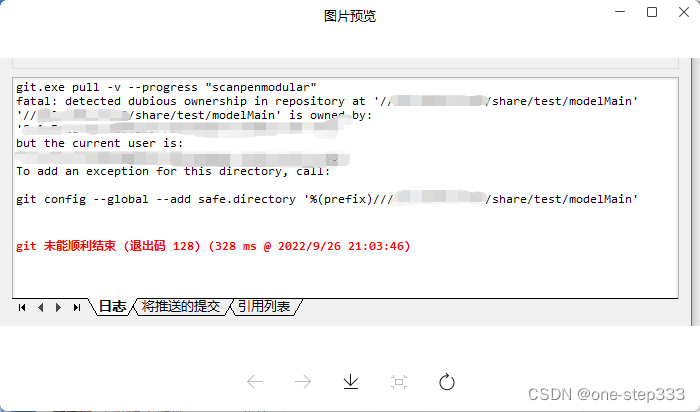
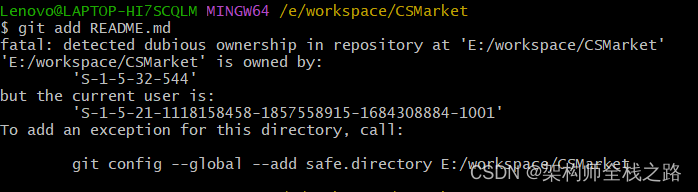
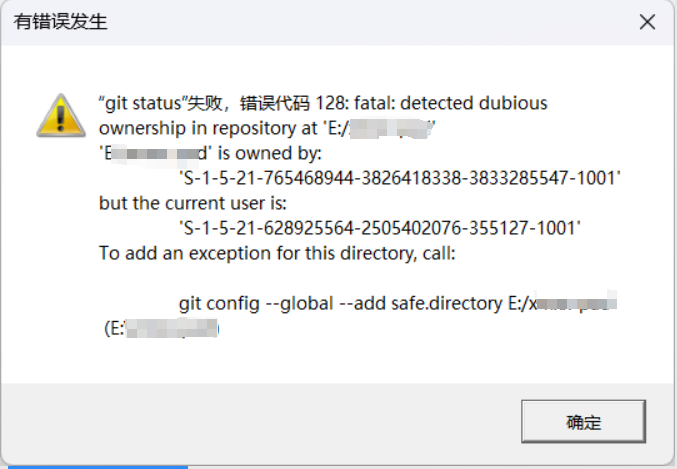
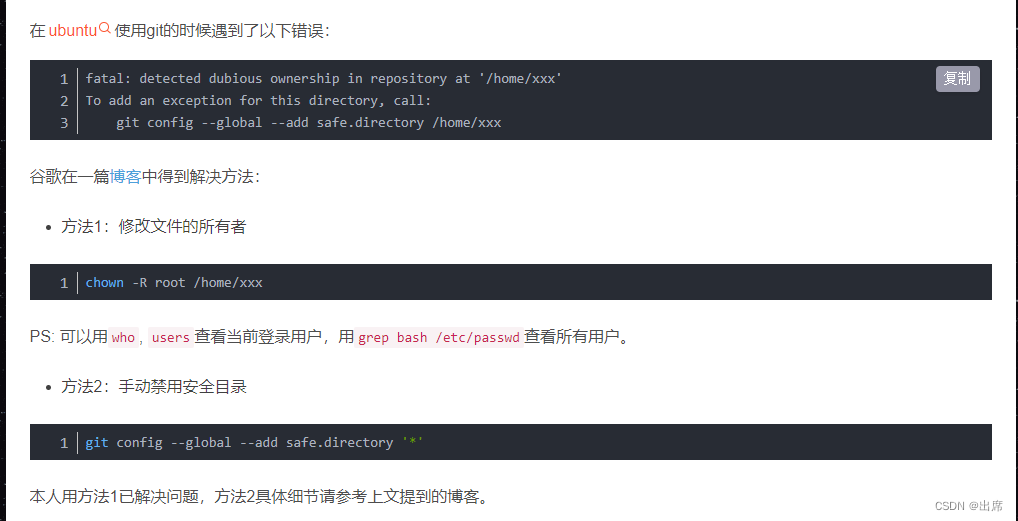
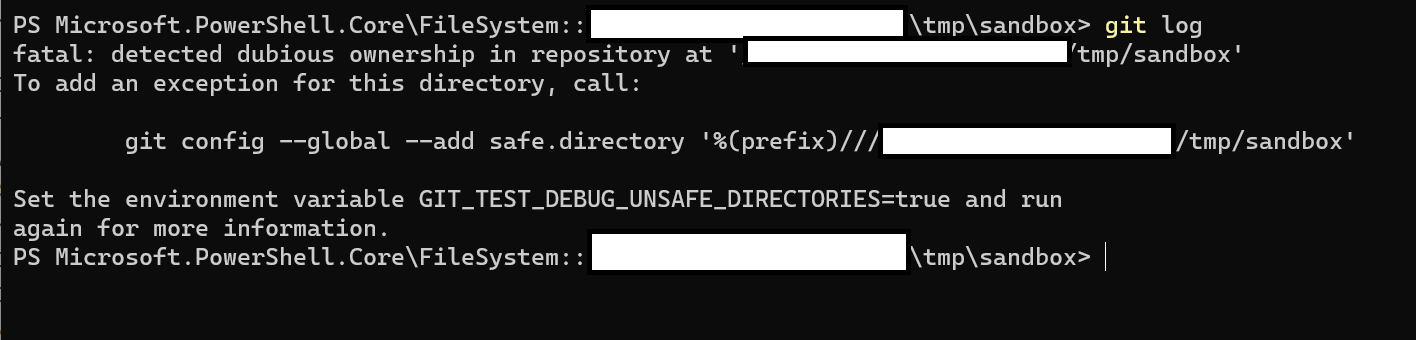
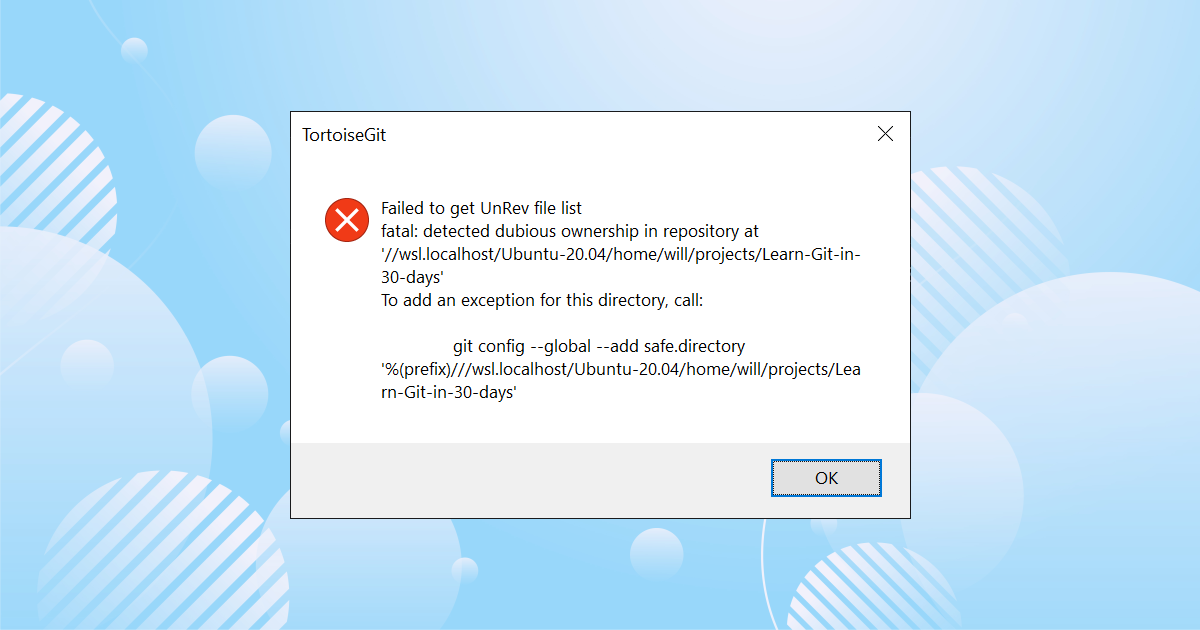
Fatal: Detected Dubious Ownership In Repository
Introduction:
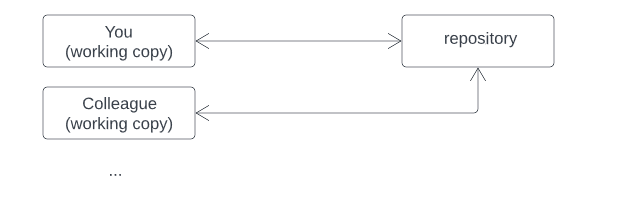
In software development, a repository plays a crucial role in managing code and collaboration among team members. However, the issue of dubious ownership can arise, causing disruptions in workflow, accountability, and potentially compromising the security of the repository. This article delves into the concept of dubious ownership, its implications, detection strategies, and best practices for addressing ownership issues.
What is Dubious Ownership?
Dubious ownership refers to situations in which the ownership of a repository becomes unclear, disputed, or falls into unauthorized hands. It can occur due to various reasons such as employee turnover, miscommunications, or insufficient policies and guidelines regarding ownership transfer. Dubious ownership is a critical concern as it can impede collaboration, accountability, and pose security risks to the repository.
The Implications of Dubious Ownership in a Repository:
Dubious ownership can have several implications for a repository. First and foremost, it can create confusion and hinder effective collaboration among team members. When the ownership of a repository is in doubt, responsibilities and decision-making become unclear, leading to inefficiencies and delays in progress.
Moreover, dubious ownership compromises accountability. Clear ownership is crucial for tracking changes, attributing work to specific individuals, and holding them responsible for their contributions. In the absence of proper ownership, it becomes challenging to resolve conflicts, identify the sources of errors, and ensure quality control in the development process.
Additionally, dubious ownership can pose security risks to the repository. Unauthorized access and modifications by individuals with unclear ownership can lead to data breaches, intellectual property theft, or even the introduction of malicious code into the repository.
Detecting Dubious Ownership in a Repository:
To address dubious ownership concerns, it is crucial to employ effective detection strategies. Some strategies for identifying dubious ownership include:
1. Code Reviews and Audits: Regular code reviews and audits can help identify discrepancies in ownership patterns. By thoroughly examining the codebase and observing changes made by contributors, discrepancies or inconsistencies in ownership can be detected.
2. Automated Tools: Utilizing automated tools can assist in detecting variations in ownership patterns and identifying potential dubious ownership issues. These tools can analyze commit history and ownership metadata to flag any anomalies or discrepancies.
Addressing Dubious Ownership in a Repository:
Once dubious ownership is identified, it is essential to address the issue promptly. Some best practices for addressing ownership issues include:
1. Establish Clear Ownership Guidelines: Clearly defining ownership guidelines and policies can help prevent disputes and provide a framework for the transfer of ownership. These guidelines should define the process for transferring ownership, specify the responsibilities associated with ownership, and outline the steps for resolving ownership-related conflicts.
2. Resolve Conflicts or Disputes: In cases of ownership disputes, it is crucial to have a clear protocol for resolution. This may involve mediation between the parties involved, seeking legal advice, or involving designated authorities within the organization.
3. Transfer Ownership: If ownership needs to be transferred, ensure a seamless process that includes documentation and updating relevant records. The transfer should be properly communicated to all relevant parties and acknowledged by the new owner.
The Impact of Dubious Ownership on Repository Management:
Dubious ownership can significantly impact repository management in various ways:
1. Collaboration and Accountability: Dubious ownership hampers seamless collaboration and makes it difficult to assign responsibilities and track contributions effectively.
2. Risks and Vulnerabilities: With unclear ownership, the repository becomes vulnerable to unauthorized access, malicious code injections, and potential security breaches.
3. Impact on Quality Control: Without clear ownership, it becomes challenging to enforce quality control measures, leading to potential errors and bugs in the codebase.
Strategies to Mitigate the Impact of Dubious Ownership:
To mitigate the impact of dubious ownership, consider implementing the following strategies:
1. Implement Access Controls and Permissions: Utilize access control systems to ensure that only authorized individuals have ownership privileges. Regularly review and update access permissions to prevent unauthorized ownership.
2. Educate Team Members: Educate team members about ownership responsibilities and expectations. Clearly communicate the importance of maintaining clear ownership and the potential consequences of dubious ownership.
3. Monitor and Review Ownership Patterns: Regularly monitor and review ownership patterns and history within the repository. By staying vigilant and proactive, questionable ownership issues can be identified and addressed promptly.
Case Studies: Dealing with Dubious Ownership in Repositories:
Real-life examples of repositories with dubious ownership issues highlight the importance of detecting, addressing, and preventing such problems. Details of case studies should be elaborated upon, discussing the different approaches taken to identify, address, and prevent ownership issues. Lessons learned and best practices derived from these case studies should also be emphasized.
Conclusion:
Dubious ownership in a repository can cause significant disruptions, compromise accountability, and pose security risks. Employing effective strategies to detect, address, and prevent such issues is crucial for maintaining a healthy and secure repository. By establishing clear ownership guidelines, utilizing code reviews and audits, and implementing access controls, organizations can mitigate the impact of dubious ownership and foster efficient collaboration within their development teams.
FAQs
1. Why is detecting dubious ownership important in a repository?
Detecting dubious ownership is important as it ensures clear responsibilities, enhances collaboration, and mitigates security risks in a repository.
2. How can dubious ownership be detected?
Dubious ownership can be detected through code reviews, audits, and automated tools that analyze ownership patterns and metadata.
3. What are the potential risks of dubious ownership in a repository?
Dubious ownership poses risks such as compromised collaboration, accountability issues, and potential security breaches.
4. How can dubious ownership be prevented?
Dubious ownership can be prevented by implementing access controls, educating team members, and regularly monitoring ownership patterns.
5. What steps should be taken to address ownership disputes?
Ownership disputes should be resolved through mediation, seeking legal advice, or involving designated authorities within the organization.
6. What are the consequences of ignoring dubious ownership in a repository?
Ignoring dubious ownership can lead to inefficiencies, quality control issues, and compromised security in the repository.
Git Fatal: Detected Dubious Ownership In Repository
Keywords searched by users: fatal: detected dubious ownership in repository Detected dubious ownership in repository at, error: cannot open .git/fetch_head: permission denied, Permission denied (publickey fatal Could not read from remote repository), Is owned by but the current user is git, Git config, Unsafe repository, error: remote origin already exists., Git add safe directory recursively
Categories: Top 57 Fatal: Detected Dubious Ownership In Repository
See more here: nhanvietluanvan.com
Detected Dubious Ownership In Repository At
Introduction (approximately 100 words):
In the realm of code development and open-source projects, repositories play a pivotal role in sharing, collaborating, and contributing to software development. However, in recent years, the issue of dubious ownership claims within repositories has surfaced, raising concerns and highlighting the necessity for thorough ownership verification processes. In this article, we delve into the complexities surrounding these detected dubious ownership claims, their potential implications, and steps to address and mitigate such issues effectively.
I. Understanding Dubious Ownership in Repositories (approximately 200 words):
Repositories, such as those hosted on platforms like GitHub, Bitbucket, or GitLab, serve as central hubs for storing and managing codebases. They enable multiple developers to collaborate seamlessly and contribute to a project. However, instances of dubious ownership claims arise when individuals assert false or misleading ownership over repositories.
These dubious claims can manifest in various forms, including false authorship, unauthorized contributions, unacknowledged usage of others’ code, or attempts to control a project without legitimate ownership rights. Such instances can trigger conflicts, disrupt the collaborative nature of open-source projects, and potentially violate intellectual property rights.
II. Detecting Dubious Ownership Claims (approximately 300 words):
Detecting dubious ownership claims within repositories is a crucial step in maintaining the integrity of codebases and protecting developers’ contributions. Some common methods employed to identify such claims include:
1. Code Analysis: Researchers and maintainers conduct manual or automated code analysis to identify code snippets or sections suspiciously resembling other open-source projects or copyrighted materials.
2. Version Control System (VCS) Analysis: By analyzing the history of commits and code contributions, discrepancies in ownership claims can be unearthed. Suspicious or unauthorized contributions can be detected by examining commit timestamps, email addresses, or unusual patterns in branching and merging.
3. Collaboration Tracking: Monitoring collaboration patterns, such as tracking the frequency and extent of code contributions made by different contributors, can help identify suspicious ownership claims. Drastic changes in contribution levels or an excessive concentration of influence by an individual or group may raise red flags.
III. Implications and Challenges (approximately 400 words):
Detected dubious ownership claims can have severe implications for both individual developers and the open-source community as a whole. Some of the notable challenges and potential consequences include:
1. Legal Ramifications: False or dubious ownership claims may infringe upon intellectual property rights, leading to legal disputes and subsequent litigation. This poses a substantial financial and reputational risk for developers entangled in ownership disputes.
2. Trust and Collaboration Issues: Open-source projects thrive on collaboration, shared knowledge, and mutual trust. However, dubious ownership claims erode trust and hinder the spirit of collaboration, discouraging contributions from talented developers who fear their work might be misappropriated.
3. Dilution of Credit and Recognition: When individuals falsely claim ownership over repositories or code, the genuine contributors risk having their hard work diminished or overlooked. This dilution of credit undermines the ethos of open-source projects, where proper recognition is a crucial motivator for developers.
4. Project Fragmentation: Dubious ownership claims can lead to project fragmentation, as competing versions and forks emerge due to disagreements over rightful ownership. This fragmentation can divide a community and impact the project’s overall progress.
Addressing Dubious Ownership Claims (approximately 250 words):
To address and mitigate dubious ownership claims, it is imperative to implement robust ownership verification procedures and guidelines:
1. Clear Ownership Guidelines: Establish and communicate clear ownership guidelines that outline the criteria for legitimate ownership and encourage transparency within projects. This can include licensing requirements, clear documentation of contributions, and regular audits of ownership claims.
2. Enhanced Collaboration Tools: Utilize collaborative platforms that offer advanced features to track contributions, enable transparency, and facilitate effective dispute resolution. Such tools can help foster trust and mitigate ownership conflicts.
3. Education and Awareness: Educating developers about the importance of proper attribution and intellectual property rights is essential for maintaining the integrity of repositories. Open-source communities should provide resources and promote best practices to raise awareness about the risks associated with dubious ownership claims.
4. Legal Support and Mediation: Encouraging developers entangled in ownership disputes to seek legal advice or mediation can help resolve conflicts in a fair and legally sound manner.
FAQs: (approximately 129 words)
1. Q: Are all instances of dubious ownership claims intentional?
A: No, some instances may arise due to oversight or genuine misunderstandings. However, intentional claims remain a significant concern.
2. Q: How can contributors protect their work against dubious ownership claims?
A: Regularly document contributions, utilize version control systems, and adhere to licensing requirements to establish a robust trail of proof.
3. Q: Can automated tools effectively detect dubious ownership claims?
A: While automated tools can flag potential issues, human intervention is often required to assess context and make accurate determinations.
4. Q: What legal actions can be pursued against false ownership claims?
A: Legal actions may include cease and desist notices, claims for copyright infringement, or breach of licensing agreements.
Conclusion (approximately 100 words):
Detected dubious ownership claims in repositories pose a significant challenge within the open-source community, hindering collaboration, diluting credit, and risking legal ramifications. Addressing this issue requires a multi-faceted approach, combining robust verification processes, enhanced collaboration tools, education, and legal support. By adopting proactive measures and fostering a culture of trust and transparency, repository owners and communities can safeguard their projects, protect contributors, and promote the integrity of open-source development as a whole.
Error: Cannot Open .Git/Fetch_Head: Permission Denied
If you have ever encountered the error “cannot open .git/fetch_head: permission denied” while using Git, you might have found it frustrating and confusing. This article will delve into the issue and provide you with a comprehensive understanding of what it means and how to resolve it. So, let’s get started!
What does the error “cannot open .git/fetch_head: permission denied” mean?
The error “cannot open .git/fetch_head: permission denied” typically occurs when Git is unable to access the fetch_head file within the .git directory due to a lack of permissions. The fetch_head file contains information about the remote branches and their latest commits. Without access to this file, Git cannot perform fetch operations correctly.
What causes the “cannot open .git/fetch_head: permission denied” error?
There are a few common causes that can trigger this error message to appear:
1. Insufficient permissions: The user or process running Git does not have sufficient permissions to access the fetch_head file.
2. Ownership issues: The fetch_head file is owned by a different user or group that does not have the necessary permissions for the user running Git.
3. Incorrect file permissions: The fetch_head file has incorrect permissions set, preventing the user from accessing it.
How to fix the “cannot open .git/fetch_head: permission denied” error?
Now that we understand the probable causes behind this error, let’s explore some solutions to fix it:
1. Check the user permissions: Ensure that you have the necessary permissions to access the fetch_head file. You can try running Git commands with administrative or superuser privileges using the “sudo” command on Unix-based systems.
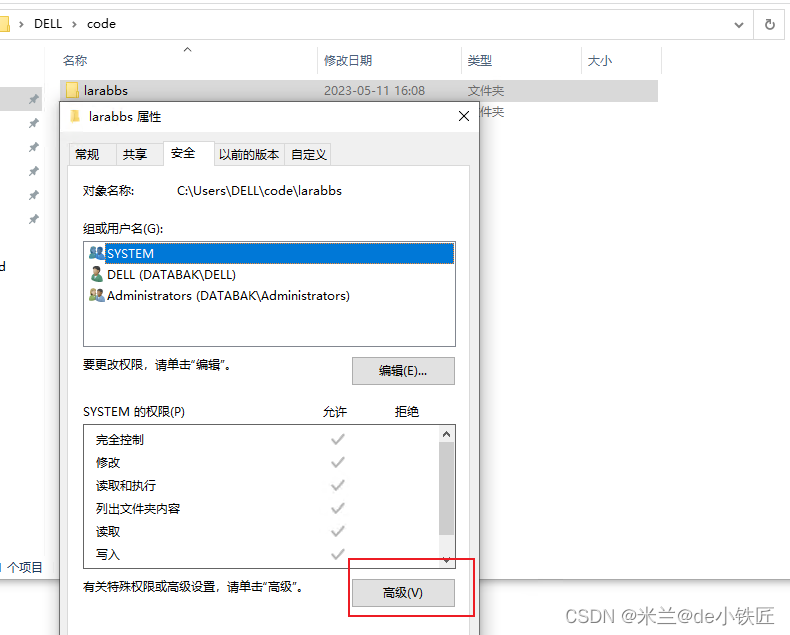
2. Change file ownership: If ownership issues are causing the error, you can change the ownership of the fetch_head file using the “chown” command. For example, if you are the user “username” on a Linux system, you can run the command “sudo chown username:username .git/fetch_head” to change the ownership to your user.
3. Adjust file permissions: Verify that the fetch_head file has the correct permissions set. You can try granting read and write permissions to the file using the “chmod” command: “sudo chmod +rw .git/fetch_head”. Be cautious with modifying permissions, as it can affect the security of your repository.
4. Enable group permissions: In some cases, granting group permissions to the fetch_head file can resolve the issue. You can use the “chmod” command to add group permissions with the command “sudo chmod g+rw .git/fetch_head”.
5. Re-clone the repository: If all else fails, you can try re-clone the repository from the remote source. This ensures a fresh copy with the correct permissions and ownership.
FAQs:
Q: Is it safe to modify file permissions in the .git directory?
A: Modifying file permissions within the .git directory should be done with caution. Incorrect permissions can compromise the integrity and security of your repository. It is recommended to make changes only if necessary and to revert them once the issue is resolved.
Q: Why am I suddenly encountering this error when I was using Git successfully before?
A: It is possible that an update or modification in the repository, file system, or user permissions caused the error to occur. Review any recent changes that may have affected the permissions of the fetch_head file.
Q: Can I use Git without administrative privileges?
A: Yes, you can use Git without administrative privileges. However, certain operations or file modifications might require elevated privileges. Running Git with administrative privileges can help mitigate permission-related errors.
Q: What if I encounter this error on a shared Git repository?
A: If you encounter this error on a shared repository, consult with the repository’s administrator or your team to ensure proper permissions and ownership are maintained.
Q: Are there any other potential solutions for this error?
A: In some cases, antivirus or security software may interfere with file permissions. Temporarily disabling such software can help identify if it is causing the issue. Additionally, checking your system’s disk for errors using tools like chkdsk on Windows or fsck on Unix-based systems might help resolve the problem.
In conclusion, the “cannot open .git/fetch_head: permission denied” error is a common issue encountered by Git users. By understanding the causes and applying the appropriate solutions, you can quickly overcome this error and continue utilizing Git smoothly. Remember to exercise caution when modifying file permissions and to seek assistance from system administrators or colleagues if working on a shared repository. Happy coding!
Permission Denied (Publickey Fatal Could Not Read From Remote Repository)
Have you encountered the frustrating error message “Permission denied (publickey) fatal: Could not read from remote repository” while trying to access a remote repository? This error is quite common when working with Git or other version control systems. It can prevent you from pushing, pulling, or cloning repositories. In this article, we will dive deep into this error, exploring its causes and providing solutions to help you overcome it.
Understanding the Error:
When you interact with a remote repository, you need to authenticate yourself to prove that you have the necessary permissions to access it. This authentication is usually done using SSH keys. The “Permission denied (publickey)” error occurs when your local machine fails to authenticate with the remote repository because it does not have the correct SSH key or the key is not properly configured.
Causes of the Error:
1. Missing or Incorrect SSH Key: One of the most common causes of this error is that your local machine does not have a valid SSH key, or the SSH key is not associated with your user account on the remote repository. Ensure that you have generated the correct SSH key pair and that the public key is uploaded to your remote repository account.
2. Improper SSH Key Permissions: Another reason for this error could be incorrect permissions on your SSH key files. For security reasons, SSH requires specific file permissions on the private and public key files. The private key file should have permissions set to 600 (-rw——-), while the public key file should have permissions set to 644 (-rw-r–r–).
3. Incorrect SSH Configuration: It is possible that your SSH configuration on your local machine is not set correctly. This could include incorrect settings for the SSH agent, incorrect configuration file location, or improper SSH port configurations.
4. Firewall or Network Restrictions: In some cases, your connection to the remote repository could be blocked by a firewall or restricted network settings. Ensure that your network environment allows SSH connections to the remote repository.
Solutions:
Now that we have identified the potential causes of the “Permission denied (publickey)” error, let’s explore some solutions to rectify the issue:
1. Verify SSH Key Setup: Begin by verifying that you have set up your SSH key correctly. Check if you have generated and uploaded the correct public key to your remote repository. Consult the documentation of your version control system for specific instructions on generating and managing SSH keys for authentication.
2. Check SSH Key Permissions: Ensure that the permissions on your private and public key files are set correctly. Use the chmod command to set the permissions accordingly. For example, run “chmod 600 ~/.ssh/id_rsa” for the private key and “chmod 644 ~/.ssh/id_rsa.pub” for the public key, assuming the default key filenames.
3. Configure SSH Agent: If you still face issues, you can configure the SSH agent to manage your SSH keys. The agent can help manage and authenticate keys automatically, eliminating the need for manual setup. There are different methods to configure the SSH agent depending on your operating system. Consult the documentation for your operating system for details on how to set up the SSH agent.
4. Review SSH Configuration: Double-check your SSH configuration file to ensure it is correctly set up. The configuration file is usually located at “~/.ssh/config” for Unix-like systems. Pay attention to settings like the SSH port, identity file location, and SSH agent configurations. Make any necessary changes and save the configuration file.
5. Test Network Connectivity: Confirm that your network environment allows SSH connections to the remote repository. Try accessing other remote repositories or services using SSH to determine if the issue is specific to the repository or connection. If necessary, contact your network administrator or service provider for assistance.
FAQs:
Q: Why am I receiving the “Permission denied (publickey)” error when I have the correct SSH key?
A: This could occur if the SSH key is not properly associated with your user account on the remote repository. Ensure that you have correctly associated the SSH key’s public key with your repository account.
Q: What should I do if I don’t have an SSH key?
A: You can generate a new SSH key pair using the “ssh-keygen” command. Consult the documentation of your version control system for specific instructions.
Q: Can I use multiple SSH keys for different repositories?
A: Absolutely! You can generate and use multiple SSH keys for different repositories or services. To use different keys, you need to configure your SSH client to select the appropriate key based on the repository’s URL.
Q: Why am I still getting the error after trying all the solutions?
A: It is possible that there is an issue with the remote repository, such as a configuration problem or temporary server downtime. Contact the repository administrator or support for further assistance.
In Conclusion:
The “Permission denied (publickey) fatal: Could not read from remote repository” error can be frustrating when working with remote repositories. By understanding the possible causes and following the suggested solutions in this article, you can overcome this error and regain access to your repositories. Remember to double-check your SSH key setup, review SSH configuration, and verify network connectivity to resolve this issue efficiently.
Images related to the topic fatal: detected dubious ownership in repository

Found 19 images related to fatal: detected dubious ownership in repository theme






![오류] fatal: detected dubious ownership in repository at '경로' 오류] Fatal: Detected Dubious Ownership In Repository At '경로'](https://velog.velcdn.com/images/ovzip/post/9eca95d1-80cd-454e-8fda-3118f6299f07/image.png)


![Bug]: stderr: fatal: detected dubious ownership in repository · Issue #9924 · AUTOMATIC1111/stable-diffusion-webui · GitHub Bug]: Stderr: Fatal: Detected Dubious Ownership In Repository · Issue #9924 · Automatic1111/Stable-Diffusion-Webui · Github](https://user-images.githubusercontent.com/124453184/235263292-87ba4801-ab33-421c-bc5f-6bc6ed5f51a8.png)
















![git] fatal: detected dubious ownership in repository at Git] Fatal: Detected Dubious Ownership In Repository At](https://img1.daumcdn.net/thumb/C176x176/?fname=https://blog.kakaocdn.net/dn/drAAGs/btrQUADbJUk/2K9pCQXRQ7LLAKZkw7rKc0/img.png)




Article link: fatal: detected dubious ownership in repository.
Learn more about the topic fatal: detected dubious ownership in repository.
- git submodule update failed with ‘fatal: detected dubious …
- Git detect dubious ownership in repository | by Dennis – Medium
- Git “fatal: detected dubious ownership in repository”
- Little Git Tricks: Fix a Dubious Ownership of a Repository
- Detected dubious ownership in repository with Jenkins upgrade
See more: https://nhanvietluanvan.com/luat-hoc