Audiences In Jwt Are Not Allowed
Introduction:
JWT (JSON Web Token) is a widely-used technology in the digital marketing landscape, playing a crucial role in enabling secure data transmission and authentication. However, audiences, an important concept in advertising, are not allowed in JWT. In this article, we will delve into the reasons behind this prohibition, the potential consequences of including audiences in JWT campaigns, and strategies for creating engaging and effective JWT campaigns without targeting specific audiences. We will also explore alternative methods for understanding and reaching potential consumers in JWT, considering the evolving landscape of advertising to diverse audiences.
1. The Purpose of JWT and Its Significance in Marketing:
JSON Web Tokens (JWTs) are compact, URL-safe tokens that facilitate secure data transmission between parties. They are commonly used in web applications and APIs for authentication, data exchange, and authorization purposes. JWTs are advantageous in marketing as they ensure the integrity and confidentiality of user data, enhancing trust between businesses and their customers.
JWTs offer a secure mechanism for transmitting user information and authentication data, providing seamless user experiences across different platforms. This technology has become a cornerstone in enabling personalized, targeted marketing campaigns that can resonate with individual users’ preferences and needs.
2. Understanding the Concept of Audiences in JWT and Their Role in Advertising:
Audiences, in the context of JWT, refer to a specific group of users targeted through marketing campaigns. They comprise individuals who share common characteristics, interests, or behaviors that make them potential consumers for a particular product or service. Identifying and understanding audiences is vital to deliver tailored advertising messages and drive conversions.
Including audience information in JWT allows marketers to create personalized experiences for users. By analyzing audience data, businesses can segment customers, craft targeted campaigns, and measure their effectiveness. This level of personalization can significantly boost the efficiency of marketing efforts by reaching users who are more likely to be interested in the products or services offered.
3. The Reasons behind the Prohibition of Audiences in JWT:
Although audiences play a crucial role in advertising, there are strong reasons behind their prohibition in JWT. One of the key aspects is security. JWTs are designed to carry concise, essential information for authentication, authorization, or other purposes. Including audience information can make the token bulkier and potentially compromise its security, increasing the risk of data breaches.
Moreover, JWTs are commonly used in various contexts, including third-party integrations and APIs. Allowing audiences in JWTs can potentially lead to unauthorized access if passed on to untrusted third-party systems. Therefore, to protect user data and maintain the integrity of the JWT technology, audiences are not allowed.
4. The Potential Consequences of Including Audiences in JWT Campaigns:
Including audiences in JWT campaigns can have several negative consequences. Firstly, it can compromise the security of user data. By storing sensitive user information within JWTs, the risk of unauthorized access increases, making it easier for malicious actors to obtain sensitive customer data.
Furthermore, including audiences in JWTs can hamper scalability. JWTs are designed to be lightweight, enabling swift transmission and processing. Adding audience information to JWTs increases their size, potentially impacting network bandwidth, server load, and overall performance.
5. Strategies for Creating Engaging and Effective JWT Campaigns without Targeting Specific Audiences:
Although audiences are not allowed in JWT, there are alternative strategies for creating engaging and effective JWT campaigns. Here are a few approaches to consider:
a. Behavioral Analysis: Instead of targeting specific audiences, focus on analyzing user behaviors within platforms, applications, or websites. By observing and understanding user actions, preferences, and demographics, businesses can tailor their marketing campaigns accordingly. Implementing pixel-based tracking and analytics tools can provide valuable insights into user behaviors.
b. Dynamic Content Delivery: Employ dynamic content delivery mechanisms based on user interactions and preferences. Use cookies or local storage to store personalized data, such as user preferences, browsing history, or past purchases. With this information, businesses can dynamically adjust the content of their JWT campaigns to make them more relevant to individual users.
c. A/B Testing and Iterative Campaigns: Implement continuous A/B testing to refine JWT campaigns and optimize their effectiveness. By testing different variations of campaign messages or visuals, businesses can empirically determine which approach resonates best with their target market. Iteratively improving campaigns based on user feedback and data analytics can lead to better engagement.
6. Exploring Alternative Methods for Understanding and Reaching Potential Consumers in JWT:
Without targeting specific audiences within JWT, businesses can still explore alternative methods for understanding and reaching potential consumers. Some effective strategies include:
a. Social Media Insights: Leverage social media platforms to gain insights into user demographics, interests, and behaviors. Utilize analytics tools provided by platforms like Facebook, Instagram, or Twitter to understand the characteristics of your audience and create targeted advertising campaigns accordingly.
b. Customer Surveys and Feedback: Implement surveys and feedback mechanisms to collect direct insights from customers. By asking targeted questions, businesses can gather valuable information about their preferences, needs, and concerns. Analyzing survey data can guide strategic decisions, ensuring better alignment with customer expectations.
c. Third-Party Data Providers: Partner with reputable third-party data providers that specialize in audience profiling and segmentation. These providers collect vast amounts of data from diverse sources, offering businesses valuable insights into user behavior, interests, and demographics.
7. The Future Outlook for JWT and the Evolving Landscape of Advertising to Diverse Audiences:
As technology continues to advance, the advertising landscape is becoming more complex and diverse. Businesses must adapt their marketing strategies to effectively reach and engage with their target audiences. Although audiences are not allowed in JWT, advancements in alternative tracking and data analytics methods ensure businesses can still deliver personalized experiences to their customers.
The future of JWT lies in striking a balance between security and personalization. As advancements in encryption and data protection continue, there may be enhanced protocols allowing secure transmission of audiences’ information in a tokenized format. Businesses should remain vigilant in staying up-to-date with industry standards and best practices to adapt to the evolving advertising landscape.
FAQs:
Q1: Why are audiences not allowed in JWT?
Ans: Audiences are not allowed in JWT to prioritize security and maintain the integrity of the token-based authentication system.
Q2: What are the potential consequences of including audiences in JWT campaigns?
Ans: Including audiences in JWT campaigns can compromise user data security and impact scalability due to increased token size.
Q3: How can businesses create effective JWT campaigns without targeting specific audiences?
Ans: Businesses can focus on behavioral analysis, dynamic content delivery, and continuous A/B testing to create engaging JWT campaigns without targeting specific audiences.
Q4: What alternative methods can businesses use to understand and reach potential consumers in JWT?
Ans: Social media insights, customer surveys and feedback, and partnering with third-party data providers can help businesses effectively understand and reach potential consumers in JWT.
Q5: What is the future outlook for JWT and advertising to diverse audiences?
Ans: The future of JWT lies in striking a balance between security and personalization. Advancements in encryption and data protection may enhance protocols for secure transmission of audience information in a tokenized format. Businesses should stay updated with industry standards to adapt to the evolving advertising landscape.
The Audience Of Tokens – 2 Min. Oauth #10
What Is The Audience And Issuer In Jwt?
JSON Web Tokens (JWT) are widely used for secure communication between parties over the internet. In the context of JWT, the terms “audience” and “issuer” are critical components of the token’s payload. They help establish and verify the identity and permissions of the entities involved in the token exchange. In this article, we will delve into the concepts of audience and issuer in JWT, their significance, and how they contribute to secure communication.
Understanding JWT:
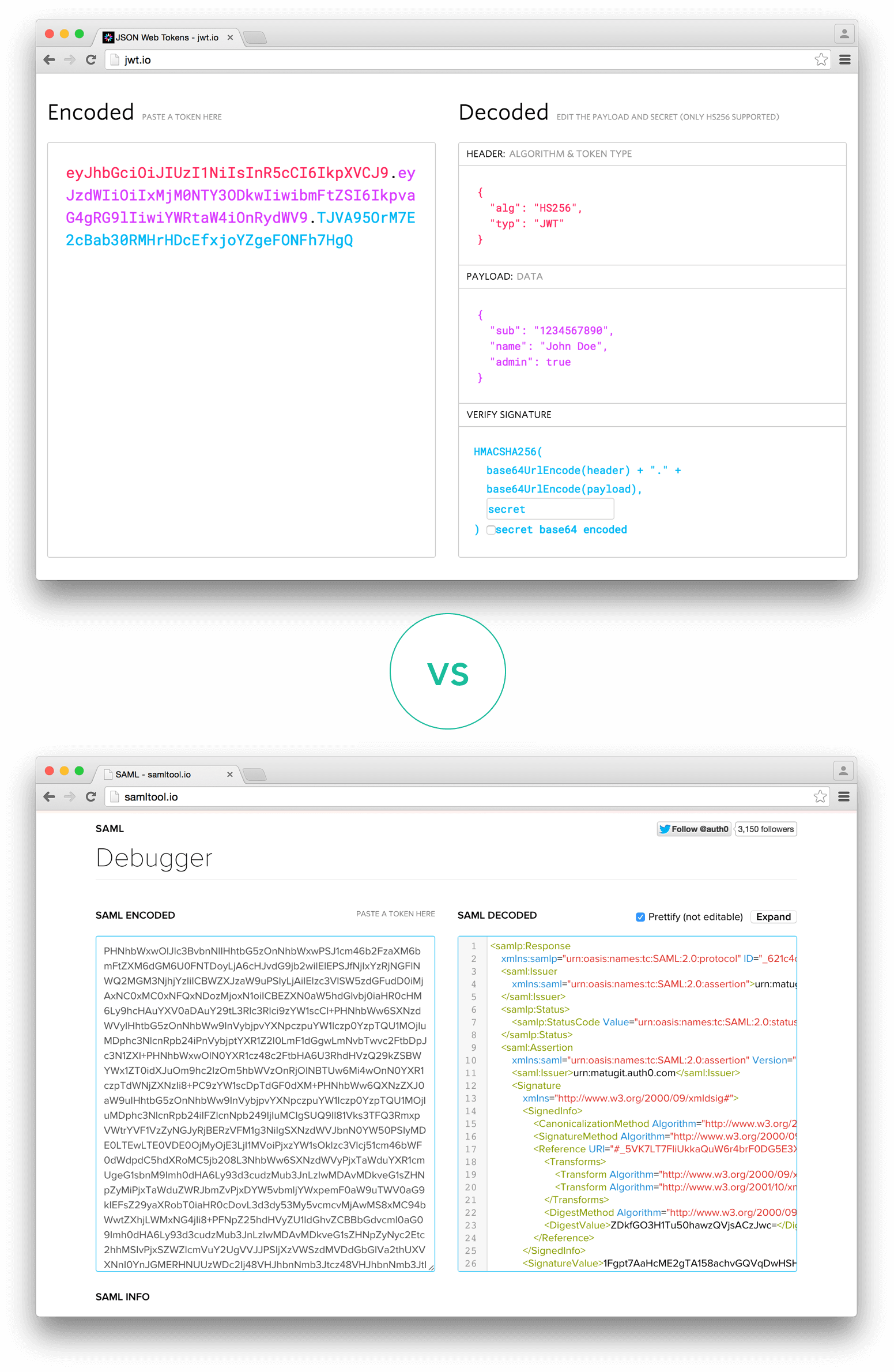
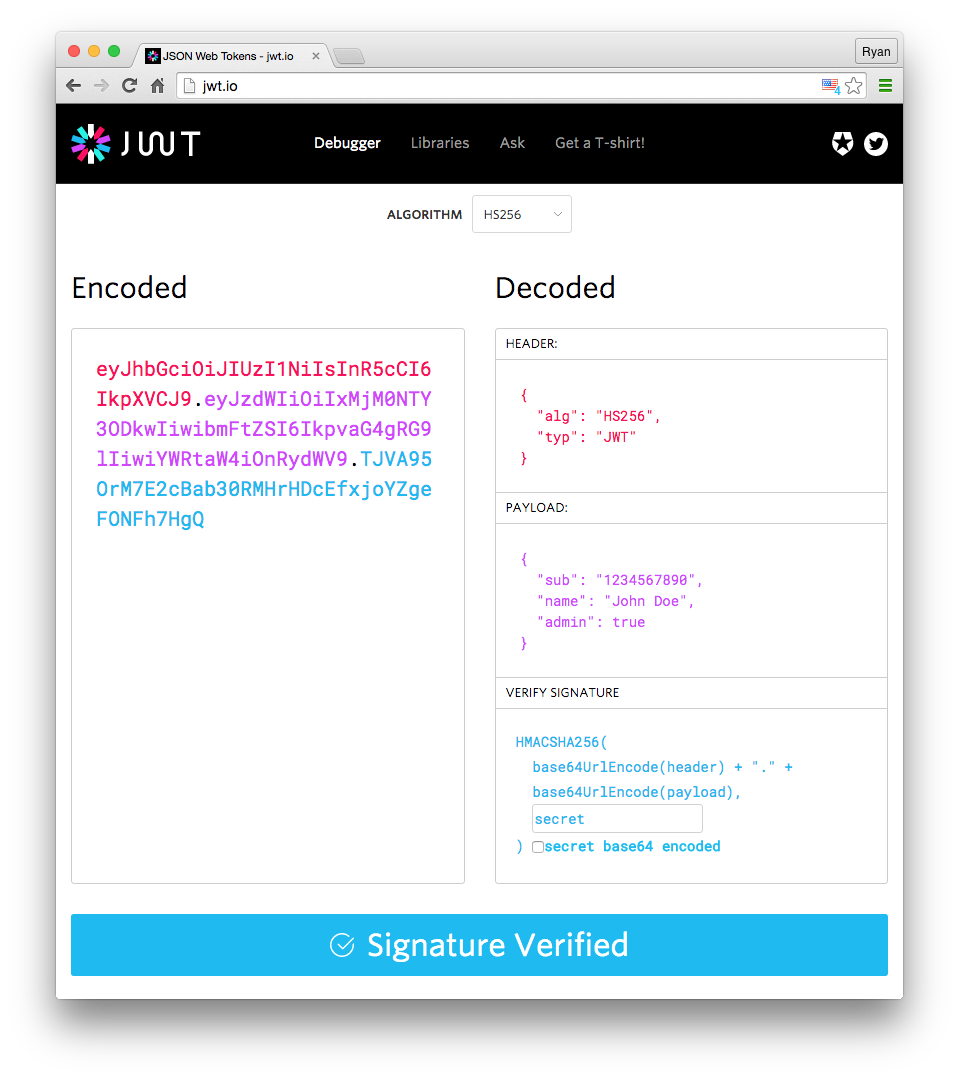
Before we dive into the specifics of the audience and issuer, let’s have a brief overview of JWT. A JWT is essentially a compact, self-contained token that contains JSON-encoded data, including any necessary claims about the identity or permissions of the authenticated user or system. These tokens are digitally signed using a secret key or a public/private key pair, enabling secure transmission and ensuring authenticity.
JWTs consist of three parts: a header, a payload, and a signature. The header defines the algorithm used to sign the token, while the payload carries the actual data, including the audience and issuer information. The signature is a combination of the encoded header and payload, signed with the issuer’s secret key.
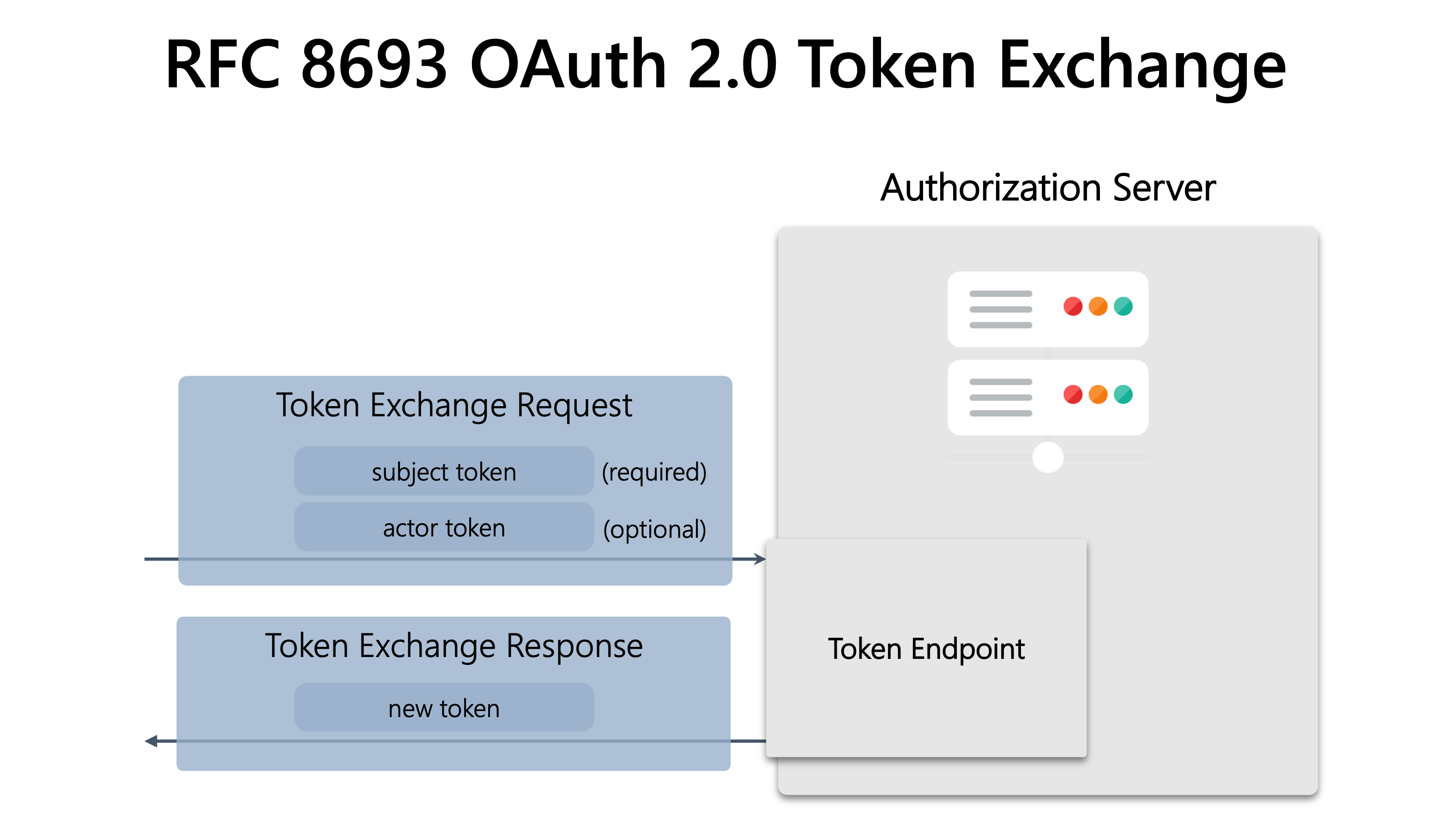
The Audience (aud) Claim:
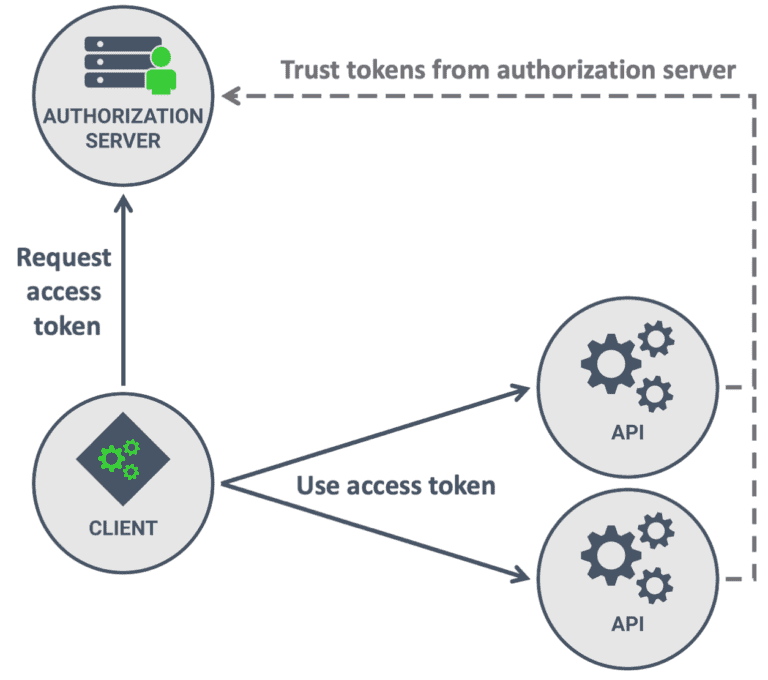
The “audience” claim in a JWT payload specifies the intended recipient or recipients of the token. It defines the system or party that is expected to receive and process the token. An audience can be an individual user, a group, or even a service or API endpoint. The audience claim is essential in ensuring that the token is only used by the intended recipient systems.
By including the audience claim, a JWT becomes more secure since it limits the token’s usability to the designated recipients. The receiving system can check whether it is the intended audience by comparing the value of the audience claim in the token against its own identity or verification rules. If the values match, the token is considered valid for that particular recipient.
The Issuer (iss) Claim:
The “issuer” claim in a JWT payload identifies the entity that issued or created the token. The issuer can be an authentication server, an identity provider, or any trusted party responsible for generating the token. The issuer claim is crucial for both the sender and recipient systems to identify and establish trust between them.
When a JWT is received, the recipient system can verify the token’s authenticity by validating the signature and then checking the issuer claim against its list of trusted issuers. If the value matches, the recipient can rely on the issuer’s identity and assume that the token is valid.
FAQs:
Q1: What happens if the audience claim in the token does not match the recipient’s identity?
A1: If the audience claim does not match the recipient’s identity, the recipient system should reject the token as it is not intended for that system. This helps prevent unauthorized access to sensitive resources.
Q2: Can a JWT have multiple audiences?
A2: Yes, a JWT can have multiple audiences. In such cases, the recipient system must match at least one of the specified audiences to consider the token valid.
Q3: How is the issuer claim verified?
A3: The recipient system verifies the issuer claim by comparing the value in the token against its trusted list of issuers. If the value matches any trusted issuer, the token is considered valid.
Q4: Is the audience claim mandatory in a JWT?
A4: The audience claim is not mandatory in a JWT, but including it enhances security and ensures the token’s usage is restricted to specific recipients.
Q5: Can the audience and issuer claims be used together?
A5: Yes, it is common to use both the audience and issuer claims in a JWT. The audience ensures the token is used by the right recipient, while the issuer establishes trust between the systems.
Conclusion:
The audience and issuer claims play fundamental roles in JWT authentication and authorization processes. The audience claim ensures that JWTs are only consumed by the intended recipients, limiting the risk of unauthorized access. On the other hand, the issuer claim helps verify the token’s trustworthiness and authenticity by matching it against a trusted list. These two components work together to establish secure communication and maintain uncompromised system interactions within the realm of JSON Web Tokens.
What Is A Jwt Error?
JSON Web Tokens, commonly known as JWTs, have become popular as a secure means of authentication and authorization. They are compact and self-contained, making them ideal for transmitting encrypted information between parties. However, like any complex technology, JWTs can encounter errors that can hinder their functionality. In this article, we will delve into the world of JWT errors, exploring their causes, types, and solutions.
Understanding JWTs
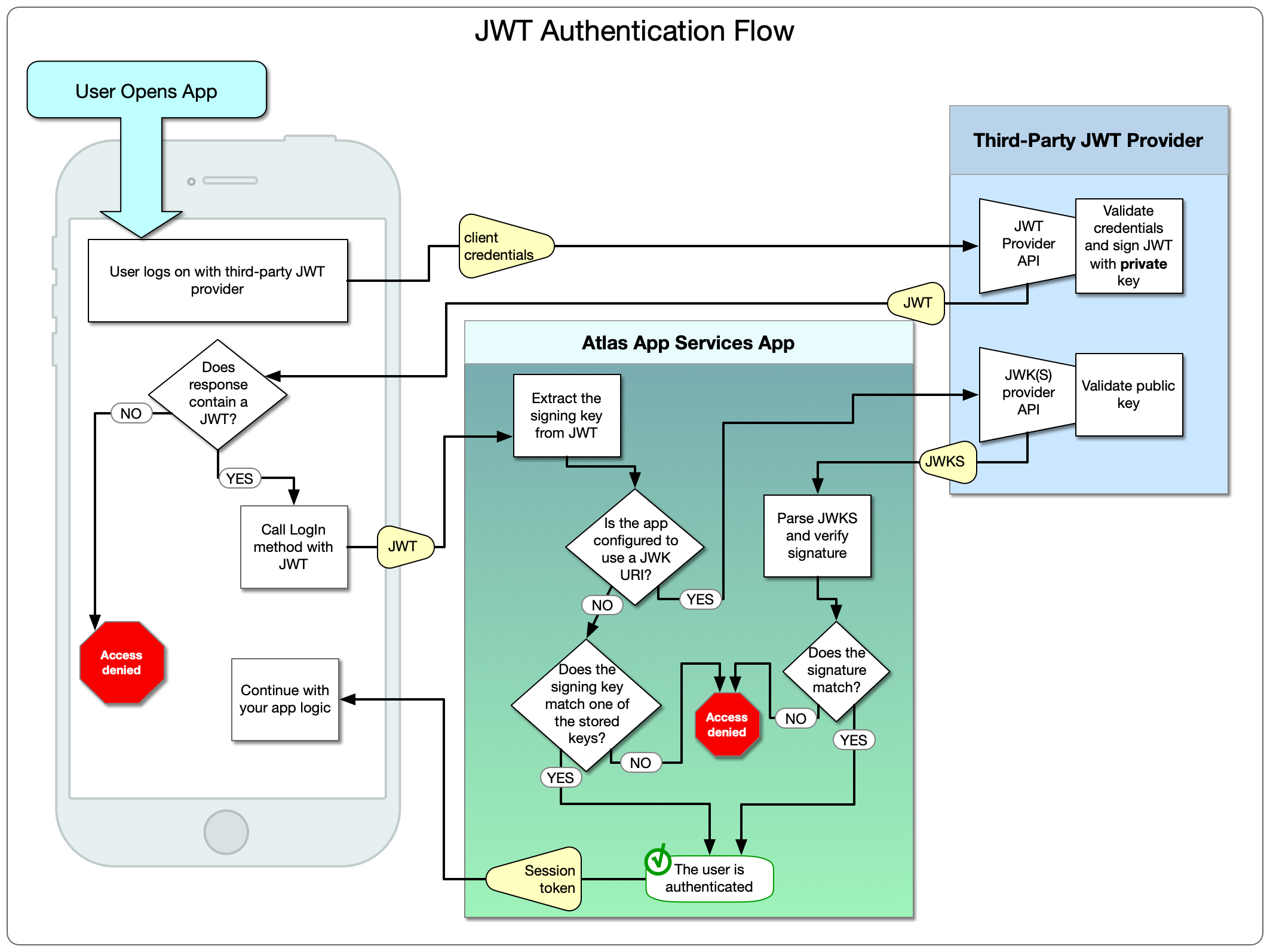
Before we dive into JWT errors, let’s briefly examine what JWTs are and how they function. A JSON Web Token consists of three parts: a header, a payload, and a signature. The header contains the token’s type and the cryptographic algorithms used for signing and encryption. The payload stores the data or claims, such as user information or access privileges. Finally, the signature ensures the token’s integrity and authenticity.
When a user logs in or performs an action, a server validates the user’s credentials and generates a JWT. This token is then sent to the client, typically stored in a cookie or local storage. On subsequent requests, the client includes the JWT in the request header’s Authorization field, allowing the server to authenticate and authorize the user.
Types of JWT Errors
While JWTs are generally reliable, various errors can occur during their usage. Let’s explore some common types of JWT errors:
1. Invalid Token: One of the most common JWT errors is an invalid token. This can happen due to various reasons, such as a token being tampered with, expired, or signed with an unknown algorithm. An invalid token causes authentication or authorization failures, preventing the user from accessing protected resources.
2. Expired Token: JWTs often have an expiration time to enhance security. If a client sends an expired token, the server rejects it, resulting in an “expired token” error. This prompts the client to request a new token before continuing the session.
3. Bad Signature: JWTs use signatures to ensure integrity and authenticity. If a token’s signature does not match the expected value, the server generates a “bad signature” error. Possible causes include tampering, misconfigured keys, or a wrong algorithm being used during verification.
4. Untrusted Issuer: JWTs include an “issuer” claim that identifies the entity generating the token. Servers typically maintain a list of trusted issuers, and if a received token’s issuer is not on that list, an “untrusted issuer” error occurs. This error helps prevent unauthorized parties from generating tokens.
5. Token Format Error: Tokens must adhere to a specific format defined by the JWT standard. Any deviations from this format, such as missing parts or incorrect encoding, trigger a “token format error” that prevents proper token parsing.
Handling JWT Errors
To mitigate JWT errors, developers should implement robust error handling mechanisms. Here are some recommended strategies:
1. Detailed Logging: Logging is crucial for troubleshooting JWT errors. Developers should log relevant information such as error messages, request details, and timestamps. These logs facilitate debugging and help identify patterns and recurring issues.
2. Custom Error Messages: Providing informative error messages can guide users and developers in resolving issues. Instead of generic messages like “invalid token,” describe the cause and suggest possible solutions. This allows users to take appropriate actions, such as refreshing their token or contacting support.
3. Token Refresh Mechanism: Expired tokens can disrupt user sessions and cause inconvenience. Implementing a token refresh mechanism allows clients to automatically acquire a new token without requiring user intervention. This enhances user experience while maintaining security.
4. Token Validation and Verification: Properly validating and verifying tokens helps mitigate various JWT errors. Ensure that tokens adhere to the expected format, have a valid signature, and come from trusted issuers. Employing libraries or frameworks specifically designed for JWT management can simplify these tasks.
Frequently Asked Questions about JWT Errors
Q: Can a JWT error be bypassed?
A: JWT errors indicate authentication or authorization failures, ensuring secure access to resources. They cannot be bypassed without addressing the underlying issue.
Q: How can I prevent JWT errors caused by token expiration?
A: Implement a token refresh mechanism that automatically acquires a new token when the old one expires. This approach eliminates the need for manual token refreshes and enhances user experience.
Q: Are JWT errors specific to a programming language or framework?
A: No, JWT errors can occur in any system that utilizes JWTs for authentication or authorization. However, the exact error messages and handling strategies may vary depending on the programming language or framework in use.
Q: Can JWT errors be caused by network issues?
A: While JWT errors are primarily related to token validation and verification, network issues can indirectly contribute to such errors. For example, if the client cannot reach the server to validate a token, it may result in an “untrusted issuer” error.
In conclusion, JWT errors can hinder the functionality of authentication and authorization systems using JSON Web Tokens. Understanding the various types of errors and implementing appropriate error handling mechanisms is crucial for ensuring a robust and secure user experience. By adopting best practices and following the recommendations outlined in this article, developers can minimize JWT errors and provide seamless access to protected resources for their users.
Keywords searched by users: audiences in jwt are not allowed x-google-audiences, Audiences in JWT are not allowed, JWT contains untrusted aud claim, jwt-decode
Categories: Top 94 Audiences In Jwt Are Not Allowed
See more here: nhanvietluanvan.com
X-Google-Audiences
Introduction (approximately 80 words):
In the ever-evolving digital advertising landscape, Google Ads offers a myriad of targeting options to reach potential customers effectively. In recent times, X-Google-Audiences has emerged as a valuable feature. This article aims to provide a comprehensive insight into X-Google-Audiences, shedding light on its definition, benefits, implementation process, and best practices. By leveraging this powerful tool, advertisers can precisely target their desired audience, optimize campaign performance, and achieve better results.
1. What are X-Google-Audiences? (approximately 120 words)
X-Google-Audiences are custom audience lists created by advertisers within the Google Ads platform. These lists are generated using first-party data, offering advertisers a high level of control and personalization. By creating and utilizing X-Google-Audiences, advertisers gain the ability to target their ads to specific groups of users who have previously visited their website or interacted with their app.
2. How to create an X-Google-Audience? (approximately 150 words)
Creating an X-Google-Audience involves a straightforward process within the Google Ads interface. Advertisers can navigate to the Audience Manager tab, select “Custom Audiences,” and then “Create custom audience.” They can choose from a range of options to define their audience, such as website visitors, app users, or CRM data.
To build a website visitor audience, a Google Ads tag or Global Site Tag (gtag.js) needs to be implemented on the website. This tag collects visitor data, enabling the creation of custom audiences. Similarly, for app user audiences, the app’s Firebase software development kit (SDK) must be integrated.
3. Benefits of X-Google-Audiences (approximately 150 words)
X-Google-Audiences offer several benefits to advertisers, including:
a) Highly targeted advertising: With X-Google-Audiences, advertisers can reach users who have already shown interest in their brand, thereby enhancing the effectiveness of their ad campaigns.
b) Improved relevance and personalization: By utilizing first-party data, advertisers can tailor their ads to specific audience segments, improving ad relevance and overall user experience.
c) Remarketing opportunities: X-Google-Audiences allow for efficient remarketing campaigns, ensuring that relevant ads are shown to engaged users who may have abandoned the conversion funnel.
d) Amplified campaign performance: By targeting customized audience lists, advertisers can focus their efforts on high-potential customers, leading to improved conversion rates and better return on investment (ROI).
4. Best Practices for X-Google-Audiences (approximately 250 words)
To make the most out of X-Google-Audiences, advertisers should consider the following best practices:
a) Segment audiences strategically: Segmenting audiences based on website behavior, app interactions, or purchase history can enhance campaign performance. This allows tailored messaging and bids for each specific segment.
b) Utilize audience exclusions: Advertisers can exclude specific segments from campaigns to minimize ad spend on users who are less likely to convert. This ensures that valuable budget is allocated to the most promising audience segments.
c) Leverage creative personalization: Tailor your ad creative to match the interests and needs of each audience segment. This personalized approach generates better engagement rates and improves overall campaign performance.
d) Continuously refine and update audiences: Regularly assess the performance of your X-Google-Audiences and update them to include new user data. This ongoing refinement helps keep the audience lists up to date and maximizes campaign effectiveness.
FAQs:
1. Can X-Google-Audiences be used in combination with other targeting options?
Absolutely! X-Google-Audiences can be used alongside other Google Ads targeting options, such as demographics, interests, and keywords. Combining various targeting methods allows for even more precise audience reach.
2. Are X-Google-Audiences created for one-time use only?
No, once an X-Google-Audience is created, it can be regularly used across multiple campaigns, ensuring continuous engagement with the desired audience groups.
3. Is X-Google-Audiences restricted to only Google Display Network campaigns?
Not at all! X-Google-Audiences can be utilized across various campaign types within the Google Ads ecosystem, including Display Network, Search Network, YouTube, and more.
4. Is setting up X-Google-Audiences time-consuming?
The process of creating and implementing X-Google-Audiences is relatively straightforward and can be done seamlessly within the Google Ads interface. However, the time required may vary based on the complexity of segmenting and defining the desired audience.
Conclusion (approximately 50 words):
X-Google-Audiences offer advertisers a powerful tool to enhance their digital advertising capabilities. By leveraging first-party data and following best practices, marketers can unlock precise audience targeting, heightened relevance, and improved campaign performance, ultimately leading to better results and a higher return on investment.
Audiences In Jwt Are Not Allowed
Audiences play a critical role in advertising and marketing campaigns. They are the groups of people who are targeted or intended to be reached with a specific message or content. However, when it comes to advertising agency JWT, audiences are not allowed to be used in their English campaigns. This unique approach sets JWT apart from other agencies and challenges traditional advertising practices. In this article, we will explore the reasons behind this decision and delve deeper into the implications for advertisers and marketers.
JWT, formerly known as J. Walter Thompson, is one of the world’s oldest and largest advertising agencies. With a rich history spanning over 150 years, the agency has been instrumental in shaping the advertising industry. However, in recent years, JWT has taken a bold stance by prohibiting the use of audiences in their English campaigns.
According to JWT’s philosophy, the exclusion of audiences helps to create inclusive and impactful campaigns. By breaking free from the constraints of targeting specific groups, JWT aims to reach a broader audience spectrum, fostering connections and resonating with a wider range of people.
One of the main reasons behind this decision is the desire to avoid stereotyping and generalizing audiences. Traditional targeting often leads to categorizing people based on demographics, such as age, gender, or location. This can often result in reinforcing stereotypes and limiting the diversity of voices and perspectives represented in advertising.
By removing audiences from the equation, JWT encourages marketers to focus on crafting messages that appeal to shared human experiences and emotions. This approach allows campaigns to transcend cultural and demographic barriers, catering to a more diverse and inclusive audience.
Another advantage of excluding audiences is the potential for surprises and unconventional connections. By not limiting their campaigns to a predefined group, JWT can generate unexpected reactions and engage with audiences that might have been overlooked otherwise. This element of surprise sparks curiosity and encourages people to question their preconceptions or biases.
Critics of this approach argue that without targeting specific audiences, advertising campaigns might lack focus and fail to generate significant results. It is true that targeting certain groups can increase the chances of reaching the intended audience and maximizing the return on investment. However, JWT’s alternative strategy relies on creating authentic and emotionally compelling stories that resonate universally.
JWT’s philosophy aligns with the rapidly changing media landscape, where diverse voices and perspectives are gaining prominence. The rise of social media platforms and the internet have empowered individuals to express their opinions and engage with content more actively. Traditional approaches to advertising might not effectively address this shift, as they often rely on passive consumption rather than active engagement.
By removing the focus on audiences, JWT encourages advertisers to adapt their strategies by placing storytelling and authentic experiences at the center of their campaigns. This requires a deep understanding of human emotions, behaviors, and aspirations, as well as the ability to craft narratives that evoke strong emotional responses.
FAQs:
Q: How does JWT ensure their campaigns reach the right audience without targeting?
A: JWT’s approach is not about reaching a specific audience but rather about creating campaigns that resonate with a broader range of people. By focusing on universal human experiences and emotions, they aim to engage with a more diverse and inclusive audience.
Q: How does JWT measure the success of their campaigns without targeting metrics?
A: JWT’s success measurement is not solely based on traditional targeting metrics like click-through rates or conversions. Instead, they aim to generate emotional reactions, provoke conversations, and ultimately build a lasting connection with their audience. Success is measured through qualitative feedback, brand perception, and the impact the campaign has on culture and society.
Q: Are there any exceptions to JWT’s no-audience policy?
A: While JWT’s English campaigns have a strict no-audience policy, they might adopt targeted strategies for campaigns in other languages or regions where cultural nuances and specific audiences need to be considered. However, the overarching philosophy of inclusive storytelling remains intact.
Q: How does this approach impact advertisers and marketers working with JWT?
A: Advertisers and marketers working with JWT need to adapt their mindset and strategies. They need to prioritize understanding human emotions, crafting authentic narratives, and creating campaigns that resonate universally. It requires a shift from the traditional focus on targeting to a broader perspective that embraces diverse audiences.
In conclusion, JWT’s decision to exclude audiences from their English campaigns is a bold and innovative approach in the advertising industry. By shifting the focus to inclusive storytelling, they aim to transcend cultural and demographic boundaries, reach a wider audience, and create impactful campaigns that resonate at a human level. While this approach challenges traditional advertising practices, it aligns with the evolving media landscape and the demand for diverse and inclusive content.
Images related to the topic audiences in jwt are not allowed

Found 49 images related to audiences in jwt are not allowed theme


























Article link: audiences in jwt are not allowed.
Learn more about the topic audiences in jwt are not allowed.
- Troubleshooting JWT validation | Cloud Endpoints with OpenAPI
- JWT Audience (aud) – MojoAuth
- Decode JWT runtime error troubleshooting | Apigee
- “409 Audience not allowed” error when making calls to ESP …
- Troubleshooting JWT validation – Cloud Endpoints
- Audience not allowed – Google Groups
- Troubleshooting External Functions for GCP
- JWT access-token without sending an audience to /authorize …
- Troubleshooting batch endpoints – Azure Machine Learning
- JWT token – audience claim – Genesys Cloud Developer Center
See more: https://nhanvietluanvan.com/luat-hoc