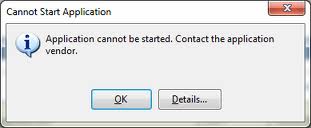
Deployment And Application Do Not Have Matching Security Zones
1. Understanding Security Zones in the Context of Deployment and Application
In the world of software development and deployment, security plays a crucial role in ensuring the integrity and confidentiality of an application. One important aspect of security is the concept of security zones. A security zone is a boundary that separates different levels of trust and privilege within a system. It defines the access control policies and permissions for various components and entities within an application.
In the context of deployment and application, security zones are used to define and enforce access control policies between different components and layers of an application. For example, an application may have a front-end web layer, a middleware layer, and a database layer. Each of these layers may have different security requirements and access privileges. By defining security zones, developers and administrators can ensure that only authorized entities can interact with each component, thereby reducing the risk of unauthorized access or malicious attacks.
2. Common Reasons for Mismatched Security Zones in Deployment and Application
Despite the importance of consistent security zones, mismatches between deployment and application security zones can occur. There are several common reasons for these mismatches:
a) Inadequate planning and design: During the initial stages of development, proper consideration and planning for security zones may be overlooked. This can result in inconsistent security zone configurations between the deployment environment and the application itself.
b) Lack of communication and collaboration: When multiple teams or departments are involved in the deployment and application process, there may be a lack of effective communication and collaboration. This can lead to misunderstandings or conflicting decisions regarding security zones, resulting in mismatches.
c) Legacy systems and applications: In scenarios where legacy systems or applications are involved, the existing security zones may not align with the modern security standards and best practices. Integrating such systems into an environment with a different security architecture can cause mismatches.
3. Implications of Deployment and Application with Inconsistent Security Zones
Mismatched security zones between deployment and application can have serious implications for the overall security posture of the system. Some of the key implications include:
a) Increased vulnerability to unauthorized access: Inconsistent security zones can create security gaps and loopholes that can be exploited by malicious actors. This can result in unauthorized access to sensitive data or systems.
b) Elevation of privileges: Mismatched security zones can lead to situations where entities with lower privileges gain unintended access to higher privilege levels. This can enable attackers to perform unauthorized actions with elevated privileges, potentially causing significant harm to the system.
c) Regulatory non-compliance: Many industries are subject to strict regulatory requirements for data protection and security. Mismatched security zones can lead to non-compliance with these regulations, exposing organizations to legal and financial risks.
4. Identifying Security Risks and Vulnerabilities in Mismatched Zones
To effectively manage and mitigate the risks associated with mismatched security zones, organizations need to identify potential security risks and vulnerabilities. Some key areas to focus on include:
a) Reviewing access control policies: Evaluate the access control policies governing each security zone in the deployment and application layers. Look for inconsistencies, gaps, or excessive permissions that can compromise the integrity of the system.
b) Analyzing privilege escalation possibilities: Assess the potential for privilege escalation through gaps in the security zones. Identify scenarios where entities with lower privileges can gain unauthorized access to higher-level components.
c) Assessing data protection mechanisms: Evaluate the security measures in place to protect sensitive data within each security zone. Identify weaknesses or vulnerabilities that can be exploited by attackers.
5. Impact of Mismatched Security Zones on System Performance and Stability
Aside from the security implications, mismatched security zones can also have a negative impact on system performance and stability. Some of the key impacts include:
a) Increased complexity: Inconsistent security zones can lead to complex and convoluted access control mechanisms. This complexity can make it harder to manage and maintain the system, potentially leading to errors or misconfigurations that compromise system stability.
b) Reduced efficiency: Mismatched security zones can result in unnecessary restrictions or limitations on authorized entities, impacting system efficiency. This can manifest as slow response times, increased resource consumption, or degraded user experience.
c) Difficulty in troubleshooting: When security zones are not aligned, troubleshooting and identifying the root causes of issues becomes more challenging. The lack of consistency in security configurations can make it harder to pinpoint and resolve problems, leading to prolonged downtime and reduced system reliability.
6. Strategies for Mitigating Risks in Deployment and Application Security Zones
To mitigate the risks associated with mismatched security zones, organizations can adopt several strategies:
a) Conduct a thorough security assessment: Perform a comprehensive assessment of the entire deployment and application architecture, identifying security gaps and vulnerabilities resulting from inconsistent security zones.
b) Implement a consistent security architecture: Define and enforce a consistent security architecture across all layers of the deployment and application. This includes defining clear security zones and access control policies that align with industry best practices.
c) Regularly review and update security configurations: Conduct periodic reviews of security configurations to ensure they remain up to date and aligned with changing security requirements. This includes reviewing access control policies, privilege levels, and data protection measures.
7. Best Practices for Aligning Security Zones in Deployment and Application
To achieve consistent security zones in deployment and application, organizations should follow these best practices:
a) Involve security experts early on: Engage security experts or consultants during the planning and design stages of the deployment and application. This ensures that security considerations, including security zones, are incorporated from the beginning.
b) Foster collaboration between teams: Foster effective communication and collaboration between development, operations, and security teams. This ensures that everyone is aligned and working towards a consistent security architecture.
c) Regularly update and patch software: Keep all software components, including the deployment and application frameworks, up to date with the latest security patches and updates. This helps to address known vulnerabilities and reduce the risk of security breaches due to outdated software.
8. Tools and Technologies to Enforce Consistent Security Zones in Deployment and Application
Several tools and technologies can help enforce consistent security zones in deployment and application:
a) Security policy management tools: These tools help organizations define, enforce, and manage security policies across the entire system. They enable centralized control and auditing of access rights, making it easier to ensure consistent security zones.
b) Vulnerability scanning and penetration testing tools: These tools help identify vulnerabilities and weaknesses in a system by simulating real-world attacks. By utilizing these tools, organizations can detect and address security zone mismatches before they are exploited.
c) Security information and event management (SIEM) systems: SIEM systems collect and analyze logs and events from various security sources, providing real-time visibility into potential security zone mismatches. They can help organizations stay proactive in identifying and resolving security issues.
9. The Role of Continuous Monitoring, Evaluation, and Adaptation in Security Zone Management in Deployment and Application.
Effective security zone management in deployment and application requires continuous monitoring, evaluation, and adaptation. Organizations should implement the following practices:
a) Continuous monitoring: Regularly monitor the system for any security zone mismatches or deviations from the defined security architecture. Implement real-time alerts to quickly identify and respond to any security incidents.
b) Evaluation and assessment: Periodically evaluate and assess the effectiveness of the implemented security zones. This includes analyzing access logs, reviewing audit reports, and conducting vulnerability assessments to identify any areas of improvement.
c) Adaptive security measures: Continuously adapt and improve security measures based on the evaluation results. This includes updating access control policies, enhancing data protection measures, and incorporating lessons learned from previous incidents.
FAQs
Q: What is the significance of security zones in deployment and application?
A: Security zones help define and enforce access control policies between different components and layers of an application, reducing the risk of unauthorized access or malicious attacks.
Q: What are the common reasons for mismatches in security zones between deployment and application?
A: Some common reasons include inadequate planning and design, lack of communication and collaboration, and integration of legacy systems with different security architectures.
Q: What are the implications of deployment and application with inconsistent security zones?
A: Mismatched security zones can result in increased vulnerability to unauthorized access, elevation of privileges, and non-compliance with regulatory requirements.
Q: How can organizations mitigate the risks associated with mismatched security zones?
A: Organizations can conduct thorough security assessments, implement a consistent security architecture, and regularly review and update security configurations.
Q: What are some best practices for aligning security zones in deployment and application?
A: Involving security experts early on, fostering collaboration between teams, and regularly updating and patching software are important best practices.
Q: What tools and technologies can help enforce consistent security zones in deployment and application?
A: Security policy management tools, vulnerability scanning and penetration testing tools, and SIEM systems can help enforce consistent security zones.
Q: Why is continuous monitoring, evaluation, and adaptation important in security zone management?
A: Continuous monitoring helps identify security incidents, evaluation and assessment allow for improvement opportunities, and adaptation ensures security measures remain effective over time.
Deployment And Application Do Not Have Matching Security Zones (2 Solutions!!)
What Are The Security Zones In Windows 10?
In the ever-expanding digital world, security has become a top concern for individuals and organizations alike. Windows 10, Microsoft’s latest operating system, provides various security features to protect users and their data. One such security mechanism is the concept of security zones. In this article, we will explore what security zones are in Windows 10 and how they contribute to a more secure computing environment.
Security zones in Windows 10 refer to distinct areas or domains in which certain security settings and permissions are applied. These zones are based on the level of trustworthiness assigned to different types of websites, local networks, or online content. By segregating various parts of the computing environment into security zones, Windows 10 ensures that appropriate security measures are applied to protect against potential threats.
The primary purpose of security zones is to help users identify and control the level of trust given to different online resources and network connections. Windows 10 defines four main security zones:
1. Internet Zone:
The Internet Zone is the least trusted zone in Windows 10. It includes all websites and online content accessed through the internet. By default, this zone comprises considerably strict security settings to protect users from potentially harmful web resources. These settings include disabling automatic downloads, active content and plugins, and enforcing strict pop-up blocking. Users can further customize these settings based on their specific requirements.
2. Local Intranet Zone:
The Local Intranet Zone consists of all the websites and content accessed via a local network, such as an organization’s internal network. Windows 10 assigns a higher level of trust to this zone compared to the Internet Zone. The security settings in this zone are relatively less restrictive, allowing certain operations and content that may be necessary for internal network usage. This includes automatic logon using Windows credentials and the execution of active content or plugins.
3. Trusted Sites Zone:
The Trusted Sites Zone includes specific websites that users explicitly trust and consider safe. This zone allows users to access these trusted websites with more relaxed security settings by default. Users can add or remove websites from this zone manually or use certain policies to manage trusted sites across an organization. Although the default settings are relatively more permissive, users should exercise caution while adding websites to this zone to avoid potential security risks.
4. Restricted Sites Zone:
The Restricted Sites Zone is the most stringent security zone in Windows 10. It comprises websites deemed as potentially harmful or untrustworthy. To protect the system, Windows 10 imposes significant restrictions on the execution of active content, plugins, and certain downloads from this zone. By default, the Restricted Sites Zone includes websites with malicious content or identified security risks. However, users can manually add or remove websites from this zone according to their preferences.
Frequently Asked Questions (FAQs):
Q1. What are the benefits of security zones in Windows 10?
A1. Security zones help users differentiate between trustworthy and potentially harmful websites or network connections. By applying different security settings to each zone, the risk of malware infections, unauthorized access, or data breaches is significantly reduced. It gives users granular control over their system’s security based on their trust level for different resources.
Q2. Can I modify the security settings for each zone in Windows 10?
A2. Yes, Windows 10 allows users to modify the security settings for each zone according to their requirements. You can access these settings through the Internet Options dialog in the Control Panel or through the Windows Security app. However, it is recommended to always exercise caution while modifying security settings to avoid unintentional security loopholes.
Q3. Are there any default websites in the Trusted Sites or Restricted Sites zones?
A3. Windows 10 does not include any default websites in the Trusted Sites zone. However, the Restricted Sites zone comes with a preconfigured list of potentially harmful websites. Users can add or remove websites from both zones manually.
Q4. Are security zones limited to web content only?
A4. No, security zones in Windows 10 are not limited to web content only. They can also apply to certain network connections, such as those made within an organization’s local network. The security settings for each zone can be customized to include both web and network-related configurations.
In summary, security zones play a vital role in Windows 10’s security architecture by segregating different parts of the computing environment into distinct zones, each with its own defined security settings. By classifying websites and network connections into these zones, users can better control and manage the security level applied to different resources. Understanding and utilizing the security zones in Windows 10 helps create a safer computing experience, protecting users and their data from potential threats.
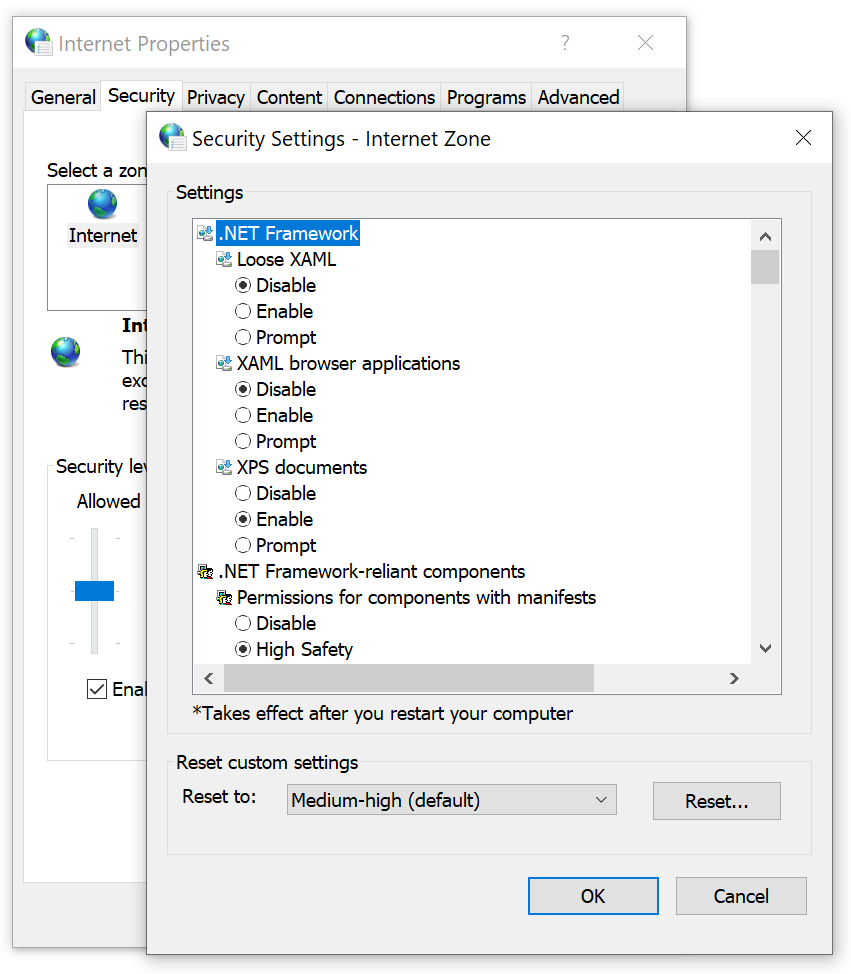
What Are The Security Zones In Internet Explorer?
In today’s digital world, browsing the internet has become an integral part of our lives. However, with the ever-growing threat of cyber-attacks and malware, it is crucial to have a secure web browsing experience. Internet Explorer, one of the most widely used web browsers, offers a robust security feature called “security zones.” These security zones aim to provide a safer web browsing experience by categorizing websites into different levels of trust. In this article, we will explore the concept of security zones in Internet Explorer and understand how they enhance online security.
Understanding Security Zones:
Internet Explorer divides websites into four distinct security zones:
1. Internet Zone:
The Internet Zone is the default zone in Internet Explorer. All websites that do not fit into any other specified zone are placed in this zone. As the internet is a diverse and dynamic platform, websites in this zone are considered potentially untrusted. Therefore, Internet Explorer applies strict security measures, restricting the execution of potentially harmful elements such as ActiveX controls, Java applets, and scripts. Additionally, Information Bar notifications often alert users to potentially malicious content in this zone.
2. Local Intranet Zone:
The Local Intranet Zone consists of websites that users trust within their organization’s network. These websites typically belong to an organization’s internal network and are considered more secure than those on the internet. Internet Explorer’s security settings for Local Intranet Zone are less strict compared to the Internet Zone, allowing websites to use certain functionalities more freely.
3. Trusted Sites Zone:
The Trusted Sites Zone includes websites that users explicitly trust. For instance, websites that require additional functionalities like installing software updates or accessing network resources can be added to this zone. Internet Explorer’s security settings for the Trusted Sites Zone are further relaxed, enabling enhanced functionality while maintaining a higher level of security as compared to the previous zones.
4. Restricted Sites Zone:
The Restricted Sites Zone includes websites that users explicitly do not trust or want to restrict. Users can choose to add specific websites to this zone to limit their access and prevent any potential threats. Internet Explorer applies the strictest security settings to this zone, restricting the website’s functionality to prevent any unauthorized or malicious activities.
Frequently Asked Questions (FAQs):
Q1: How can I view and modify security zone settings in Internet Explorer?
A1: To view and modify security zone settings, open Internet Explorer, go to the “Tools” menu, select “Internet Options,” and click on the “Security” tab. From here, you can select a zone and customize the security level for that zone.
Q2: Can I add or remove websites from security zones in Internet Explorer?
A2: Yes, you can manually add or remove websites from different security zones. To do this, go to the “Security” tab in the “Internet Options” menu, select a zone, click on the “Sites” button, and add or remove websites as required.
Q3: Are there any risks associated with adding websites to the Trusted Sites Zone?
A3: Adding websites to the Trusted Sites Zone should only be done for websites that you explicitly trust and know are secure. However, be cautious while adding websites, as there is still a risk associated with them, especially if the site becomes compromised. Regularly review the list of trusted sites to ensure their continued trustworthiness.
Q4: What if I visit a website that doesn’t fall into any security zone?
A4: If you visit a website that doesn’t fall into any of the defined security zones, it will automatically be considered as part of the Internet Zone. Internet Explorer will apply the default high-security settings to protect you from potentially harmful content.
Q5: Are security zones exclusive to Internet Explorer?
A5: While security zones were initially introduced in Internet Explorer, other web browsers also offer similar security features, although they may use different terminologies.
In conclusion, security zones in Internet Explorer play a vital role in protecting users from potential threats while browsing the internet. By categorizing websites into different zones, Internet Explorer can apply varying levels of security to ensure a secure browsing experience. Understanding these security zones and customizing their settings can significantly enhance online security and protect against potential cyber-attacks.
Keywords searched by users: deployment and application do not have matching security zones system.deployment.application.invaliddeploymentexception (zone), System Deployment application InvalidDeploymentException, the manifest for this application does not have a signature signature validation will be ignored
Categories: Top 63 Deployment And Application Do Not Have Matching Security Zones
See more here: nhanvietluanvan.com
System.Deployment.Application.Invaliddeploymentexception (Zone)
InvalidDeploymentException falls under the System.Deployment.Application namespace, which is a part of the .NET Framework provided by Microsoft. It specifically handles exceptions related to application deployment using ClickOnce technology, a Microsoft technology that allows for easy deployment of Windows-based applications.
When an application is developed using ClickOnce, it is typically deployed from a web server or a file share location. ClickOnce applications have certain prerequisites and dependencies that need to be met in order for them to run smoothly. If any of these requirements are not met, an InvalidDeploymentException is thrown.
The most common cause of an InvalidDeploymentException is a mismatch between the application’s manifest file and the actual files present on the deployment location. The manifest file contains important information about the application, such as its version, dependencies, and security settings. If any of these details are incorrect or if the files mentioned in the manifest are not present, the exception is thrown.
Another possible cause of this exception is an issue with the user’s system configuration. ClickOnce applications rely on certain configurations to be set correctly on the client machine. If these settings are configured improperly or if the required components are missing, the deployment may fail, resulting in an InvalidDeploymentException.
Now that we understand the possible causes, let’s explore some methods to prevent encountering this exception in our applications.
1. Ensure Proper Manifest Generation: When building ClickOnce applications, it is crucial to generate the manifest file accurately. Pay close attention to the version numbers, dependencies, and file references mentioned in the manifest.
2. Validate Deployment Location: Before deploying an application, always ensure that the deployment location contains all the necessary files mentioned in the manifest. A missing or incorrect file can cause the deployment to fail.
3. Test on Different Configurations: Testing the application on different client machines with various configurations can help identify any potential deployment issues. This includes verifying that the required components, such as .NET Framework versions, are installed and properly configured.
4. Handle Exceptions Gracefully: When working with ClickOnce deployments, it is essential to handle exceptions, including the InvalidDeploymentException, in a graceful manner. Inform the users of the issue and provide guidance on what steps they need to follow to resolve it.
In case you do encounter an InvalidDeploymentException, here are a few potential solutions to consider:
1. Check Deployment Location: Verify that the deployment location contains all the required files mentioned in the manifest. If any file is missing or corrupted, fix the issue by redeploying the application with the correct files.
2. Redeploy the Application: If the exception persists, try redeploying the application from scratch, ensuring that all files and dependencies are properly included.
3. Update .NET Framework: If the user’s system has an older version of the .NET Framework, consider updating it to the required version specified in the application’s manifest.
4. Clear Application Cache: ClickOnce applications are stored in a cache on the client machine. Clearing this cache might help resolve any issues related to the InvalidDeploymentException. You can find the cache location by checking the ClickOnce cache settings on the client machine, usually located in “C:\Users\[username]\AppData\Local\Apps\2.0.”
In conclusion, System.Deployment.Application.InvalidDeploymentException is a notable exception that occurs during the deployment of ClickOnce applications. By understanding its causes, prevention methods, and potential solutions, developers can ensure a smoother deployment process for their applications.
— FAQ —
Q: How can I prevent an InvalidDeploymentException?
A: Proper manifest generation, validating the deployment location, testing on different configurations, and handling exceptions gracefully are some of the steps you can take to prevent encountering this exception.
Q: Why does InvalidDeploymentException occur?
A: InvalidDeploymentException occurs when there are issues with the deployment of a ClickOnce application, such as a mismatch between the manifest file and the deployed files or improper system configurations.
Q: How can I fix an InvalidDeploymentException?
A: To fix an InvalidDeploymentException, you can check the deployment location for all necessary files, redeploy the application, update the .NET Framework, or clear the application cache.
Q: Can a user fix an InvalidDeploymentException on their own?
A: Certain solutions, such as clearing the application cache or updating the .NET Framework, can be performed by the user. However, in some cases, the developer may need to intervene to resolve the issue.
Q: Is InvalidDeploymentException specific to ClickOnce applications?
A: Yes, InvalidDeploymentException is specific to ClickOnce applications as it is related to their deployment process.
System Deployment Application Invaliddeploymentexception
The InvalidDeploymentException is a type of exception that is thrown when a problem arises during the deployment of a software system. It is part of the System.Deployment.Application namespace in .NET, which provides classes for deploying applications in a secure and user-friendly manner. This exception indicates that the deployment manifest is either corrupted or does not conform to the required specifications.
There are several reasons why this exception might occur. One possibility is that the deployment manifest, which contains information about the application and its dependencies, is not valid. This could be due to an error in the manifest file itself or a problem with one of its components. Another reason could be that the application being deployed requires a specific version of a dependency that is not available or is incompatible with the system.
Handling the InvalidDeploymentException requires understanding the root cause of the issue. Since the exception is thrown when there is a problem with the deployment manifest, one approach is to inspect the manifest file for any errors. Looking for typos, missing dependencies, or other issues within the manifest can help identify the cause of the exception. Additionally, verifying that all the required dependencies are correctly included can also prevent this exception from occurring.
To resolve the InvalidDeploymentException, developers need to correct the manifest or the misconfiguration that caused the exception. This could involve updating the manifest file to fix any errors or ensuring that the necessary dependencies are available and compatible with the deployment environment. Once the issues are addressed, the application can be redeployed, and the exception should no longer be raised.
FAQs:
Q: How can I determine if the deployment manifest is the cause of the InvalidDeploymentException?
A: You can try opening the manifest file and checking for any syntax errors or missing dependencies. Additionally, you might want to validate the manifest against the specifications to ensure it adheres to the required format.
Q: What should I do if the deployment manifest is corrupted?
A: If the manifest file itself is corrupted, you should consider regenerating it from the original source. Alternatively, if you have a backup of the manifest, you can restore it. Making sure that the backup is not corrupted is crucial.
Q: Can an InvalidDeploymentException be caused by missing or incompatible dependencies?
A: Yes, one of the reasons for this exception is when the application being deployed requires a specific version of a dependency that is missing or incompatible. Make sure all the necessary dependencies are included and compatible with the target system.
Q: Are there any tools available to help troubleshoot the InvalidDeploymentException?
A: Yes, there are various tools, both built-in and third-party, that can assist in troubleshooting deployment issues. Some examples include the ClickOnce Manifest Inspector, MageUI, and Mage.exe.
Q: Can misconfiguration of the deployment environment lead to an InvalidDeploymentException?
A: Yes, misconfigurations such as incorrect file permissions, insufficient disk space, or network connectivity issues can also cause the InvalidDeploymentException. Ensure that the deployment environment is properly set up and all prerequisites are met.
In conclusion, the InvalidDeploymentException is an exception that developers may encounter during the system deployment process. It occurs when there is a problem with the deployment manifest, whether due to corruption or an incorrect configuration. By carefully inspecting the manifest file for errors and ensuring the availability and compatibility of dependencies, developers can resolve this exception and successfully deploy their applications.
The Manifest For This Application Does Not Have A Signature Signature Validation Will Be Ignored
In the world of software development, the manifest file plays a crucial role in ensuring the integrity and authenticity of an application. Essentially, a manifest is a file that contains essential information about the application, such as its version, package name, permissions, and digital signatures. These signatures act as a seal of trust, verifying that the application has not been tampered with and can be trusted by users.
However, encountering an error message stating “The manifest for this application does not have a signature: signature validation will be ignored” can be perplexing for both developers and users alike. This error message indicates that the manifest file of the application lacks a valid digital signature, hence rendering the signature validation process ineffective.
What Does It Mean When the Manifest Does Not Have a Signature?
When an application is deployed, the manifest file is supposed to include a digital signature. This signature ensures that the application has not been altered or compromised since it was signed by the original developer or company. A missing or invalid signature raises a red flag, indicating that the application cannot be verified as genuine. Consequently, most operating systems will ignore the signature validation process altogether, potentially compromising the security and integrity of the application.
Why Would an Application’s Manifest Lack a Signature?
1. Development and Testing Environments: During the development and testing stages, it is common for developers to omit or exclude the signing process. This is because the signature verification can slow down testing and debugging activities. However, it is essential to ensure that the application is thoroughly tested and signed before being released to the public.
2. Deployment Errors: Sometimes, deploying an application can introduce errors or glitches that result in a missing or invalid signature. This can occur due to misconfigured build processes, incorrect permissions, or issues during packaging and signing.
3. Third-party Dependencies: In some cases, an application relies on third-party libraries or components that lack a proper signature. When these components are integrated into the application, the overall manifest may end up missing a valid signature.
How Does the Lack of Signature Validation Affect Users?
The absence of signature validation can have several implications for the end-users:
1. Security Risks: By ignoring the signature validation, users are exposed to potential security risks. A compromised application might contain suspicious code, malicious payloads, or vulnerabilities that hackers can exploit to gain unauthorized access to users’ devices or personal information.
2. Trust Issues: Lack of signature validation erodes trust in the application and its developers. Users may become hesitant to download or use an application that lacks the seal of authenticity provided by a valid digital signature.
3. Inconsistent Behavior: Depending on the operating system and device, an application without a valid signature may exhibit inconsistent behavior. Certain security features, such as app sandboxing or permissions management, might not function correctly, affecting the user experience and potentially leading to unexpected errors or crashes.
FAQs:
Q: Is it safe to use applications without a signature?
A: While there are legitimate applications without signatures, it is generally safer to use applications that have been digitally signed. Digital signatures provide assurance that the application has not been tampered with or compromised by malicious actors.
Q: Can I manually add a signature to an application’s manifest?
A: No, as an end-user, you cannot add or modify a signature in an application’s manifest. Only the original developer or authorized parties can sign application files.
Q: How can I ensure the security of an application that lacks a signature?
A: If an application lacks a valid signature, exercise caution before downloading and using it. Consider the reputation and source of the application, read reviews, and use trusted app stores to minimize the risk of downloading potentially harmful software.
Q: Is there a way for developers to fix the lack of signature issue?
A: Yes, developers can resolve this issue by properly signing the application’s manifest file using tools provided by the respective development platforms, such as signing certificates or cryptographic keys.
In conclusion, encountering an error message stating “the manifest for this application does not have a signature: signature validation will be ignored” is a concern for both developers and end-users. It indicates a potential security risk and challenges the trustworthiness of the application. Developers should ensure that their applications are properly signed, providing users with the confidence that they are downloading authentic and secure software. End-users, on the other hand, should exercise caution when using applications without valid signatures, prioritizing applications from trusted sources to mitigate potential risks.
Images related to the topic deployment and application do not have matching security zones

Found 30 images related to deployment and application do not have matching security zones theme



















Article link: deployment and application do not have matching security zones.
Learn more about the topic deployment and application do not have matching security zones.
- Deployment and Application Do Not … – Position Is Everything
- Deployment and Application do not have matching Security …
- How To Fix “Deployment And Application Do Not Have …
- Exchange hybrid configuration wizard with the error …
- Fix Deployment and Application do not have Matching …
- Deployment and application do not have matching security …
- Per-site configuration by policy | Microsoft Learn
- Change Internet Explorer Security settings – Microsoft
- Deployment and application do not have matching security …
- Error: Deployment and application do not have matching …
- Deployment and application do not have matching security …
See more: nhanvietluanvan.com/luat-hoc