Fatal: Detected Dubious Ownership In Repository At
Overview of the Detected Dubious Ownership in the Repository
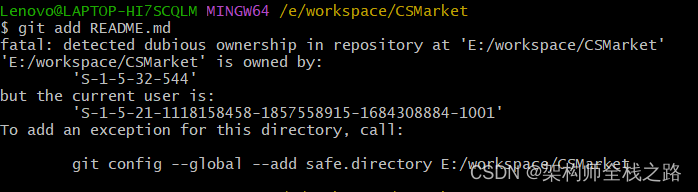
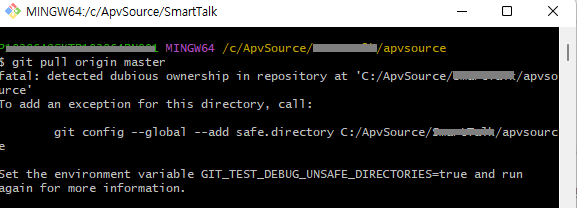
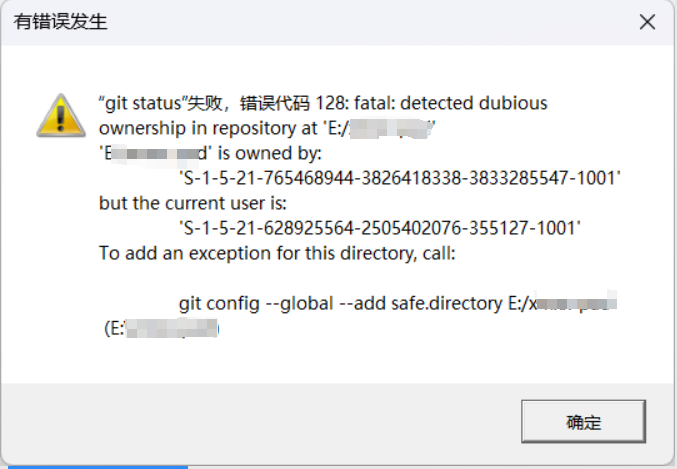
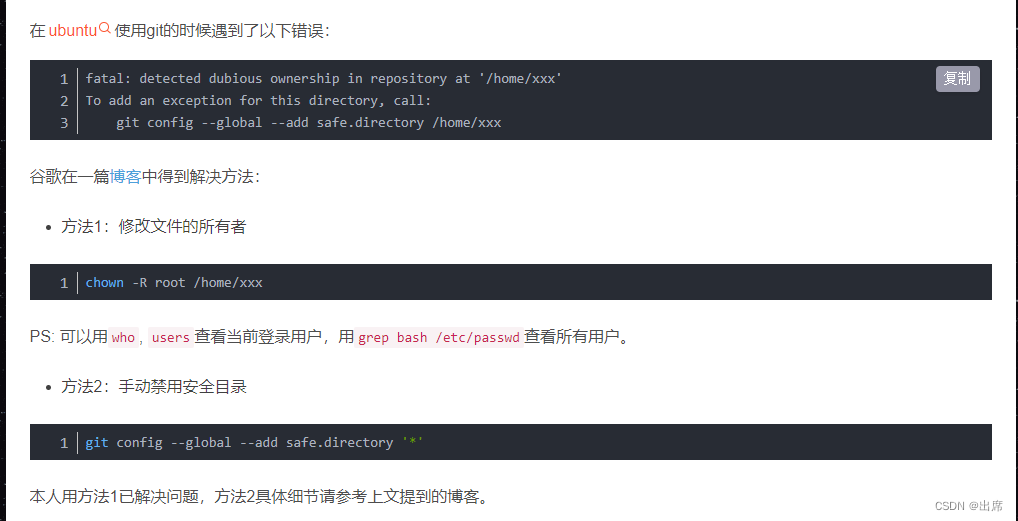
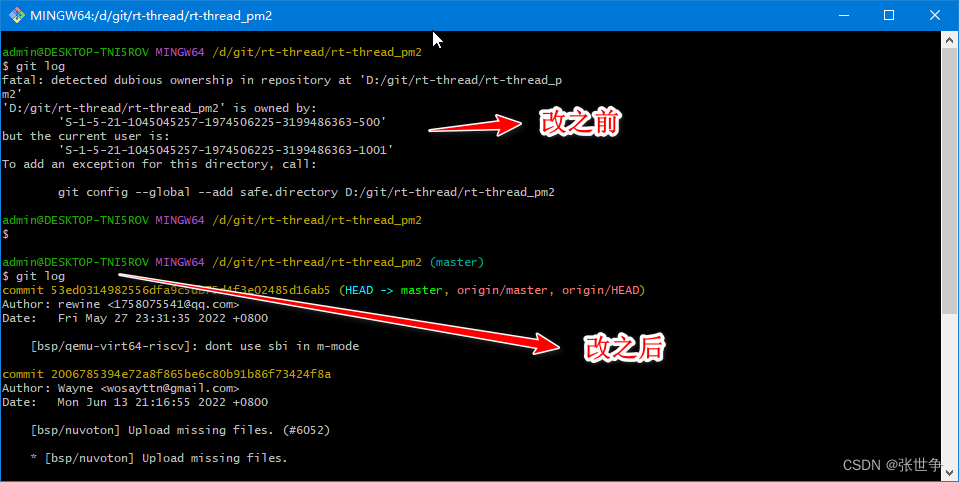
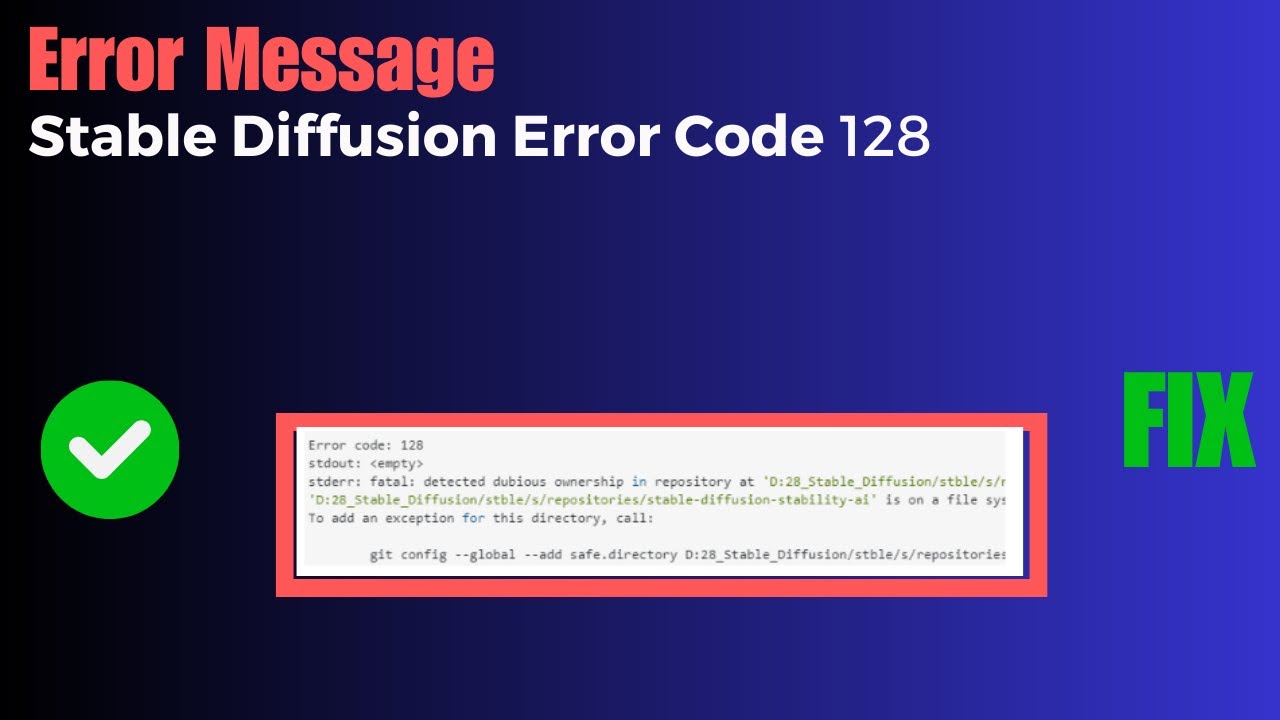
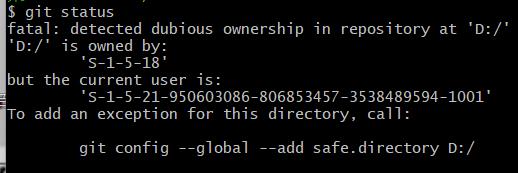
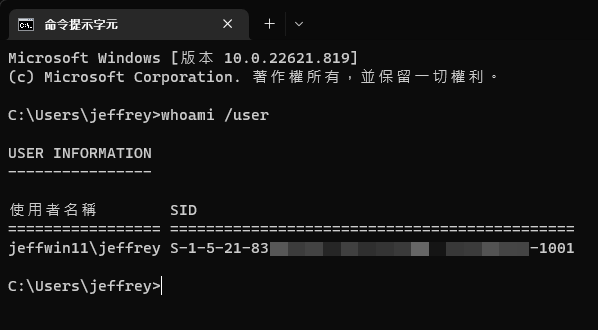
“Fatal: detected dubious ownership in repository at” is an error message that Git users may encounter while working with repositories. This error occurs when there is a discrepancy between the ownership of the repository and the user attempting to access or make changes to it.
Ownership in a Git repository refers to the user or group that has the necessary permissions and control over the repository. It is essential to ensure that the correct ownership is set to avoid issues like unauthorized access, failed push or pull requests, and potential data loss.
Causes and Consequences of the Dubious Ownership Issue
Several factors can lead to the detection of dubious ownership in a repository. Let’s explore some of the main causes and the potential consequences they can have.
1. Invalid User Permissions: Improper user permissions can trigger the dubious ownership issue. If a user does not have the necessary rights to access or modify the repository, Git will raise an error. This can happen when project directories or files are moved or copied without proper permission updates.
2. User Mismatch: If the active user attempting to access the repository differs from the user assigned as the owner, Git will detect dubious ownership. This commonly occurs when collaborating with multiple team members or using different accounts on a single machine.
3. Remote Repository Ownership: When attempting to push changes to a remote repository, Git verifies ownership and authorization. If the remote repository is owned by a different user or account than the current one, the dubious ownership issue can arise.
The consequences of the dubious ownership issue can be severe. Users may encounter errors like “Permission denied (publickey), fatal: could not read from remote repository,” preventing them from accessing or modifying the repository. Additionally, failed push or pull requests can disrupt collaboration and hinder the progress of projects. Data loss is also a potential risk if unauthorized users gain access to a wrongly owned repository.
Methods and Tools Used to Detect Dubious Ownership in Repositories
To detect dubious ownership in a repository, Git utilizes several methods and tools. These mechanisms help identify inconsistencies and provide users with error messages and warnings when ownership issues occur.
1. Git Configuration: Git uses the configuration settings to determine the owner and permissions associated with a repository. It verifies the user who made the initial commit and tracks subsequent changes made by authorized users.
2. SSH Keys: Secure Shell (SSH) keys are often used for secure communication between systems. Git uses these keys to authenticate users and establish ownership of repositories during remote operations. Any mismatch between the SSH keys and repository ownership leads to the detection of dubious ownership.
3. User Identification: Git relies on user identification information such as email addresses and usernames to detect dubious ownership. When different users attempt to gain access to a repository, Git compares the identification details with the configured ownership to confirm authorization.
Strategies for Addressing and Resolving the Issue of Dubious Ownership
To address and resolve issues related to dubious ownership in Git repositories, various strategies can be employed. These strategies focus on verifying ownership, updating permissions, and resolving mismatches between users and repositories.
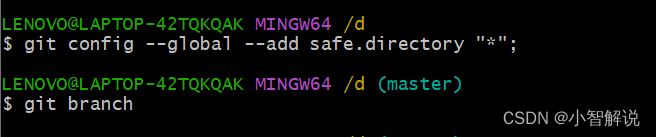
1. Review Ownership: Carefully review the repository ownership to ensure it matches the intended user or group. Use Git commands like “git config –list” to display the repository settings and verify the owner’s information.
2. Check SSH Keys: Confirm that SSH keys are correctly set up and associated with the appropriate user account. Make sure the public key is configured in the remote repository for proper authentication.
3. Grant Proper Permissions: Adjust user permissions to allow for proper access and modifications. Use Git commands such as “git add” or “git chown” to change ownership or set permissions accordingly.
4. Resolve User Mismatches: If multiple users are collaborating on a repository, ensure that all users have the necessary rights and access. They should use the correct user accounts or configure Git’s user identification settings accordingly.
Best Practices for Preventing and Minimizing Dubious Ownership in Repositories
To prevent and minimize issues related to dubious ownership in repositories, it is advisable to follow a set of best practices. These practices help maintain consistency, prevent unauthorized access, and ensure smooth collaboration within development teams.
1. Standardize User Accounts: In a team environment, standardize user accounts by using a shared version control system. This reduces the chances of user mismatches and ensures everyone uses the same authentication mechanisms.
2. Regularly Review Ownership: Conduct routine checks of repository ownership to confirm it aligns with the intended user or group. This can be done by reviewing Git configuration settings and comparing them against the actual owner’s information.
3. Implement Access Control: Establish access control mechanisms to grant appropriate permissions to users based on their responsibilities and involvement in the project. Limit access to critical repositories and ensure that only authorized individuals can make changes.
4. Utilize Git Hooks: Git hooks allow the execution of custom scripts before or after specific Git actions. By leveraging hooks, you can automate checks to prevent dubious ownership, enforce proper permissions, and validate user identification before any repository operations.
Case Studies and Real-Life Examples of Repositories Affected by Dubious Ownership Issues
To understand the impact of dubious ownership issues in real-life scenarios, let’s explore a few cases:
1. Failed to Push to Remote Repository: A developer working on a collaborative project tries to push their changes to a remote repository but receives an error stating, “failed to push to the remote repository, see the output window for more details.” This error could be attributed to dubious ownership, where the developer lacks the necessary permissions to access or modify the remote repository.
2. Git Delete Remote Repository: When attempting to delete a remote repository, Git may raise an error if the current user does not have the proper authorization to perform the operation. This can occur, for example, when a developer is unaware of the existing repository’s ownership details.
3. Permission Denied (Publickey Fatal Could Not Read from Remote Repository): This error message is often encountered when attempting to clone or fetch from a remote repository. It indicates that the user’s SSH key or authentication credentials do not match the repository’s ownership, leading to a dubious ownership detection.
Conclusion
Dubious ownership in repositories is a significant concern in the Git ecosystem. Understanding the causes, consequences, and strategies for addressing this issue is essential for maintaining the integrity and security of repositories. By implementing best practices, regularly reviewing ownership, and ensuring proper user identification and permission management, developers can prevent and minimize the impact of dubious ownership errors.
Git Fatal: Detected Dubious Ownership In Repository
Keywords searched by users: fatal: detected dubious ownership in repository at Detected dubious ownership in repository, Permission denied (publickey fatal Could not read from remote repository), Is owned by but the current user is git, error: remote origin already exists., Git delete remote repository, Failed to push to the remote repository see the output window for more details, Git add safe directory recursively, Git config –list
Categories: Top 71 Fatal: Detected Dubious Ownership In Repository At
See more here: nhanvietluanvan.com
Detected Dubious Ownership In Repository
Introduction:
In today’s digital era, repositories have become essential for storing and managing code, documents, and other valuable assets. However, despite their convenience, repositories can sometimes harbor hidden risks, particularly when it comes to ownership. Detected dubious ownership in repositories has become a concerning issue that organizations need to address diligently. In this article, we will explore the concept of dubious ownership, its potential consequences, and how organizations can mitigate these risks.
Understanding Dubious Ownership in Repositories:
Dubious ownership refers to cases in which unauthorized or questionable individuals or entities gain control over repositories that contain valuable assets. This can occur due to various reasons, such as weak access controls, inadequate security measures, or even insider threats. When dubious ownership is present in a repository, it can lead to serious consequences such as unauthorized access, data breaches, intellectual property theft, and compromised code integrity.
Consequences of Dubious Ownership in Repositories:
1. Unauthorized Access: Dubious ownership allows unauthorized individuals to access sensitive information, including proprietary code, internal documentation, or customer data. This can result in legal and reputational damage, financial losses, or compliance breaches.
2. Data Breaches: If dubious owners gain access to repositories containing personal or sensitive data, it could lead to data breaches. This can have severe consequences, including identity theft, financial fraud, or regulatory fines.
3. Intellectual Property Theft: Ownership by dubious entities may facilitate the theft of intellectual property from repositories. This can result in significant financial losses, competitive disadvantages, and compromised business strategies.
4. Compromised Code Integrity: Dubious ownership can also compromise code integrity within repositories by allowing unauthorized modifications or introducing malicious code. This can lead to substandard software products, security vulnerabilities, and potential cyber-attacks.
Mitigating the Risks of Dubious Ownership in Repositories:
1. Strengthen Access Controls: Implementing robust and granular access controls is crucial to prevent unauthorized ownership claims. Organizations should regularly review and update access permissions, establishing a principle of least privilege to restrict repository access to only necessary individuals or groups.
2. User Identity Verification: Implementing stringent user identity verification measures, such as multi-factor authentication and regular password updates, helps combat dubious ownership. This ensures that only authorized and verified users can gain access to repositories.
3. Regular Audits: Conducting regular audits to review repository ownership and access logs is crucial for detecting any dubious ownership. Monitoring and analyzing access patterns can help identify anomalies or suspicious activities, allowing prompt remediation measures to be taken.
4. Security Awareness Training: Employees should receive comprehensive security awareness training to recognize potentially malicious activities, prevent phishing attacks, and understand the importance of securing repositories. Regular training sessions help promote a culture of security awareness within the organization.
5. Implementing Security Technologies: Utilizing security technologies like intrusion detection systems, data leakage prevention tools, and privileged access management solutions can significantly enhance repository security. These technologies can help detect and prevent unauthorized access attempts or dubious ownership activities.
6. Incident Response Plans: Organizations should have well-defined incident response plans to swiftly respond to any detected dubious ownership activities. These plans should outline procedures for investigating and mitigating the risks, as well as notifying relevant stakeholders and authorities, if necessary.
FAQs:
Q1. What are the common signs of dubious ownership in repositories?
A1. Common signs include sudden ownership changes, unauthorized modifications to code or documents, irregular access patterns, or unidentified user accounts.
Q2. Can open-source repositories be vulnerable to dubious ownership?
A2. Yes, open-source repositories can also be susceptible to dubious ownership. Proper access controls and regular monitoring are still essential to mitigate this risk.
Q3. Can third-party tools help detect or prevent dubious ownership?
A3. Yes, there are third-party tools available that specialize in repository security. These tools provide features like access monitoring, user behavior analytics, and automated threat detection.
Q4. How often should repositories be audited for dubious ownership?
A4. Regular audits should be conducted, ideally on a quarterly basis. However, the frequency may depend on the organization’s risk appetite, industry regulations, and the sensitivity of the stored assets.
Q5. What should organizations do if they detect dubious ownership in their repositories?
A5. If dubious ownership is detected, organizations should immediately initiate the incident response plan, investigate the issue, remediate any potential damage, and take necessary legal or regulatory actions.
Conclusion:
Detecting and preventing dubious ownership in repositories is essential for safeguarding valuable assets, ensuring data privacy, and maintaining code integrity. By implementing robust access controls, conducting regular audits, and raising security awareness, organizations can significantly mitigate the risks associated with dubious ownership. In today’s ever-evolving digital landscape, ensuring repository security should be a top priority for organizations of all sizes and industries.
Permission Denied (Publickey Fatal Could Not Read From Remote Repository)
The error message “Permission denied (publickey fatal: Could not read from remote repository)” is an issue encountered by many developers when trying to access or clone a remote repository using Git. This error is often frustrating and confusing, especially for beginners. In this article, we will delve into the root causes of this error and provide solutions to get you back on track with your Git workflow.
Understanding the Error:
When attempting to access a remote repository, Git uses a secure shell (SSH) protocol to establish a connection. This error message usually indicates that the SSH key being used for authentication is not recognized or authorized by the remote repository server. In simpler terms, your local machine is denied permission to access the remote repository due to a problem with your SSH key.
Possible Causes:
1. Incorrect SSH Key: One common cause is using the wrong SSH key. Each repository typically requires a unique SSH key to establish a secure connection. If you accidentally or unknowingly provide the wrong key, the server will deny access, resulting in the error message.
2. Missing SSH Key: In some cases, you may not have set up an SSH key or configured it correctly on your local machine. Without a valid SSH key, the server cannot verify your identity, leading to permission denial.
3. Inadequate Permissions: The remote repository may have specific permissions set up that restrict access to only authorized users. If your account does not have the necessary permissions, you may encounter this error.
4. Firewall or Proxy Interference: Firewalls or proxy servers can sometimes interfere with SSH connections, leading to authentication failures. It’s worth checking if your network setup or security settings are causing any disruptions.
Solutions:
1. Verify SSH Key: Double-check if you are using the correct SSH key. Make sure that the key you are using corresponds to the specific repository you are trying to access. You can review and manage your SSH keys in your Git hosting platform or in your local SSH configuration files.
2. Generate and Add SSH Key: If you don’t have an SSH key or want to create a new one, follow the instructions provided by your Git hosting platform or the SSH documentation for your operating system. Once generated, add the key to your Git hosting platform and update your local SSH configuration to point to the newly generated key.
3. Check Permissions: Ensure that your account has the necessary permissions to access the remote repository. Contact the repository owner or project administrator to confirm that you have been granted the appropriate access rights.
4. Firewall/Proxy Settings: If you suspect that the firewall or proxy server is causing the issue, you can try temporarily disabling them to see if it resolves the problem. Alternatively, consult your network administrator for assistance with configuring the firewall or proxy settings to allow SSH connections.
5. Debugging SSH: Git provides a flag, “-v” or “–verbose,” which can help in debugging SSH connection issues. Running the Git command with the verbose flag will display detailed information about the connection process, allowing you to identify any potential problems.
FAQs:
Q1. I have multiple SSH keys; how do I ensure I am using the correct one?
A: To use the correct SSH key, you can modify your SSH configuration or specify the key explicitly when cloning or accessing a repository using the git command. Consult the SSH documentation for your operating system to understand how to accomplish this.
Q2. I’ve verified and added my SSH key correctly, but the error persists. What should I do?
A: In such cases, ensure that your SSH key is correctly associated with your Git hosting platform account. Additionally, check if the repository permissions are properly configured. If the issue persists, contact the Git hosting platform support or the repository owner for further assistance.
Q3. Can I use HTTPS instead of SSH to avoid this error?
A: Yes, Git also supports HTTPS URLs for cloning and accessing repositories. However, note that using SSH is generally recommended as it provides a more secure method of communication and is often required for write access to repositories.
Q4. Why did it work previously, but not now?
A: There can be various reasons why it was previously working but not anymore. It is possible that the SSH key was unintentionally removed or revoked, or there may have been changes to the repository permissions. Check with the repository owner or account administrator to investigate any recent changes.
In conclusion, the error “Permission denied (publickey fatal: Could not read from remote repository)” is commonly encountered when accessing remote repositories in Git. By understanding the potential causes and applying the solutions provided in this article, you should be able to resolve this error and continue with your Git workflow seamlessly.
Images related to the topic fatal: detected dubious ownership in repository at

Found 33 images related to fatal: detected dubious ownership in repository at theme























![git] fatal: detected dubious ownership in repository at Git] Fatal: Detected Dubious Ownership In Repository At](https://img1.daumcdn.net/thumb/C176x176/?fname=https://blog.kakaocdn.net/dn/drAAGs/btrQUADbJUk/2K9pCQXRQ7LLAKZkw7rKc0/img.png)


![git] fatal: detected dubious ownership in repository at Git] Fatal: Detected Dubious Ownership In Repository At](https://img1.daumcdn.net/thumb/C176x176/?fname=https://blog.kakaocdn.net/dn/mnNFI/btrJgxl5QmV/YRwRmrmMWBGOtqrHvSANLK/img.png)






Article link: fatal: detected dubious ownership in repository at.
Learn more about the topic fatal: detected dubious ownership in repository at.
- git submodule update failed with ‘fatal: detected dubious …
- Git detect dubious ownership in repository | by Dennis – Medium
- Deleting a repository – GitHub Docs
- Git fatal: ‘origin’ does not appear to be a git repository Solution
- I cannot add the parent directory to *safe.directory* in Git – Stack Overflow
- Git “fatal: detected dubious ownership in repository”
- Little Git Tricks: Fix a Dubious Ownership of a Repository
- Detected dubious ownership in repository with Jenkins upgrade
See more: https://nhanvietluanvan.com/luat-hoc