Certificate Signed By Unknown Authority
I. Definition and Explanation of Unknown Authority
In the digital world, certificates serve as a means of establishing trust and authenticity. Certificate Authorities (CAs) are trusted third-party entities that issue these certificates to confirm the identity of individuals, organizations, or websites. However, when a certificate is signed by an unknown authority, it means that the CA’s signature cannot be verified or recognized. This raises concerns about the legitimacy and trustworthiness of the certificate.
II. Reasons for Certificates Signed by Unknown Authority
Certificates signed by unknown authorities can occur for various reasons. One common reason is when an organization or individual attempts to create self-signed certificates without any validation from a trusted CA. This might be due to cost constraints, lack of knowledge, or simply a disregard for security protocols. Additionally, it can also happen when an attacker manipulates or forges a certificate, thereby bypassing the CA verification process.
III. Potential Consequences of Certificates Signed by Unknown Authority
Certificates signed by unknown authorities pose significant risks to both individuals and organizations. Firstly, these certificates are highly vulnerable to being exploited by attackers. They can be used to conduct phishing attacks, where malicious actors impersonate trusted entities to deceive users into sharing sensitive information. Moreover, such certificates can facilitate man-in-the-middle attacks, enabling attackers to intercept and alter communication between two parties without their knowledge.
IV. Risks and Dangers of Accepting Certificates Signed by Unknown Authority
Accepting certificates signed by unknown authorities can have severe implications. When a user encounters a certificate signed by an unknown authority, their web browser or system will issue a warning. This warning indicates that the certificate cannot be trusted and that connecting to or interacting with the website or application may compromise security. Ignoring these warnings and proceeding with the connection exposes users to potential data breaches, identity theft, and malware infections.
V. Steps to Verify the Authenticity of Certificates Signed by Unknown Authority
While it may be tempting to circumvent security warnings and proceed with accessing a website or application, it is crucial to verify the authenticity of certificates. Here are some steps to follow:
1. Contact the website or organization: If the certificate belongs to a website you are trying to access, reach out to their support or customer service to confirm the validity of the certificate.
2. Check for revoked certificates: Use tools like Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP) to determine if the certificate has been revoked or compromised.
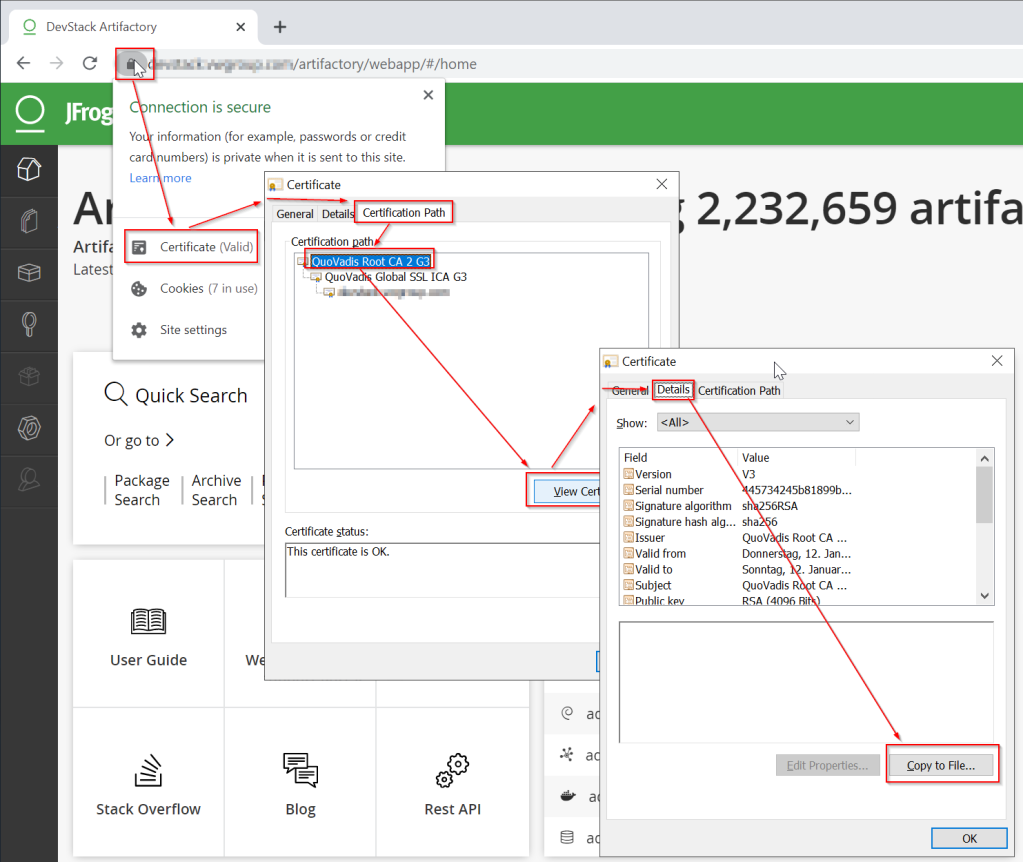
3. Perform a domain and certificate analysis: Utilize online tools to analyze the certificate’s metadata, including its subject, issuer, and validity period. Look for any discrepancies or red flags.
4. Seek expert advice: Consult with cybersecurity professionals or IT experts for guidance on validating the certificate and ensuring the safety of your digital interactions.
VI. The Role of Trusted Certificate Authorities in Ensuring the Legitimacy of Certificates
Trusted Certificate Authorities play a crucial role in maintaining the integrity of certificates. When a CA issues a certificate, it confirms that the entity or website possessing the certificate is legitimate and can be trusted. CAs follow rigorous verification processes, checking the applicant’s identity and domain ownership, before issuing a certificate. By relying on these trusted entities, users can confidently navigate the digital landscape and establish secure connections.
VII. Measures to Protect Against Fraudulent Certificates and Unknown Authorities
To protect against fraudulent certificates and unknown authorities, it is essential to follow these best practices:
1. Regularly update and patch software: Keep your operating system, web browser, and other applications up to date with the latest security patches to guard against known vulnerabilities.
2. Use reputable and up-to-date security software: Install and regularly update antivirus and anti-malware software to detect and prevent potential threats.
3. Exercise caution while browsing: Be vigilant when clicking on links, downloading files, or sharing personal information. Verify the website’s legitimacy and look for secure connections (HTTPS) indicated by the padlock symbol.
4. Educate yourself and your employees: Stay informed about the latest cybersecurity threats and train your team to identify and report suspicious certificates or websites.
VIII. Legal Implications of Certificates Signed by Unknown Authority
From a legal standpoint, accepting certificates signed by unknown authorities can expose individuals and organizations to liability. If a breach or security incident occurs due to negligence in verifying certificates, legal consequences may ensue. Additionally, if certificate-related vulnerabilities are exploited to compromise personal or sensitive data, compliance with data protection regulations could be called into question.
IX. Cases and Examples of Certificates Signed by Unknown Authority
Below are some examples of situations where “certificate signed by unknown authority” errors may be encountered:
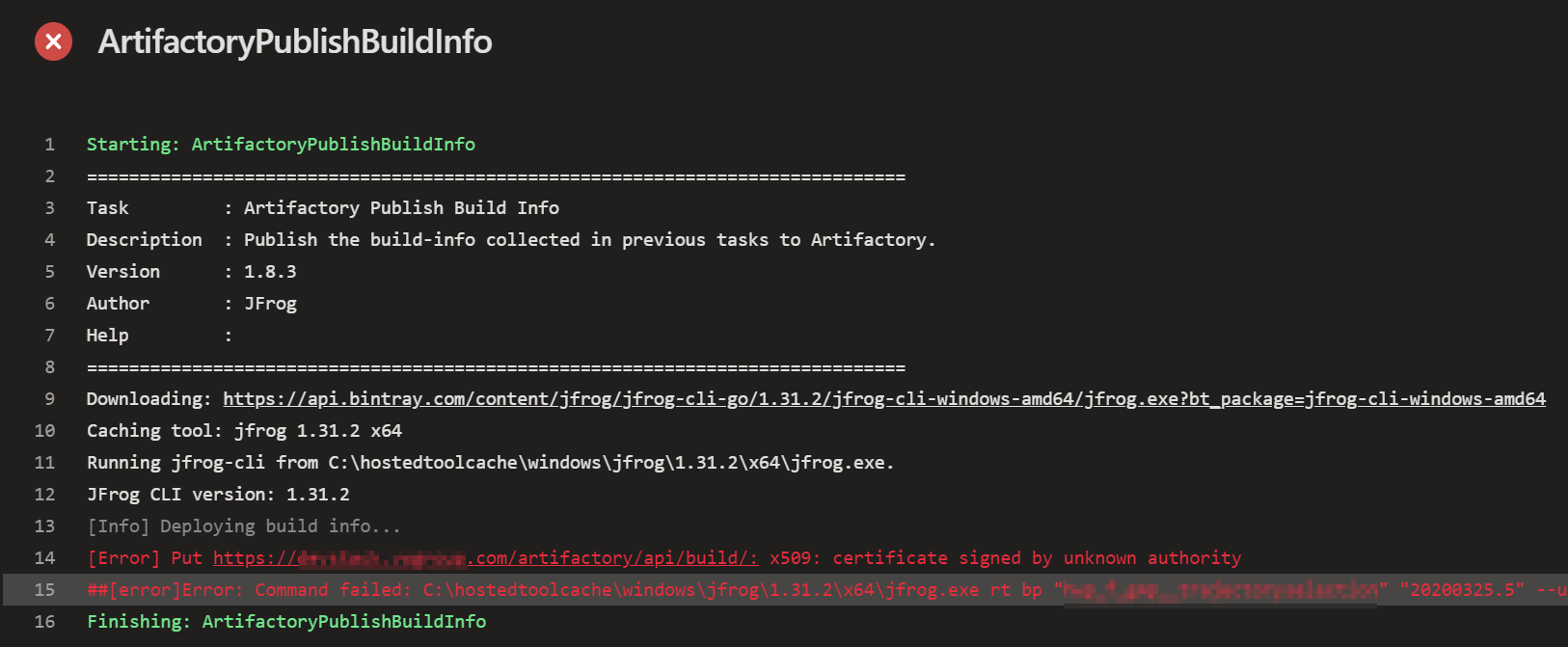
– x509: certificate signed by unknown authority docker: This error occurs when a Docker container attempts to pull an image from a registry using an SSL/TLS certificate that is not recognized by the system’s trust store.
– X509: certificate signed by unknown authority Ubuntu: Ubuntu users may encounter this error while attempting to connect to certain websites or repositories that have self-signed or untrusted certificates.
– x509: certificate signed by unknown authority harbor: This error is commonly seen in the context of container image registries, such as Harbor, when the SSL/TLS certificate used by the registry is not trusted.
– Kubernetes pull image x509: certificate signed by unknown authority: In Kubernetes clusters, this error occurs when a pod tries to pull an image from a registry with an untrusted or self-signed certificate.
– X509: certificate signed by unknown authority gitlab-runner: GitLab CI/CD pipelines may encounter this error when trying to download dependencies or artifacts from sources with untrusted certificates.
– Tls: failed to verify certificate: x509: certificate signed by unknown authority: This error can occur in various scenarios where a TLS connection is attempted with a server presenting an untrusted certificate.
– Unable to connect to the server: x509: certificate signed by unknown authority: This error often appears when trying to establish secure connections with network devices or services that have untrusted certificates.
Certificates signed by unknown authorities can cause significant disruptions and pose security risks. It is crucial for individuals and organizations to understand the implications and take necessary precautions to protect themselves from potential threats. By diligently verifying certificates and relying on trusted authorities, we can navigate the digital landscape with confidence and security.
Generate X.509 Certificates Using Openssl
What Does Certificate Signed By Unknown Authority Mean?
In today’s digital age, securing information online is of utmost importance. Websites and web applications often use encryption to protect sensitive data being transmitted over the internet. One critical element of this security is the use of SSL/TLS certificates, which validate the identity of a website and encrypt the data exchanged between a user and the site. However, there are instances where users may come across a message stating, “Certificate signed by unknown authority.” This article aims to dive into this issue and shed light on what it means when a certificate is signed by an unknown authority.
SSL/TLS Certificates and Certificate Authorities:
To understand the concept of certificates signed by unknown authorities, we need to first grasp the basis of SSL/TLS certificates and the role of Certificate Authorities (CAs). An SSL/TLS certificate is a small data file that cryptographically binds an organization’s details to a unique cryptographic key. This certificate is issued by a trusted third party known as a Certificate Authority.
Certificate Authorities are trusted entities that verify the authenticity of the information provided by an organization applying for an SSL/TLS certificate. These CAs establish trust through rigorous checks and balances to ensure that the certificate applicant owns or has control over the domain for which they are requesting a certificate. When a CA performs these checks and verifies the provided information, it digitally signs the certificate, indicating that it can be trusted.
Unknown Authorities and Untrusted Certificates:
Unfortunately, not all certificates go through this stringent verification process, leading to the existence of certificates signed by unknown authorities. This could happen in cases where a website owner may choose to generate their own self-signed certificate or use a lesser-known CA that is not universally trusted. When users come across such certificates, their web browsers display a warning message indicating that the certificate is signed by an unknown authority or is untrusted. This warning acts as a safeguard for users, notifying them that the authenticity of the certificate cannot be fully validated, and there may be potential security risks involved.
Security Risks Associated with Unknown Authorities:
Certificates signed by unknown authorities pose certain security risks that users need to be aware of. Since these certificates lack the validation from trusted CAs, they can be created by malicious individuals or entities, misleading users into believing they are connected to a legitimate website. Attackers could use such certificates to conduct man-in-the-middle attacks, intercepting and manipulating sensitive data being transmitted between the user and the website. Therefore, it is essential for users to exercise caution when encountering untrusted certificates and consider the potential security implications before proceeding.
FAQs:
Q: Can I trust a website with a certificate signed by an unknown authority?
A: While it may be tempting to ignore the warning and proceed to the website, it is generally recommended not to trust websites with untrusted certificates. To ensure your data’s security, it is best to stick to websites with trusted certificates.
Q: Are all unknown authorities untrustworthy?
A: Not necessarily. While some unknown authorities may be legitimate, the lack of widespread trust makes it challenging to discern the authenticity of their certificates. It is advisable to exercise caution when encountering unknown authorities.
Q: Can I still access a website with an untrusted certificate?
A: Web browsers typically allow users to proceed to websites with untrusted certificates by acknowledging the risks involved. However, it is crucial to be aware of the potential security risks and only proceed if you trust the website and understand the potential consequences.
Q: How can I ensure the security of my data when encountering an untrusted certificate?
A: It is advisable to refrain from entering any sensitive information on websites with untrusted certificates. Instead, look for alternative websites with trusted certificates to ensure the security of your data.
Q: Can website owners resolve the “certificate signed by unknown authority” warning?
A: Yes, website owners can choose to obtain an SSL/TLS certificate from a trusted certificate authority recognized by major web browsers to avoid the warning message. By doing so, they can provide a secure connection to their users and establish trustworthiness.
In conclusion, encountering a certificate signed by an unknown authority signifies that the certificate lacks validation from a trusted Certificate Authority. Users need to exercise caution when facing such warnings, as untrusted certificates can pose significant security risks. It is always recommended to rely on websites with trusted certificates to ensure the protection of sensitive data and guard against potential cyber threats.
What Is X509 Certificate Signed By Unknown Authority?
In the realm of digital security, X509 certificates serve as an essential tool to establish trust and encrypt data over the internet. These certificates are issued by Certification Authorities (CAs) to verify the authenticity of a website or digital entity. However, encountering an X509 certificate signed by an unknown authority can be a cause for concern. This article will delve into the details of what it means to encounter such a certificate and explore the implications it carries.
Understanding X509 Certificates:
Before delving into the concept of an X509 certificate signed by an unknown authority, it is crucial to comprehend the purpose and structure of these certificates.
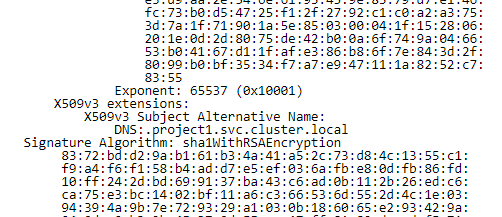
An X509 certificate is a digital document that binds a public key to an identity, typically associated with a website or online service. It contains information such as the entity’s name, public key, and details of the Certification Authority responsible for issuing the certificate.
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols rely heavily on X509 certificates to verify the authenticity of websites and secure sensitive communications. When a user initiates an encrypted connection, the server presents its X509 certificate. The client’s web browser, or any other software that implements SSL/TLS protocols, then validates the certificate by checking its signature against the trusted root certificates stored locally.
Unknown Authority: A Cause for Concern
When encountering an X509 certificate signed by an unknown authority, it implies that the client’s web browser or software failed to verify the certificate’s authenticity. As a result, it raises suspicion about the legitimacy of the website or service being accessed. The cause for such an unknown authority may vary and could indicate potential security risks. These risks could include issues such as server misconfiguration, man-in-the-middle attacks, or attempted phishing.
Possible Causes for X509 Certificates Signed by Unknown Authorities:
There are multiple scenarios that can lead to the appearance of an X509 certificate signed by an unknown authority:
1. Self-signed Certificate: Sometimes, website administrators generate self-signed certificates for testing purposes or when SSL/TLS is deployed in local network setups. As these certificates are not issued by a trusted CA, they are considered “self-signed” and will be flagged by clients as signed by an unknown authority.
2. Expired or Revoked Certificate: X509 certificates have an expiration date, and if not renewed, they become invalid. Similarly, if a certificate is compromised, stolen, or no longer trusted, it may be revoked. In such cases, the certificate will be treated as signed by an unknown authority.
3. Certification Authority Not Trusted: Every web browser and other software that handles SSL/TLS maintain a list of trusted CAs, known as root certificates. If the issuing Certification Authority isn’t part of this trusted list, the client will consider the certificate as signed by an unknown authority.
4. Malicious Attack: In certain cases, encountering an X509 certificate signed by an unknown authority might indicate a malicious attack, usually through a man-in-the-middle (MITM) scenario. Attackers can intercept traffic and present a forged certificate to trick users into revealing sensitive information. This highlights the importance of validating the authority behind an X509 certificate to avoid falling victim to such attacks.
FAQs:
Q: Should I trust a website with an X509 certificate signed by an unknown authority?
A: Trusting a website with an X509 certificate signed by an unknown authority is not recommended. It is crucial to exercise caution and investigate further to ensure the security of your communications.
Q: How can I verify the legitimacy of an X509 certificate?
A: You can verify the legitimacy of an X509 certificate by checking if it is signed by a trusted Certification Authority. Pay attention to the certificate’s details, including its expiration date, issuing CA, and any warnings or error messages from your browser or security software.
Q: What should I do if I encounter an X509 certificate signed by an unknown authority?
A: If you encounter an X509 certificate signed by an unknown authority, it is advisable to avoid proceeding further as it may pose a security risk. Contact the website administrator or service provider for clarification, or consider using an alternative trusted source.
Q: Are self-signed certificates always dangerous?
A: Self-signed certificates are not inherently dangerous, but they lack the guarantee of authenticity provided by trusted CAs. Using self-signed certificates in secure production environments is generally discouraged, as it can make users vulnerable to various attacks.
Q: How can websites avoid having X509 certificates signed by an unknown authority?
A: Websites can avoid having X509 certificates signed by an unknown authority by obtaining valid certificates from trusted CAs. Ensuring that certificates are properly installed, not expired, and serving them through secure protocols (i.e., HTTPS) are crucial steps to maintain trustworthiness.
Conclusion:
Encountering an X509 certificate signed by an unknown authority can raise concerns about the legitimacy and security of a website or online service. It is essential to verify the validity of a certificate before proceeding with secure communications. By familiarizing ourselves with the causes and implications of encountering such certificates, we can stay vigilant and safeguard our online interactions.
Keywords searched by users: certificate signed by unknown authority x509: certificate signed by unknown authority docker, X509: certificate signed by unknown authority Ubuntu, x509: certificate signed by unknown authority harbor, kubernetes pull image x509: certificate signed by unknown authority, X509: certificate signed by unknown authority gitlab-runner, Failed to pull image x509: certificate signed by unknown authority, Tls: failed to verify certificate: x509: certificate signed by unknown authority, Unable to connect to the server: x509: certificate signed by unknown authority
Categories: Top 50 Certificate Signed By Unknown Authority
See more here: nhanvietluanvan.com
X509: Certificate Signed By Unknown Authority Docker
In the world of software development and deployment, security is of paramount importance. Docker, which has revolutionized the way we build, ship, and run applications, is no exception. Docker helps package applications into containers, ensuring consistency and portability across different environments. To ensure secure communication between Docker containers, X.509 certificates are widely used. However, sometimes you may encounter the issue of a “certificate signed by unknown authority” in Docker. In this article, we will delve into the details of this problem, understand its causes, and explore possible solutions.
What is X.509?
X.509, developed by the International Telecommunication Union (ITU-T), is a widely adopted standard for public key infrastructure (PKI) certificates. It is used to authenticate and secure communication channels in various applications, including web servers, email systems, and virtual private networks (VPNs). X.509 certificates contain information such as the certificate holder’s name, public key, and digital signature.
The “Certificate signed by unknown authority” Error
Docker, being a containerization platform, offers the option to secure communication channels between containers using SSL/TLS encryption via X.509 certificates. However, when a certificate cannot be verified by the Docker engine, it raises the error message “Error response from daemon: x509: certificate signed by unknown authority.”
This error occurs when a Docker container tries to communicate with another container or an external service that presents a certificate signed by an unknown or untrusted certificate authority (CA). The CA is responsible for verifying the authenticity of the certificate and is trusted by the Docker engine.
Causes of the Error
There are several possible causes for the “certificate signed by unknown authority” error:
1. Self-signed certificates: If the certificate presented by the external service or container is self-signed, meaning it is not signed by a trusted CA, Docker will raise the error.
2. Untrusted certificate authority: If the certificate presented by the external service or container is signed by a CA that is not trusted by the Docker engine, the error will occur.
3. Misconfiguration: If there is a misconfiguration in the Docker engine or container, such as incorrect certificate paths or missing CA certificates, it can result in the “certificate signed by unknown authority” error.
Resolving the Issue
To resolve the “certificate signed by unknown authority” error, there are a few potential solutions:
1. Trust the certificate authority: If the certificate is signed by a trusted CA, you can add the CA certificate to the Docker engine’s trust store. This can be done by copying the CA certificate to the “/etc/docker/certs.d/” directory or by using the “docker trust” command.
2. Disable certificate verification: Although not recommended for production environments, you can disable certificate verification within Docker by configuring the “insecure-registries” option with the “–insecure-registry” flag.
3. Provide a valid certificate: If the certificate is self-signed or signed by an untrusted CA, obtaining a valid certificate signed by a trusted CA is the best solution. This ensures secure communication and eliminates the “certificate signed by unknown authority” error.
4. Verify container and Docker engine configuration: Check the configuration of the Docker engine and container to ensure proper certificate paths, CA certificates, and other relevant configurations are correctly set.
FAQs
Q1. Can I use self-signed certificates in Docker for production environments?
Ans. While it is technically possible to use self-signed certificates in Docker, it is not recommended for production environments. Self-signed certificates lack the cryptographic validation provided by trusted CAs, making them susceptible to man-in-the-middle attacks.
Q2. How can I obtain a valid certificate signed by a trusted CA?
Ans. To obtain a valid certificate signed by a trusted CA, you can reach out to a reputable CA provider, either public or private, and follow their certificate issuance process. This usually involves proving your domain ownership and providing necessary documentation.
Q3. I renewed my certificate, but Docker still raises the error. What should I do?
Ans. When you renew a certificate, it is essential to replace the old certificate with the new one in the Docker engine’s trust store. Ensure that the new certificate is properly configured and accessible within the Docker environment.
Q4. Can I use my own CA certificate to sign Docker-generated certificates?
Ans. Yes, Docker allows you to use your own CA certificate to sign Docker-generated certificates. By configuring the Docker engine to trust your CA certificate, you can ensure that the Docker-generated certificates are accepted by the Docker engine.
In conclusion, the “certificate signed by unknown authority” error in Docker can be a roadblock when establishing secure communication channels. By understanding the causes and implementing the appropriate solutions, you can overcome this issue and ensure secure and uninterrupted Docker container communication. Remember to prioritize security and use valid certificates signed by trusted certificate authorities to safeguard your containers and applications.
X509: Certificate Signed By Unknown Authority Ubuntu
Introduction:
In the world of secure communication on the internet, X509 certificates play a key role. These certificates are used to authenticate and verify the identity of various entities, such as websites and servers. However, encountering an X509 certificate signed by an unknown authority error on Ubuntu can be quite frustrating. In this article, we will delve into the details of what an X509 certificate is, how it works, and discuss troubleshooting steps to resolve the “certificate signed by unknown authority” error on Ubuntu.
Understanding X509 Certificates:
An X509 certificate is a digital document that is issued by a trusted Certificate Authority (CA). It contains information about the entity it is issued to, including their public key and digital signature. It provides a means of verifying the identity and authenticity of the entity it represents. When connecting to a website, for example, the browser checks the X509 certificate presented by the server to ensure it has been issued by a trusted CA, indicating that the website can be trusted.
What Causes the “Certificate Signed by Unknown Authority” Error?
When browsing the internet or accessing secured resources on Ubuntu, you may sometimes encounter an error stating “certificate signed by unknown authority.” This error typically occurs when the server’s X509 certificate is signed by a certificate authority that is not recognized or trusted by your operating system. This can happen due to various reasons, including self-signed certificates, expired certificates, or certificates signed by CA’s that are not included in the default trusted CA list on Ubuntu.
Resolving the “Certificate Signed by Unknown Authority” Error:
If you encounter this error, there are a few troubleshooting steps you can follow to resolve it:
1. Update the CA Certificates:
Start by ensuring that your operating system’s trusted Certificate Authority (CA) certificates are up to date. On Ubuntu, this can be done by running the following command:
`sudo apt update && sudo apt install ca-certificates`
This command will update the CA certificates package, which includes a list of trusted CAs.
2. Import the Root CA Certificate:
If the certificate error is caused by a self-signed certificate or a certificate issued by an unrecognized CA, you can manually import the root CA certificate into your system’s trusted store. To do this, follow these steps:
a. Obtain the root CA certificate from the server or website you are trying to access. This can typically be downloaded from the website itself.
b. Open the Ubuntu “Settings” and go to “Privacy & Security.”
c. Under the “Certificates” tab, click on “Manage Certificates.”
d. In the Certificate Manager, go to the “Authorities” tab and click on “Import.”
e. Locate the root CA certificate file and import it into the trusted authorities.
By importing the root CA certificate, you are explicitly trusting the certificate authority responsible for signing the server’s certificate.
FAQs (Frequently Asked Questions):
Q: What is a self-signed certificate, and why does it cause the “certificate signed by unknown authority” error?
A: A self-signed certificate is a certificate that is signed by itself instead of a trusted Certificate Authority (CA). Since it is not issued by a recognized CA, it is considered untrusted by default, leading to the “certificate signed by unknown authority” error.
Q: What should I do if the error persists even after updating CA certificates and importing the root CA certificate?
A: If the error persists, it may indicate a more severe security issue, such as a possible man-in-the-middle attack. In such cases, it is recommended to avoid accessing the website or server until the issue is resolved. Contact the website administrator or network administrator for further assistance.
Q: Can I disable the “certificate signed by unknown authority” error notification?
A: Disabling the error notification is not recommended as it compromises the security of your system. Certificates play a critical role in ensuring the authenticity and security of online communications. Disabling or ignoring certificate errors may expose you to potential security threats.
Conclusion:
Encountering the “certificate signed by unknown authority” error on Ubuntu can be frustrating, but it can usually be remedied by updating the CA certificates or importing the root CA certificate into your trusted store. It is essential to remember that certificates play a vital role in ensuring secure communication on the internet, and ignoring certificate errors can put your security at risk. Stay vigilant and follow the troubleshooting steps outlined in this article to resolve the issue and ensure a safe browsing experience.
Images related to the topic certificate signed by unknown authority

Found 45 images related to certificate signed by unknown authority theme
























![DirectAdmin] Fix certificate signed by unknown authority Certificate generation failed Directadmin] Fix Certificate Signed By Unknown Authority Certificate Generation Failed](https://www.itcweb.net/Images/Posts/637919379535204104_directadmin-fix-certificate-signed-by-unknown-authority-certificate-generation-failed.jpg)





![Fixed] X509: Certificate Signed by Unknown Authority( Running a docker application on an AWS Ec2 instance) | by Chetan Pandey | Medium Fixed] X509: Certificate Signed By Unknown Authority( Running A Docker Application On An Aws Ec2 Instance) | By Chetan Pandey | Medium](https://miro.medium.com/v2/resize:fit:760/1*ltk5eGDjLVH7bHiGGCHzpA.png)








Article link: certificate signed by unknown authority.
Learn more about the topic certificate signed by unknown authority.
- “docker pull” certificate signed by unknown authority
- x.509 certificate là gì? Cách khắc phục lỗi x.509 … – SSL.VN
- Directamin – x509: certificate signed by unknown authority
- ERROR: x509: certificate signed by unknown authority error is …
- How to Fix the “X.509 Certificate Signed by Unknown Authority …
- Resolve “Certificate Signed By Unknown Authority” error in Alpine …
- X509 Certificate Signed by Unknown Authority: Causes & Fixes
- Docker x509: certificate signed by unknown authority | Resolved
- ERROR: x509: certificate signed by unknown authority error is …
- X509 Certificate Signed by Unknown Authority: Causes & Fixes
- How to fix Docker error certificate signed by unknown authority …
- Docker Private Registry: x509: certificate signed by unknown …
- Certificate signed by unknown authority – How to troubleshoot …
- Lưu trữ Top 88 X509: Certificate Signed By Unknown Authority