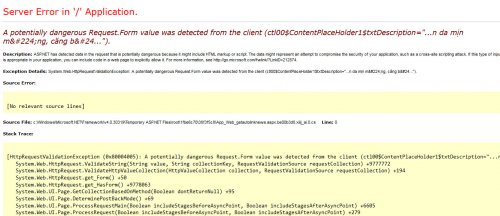
A Potentially Dangerous Request.Path Value Was Detected From The Client
1. Understanding Request.Path Value and Its Significance
The Request.Path value represents the path of the requested resource in a URL, including any virtual directory or file information. It is an essential part of the HTTP request and helps the server locate and serve the requested resource. The significance of Request.Path value lies in its role in routing user requests to the appropriate server-side application logic.
2. Identifying the Potential Risks Associated with a Dangerous Request.Path Value
A dangerous Request.Path value can pose various security risks to web applications. Malicious attackers can exploit vulnerabilities in the way web applications handle these values to execute attacks such as remote code execution, command injection, SQL injection, and cross-site scripting (XSS). By injecting malicious code into the Request.Path value, attackers can manipulate the behavior of the web application and gain unauthorized access to sensitive information.
3. Common Security Vulnerabilities Exploited through Request.Path Value
There are several common security vulnerabilities that can be exploited through the Request.Path value. These include directory traversal attacks, where attackers attempt to access files or directories outside the intended scope of the web application. Path manipulation attacks involve modifying the Request.Path value to bypass security measures and gain unauthorized access. Additionally, attackers may use encoded or obfuscated Request.Path values to evade detection and exploit vulnerabilities.
4. Impact of a Potentially Dangerous Request.Path Value on Web Applications
A potentially dangerous Request.Path value can have severe consequences for web applications. It can lead to unauthorized access to sensitive information, compromise user privacy, disrupt application functionality, and even result in server compromise. By exploiting vulnerable Request.Path values, attackers can cause financial losses, reputational damage, and legal implications for organizations.
5. Analyzing the Causes and Scope of Request.Path Value Attacks
The causes of Request.Path value attacks can be attributed to insecure coding practices, lack of input validation and sanitization, inadequate security configurations, and outdated software. The scope of these attacks can extend to various web application frameworks and technologies, such as ASP.NET WebForms, ASP.NET Web API, and other platforms where Request.Path values are used.
6. Techniques to Detect and Mitigate Request.Path Value Vulnerabilities
There are several techniques to detect and mitigate Request.Path value vulnerabilities. Implementing input validation and filtering to sanitize user input can help prevent attacks. Regularly updating and patching web applications and their dependencies can address known vulnerabilities. Employing robust logging and monitoring mechanisms can help detect and respond to suspicious Request.Path values. Additionally, implementing web application firewalls and intrusion detection systems can provide an added layer of security.
7. Best Practices to Securely Handle Request.Path Value in Web Development
To securely handle Request.Path value in web development, it is crucial to follow best practices. These include enforcing strict input validation and sanitization, limiting access to sensitive files and directories, implementing secure coding practices, using parameterized queries to prevent SQL injection attacks, and validating and encoding user-generated content to prevent XSS attacks. It is also recommended to apply security patches and updates promptly and configure security settings properly.
8. Importance of Regularly Updating and Patching Web Applications
Regularly updating and patching web applications is vital to address vulnerabilities and protect against Request.Path value attacks. Developers should stay informed about the latest security updates and patches released by vendors and promptly apply them to all web applications. Failure to update and patch web applications exposes them to known vulnerabilities and increases the risk of exploitation.
9. Educating Developers and Webmasters on Request.Path Value Security
Educating developers and webmasters on Request.Path value security is crucial in fostering a proactive security culture. Training programs and resources should emphasize secure coding practices, input validation techniques, and the best practices for handling Request.Path values. Developers and webmasters need to be aware of common attack vectors, understand the potential risks associated with unprotected Request.Path values, and have the necessary skills to detect and mitigate vulnerabilities.
10. Evaluating the Role of Web Application Firewalls in Preventing Request.Path Value Attacks
Web application firewalls (WAFs) play an important role in preventing Request.Path value attacks. WAFs can inspect and filter incoming requests, blocking malicious traffic that may contain dangerous Request.Path values. By implementing a WAF, organizations can add an additional layer of protection to their web applications and detect and block potential attacks in real-time.
In conclusion, a potentially dangerous Request.Path value can pose significant risks to web applications if not properly handled. It is essential for developers, webmasters, and organizations to understand these risks and implement effective security measures to prevent attacks. By following best practices, regularly updating and patching web applications, and leveraging tools like web application firewalls, organizations can enhance the security of their web applications and protect against potential threats.
FAQs:
Q: What is a Request.Path value?
A: Request.Path value represents the path of the requested resource in a URL, including any virtual directory or file information.
Q: What are the risks associated with a dangerous Request.Path value?
A: A dangerous Request.Path value can be exploited to execute attacks such as remote code execution, command injection, SQL injection, and cross-site scripting (XSS).
Q: How can web applications handle Request.Path value securely?
A: Web applications can handle Request.Path value securely by enforcing strict input validation and sanitization, limiting access to sensitive files and directories, and implementing secure coding practices.
Q: Why is it important to regularly update and patch web applications?
A: Regularly updating and patching web applications is crucial to address vulnerabilities and protect against known exploits.
Q: What is the role of a Web Application Firewall (WAF) in preventing Request.Path value attacks?
A: Web Application Firewalls can inspect and filter incoming requests, blocking malicious traffic that may contain dangerous Request.Path values, thus providing an additional layer of protection to web applications.
Fix: Potentially Dangerous Request Form Value Was Detected From The Client
What Does A Potentially Dangerous Request Path Value Was Detected From The Client Bypass?
Introduction:
In today’s digital landscape, ensuring web application security is of utmost importance to protect sensitive information and prevent unauthorized access. One commonly observed security vulnerability is the bypass of potentially dangerous request path value detection. In this article, we delve into the intricacies of this vulnerability, its implications, and ways to mitigate it.
1. What is a Potentially Dangerous Request Path Value?
A Potentially Dangerous Request Path Value refers to a user-supplied input received by a web application through the URL path. This input may include special characters or encoded data that could potentially pose a security risk, such as SQL injection, cross-site scripting (XSS), or directory traversal attacks.
2. How is Potentially Dangerous Request Path Value Detected?
Web frameworks and servers often include security mechanisms to detect and defend against potentially dangerous request path values. These mechanisms analyze the requested URL path for suspicious patterns, special characters, and encoded data. Upon detection, they raise an exception or block the request to prevent possible exploits.
3. What is a Potentially Dangerous Request Path Value Detection Bypass?
A Potentially Dangerous Request Path Value Detection Bypass occurs when an attacker successfully circumvents the security mechanisms intended to detect and block potentially dangerous request path values. Through various techniques, an attacker can manipulate the URL path to bypass detection mechanisms, allowing the execution of malicious code or unauthorized access.
4. Techniques used for Bypassing Detection:
a. URL Encoding: Attackers often encode malicious characters or payloads using various encoding techniques to make them appear benign. By doing so, they can evade detection and successfully inject malicious code or perform other nefarious activities.
b. Double URL Encoding: Attackers leverage the concept of double URL encoding, where they encode the injected payload twice to further obfuscate the malicious intent. This technique can confuse detection mechanisms and allow attackers to slip past security measures.
c. Alternative Encodings: Attackers may employ alternative encodings, such as hexadecimal or Unicode, to disguise payloads and evade detection. These encodings can bypass traditional security filters that target common encodings, increasing the chances of a successful bypass.
d. Obfuscation: Attackers may use obfuscation techniques to hide malicious code within valid requests. By employing techniques like character substitution, white-space padding, or using different file extensions, they can masquerade the request path value as legitimate and bypass detection mechanisms.
5. Implications of a Potentially Dangerous Request Path Value Detection Bypass:
When an attacker successfully bypasses the detection mechanisms, it exposes the web application to various security risks, including:
a. Injection Attacks: Potentially dangerous request path values may enable SQL injection attacks, allowing attackers to manipulate or extract data from the application’s underlying databases.
b. Cross-Site Scripting (XSS): By exploiting a bypass, attackers can inject malicious scripts into web pages, compromising users’ browsers and potentially stealing sensitive information such as login credentials or session tokens.
c. Directory Traversal: A successful bypass can facilitate the traversal of directory boundaries, allowing attackers to access confidential files outside of the application’s designated boundaries. This could lead to exposure of sensitive data or unauthorized access to critical resources.
Mitigation Strategies:
To mitigate the risks associated with a Potentially Dangerous Request Path Value Detection Bypass, consider implementing the following security measures:
a. Input Validation: Implement robust input validation techniques and enforce strict restrictions on user-supplied input. Validate and sanitize URL path values before processing them.
b. Encoded Data Handling: Decode and normalize URL-encoded data to ensure consistency and accurate detection. Implement a comprehensive decoding mechanism that can handle multiple encodings.
c. Security Awareness: Educate developers about the risks and vulnerabilities associated with request path values. Provide training on secure coding practices and encourage regular security assessments.
d. Web Application Firewall (WAF): Utilize a WAF to monitor and block potentially dangerous requests. Configure the WAF to detect patterns and known attack signatures associated with request path value bypasses.
FAQs:
Q1. How can I prevent bypass of potentially dangerous request path value detection in my web application?
A1. Implementing input validation, handling encoded data properly, and utilizing a Web Application Firewall (WAF) are effective measures to prevent bypass of potentially dangerous request path value detection.
Q2. Is URL encoding sufficient to protect against bypass attacks?
A2. No, URL encoding alone is not sufficient. Attackers can employ techniques like double URL encoding, alternative encodings, or obfuscation, requiring additional security measures such as decoding and normalization of URL-encoded data.
Q3. What can be the consequences of a successful bypass?
A3. The consequences vary but can include injection attacks (e.g., SQLi), cross-site scripting (XSS), and unauthorized access via directory traversal. These can lead to data breaches, compromised user sessions, or exposure of critical resources.
Q4. How often should I conduct security assessments for request path value detection bypass vulnerabilities?
A4. Regular security assessments are recommended to identify potential vulnerabilities. Conduct assessments during the development phase and periodically thereafter to ensure ongoing protection against these attacks.
Conclusion:
Understanding the nature and consequences of a Potentially Dangerous Request Path Value Detection Bypass is crucial to maintaining a secure web application. By implementing appropriate security measures, regularly assessing vulnerabilities, and staying abreast of emerging bypass techniques, developers and organizations can safeguard their web applications from potential exploits and mitigate associated risks.
What Is A Potentially Dangerous Request Path Value Was Detected From The Client Sitecore?
Sitecore is a powerful content management system (CMS) that allows website administrators to create and manage digital content. However, like any other software, it has its own set of vulnerabilities. One common issue that Sitecore users may encounter is the “Potentially dangerous request path value was detected from the client” error message.
This error is a security feature implemented by Sitecore to protect against potential cross-site scripting (XSS) attacks. XSS attacks occur when an attacker injects malicious code into a website that is viewed by other users, leading to potential data breaches or unauthorized access. Sitecore, by default, restricts the use of certain characters and values in request paths to mitigate this risk.
When Sitecore detects a request path value that it deems potentially dangerous, it triggers this error message and prevents the request from being executed. The purpose of this feature is to ensure that only safe and valid requests are allowed to access the system, protecting it from potential security threats.
Understanding the Error Message:
The error message “Potentially dangerous request path value was detected from the client” may seem intimidating or confusing to Sitecore users who are encountering it for the first time. However, it is crucial to understand the reasons behind this error and how to handle it properly.
1. What causes the error?
The error occurs when the request path value sent by the client contains characters or values that are restricted by Sitecore. These may include special characters, HTML tags, or any other potentially risky content.
2. How does Sitecore determine if a request path value is potentially dangerous?
Sitecore uses a predefined set of rules to identify potentially dangerous values. This set of rules is based on industry best practices and common security vulnerabilities. If the request path value violates any of these rules, Sitecore triggers the error message.
3. Is this error specific to Sitecore?
No, this error message is not unique to Sitecore. Many other CMS platforms and web applications implement similar security measures to protect against potential XSS attacks. It is a common best practice to restrict potentially dangerous values in request paths.
Handling the Error:
Encountering the “Potentially dangerous request path value was detected from the client” error does not necessarily mean that your Sitecore instance is compromised or that there is a security breach. It simply indicates that the request path value being sent to the system may pose a security risk.
To handle this error effectively, consider the following steps:
1. Evaluate the request path value: Review the request path value causing the error and identify any potentially dangerous characters or values. Ensure that these are not indicative of any suspicious activity or malicious intent.
2. Investigate the source: If the error persists or if you suspect that the request path value is being generated by a malicious user or script, investigate the source and take appropriate action. This may involve blocking the IP address, disabling the incorrect feature, or applying additional security measures.
3. Sanitize input or encode the request path value: To prevent this error from occurring in the future, ensure that the request path value is properly sanitized or encoded to eliminate any potentially dangerous content. This can be achieved by applying input validation or using encoding techniques.
FAQs:
Q1. Can I disable this security feature in Sitecore?
While it is technically possible to disable the “Potentially dangerous request path value” feature in Sitecore, it is strongly discouraged. This security feature exists to protect your instance from potential XSS attacks and disabling it would leave your system vulnerable. It is recommended to handle the error correctly instead of disabling the feature.
Q2. How can I identify the specific character causing the error?
Sitecore does not provide explicit information about the specific character causing the error in the default error message. However, by analyzing the request path value, you can scrutinize the input for potentially dangerous characters or patterns. Additionally, you can enable Sitecore logging and review the logs to gain more insights into the error.
Q3. Can this error be encountered by end-users or only during development?
This error can be encountered by both end-users and developers. In the development phase, it is common to test the system with different inputs, which may trigger the error. However, end-users can also encounter this error if they unknowingly input restricted characters or values in the website’s URL.
Conclusion:
The “Potentially dangerous request path value was detected from the client” error in Sitecore is a security feature aimed at protecting the CMS from potential XSS attacks. While encountering this error can be frustrating, it is essential to understand its purpose and handle it appropriately. By evaluating the request path value, investigating the source if necessary, and taking steps to sanitize the input or encode it correctly, Sitecore users can effectively mitigate the risk of potential security breaches. Remember, it is crucial to prioritize security over convenience and not to disable this security feature.
Keywords searched by users: a potentially dangerous request.path value was detected from the client A potentially dangerous Request form value was detected from the client, A potentially dangerous Request form value was detected from the client asp net webforms, requestPathInvalidCharacters, potentially dangerous path variables 172180, a potentially dangerous request form value was detected from the client web api, a potentially dangerous request form value was detected from the client asmx
Categories: Top 17 A Potentially Dangerous Request.Path Value Was Detected From The Client
See more here: nhanvietluanvan.com
A Potentially Dangerous Request Form Value Was Detected From The Client
Security is a top priority when it comes to technology and online platforms. In today’s digital landscape, where cyber attacks and data breaches are on the rise, it’s crucial for developers and website administrators to be vigilant and proactive in protecting their systems. One form of threat that often goes unnoticed is a potentially dangerous request form value from the client.
When a user interacts with a website, they often submit data through various forms, such as login pages, contact forms, or search fields. These forms allow users to input their information and send it to the server for processing. However, there are instances when an input received from the client can be potentially dangerous and pose a threat to the website’s security.
A potentially dangerous request form value occurs when a user intentionally or unintentionally inputs malicious code or harmful data into a form field. This can include SQL injection attempts, cross-site scripting (XSS) attacks, or other malicious activities that can exploit vulnerabilities or compromise the server’s security.
The detection of such dangerous requests is crucial to prevent the execution of these harmful actions. Most modern web frameworks and platforms have built-in security measures that analyze incoming data for potential threats. When a potentially dangerous request form value is detected, the server can take preventive actions such as rejecting the request, sanitizing the input, or notifying the website administrator.
To understand the gravity of this form of threat, let’s discuss some common forms of potentially dangerous request values:
1. SQL Injection: This occurs when an attacker inserts SQL statements into a form field, manipulating the database and potentially gaining unauthorized access to sensitive data. By injecting additional SQL commands, an attacker can modify or delete data, bypass authentication, or even execute system commands.
2. Cross-Site Scripting (XSS): This type of attack involves injecting malicious scripts into a form field. When the server renders the data back to the user, the script is executed, allowing the attacker to steal sensitive information or gain unauthorized access to user accounts.
3. File Upload Attacks: Attackers can exploit file upload forms to execute unauthorized scripts or upload malicious files to a server. For example, an attacker might upload a file containing a virus or malware, which can then be executed when accessed by other users.
These are just a few examples of the potentially dangerous request form values that can put websites at risk. Web developers and administrators should implement thorough security measures to defend against these threats.
Frequently Asked Questions (FAQs):
Q: How can potentially dangerous request form values be detected?
A: Most web frameworks and platforms have built-in security features that analyze incoming data for potential threats. These features often include input validation and sanitization, as well as filters and firewalls that can detect and block malicious code or potentially harmful requests.
Q: How can website administrators protect their systems from these threats?
A: There are several steps website administrators can take to protect their systems. Implementing secure coding practices, such as input validation and output encoding, can help prevent malicious code injection. Regularly updating and patching web frameworks, plugins, and server software can also reduce the risk of exploitation. Web Application Firewalls (WAFs) can provide an additional layer of protection by monitoring and filtering incoming traffic for potential threats.
Q: What should I do if a potentially dangerous request form value is detected on my website?
A: If a potentially dangerous request form value is detected, it’s essential to take immediate action. First, investigate the incident to understand the nature of the threat and assess the potential damage. Remove the malicious code or harmful data and sanitize the affected form field. Analyze your server logs to identify possible vulnerabilities and address them promptly. Finally, consider notifying affected users and providing guidance on securing their accounts if necessary.
Q: Can users protect themselves from being victims of these attacks?
A: While users may not have control over the security measures implemented on the websites they interact with, there are precautions they can take. Using strong, unique passwords for each online account, enabling two-factor authentication, and regularly updating their devices and software can help protect against potential attacks. It’s also essential for users to be cautious when submitting personal information or interacting with unfamiliar websites.
In conclusion, a potentially dangerous request form value from the client can pose a serious threat to the security of a website. Developers and administrators should implement robust security measures and continuously monitor incoming data to protect against these types of attacks. By staying vigilant and proactive, we can ensure safer and more secure digital experiences for users worldwide.
A Potentially Dangerous Request Form Value Was Detected From The Client Asp Net Webforms
Introduction:
ASP.NET Web Forms, a widely-used framework for building web applications, provides a rich set of controls that make it easy to develop interactive and responsive websites. However, like any technology, there are potential vulnerabilities that developers need to be aware of and address.
One such vulnerability is the potential danger posed by a Request.Form value detected from the client. This article aims to delve deep into this issue, discussing the risks involved and offering ways to mitigate them.
Understanding the Risk:
When a potentially dangerous Request.Form value is detected from the client, it means that the server has identified input that could potentially harm the application or its users. This detection is done by scrutinizing the input for potentially harmful content, such as script tags or SQL injection attempts.
This vulnerability can be exploited by attackers to perform various malicious activities, such as executing arbitrary code on the server, stealing sensitive information, or perpetrating cross-site scripting (XSS) attacks.
The risks associated with a potentially dangerous Request.Form value are not to be taken lightly. Unmitigated, they can lead to serious consequences, including unauthorized access to sensitive data, compromised user accounts, or even a complete system compromise.
Mitigating the Risk:
Thankfully, there are several steps developers can take to mitigate the risk associated with a potentially dangerous Request.Form value. Here are some best practices to follow:
1. Input Validation:
Ensure that all input received from clients is validated thoroughly. Use server-side validation techniques such as regular expressions, input length checks, and input type checking. By validating inputs, you can prevent malicious code or harmful content from being executed or injected into your application.
2. Encoding:
Always encode any user-provided input before rendering it back to the user. This helps to prevent XSS attacks by neutralizing any potentially dangerous characters or scripts. ASP.NET Web Forms provides built-in encoding mechanisms to simplify this process.
3. Parameterized Queries:
When dealing with databases, use parameterized queries or stored procedures instead of concatenating user-provided input directly into SQL statements. This practice eliminates the risk of SQL injection attacks, as the input is treated as data and not as part of the SQL command.
4. Request Validation:
Enforce request validation at the application level. ASP.NET Web Forms provides request validation by default, which rejects potentially harmful input. However, it’s advisable to double-check and ensure that request validation is enabled in your application’s configuration.
5. Input Sanitization:
Apply input sanitization techniques to remove or neutralize potentially dangerous characters or scripts from user input. This can be achieved by using libraries or frameworks specifically designed for this purpose.
6. Use Proper Error Handling:
Implement proper error handling and logging mechanisms to avoid displaying sensitive information to users. Error messages should be generic and not disclose underlying system or application details.
FAQs:
Q: What is ASP.NET Web Forms?
A: ASP.NET Web Forms is a framework developed by Microsoft that enables the creation of dynamic and interactive web applications. It provides a model-driven approach for building web pages and simplifies the development process by abstracting away low-level details.
Q: How does a potentially dangerous Request.Form value pose a risk?
A: A potentially dangerous Request.Form value can allow attackers to inject malicious code into an application or perform unauthorized actions. This can lead to security breaches, data leakage, or other harmful consequences.
Q: Can’t client-side validation alone mitigate the risk?
A: Client-side validation can provide a better user experience by catching potential errors early. However, it is essential to perform server-side validation to ensure the security and integrity of the application. Client-side validation can be bypassed or manipulated, making it unreliable as the sole line of defense.
Q: Are there any tools available to help with vulnerability scanning and mitigation?
A: Yes, several commercial and open-source tools are available for vulnerability scanning, such as Nessus, Burp Suite, and OWASP ZAP. These tools can help identify potential vulnerabilities in your application and suggest mitigation steps.
Q: Is it essential to keep up with the latest security patches and updates?
A: Yes, regularly updating your ASP.NET Web Forms framework, libraries, and dependencies is crucial. Security patches often include fixes for known vulnerabilities that may be present in previous versions. Staying up to date with patches and updates ensures that you have the latest security measures in place.
Conclusion:
A potentially dangerous Request.Form value detected from the client in ASP.NET Web Forms can pose serious risks to the security and integrity of an application, leaving it vulnerable to various types of attacks. However, by following best practices such as input validation, encoding, parameterized queries, and input sanitization, developers can significantly minimize the risk of exploitation.
It’s crucial to remain vigilant, stay updated on the latest security practices, and use tools to scan for vulnerabilities regularly. By doing so, developers can ensure that their ASP.NET Web Forms applications are robust, secure, and protect user data effectively.
Images related to the topic a potentially dangerous request.path value was detected from the client

Found 5 images related to a potentially dangerous request.path value was detected from the client theme








Article link: a potentially dangerous request.path value was detected from the client.
Learn more about the topic a potentially dangerous request.path value was detected from the client.
- A potentially dangerous Request.Path value was detected …
- A potentially dangerous Request.Path value … – Microsoft Learn
- “A potentially dangerous Request.Path value was detected …
- “A potentially dangerous Request.Path value was detected …
- Message: A potentially dangerous Request.Path value was …
- ASP.Net Error: A potentially dangerous Request.Form value …
- A potentially dangerous Request.Path value … – OutSystems
- Message: A potentially dangerous Request.Path value was …
- [ASPNET] Fix A potentially dangerous Request.Path value …
- System.Web.HttpException: A potentially dangerous Request …
- Potentially dangerous Request.Path value was detected
- A potentially dangerous Request.Path … – Mandarina Duck
- “A potentially dangerous Request.Path value was detected …
See more: nhanvietluanvan.com/luat-hoc