Docker Build X509 Certificate Signed By Unknown Authority
x509 certificates are digital certificates that serve as a crucial component in ensuring secure communication over networks such as the internet. They are widely used in various applications, including web servers, email systems, and virtual private networks (VPNs). The x509 certificate format is an industry standard defined by the International Telecommunication Union (ITU) and specifies the content and structure of a digital certificate.
Overview of x509 Certificates
x509 certificates contain information about the identity of an entity, such as a website or an individual, and provide a means for verifying their authenticity. The certificate includes details such as the common name (CN) of the entity, the issuer, the certificate’s validity period, and a public key. This information is digitally signed by a certificate authority (CA) to establish the trustworthiness of the certificate.
Role and Importance of x509 Certificates in Secure Communication
x509 certificates play a vital role in establishing secure communication between two entities. When a client connects to a server, the server presents its x509 certificate, allowing the client to verify the server’s identity and public key. This verification process is essential in preventing man-in-the-middle attacks, where an attacker intercepts the communication and poses as the server.
Furthermore, x509 certificates enable encrypted communication using technologies like Transport Layer Security (TLS) or Secure Sockets Layer (SSL). These protocols leverage the information stored in the certificate to initiate a secure connection and encrypt the transmitted data, ensuring confidentiality and integrity.
Docker Build Process
Introduction to Docker Build Process
Docker is a popular containerization platform that allows developers to package applications and their dependencies into lightweight and portable containers. The Docker build process enables the creation of these containers by executing a series of instructions defined in a Dockerfile.
Utilizing x509 Certificates in Docker Build
The Docker build process can involve fetching external resources, such as packages or base images, from remote repositories. To ensure the authenticity and integrity of these resources, Docker can utilize x509 certificates for secure communication with the repositories.
By configuring Docker to trust the CA that issued the x509 certificate used by the repository, the build process can verify the authenticity of the resources. This provides an additional layer of security and mitigates the risk of downloading compromised or tampered packages.
Importance of Properly Configuring Certificates in Docker Build
Properly configuring x509 certificates in the Docker build environment is crucial for ensuring the security and integrity of the built containers. Failure to configure certificates correctly can result in the “x509 certificate signed by unknown authority” error, indicating that Docker cannot verify the authenticity of a certificate.
Common Causes of “x509 Certificate Signed by Unknown Authority” Error
Invalid or Misconfigured Certificates
One of the common causes of the “x509 certificate signed by unknown authority” error is using invalid or misconfigured certificates in the Docker build environment. This error occurs when the certificate presented by the remote repository does not match the expected certificate or does not have a trusted root authority.
Expired or Revoked Certificates
Another possible cause of the error is using expired or revoked certificates. Certificates have a defined validity period, and if a certificate used in the Docker build process has expired or has been revoked, Docker will raise the “x509 certificate signed by unknown authority” error.
Self-Signed Certificates without Trusted Root Authority
If the certificate used in the Docker build process is self-signed and does not have a trusted root authority, it will also result in the “x509 certificate signed by unknown authority” error. Self-signed certificates are not automatically trusted by Docker, as they lack the validation provided by a trusted CA.
Troubleshooting and Resolving the Issue
Verifying the Certificate Chain
To troubleshoot the “x509 certificate signed by unknown authority” error, it is essential to verify the certificate chain. This involves checking if the presented certificate can be traced back to a trusted root authority. Tools like OpenSSL can be used to examine the certificate and validate its chain.
Updating Root Certificate Authorities
If the certificate chain is valid, but the root certificate authority is not recognized by Docker, updating Docker with the appropriate root certificate authority can resolve the issue. Docker uses the system’s trusted root certificates for validation, so updating the system’s certificate store may be necessary.
Manually Trusting Certificates
In cases where the presented certificate cannot be automatically validated, manually trusting the certificate in Docker can be a workaround. This involves adding the certificate to Docker’s trust store to establish its authenticity. However, this should be done cautiously, as manually trusting certificates can introduce security risks if not handled properly.
Disabling Certificate Validation (Not Recommended)
As a last resort, disabling certificate validation in Docker can bypass the “x509 certificate signed by unknown authority” error. However, this approach compromises the security of the build environment, as it allows potentially unverified certificates to be trusted. Disabling certificate validation should only be used temporarily for troubleshooting purposes and not as a long-term solution.
Best Practices for Docker Build and x509 Certificates
Regular Certificate Maintenance and Renewal
To avoid issues with x509 certificates in the Docker build process, regular maintenance and renewal of certificates are essential. Monitoring the validity periods of certificates and renewing them before expiration helps ensure uninterrupted and secure communication with external resources.
Proper Certificate Configuration in Docker Build Environment
Properly configuring certificates in the Docker build environment is crucial for secure communication. This includes ensuring that the correct certificates are used and that they have trusted root authorities. Certificates should be obtained from reputable CAs and properly installed in Docker and the underlying operating system.
Validation and Verification of Certificates
Validating and verifying x509 certificates used in Docker builds can prevent potential security risks. It is important to ensure that all certificates are properly issued, have valid dates, and are signed by trusted authorities. Regular checks and audits of certificates can help identify and resolve any potential issues.
Potential Risks and Mitigation Strategies
Risks of Ignoring Certificate Validation Issues
Ignoring certificate validation issues in the Docker build process can expose the environment to various security risks. A compromised or untrusted certificate can lead to the installation of malicious or tampered packages, compromising the integrity of the built containers.
Implementing Strict Certificate Validation Policies
To mitigate security risks, organizations should implement strict certificate validation policies in their Docker build environments. This includes using certificates issued by trusted authorities, regularly renewing certificates, and ensuring that the entire certificate chain is valid and recognized.
Monitoring and Auditing Containerized Environments for Security Compliance
Regular monitoring and auditing of containerized environments can help ensure compliance with security standards. This includes verifying that Docker build processes adhere to proper certificate validation practices and detecting any anomalies or potential security breaches.
FAQs
Q: What is the “x509 certificate signed by unknown authority” error?
A: The “x509 certificate signed by unknown authority” error occurs when Docker cannot validate the authenticity of a certificate presented by a remote repository.
Q: How can I troubleshoot the “x509 certificate signed by unknown authority” error?
A: Troubleshooting steps include verifying the certificate chain, updating root certificate authorities, manually trusting certificates, and, as a last resort, disabling certificate validation (not recommended).
Q: What are the common causes of the “x509 certificate signed by unknown authority” error?
A: Common causes include using invalid or misconfigured certificates, expired or revoked certificates, and self-signed certificates without trusted root authority.
Q: How can I prevent the “x509 certificate signed by unknown authority” error in Docker builds?
A: Best practices include regular certificate maintenance and renewal, proper certificate configuration in Docker build environments, and validation and verification of certificates.
Q: What are the potential risks of ignoring certificate validation issues in Docker builds?
A: Ignoring certificate validation issues can expose Docker builds to security risks, such as the installation of malicious or tampered packages, compromising the integrity of containers.
Q: How can organizations mitigate security risks related to Docker build and x509 certificates?
A: Mitigation strategies include implementing strict certificate validation policies, regularly monitoring and auditing containerized environments, and ensuring compliance with security standards.
Docker Private Registry With Self Signed Certificate
How To Bypass X509 Certificate Signed By Unknown Authority?
In the ever-growing digital landscape, security protocols play a vital role in safeguarding information and ensuring the safety of online transactions. One such security measure is the X509 certificate, which is used to verify and authenticate the identity of a website or server. However, there may be instances when you encounter an X509 certificate signed by an unknown authority. This situation can raise concerns about the authenticity of the certificate. In this article, we will explore what an X509 certificate is, the reasons for encountering an unknown authority, and various ways to bypass such certificates.
Understanding X509 Certificates
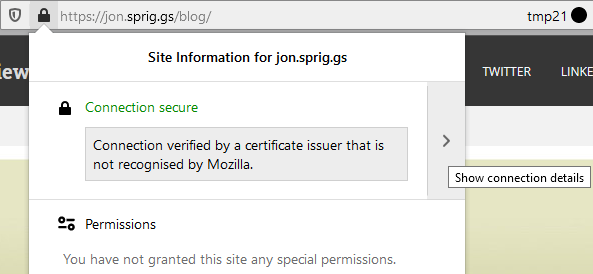
An X509 certificate is an electronic document issued by a trusted third party known as a Certification Authority (CA). It contains information about the entity or individual for whom it is issued, along with a unique digital signature that verifies its authenticity. These certificates are primarily used to secure online communication, authenticate websites, and establish secure connections between clients and servers.
Encountering an X509 Certificate Signed by an Unknown Authority
There can be specific scenarios when you come across an X509 certificate signed by an unknown authority. Some possible reasons for this include:
1. Self-Signed Certificates: In some cases, the certificate may have been self-signed, which means it was generated by the entity it represents without the involvement of a trusted CA. When encountering such certificates, your browser considers them as unknown authorities, as they do not match against a known CA’s list.
2. Expired or Revoked Certificates: Certificates come with an expiration date and can be revoked if compromised or no longer valid. If you encounter a certificate that has expired or been revoked, your browser will show it as signed by an unknown authority.
3. Certificate Chains: X509 certificates can be part of a chain, where each certificate in the chain is issued by the previous one. If your system does not have the complete chain or is missing an intermediate certificate, it may show the certificate as signed by an unknown authority.
Bypassing X509 Certificates Signed by Unknown Authorities
Although encountering an X509 certificate signed by an unknown authority might initially create a sense of distrust, there are legitimate cases where you may need to bypass these certificates. Below are a few methods to accomplish this:
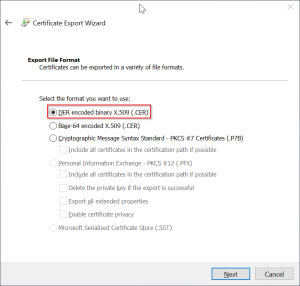
1. Importing the Certificate: If you trust the website or server in question, you can choose to import the certificate manually into your browser’s trust store. By doing so, you establish a direct trust relationship with the entity, allowing you to bypass the unknown authority warning.
2. Using a Different Browser: If the X509 certificate issue is specific to a particular browser, you can try accessing the website or server using an alternative browser. Sometimes, different browsers have different trust stores, and the certificate may be recognized as valid in one but not in another.
3. Adjusting Security Settings: Some browsers allow you to adjust security levels and customize certificate validation rules. If you are comfortable with it, you can tweak these settings to lessen the strictness of certificate verification temporarily. However, exercise caution when modifying security settings, as it may expose you to potential security risks.
4. Contacting the Website/Server Administrator: If you encounter an X509 certificate signed by an unknown authority on a website or server you frequently use, it may be worth reaching out to their administrator. They can verify the certificate’s authenticity and explain any changes or issues that might be causing the unknown authority warning.
FAQs
Q: Is it safe to bypass an X509 certificate signed by an unknown authority?
A: Bypassing a certificate signed by an unknown authority should be done cautiously. It may be safe in certain situations where you trust the website or server, but generally, it is recommended to investigate the certificate’s authenticity before bypassing it.
Q: Can bypassing these certificates lead to security risks?
A: Yes, bypassing certificates signed by unknown authorities can potentially expose you to security risks. These certificates lack the validation provided by trusted CAs, and bypassing them means you are accepting the risk of interacting with an entity whose identity cannot be fully verified.
Q: Are there other risks associated with bypassing X509 certificates?
A: Apart from the obvious security risks, bypassing X509 certificates can also lead to a lack of privacy. These certificates are an essential part of secure communication protocols, and bypassing them may compromise the confidentiality of your data.
Q: Are there tools available to verify the authenticity of unknown certificates?
A: Yes, several online tools allow you to verify the authenticity of certificates signed by unknown authorities. You can enter the certificate details, and these tools will provide insights into the certificate’s validity.
Q: Can bypassing an X509 certificate affect the server or website I am accessing?
A: Bypassing a certificate signed by an unknown authority does not directly impact the server or website. However, it removes a layer of security and can affect the integrity and confidentiality of your communication with that server or website.
Conclusion
Encountering an X509 certificate signed by an unknown authority can be a cause for concern. However, it is important to understand the reasons behind such certificates and weigh the risks associated with bypassing them. By following the methods mentioned above and exercising caution, you can navigate these situations while maintaining a balance between security and functionality in the digital realm.
What Is X509 Certificate Signed By Unknown Authority Inside Docker?
When it comes to securing communication between containers and external services in a Docker environment, x509 certificates play a crucial role. These certificates are used to authenticate the identity of the services involved in the communication, ensuring a secure and reliable connection. However, encountering an x509 certificate signed by an unknown authority can be a cause for concern and confusion. In this article, we will explore what it means to have an x509 certificate signed by an unknown authority inside Docker and how to address this issue effectively.
Understanding x509 Certificates:
Before diving into the intricacies of x509 certificates, it’s important to have a basic understanding of what they are. An x509 certificate is a digital document that helps to establish the identity of an entity, such as a website or a service. It contains information about the entity, including its public key and digital signature. The digital signature is generated by an authority, also known as a Certificate Authority (CA), to verify the authenticity of the certificate. By verifying the digital signature, one can ensure that the certificate hasn’t been tampered with and that the entity it represents is indeed authentic.
Certificate Authorities (CAs):
Certificate Authorities play a vital role in the generation and signing of x509 certificates. They act as trusted third parties that verify the identity of entities requesting certificates. CAs are responsible for signing certificates after performing necessary identity verification processes, ensuring that certificates issued by them are valid and trustworthy. Common examples of CAs are Let’s Encrypt, DigiCert, and GlobalSign.
Unknown Authority Error:
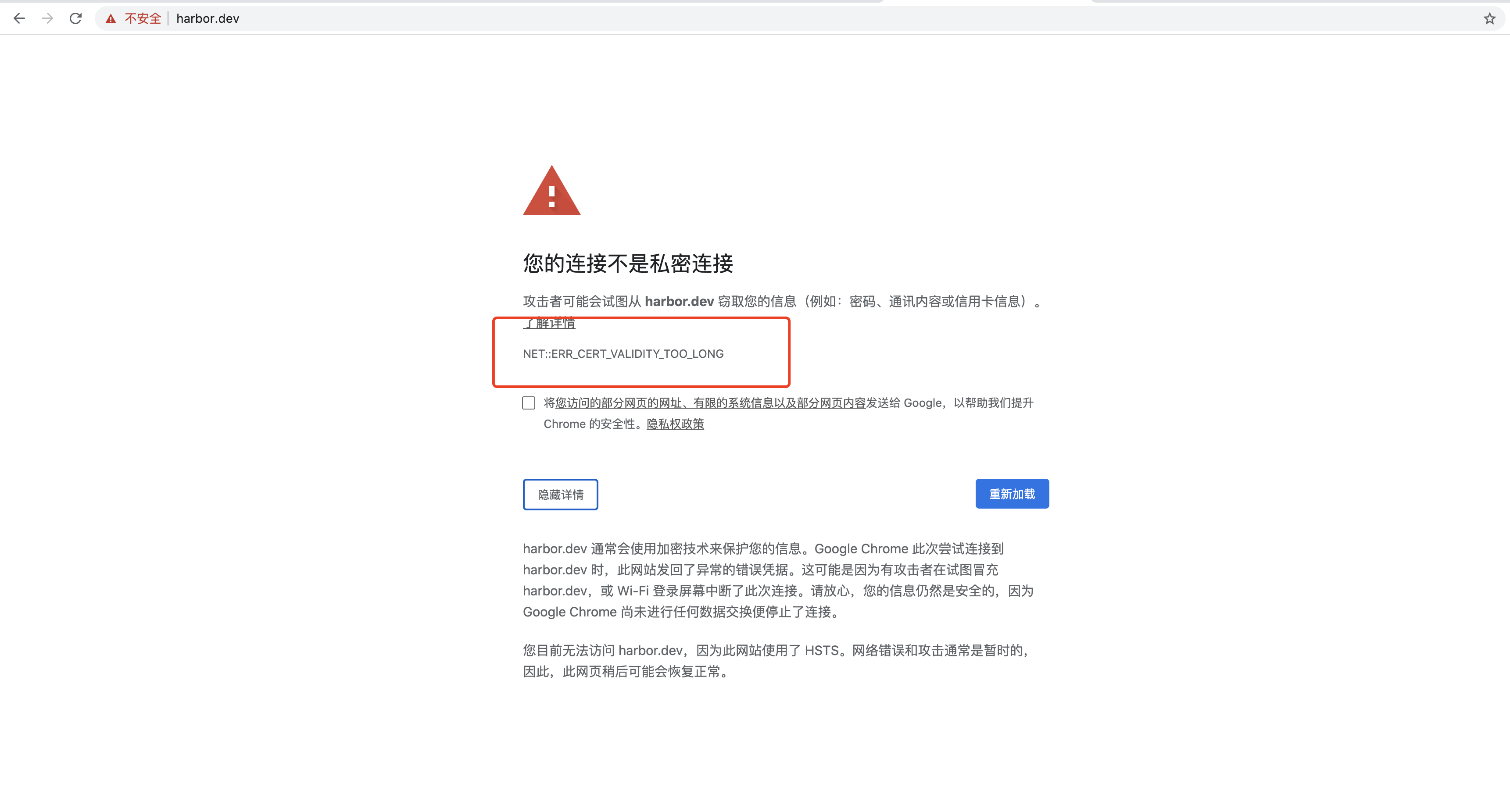
An x509 certificate signed by an unknown authority error occurs when a certificate presented by a service or website is signed by a CA that is not recognized as trusted by the system attempting to establish the connection. This error message often indicates a potential security risk, as the system cannot verify the authenticity and trustworthiness of the certificate presented. The unknown authority could result from using a self-signed certificate or a certificate signed by an unrecognized or untrusted CA.
Addressing the Unknown Authority Error:
To address the x509 certificate signed by an unknown authority error, several steps can be taken:
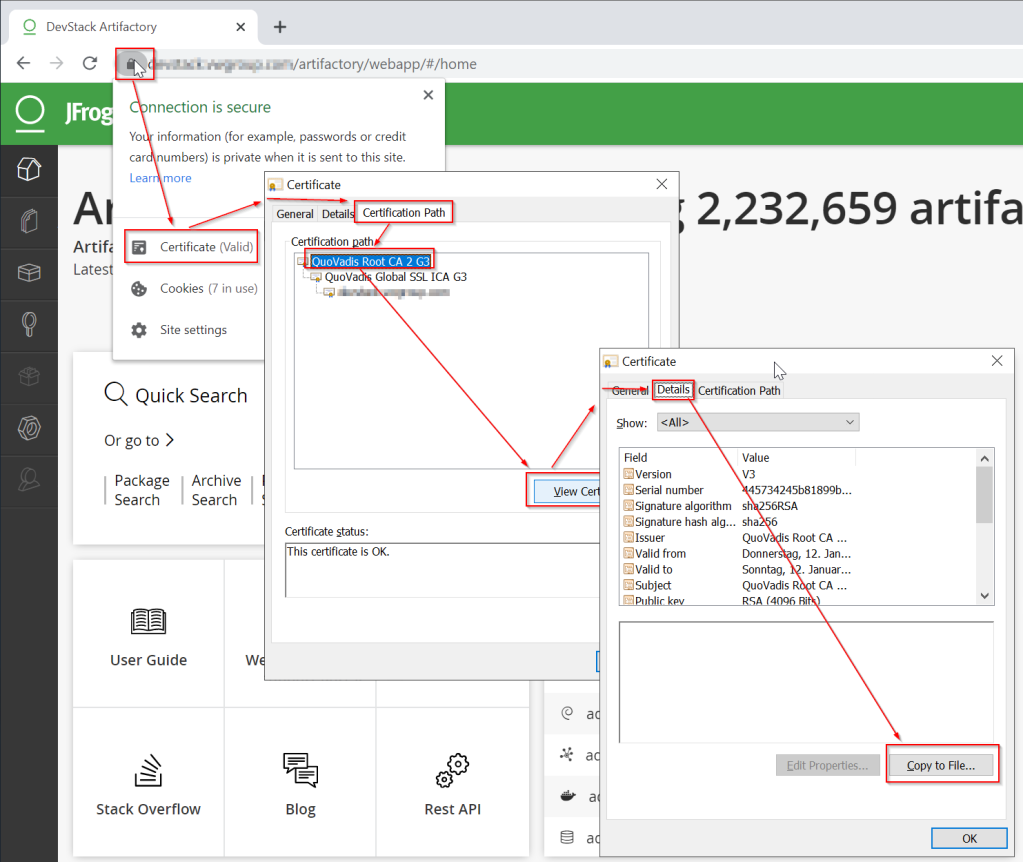
1. Verify the certificate: Before taking any action, it’s essential to verify the certificate presented. Check the certificate details, including the authority that issued it, the expiration date, and the common name (CN) or subject alternative names (SANs) it covers. Assessing the certificate’s details will help determine whether the error is due to an actual security risk or a misconfiguration.
2. Install the missing CA certificate: If the unknown authority error is due to an unrecognized CA, you can install the missing CA certificate into the system or Docker environment. This will allow the system to recognize and trust certificates signed by that particular CA. Care should be taken to ensure the CA certificate is obtained from a reliable source to avoid introducing potential security vulnerabilities.
3. Replace the certificate: In cases where the x509 certificate is self-signed or not signed by a trusted CA, it’s recommended to replace the certificate with one signed by a recognized and trusted CA. This will ensure the authenticity and trustworthiness of the certificate, reducing the risk of security breaches.
4. Update the trust store: Updating the trust store of the system or Docker environment can also help resolve the unknown authority error. A trust store contains a collection of CA certificates that the system recognizes and trusts. By adding the CA certificate to the trust store, the system can verify and trust certificates signed by that CA.
FAQs:
Q1. What should I do if I encounter an x509 certificate signed by an unknown authority in a Docker environment?
A1. Verify the certificate details, install the missing CA certificate if applicable, or replace the certificate with one signed by a trusted CA.
Q2. Can I ignore the unknown authority error and continue with the connection?
A2. While it’s technically possible, ignoring the error is not recommended as it may expose you to potential security risks.
Q3. How can I obtain a trusted CA certificate?
A3. Trusted CA certificates can be obtained from the CAs themselves or through reliable sources that provide bundled CA certificates.
Q4. Why do self-signed certificates result in the unknown authority error?
A4. Self-signed certificates are not signed by a trusted CA, leading to the unknown authority error. They typically raise security concerns due to the lack of third-party verification.
In summary, encountering an x509 certificate signed by an unknown authority inside Docker raises security concerns, as the authenticity and trustworthiness of the certificate cannot be verified. By properly assessing the certificate and taking necessary actions such as installing missing CA certificates or replacing the certificate, this issue can be effectively addressed, ensuring secure communication in a Docker environment.
Keywords searched by users: docker build x509 certificate signed by unknown authority X509: certificate signed by unknown authority docker desktop, X509: certificate signed by unknown authority Ubuntu, x509: certificate signed by unknown authority golang, kubernetes pull image x509: certificate signed by unknown authority, Docker x509 certificate is not valid for any names but wanted to match, Failed to pull image x509: certificate signed by unknown authority, X509: certificate has expired or is not yet valid, X509 certificate signed by unknown authority harbor
Categories: Top 70 Docker Build X509 Certificate Signed By Unknown Authority
See more here: nhanvietluanvan.com
X509: Certificate Signed By Unknown Authority Docker Desktop
In the world of software development and application deployment, Docker has become a popular choice for many developers, providing a convenient way to package and distribute applications in containers. Docker Desktop, the native desktop application of Docker, enables developers to build, test, and deploy containerized applications directly on their desktop. However, when working with Docker Desktop, you may encounter an issue with certificates, specifically the “Certificate Signed by Unknown Authority” error related to X509 certificates. In this article, we will delve into this topic, exploring what X509 certificates are, why they are important in the context of Docker Desktop, and how to resolve the “Certificate Signed by Unknown Authority” error.
What is an X509 certificate?
X509 is a standard format for public key certificates defined by the International Telecommunication Union (ITU) and ISO/IEC. It is widely used in various security protocols and applications, including SSL/TLS for secure communication over the web. X509 certificates serve as a digital identity for entities, such as websites or software applications, verifying their authenticity and establishing secure connections.
Why are X509 certificates important in Docker Desktop?
When Docker Desktop runs containers, it needs to establish secure connections with various components and services. This includes pulling images from public or private registries, communicating with remote Docker hosts, and interacting with the Docker daemon. X509 certificates play a crucial role in these interactions, ensuring that the connections are secure and the entities involved can be trusted.
The “Certificate Signed by Unknown Authority” error
One common issue that Docker Desktop users encounter is the “Certificate Signed by Unknown Authority” error. This error occurs when Docker Desktop tries to establish a secure connection or validate an X509 certificate, but it fails because the certificate is signed by an unknown or untrusted authority.
When encountering this error, Docker Desktop perceives the certificate as potentially insecure and refuses to establish the connection. This is a protective measure to prevent potential data breaches or unauthorized access.
Resolving the “Certificate Signed by Unknown Authority” error
Fortunately, there are a few steps you can follow to resolve this error and establish secure connections within Docker Desktop:
1. Identify the root cause: The first step is to identify the actual cause of the error. Check if the error is specific to a certain component or service. For example, if the error occurs when pulling images from a private registry, it is likely related to that specific registry’s certificate.
2. Obtain the root certificate: Once you have identified the source of the error, you need to obtain the root certificate or the certificate chain leading to the unknown authority. This can usually be obtained from the service or component provider.
3. Add the root certificate to Docker Desktop: To resolve the error, you need to add the obtained root certificate to Docker Desktop’s trusted certificate store. Docker Desktop maintains its own certificate store, separate from the system’s certificate store.
4. Restart Docker Desktop: After adding the root certificate, restart Docker Desktop to ensure the changes come into effect.
5. Verify the connectivity: Finally, verify if the error has been resolved by attempting the action that initially triggered the error. If the error no longer occurs, the issue is resolved.
FAQs:
1. Can I ignore the “Certificate Signed by Unknown Authority” error?
Ignoring the error is not recommended as it compromises the security and integrity of the connections established by Docker Desktop. It is important to resolve the error to ensure secure communication and prevent potential security breaches.
2. Does every X509 certificate cause this error?
No, the error occurs only when Docker Desktop encounters a certificate signed by an unknown or untrusted authority. Certificates signed by trusted authorities, such as well-known certificate authorities (CAs), do not cause this error.
3. Is it safe to add the root certificate to Docker Desktop?
Adding the root certificate to Docker Desktop is generally safe as long as you obtained it from a trusted source. However, it is essential to verify the legitimacy and authenticity of the certificate before adding it, as adding a malicious or compromised certificate could introduce security risks.
4. Do I need to follow the same steps for every occurrence of the error?
The steps to resolve the error may vary depending on the specific service or component causing the error. However, the general steps of identifying the root cause, obtaining the root certificate, adding it to Docker Desktop, and restarting Docker Desktop remain consistent.
In conclusion, X509 certificates serve a vital purpose in securing connections and establishing trust within Docker Desktop. The “Certificate Signed by Unknown Authority” error is a common obstacle that can be remedied by adding the root certificate to Docker Desktop’s trusted certificate store. Taking the necessary steps to identify the source of the error and resolve it ensures the secure and reliable functioning of Docker Desktop.
X509: Certificate Signed By Unknown Authority Ubuntu
In the world of digital security, X509 certificates play a crucial role in ensuring the integrity and authenticity of online communications. These certificates, often used in secure website connections and email encryption, serve as a digital passport that validates the identity of an online entity. However, encountering the error message “Certificate Signed by Unknown Authority” can be frustrating for Ubuntu users. In this article, we will delve into the intricacies of the X509 certificate and explore possible solutions to resolve this issue.
Understanding X509 Certificates
X509 certificates are issued by Certificate Authorities (CAs) and are used to verify the authenticity of websites, email servers, and other online services. These certificates consist of several components, including the entity’s public key, digital signature, validity period, and information about the issuer. The digital signature, created with the issuer’s private key, ensures the integrity of the certificate and proves that it was not tampered with during transmission.
When a user encounters the “Certificate Signed by Unknown Authority” error on Ubuntu, it typically means that the system cannot verify the authenticity of the certificate because the issuing CA is not recognized or trusted by the system. This can happen if the certificate is self-signed or if it originates from a CA that is not included in Ubuntu’s list of trusted CAs.
Resolving the Error
To resolve the “Certificate Signed by Unknown Authority” error in Ubuntu, you have several options available:
1. Import the CA Certificate: If the certificate is from a legitimate CA but is not recognized by your system, you can manually import the CA certificate into Ubuntu’s trusted certificates store. This can typically be done through the system’s graphical interface or by using the command line tool “update-ca-certificates.”
2. Verify the Authenticity of the Certificate: If you encounter the error on a website, it is essential to verify the website’s legitimacy. Ensure that the domain name matches the certificate’s subject and scrutinize the certificate’s details for any suspicious information. However, exercise caution when encountering self-signed certificates, as they do not require CA verification.
3. Obtain a Trusted Certificate: If you are encountering the error when accessing a website or online service, you may consider contacting the website owner or service provider to obtain a trusted certificate from a recognized CA. This will prevent the error from recurring and ensure a secure connection.
4. Manually Trust the Certificate: In some cases, you may trust the certificate despite it not being recognized by your system. While this approach bypasses the verification process, it should only be done if you are confident in the certificate’s authenticity and trustworthiness.
Frequently Asked Questions (FAQs):
Q: Why does Ubuntu show the “Certificate Signed by Unknown Authority” error?
A: This error occurs when Ubuntu cannot verify the authenticity of a certificate because the issuing CA is not recognized or trusted by the system.
Q: Can I resolve this error by adding the CA certificate manually?
A: Yes, you can import the CA certificate into Ubuntu’s trusted store using the “update-ca-certificates” command or the system’s graphical interface.
Q: Is it safe to trust a certificate that is not recognized by the system?
A: Trusting an unrecognized certificate should be done with caution. Ensure the certificate’s authenticity and trustworthiness before manually trusting it.
Q: How can I verify the authenticity of a certificate?
A: To verify a certificate, check if the domain name matches the certificate’s subject and examine the certificate’s details for any inconsistencies or suspicious information.
Q: What should I do if I encounter a self-signed certificate?
A: Exercise caution when encountering self-signed certificates, as they do not require CA verification. Assess the trustworthiness of the website or service before proceeding.
In conclusion, encountering the “Certificate Signed by Unknown Authority” error in Ubuntu can be a frustrating experience. However, by understanding the role of X509 certificates and implementing the appropriate solutions, you can overcome this error and ensure secure online connections. Remember to prioritize the authenticity and trustworthiness of certificates and proceed cautiously when encountering self-signed certificates.
X509: Certificate Signed By Unknown Authority Golang
In the realm of computer security, X509 certificates are widely used to verify the authenticity and integrity of digital communication. These certificates are essential for establishing secure connections over networks using protocols such as HTTPS, TLS, and SSL. However, encountering an error message like “certificate signed by unknown authority” can be frustrating. In this article, we will explore this issue specifically in the context of Go programming language (Golang). We will delve into the technical aspects underlying X509 certificates, the reasons for this error, and the steps to mitigate it.
Understanding X509 Certificates:
X509 certificates form the backbone of Public Key Infrastructure (PKI) systems. These certificates are used to bind a public key with an entity, typically an individual or an organization, and are digitally signed by a trusted third-party certificate authority (CA). The CA vouches for the legitimacy of the certificate, establishing trust and authenticity between parties. X509 certificates consist of various fields such as subject, issuer, validity period, public key, and the digital signature itself.
Certificate Chains and Trust:
To verify the authenticity of a certificate, a certificate chain is constructed from the leaf certificate (also known as an end-entity certificate) to the root certificate. Each intermediate certificate in the chain is signed by the issuer of the subsequent certificate, with the root certificate being the ultimate trust anchor. When a certificate is received, the verifying entity traverses the chain and performs cryptographic validation at each step until reaching the root certificate. If any certificate in this chain is not trusted, the entire chain is considered invalid.
Certificate Signed by Unknown Authority Error:
Go, being a powerful and versatile programming language, provides extensive support for working with X509 certificates and building secure applications. However, when a certificate signed by an unknown authority is encountered, it implies that the certificate chain could not be validated to a trusted root certificate. This error is raised as a security measure to avoid potential malicious or insecure connections.
Reasons for encountering this error include:
1. Self-signed or untrusted certificate: If the server presents a self-signed certificate or a certificate issued by an untrusted CA, it is deemed unknown to the client.
2. Certificate chain misconfiguration: If the server fails to provide the complete chain from the end-entity certificate to the root certificate, the client cannot validate it properly.
3. Outdated or missing root CA certificates: The client’s trust store might lack the necessary root CA certificates, resulting in failure to validate the incoming certificate chain.
4. Man-in-the-middle attacks: If an attacker intercepts and replaces the server’s certificate with their own, which is not trusted by the client, the error occurs.
Mitigating the Error:
When encountering the “certificate signed by unknown authority” error, there are several steps that can be taken to resolve the issue:
1. Trust the specific certificate: If you are certain about the validity of the certificate, and it is signed by an authority that is not included in the client’s trust store, you can manually trust the certificate by adding it to the trust store.
2. Trust all certificates: Beware that this approach is not recommended for production environments, as it disables certificate validation altogether. However, it can be used for testing or development purposes. By configuring the client to trust all certificates, including self-signed and untrusted ones, the error will be bypassed.
3. Update the root CA certificates: Ensure that your client’s trust store is up to date. It is essential to regularly update the trusted root CA certificates to ensure effective validation of certificate chains.
4. Investigate and rectify certificate chain issues: If the server misconfigures the certificate chain, causing it to be invalid, you should work towards correcting this misconfiguration. Ensure that the complete chain, up to the trusted root CA certificate, is provided by the server.
FAQs:
Q: How can I view the details of a certificate using Go?
A: Go provides the “crypto/x509” package, which allows you to parse and examine X509 certificates. You can use the functions provided by this package to access various fields such as subject, issuer, validity period, and public key.
Q: Can I trust a certificate issued by a CA that is not included in the client’s trust store?
A: While you can manually trust a specific certificate, it is generally recommended to only trust certificates signed by known and trusted CAs. Adding unknown CAs to the trust store can expose your application to potential security risks.
Q: Is it safe to disable certificate validation?
A: Disabling certificate validation should only be done in controlled environments, such as testing or development setups. In production environments, certificate validation helps ensure the authenticity and integrity of connections, and disabling it can expose your application to security vulnerabilities.
Conclusion:
X509 certificates play a vital role in securing digital communication, but encountering the “certificate signed by unknown authority” error can hinder the establishment of secure connections. By understanding the reasons behind this error and following the recommended steps to mitigate it, developers can ensure secure and trusted communication in their Go applications.
Images related to the topic docker build x509 certificate signed by unknown authority

Found 49 images related to docker build x509 certificate signed by unknown authority theme

















![Docker: ERROR: [doc=sitecore://master/] unknown field 'schedule_t_en' - Sitecore Stack Exchange Docker: Error: [Doc=Sitecore://Master/] Unknown Field 'Schedule_T_En' - Sitecore Stack Exchange](https://i.stack.imgur.com/5bjW5.png)








![Docker] Error response from daemon: Get Docker] Error Response From Daemon: Get](https://velog.velcdn.com/images/ptah0414/post/0bfd47c5-d455-4506-988a-adf4729aff67/image.jpg)
Article link: docker build x509 certificate signed by unknown authority.
Learn more about the topic docker build x509 certificate signed by unknown authority.
- “docker pull” certificate signed by unknown authority
- Docker Private Registry: x509: certificate signed by unknown …
- “x509: certificate signed by unknown authority” error … – GitHub
- How to fix Docker error certificate signed by unknown authority …
- Docker x509: certificate signed by unknown authority | Resolved
- Bamboo running on Docker fails to checkout code from Bitbucket due …
- Using your own SSL Certificate – Maltego Support
- X509 Certificate Signed by Unknown Authority: Causes & Fixes
- ERROR: x509: certificate signed by unknown authority error is …
- Docker x509: certificate signed by unknown authority | Resolved
- Error: error contacting notary server: x509: certificate signed …
- Configure your Docker Engine
See more: https://nhanvietluanvan.com/luat-hoc