Sign_And_Send_Pubkey: No Mutual Signature Supported
Introduction
In the realm of secure communication, the exchange of cryptographic signatures plays a vital role in ensuring the integrity, authenticity, and confidentiality of data. However, encountering an error message like “Sign_and_send_pubkey: no mutual signature supported” can be confusing and frustrating. In this article, we will delve into the details of this error, explore the significance of mutual signatures, analyze the risks associated with one-way signatures, and provide recommendations to mitigate the risks of no mutual signature support. Let’s start by understanding the sign_and_send_pubkey error itself.
Explanation of Sign_and_send_pubkey Error
When attempting to establish an SSH (Secure Shell) connection, the error message “Sign_and_send_pubkey: no mutual signature supported” may surface. This error typically indicates that the client and server are unable to agree on the type of cryptographic signature to be used during the key exchange process. In more technical terms, this error occurs when the server does not support the signing algorithm used by the client or vice versa.
Overview of Cryptographic Signatures
Cryptographic signatures serve as digital fingerprints and play a crucial role in verifying the authenticity and integrity of data. When a client and server engage in a secure communication, cryptographic signatures ensure that the transmitted data has not been tampered with and originates from the expected source. The process involves the generation of a signature using the private key and subsequent verification using the corresponding public key.
Importance of Mutual Signature in Secure Communication
In secure communication protocols like SSH, mutual signature support is of utmost importance. A mutual signature ensures that both the client and server possess trust in each other’s identity. It establishes a bidirectional trust, safeguarding against potential malicious actors that may attempt to impersonate either party. Without mutual signature support, the client and server cannot confidently verify each other’s identities, leaving the communication vulnerable to attacks like man-in-the-middle.
Differences Between One-Way Signature and Mutual Signature
In the context of secure communication, it is essential to differentiate between one-way signature and mutual signature. One-way signature refers to the signing process performed by the initiator of the communication alone, whereas mutual signature involves both the client and server performing signing operations. With one-way signatures, the server only verifies the signature generated by the client. In contrast, mutual signatures require both parties to verify each other’s signatures, thereby establishing a trust relationship.
Risks Associated with One-Way Signature
One-way signature authentication poses various risks in secure communication. As it solely relies on the initiator’s signature, this method is susceptible to attacks where an adversary gains unauthorized access to the server’s private key. If the server’s private key is compromised, an attacker can impersonate the server and intercept or manipulate transmitted data. This risk highlights the significance of mutual signature support and the need for its implementation in secure communication protocols.
Significance of Mutual Signature in Public Key Exchange
Public key exchange is a fundamental component of secure communication protocols. It enables both parties to securely exchange and verify each other’s public keys, forming the basis of mutual understanding and trust. Mutual signatures enhance the security of public key exchange by ensuring the integrity and authenticity of the exchanged information. This guarantees that the public keys come from their claimed sources and have not been tampered with by malicious actors.
Possible Reasons for Lack of Mutual Signature Support
The lack of mutual signature support can be attributed to various factors. One of the primary reasons could be the use of different signing algorithms or key types between the client and server. For example, if the server only supports the ECDSA (Elliptic Curve Digital Signature Algorithm) signing algorithm, but the client attempts to use RSA, a “no mutual signature supported” error may arise. Other reasons could involve misconfigured SSH settings, incompatible software versions, or limitations imposed by security policies.
Impact of No Mutual Signature Support on Security
When mutual signature support is absent, the security of the communication is substantially compromised. Without bidirectional trust established through mutual signatures, an attacker can potentially intercept, modify, or inject malicious code into transmitted data without detection. This can lead to information leakage, unauthorized access, and various other security breaches, ultimately undermining the integrity, confidentiality, and availability of the communication.
Alternate Methods for Secure Key Exchange without Mutual Signature
Despite the risks associated with lack of mutual signature support, there are alternative methods for secure key exchange. One such method involves using asymmetric encryption to protect the exchanged keys. By encrypting the keys using the recipient’s public key, it ensures that only the recipient with the corresponding private key can decrypt and access the keys. This mitigates the risks posed by a lack of mutual signature support, as the keys themselves remain inaccessible to potential attackers.
Recommendations for Mitigating the Risks of No Mutual Signature Support
To mitigate the risks of encountering the “Sign_and_send_pubkey: no mutual signature supported” error and lack of mutual signature support, several measures can be taken:
1. Ensure consistent signing algorithms and key types between the client and server to achieve mutual compatibility.
2. Regularly update software and maintain compatibility with the latest versions to address any potential security vulnerabilities or compatibility issues.
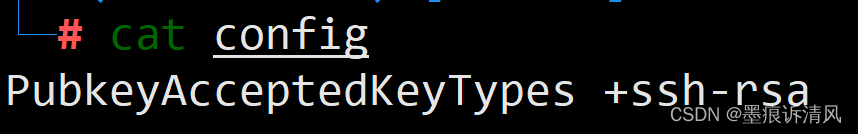
3. Configure SSH settings, such as “PubkeyAcceptedKeyTypes,” to include supported signing algorithms and key types, improving the chances of achieving mutual signature support.
4. Analyze and adjust security policies to permit mutual signature support, while still adhering to best practices and organizational requirements.
5. Utilize supplementary security measures like key rotation, certificate authorities, and multi-factor authentication to further enhance the security of key exchange protocols.
Conclusion
The “Sign_and_send_pubkey: no mutual signature supported” error highlights the importance of mutual signatures in secure communication. By establishing bidirectional trust and verifying each other’s identity, mutual signatures play a critical role in ensuring the integrity and authenticity of exchanged data. While encountering this error can be frustrating, understanding the risks associated with one-way signatures and implementing recommended security measures can mitigate the risks and enhance the security of key exchange protocols. Remember to stay vigilant, update software regularly, and configure SSH settings appropriately to safeguard against potential security breaches.
How Do I Resolve The Ssh Error “Authentication Failed, Permission Denied” On My Ec2 Instance?
Keywords searched by users: sign_and_send_pubkey: no mutual signature supported Sign_and_send_pubkey: signing failed for RSA, PubkeyAcceptedKeyTypes ssh config, Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth), Permission denied (publickey), Ssh-keygen, We did not send a packet, disable method, Gen key SSH, Receive packet: type 51
Categories: Top 84 Sign_And_Send_Pubkey: No Mutual Signature Supported
See more here: nhanvietluanvan.com
Sign_And_Send_Pubkey: Signing Failed For Rsa
In the world of cryptography, RSA is one of the most widely used and respected algorithms for secure communication and digital signatures. However, while using RSA to sign and send a public key, you may at times encounter the error message: “Sign_and_send_pubkey: signing failed for RSA.” This error can be puzzling and frustrating, as it disrupts the smooth functioning of cryptographic operations. In this article, we will delve into the reasons behind this error, explore possible solutions, and address some frequently asked questions.
Understanding RSA Sign and Send Pubkey
RSA (Rivest-Shamir-Adleman) is an asymmetric cryptographic algorithm widely used for secure data transmission, digital signatures, and key exchange. It relies on the mathematical properties of large prime numbers and their products. The RSA algorithm involves key pair generation, consisting of a public key and a corresponding private key. The public key is used to encrypt data, while the private key is utilized for decryption and digital signing.
The “Sign_and_send_pubkey: signing failed for RSA” error, typically encountered during SSH (Secure Shell) communication, occurs when the system encounters a problem while signing and sending the public key using RSA. This error can be triggered by various causes, including incorrect key permissions, insufficient system resources, or compatibility issues.
Possible Causes and Solutions
1. Incorrect Key Permissions: One common cause of “Sign_and_send_pubkey: signing failed for RSA” is incorrect permissions set for the key files. To resolve this issue, ensure that the private and public key files have the appropriate file permissions. In most cases, these files should have restricted permissions and only be accessible by the owner. You can adjust the permissions using the `chmod` command or through a file manager.
2. Insufficient System Resources: Another reason for this error can be insufficient system resources required for the cryptographic operations. RSA encryption and signing involve heavyweight calculations, particularly for larger keys. If your system does not have enough resources, such as CPU power or memory, it may fail to sign and send the public key. In such cases, freeing up resources or upgrading your system may resolve the issue.
3. Compatibility Issues: Sometimes, compatibility issues between different software versions or settings can lead to the “Sign_and_send_pubkey: signing failed for RSA” error. Ensure that your SSH client and server are using compatible versions and configurations. Updating the software or adjusting the settings to match the requirements can help resolve this issue.
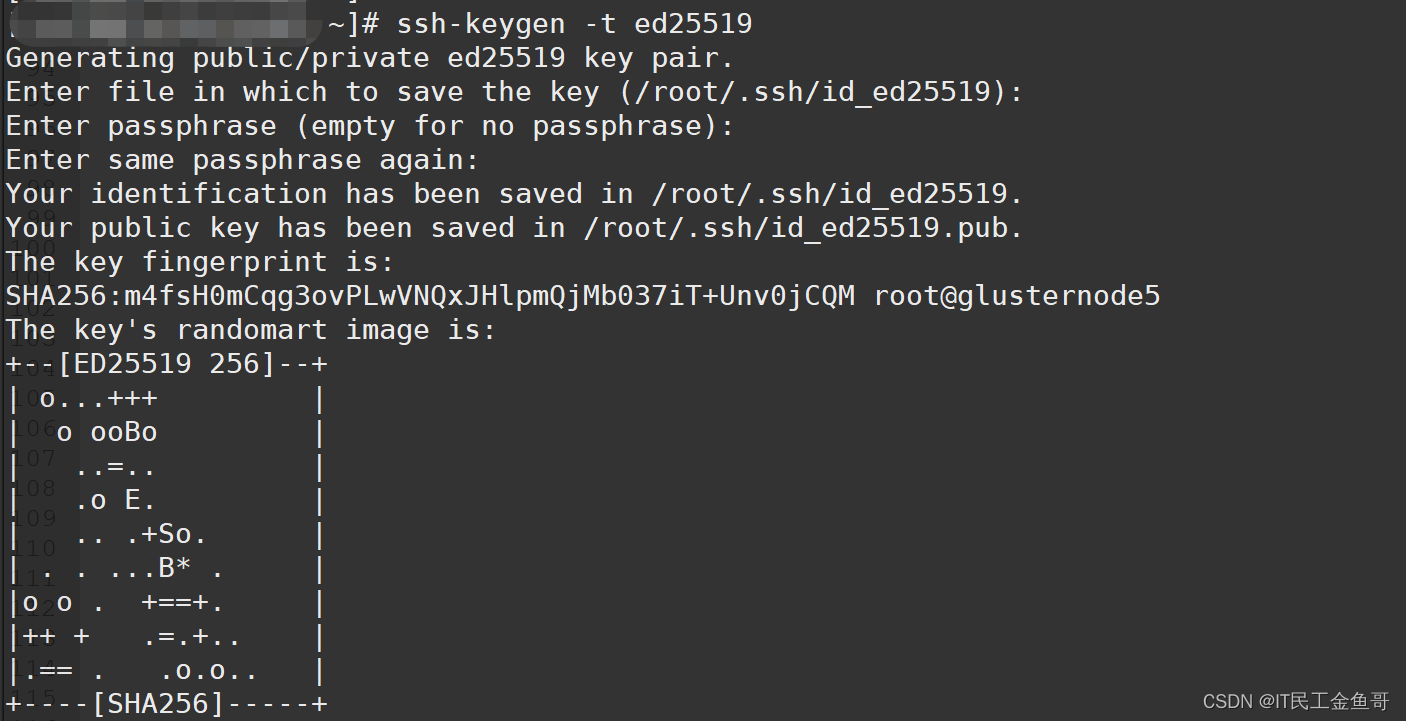
4. Corrupted Key Files: If the private or public key files have been corrupted, the signing process may fail, resulting in the error message. To rectify this, you can try generating a new key pair and replacing the old files. Keep in mind to securely store your private key to avoid unnecessary exposure.
Frequently Asked Questions (FAQs)
Q1: Can I use a different cryptographic algorithm instead of RSA to avoid this error?
A: Yes, there are alternatives to RSA, such as Elliptic Curve Cryptography (ECC) or Digital Signature Algorithm (DSA). However, RSA remains widely supported and recommended for its security and widespread adoption. Switching to an alternative algorithm may require modifications to your cryptographic setup and ensuring compatibility with the systems you interact with.
Q2: I have followed the suggested solutions, but the error still persists. What should I do?
A: If the error continues to persist after attempting the suggested solutions, it is advisable to seek further assistance from relevant support forums or consult a cryptography expert. They can provide a more in-depth analysis of the issue specific to your setup and assist in troubleshooting.
Q3: How can I prevent this error from occurring in the future?
A: To minimize the occurrence of the “Sign_and_send_pubkey: signing failed for RSA” error, ensure that you follow proper key file management practices, regularly back up your key files, and securely store your private key. Keeping your system resources optimized and up to date can also help prevent resource-related issues.
Q4: Is this error specific to SSH communication only?
A: While this error is commonly experienced during SSH communication, it can potentially occur in other scenarios involving RSA-based digital signatures. RSA is used in various contexts, including SSL/TLS, secure email, and secure file transfer protocols. The root causes and solutions discussed in this article can be applied to these scenarios as well.
Conclusion
The “Sign_and_send_pubkey: signing failed for RSA” error can disrupt secure communication protocols relying on RSA-based public key signing. By understanding the causes and implementing the suggested solutions, you can troubleshoot and resolve this error effectively. Remember to ensure correct key permissions, allocate sufficient system resources, address compatibility issues, and consider regenerating key pairs if necessary. With diligent maintenance and troubleshooting, you can ensure seamless RSA-based operations and secure communication.
Pubkeyacceptedkeytypes Ssh Config
Introduction:
SSH, or Secure Shell, is a widely used cryptographic protocol that allows secure remote login and secure file transfers over an unsecured network. It uses a combination of public key cryptography and asymmetric encryption to ensure secure communication between a client and a server. To enhance security, SSH configurations can be customized to specify the accepted key types for public key authentication. This article delves into the details of “PubkeyAcceptedKeyTypes” in the SSH configuration file and answers some frequently asked questions.
Understanding PubkeyAcceptedKeyTypes:
The “PubkeyAcceptedKeyTypes” directive is a configuration option that enables administrators to specify the public key types that are accepted for public key authentication by the SSH server. By default, SSH servers accept multiple key types, including RSA, DSA, and ECDSA. However, there might be scenarios where you may want to restrict the accepted key types for stronger security.
How to use PubkeyAcceptedKeyTypes:
To use the “PubkeyAcceptedKeyTypes” directive, you need to make changes to the SSH server’s configuration file (/etc/ssh/sshd_config). Here’s an example of how to limit the accepted key types to RSA and ECDSA:
1. Open the SSH configuration file:
“`
sudo nano /etc/ssh/sshd_config
“`
2. Locate the line containing “PubkeyAcceptedKeyTypes” (if it doesn’t exist, you can add it):
“`
PubkeyAcceptedKeyTypes rsa-sha2-256,ecdsa-sha2-nistp256
“`
3. Save the file and exit the editor.
4. Restart the SSH server to apply the changes:
“`
sudo service ssh restart
“`
Now, the SSH server will only accept RSA and ECDSA keys for public key authentication.
Commonly used key types:
SSH supports various key types, and the following are commonly used:
1. RSA (rsa-sha2-256)
RSA keys are widely supported and have been the default choice for many years. They provide good security with strong encryption and signature algorithms. However, RSA keys can be slower compared to modern alternatives.
2. DSA (ssh-dss)
DSA keys are widely supported, although they have some security limitations and are generally considered weaker than RSA or ECDSA keys. For better security, it is recommended to use RSA or ECDSA keys instead.
3. ECDSA (ecdsa-sha2-nistp256, ecdsa-sha2-nistp384, ecdsa-sha2-nistp521)
ECDSA keys are based on elliptic curve cryptography and offer similar security to RSA keys but with smaller key sizes. They are considered more efficient and are a good alternative to RSA keys.
4. Ed25519 (ssh-ed25519)
Ed25519 keys are based on elliptic curve cryptography and provide excellent security with shorter key lengths compared to RSA or ECDSA keys. They are considered highly secure and performant.
Frequently Asked Questions:
Q1. Why would I restrict the accepted key types?
Restricting the accepted key types can further enhance the security of SSH access by eliminating weaker or deprecated algorithms. It ensures that only stronger and more secure key types are used for authentication.
Q2. Are there any risks in limiting the accepted key types?
While limiting the accepted key types can improve security, it is essential to consider compatibility with existing systems or client configurations. Older SSH clients or systems that rely on deprecated key types may lose the ability to authenticate if restricted.
Q3. How do I know which key types my SSH client supports?
SSH clients support different key types based on their configurations and versions. You can refer to the client’s documentation or configuration settings to determine the supported key types.
Q4. Can I specify multiple accepted key types?
Yes, you can specify multiple accepted key types in the “PubkeyAcceptedKeyTypes” directive by separating them with commas. For example:
“`
PubkeyAcceptedKeyTypes rsa-sha2-512, ecdsa-sha2-nistp384, ssh-ed25519
“`
Ensure that the specified key types are supported by your SSH server and client.
Q5. What if I specify an unsupported key type in “PubkeyAcceptedKeyTypes”?
If you specify an unsupported key type, the SSH server will no longer accept authentication attempts using that key type. Make sure to have suitable alternatives specified to ensure compatibility.
Conclusion:
The “PubkeyAcceptedKeyTypes” SSH configuration option provides administrators with the flexibility to limit the accepted public key types, thereby enhancing the security of SSH connections. By referring to commonly used key types and understanding the potential risks and benefits, administrators can make informed decisions to strengthen their SSH servers’ security while maintaining compatibility with existing systems. Always ensure that SSH server configurations are thoroughly tested before applying them to production environments.
Images related to the topic sign_and_send_pubkey: no mutual signature supported

Found 32 images related to sign_and_send_pubkey: no mutual signature supported theme






Article link: sign_and_send_pubkey: no mutual signature supported.
Learn more about the topic sign_and_send_pubkey: no mutual signature supported.
- Sign_and_send_pubkey: no mutual signature supported
- SSH-RSA key rejected with message “no mutual signature …
- SSH no mutual signature supported – Coder v1 Docs
- sign_and_send_pubkey: no mutual signature supported
- ssh handshake is rejected with ‘no mutual signature algorithm …
- “no mutual signature algorithm” because of disabled ssh-rsa …
- SSH-RSA key rejected with message “no … – Virtuozzo Support
- No Mutual Signature Supported – SFTP Gateway Support ·
- How to Fix sign_and_send_pubkey: no mutual signature …
- SFTP connection error (sign_and_send_pubkey: no mutual …
See more: nhanvietluanvan.com/luat-hoc