Csrf Token From Post Incorrect.
1. Introduction to CSRF Token
In the vast digital landscape, security remains a paramount concern for organizations worldwide. As technology advances, so do the threats that exploit vulnerabilities in web applications. One such threat is Cross-Site Request Forgery (CSRF), which leverages the trust between a user’s browser and a website to perform malicious actions. To mitigate this risk, web developers employ CSRF tokens, which play a crucial role in preventing such attacks. However, CSRF tokens themselves can be subject to manipulation, leading to incorrect token handling and potential vulnerabilities.
2. Understanding the Importance of CSRF Tokens
CSRF tokens serve as an additional layer of security, aiming to protect users from unauthorized actions performed on their behalf. These tokens provide a unique and random value associated with a user’s session, ensuring that requests originating from their browser are indeed legitimate. By incorporating CSRF tokens into web applications, developers can validate whether an action is intentional and authorized, significantly reducing the risk of CSRF attacks.
3. The Role of Tokens in Preventing Cross-Site Request Forgery Attacks
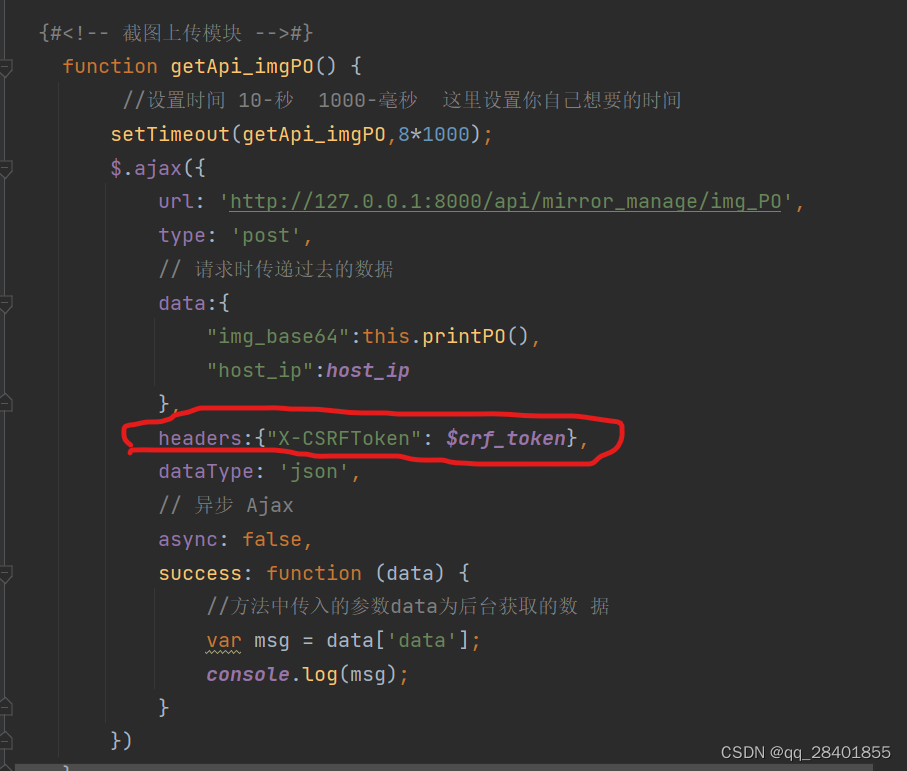
CSRF tokens act as a safeguard against unauthorized requests by validating the authenticity of the source. When a user initiates a request, the server includes a CSRF token in the response, which is saved either in a cookie or as a hidden form field. Subsequently, when the user submits a request, the client-side script adds the CSRF token to the payload. The server then verifies this token, comparing it against the stored value. If the token matches, the server considers the request legitimate and processes it accordingly. Otherwise, it denies the request, preventing potential CSRF attacks.
4. Common Mistakes and Causes of CSRF Token Post Incorrect
Despite the importance of CSRF tokens, several mistakes can occur during their implementation, leading to incorrect or missing tokens. Some prevalent causes are:
a) CSRF Token from Post Has Incorrect Length: This error occurs when the length of the CSRF token received does not match the expected length, indicating a potential manipulation during transmission.
b) CSRF Token Missing or Incorrect: In this scenario, the CSRF token is either absent from the request or provided incorrectly. Such issues can result from inconsistencies in storing or retrieving the CSRF token value.
c) CSRF Token Missing or Incorrect Django Postman: CSRF token issues within Django Postman can stem from improper configurations or incorrect usage of the CSRF middleware.
d) Invalid CSRF Token Found: This error typically occurs when the server detects a mismatch between the CSRF token received and the expected value. Possible causes include token tampering attempts or misconfigured server-side logic.
e) CSRF Token Missing Django: If a CSRF token is missing in Django, it can lead to unauthorized requests or potential security breaches. This issue may arise due to CSRF protection being disabled or custom configurations.
f) 403 CSRF Token Invalid: When a CSRF token is deemed invalid, the server responds with a 403 Forbidden status. This indicates that the request cannot proceed, as the provided token does not match the expected value.
g) Python CSRF Token: Python web frameworks like Django often employ built-in functionalities to handle CSRF tokens. However, incorrect handling or usage of these features can introduce vulnerabilities and weaken the overall security of the application.
5. Impact of CSRF Token Post Incorrect
When CSRF tokens are incorrect or missing, the consequences can be severe. Malicious actors can exploit these vulnerabilities and execute unauthorized actions on behalf of users. For instance, they may manipulate the client-side script to initiate transactions, change user data, or perform actions that compromise privacy and security. Without properly functioning CSRF tokens, users become vulnerable to attacks, leading to potential financial losses, reputational damage, and compromised data integrity.
6. Best Practices for Implementing and Handling CSRF Tokens
To ensure the effectiveness of CSRF tokens and prevent post incorrect scenarios, web developers should follow these best practices:
a) Enable CSRF protection: Enable and configure CSRF protection in frameworks and platforms used in web development. This ensures that all requests are validated against a CSRF token.
b) Use strong and unpredictable tokens: Generate unique and random CSRF tokens for each user session. Employ cryptographic techniques to ensure token unpredictability.
c) Set proper token length: Ensure that the token length matches the expected length both during generation and verification. Mismatched token lengths can lead to potential exploits.
d) Store tokens securely: Tokens should be stored in secure session cookies or hidden form fields. Protect these storage mechanisms from unauthorized access and tampering.
e) Regularly refresh tokens: Periodically refresh CSRF tokens to reduce the window of opportunity for potential attacks.
f) Educate users: Clearly communicate the importance of CSRF tokens to users, emphasizing the significance of not sharing or revealing their tokens to maintain security.
g) Employ additional security measures: Complement CSRF tokens with other security mechanisms, such as CAPTCHA, multi-factor authentication, and thorough input validation, to further enhance protection against various attacks.
7. Tools and Techniques for Verifying CSRF Token Correctness
To verify CSRF token correctness and detect potential vulnerabilities, developers can employ various tools and techniques, including:
a) Manual code review: Conduct a thorough review of the codebase, focusing on CSRF token generation, storage, and verification procedures.
b) Automated security scanners: Utilize specialized security testing tools that can identify CSRF token-related issues, such as incorrect length, missing tokens, or misconfigured CSRF protection.
c) Static code analyzers: Implement static analysis tools capable of detecting CSRF token mishandling or potential weaknesses that can be exploited.
d) Penetration testing: Conduct periodic penetration testing to simulate real-world attack scenarios and identify any CSRF token-related vulnerabilities.
8. Continual Monitoring and Updating to Ensure CSRF Token Effectiveness
Web applications and security threats evolve over time, necessitating consistent monitoring and updating of CSRF token implementation. Regular vulnerability assessments, keeping frameworks and platforms up to date, and staying informed about emerging security practices and recommendations help maintain the effectiveness of CSRF tokens.
FAQs:
Q1. What happens if a CSRF token is missing?
If a CSRF token is missing, the server will not be able to validate the authenticity of a request. As a result, the server will likely deny the request, preventing potential CSRF attacks.
Q2. How can I troubleshoot an invalid CSRF token error?
To troubleshoot an invalid CSRF token error, ensure that the token is generated and stored correctly, and that the received token matches the expected value during verification. Review the code for any inconsistencies or misconfigurations that may impact token handling.
Q3. Should I manually refresh CSRF tokens?
Regularly refreshing CSRF tokens adds an additional layer of security and reduces the time window for potential attacks. It is recommended to automatically refresh tokens after a specific duration or whenever certain events, such as login or session expiration, occur.
Q4. Can CSRF tokens be reused across different sessions?
No, CSRF tokens should always be unique to each user session. Reusing tokens would undermine their effectiveness in preventing CSRF attacks, as the tokens need to be unpredictable and associated with a specific session.
Q5. Can CSRF tokens offer complete protection against all web application attacks?
While CSRF tokens significantly mitigate the risk of CSRF attacks, they do not provide complete protection against all web application attacks. It is crucial to implement a comprehensive security strategy, including input validation, secure coding practices, and other security measures, to ensure overall application security.
In conclusion, CSRF tokens play a crucial role in safeguarding web applications against Cross-Site Request Forgery attacks. However, ensuring their correctness and effectiveness requires proper implementation, handling, and continual monitoring. By following best practices, employing the right tools, and prioritizing security throughout the development lifecycle, developers can enhance the protection of user data and maintain the integrity of web applications.
How To Resolve Csrf Token Missing Or Incorrect In Django Form Submission, Csrf Verification Failed,
Keywords searched by users: csrf token from post incorrect. csrf token from post has incorrect length, csrf token missing or incorrect, csrf token missing or incorrect django postman, invalid csrf token, invalid csrf token found, csrf token missing django, 403 csrf token invalid, python csrf token
Categories: Top 46 Csrf Token From Post Incorrect.
See more here: nhanvietluanvan.com
Csrf Token From Post Has Incorrect Length
In the dynamic realm of web development, web applications rely on various security measures to protect user data and prevent unauthorized access. One such security measure is Cross-Site Request Forgery (CSRF) token. However, an issue can arise when a POST request’s incorrect length compromises the effectiveness of this token. In this article, we will explore the intricacies of CSRF tokens, the impact of an incorrect length, and ways to mitigate the associated risks.
Understanding CSRF Tokens
Before delving deeper into the problem at hand, let’s first understand what CSRF tokens are and why they are crucial. A CSRF token is a unique randomly generated value, usually stored either in a cookie or as a hidden field in a form. When a user initiates a POST request, this token is included to verify the request’s authenticity.
By incorporating CSRF tokens, web applications can ensure that only requests originating from their own pages are accepted, effectively preventing attackers from manipulating user actions and performing unauthorized actions on their behalf. This security measure adds an additional layer of protection against CSRF attacks, making it significantly harder for malicious entities to exploit vulnerabilities.
The Issue of Incorrect Length
While CSRF tokens are invaluable for security, they are not impervious to potential vulnerabilities. One such vulnerability is the issue of an incorrect length of a POST request’s CSRF token. As tokens are randomly generated, their lengths must be consistent across various parts of a web application.
When a CSRF token’s length is inconsistent, it can severely impact the effectiveness of the protection it provides. Attackers can exploit this discrepancy by crafting malicious requests with a token of incorrect length, bypassing the verification process, and successfully executing unauthorized actions. Such actions might include transferring funds, changing account details, or even injecting harmful code.
The consequences of an incorrect length CSRF token are dire as they undermine the very purpose of CSRF protection. It renders web applications vulnerable to attacks that can compromise user data, cause financial losses, and damage the reputation of both users and developers.
Mitigating the Risk
Fortunately, developers can take several measures to mitigate the risks associated with CSRF tokens having incorrect lengths:
1. Consistency: Ensure that all parts of the web application generating and validating CSRF tokens use the same algorithm for random token generation. This includes the server-side code for issuing tokens and the client-side code responsible for embedding them in forms or cookies.
2. Validation: Implement strict validation mechanisms to compare the length of the token in the POST request with the expected length. If a discrepancy is detected, the request should be rejected. Additionally, regular audits and security testing should be conducted to identify any inconsistencies in token length.
3. Token Regeneration: Consider regenerating CSRF tokens periodically or on specific events, such as user logout/login or session expiration. This minimizes the window of opportunity for attackers to exploit any issued tokens with incorrect lengths.
4. Cryptographically Secure Token Generation: Utilize a secure random number generator to generate CSRF tokens instead of relying on predictable or weak pseudo-random algorithms. This ensures the uniqueness and randomness of the tokens, making it more difficult for attackers to guess or forge them.
FAQs about CSRF Tokens with Incorrect Lengths:
Q1. How does an attacker exploit an incorrect length CSRF token?
A1. Attackers can craft malicious requests with a token of incorrect length, bypassing the verification process, and executing unauthorized actions.
Q2. Can an incorrect length CSRF token be detected?
A2. Yes, by implementing strict validation mechanisms, developers can detect if a CSRF token’s length in a POST request is inconsistent with the expected length.
Q3. How often should CSRF tokens be regenerated?
A3. Regenerating CSRF tokens periodically or on specific events, such as user logout/login or session expiration, limits the window of opportunity for attackers.
Q4. Are there tools available for testing CSRF token vulnerabilities?
A4. Yes, various web vulnerability scanners, such as OWASP ZAP or Burp Suite, can help identify potential vulnerabilities in CSRF token handling.
In conclusion, CSRF tokens serve as critical safeguards against unauthorized actions and protect user data within web applications. However, an incorrect length of a POST request’s CSRF token can undermine the security they provide. By maintaining consistency, validating tokens, regenerating them periodically, and utilizing secure token generation, developers can mitigate the risks associated with this issue and ensure enhanced security for their users.
Csrf Token Missing Or Incorrect
Introduction:
In today’s digital world, web applications are an integral part of our daily lives. However, these applications can also be vulnerable to various cyber threats. One such vulnerability is the Cross-Site Request Forgery (CSRF) attack. CSRF attacks can cause significant damage to both individuals and organizations. In this article, we will discuss CSRF token missing or incorrect, understand its implications, and explore ways to mitigate this security risk.
Understanding CSRF:
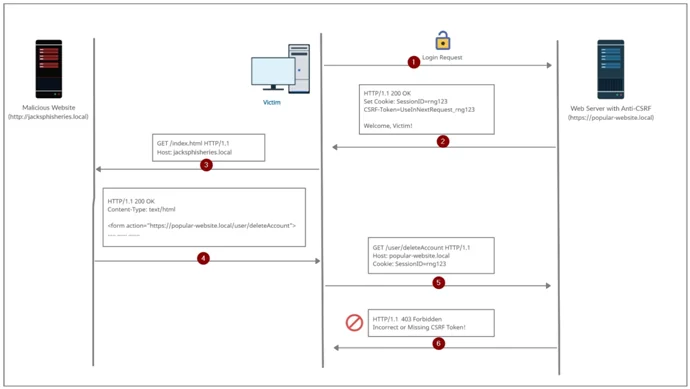
Before delving into CSRF token missing or incorrect, it is essential to understand what CSRF is. CSRF is a type of attack where an attacker tricks a victim into performing unwanted actions on a web application in which the victim is authenticated. This attack leverages the trust a website has for a user’s browser and can result in unauthorized actions, such as changing a user’s password or making financial transactions without their consent. It is crucial to note that CSRF attacks do not exploit vulnerabilities within the website’s code but rather abuse the trust between the user and the website.
The Role of CSRF Tokens:
To protect against CSRF attacks, developers commonly utilize a security measure known as CSRF tokens. A CSRF token is a random string of characters generated by a web application and associated with a user’s session. This token is then embedded within web forms or added as an additional parameter to AJAX requests. In subsequent requests, the server validates the token, ensuring that it matches the one associated with the user’s session. If the token is missing or incorrect, the server can reject the request as a potential CSRF attack.
CSRF Tokens Missing or Incorrect:
When a CSRF token is missing or incorrect, it means that the web application fails to include the necessary token in a user’s request, or the token provided does not match the one associated with the user’s session. Both scenarios can leave the application vulnerable to CSRF attacks. If a web application does not properly validate CSRF tokens, an attacker can craft malicious requests that the server will mistakenly consider as legitimate.
Implications of CSRF Token Missing or Incorrect:
The implications of CSRF token missing or incorrect can be severe. These attacks enable unauthorized actions that can compromise user accounts, steal sensitive information, or lead to financial losses. For instance, an attacker may trick a victim into clicking a malicious link that automatically transfers funds from their account to the attacker’s account. Without a valid CSRF token, the server fails to detect the attack, resulting in unauthorized actions being performed on behalf of the victim.
Mitigating CSRF Attacks:
To effectively mitigate CSRF attacks, developers and website administrators must follow best practices in implementing CSRF token protection. Here are some strategies to consider:
1. Implement CSRF Protection Mechanisms: All web forms and AJAX requests should include CSRF tokens. Developers should utilize frameworks or libraries that provide built-in protection against CSRF attacks, such as Django for Python or Laravel for PHP.
2. Generate Strong and Random CSRF Tokens: Use a secure random number generator to generate unpredictable CSRF tokens, ensuring that each user session has a unique token associated with it. This prevents attackers from guessing or brute-forcing tokens.
3. Store CSRF Tokens in Secure Locations: CSRF tokens should be stored in secure locations, such as session cookies or HTTP-only cookies, rather than in client-side storage (e.g., local storage or URL parameters). This makes it more challenging for attackers to access or manipulate the tokens.
4. Validate CSRF Tokens: When processing requests, ensure that the submitted CSRF token matches the one associated with the user’s session. If the token is missing or incorrect, reject the request as a potential CSRF attack.
5. Implement Same-Site Cookies: Configure cookies to have the ‘SameSite’ attribute set to ‘Strict’ or ‘Lax’. This prevents the browser from automatically including cookies for requests originating from different websites, further reducing the risk of CSRF attacks.
FAQs:
Q1. What other security measures can complement CSRF token protection?
A1. Alongside CSRF token protection, implementing robust authentication and session management practices, such as session expiration and secure password storage, can bolster overall security.
Q2. Are there any tools available to detect and prevent CSRF vulnerabilities?
A2. Yes, several web vulnerability scanners and security testing tools, such as OWASP ZAP or Burp Suite, can help identify potential CSRF vulnerabilities and guide developers in securing their applications.
Q3. Can CSRF attacks be prevented entirely?
A3. While it is challenging to completely eliminate all possible attack vectors, implementing proper CSRF protection mechanisms significantly reduces the risk of successful CSRF attacks.
Q4. How often should CSRF tokens be refreshed?
A4. It is recommended to refresh CSRF tokens after each successful request or periodically within a user session to limit the window of opportunity for potential attackers.
Conclusion:
Protecting web applications from CSRF attacks is of utmost importance in ensuring the security and integrity of user data. Understanding the role of CSRF tokens, the implications of CSRF token missing or incorrect, and implementing appropriate protective measures can significantly mitigate the risk of CSRF attacks. By following industry best practices, developers and website administrators can enhance security and provide users with a safer online experience.
Images related to the topic csrf token from post incorrect.

Found 20 images related to csrf token from post incorrect. theme

















![postman] Postman]](https://blog.kakaocdn.net/dn/bH8i2n/btq12l2pFNN/I9SzOD71LPO08G3HOHrPJ1/img.png)


![django] 403 forbidden Error 해결하기(CSRF token) Django] 403 Forbidden Error 해결하기(Csrf Token)](https://blog.kakaocdn.net/dn/FmZyP/btqP9r7wfsT/mNYKTROFQkOHCeaA53JGYk/img.png)






Article link: csrf token from post incorrect..
Learn more about the topic csrf token from post incorrect..
- CSRF token missing or incorrect . How to resolve this error?
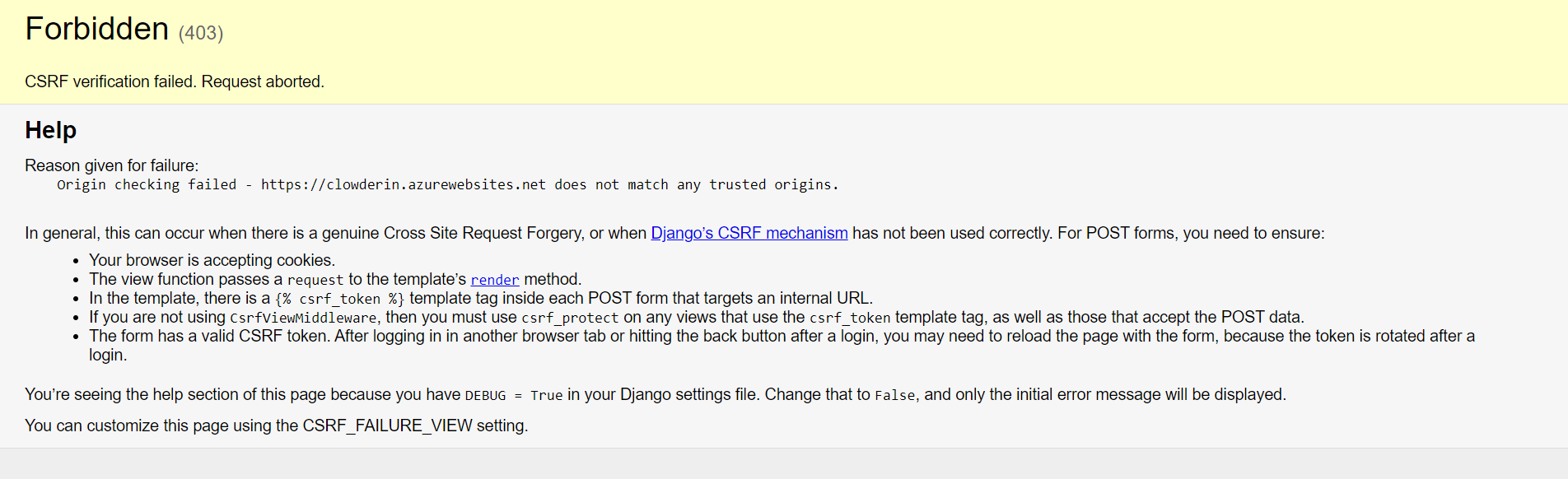
- Forbidden (CSRF token from POST incorrect.): /accounts/login
- How to Fix Instagram Login Error – CSRF Token Missing or Incorrect
- Error “Forbidden CSRF verification failed” occurs when trying to create …
- Assets Server REST API – Performing a POST request with a csrf token
- How To Fix Missing CSRF Token Error In Safari – Maisie AI
- How to fix the “CSRF token mismatch error” message
- CSRF token error messages – Todoist
- “CSRF token missing or incorrect” when trying to upload …
- Instagram CSRF Token Missing Or Incorrect – Reasons & How …