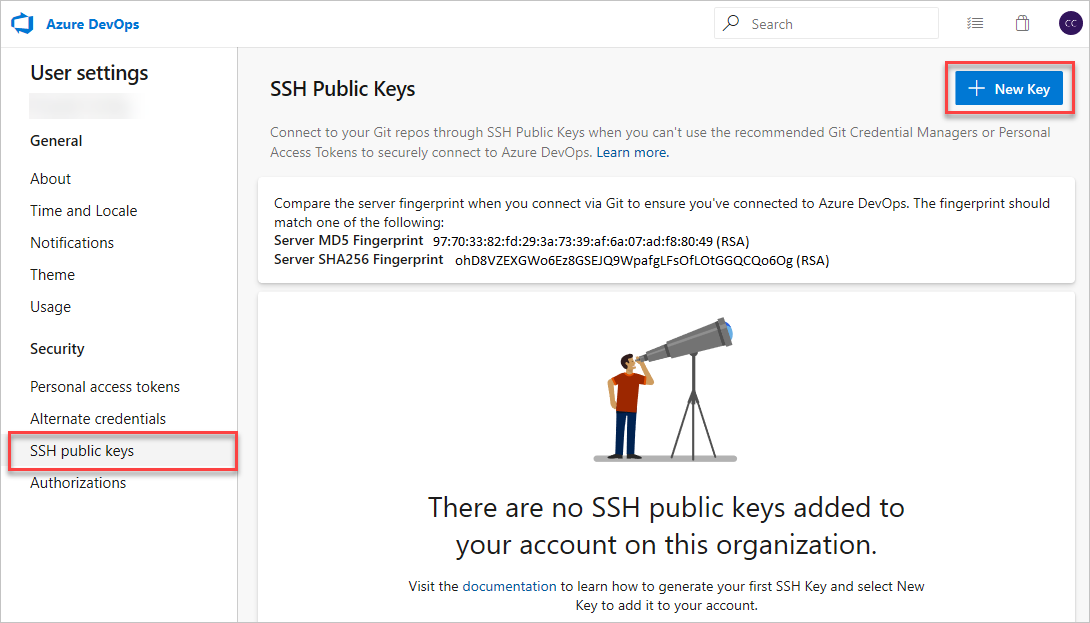
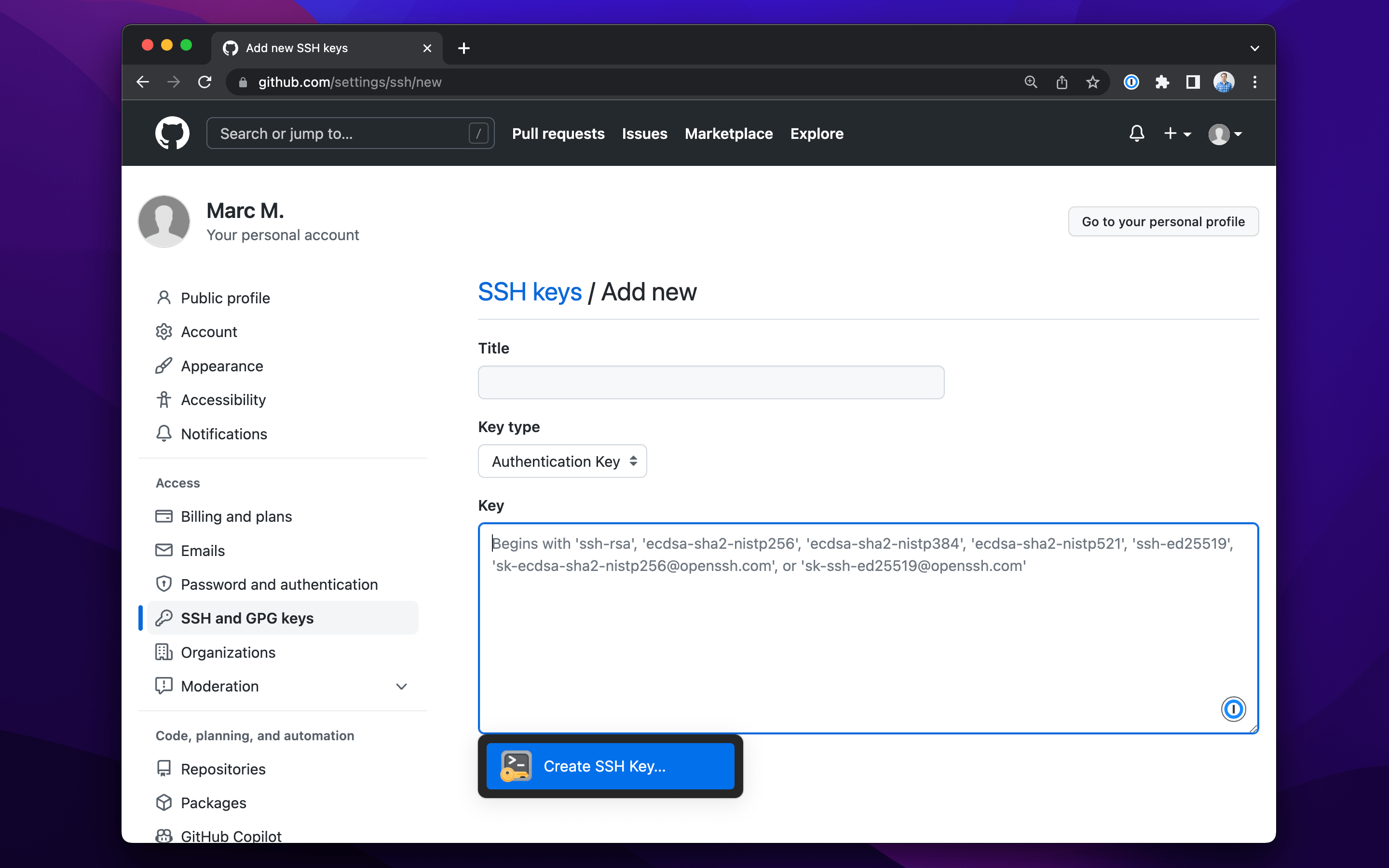
2. Access your GitHub account settings and navigate to the “SSH and GPG keys” section.
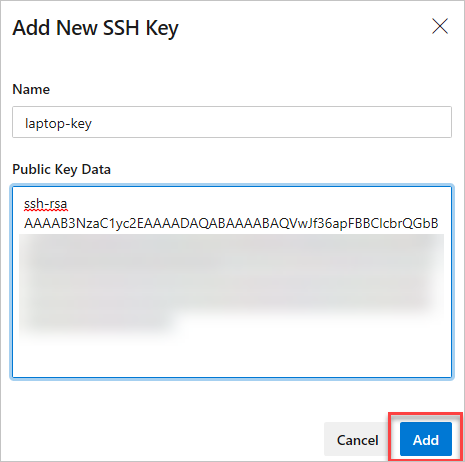
3. Click on “New SSH key” (or “New GPG key” if applicable), and paste your new public key into the corresponding field.
4. Save the changes, update your local machine’s configuration with the new private key, and remove the older private key entry.
VII. Potential Challenges in Changing RSA Keys in GitHub
While changing RSA keys is a critical security measure, it can present some challenges:
1. Compatibility Issues: Changing RSA keys might cause compatibility problems with existing integrations, automated processes, or Continuous Integration/Continuous Deployment (CI/CD) pipelines. It is essential to carefully assess any potential impact before changing keys.
2. User Awareness and Key Management: Users must be made aware of RSA key changes and how to update their keys properly. Additionally, it is important to maintain a well-organized key management system to prevent any confusion or misconfigurations.
VIII. Best Practices for Changing RSA Keys in GitHub
To successfully change RSA keys, GitHub users should adhere to the following best practices:
1. Regularly Rotate RSA Keys: Establish a key rotation strategy, such as quarterly or semi-annually, to ensure maximum security and minimize the risk of unauthorized access.
2. Implement Dual-Key Verification: Use two-factor authentication mechanisms, such as TOTP (Time-Based One-Time Password), WebAuthn, or security keys, in conjunction with RSA keys to provide an added layer of security.
3. Communicate Key Changes: Inform users well in advance about RSA key changes and provide clear instructions on how to update their keys to avoid disruptions or access issues.
IX. Considerations for Managing RSA Keys in GitHub
In addition to changing RSA keys, organizations need to consider the overall management of these keys:
1. Secure Key Storage: Properly secure private RSA keys on users’ local machines using strong passwords or passphrase-protected key files.
2. Revocation Process: Establish a well-defined process for revoking access to old RSA keys, especially in scenarios like employee termination or privilege changes.
3. Key Backup and Recovery: Implement a robust key backup mechanism to ensure that private keys are not lost or irretrievable in case of hardware failures or system crashes.
X. Tips for Ensuring Security with RSA Keys in GitHub
To enhance the security of RSA keys in GitHub, consider the following tips:
1. Regular Security Audits: Perform regular audits and vulnerability assessments to identify any weaknesses or misconfigurations in the key management process.
2. Use Strong Key Length: Ensure that RSA keys have an appropriate length, typically at least 2048 bits or higher, to enhance security strength against potential attacks.
3. Key Rotation Automation: Consider automating the process of key rotation to reduce human errors and guarantee timely updates.
FAQs:
Q1. What happens if I don’t change my RSA keys in GitHub?
A1. Failing to change RSA keys periodically can expose you to potential security breaches. Attackers might gain unauthorized access to your repositories, manipulate your data, or intercept sensitive information.
Q2. How often should I change my RSA keys in GitHub?
A2. Typically, RSA keys should be changed every three to six months, but the frequency may vary depending on your organization’s security policies and requirements.
Q3. Can I use the same RSA key pair for multiple GitHub accounts?
A3. It is not recommended to use the same RSA key pair for multiple GitHub accounts, as this can compromise individual account security. It is advisable to use a unique key pair for each account.
Q4. What should I do if I suspect my RSA keys have been compromised?
A4. If you suspect your RSA keys have been compromised, it is crucial to change them immediately to prevent any further unauthorized access. Additionally, you should review your account activity, verify for any suspicious actions, and consider enabling two-factor authentication for added security measures.
Conclusion
In conclusion, RSA keys play a vital role in securing access and ensuring the authenticity of data in GitHub. Changing RSA keys periodically enhances security, mitigates risks, and boosts user confidence. By following best practices and considering key management, organizations can maintain a robust security posture while utilizing GitHub’s collaborative development platform. Stay vigilant, update your RSA keys regularly, and protect your repositories from potential threats.
Github Changed Rsa Key On March 24, 2023 : How To Solve The Problem?
Keywords searched by users: github rsa key changed
Categories: Top 86 Github Rsa Key Changed
See more here: nhanvietluanvan.com
Images related to the topic github rsa key changed

Found 47 images related to github rsa key changed theme






























Article link: github rsa key changed.
Learn more about the topic github rsa key changed.
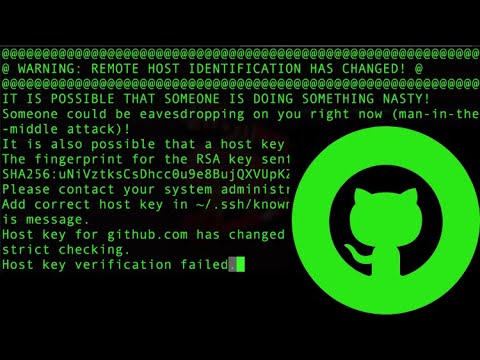
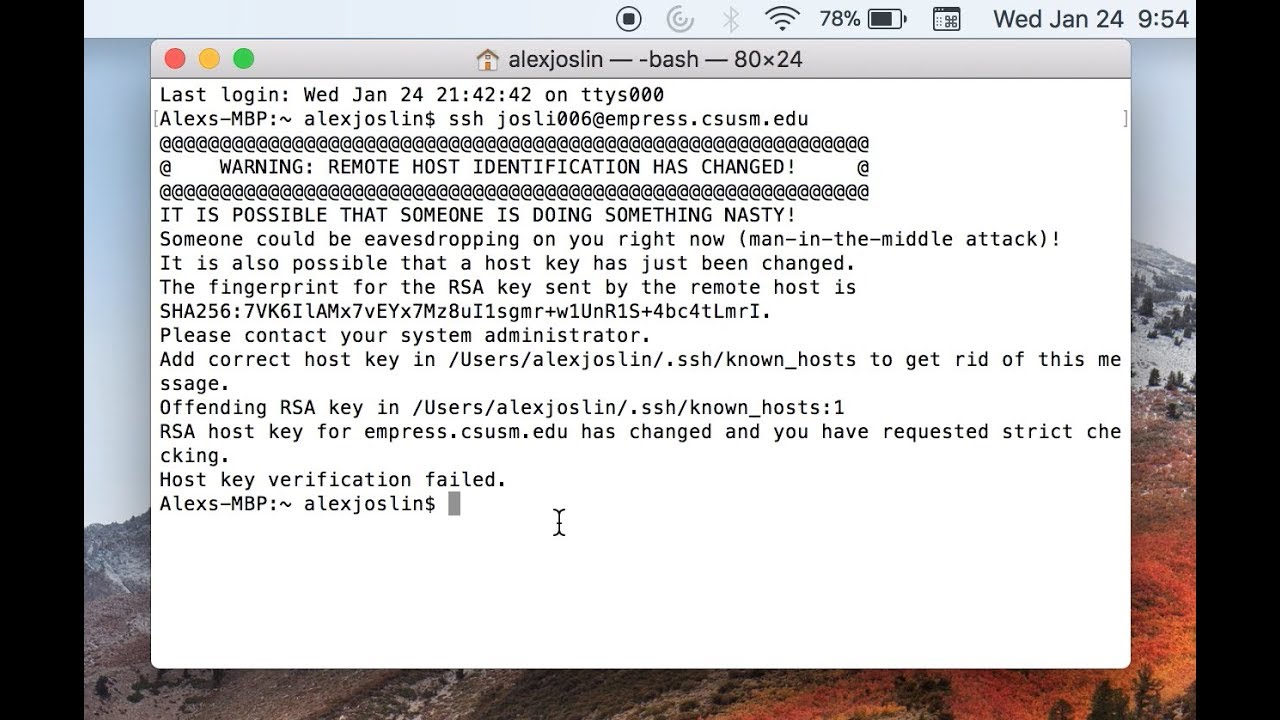
- We updated our RSA SSH host key – The GitHub Blog
- Has GitHub changed his remote host key ? #50878
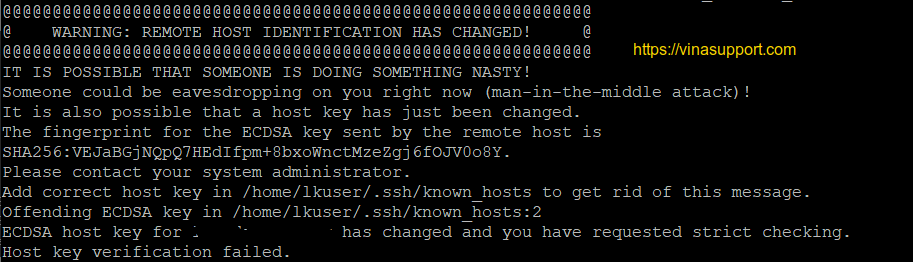
- How To Deal With the “Remote Host Identification Has …
- RSA host key changed for github.com – DEV Community
- GitHub changes its compromised SSH key – Malwarebytes
- RSA SSH host key from github changed? – Stack Overflow
- GitHub publishes RSA SSH host keys by mistake, issues update
- Some GitHub users must take action after RSA SSH host key …
- Github host key changed? – LLVM Discourse
See more: nhanvietluanvan.com/luat-hoc