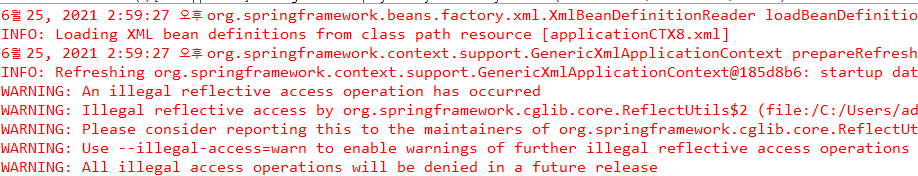
Warning: An Illegal Reflective Access Operation Has Occurred
In the world of Java programming, one might come across a warning message that says, “Warning: An illegal reflective access operation has occurred.” This warning can be a cause for concern for developers, as it indicates that the code is attempting to perform an operation that goes against the conventions and rules of Java programming. In this article, we will dive into the concept of illegal reflective access operations, understand why they occur, and explore best practices for handling them.
What is an Illegal Reflective Access Operation?
To understand illegal reflective access operations, we must first understand reflection in Java. Reflection is a powerful feature of Java that allows developers to inspect and manipulate code at runtime. It enables the retrieval of class information, method invocations, and field modifications dynamically.
An illegal reflective access operation occurs when a piece of code attempts to access or modify a private or protected member of a class, outside the scope of its normal usage permissions. This can be achieved by bypassing the usual Java programming conventions and accessing private or protected members directly through reflection.
Why Does an Illegal Reflective Access Operation Occur?
Illegal reflective access operations occur due to various reasons. One common reason is when libraries or frameworks use reflection to access internal APIs or classes that are not meant to be accessed by external code. These libraries may be using older versions of Java that allowed such access, but newer versions restrict it.
Another reason for reflective access warnings is when code interacts with external libraries or dependencies that use reflection internally. These libraries might be obsolete or need to be updated to comply with the latest Java standards.
Understanding Reflection
Reflection allows developers to examine the structure, behavior, and state of objects or classes dynamically. It provides the ability to access private or protected members that are otherwise inaccessible. While reflection can be a powerful tool, it should be used with caution, as it can lead to code that is difficult to understand and maintain.
The Concept of Reflective Access
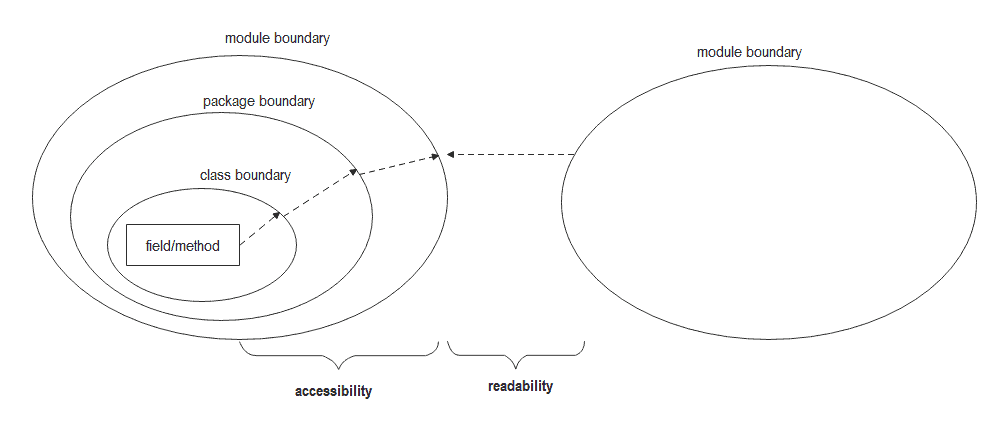
In Java programming, reflective access refers to the ability to access or modify private or protected members of a class through reflection. It provides a way to break encapsulation and access parts of the code that are not meant to be accessed by external entities.
The Java Reflection API
The Java Reflection API is a collection of classes and interfaces that provide the ability to perform reflective operations in Java. It allows developers to retrieve class information, examine and modify fields, invoke methods, and create new objects dynamically. The Reflection API is powerful but should be used judiciously to avoid security vulnerabilities and maintain code readability.
The Purpose of Reflection in Java
Reflection serves various purposes in Java programming. It enables the creation of powerful tools like debuggers, profilers, and code generators that can work with any Java code dynamically. It also allows frameworks and libraries to provide flexible and extensible solutions by adapting to the needs of different applications dynamically. Additionally, frameworks like Spring heavily rely on reflection for dependency injection and component scanning.
Why Does Java Provide Reflection?
Java provides reflection as a feature to cater to the need for dynamic programming and to provide flexibility to developers. It allows developers to extend the capabilities of the language by providing access to private and protected members that are otherwise inaccessible. However, the unrestricted use of reflection can lead to security vulnerabilities and code that is difficult to understand and maintain.
Common Causes of Illegal Reflective Access Operations
There are several common causes that can lead to illegal reflective access operations. Let’s explore some of them:
1. Using outdated libraries or frameworks: Older versions of libraries or frameworks may use reflection to access APIs that are restricted in newer versions of Java. Updating these dependencies to their latest versions can resolve the issue.
2. Accessing internal APIs: Some libraries or frameworks may attempt to access internal APIs or implementation details using reflection. This is not recommended, as it relies on undocumented behavior and can break in newer versions of Java.
3. Using deprecated or obsolete code: Deprecated or obsolete code may rely on reflection to access internal APIs. Replacing such code with newer alternatives can help prevent illegal reflective access warnings.
How to Handle Illegal Reflective Access Operations
Handling illegal reflective access operations involves addressing the root causes and taking appropriate actions. Here are some steps to handle such operations:
1. Update dependencies: Ensure that all dependencies, libraries, and frameworks used in your project are up to date. Updating to the latest versions can help avoid compatibility issues and illegal reflective access operations.
2. Avoid obsolete or deprecated code: Identify and replace any deprecated or obsolete code in your codebase. This will reduce reliance on reflective access to internal APIs and improve compatibility with newer versions of Java.
3. Configure the Java runtime environment: In some cases, it might be necessary to configure the Java runtime environment to allow reflective access to specific APIs. However, this should only be done after careful consideration, as it can introduce security risks.
Best Practices for Using Reflection in Java
While reflection can be a powerful tool, it should be used sparingly and judiciously. Here are some best practices for using reflection in Java:
1. Limit the use of reflection: Whenever possible, avoid using reflection and favor conventional programming techniques. Reflection should be used sparingly and only when there is a compelling reason to do so.
2. Understand the performance implications: Reflection can have significant performance overhead compared to direct method or field access. Use reflection judiciously and consider the performance impact on your application.
3. Avoid breaking encapsulation: Reflection allows access to private and protected members, breaking encapsulation rules. Make sure to only use reflection to access or modify members when there is a valid reason, and consider whether alternative approaches are available.
4. Be mindful of security risks: Reflective access circumvents access restrictions, so it’s important to be cautious of potential security vulnerabilities. Do not expose sensitive information or grant reflective access to untrusted code.
Frequently Asked Questions (FAQs):
Q: What does the warning “All illegal-access operations will be denied in a future release” mean?
A: This warning indicates that the code is utilizing reflective access operations that will be disallowed in future versions of Java. It serves as a reminder to update and adapt the code to comply with the upcoming changes.
Q: How do I resolve the “An illegal reflective access operation has occurred” warning in IntelliJ?
A: To resolve this warning in IntelliJ, you can update the dependencies to their latest versions or modify the IntelliJ IDEA settings to suppress the warning if it is deemed noncritical.
Q: Why do I see “Illegal reflective access by org/apache/spark/unsafe/platform” warning?
A: This warning is related to Apache Spark and indicates that the code is using reflective access operations that go against the latest Java standards. Updating the version of Spark or modifying the code to avoid reflective access can resolve this warning.
Q: What should I do if I encounter the warning “An illegal reflective access operation has occurred” in Eclipse?
A: To handle this warning in Eclipse, ensure that the project’s dependencies are up to date, and make any necessary updates to code that interacts with deprecated or obsolete libraries or APIs.
Q: How can I resolve the “Illegal reflective access by retrofit2.platform” warning?
A: This warning is related to the Retrofit library and suggests that the code is using reflective access operations that violate Java conventions. Ensure that you are using the latest version of Retrofit, as newer versions may address this warning.
Q: What does the warning “Illegal reflective access by org/apache/ibatis/reflection/reflector” mean?
A: This warning implies that the code is using reflective access to restricted APIs from the Apache iBATIS Reflection package. Check for updated versions of the library or consider alternative solutions that do not rely on reflective access.
Q: How do I handle the warning “Illegal reflective access by org.springframework.cglib.core.ReflectUtils”?
A: This warning points to the usage of reflective access operations by the Spring Framework’s CGLIB library. Updating the Spring Framework to the latest version may resolve this warning.
Q: Why am I seeing the warning “Illegal reflective access by net.sf.jasperreports.engine.util.ClassUtils”?
A: This warning indicates that the code is attempting reflective access that is no longer allowed. Ensure that you are using an updated version of the JasperReports library to address this warning.
In conclusion, the warning “An illegal reflective access operation has occurred” serves as a reminder to Java developers that their code is attempting to access or modify members in a way that violates Java conventions and might not be supported in the future. By understanding the concept of reflective access, identifying the causes of illegal reflective access operations, and following best practices for using reflection in Java, developers can address these warnings, improve code quality, and ensure compatibility with future versions of the Java platform.
Why Groovy Shows Warning \”An Illegal Reflective Access Operation Has Occurred\” When I Use Jdk11?
How To Avoid Warning An Illegal Reflective Access Operation Has Occurred?
Java programming language provides numerous powerful features, including reflection, which allows a program to analyze and manipulate its own structure at runtime. While reflection can greatly enhance the flexibility and adaptability of Java programs, it can sometimes lead to warnings such as “Illegal Reflective Access Operation Has Occurred.” This warning indicates that a reflective operation attempted to access a module, package, or class that it should not access, violating the rules of the Java module system. In this article, we will explore how to avoid this warning, understand its causes, and provide practical solutions.
Understanding the Causes of the Warning:
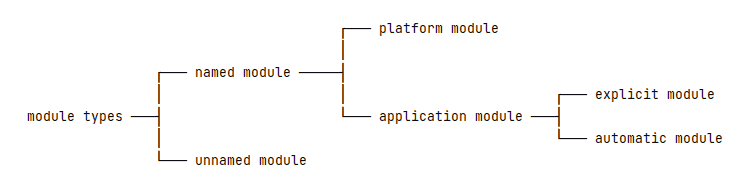
The reflective access warning emerged with the introduction of the Java Platform Module System (JPMS) in Java 9. JPMS introduced a significant change in how Java applications are organized and executed by enforcing strong encapsulation of modules. Previously, anyone could access any internal member of a class, but with JPMS, modules could explicitly export certain packages for other modules to access via reflection.
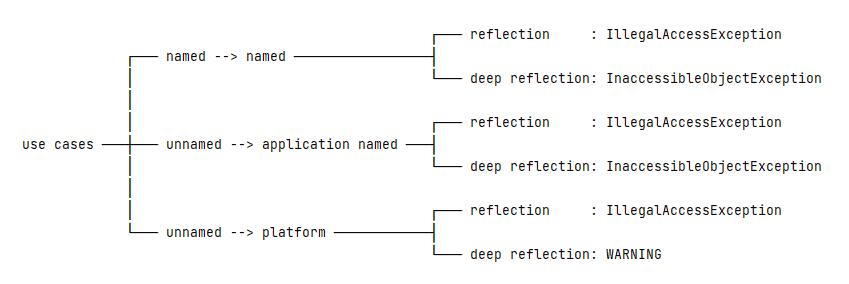
Java checks if reflective operations adhere to the module boundaries and issues a warning if a violation occurs. This warning highlights potential security, reliability, and maintainability issues in the application. It is essential to understand the causes of these warnings to effectively mitigate them.
Potential causes of the “Illegal Reflective Access Operation Has Occurred” warning include:
1. Attempting to access restricted packages or classes that are not exported by modules.
2. Using deprecated or removed APIs, which are no longer supported by Java.
3. Running a Java application with an older version of the Java runtime that lacks the module system.
Now that we’re familiar with the causes, let’s delve into practical solutions to avoid this warning:
1. Updating Dependencies:
If you encounter this warning while using a third-party library, first check if a newer version of the library is available. The library may have been updated to be compliant with the JPMS, resolving the reflective access issue.
2. Using java.lang.reflect Module:
Java provides a module called java.lang.reflect that allows reflective access to any module, regardless of the encapsulation rules. However, using this module should be done carefully, as it undermines the security and encapsulation features of the module system. Consider this solution only if you have no alternative and thoroughly understand the potential implications.
3. Obtaining Access through the Module System:
When using reflection, you can request access to non-public members through the Module System API. This mechanism allows you to obtain access with proper checks and without triggering the reflective access warning.
We can use the following code snippet as an example to obtain the access:
“`
Module myModule = MyClass.class.getModule();
myModule.addReads(targetModule);
“`
The code snippet first retrieves the module of the class that requires access and then adds a “reads” edge to the target module, allowing reflective access without triggering the warning.
FAQs:
1. Is it safe to ignore the “Illegal Reflective Access Operation Has Occurred” warning?
Ignoring the warning should be avoided as it often indicates a violation of the encapsulation rules and can lead to security vulnerabilities or compatibility issues when running the application on different Java runtimes. The warning should always be addressed by making the necessary changes to the code.
2. How can I identify the specific reflective operation causing the warning?
Java provides a command-line option, “–illegal-access=debug,” which provides additional debugging information for reflective access operations. By enabling this option, you can identify the exact location where the reflective access occurs and subsequently resolve it.
3. Can I disable the warning completely?
While it is possible to suppress the warning by using the “–illegal-access=deny” flag when running the application, it is generally not recommended. This option disallows all illegal reflective access operations, including those benign ones that might have been used for valid reasons. It’s preferable to address the root cause of the warning instead.
4. Are all warnings about reflective access operations problematic?
Not all reflective access warnings are problematic. Some warnings may be benign if they occur within the internal Java libraries or when using deprecated APIs. However, it is essential to analyze and understand the context of the warning to determine its severity and whether it requires action.
In conclusion, encountering the “Illegal Reflective Access Operation Has Occurred” warning can be resolved by understanding its causes and applying appropriate solutions. Ensuring code compliance with the Java Platform Module System, updating dependencies, and using the Java Module System API to obtain access are effective ways to avoid this warning. By addressing the warning, you enhance the security, reliability, and compatibility of your Java applications.
What Is Jdk 11 Warning An Illegal Reflective Access Operation Has Occurred?
With the release of JDK 9, the Java Development Kit introduced stricter access controls known as JEP 260. These controls aim to improve the security and stability of Java applications by limiting illegal access to internal APIs. As a result, in JDK 11, users may encounter warnings called “illegal reflective access operation has occurred” when running their Java applications.
The warning message indicates that a certain part of the code is attempting to access an internal API through reflection, which is now considered illegal. Reflection is a powerful mechanism in Java that allows the program to inspect and modify its own structure. However, it can also be misused and compromise the integrity of the system.
In previous versions of Java, developers had unrestricted access to internal APIs. This meant that they could use them without any restrictions, even though they were not intended for public use. However, such unrestricted access poses security risks and can lead to unpredictable behavior in the application.
To address these concerns, JDK 9 implemented a more secure approach by encapsulating internal APIs and limiting access to only the Java platform itself. JDK 11, and subsequent versions, enforce these access restrictions, resulting in the warning message when reflective access to internal APIs is detected.
Why was this change made?
The change was made to improve the security and stability of Java applications. By limiting access to internal APIs, developers are encouraged to use the public APIs that are officially supported and documented. This helps ensure that applications are built on a solid foundation and reduces the risk of security vulnerabilities and unexpected behavior.
Encapsulating and restricting access to internal APIs also enables the Java Development Kit to evolve more easily. Since internal APIs are not intended for public use, they can be modified or even removed in future releases without affecting the backward compatibility of applications that rely on them. This flexibility allows for efficient improvements and refinements to the Java platform over time.
How does the warning affect my application?
The warning itself does not necessarily indicate an error or a problem with your application. It serves as a notification that reflective access to internal APIs is occurring, which may have been unintentional or may indicate a design flaw.
However, it is important to note that relying on internal APIs is not recommended as they are subject to change or removal in future JDK releases. If your application heavily relies on internal APIs, it may not be compatible with future versions of Java. It is highly recommended to review and modify your codebase to use public APIs instead.
How can I fix the warning?
To address the warning, the recommended approach is to refactor your code to avoid reflective access to internal APIs. This means identifying the parts of your code that trigger the warning and finding alternative ways to achieve the desired behavior using the public APIs provided.
In some cases, the warning can be resolved by updating your code to use the recommended public APIs instead of relying on internal APIs. This approach ensures that your application remains compatible with future JDK versions and reduces the potential security risks.
However, in certain situations, alternative options may not be available or practical. If you find that reflective access to internal APIs is necessary for your application, you can suppress the warning by adding the command line argument `–add-opens
It is important to balance the convenience of reflective access with the long-term compatibility and security of your application. It is advisable to consult the official documentation, release notes, and mailing lists of the JDK to stay updated on the recommended practices and alternatives to using internal APIs.
In conclusion, the JDK 11 warning “an illegal reflective access operation has occurred” is a result of enhanced security measures implemented by JDK 9 to limit access to internal APIs. While it may initially cause some inconvenience, it ultimately contributes to the security and stability of Java applications. Developers are encouraged to review and modify their codebase to rely on public APIs instead of internal ones to ensure compatibility with future JDK versions and maintain the integrity of their applications.
FAQs:
Q: Will my Java application stop working if I see this warning?
A: No, the warning itself does not imply that your application will stop working. However, relying on internal APIs may cause compatibility issues in future JDK versions. It is recommended to refactor your code to use public APIs.
Q: Can I completely ignore the warning and continue using internal APIs?
A: While it is possible to suppress the warning, it is not advisable to rely on internal APIs. They may change or be removed in future JDK releases, which can lead to unexpected behavior or security vulnerabilities in your application.
Q: How can I find which part of my code is causing the warning?
A: The warning message includes the stack trace, which indicates the exact location in your code where the illegal reflective access operation occurs. Checking the stack trace can help you identify the problematic code.
Q: Is there a tool to automatically refactor my code to use public APIs?
A: There are tools and IDE plugins available that can assist with the refactoring process. However, manual review and modification of the codebase are often required to ensure the desired behavior and maintain the integrity of the application.
Keywords searched by users: warning: an illegal reflective access operation has occurred All illegal-access operations will be denied in a future release, An illegal reflective access operation has occurred intellij, An illegal reflective access operation has occurred eclipse, Illegal reflective access by retrofit2 platform, Warning illegal reflective access by org apache spark unsafe platform, Illegal reflective access by org apache ibatis reflection reflector, Illegal reflective access by org/springframework CGLIB core reflectutils, Illegal reflective access by net sf jasperreports engine util classutils
Categories: Top 51 Warning: An Illegal Reflective Access Operation Has Occurred
See more here: nhanvietluanvan.com
All Illegal-Access Operations Will Be Denied In A Future Release
In today’s technology-driven world, data security and privacy are of utmost importance. With the constant evolution of cyber threats, developers and tech companies are constantly working towards improving security measures to protect confidential information. As a result, there have been increasing efforts to crack down on illegal access operations by implementing robust security protocols. In a future release, all illegal-access operations will be denied, ensuring enhanced protection against potential breaches.
Illegal-access operations refer to any attempts to gain unauthorized access or control over digital systems or networks. These operations include hacking, phishing, unauthorized data retrieval, and other malicious activities. The consequences of such operations can be dire, ranging from data theft and financial loss to compromised personal privacy. Thus, it is crucial to implement strict measures to deter and deny any such illegal activities.
To combat these threats, developers and security professionals are working on various strategies that will be included in future releases. These strategies aim to fortify security systems, making them resilient to hacking attempts and unauthorized access. By denying illegal access operations, potential attackers will be unable to penetrate a system, ensuring the integrity and privacy of sensitive data.
One approach to denying illegal access operations is the implementation of multi-factor authentication (MFA). MFA adds an extra layer of security by combining multiple verification methods, such as passwords, biometrics, or physical tokens. This prevents unauthorized individuals from accessing accounts or systems even if they somehow obtain login credentials. Future releases will prioritize MFA, making it a mandatory requirement for all users to ensure maximum protection.
Another important aspect of denying illegal access operations is the continuous monitoring and detection of suspicious activities. Advanced algorithms and artificial intelligence (AI) will be employed to analyze data patterns and identify potential threats in real-time. This proactive approach will enable immediate action to be taken to prevent any unauthorized access attempts. Additionally, future releases will also enhance anomaly detection, flagging any unusual or suspicious behavior even before it becomes a serious threat.
Encryption is yet another crucial element in the fight against illegal-access operations. Encryption is the process of transforming data into an unreadable format, which can only be deciphered by authorized parties with the encryption key. By implementing robust encryption techniques, even if a hacker manages to breach a system, the stolen data will be useless without the encryption key. This ensures that sensitive information remains secure, even in the event of a successful illegal access operation.
Frequently Asked Questions (FAQs):
Q: Will these security measures slow down the system?
A: The goal of implementing stricter security measures is to ensure enhanced protection without compromising system performance. Developers are working to strike a balance between robust security and system efficiency. With advancements in technology, it is possible to implement these measures without causing significant slowdowns.
Q: How will these measures affect user experience?
A: While it is true that some additional steps, such as multi-factor authentication, may require users to take extra actions during the login process. However, these measures are essential to safeguard sensitive data and protect user privacy. Developers are striving to make these security protocols as seamless and user-friendly as possible.
Q: Can these measures guarantee complete security?
A: While these measures significantly reduce the risk of illegal access operations, it is essential to remain vigilant and adopt good security practices. Users must keep their passwords secure, avoid suspicious emails or links, and regularly update their devices and software. No security system can provide 100% guarantee, but by implementing these measures, the threat of illegal access can be greatly mitigated.
Q: Will these security measures be backward-compatible with older systems?
A: Developers understand the importance of ensuring compatibility with existing systems. Although some security measures may require hardware or software upgrades, efforts are being made to ensure that future releases are as backward-compatible as possible, minimizing disruption to users.
In conclusion, the future release of robust security measures will prove instrumental in denying illegal-access operations. By implementing multi-factor authentication, continuous monitoring, advanced encryption techniques, and proactive anomaly detection, developers aim to fortify system defenses against potential threats. While these security measures will have some impact on system performance and user experience, they are essential to protect sensitive data and maintain user privacy. It is crucial for developers and users alike to remain proactive in adhering to good security practices, ensuring a safer digital environment for all.
An Illegal Reflective Access Operation Has Occurred Intellij
The illegal reflective access operation error typically arises in IntelliJ when a piece of code attempts to access a declared field, method, or constructor using reflection, violating the language’s access control rules. This error is prevalent in newer versions of Java, such as Java 9 and later, as these versions introduced stricter checks on reflective access.
Why does this error occur?
The main reason behind the occurrence of an illegal reflective access operation in IntelliJ is the attempt to access or modify a field, method, or constructor from a different module or package that is not accessible through regular means. Java’s access control rules define the visibility of these members within classes and packages, ensuring encapsulation and information hiding.
However, sometimes it becomes necessary to bypass these access control rules and access or modify private or protected members for certain advanced operations. Reflection is a powerful technique in Java that allows such access, but it must be employed judiciously to avoid unexpected behaviors and security vulnerabilities.
When running on a Java version that strictly enforces visibility restrictions, like Java 9 and above, calling a reflective operation without the appropriate permissions will trigger the illegal reflective access operation error in IntelliJ. This check is intended to alert the developer about the potential risks associated with bypassing the access control rules.
How can this error impact your code?
The illegal reflective access operation error has the potential to cause unforeseen consequences in your code. By bypassing access control rules, you risk introducing bugs and instability to your application. Reflection can be a double-edged sword, as it allows you to perform advanced operations but also opens up possibilities for unintended side effects.
Furthermore, relying heavily on reflective access can make your code less maintainable and readable. It becomes harder to reason about the behavior of your program when key operations are obscured within reflection calls. Therefore, it is recommended to use reflection sparingly and resort to it only when absolutely necessary.
How to resolve the illegal reflective access operation error?
To address the illegal reflective access operation error in IntelliJ, you have a few options at your disposal:
1. Upgrade your Java version: If you are using a version earlier than Java 9, consider upgrading to a more recent version. The illegal reflective access operation error is more strictly enforced in newer versions, motivating developers to write cleaner and safer code. However, this might require additional effort in ensuring that your project is compatible with the newer Java version.
2. Use the `–illegal-access` flag: Starting from Java 9, you can launch your application with the command-line option `–illegal-access=permit` to allow illegal reflective access. While this can be a quick solution during development, it is essential to fix the underlying cause and not rely on this flag in production.
3. Modify the access control permissions: If you have control over the targeted class or library causing the error, you can adjust the access control permissions to allow legal reflective access. This can be achieved by adding the `–add-exports` flag to the command-line arguments, specifying the module and package you want to access.
4. Refactor the code: Instead of relying on reflection, consider refactoring your code to follow proper encapsulation and access control rules. Identify alternative solutions that achieve your goals without compromising the integrity and security of your codebase.
Frequently Asked Questions (FAQs):
Q: Can I just disable the illegal reflective access operation error in IntelliJ?
A: While it is technically possible to disable the error notification in your IDE, it is strongly discouraged as it can hide potential issues and lead to unstable code. Addressing the underlying cause is the recommended course of action.
Q: Does this error only occur in IntelliJ?
A: No, the illegal reflective access operation error can occur in any Java IDE or runtime environment that enforces access control rules, not just in IntelliJ.
Q: Is it always safe to use reflection?
A: Reflection should be used with caution and considered a last resort. Incorrect usage of reflection can introduce bugs, security vulnerabilities, and hinder maintainability. Therefore, it is generally advisable to explore alternative approaches before resorting to reflection.
In conclusion, the illegal reflective access operation error in IntelliJ signifies a violation of Java’s access control rules when attempting to perform reflective operations. It is crucial to understand the implications of this error, as bypassing access control can introduce instability and make code harder to maintain. By following best practices and considering alternative solutions, developers can both address and prevent the illegal reflective access operation error in their IntelliJ projects.
An Illegal Reflective Access Operation Has Occurred Eclipse
Introduction:
Eclipse is a popular Integrated Development Environment (IDE) widely used by programmers for Java development. However, while working on Java projects, developers may encounter an error message stating “An Illegal Reflective Access Operation Has Occurred.” In this article, we will delve into the details of this error, explore the causes, and provide solutions to help you overcome this common obstacle during your coding journey.
Understanding the Error:
The error message “An Illegal Reflective Access Operation Has Occurred” typically indicates a violation of the Java Platform Module System (JPMS) access controls. Introduced in Java 9, JPMS aims to enhance the security, performance, and maintainability of Java applications by enforcing strict access controls.
However, this error is not caused solely by the JPMS; it can manifest in earlier versions of Java as well. The underlying reason is that your program is trying to access a part of the code that may have restricted access due to the modular system.
Causes of the Error:
1. Reflection Access: The error commonly occurs when your code uses reflection to access a class, method, or field that is not accessible from the current module. Reflection allows your program to examine and modify the runtime behavior of classes, methods, and objects. Developers must use it judiciously to avoid conflicts with access control restrictions.
2. Incorrect Classpath or Modulepath: If your Eclipse project references classes or libraries that are not part of the modulepath or classpath, the Java runtime may flag these references as illegal reflective access operations.
3. Incompatible Java Versions: Migrating projects developed in earlier Java versions to a newer Java platform, such as Java 9 or above, can lead to the illegal reflective access error. The JPMS introduced in Java 9 imposes stricter access rules by default, which may cause previously allowed operations to become illegal.
Solutions:
1. Specify Accesses Using Command Line: If you encounter this error while running your program from the command line, you can use the `–add-opens` flag to explicitly grant access to a package or module. For example, running `java –add-opens my.module/package=other.module` allows `my.module` to access restricted packages in `other.module`. However, this solution requires manual intervention and may require modifications to your project’s runtime configuration.
2. Update Project’s JVM Arguments: In Eclipse, you can modify the JVM arguments to resolve the issue. Right-click on your project, select Properties, and navigate to the Run/Debug Settings. Edit the launch configuration for your project, switch to the Arguments tab, and include the `–add-opens` argument as mentioned above. Apply the changes and run your project again.
3. Modify Module Dependencies: Review your project’s module dependencies and ensure that all referenced modules are appropriately declared in the module-info.java file. Make sure you are using compatible libraries and dependencies that are compatible with your Java version.
FAQs:
Q1. Can this error affect applications developed in earlier Java versions?
A1. Yes, this error can occur in earlier Java versions if you migrate the application to a Java version that enforces JPMS access controls, such as Java 9 and above.
Q2. Is there a simpler solution for temporarily bypassing the error during development?
A2. You can add the `–illegal-access=permit` flag to your JVM arguments. However, this flag is a temporary workaround and should not be used in production environments.
Q3. How can I determine which access is causing the error?
A3. The error message provided by Eclipse often includes a stack trace indicating the location of the illegal reflective access. Analyze the stack trace to identify the class or method involved, enabling you to address the issue more effectively.
Q4. Can I suppress the “illegal reflective access” warning?
A4. While it is technically possible to suppress the warning, it is highly discouraged as it may lead to security vulnerabilities or compatibility issues. It is better to address the root cause of the error instead of suppressing the warning.
Conclusion:
Encountering an “Illegal Reflective Access Operation Has Occurred” error in Eclipse can be frustrating, but with a thorough understanding of its causes and effective solutions, you can overcome this obstacle in your Java development journey. By following the recommended solutions and taking care to align your project dependencies with the Java version being used, you can continue to build robust, secure, and maintainable applications.
Images related to the topic warning: an illegal reflective access operation has occurred

Found 19 images related to warning: an illegal reflective access operation has occurred theme


![WARNING] An illegal reflective access operation has occurred Warning] An Illegal Reflective Access Operation Has Occurred](https://user-images.githubusercontent.com/8222265/133714440-9f825320-0305-4a24-82da-641b9a1ffbb2.png)










![WARNING] An illegal reflective access operation has occurred Warning] An Illegal Reflective Access Operation Has Occurred](https://user-images.githubusercontent.com/8222265/133714169-cf91ff89-a63b-4ae2-8055-3bfddffa35bb.png)

![Spring] An illegal reflective access operation has occurred 오류 해결 방법 : 네이버 블로그 Spring] An Illegal Reflective Access Operation Has Occurred 오류 해결 방법 : 네이버 블로그](https://mblogthumb-phinf.pstatic.net/MjAxOTEwMTFfOTcg/MDAxNTcwODAzMDc3Nzk2.JpVGddLpJuvrGm15haEndK8MM8rTnc__rlcoGZO9HYUg.8YzCJfLWflGd7XmRAvBjB2brqk0VBh3gao8ItfZ_FEog.PNG.10hsb04/spring-by-pivotal-9066b55828deb3c10e27e609af322c40.png?type=w800)







![JAVA] JDK 환경설정 / WARNING: An illegal reflective access operation has occurred 경고 해결 Java] Jdk 환경설정 / Warning: An Illegal Reflective Access Operation Has Occurred 경고 해결](https://img1.daumcdn.net/thumb/R800x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdn%2FbI1EFz%2Fbtrl6QckVIZ%2FmrXcXIWv8m3Y2HEtitkQZk%2Fimg.png)














Article link: warning: an illegal reflective access operation has occurred.
Learn more about the topic warning: an illegal reflective access operation has occurred.
- What is an illegal reflective access? – java – Stack Overflow
- Java 9 Illegal Reflective Access Warning – Baeldung
- How to fix “an illegal reflective access operation has occurred”
- Getting warnings about “illegal reflective access operation …
- Transition from Java 8 to Java 11 – Azure – Microsoft Learn
- An Illegal Reflective Access Operation Has Occurred: Fixed
- An illegal reflective access operation has occurred when …
- Getting warnings about “illegal reflective access operation …
- How can I solve “WARNING:An illegal reflective access …
- running under Java 11 gives “illegal reflective access” warnings
- Solved: Getting An illegal reflective access operation has…
- Illegal reflective access in JDK 11 : XD-888 – YouTrack
See more: nhanvietluanvan.com/luat-hoc