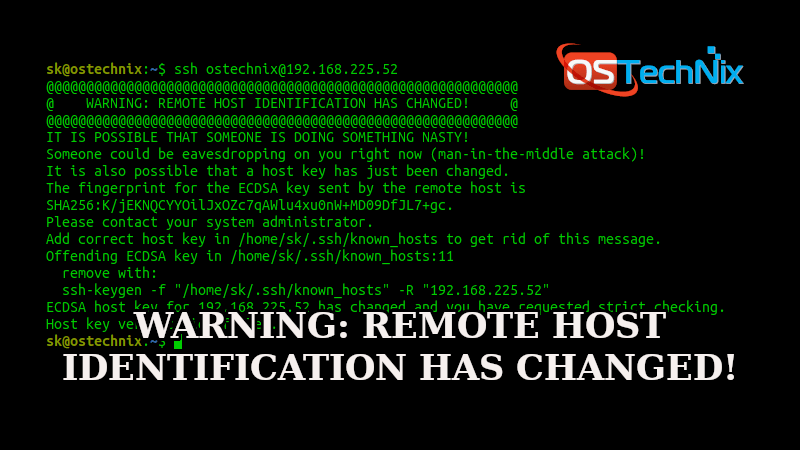
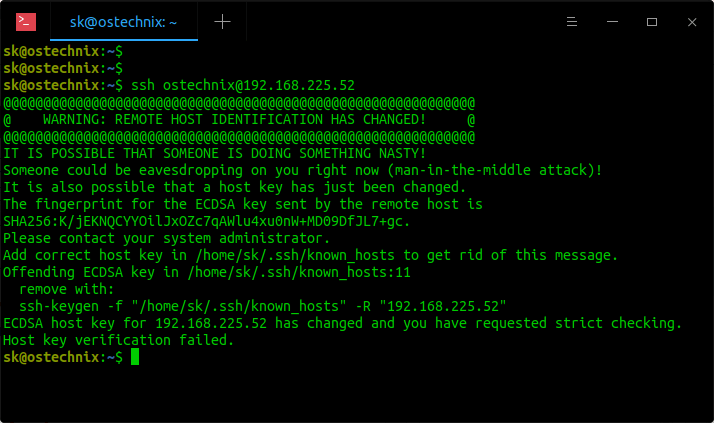
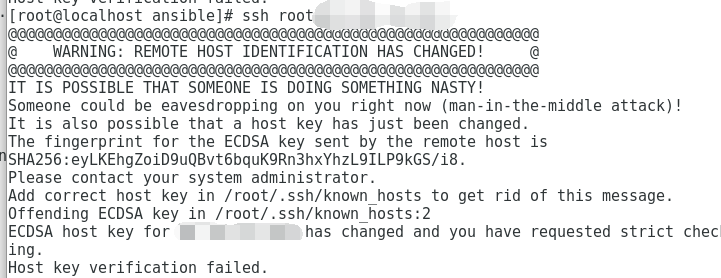
Git Warning Remote Host Identification Has Changed
Introduction:
When working with Git, users may encounter a warning message stating “remote host identification has changed.” This issue occurs when the host key, which is used to authenticate the remote server, has changed since the last connection. While it may seem alarming, this warning is designed to protect users from potential security risks. In this article, we will delve into the potential causes of this warning, steps to verify the authenticity of the remote host, how to update the remote host identification, preventive measures, and the consequences of ignoring the warning.
1. Overview of the “Git Warning: Remote Host Identification Has Changed” Message:
The warning message indicates that the remote host key has changed since the last connection and advises users to take appropriate action. It serves as a security measure by ensuring that users are not connecting to a different or compromised server.
2. Potential Causes for the Remote Host Identification Change:
Several factors can lead to a change in remote host identification:
– The remote server has been reinstalled or reconfigured.
– The IP address or DNS name of the remote server has changed.
– A man-in-the-middle attack has occurred, compromising the security of the connection.
3. How to Verify the Authenticity of the Remote Host:
To validate the authenticity of the remote host, follow these steps:
– Compare the host key fingerprint displayed in the warning message with the previously known fingerprint.
– Confirm the change with the system administrator or the owner of the remote host.
– Utilize alternative methods to authenticate the server, such as checking with a trusted source or using PGP keys.
4. Steps to Resolve the Warning and Update the Remote Host Identification:
To resolve the warning, execute the following steps:
– Firstly, do not ignore the warning as it may pose a security risk.
– Confirm the change in host identification to ensure validity.
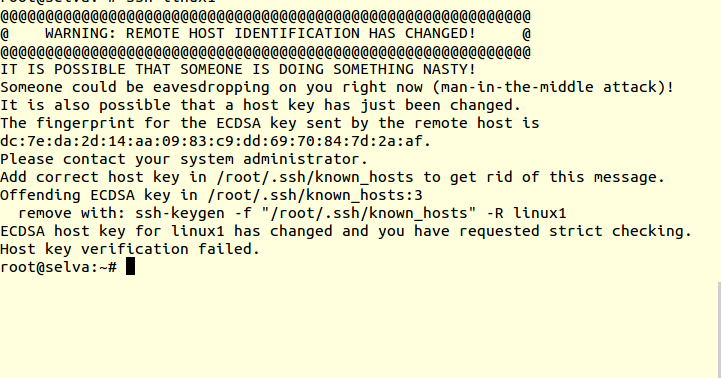
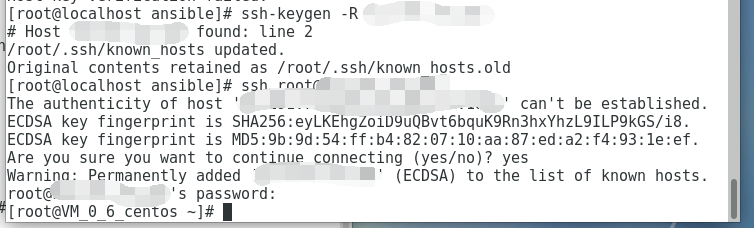
– Remove the outdated host key by editing the known_hosts file or using SSH-keygen to delete the specific entry.
– Initiate a new connection to the remote host to obtain the updated host key.
– Confirm that the new host key has been added to the known_hosts file.
5. Tips for Preventing Remote Host Identification Changes in the Future:
To mitigate the likelihood of encountering this warning:
– Regularly update and maintain your system, including the remote server and client machine.
– Utilize static IP addresses or reliable DNS systems.
– Implement measures such as two-factor authentication for added security.
– Use SSH known_hosts file hashing to improve and secure host key storage.
6. Understanding the Potential Consequences of Ignoring the Warning:
Choosing to ignore the “remote host identification has changed” warning can lead to severe consequences, including:
– Compromised security: Connecting to an unauthorized or falsified remote host can expose sensitive data and lead to unauthorized access.
– Impacted reputation: Ignoring security warnings may result in breaches and damage your reputation.
– Loss of data: Connecting to an unauthenticated remote host can lead to data loss, corruption, or tampering.
FAQs:
Q1. Why do I receive a “Warning: remote host identification has changed” message on Ubuntu?
A1. This warning typically occurs when the host key of the remote server has changed, possibly due to reinstallation, reconfiguration, or a man-in-the-middle attack.
Q2. How do I fix the warning “Warning: remote host identification has changed” on a Raspberry Pi?
A2. To resolve the warning on a Raspberry Pi, you can edit the known_hosts file or utilize SSH-keygen to remove the outdated entry and establish a new connection to the remote host.
Q3. I am unable to connect to GitHub due to “[email protected]: permission denied (publickey)” error. What should I do?
A3. This error often occurs due to changes in the GitHub host key. To resolve the issue, follow the instructions provided by GitHub, such as updating your SSH keys or confirming the host key.
Q4. How can I avoid future remote host identification changes?
A4. Regularly updating and maintaining your system, using static IP addresses or reliable DNS systems, and implementing security measures like two-factor authentication can help prevent such changes in the future.
Conclusion:
The “git warning: remote host identification has changed” message serves as a valuable alert, ensuring users are not connecting to compromised servers. By promptly addressing this warning, verifying the authenticity of the remote host, and taking necessary actions, users can safeguard their data, maintain security, and prevent potential threats.
How To Fix Warning Remote Host Identification Has Changed
Why Does Warning Remote Host Identification Has Changed?
Introduction:
When working with remote servers and establishing SSH (Secure Shell) connections, you may come across a warning message stating “Remote Host Identification Has Changed.” This security feature may confound some users who are uncertain about its cause and potential implications. In this article, we will delve into the reasons behind this warning message, exploring both technical and security aspects, and provide clarity for users encountering this warning.
Understanding the Warning:
When connecting to a remote server via SSH, your client software stores the server’s host key locally to verify its identity in subsequent connections. The host key acts as a fingerprint for the server—a unique identifier that allows the client to recognize and trust the remote server. The first time you connect to a new server, your client software prompts you to verify the host key and, if confirmed, saves it for future references.
If at any point the server’s host key changes, your client software perceives it as a potential security threat. To keep users informed about any modifications to the host key, the “Remote Host Identification Has Changed” warning message is displayed. This alert aims to protect users from man-in-the-middle attacks, where a malicious actor attempts to intercept and manipulate the communication between the user and the server.
Reasons for Host Key Change:
Several legitimate reasons can result in a host key change, and it’s crucial to understand them to assess the severity of the warning message. Below are some common scenarios that can lead to a changed host key:
1. Server Reinstallation or Migration: When a server undergoes reinstallation, or if it is migrated to a different hosting provider or physical machine, a new host key is generated. This change is normal and expected in such cases.
2. Security Breach or Compromise: In unfortunate situations where a server falls victim to a security breach, the attacker might gain access to the server’s private key. To prevent further unauthorized access, the administrator will revoke the compromised key and generate a new one. These instances should raise significant concern and warrant thorough investigation.
3. Server Updates or SSH Reconfiguration: Sometimes, performing system updates or reconfiguring SSH settings leads to a change in the host key. These updates may include changes to the SSH protocol version, key exchange algorithms, or cryptographic settings.
Handling the Warning:
When confronted with the warning message stating “Remote Host Identification Has Changed,” it is essential to cautiously investigate the reason behind the key change. Before proceeding, consider the following steps:
1. Verify the Server Authenticity: Ensure that you are connecting to the correct server. Check the server’s IP address, hostname, and any other identifier to confirm that it matches your intended destination. Confirm with other reliable sources if required.
2. Understand the Severity: If the host key change is due to a server reinstallation or migration, but the server identity can be verified, the warning can be safely ignored. However, if there is any doubt regarding the server’s integrity or a security breach is suspected, it is recommended to proceed with caution and contact the server administrator for further guidance.
3. Update Local Host Key: If necessary, update your local copies of the server’s host key to rectify the warning message. Depending on the client software you are using, you might need to locate the host key file and delete the existing entry to generate and save the new host key associated with the server.
FAQs:
1. Can I trust the new host key after encountering the warning message?
The trustworthiness of the new host key depends on the reason for its change. If it was a result of a server reinstallation or migration, n\there should be no cause for concern. However, if there is suspicion of a security breach or compromise, further authentication and investigation are necessary before proceeding.
2. Is it always necessary to update the local host key after encountering the warning?
No, it is not always necessary to update the host key. If you are confident in the server’s identity and the reason for the change is legitimate (e.g., server reinstallation), you can safely ignore the warning. However, caution should be exercised when dealing with the warning in suspicious circumstances.
3. Can I restore the previous host key if I made a mistake in accepting the new one?
In some cases, the previous host key might still be stored locally, usually in a known_hosts file. By restoring the previous entry in this file, you can revert to the previous key. However, exercise caution and ensure that you are reverting to a trusted host key to avoid any security risks.
Conclusion:
Encountering the warning message “Remote Host Identification Has Changed” during SSH connections might initially cause unease, but understanding the reasons behind it can bring clarity. By distinguishing between different causes for a host key change, users can assess the severity of the warning and take appropriate actions to ensure their security and protect against potential attacks. Always be cautious when handling such warnings and verify the server’s authenticity before proceeding, particularly if any suspicion of a security breach arises.
Why Does Rsa Host Key Change?
RSA (Rivest-Shamir-Adleman) is a widely used public key cryptosystem that ensures secure and encrypted communication over the internet. To establish a secure connection, RSA uses a host key for key exchange and authentication. However, users often encounter situations where the RSA host key changes. In this article, we will delve into the reasons behind RSA host key changes, discuss the implications, and address frequently asked questions related to this topic.
Understanding the RSA Host Key:
Before we dive into why the RSA host key changes, let’s gain a basic understanding of what it actually is. In RSA, the host key is a cryptographic key used by the server to prove its identity to clients during the initial handshake process. It allows clients to verify that they are connecting to the intended server and not to an imposter.
Why Does RSA Host Key Change?
There are several reasons why the RSA host key may change:
1. Security Breach: If a server experiences a security breach, it is highly recommended to change its host key. If an attacker gains unauthorized access to the server’s private key, they can impersonate the server and potentially intercept sensitive information. Changing the host key mitigates the risk of compromised security.
2. Key Expiration: RSA host keys are typically associated with a validity period. After the expiration, the server requires a new key to ensure the highest level of security. The process of changing the host key before its expiration is a proactive measure to maintain the encryption integrity.
3. Server Migration: In the case of server migration, where a website/app moves to a new hosting provider or infrastructure, the RSA host key has to change. This change is necessary as the new server will have a different public-private key pair.
4. Software Upgrades: Sometimes, servers undergo software upgrades, which can lead to changes in the RSA host key. Upgrades may be required to patch security vulnerabilities or improve performance. Such upgrades often result in a host key change to ensure the new software version aligns with the latest cryptographic standards.
5. Key Compromise: If the server’s private key is compromised due to a stolen or lost key pair, an immediate key change is crucial. It prevents unauthorized access and ensures the confidentiality of the data exchanged between the server and clients.
Implications of RSA Host Key Changes:
When the RSA host key changes, it has implications for both server administrators and clients:
1. Trust Establishment: Clients may become wary when they encounter a changed host key. Initially, they might assume it to be a potential security threat or a man-in-the-middle attack. However, they should understand that key changes are often necessary for maintaining the security of their connection.
2. Verification Process: Clients need to verify the new host key to ensure that they are connecting to the intended server. They should cross-check the new key with a trusted source, such as the server administrator or their organization’s IT department. Failure to verify the new host key may result in connecting to an imposter server, compromising data security.
Frequently Asked Questions (FAQs):
Q1: How can I verify the authenticity of the new RSA host key?
A1: To verify the authenticity of the new RSA host key, you should contact the server administrator or a trusted source. Consult the server’s website, official documentation, or contact the organization’s IT department to obtain the new key.
Q2: Is it safe to accept the new host key when connecting to a server?
A2: If you have verified the authenticity of the new host key through a trusted source, it is safe to accept it. However, be cautious when accepting host keys without proper verification, as it could indicate a potential security risk.
Q3: Can a changed RSA host key affect existing connections?
A3: No, a changed RSA host key does not affect existing connections. The new host key only applies to future connections. Existing connections will continue to use the old host key until they are terminated.
Q4: How often should I expect the RSA host key to change?
A4: The frequency of RSA host key changes depends on various factors such as security policies, server administration practices, and the specific circumstances mentioned earlier. It is recommended to review and change host keys periodically to ensure optimal security.
Conclusion:
The RSA host key change is a fundamental process to maintain data security and prevent unauthorized access. It occurs due to security breaches, key expiration, server migrations, software upgrades, or key compromises. While changes in the RSA host key may initially raise concerns, it is crucial for clients to verify the new key through trusted sources. By understanding the reasons behind these changes and taking necessary precautions, users can continue to communicate securely over the internet.
Keywords searched by users: git warning remote host identification has changed WARNING: remote host IDENTIFICATION has changed ubuntu, Warning remote host identification has changed vps, RSA host key for GitHubcom has changed and you have requested strict checking, Ssh-keygen, host key verification failed., Warning remote host identification has changed raspberry pi, [email protected]: permission denied (publickey)., GitHub SSH key
Categories: Top 25 Git Warning Remote Host Identification Has Changed
See more here: nhanvietluanvan.com
Warning: Remote Host Identification Has Changed Ubuntu
Remote host identification is an important aspect of secure communication between client and server systems. When connecting to a remote server, Ubuntu performs a host identification check to ensure that the server’s identity matches the previously stored fingerprint. This process is crucial for protecting against man-in-the-middle attacks and verifying the authenticity of the remote server.
However, there are instances when the remote host identification changes, resulting in a warning message displayed by Ubuntu. This warning is an indication that the server’s identity has changed since the last successful connection, flagging a potential security risk. Let’s delve deeper into this warning, its causes, and how to mitigate the associated risks.
Causes of Remote Host Identification Change
Several reasons can lead to a remote host identification change in Ubuntu. The most common causes are:
1. System Reinstallation: If the server’s operating system undergoes a reinstallation or upgrade, the associated SSH keys used for host identification will also change. As a result, clients connecting to the server will be prompted with the warning message.
2. Server IP Address Change: When a server changes its IP address due to network modifications or reconfiguration, the remote host identification will also change. This can occur if the server is moved to a different physical location or if the IP assignment is altered on the network.
3. Security Breach: Another potential cause for remote host identification change is a security breach. If unauthorized individuals gain access to the server and tamper with its SSH keys, the subsequent change will trigger the warning message when clients attempt to connect to the compromised server.
4. Host Key Rotation: Server administrators may occasionally rotate their host keys for security reasons. This involves generating new SSH keys and exchanging them with clients. Since the new keys differ from the previously stored ones, Ubuntu will raise the remote host identification warning.
Mitigating the Risks and Addressing the Warning
When faced with the remote host identification warning in Ubuntu, it is crucial to take appropriate steps to safeguard your communication. Depending on the cause of the identification change, there are several approaches to address the issue:
1. Verify the Change: If you believe the change was intentional, such as due to an OS upgrade or a planned host key rotation, you can proceed with accepting the new identification. Before accepting, make sure to confirm the change with the server administrator through a trusted communication channel to ensure that the identification change is legitimate.
2. Confirm the IP Address Change: In cases when the remote host identification changed due to an IP address modification, it is essential to verify that the server’s IP address was indeed altered. Confirm with the server administrator or refer to network configuration documentation to ensure that the server’s new IP address is accurate.
3. Investigate Security Breach Possibility: If the remote host identification changed unexpectedly, it could indicate a security breach. In such cases, it is crucial to investigate the possibility of unauthorized access and the subsequent tampering of SSH keys. Analyze log files, review system activity, and consult with your organization’s security team to determine if a breach occurred and take necessary remedial actions.
4. Remove Old Host Keys: If you are certain that the remote host identification change is not due to an authorized action and that there are no security breaches, there is a possibility that the stored SSH keys on your Ubuntu client system are outdated or inaccurate. In such cases, you can remove the old and potentially compromised host keys from your client’s known_hosts file. This file is typically located in the ~/.ssh directory, and removing the relevant line for the affected server will prompt Ubuntu to store the new identification on the next connection attempt.
FAQs
Q1. Can I trust the new remote host identification after receiving the warning?
A1. It depends on the circumstances. If the identification change was authorized by the server administrator or could be confirmed through a trusted communication channel, you can trust the new identification. However, if the change was unexpected or suspicious, further investigation is necessary to ensure the server’s integrity and security.
Q2. How often should I expect remote host identification changes?
A2. Remote host identification changes are not frequent occurrences. They typically happen during server system upgrades, IP address modifications, or host key rotations, which are infrequent events in a stable system. Unexpected changes can indicate potential security breaches and should be handled diligently.
Q3. Does the warning mean I am being hacked?
A3. Not necessarily. The warning is a cautionary message that can signal a potential security risk, but it does not confirm a hacking attempt. It is essential to investigate further to determine if any unauthorized access or tampering has occurred.
Q4. Can I disable the remote host identification warning in Ubuntu?
A4. Disabling the remote host identification warning is not recommended, as it eliminates an essential security feature. The warning serves as a safeguard against man-in-the-middle attacks and unauthorized server access attempts. Instead, addressing the issue causing the warning is the recommended course of action.
Warning Remote Host Identification Has Changed Vps
Introduction:
In the world of virtual private servers (VPS), it is important to maintain a secure connection with the host. However, there may be instances where you receive a warning that says, “Warning: remote host identification has changed.” This notification can be quite alarming to those unfamiliar with the message, as it may indicate a potential security breach. In this article, we will delve into the details of this warning, discuss its implications, and provide guidance on how to proceed.
Understanding the Warning:
The warning, “Warning: remote host identification has changed,” typically appears when attempting to connect to a VPS using a Secure Shell (SSH). This message is designed to safeguard users from potential security threats. SSH relies on cryptographic keys to authenticate and establish a secure connection. The first time you connect to a host, your local machine stores the host’s key fingerprint. In subsequent connections, SSH compares the stored fingerprint with the one received from the host. If the fingerprints do not match, the warning is triggered.
Implications and Potential Risks:
While the warning can be a symptom of a security breach, it is essential not to panic. There are several scenarios where the remote host identification may change innocuously. For instance, if the host’s administrator regenerated the host keys due to a security update, or if the IP address of the host changed, the warning would be triggered. However, it is crucial to assess the situation carefully and consider potential risks before proceeding.
If the warning is unexpected and you cannot attribute it to any administrative changes, it could signify a compromised server or a man-in-the-middle attack. In such instances, an unauthorized third party might redirect your connection to a malicious host that mimics the original. Attackers can intercept sensitive information or launch further attacks on your system. Therefore, it is essential to investigate the matter further before proceeding with the connection.
How to Proceed:
1. Confirm Legitimacy: In case of an unexpected warning, it is crucial to verify the legitimacy of the host by contacting the server administrator. Use a different communication channel, such as a phone call or a trusted email address, to ensure you are not inadvertently contacting the attacker.
2. SSH Key Change: If the host’s cryptographic keys have been legitimately changed, you need to update your local machine with the new fingerprint. Remove the outdated fingerprint by editing or deleting the corresponding line in your SSH known_hosts file. When you attempt to reconnect, your local machine will store and recognize the new fingerprint.
3. Verify Logs: Checking system logs, especially the SSH logs, may provide valuable insights into any unauthorized access attempts or malicious activities. Look for any suspicious entries or patterns that justify the remote host identification change.
4. Enhance Security Measures: Regardless of the outcome, it is advisable to reinforce your security measures. Enable multi-factor authentication, regularly update your software, use strong passwords, and consider implementing intrusion detection and prevention systems on your VPS.
FAQs:
1. Can I simply ignore the warning and proceed with the connection?
Ignoring the warning without proper investigation can potentially expose your system to security risks. Always err on the side of caution and investigate the cause before proceeding.
2. Why should I contact the server administrator?
Contacting the server administrator helps confirm the legitimacy of the host, providing an additional layer of security and reassurance.
3. What should I do if the fingerprints do not match and the administrator confirms no changes were made?
In this scenario, it is critical to remain vigilant. Treat the situation as a potential security breach and proceed by assessing logs, investigating any suspicious activities, and enhancing your security measures.
4. How frequently do host key changes occur?
Host key changes vary depending on the server’s security policies, software updates, or IP address changes. It is not uncommon for host keys to change periodically.
Conclusion:
When faced with the warning, “Warning: remote host identification has changed,” it is paramount to approach the situation with caution. While it can be due to legitimate administrative changes, it may also indicate a security breach. By following the guidelines provided in this article, you can verify the legitimacy of the host, protect your system from potential risks, and ensure a secure connection to your VPS. Stay vigilant and prioritize security to safeguard your online presence.
Images related to the topic git warning remote host identification has changed

Found 23 images related to git warning remote host identification has changed theme









![SOLVED] SSH : WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED - YouTube Solved] Ssh : Warning: Remote Host Identification Has Changed - Youtube](https://i.ytimg.com/vi/d0RBXye8qpI/maxresdefault.jpg)
















Article link: git warning remote host identification has changed.
Learn more about the topic git warning remote host identification has changed.
- How To Deal With the “Remote Host Identification Has …
- How To Fix “Warning: Remote Host Identification Has … – Kinsta
- Why are connections to GitHub over SSH throwing an error …
- How to fix “Warning: remote host identification has changed”
- Solved: Git Clone “Remote Host Identification Has Changed …
- GitHub Error: WARNING: REMOTE HOST IDENTIFICATION …
- 3 Ways to fix remote host identification has changed
- Error Fix – Warning: Remote Host Identification Has Changed ⚠️
- We updated our RSA SSH host key – The GitHub Blog
- GitHub’s Private RSA SSH Key Mistakenly Exposed in Public …
- SSH Host Key Management Demystified
- How to fix: “WARNING: REMOTE HOST IDENTIFICATION …
See more: nhanvietluanvan.com/luat-hoc