Github Remote Host Identification Has Changed
Remote host identification is an essential aspect of secure communication between clients and servers. In the context of GitHub, remote host identification refers to the process of verifying the identity of the remote host (GitHub server) before establishing a connection. It ensures that users are communicating with the intended GitHub server and not an imposter, thereby preventing security vulnerabilities.
However, there are instances where the remote host identification for GitHub may change due to certain reasons. These changes can result in users encountering warnings or connectivity issues when attempting to establish a connection with GitHub. In this article, we will explore the explanation, common causes, implications, resolution steps, best practices, and security risks associated with GitHub remote host identification changes.
Explanation of Remote Host Identification in a GitHub Context
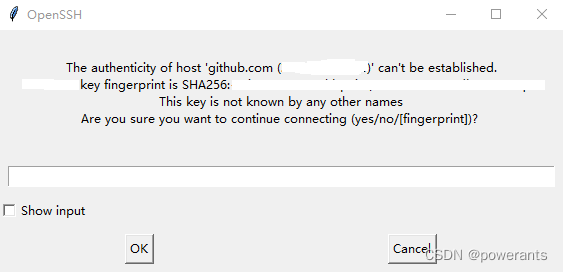
In the context of GitHub, remote host identification involves verifying the authenticity of the server’s host key. When a client connects to a GitHub server for the first time, the server presents its host key to the client. The client then compares this key with the known host keys stored on the local machine. If the host key matches, the connection is deemed secure, and the client proceeds with the communication.
Common Causes and Implications of Changes in Remote Host Identification
1. Server Upgrade or Change: GitHub periodically updates its servers to improve performance, security, and add new features. As a result, the host key may change, thereby causing the remote host identification to change.
2. Mitigating Security Risks: GitHub may change the host key in response to identified security vulnerabilities or to strengthen the encryption protocols used during communication. This change is done to enhance the overall security of the platform.
3. DNS and Routing Changes: GitHub’s infrastructure is distributed across multiple regions and data centers. Changes in DNS records or routing configurations can cause the remote host identification to change as traffic is redirected to different servers.
Implications:
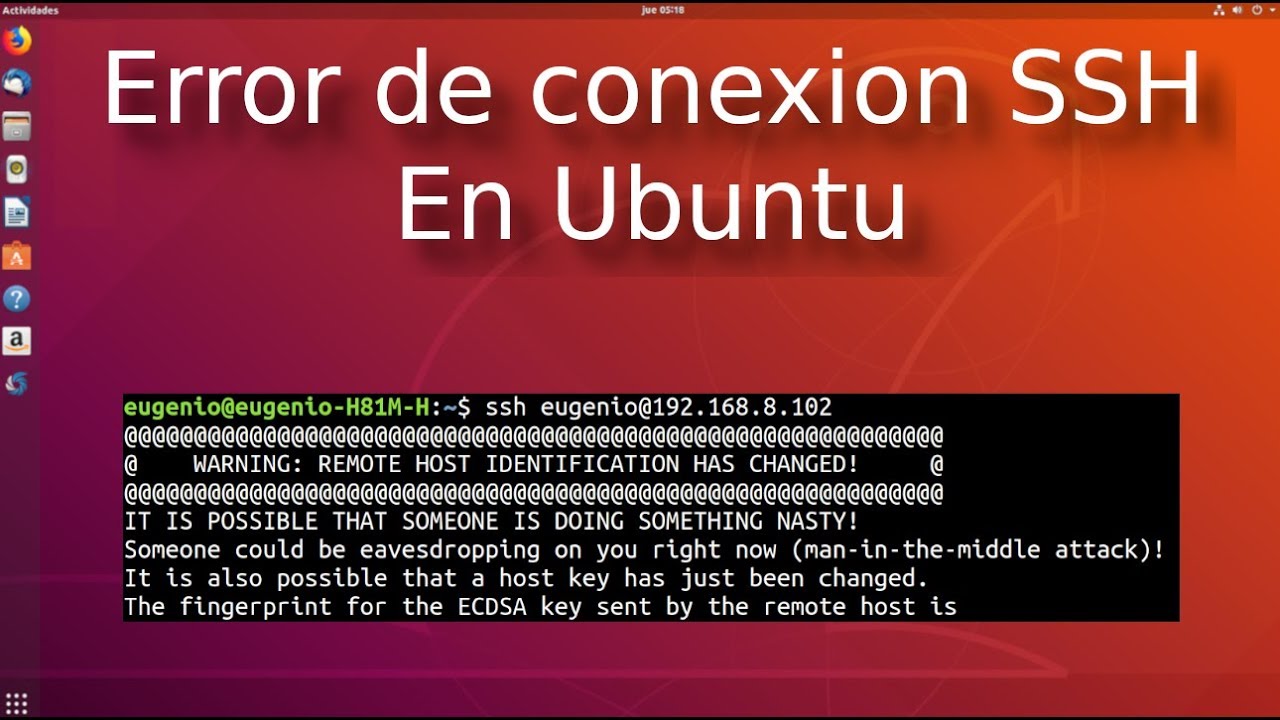
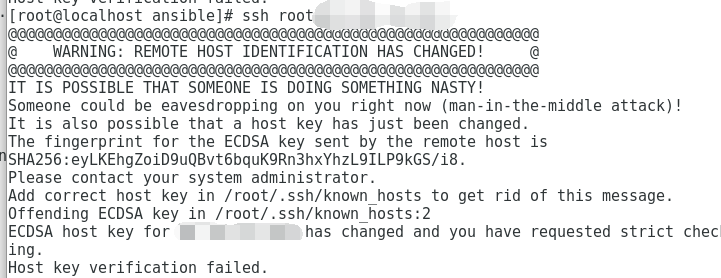
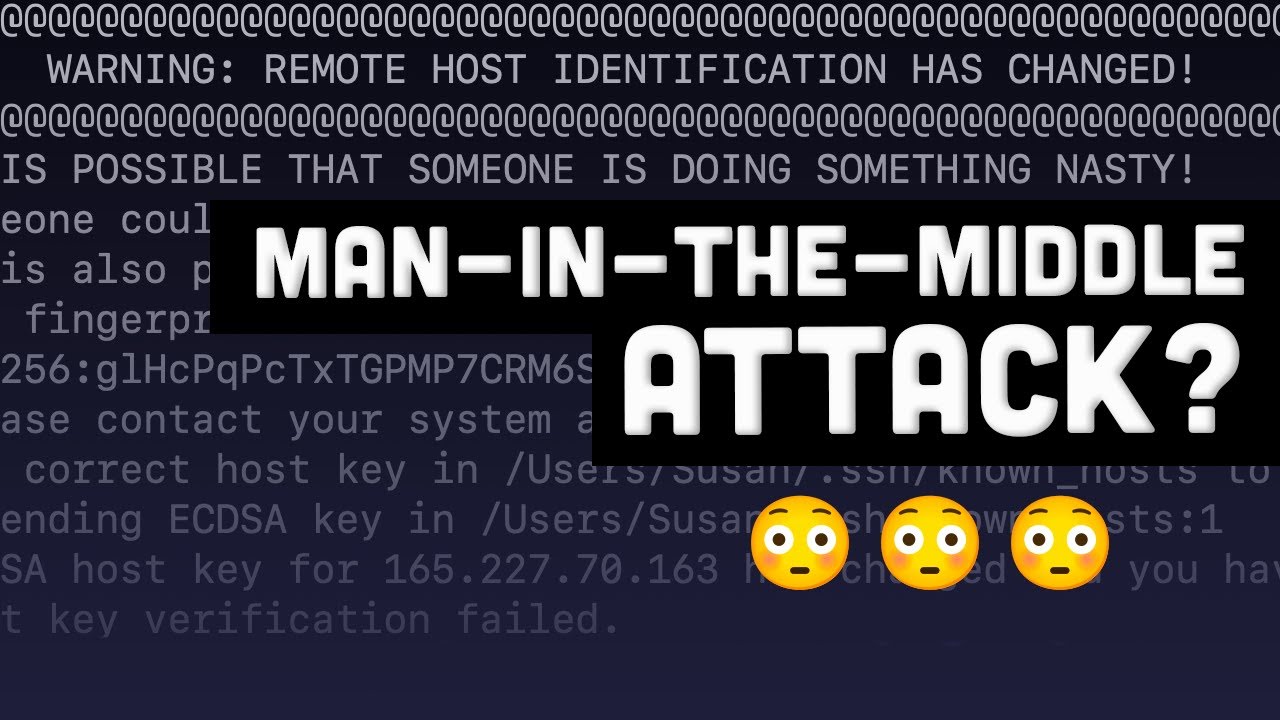
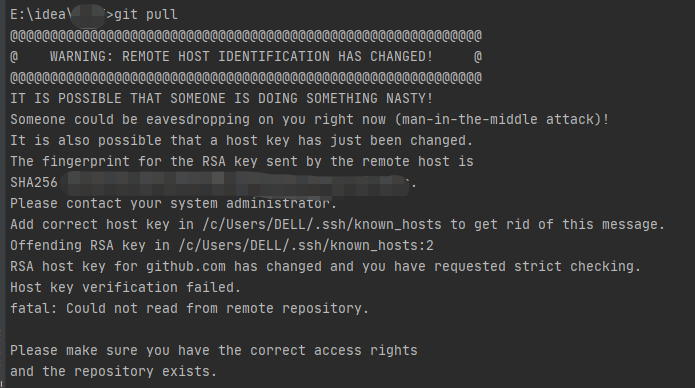
1. Connectivity Issues: When the remote host identification changes, users may encounter connection errors or warnings stating that the connection to GitHub is not secure. This can affect the ability to push, pull, clone, or interact with repositories.
2. Security Risks: Ignoring or bypassing remote host identification changes can expose users to security risks. Without proper verification, it becomes easier for attackers to impersonate GitHub servers and intercept sensitive data or inject malicious code.
Step-by-Step Guide to Resolving Remote Host Identification Changes on GitHub
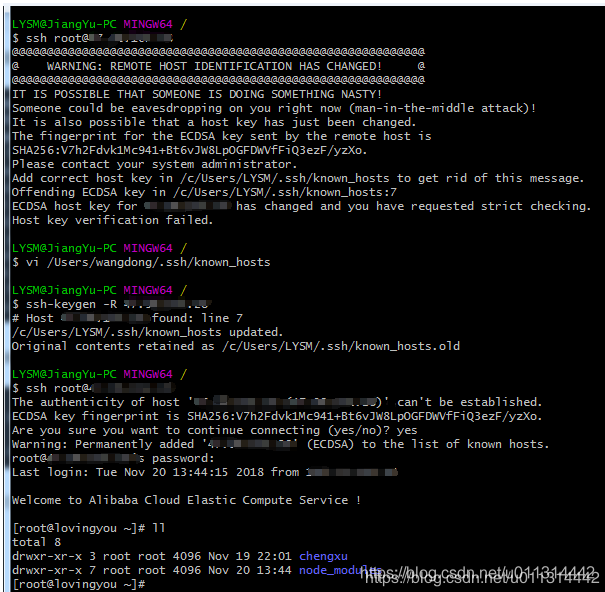
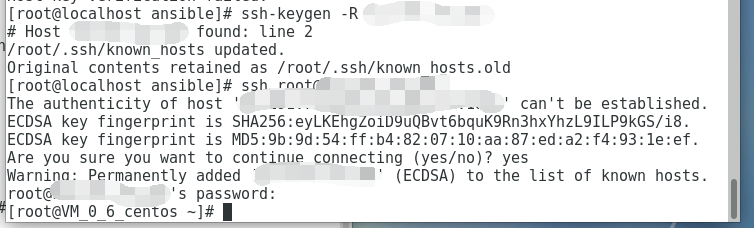
1. Update SSH Known Hosts: If you encounter a warning about a changed remote host identification, update the SSH known hosts file on your local system. Use the following command in the terminal or command prompt:
“`
ssh-keygen -R [hostname]
“`
Replace `[hostname]` with the GitHub hostname causing the identification change warning.
2. Confirm Change with GitHub: Visit the GitHub Status page or the GitHub help documentation to confirm whether there have been any recent host key changes. This will help determine whether the warning is valid or if it could potentially be a security breach.
3. Verify New Host Key: Once you have confirmed the change, obtain the new host key by connecting to the GitHub server using SSH and accepting the updated host key. For example:
“`
ssh -T [email protected]
“`
Follow the instructions provided to add the new host key to your known hosts file.
4. Update Known Hosts with StrictHostKeyChecking: You can avoid future remote host identification warnings by enabling the StrictHostKeyChecking option in your SSH configuration file. This option ensures that SSH only connects to hosts whose keys are already present in the known hosts file. Add the following line in the `~/.ssh/config` file:
“`
StrictHostKeyChecking yes
“`
Best Practices to Prevent and Manage Remote Host Identification Changes
1. Regularly Update Known Hosts: To prevent surprises, periodically update your known hosts file with the latest host keys for GitHub. This ensures that your local machine is up to date with any changes made to the remote host identification.
2. Monitor GitHub Status: Stay informed about any scheduled or unexpected host key changes by regularly checking the GitHub Status page. This allows you to quickly identify whether a remote host identification change is legitimate or a potential security threat.
3. Leverage Two-Factor Authentication: Enable two-factor authentication (2FA) on your GitHub account to add an extra layer of security. By doing so, even if an attacker gains access to your SSH credentials, they would not be able to authenticate without the 2FA code.
Understanding the Security Implications and Risks Associated with Remote Host Identification Changes
Remote host identification changes pose potential security risks if not addressed properly. Ignoring or bypassing these identification changes can result in establishing connections with unauthorized servers, leading to unintended consequences such as unauthorized access, data interception, or code injection.
Subsequently, it becomes crucial to verify remote host identification changes and ensure their authenticity before proceeding with any communication or interactions with GitHub. By promptly updating known host keys and taking necessary security precautions, users can mitigate these risks and maintain a secure environment for their GitHub activities.
Resources for Further Learning about Remote Host Identification on GitHub
1. GitHub Help Documentation: The GitHub Help documentation provides detailed information about various aspects of remote host identification, including best practices, troubleshooting steps, and security considerations. Visit the following link to access relevant resources: [https://docs.github.com/en/authentication/troubleshooting-ssh](https://docs.github.com/en/authentication/troubleshooting-ssh)
2. GitHub Community Forum: The GitHub Community Forum serves as a platform for users to ask questions, seek assistance, and share experiences related to remote host identification and other GitHub-related topics. Interacting with the community can provide valuable insights and help resolve any issues you may encounter. Access the forum at: [https://github.community/c/how-to-use-github/47](https://github.community/c/how-to-use-github/47)
3. SSH Documentation: If you want to explore SSH and remote host identification in more detail, the official SSH documentation provides comprehensive information about the SSH protocol, its security features, and how to configure SSH for secure communication. Refer to the following link: [https://www.ssh.com/ssh/](https://www.ssh.com/ssh/)
FAQs
Q1. Why am I seeing a remote host identification warning on GitHub?
A1. Remote host identification warnings on GitHub usually occur when the host key presented by the GitHub server does not match the known host key stored on your local machine. This can happen due to host key changes on GitHub’s end or potential security breaches. It is important to verify the change before proceeding.
Q2. Is it safe to accept a changed remote host identification on GitHub without verifying it?
A2. No, it is not recommended to accept a changed remote host identification without verifying its authenticity. Doing so can potentially expose you to security risks, as it could indicate an attempt by an attacker to impersonate the GitHub server. Always confirm the change with reliable sources before updating the known hosts file.
Q3. How often does GitHub change its remote host identification?
A3. GitHub periodically updates host keys for various reasons, including security enhancements or server infrastructure changes. The frequency of host key changes can vary, and it is best to rely on GitHub’s official channels, such as the Status page, for up-to-date information on any changes.
Q4. Can I disable remote host identification checks to avoid warnings?
A4. Disabling remote host identification checks is highly discouraged, as it compromises the security of your connection. Remote host identification serves as a crucial security measure to prevent attacks and ensure the authenticity of the server you are connecting to. Always follow best practices and update known hosts on your local machine instead.
How To Fix Warning Remote Host Identification Has Changed
Keywords searched by users: github remote host identification has changed
Categories: Top 51 Github Remote Host Identification Has Changed
See more here: nhanvietluanvan.com
Images related to the topic github remote host identification has changed

Found 36 images related to github remote host identification has changed theme










![SOLVED] SSH : WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED - YouTube Solved] Ssh : Warning: Remote Host Identification Has Changed - Youtube](https://i.ytimg.com/vi/d0RBXye8qpI/maxresdefault.jpg)






![SOLVED] Cannot access over SSH - Remote Host ID changed - Beginners - openHAB Community Solved] Cannot Access Over Ssh - Remote Host Id Changed - Beginners - Openhab Community](https://community-openhab-org.s3.dualstack.eu-central-1.amazonaws.com/original/3X/c/3/c35ebcdc04ac2bc32bf270302d9547a73f60c04c.png)














Article link: github remote host identification has changed.
Learn more about the topic github remote host identification has changed.
- How To Deal With the “Remote Host Identification Has …
- Has GitHub changed his remote host key ? #50878
- Why are connections to GitHub over SSH throwing an error …
- We updated our RSA SSH host key – The GitHub Blog
- GitHub Error: WARNING: REMOTE HOST IDENTIFICATION …
- How To Fix “Warning: Remote Host Identification Has … – Kinsta
- Solved: Git Clone “Remote Host Identification Has Changed …
- Git Error for GitHub repositories: warning: remote host …
- How to fix “Remote Host Identification Has Changed” Issue …
- Github host key changed? – LLVM Discourse