An Illegal Reflective Access Operation Has Occurred
Introduction:
In the world of Java programming, reflection plays a crucial role in enabling powerful features such as code manipulation, dynamic loading, and introspection. However, it also opens the door to potential security vulnerabilities, particularly in the form of illegal reflective access operations. This article aims to shed light on this issue, providing a comprehensive understanding of illegal reflective access operations, their causes, impacts, and how to mitigate and troubleshoot them effectively.
1. Definition of an Illegal Reflective Access Operation:
An illegal reflective access operation refers to the use of Java reflection API to access or modify a class member (a field, method, or constructor) that is normally not accessible to the caller using standard Java language rules. This violation of language restrictions can lead to unforeseen consequences and is generally considered unsafe and discouraged.
2. Understanding the Background and Purpose of Reflection in Java:
Reflection is a powerful mechanism in Java that allows the examination and manipulation of the internal properties, structures, and behaviors of classes at runtime. It enables dynamic loading of classes, retrieval of field values, invocation of methods, and instantiation of objects that may not be known or available during compile-time. Reflection is primarily used in scenarios like frameworks, libraries, or tools that require a deeper understanding and interaction with the code structure.
3. Causes and Triggers of Illegal Reflective Access Operations:
Illegal reflective access operations can occur due to several reasons and situations:
a. Deprecated or Deprecated-For-Removal APIs: As Java evolves, APIs can become deprecated or marked for removal in future releases. Using reflection to access or modify these APIs can trigger an illegal reflective access operation.
b. Accessing Private/Internal Members: Reflection allows access to private and internal members of classes, bypassing their intended encapsulation. This can result in illegal reflective access operations if not properly managed.
c. Security Managers and Restricted APIs: Security managers may restrict the use of certain APIs as a security measure. Reflection bypasses these restrictions if not used carefully, leading to illegal reflective access operations.
d. Libraries and Frameworks: Some libraries and frameworks may rely on reflection for their functioning. If they are not updated to utilize recommended APIs, they may inadvertently trigger illegal reflective access operations.
4. Impact and Potential Risks of Illegal Reflective Access Operations:
Illegal reflective access operations pose potential risks and impacts on the Java ecosystem, including:
a. Security Vulnerabilities: Bypassing the encapsulation of private members can expose sensitive information or allow unauthorized modifications, potentially compromising the overall security of the system.
b. Compatibility Issues: Java evolves with each release, and future versions may deny all illegal-access operations, rendering prior reflective code non-functional. This can lead to compatibility issues and code breakages.
c. Performance Degradation: Reflection is inherently slower than regular Java code execution. Excessive use of reflection, including illegal reflective access operations, can negatively impact the performance of an application.
5. Identifying and Troubleshooting Illegal Reflective Access Operations:
Detecting and resolving illegal reflective access operations can be challenging but crucial for maintaining a secure and efficient application. Here are some steps to follow:
a. Enable Access Warnings: Enable compiler warnings (-Xlint:unchecked and -Xlint:deprecation) to get notifications about illegal reflective access operations during the compilation process.
b. Use Diagnostic Tools: Integrated Development Environments (IDEs) such as IntelliJ and Eclipse provide tools that can help in identifying illegal reflective access operations. These tools can highlight the problematic code and suggest potential fixes.
c. Analyze Stack Traces: Runtime stack traces can provide insights into the specific illegal reflective access operation and its root cause. Analyzing these stack traces can help in troubleshooting and finding a solution.
6. Mitigating Illegal Reflective Access Operations through Best Practices:
To avoid illegal reflective access operations and their associated risks, follow these best practices:
a. Prefer Standard APIs: Whenever possible, use standard libraries and APIs instead of relying on reflection. Standard APIs are better supported, more secure, and less likely to trigger illegal reflective access operations.
b. Minimize the Use of Reflection: Reflection should be used judiciously and only when required. Overusing or relying heavily on reflection can make the code unnecessarily complex and prone to errors.
c. Update Libraries and Frameworks: Keep your libraries and frameworks up to date to ensure they are compatible with newer Java releases and use recommended APIs to avoid illegal reflective access operations.
d. Leverage Security Managers: Utilize security managers to restrict reflective access to sensitive areas of the code and prevent unauthorized operations.
7. Future Solutions and Updates to Prevent Illegal Reflective Access Operations:
Oracle strives to enhance Java’s security and stability. As a part of their efforts, future releases of Java plan to deny all illegal-access operations completely. It is essential to keep track of these updates, understand the impact on the codebase, and modify the reflective operations accordingly to ensure the continued functionality and compatibility of the application.
8. Summary and Conclusion:
Illegal reflective access operations pose security risks, compatibility issues, and performance degradation in Java applications. Understanding the causes, impacts, and best practices for mitigating and troubleshooting these operations is crucial for developers. By adhering to recommended practices, minimizing the use of reflection, and staying abreast of Java updates, developers can safeguard their applications from illegal reflective access operations and promote a robust and secure coding environment.
FAQs:
Q1. What does “All illegal-access operations will be denied in a future release” mean?
A1. This statement indicates that future versions of Java will reject any reflective code that attempts to access members in an illegal or non-standard way. Developers need to modify their reflective operations to adhere to the new standard APIs to ensure compatibility and avoid code breakages.
Q2. How can I resolve “An illegal reflective access operation has occurred” in IntelliJ or Eclipse?
A2. IntelliJ and Eclipse usually provide warnings or error messages about illegal reflective access operations during compilation. Identifying the problematic code and finding a suitable alternative or fixing the code based on these messages can help resolve these issues.
Q3. Why are some popular libraries triggering illegal reflective access operations?
A3. Libraries often rely on reflection to achieve dynamic behavior or interact with internal Java structures. If these libraries are not updated to use recommended APIs, they can inadvertently trigger illegal reflective access operations. Staying up to date with library releases and using compatible versions is essential to avoid such issues.
Q4. What are some examples of libraries/frameworks triggering illegal reflective access operations?
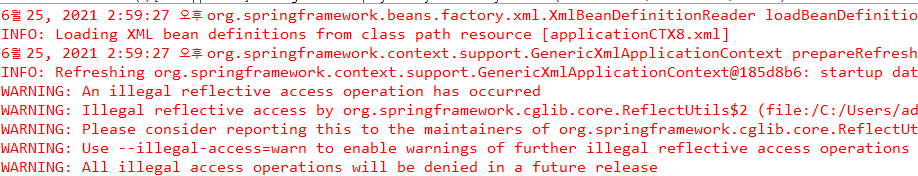
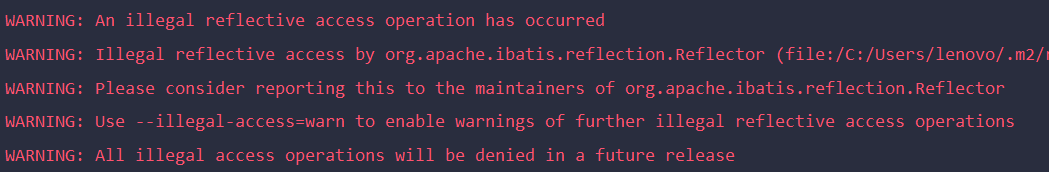
A4. Libraries/frameworks such as “org.apache.ibatis.reflection.Reflector,” “retrofit2.Platform,” “org.apache.spark.unsafe.Platform,” and “org.springframework.cglib.core.ReflectUtils” have been reported to trigger illegal reflective access operations. These issues can be resolved by using updated versions that utilize recommended APIs.
Q5. How can I identify illegal reflective access operations in my code?
A5. Enable compiler warnings, use diagnostic tools provided by IDEs, and analyze runtime stack traces to identify illegal reflective access operations in your code. These methods will help pinpoint the problematic code and suggest potential resolutions.
Why Groovy Shows Warning \”An Illegal Reflective Access Operation Has Occurred\” When I Use Jdk11?
What Is Jdk 11 Warning An Illegal Reflective Access Operation Has Occurred?
JDK 11, short for Java Development Kit 11, is a widely used software development platform that provides developers with the tools necessary to create, test, and deploy Java applications. However, while working with JDK 11, you may occasionally encounter a warning message stating, “An illegal reflective access operation has occurred.” This warning is issued by the Java Virtual Machine (JVM) when it detects that certain parts of the code are accessing internal APIs in a way that is not recommended or considered safe by the Java community.
In simpler terms, an illegal reflective access operation occurs when code tries to access or modify internal Java components, such as fields, methods, or classes, through mechanisms that are not intended for direct use by external code. These internal APIs are typically reserved for JVM implementation details and are not part of the public Java API. The warning aims to bring attention to these improper usages and prompt developers to evaluate their code for potential security and compatibility issues.
It’s worth noting that the reflective access itself is not inherently bad or dangerous. Java provides the Reflection API, which allows developers to analyze and manipulate code during runtime by accessing private members or invoking methods dynamically. Reflective access can facilitate powerful features like dependency injection, object creation at runtime, or testing frameworks. However, using reflective access to circumvent the encapsulation of internal APIs can lead to a variety of potential issues.
Why does the warning occur?
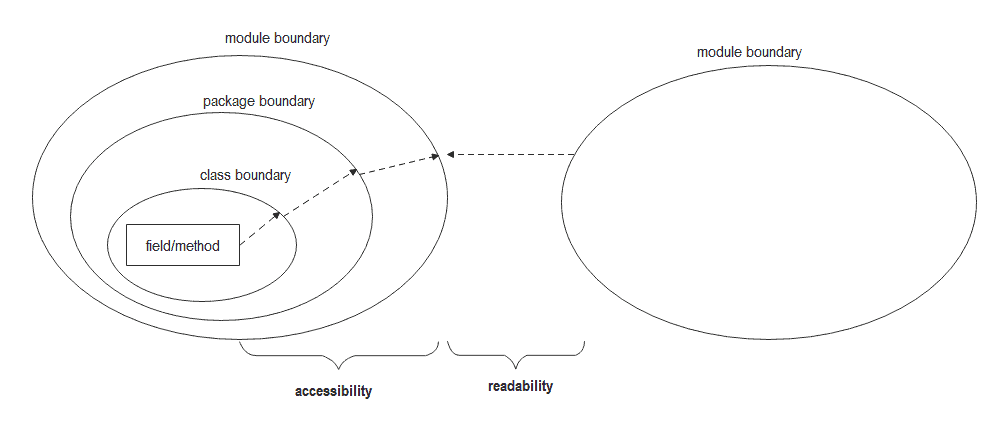
The warning message, “An illegal reflective access operation has occurred,” is primarily a result of the changes introduced in JDK 9. In JDK 9, the Java Platform Module System (JPMS) was introduced to enhance modularity and improve security. As part of this change, many internal APIs were encapsulated and restricted for use within the Java SE Platform modules.
To enforce modularity and encapsulation, JDK 9 introduced a new concept called “Modules.” These modules allow developers to explicitly define the dependencies and access restrictions for their code. However, since many existing libraries and frameworks were written before the introduction of modules, they may still rely on internal APIs that are now encapsulated. When reflective access is used to bypass encapsulation and access these internal APIs, the JVM issues the warning message.
It’s important to understand that this warning is not an error but only an indication of potential compatibility issues. However, it’s advisable to investigate and address the warnings as they may lead to future incompatibilities in newer Java versions or with different JVM implementations.
How to resolve the warning?
To resolve the warning, you have a few options depending on the specific circumstances:
1. Update dependent libraries: If you encounter the warning while using a third-party library, check if there is a newer version available that is compatible with JDK 11. Many popular libraries and frameworks have already updated their codebase to support the encapsulation introduced by JPMS.
2. Use command-line flags: If you cannot immediately update the library or framework, you can provide command-line arguments to the JVM, which essentially allow the reflective access to continue without emitting the warning. However, keep in mind that this solution is more of a temporary workaround and may not be recommended in the long term.
3. Replace dependency: In some cases, the library or framework you’re using may not have a compatible version available. In such cases, you may need to consider finding an alternative library or framework that is actively maintained and supports the encapsulation introduced in JDK 9.
It’s important to note that accessing encapsulated APIs via reflective access potentially brings security risks, as the encapsulation was introduced precisely to prevent unauthorized access to internal implementation details. Therefore, it is advisable to thoroughly evaluate the security implications and consider alternative solutions before resorting to reflective access.
FAQs:
Q: Can I ignore the warning and continue without addressing it?
A: Although the warning does not prevent the execution of your code, it’s advisable not to ignore it as future Java versions or JVM implementations may introduce stricter checks that may break your code. It’s better to address the warnings as early as possible to ensure future compatibility.
Q: How can I determine which part of my code is triggering the warning?
A: The warning message usually contains a stack trace, including the class and method names involved. Analyzing the stack trace can help identify the specific part of your code that is accessing the encapsulated API. Tools like IDE debuggers or static analysis tools can also assist in locating the problematic code.
Q: Will fixing the warning cause any backward compatibility issues?
A: Resolving the warning by using proper APIs doesn’t usually cause backward compatibility issues. However, be cautious while making changes and ensure thorough testing to verify that the modifications do not introduce any regressions or unexpected behaviors.
Q: Is it safe to disable the warning completely?
A: Disabling the warning completely is not recommended, as it hides potential issues and may lead to security vulnerabilities or compatibility problems. It is advisable to address the specific instances of illegal reflective access instead of blanket disabling the warning.
In conclusion, encountering the “An illegal reflective access operation has occurred” warning in JDK 11 is an indication that your code is accessing internal APIs in an unauthorized manner. While reflective access itself is not necessarily harmful, it’s important to investigate and address the warning to avoid potential compatibility issues or security vulnerabilities. Updating dependent libraries, using command-line flags, or finding alternative solutions are some of the ways to resolve the warning and ensure future compatibility with Java and JVM environments.
How To Avoid Warning An Illegal Reflective Access Operation Has Occurred?
Introduction:
As a Java developer, you may have come across the warning message “An Illegal Reflective Access Operation has Occurred” while working on your projects. This warning occurs when your code performs a reflective access operation without appropriate access or permissions. Reflective access allows a program to inspect or modify the behavior of other classes dynamically, even if the classes involved are not part of the public API. In this article, we will explore this warning and discuss ways to avoid it in your Java projects.
Understanding Reflective Access:
Reflective access is a powerful feature that enables a Java program to analyze and modify class behavior at runtime. It provides the ability to access private members, instantiate objects, invoke methods, and perform other operations that would otherwise be inaccessible. This feature is primarily used in libraries, frameworks, and testing tools, where dynamic behavior needs to be achieved.
The Warning Message:
When an illegal reflective access operation occurs, the Java runtime environment emits a warning message as follows:
“`
WARNING: An illegal reflective access operation has occurred
WARNING: Reflective access of
WARNING: Use –illegal-access=
“`
By default, Java 9 and later versions have restricted the use of reflective access in order to enhance security. This warning message acts as a reminder that the code might be using reflective access inappropriately and needs immediate attention.
Avoiding the Warning:
To avoid the warning, there are several recommended approaches that you can follow:
1. Update the Code:
The ideal way to address the warning is to modify your code and avoid using reflective access operations whenever possible. Instead, try to utilize the public API or alternative mechanisms that are accessible without reflection. By refactoring your code, you can eliminate the need for reflective access and, hence, bypass the warning altogether.
2. Use Compatible Libraries:
If you are using third-party libraries that cause the warning, check if there are updated versions available, especially those compatible with newer Java versions. Many libraries have been updated to comply with the security restrictions imposed in Java 9 and later. By updating to a compatible version, you can ensure that the library no longer triggers the reflective access warning.
3. Enable Legal Access:
If you have no control over the code generating the warning (e.g., a third-party library), you can explicitly allow that code to use reflective access using the `–illegal-access` option. However, note that this approach should be used as a short-term solution, as it compromises the security provided by stricter access controls. To enable reflective access warnings, use the following command-line option during compilation and execution:
“`
–illegal-access=warn
“`
4. Package Configuration:
In some cases, you might need to change your module/package configurations. If you are using a modular Java project, ensure that the required modules are properly declared in the module-info.java file. The reflection-related packages should be listed under the `opens` or `opens/exports` keyword, depending on whether you want full or limited access.
FAQs:
1. Does the reflective access warning impact the functionality of my code?
No, the warning itself does not directly affect the functionality of your code. It is an informational message designed to highlight potential security risks. However, it is essential to address the warning to maintain code quality and adhere to security best practices.
2. Can I disable the warning completely?
It is recommended not to disable the warning completely, as it helps identify potential security vulnerabilities. However, if necessary, you can disable the warning using the `–illegal-access=permit` option. Remember, this is not an encouraged practice unless you have a thorough understanding of the risks involved.
3. Are there any tools available to detect and fix reflective access issues?
Yes, various static analysis tools such as IntelliJ IDEA, Eclipse, and SonarLint offer detection mechanisms to identify and resolve reflective access issues. These tools can help locate the code triggering the warning and suggest possible alternatives or fixes to avoid reflective access.
4. How important is it to address reflective access warnings?
While it is not mandatory to resolve every single reflective access warning, it is highly recommended to address them whenever possible. Ignoring these warnings could lead to unexpected runtime errors if the underlying code is modified or deprecated in future Java releases. Resolving the warnings ensures code robustness and compatibility with future versions of Java.
Conclusion:
The reflective access warning in Java indicates potential security risks and should be promptly addressed. By updating the code, using compatible libraries, enabling legal access, and configuring packages correctly, you can avoid these warnings and enhance the security and stability of your Java projects. It is crucial to follow best practices and stay updated with the latest Java releases to ensure smooth functioning and maintainable codebases.
Keywords searched by users: an illegal reflective access operation has occurred All illegal-access operations will be denied in a future release, An illegal reflective access operation has occurred intellij, An illegal reflective access operation has occurred eclipse, Illegal reflective access by org apache ibatis reflection reflector, Illegal reflective access by retrofit2 platform, Warning illegal reflective access by org apache spark unsafe platform, Illegal reflective access by org/springframework CGLIB core reflectutils, Illegal reflective access by org powermock-reflect internal whiteboximpl
Categories: Top 42 An Illegal Reflective Access Operation Has Occurred
See more here: nhanvietluanvan.com
All Illegal-Access Operations Will Be Denied In A Future Release
In our ever-advancing digital world, it is crucial to prioritize security measures to protect sensitive information and ensure the safety of online users. One key aspect of this is preventing illegal-access operations from occurring. In response to this growing concern, developers are working diligently to enhance security protocols, leading to the upcoming release of an innovative solution that promises to deny all illegal-access operations.
Illegal-access operations refer to any unauthorized attempts to breach security systems or gain access to private information. These operations may include hacking, phishing, data breaches, or any other nefarious activities that compromise the integrity of digital platforms. The consequences of illegal-access operations can be devastating, ranging from financial losses and identity theft to reputational damage and disrupted services.
To combat these issues and safeguard user information, a future release is being developed to prevent all illegal-access operations through advanced security mechanisms. This solution aims to raise the bar for digital protection, making it incredibly challenging for any unauthorized user to breach security walls and obtain unauthorized access.
The upcoming release focuses on several key areas to effectively deny illegal-access operations. First and foremost, it integrates robust encryption techniques, making it incredibly difficult for hackers to intercept and decipher sensitive data. Encryption ensures that data is converted into a code that can only be decrypted with the correct cryptographic key. Thus, even if a hacker manages to access encrypted data, they cannot decipher it without the appropriate key, rendering it useless to them.
Additionally, the future release employs multi-factor authentication (MFA) to further secure access to sensitive information. MFA requires users to provide multiple forms of verification, such as a password, fingerprint, or facial recognition, before granting access to restricted areas. This additional layer of security greatly reduces the chances of unauthorized access, as hackers would need to bypass multiple authentication methods simultaneously.
Furthermore, the solution focuses on continuously updating security measures to stay ahead of emerging threats. Developers will dedicate time and resources to monitor the ever-evolving cybersecurity landscape and adapt the release accordingly. This proactive approach ensures that the denial of illegal-access operations remains effective in the face of new attack vectors and vulnerabilities.
As this future release approaches, many users might have questions regarding its implementation and effectiveness. Here are some frequently asked questions to address common concerns:
Q: How will this future release impact my day-to-day online activities?
A: The primary goal of this release is to reinforce the security of digital platforms, ensuring the protection of user information. While there may be minor changes to the login process, the overall impact on day-to-day activities will be minimal.
Q: Will this release guarantee 100% protection against illegal-access operations?
A: While this release significantly enhances security measures, it is important to acknowledge that no system can provide absolute protection. However, it aims to raise the bar for security standards and make illegal-access operations exceedingly difficult and unlikely.
Q: Will the release be compatible with existing systems and applications?
A: Developers are working diligently to ensure compatibility with existing systems. However, in some cases, minor adjustments may be required to integrate the new security protocols seamlessly.
Q: Will this release affect the performance or speed of digital platforms?
A: Efforts are being made to minimize any impact on performance or speed. Developers understand the importance of maintaining a seamless and efficient user experience, and they are working to enhance security without compromising overall performance.
Q: How will the release address emerging and sophisticated cyber threats?
A: The developers are committed to continuously monitoring the cybersecurity landscape and adapting the release accordingly. Regular updates and security patches will be implemented to address any emerging threats and vulnerabilities effectively.
It is essential to realize that combating illegal-access operations is an ongoing process. The transparent commitment of developers to improving digital security is exemplified through this upcoming release. By integrating advanced security mechanisms, continuous updates, and proactive measures to combat emerging threats, the denial of illegal-access operations will undoubtedly prove to be an effective solution in safeguarding sensitive information.
In conclusion, as our digital world continues to evolve, the need for robust security measures cannot be overemphasized. The future release that will deny all illegal-access operations signifies a significant step towards enhancing digital security. Through encryption, multi-factor authentication, and continuous updates, this solution aims to mitigate the risks associated with illegal-access operations and ensure a safer online environment for all users.
An Illegal Reflective Access Operation Has Occurred Intellij
In this article, we will delve into the details of illegal reflective access operations, explore the reasons behind this error message, and discuss possible solutions to resolve it. Let’s dive in!
Understanding Illegal Reflective Access Operations
Java’s reflection API allows developers to examine, modify, and even invoke classes, methods, and fields at runtime. It grants powerful capabilities to access and manipulate otherwise inaccessible parts of the code. However, accessing certain restricted parts of the code using reflection is considered illegal.
When an illegal reflective access operation is encountered, it means that the code is accessing a restricted part of the codebase via reflection. Java’s access control mechanism aims to ensure encapsulation and restrict unauthorized access, but reflective operations can potentially bypass these checks, hindering the integrity and security of the code.
Reasons Behind Illegal Reflective Access Operations in IntelliJ
There can be various reasons why IntelliJ throws an illegal reflective access operation error. Some of the common causes include:
1. Java Version Compatibility: This error primarily occurs when running code written in an older version of Java on a newer Java runtime environment (JRE). Changes between Java versions can introduce restrictions or modifications to the internal structures of the Java Virtual Machine (JVM). This misalignment can trigger illegal reflective access operations.
2. Third-Party Libraries or Frameworks: If your project utilizes third-party libraries or frameworks, they may not be fully compatible with your current Java version or IntelliJ IDEA. These external dependencies may rely on reflection to access internals, leading to illegal reflective access operations.
3. IntelliJ IDEA Configuration: Occasionally, the error may arise due to some misconfiguration in your IntelliJ IDEA settings. Incorrect settings can cause conflicts and result in the illegal reflective access operation error.
Solutions to Resolve Illegal Reflective Access Operations
Now that we understand the possible causes, let’s explore some solutions to tackle the illegal reflective access operation error in IntelliJ IDEA:
1. Update JDK and IntelliJ IDEA: Ensure that you are using the latest available versions of both JDK (Java Development Kit) and IntelliJ IDEA. Updating to the latest official releases can resolve compatibility issues and address known bugs related to illegal reflective access operations.
2. Configure IntelliJ IDEA Project Settings: Navigate to your project settings in IntelliJ IDEA and make sure you have set the correct JDK version. Additionally, verify that the language level setting matches the Java version used in your project. This step ensures that IntelliJ IDEA uses the appropriate compiler settings compatible with your code.
3. Check Third-Party Dependencies: If you are using external libraries or frameworks, ensure that they are updated to a compatible version. Visit the official documentation of those dependencies and check for any recommended updates or known issues related to reflective access operations.
4. Handle Reflective Access Legitimately: In some cases, you may need to access restricted code via reflection intentionally. If that is the case, consider using APIs provided by the Java Platform Module System (JPMS) to declare dependencies explicitly. Explicit dependency declaration allows the JVM to grant access to the necessary code without triggering the illegal reflective access operation error.
Frequently Asked Questions (FAQs):
Q1. Is illegal reflective access operation an error?
Yes, an illegal reflective access operation is an error that occurs when code attempts to access restricted parts of the codebase via reflection. It violates the access control rules of Java and can potentially compromise code integrity and security.
Q2. Can I ignore the illegal reflective access operation error?
While it is possible to ignore the error, it is not recommended. Ignoring the error means allowing the code to access restricted parts of the codebase, which can lead to potential security vulnerabilities and unexpected behavior. It is advised to address the cause of the error and resolve it appropriately.
Q3. Do all reflective operations lead to illegal reflective access operations?
No, not all reflective operations lead to illegal reflective access operations. Reflective operations are legitimate and commonly used techniques in certain scenarios. It is only the illegal access to restricted parts of the codebase through reflection that results in the error.
Q4. How can I identify the source of an illegal reflective access operation error?
The error message provided by IntelliJ IDEA usually includes the stack trace and the classes involved in the illegal reflective access operation. By examining the stack trace, you can identify which part of your code or third-party library is causing the error. This information is crucial in resolving the issue effectively.
In conclusion, encountering an illegal reflective access operation error in IntelliJ IDEA can be an indication of unauthorized code access via reflection. By understanding the reasons behind this error and following the suggested solutions, you can successfully resolve the issue and ensure the integrity and security of your Java projects. Stay up-to-date with Java versions, configure IntelliJ IDEA correctly, and handle reflective access operations legitimately to avoid such errors in the future.
An Illegal Reflective Access Operation Has Occurred Eclipse
Eclipse is a popular integrated development environment (IDE) that allows developers to write, run, and debug applications efficiently. However, like any software tool, it is not immune to occasional errors and issues. One such common error that developers may encounter while using Eclipse is “An illegal reflective access operation has occurred.” In this article, we will delve into what exactly this error means, why it occurs, and how to troubleshoot it effectively.
Understanding the error:
When Eclipse encounters an illegal reflective access operation, it means that the Java Virtual Machine (JVM) is trying to access or modify a member of a class using reflection in a way that is not allowed. Reflection is a powerful feature of Java that allows programs to inspect and modify the behavior of classes, methods, and fields at runtime. However, it can also be misused due to its flexible nature, leading to this error.
Reasons for illegal reflective access operation:
1. Java version mismatch: One common reason for this error is a mismatch between the version of Java being used by Eclipse and the Java version compatibility of the project or library being used. Eclipse might be using a newer version of Java that has stricter rules for reflective access, causing compatibility issues.
2. Deprecated API usage: Eclipse may throw this error if you are using deprecated APIs that have been restricted from reflective access for security reasons.
3. Security Manager settings: If a security manager is enabled in the JVM, it can restrict reflective access operations. If the security manager configuration is not properly set, it can cause this error.
4. Access control changes: Java has implemented changes in access control rules for reflective operations in recent versions. If the code is written to rely on older access control rules, it may cause this error when run on a newer JVM.
Troubleshooting steps:
1. Check for Java version compatibility: Ensure that the Java version used by Eclipse is compatible with the project or library you are working with. Update the Java version on your machine, if necessary, and make the necessary changes in the Eclipse settings to use the updated version.
2. Library update: If the error is caused by a library, check if an updated version of the library is available that is compatible with the Java version being used.
3. Handle deprecated APIs: If the error is occurring due to the use of deprecated APIs, update your code to use the recommended alternatives instead. This will not only resolve the error but also ensure better code quality and maintainability.
4. Review security manager settings: If a security manager is enabled, review its configuration to ensure that it is not overly restrictive. Consult the Java documentation for correct settings and make necessary changes.
5. Update code for compatibility: If the error is caused by changes in access control rules, you might need to update your code to comply with the new rules. Look for APIs or methods that are no longer accessible through reflection and find alternative approaches to achieve the required functionality.
Frequently Asked Questions (FAQs):
Q1: How can I determine the Java version used by Eclipse?
A1: In Eclipse, go to “Help” -> “Eclipse Marketplace” -> “Installed” tab. You will find the Java version displayed in the list of installed software.
Q2: Can I suppress the “illegal reflective access operation” warning?
A2: Yes, but it is not recommended. You can suppress the warning by adding the argument “–add-opens” to the JVM arguments in your Eclipse Run Configuration. However, it’s advisable to resolve the issue causing the warning instead of suppressing it.
Q3: Are there any tools or plugins available to automatically fix this error?
A3: While there are no specific tools or plugins solely dedicated to fixing this error, using code analysis tools like SonarLint or IDE plugins like ErrorProne can help identify potential issues related to illegal reflective access operations in your code.
Q4: I’m encountering this error in a specific library. What can I do?
A4: Check if an updated version of the library is available, which may resolve any compatibility issues with the Java version you are using. If an update is not available, consider reaching out to the library’s maintainers for support or look for alternative libraries that are compatible with your setup.
In conclusion, encountering the “An illegal reflective access operation has occurred” error in Eclipse can be quite frustrating for developers. However, with a clear understanding of the error and following the troubleshooting steps outlined in this article, you will be well-equipped to resolve this issue effectively. Keep your Java version up to date, handle deprecated APIs properly, review security manager settings, and adapt your code as necessary for compatibility with newer JVMs. By doing so, you can ensure a smooth development experience in Eclipse.
Images related to the topic an illegal reflective access operation has occurred

Found 38 images related to an illegal reflective access operation has occurred theme














![WARNING] An illegal reflective access operation has occurred Warning] An Illegal Reflective Access Operation Has Occurred](https://user-images.githubusercontent.com/8222265/133714169-cf91ff89-a63b-4ae2-8055-3bfddffa35bb.png)
![Spring] An illegal reflective access operation has occurred 오류 해결 방법 : 네이버 블로그 Spring] An Illegal Reflective Access Operation Has Occurred 오류 해결 방법 : 네이버 블로그](https://mblogthumb-phinf.pstatic.net/MjAxOTEwMTFfOTcg/MDAxNTcwODAzMDc3Nzk2.JpVGddLpJuvrGm15haEndK8MM8rTnc__rlcoGZO9HYUg.8YzCJfLWflGd7XmRAvBjB2brqk0VBh3gao8ItfZ_FEog.PNG.10hsb04/spring-by-pivotal-9066b55828deb3c10e27e609af322c40.png?type=w800)


![JAVA] JDK 환경설정 / WARNING: An illegal reflective access operation has occurred 경고 해결 Java] Jdk 환경설정 / Warning: An Illegal Reflective Access Operation Has Occurred 경고 해결](https://img1.daumcdn.net/thumb/R800x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdn%2FbI1EFz%2Fbtrl6QckVIZ%2FmrXcXIWv8m3Y2HEtitkQZk%2Fimg.png)

















Article link: an illegal reflective access operation has occurred.
Learn more about the topic an illegal reflective access operation has occurred.
- What is an illegal reflective access? – java – Stack Overflow
- How to fix “an illegal reflective access operation has occurred”
- Transition from Java 8 to Java 11 – Azure – Microsoft Learn
- Getting warnings about “illegal reflective access operation …
- Java 9 Illegal Reflective Access Warning – Baeldung
- An Illegal Reflective Access Operation Has Occurred: Fixed
- An illegal reflective access operation has occurred when …
- How can I solve “WARNING:An illegal reflective access …
- Getting warnings about “illegal reflective access operation …
- Solved: Getting An illegal reflective access operation has…
- running under Java 11 gives “illegal reflective access” warnings
- Illegal reflective access in JDK 11 : XD-888 – YouTrack