Blocked A Frame With Origin From Accessing A Cross-Origin Frame
Cross-origin frames, also known as iframes, are a fundamental component of modern web development. They allow websites to embed content from different origins, such as external websites or resources, into their own webpages. This functionality enables developers to enrich their websites with interactive content, like maps, videos, or social media plugins, without having to build everything from scratch.
How Cross-Origin Frames Communicate
Cross-origin frames communicate with each other using the postMessage() method, which allows scripts running in different frames to exchange messages securely. This method requires both the sending and the receiving frames to explicitly trust each other by specifying the target origin. The target origin is a combination of the protocol, domain, and port of the frame that should receive the message. This mechanism ensures that sensitive information is not shared with unauthorized frames or domains.
Restrictions and Security Measures for Cross-Origin Frames
Due to security concerns, cross-origin frames are subject to several restrictions and security measures. These measures are enforced by the Same-Origin Policy, which governs how web browsers handle interactions between different origins. The Same-Origin Policy restricts cross-origin access to crucial resources like cookies, local storage, and sensitive DOM elements.
Blocked Access: Cross-Origin Frame and Same-Origin Policy
The Same-Origin Policy plays a vital role in protecting user data and preventing malicious attacks. One key implication of the Same-Origin Policy is that a frame with a specific origin is blocked from accessing a cross-origin frame. This restriction is in place to prevent possible security vulnerabilities that could arise from unauthorized frame access.
Reasons Why a Frame with Origin is Blocked from Accessing a Cross-Origin Frame
There are several reasons why a frame with a specific origin is blocked from accessing a cross-origin frame. One common reason is the lack of proper validation and authorization. If the cross-origin frame does not explicitly allow access from the originating frame, the browser will block the request for security reasons.
Another reason for blocked access can be the presence of the “X-Frame-Options” header. This header allows website owners to specify whether or not their content can be embedded in a frame from a different origin. If the header is set to deny or sameorigin, the browser will prevent any cross-origin framing.
Preventing Cross-Origin Frame Access Blocking
To prevent the blocking of cross-origin frame access, developers must ensure that the cross-origin frame validates and authorizes the requesting frame. This can be achieved by implementing server-side validation or using client-side techniques like the postMessage() method.
Additionally, website owners can utilize the “X-Frame-Options” header to specify the framing policy for their content. The header should be configured according to the desired level of security, allowing access only to trusted frames.
Implementing Cross-Origin Resource Sharing (CORS) is another approach to enable cross-origin frame access. CORS allows servers to specify which origins are allowed to access their resources, providing a fine-grained control mechanism for cross-origin communication.
Security Risks and Threats
Cross-origin frame access poses potential security risks that developers must be aware of. One major risk is the possibility of data leakage and exposure of confidential information. If a frame with malicious intent gains access to a cross-origin frame, it can potentially extract sensitive data or manipulate the content of the embedded frame.
Attackers can exploit vulnerabilities in cross-origin frames to launch various types of attacks, including clickjacking, where the attacker tricks the user into clicking on hidden or invisible elements, and cross-site scripting (XSS), where the attacker injects malicious scripts into the cross-origin frame.
Addressing Frame Access Restrictions
When faced with a frame access restriction, developers should first ensure that their coding practices follow security guidelines and best practices. They should validate and authorize cross-origin frame access to prevent any unauthorized requests.
If a frame is blocked from accessing a cross-origin frame, developers should investigate the cause of the issue and troubleshoot common problems. This can involve checking the existence and correctness of the “X-Frame-Options” header or verifying the implementation of proper validation and authorization mechanisms.
In some cases, frame access restrictions can be due to browser settings. Developers can configure the browser settings to allow cross-origin frame access if they deem it necessary for their application.
Best Practices for Cross-Origin Frame Access
To ensure the security of cross-origin frame access, developers should adhere to the following best practices:
1. Follow security guidelines and best practices: Stay up-to-date with the latest security standards and recommendations to minimize the risk of vulnerabilities.
2. Minimize cross-origin frame access to trusted sources: Only allow access to frames from trusted origins to minimize the risk of exposing confidential information to unauthorized entities.
3. Regularly update and patch browser vulnerabilities: Keep browsers and frameworks up-to-date to benefit from the latest security patches and bug fixes.
Future Developments and Alternatives
In the ever-evolving landscape of web development, cross-origin frame restrictions are continuously being addressed and enhanced in web standards. New mechanisms for cross-origin communication, such as the Cross-Origin Opener Policy (COOP) and Cross-Origin Embedder Policy (COEP), aim to improve security and provide granular control over frame access.
Alternatives to cross-origin frames are also emerging, offering enhanced security without compromising functionality. Some alternatives include Web Components, which encapsulate HTML, CSS, and JavaScript into reusable custom elements, and Cross-Origin Isolated Pages, which provide a higher level of isolation and security for web applications.
As web standards evolve, it is essential for developers to stay informed about these developments and adopt the most secure and efficient approaches for cross-origin communication. By implementing proper security measures and following best practices, developers can mitigate the risks associated with cross-origin frame access and ensure the safety of their web applications.
FAQs
1. What does “blocked a frame with origin” mean?
When a frame with a specific origin (the website it belongs to) is blocked from accessing a cross-origin frame (a frame from a different website), it means that the web browser has restricted the interaction between the two frames due to security concerns.
2. Why am I getting the error “Uncaught DOMException Blocked a frame with origin”?
The “Uncaught DOMException Blocked a frame with origin” error occurs when an attempt is made to access or interact with a frame from a different origin, which is not permitted by the Same-Origin Policy. This error is a security measure to protect against potential vulnerabilities and attacks.
3. What is the “X-Frame-Options” header?
The “X-Frame-Options” header is a security mechanism that allows website owners to specify the framing policy for their content. By configuring this header, website owners can control whether their content can be embedded in a frame from a different origin or restrict framing altogether.
4. How can I fix the “Blocked autofocusing on a form control in a cross-origin subframe” issue?
The “Blocked autofocusing on a form control in a cross-origin subframe” issue occurs when a frame from a different origin attempts to automatically focus on a form control. To fix this issue, you can modify your code to avoid automatic focusing or ensure that the cross-origin frame allows autofocusing by enabling appropriate permissions.
5. How can I make an iframe height fit its content from a cross-domain origin?
Making an iframe’s height fit its content from a cross-domain origin can be challenging due to security restrictions. One approach is to use the postMessage() method to communicate the desired height from the cross-origin frame to the parent frame and then adjust the iframe’s height based on the received message.
Javascript : Securityerror: Blocked A Frame With Origin From Accessing A Cross-Origin Frame
What Blocked A Frame With Origin Domain From Accessing A Cross-Origin Frame?
A web page often consists of numerous frames, allowing for the display of multiple documents within a single browser window. These frames can be sourced from different domains, resulting in a scenario referred to as cross-origin or cross-domain frames. However, due to security concerns, web browsers implement the same-origin policy, which restricts the interaction between frames from different domains. This article aims to explore the reasons behind the blockage of a frame with an origin domain from accessing a cross-origin frame, shedding light on the security measures implemented by browsers to safeguard users’ data and privacy.
The Same-Origin Policy:
The same-origin policy is a crucial security feature widely supported by web browsers to prevent malicious activities on the web. It aims to ensure that web content from one origin (domain, protocol, and port) cannot access or tamper with content from a different origin, unless explicitly permitted. The same-origin policy prevents the following scenarios:
1. Access to DOM: JavaScript code running within a frame can only access the Document Object Model (DOM) of pages originating from the same domain as itself. This restriction prevents codes running in a frame from reading or modifying content belonging to a different origin.
2. AJAX Requests: AJAX, or Asynchronous JavaScript and XML, refers to a technique that allows web pages to update content dynamically without requiring a full page reload. The same-origin policy mandates that AJAX requests can only be made to the same origin as the frame initiating the request. This limitation prevents scripts from fetching sensitive data from a different domain.
3. Cookies and Local Storage: Cookies and the Local Storage API are crucial components for maintaining user sessions and storing client-side data. The same-origin policy ensures that cookies and local storage are isolated to the origin that created them, preventing cross-origin access. This restriction aids in protecting sensitive information stored in cookies, such as authentication tokens or session IDs.
Reasons Behind Blockage:
When a frame from an origin domain attempts to access a cross-origin frame, it often encounters blockages from the browser. Several factors contribute to the blockage, including:
1. Security Concerns: The primary reason behind blocking cross-origin frame access is to mitigate potential security risks. Allowing unrestricted access between frames from different origins would create opportunities for malicious activities, such as cross-site scripting (XSS) attacks or data theft. Web browsers prioritize protecting users’ data and privacy, which is achieved by enforcing the same-origin policy.
2. Different Security Contexts: Each origin often has its own distinct security context. Allowing a frame to access another frame from a different origin would introduce a blending of security contexts. This could lead to vulnerabilities and expose users to unintended threats. By isolating the frames, the browser maintains a clear distinction between their respective security contexts, minimizing potential risks.
FAQs
Q: Can the same-origin policy be disabled?
A: No, the same-origin policy is a core security feature implemented by web browsers and cannot be disabled. However, there are mechanisms available, such as Cross-Origin Resource Sharing (CORS), which allow controlled data exchange between specific domains.
Q: Are there any exceptions to the same-origin policy?
A: Yes, there are some exceptions to the same-origin policy. For example, the policy does not prevent embedding cross-origin images or stylesheets, as these resources do not have access to the DOM. Additionally, certain HTTP headers, like Access-Control-Allow-Origin, can be utilized to explicitly allow cross-origin access.
Q: Can the same-origin policy cause any compatibility issues?
A: The same-origin policy rarely causes compatibility issues. However, in some specific scenarios, such as when integrating third-party widgets or content, cross-origin restrictions may require additional configurations. In these cases, developers can utilize mechanisms like JSONP (JSON with Padding) or emerging approaches like Cross-Origin Embedder Policy (COEP) and Cross-Origin Opener Policy (COOP).
Q: Are there any alternatives to cross-origin access for integration purposes?
A: Yes, for scenarios where cross-origin access is required for integration, multiple techniques can be employed. These include using server-side proxies, implementing APIs that facilitate secure data exchange, or utilizing modern web standards like Web Components, which allow encapsulation and reuse of web elements across different domains.
In conclusion, the same-origin policy serves as a foundational security measure within web browsers to prevent unauthorized access and protect users’ data. By blocking a frame with an origin domain from accessing a cross-origin frame, browsers enforce boundaries that help maintain users’ security and privacy. While limiting access may sometimes require additional approaches or configurations, the same-origin policy is a crucial aspect of web security that maintains the integrity of the web ecosystem.
What Is A Cross-Origin Frame?
In the world of web development and security, the term “cross-origin frame” refers to a frame or an iframe that is embedded within a webpage from a different origin. An origin is defined by the combination of the protocol (HTTP, HTTPS), domain (example.com), and port (optional) of a webpage’s URL.
When a website contains embedded frames from different origins, it gives rise to cross-origin communication between the frames. This communication can be between two different websites, or it may involve a parent frame and its embedded frames. The concept of cross-origin frames plays a crucial role in enhancing web functionality and facilitating seamless integration of various web components. However, it also raises security concerns and requires special attention to prevent potential vulnerabilities.
Cross-Origin Frame Communication:
Cross-origin communication between frames is possible using JavaScript’s postMessage API. This API enables scripts running in different frames to securely exchange data and messages. With the postMessage API, one can trigger events, send structured data, or even request specific actions from the target frame. It acts as a messaging mechanism allowing communication between different origins.
To establish communication using postMessage, the sender frame calls the postMessage method, passing the target origin (the domain of the recipient frame) and the data to be sent. The recipient frame, on the other hand, listens for messages using the “message” event and performs the appropriate actions based on the received data.
Cross-Origin Frame Security:
While cross-origin frame communication can be beneficial, it also introduces security risks, primarily related to cross-site scripting (XSS) attacks. If a website fails to properly validate the origin of incoming messages, malicious actors can exploit these vulnerabilities to execute unauthorized actions or steal sensitive information. As a precaution, browsers have implemented the “Same-Origin Policy” (SOP), which restricts JavaScript code in a frame to access data or interact with frames from different origins.
To mitigate the security risks associated with cross-origin frames, there are several preventive measures and techniques that developers should implement:
1. Origin Validation: Before processing any incoming messages, always verify that the origin matches the expected value and discard any unexpected or suspicious messages.
2. Message Verification: Implement mechanisms to ensure the integrity and authenticity of received messages. This can involve techniques like digital signatures, where the sender can sign the message using a private key, and the recipient can verify the signature using the corresponding public key.
3. Content Security Policy (CSP): Implementing a Content Security Policy can further enhance security by restricting the sources of content that a webpage can load. It allows developers to define which origins are allowed to be embedded within frames, thereby reducing the risk of unauthorized frame communication.
Frequently Asked Questions (FAQs):
Q1: What are the benefits of using cross-origin frames?
A1: Cross-origin frames allow websites to incorporate external components seamlessly, enhancing functionality and improving user experience. It enables features like embedding maps, videos, or social media plugins, all while keeping the main website and the embedded components isolated from each other.
Q2: Can cross-origin frames communicate directly without using postMessage?
A2: No, direct communication between cross-origin frames is prohibited due to security concerns. The postMessage API provides a secure and controlled method of communication between frames.
Q3: How can I prevent my cross-origin frames from being misused?
A3: Implementing proper origin validation and message verification ensures that only trusted sources can communicate with your frames. Applying a Content Security Policy can also greatly reduce the risk of unauthorized frame communication.
Q4: Are there any security risks associated with cross-origin frames?
A4: Yes, cross-origin frames can introduce security risks, primarily related to cross-site scripting attacks. Without proper security measures, an attacker may impersonate a trusted origin, potentially leading to unauthorized actions or data theft.
Q5: Are there any browser limitations for cross-origin frames?
A5: Yes, browsers implement policies such as the Same-Origin Policy to restrict cross-origin frame communication. However, these restrictions can be overcome by implementing proper security measures and utilizing the postMessage API for secure communication.
In conclusion, cross-origin frames play a crucial role in web development, facilitating seamless integration of web components from different origins. While they provide numerous benefits, security precautions must be taken to mitigate the risks associated with unauthorized communication and cross-site scripting attacks. By implementing proper origin validation, message verification, and Content Security Policies, developers can ensure secure and reliable cross-origin frame communication.
Keywords searched by users: blocked a frame with origin from accessing a cross-origin frame blocked a frame with origin “http://localhost:3000” from accessing a cross-origin frame., Uncaught DOMException Blocked a frame with origin iframe, x-frame-options, Blocked autofocusing on a form control in a cross origin subframe, Iframe height fit content cross domain, Iframe contentWindow cross origin, Iframe CORS, Safari disable cors
Categories: Top 33 Blocked A Frame With Origin From Accessing A Cross-Origin Frame
See more here: nhanvietluanvan.com
Blocked A Frame With Origin “Http://Localhost:3000” From Accessing A Cross-Origin Frame.
Cross-origin frame access refers to the ability of a website or web application to load content from a different domain into an iframe. This feature is a fundamental aspect of web development, allowing developers to integrate content from multiple sources into a single web page. However, due to security concerns, browsers implement restrictions on cross-origin frame access to mitigate potential threats.
One common security feature implemented in modern browsers is the Same-Origin Policy (SOP). The SOP mandates that web pages served from different origins (domains, protocols, or ports) should not be able to access each other’s information or execute scripts unless they explicitly permit such interactions.
When a frame from one origin attempts to access a frame from a different origin, the browser blocks this operation. This is commonly known as a blocked frame or a Cross-Origin Frame Blocking (COFB) error. In this article, we will discuss the scenario where a frame with the origin “http://localhost:3000” is blocked from accessing a cross-origin frame.
The localhost:3000 Origin and its Significance
The origin “http://localhost:3000” typically refers to a locally hosted web server running on the developer’s machine during the development or testing phase. This local server allows developers to build and test their web applications without the need for deployment to a remote server. The “localhost” represents the local machine, and the “:3000” denotes the port number on which the server is running.
Blocked Cross-Origin Frame Access
When a web page containing frames is loaded, the browser enforces the SOP by default and prevents cross-origin frame access. If a frame from “http://localhost:3000” attempts to access a frame hosted on a different origin, such as “http://example.com,” the browser blocks the access.
The browser displays an error message indicating that the frame access was denied due to security restrictions. The message typically reads, “Blocked a frame with origin ‘http://localhost:3000′ from accessing a cross-origin frame.” This error is designed to protect users’ data and ensure that sensitive information is not accessed or tampered with by unauthorized sources.
To overcome this issue, developers can use techniques such as Cross-Origin Resource Sharing (CORS) or proxy methods to allow cross-origin frame access between trusted domains. However, these techniques require proper configuration and implementation to ensure security is not compromised.
Frequently Asked Questions (FAQs)
Q: Why does the browser block cross-origin frame access?
A: Cross-origin frame access is blocked to prevent potential security risks. Allowing unrestricted access to frames from different origins could expose sensitive information or enable unauthorized execution of scripts, potentially leading to unauthorized access or data breaches.
Q: Can cross-origin frame access be enabled for specific domains?
A: Yes, it is possible to enable cross-origin frame access for specific domains by configuring the server’s response headers using CORS. The server response should include the ‘Access-Control-Allow-Origin’ header, specifying the allowed origins.
Q: Are there any alternative methods to enable cross-origin frame access?
A: Yes, if direct CORS configurations are not feasible, developers can use proxy methods. These involve making requests from the local server to retrieve remote content and serving it from the same origin to avoid cross-origin restrictions.
Q: How can I resolve the “Blocked a frame with origin ‘http://localhost:3000’ from accessing a cross-origin frame” error?
A: To resolve this error, you can modify the server’s response headers to allow cross-origin frame access. If you don’t have control over the server, consider using a proxy method or implementing server-side scripts to retrieve and serve the remote content.
Q: Does this error affect production environments?
A: No, this error primarily occurs during development or testing phases when running a locally hosted development server. In production environments, where web applications are hosted on remote servers, cross-origin frame access restrictions may not be encountered.
In conclusion, blocked cross-origin frame access acts as a vital security measure implemented by modern browsers. The SOP prevents frames hosted on different origins from accessing each other’s information or executing scripts by default. Although encountering the “Blocked a frame with origin ‘http://localhost:3000’ from accessing a cross-origin frame” error may hinder development or testing, it ensures the integrity and security of web applications in live environments. Developers can overcome this error by configuring CORS headers or employing proxy methods to enable controlled cross-origin frame access during development.
Uncaught Domexception Blocked A Frame With Origin Iframe
What is an Uncaught DOMException?
The DOMException represents an abnormal event or error that occurs during the manipulation of web documents using the Document Object Model (DOM). It is a standard built-in JavaScript object which inherits from the Error class. The Uncaught DOMException is a specific type of DOMException that occurs when a web page tries to communicate across different origins (domains, protocols, or ports) or access restricted resources within iframes.
Causes of the Uncaught DOMException: Blocked a frame with origin iframe
1. Cross-Origin Resource Sharing (CORS): Browsers strictly enforce the Same-Origin Policy to prevent malicious websites from accessing sensitive data. This policy restricts JavaScript code from making requests to resources (scripts, stylesheets, images, etc.) located on a different domain. When an iframe tries to access a resource from a different origin, the browser blocks it and throws the “Blocked a frame with origin iframe” error.
2. Missing or incorrect HTTP headers: The server hosting the resource accessed by the iframe needs to send appropriate CORS headers to indicate that cross-origin requests are allowed. These headers include ‘Access-Control-Allow-Origin’, ‘Access-Control-Allow-Methods’, and ‘Access-Control-Allow-Headers’. If these headers are missing or misconfigured, the browser blocks the iframe’s requests, leading to the Uncaught DOMException error.
3. Sandbox attribute on the iframe: The sandbox attribute, applied to an iframe, restricts the permissions and capabilities of its contents. When certain sandbox values are specified, such as ‘allow-same-origin’ or ‘allow-scripts’, the iframe’s ability to access resources or execute scripts outside its origin is restricted, resulting in the Uncaught DOMException error.
Solutions to the Uncaught DOMException: Blocked a frame with origin iframe
1. Configure CORS headers on the server: To allow cross-origin requests, the server hosting the requested resource should send appropriate CORS headers. Ensure that the ‘Access-Control-Allow-Origin’ header is set to the domain that will access the resource, or use the wildcard ‘*’ to allow all origins. Additionally, the ‘Access-Control-Allow-Methods’ and ‘Access-Control-Allow-Headers’ headers should be properly configured depending on the resource’s requirements.
2. Utilize the ‘sandbox’ attribute correctly: If you have control over the iframe’s code, ensure that the ‘sandbox’ attribute is correctly set to match the required permissions. For example, if cross-origin communication is needed, include the ‘allow-same-origin’ value. Refer to the Mozilla Developer Network documentation on the sandbox attribute for more information on its usage and available values.
3. Utilize postMessage for cross-origin communication: The postMessage API enables secure communication between iframes and their parent or child windows across different origins. It allows exchanging data or triggering actions using a safe messaging mechanism. Both the sender and receiver need to implement the postMessage API to establish reliable cross-origin communication.
FAQs about the Uncaught DOMException: Blocked a frame with origin iframe error
Q1. Why does the browser block cross-origin requests?
A1. The browser blocks cross-origin requests to prevent potentially malicious websites from accessing data or executing actions on other domains without proper authorization.
Q2. Can I bypass the Uncaught DOMException error?
A2. The browser’s security measures are in place to protect users and their data. While there are potential workarounds, it is essential to follow proper security practices and implement solutions like CORS headers or postMessage for safe cross-origin communication.
Q3. Can I configure CORS headers on third-party resources?
A3. Unfortunately, you cannot modify the response headers of third-party resources directly. If you encounter the Uncaught DOMException error when trying to access a third-party resource, you should contact the resource owner and request them to configure the appropriate CORS headers.
Q4. Are there any browser-specific limitations related to the Uncaught DOMException?
A4. Different browsers might have slightly different restrictions or error messages related to the Uncaught DOMException. It is advisable to test and ensure compatibility across multiple browsers during the development process.
In conclusion, the Uncaught DOMException: Blocked a frame with origin iframe is a common error that web developers encounter while trying to access resources or execute code across different origins using iframes. By understanding its causes and implementing appropriate solutions like configuring CORS headers or utilizing postMessage for cross-origin communication, developers can overcome this error and ensure seamless functionality within their web applications.
X-Frame-Options
In the ever-evolving world of web development, security is a crucial aspect that cannot be overlooked. As technology advances, so do the methods employed by malicious actors to exploit vulnerabilities in web applications. One such vulnerability is clickjacking, where an attacker tricks a user into clicking on a button or a link on a webpage that they did not intend to interact with. To combat this, web developers can utilize the x-frame-options header, an important component of web security.
What is the x-frame-options Header?
The x-frame-options header is a simple and effective security measure that prevents clickjacking attacks by limiting how a webpage can be embedded within an iframe element. With this header, a website can specify whether it is allowed to be framed by other websites or not. It was introduced by Microsoft in Internet Explorer 8 and has since been adopted by other major browsers.
How does the x-frame-options Header Work?
When a browser attempts to load a webpage, it checks for the x-frame-options header in the server’s response. If the header is present, the browser evaluates its value and takes appropriate action. The header supports three different directives or values:
1. DENY: This directive completely prevents a webpage from being displayed within an iframe on any other website, regardless of the domain.
2. SAMEORIGIN: With this directive, a webpage can only be displayed within an iframe on a page that originates from the same domain. This restricts the embedding of a webpage on other domains.
3. ALLOW-FROM uri: This value allows a webpage to be framed by the specified URI (Uniform Resource Identifier) while restricting embedding on other domains.
The x-frame-options header is sent in the server’s response headers, usually via the Content-Security-Policy (CSP) headers or directly by the web server. This header works because browsers adhere to the security policies specified by the website, protecting users from potential clickjacking attacks and maintaining the integrity of their browsing experience.
FAQs about the x-frame-options Header:
Q1. Which browsers support the x-frame-options header?
A1. The x-frame-options header is supported by all major browsers, including Google Chrome, Mozilla Firefox, Microsoft Edge, and Safari.
Q2. Can I use multiple directives in the x-frame-options header?
A2. No, only one directive can be used at a time in the x-frame-options header. If multiple directives are specified, the browser ignores all but the first directive encountered.
Q3. Are there any alternatives to the x-frame-options header?
A3. Yes, the newer Content-Security-Policy (CSP) header can be used as an alternative. It provides greater flexibility and control over various aspects of web security, including limiting frame embedding.
Q4. Are there any potential drawbacks to using the x-frame-options header?
A4. One potential drawback is that if the header is misconfigured or not implemented correctly, it can inadvertently prevent legitimate framing of a webpage, leading to a poor user experience. It is important to thoroughly test the impact of implementing the header before enforcing it.
Q5. Does the x-frame-options header provide protection against all types of attacks?
A5. No, while the x-frame-options header is effective against clickjacking attacks, it does not offer protection against other types of vulnerabilities or attacks, such as cross-site scripting (XSS) or cross-site request forgery (CSRF). Web developers must employ other security measures alongside the x-frame-options header to ensure comprehensive protection.
In conclusion, the x-frame-options header is a powerful tool in the fight against clickjacking attacks. By including this header in server responses, web developers can restrict how their webpages are embedded in iframes, thereby safeguarding users from falling victim to malicious actions. It is crucial for developers to understand the various directives of the x-frame-options header, as well as any potential drawbacks, in order to implement it effectively and ensure the security of their web applications.
Images related to the topic blocked a frame with origin from accessing a cross-origin frame

Found 26 images related to blocked a frame with origin from accessing a cross-origin frame theme




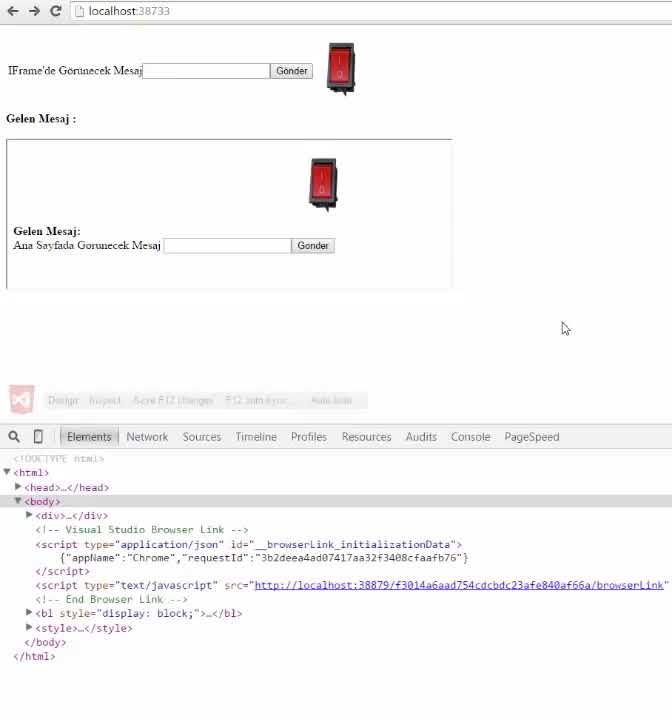


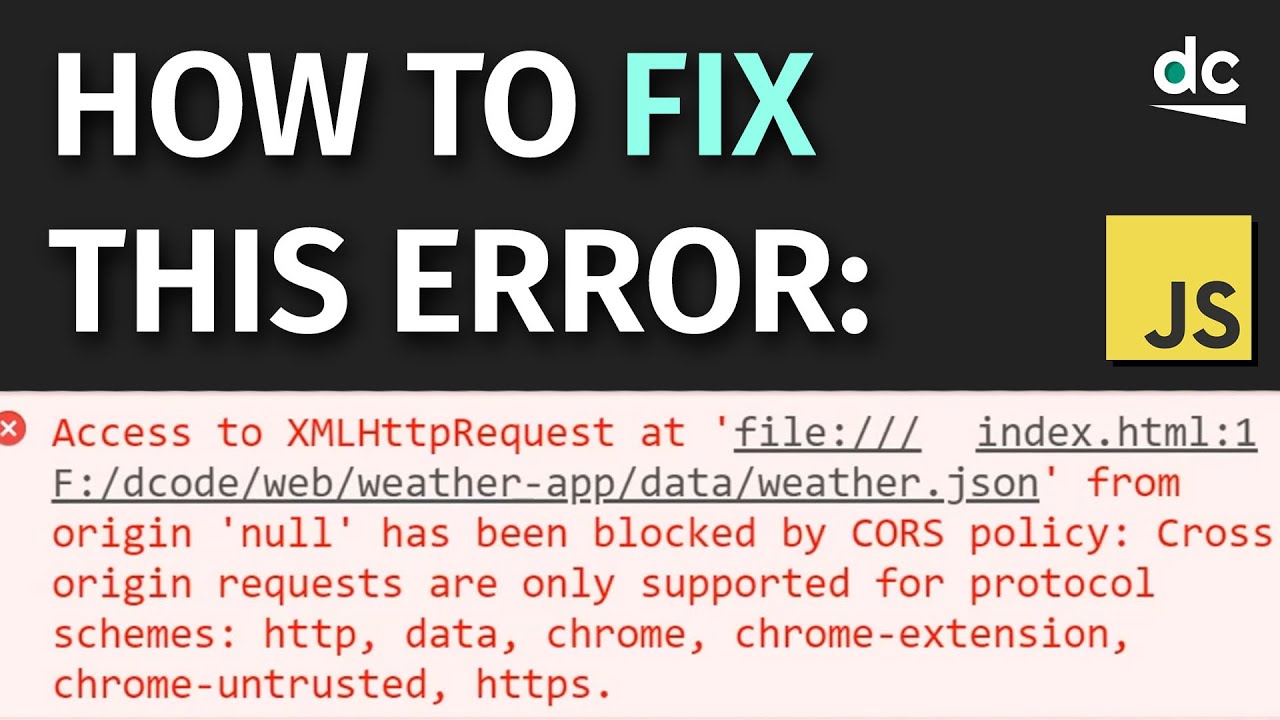





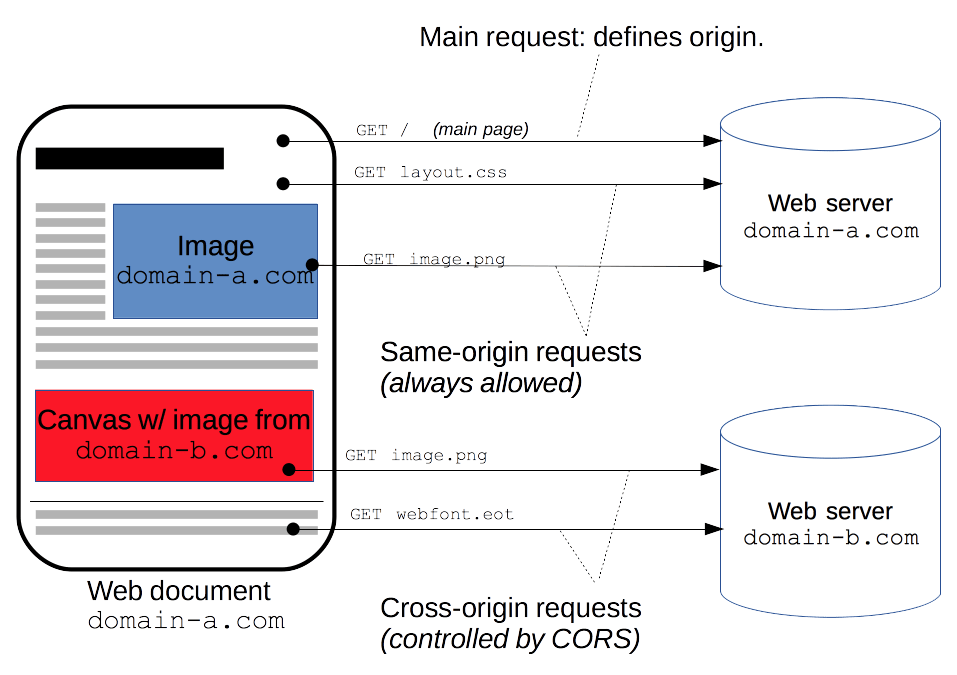





Article link: blocked a frame with origin from accessing a cross-origin frame.
Learn more about the topic blocked a frame with origin from accessing a cross-origin frame.
- SecurityError: Blocked a frame with origin from accessing a …
- Resolving the Blocked a Frame with Origin “null … – HackerNoon
- Blocked a frame with origin from accessing a cross-origin frame
- Cross-Origin Resource Sharing (CORS) – HTTP – MDN Web Docs
- Blocked a Frame With Origin From Accessing a Cross-origin …
- Blocked a frame with origin from accessing a cross-origin frame
- Blocked a frame with origin “domain.com” from accessing
- Blocked a frame with origin from accessing a cross-origin frame
- Uncaught DOMException: Blocked a frame with origin
See more: https://nhanvietluanvan.com/luat-hoc/