Ec2 Cloud Init Logs
In today’s technology-driven world, cloud computing has become an essential component for businesses seeking scalability, flexibility, and cost-effectiveness in their infrastructure. Amazon Web Services (AWS) offers a wide range of cloud services, including Amazon Elastic Compute Cloud (EC2), which provides secure and resizable compute capacity in the cloud.
One of the powerful features of EC2 is Cloud Init, a service that enables you to customize and configure your instances during the boot process. As instances launch, Cloud Init runs user data scripts and applies metadata to configure the instance according to your desired specifications.
However, with the complexity of cloud infrastructure, it’s crucial to have a solid understanding of Cloud Init logs. These logs are invaluable in troubleshooting issues, monitoring the system’s behavior, and gaining insights into the various configurations applied during the launch process.
Overview of EC2 and Cloud Init
Amazon EC2 allows you to launch instances with different operating systems and software configurations. By leveraging the user data feature, you can script the initial configuration of your instances and automate tasks such as installing software, setting up user accounts, and mounting storage.
Cloud Init is the underlying technology that processes and applies this user data during the instance initialization process. It retrieves user data either from the EC2 user data field, an instance metadata endpoint, or a specified URL. The user data is typically a text script written in cloud-config format or a bash script.
Understanding Cloud Init Logs
Cloud Init logs provide detailed information about the execution of user data scripts and the configuration applied during the instance boot process. These logs are crucial for troubleshooting issues related to misconfigurations, failed scripts, or unexpected behaviors.
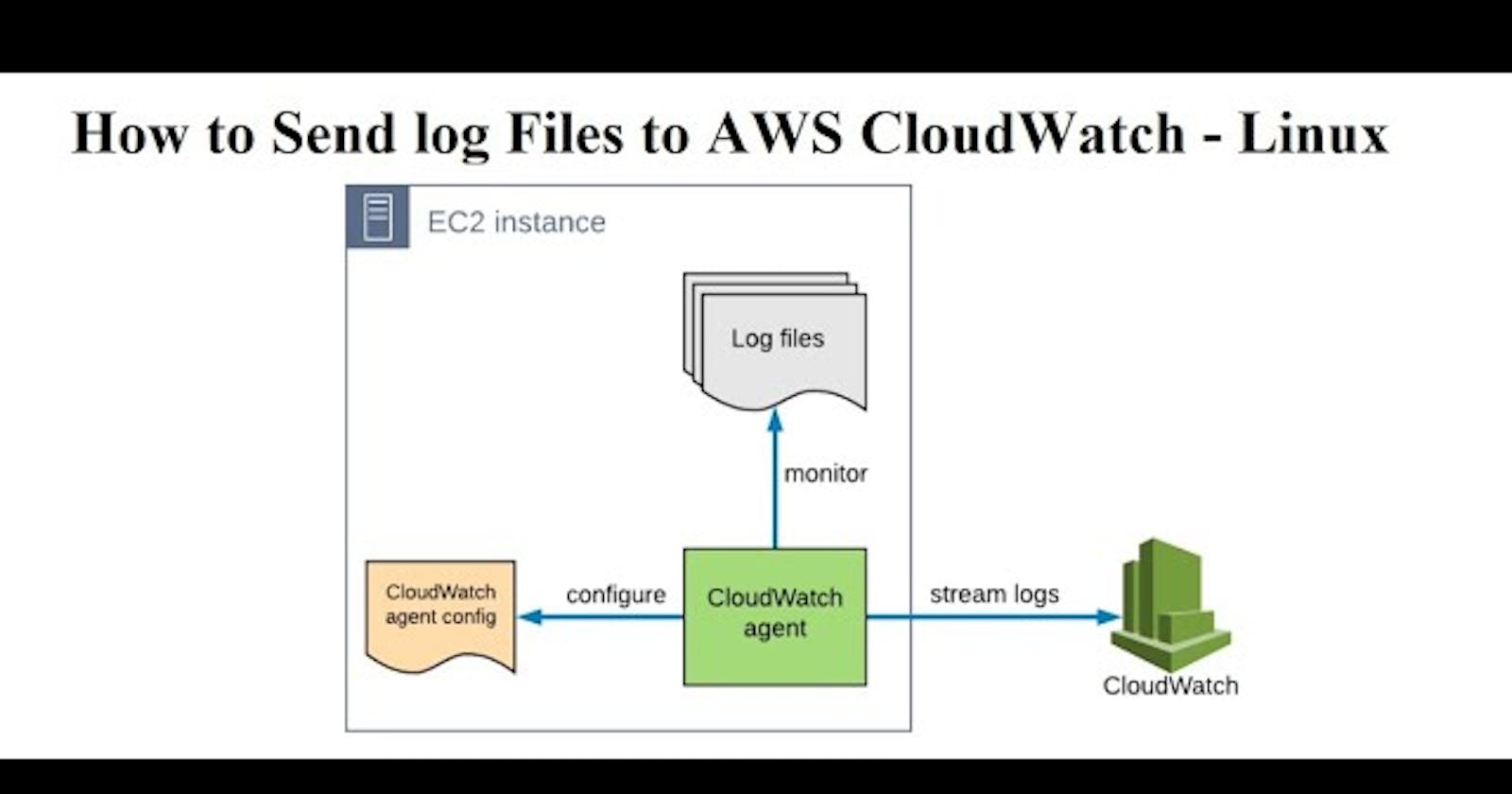
The Cloud Init logs are located in the `/var/log/cloud-init.log`, `/var/log/cloud-init-output.log`, and `/var/log/cloud-init-status.log` files on Linux instances. On Windows instances, the logs are available in the `C:\Program Files\Amazon\EC2ConfigService\Logs\Cloud-init.log` file.
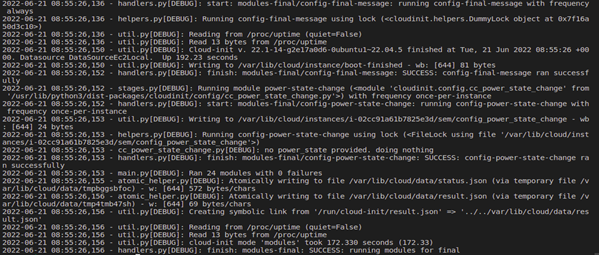
Examining these logs allows you to track the execution of each module, understand the order in which modules were processed, and identify any errors or warnings encountered during the boot process. The logs include timestamps, process IDs, and pertinent details to aid in troubleshooting.
Configuring Cloud Init Logs
By default, Cloud Init logs are automatically generated during the boot process. However, you have the flexibility to configure the logging behavior based on your specific needs.
To configure Cloud Init logs, you can edit the `/etc/cloud/cloud.cfg` file on Linux instances or modify the EC2Config service settings on Windows instances. These configurations allow you to specify log file locations, increase the verbosity of logs, enable/disable logging of certain modules, and control log rotation and retention policies.
Analyzing Cloud Init Logs
When analyzing Cloud Init logs, it is crucial to pay attention to specific sections that can provide valuable information. The `cloud-init-nonet`, `cloud-init-local`, `cloud-init-modules`, and `cloud-init-config` sections highlight the various stages of the boot process, detailing the actions performed and any errors encountered.
Additionally, you should examine the `status` field, which indicates whether a particular module succeeded or failed during execution. Failed modules can point to misconfigurations or external dependencies that lead to issues during initialization.
Troubleshooting Cloud Init Logs
Troubleshooting Cloud Init logs can be a complex task, given the numerous factors that can impact the boot process. However, there are some common troubleshooting steps you can follow:
1. Check user data logs EC2: Ensure that the user data script you provided has been correctly passed to the instance and is visible in the Cloud Init logs. This ensures that the correct instructions are being executed.
2. Verify the format and syntax of your user data script: A misplaced character, missing syntax, or incorrect indentation can cause the script to fail. Validate your script using online tools or refer to the Cloud Init documentation for the supported syntax.
3. Review Cloud Init error messages: Pay close attention to error messages in the logs. They often provide hints about misconfigurations, incorrect permissions, or other issues that may prevent the successful execution of user data scripts.
4. Check dependencies and resource availability: Ensure that any external dependencies or resources required by your user data script, such as package repositories or network connectivity, are available during the instance boot process.
Best Practices for Managing Cloud Init Logs
To effectively manage and utilize Cloud Init logs, consider the following best practices:
1. Enable verbose logging during troubleshooting: Increasing the verbosity level of Cloud Init logs can provide more detailed information about each step of the boot process. Once the issue is resolved, you can revert to the default log level to reduce log noise.
2. Regularly monitor and analyze Cloud Init logs: Set up a monitoring system to alert you of any errors or warnings in Cloud Init logs. Regularly reviewing the logs helps identify potential issues before they become critical and impact your system’s stability.
3. Implement log rotation and retention policies: Cloud Init logs can consume significant disk space over time. Implement log rotation and retention policies to control log file sizes and ensure that logs are retained for an appropriate period for auditing and troubleshooting purposes.
4. Leverage Cloud Init examples and documentation: Familiarize yourself with the Cloud Init documentation and explore available examples. These resources provide insights into the supported cloud-config syntax, module configurations, and best practices for implementing custom bootstrapping procedures.
Frequently Asked Questions (FAQs):
Q: How can I check if my user data script is successfully executed on an EC2 instance?
A: You can check the Cloud Init logs (`/var/log/cloud-init.log` or `Cloud-init.log`) to verify if your user data script has executed successfully. Look for any errors or warnings during the boot process.
Q: Can I edit the user data script of an already running EC2 instance?
A: No, you cannot edit the user data script of a running EC2 instance. To update the user data, you need to stop the instance, modify the user data field, and then start the instance again.
Q: What are some common cloud-init examples for Ubuntu?
A: Some common cloud-init examples for Ubuntu include installing packages, configuring users and groups, setting up SSH keys, executing custom scripts, and mounting storage volumes.
Q: How can I configure cloud-init to run my user data script on EC2 instances?
A: To configure cloud-init to run your user data script, you need to provide the script in the user data field during instance launch or specify a URL from which the user data script can be retrieved.
Q: What is cloud-config in EC2 Cloud Init logs?
A: Cloud-config is a subset of the cloud-init syntax. It allows you to specify key-value pairs to configure various aspects of the instance, such as installing packages, running scripts, creating users, and configuring network interfaces.
In conclusion, understanding and effectively managing EC2 Cloud Init logs is essential for optimizing the boot process, troubleshooting issues, and ensuring the successful initialization of your instances. By following the best practices outlined in this article and leveraging the insights gained from analyzing these logs, you can enhance the stability and performance of your EC2 instances on AWS.
Send Aws Ec2 Instance Logs To Aws Cloudwatch
Where Are Cloud-Init Logs?
Cloud-init is a widely used tool in cloud computing that enables automatic configuration and initialization of virtual machine instances. It simplifies the process of setting up instances by providing a versatile and efficient platform for customization. However, like any software, troubleshooting issues that arise during cloud-init usage is important for achieving optimal performance and maintaining a stable infrastructure. One crucial aspect of troubleshooting is locating and analyzing cloud-init logs, as they contain valuable information that can help identify and resolve problems. In this article, we will explore the various locations where cloud-init logs can be found, as well as provide answers to some frequently asked questions.
Cloud-init logs can provide insights into several stages of an instance’s initialization, including the boot process, network configuration, and user data execution. As each cloud provider may have its own unique implementation of cloud-init, the locations of these logs might differ. Let’s explore a few common cloud providers and where their cloud-init logs are typically stored.
Amazon Web Services (AWS):
In AWS, cloud-init logs can be found in the ‘/var/log/cloud-init-output.log’ file. This log file contains the output messages generated by cloud-init during the instance initialization process. It can be accessed by logging into the instance and navigating to the specified directory.
Google Cloud Platform (GCP):
For instances running on GCP, the cloud-init logs are stored in the ‘/var/log/cloud-init.log’ file. This log file provides detailed information about the cloud-init process, including any errors or warnings encountered. Similarly to AWS, accessing this log file requires logging into the instance and navigating to the correct file location.
Microsoft Azure:
In Azure, cloud-init logs are available in the ‘waagent.log’ file, which is located at ‘/var/log/waagent.log’. This log file contains a mix of cloud-init logs and other Azure-specific logs related to the instance’s initialization process. Users can access this log file by logging into the Azure instance and locating the specified file path.
These are just a few examples of popular cloud providers, but other providers may store cloud-init logs in different locations. It is important to consult the documentation of your specific cloud provider in order to ascertain the correct log file and directory for retrieving cloud-init logs.
FAQs:
Q: Are cloud-init logs essential for troubleshooting issues?
A: Yes, cloud-init logs are a crucial resource for troubleshooting and diagnosing issues. They provide valuable information about the instance’s initialization process and can help identify errors, warnings, or misconfigurations that may be impacting the desired behavior.
Q: Can cloud-init logs be accessed remotely?
A: In most cases, cloud-init logs can only be accessed by logging into the instance directly. Remote access to these logs is not typically provided by cloud providers due to security considerations. However, you can often remotely access the instance using SSH or remote desktop protocols and then review the logs.
Q: Can cloud-init logs be viewed in real-time?
A: Yes, it is possible to view cloud-init logs in real-time by using commands like ‘tail’ or ‘less’ on the log file. This can be particularly useful when you are debugging during the instance initialization process and need to monitor the output.
Q: Is there a way to customize cloud-init log locations?
A: Yes, it is usually possible to configure custom log locations for cloud-init. However, this may vary depending on the cloud provider and their specific implementation. Consulting the documentation or support resources provided by your cloud provider is recommended for instructions on customizing log locations.
Q: Are cloud-init logs persistent?
A: Cloud-init logs are generally persistent within the instance, meaning that they are retained even after rebooting the instance. This allows for easier troubleshooting and analysis of past instance initialization processes.
In conclusion, locating and analyzing cloud-init logs is essential for troubleshooting and diagnosing issues related to instance initialization. By understanding where these logs are stored, users can effectively investigate and resolve problems that may arise during the cloud-init process. Checking documentation and resources provided by your specific cloud provider is crucial for accurate information regarding the log locations and understanding any provider-specific variations. Take advantage of cloud-init logs to ensure a smooth experience and optimal performance in your cloud computing infrastructure.
Where Are Ec2 Startup Logs?
When it comes to running applications and services in the cloud, Amazon Web Services (AWS) offers a wide range of flexible and powerful options. One of the most popular services within AWS is Elastic Compute Cloud (EC2), which provides users with virtual servers or instances in the cloud. When working with EC2 instances, it’s essential to be aware of the startup logs—these logs can provide valuable information to troubleshoot issues, monitor system health, and track the overall performance of your instances.
EC2 instances boot from Amazon Machine Images (AMI), which contain the operating system and other software installed on the instance. As these instances launch, several system processes execute, and the startup logs document this process. The logs hold crucial information about the instance initialization and any errors or warnings encountered during startup.
By default, EC2 instances store their logs in the /var/log directory, particularly under the cloud-init module. Within this module, there are several log files that are useful for troubleshooting startup and initialization issues. Let’s take a closer look at some of these log files:
1. cloud-init.log:
This is the main log file for cloud-init, a system initialization process that runs during instance startup. It provides detailed information about the progress of instance initialization, including network configuration, SSH key imports, and user data execution. The cloud-init.log file is typically the go-to log for analyzing issues related to the instance launch and initialization.
2. cloud-init-output.log:
As the name suggests, this log file contains the standard output and error streams of cloud-init. It captures the console output during the instance launch process. This log file can be particularly helpful for debugging purposes, as it documents any scripts or commands executed as part of the user data during instance boot.
3. cloud-init-per.log:
The cloud-init-per.log file records the execution of individual modules and their corresponding output. It can provide greater insight into specific module failures or errors encountered during instance initialization. By examining this log file, you can identify any configuration issues or misconfigurations that might be causing startup problems.
4. messages or syslog:
EC2 instances also write system logs to the messages or syslog file. These logs capture various system activities, including error messages, warnings, and informational messages. Monitoring this log can help administrators identify system-level issues if they are not specific to the cloud-init process.
Now that we know where the startup logs reside, let’s answer some frequently asked questions related to EC2 startup logs:
FAQs:
Q: Can I access the EC2 startup logs through the AWS Management Console?
A: While the AWS Management Console provides a graphical interface for managing EC2 instances, it does not directly facilitate access to the EC2 startup logs. To access the logs, you’ll need to connect to your EC2 instance using SSH or a remote desktop protocol and navigate to the log file locations mentioned above.
Q: Are the EC2 startup logs available for all instance types and operating systems?
A: Yes, EC2 startup logs are available for all instance types and supported operating systems. Regardless of whether you are running a Windows Server, Ubuntu, CentOS, or any other supported operating system, you can access the startup logs in the same manner.
Q: How long are the EC2 startup logs retained?
A: By default, EC2 retains the logs for a specific duration, which depends on the operating system. For Linux instances, the logs are typically stored for a week, while for Windows instances, it’s around one month. However, it’s important to note that you can configure log retention periods to best suit your requirements.
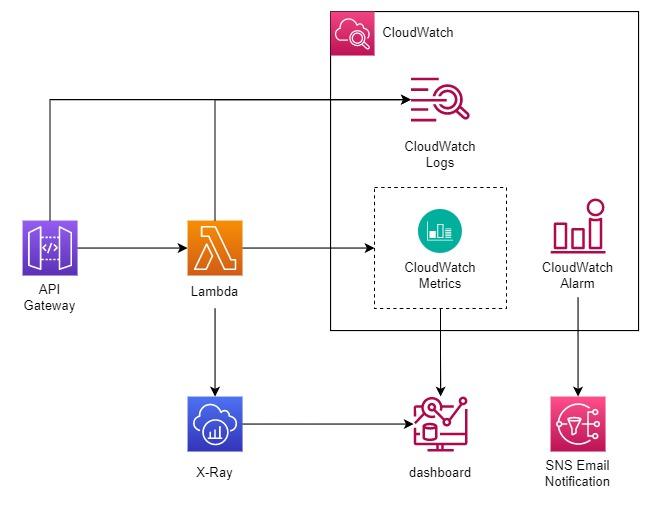
Q: Can I view the EC2 startup logs through AWS CloudWatch?
A: AWS CloudWatch, a monitoring service provided by AWS, can indeed be used to view EC2 instance logs. By configuring EC2 instances to send log data to CloudWatch Logs, you can centralize log management and analysis. This integration allows you to view and search logs using the CloudWatch console or programmatically.
Q: How can I troubleshoot and resolve any startup issues with my EC2 instance?
A: When troubleshooting EC2 startup issues, it’s essential to review the startup logs mentioned above. By examining the logs, you can identify any errors or warnings that may have occurred during the initialization process. Paying attention to cloud-init.log, cloud-init-output.log, and cloud-init-per.log will often provide the necessary insights to resolve startup issues. Additionally, reviewing system-level logs like messages or syslog might help identify broader system-level issues.
In conclusion, EC2 startup logs are a valuable resource for monitoring, troubleshooting, and optimizing your EC2 instances. By understanding where these logs are located and how to analyze them, you can effectively troubleshoot any issues that arise during instance initialization. Whether you access the logs through a command-line interface or integrate with AWS CloudWatch, being proactive in reviewing the startup logs will help ensure the overall health and performance of your EC2 instances.
Keywords searched by users: ec2 cloud init logs Check user data logs EC2, Aws cloud init, User data EC2, Edit user data ec2, Cloud-init examples, Cloud-init Ubuntu, Cloud init user data, Cloud-config
Categories: Top 81 Ec2 Cloud Init Logs
See more here: nhanvietluanvan.com
Check User Data Logs Ec2
Introduction:
In today’s digital world, ensuring the security and compliance of user data is of utmost importance. With the rise of cloud computing, businesses are increasingly adopting Amazon Elastic Compute Cloud (EC2) to host their applications and store critical user data. EC2 offers various tools and features to monitor and manage user activity logs, providing administrators with a comprehensive overview of user actions within their environment. This article explores the process of checking user data logs in EC2, explaining its significance and presenting commonly asked questions.
Why is Checking User Data Logs Important?
By checking user data logs in EC2, administrators can effectively track user activity, detect suspicious behavior, and identify potential security threats. Logs provide detailed information about user actions, including login attempts, resource access, and modifications made, enabling admins to monitor and audit user activity. This helps ensure adherence to security policies, GDPR regulations, and other compliance requirements.
Types of User Data Logs in EC2:
EC2 offers several logs that provide critical insights into user activities. These logs include:
1. AWS CloudTrail Logs: CloudTrail logs records API calls and captures data on user activities within the AWS Management Console, AWS SDKs, command-line tools, and third-party applications. These logs are stored in an S3 bucket and store information such as actions performed, source IP address, and timestamp.
2. AWS Config Logs: AWS Config provides visibility into configuration changes made to AWS resources. It helps track resource modifications and offers comprehensive information about changes made, facilitating proactive monitoring of compliance and security.
3. Amazon VPC Flow Logs: VPC Flow Logs capture network flow information for AWS resources within a VPC, including traffic destined to or from Amazon EC2 instances. These logs offer insights into network traffic patterns, aiding in security analysis and troubleshooting.
Checking User Data Logs in EC2:
To check user data logs in EC2, follow these steps:
1. Access AWS Management Console: Log in to the AWS Management Console using your administrator credentials.
2. Navigate to CloudTrail: In the management console, go to the AWS CloudTrail service.
3. Select Trail: Choose the desired trail (configured to capture logs) from the list of trails displayed.
4. Monitor Events: The CloudTrail event history page displays detailed information about user actions. Use the search filter to narrow down specific events like API calls, user identity, or IP addresses.
5. Analyze CloudTrail Insights: Utilize CloudTrail Insights to identify suspicious activity and patterns. Insights are anomalies or potential security risks detected by AWS.
6. Access AWS Config: To access AWS Config logs, go to the AWS Config service within the AWS Management Console.
7. Review Configuration Changes: AWS Config offers different views to analyze historical configuration changes, rule compliance, or custom configurations.
8. Examine VPC Flow Logs: Navigate to the Amazon VPC dashboard within the AWS Management Console.
9. Select Flow Logs: Choose the VPC for which you want to review flow logs and select the Flow Logs tab.
10. Analyze Traffic Patterns: VPC Flow Logs enable administrators to understand network traffic patterns, detect anomalies, and enhance security monitoring.
FAQs:
Q1. Are user data logs available by default in EC2?
A. No, user data logs are not enabled by default in EC2. Administrators need to configure AWS services such as CloudTrail, AWS Config, and VPC Flow Logs to capture user activity.
Q2. How long are the logs retained in EC2?
A. The retention period for user data logs in EC2 varies depending on the service. For CloudTrail, the logs are retained for 90 days, while AWS Config retains logs for 7 years. VPC Flow Logs can be stored for any duration based on user preference.
Q3. Can I set up alerts for specific user activities?
A. Yes, EC2 allows you to create alarms and notifications based on specific log events. For example, you can configure an alarm to trigger when an unauthorized access attempt is detected.
Q4. Can I export user data logs to external tools for analysis?
A. Yes, EC2 provides options to export logs to Amazon S3, permitting integration with external tools like AWS Athena, Splunk, or other log analysis systems.
Q5. Can I use third-party log analysis tools with EC2?
A. Yes, EC2 logs are easily accessible and can be consumed by third-party log analysis tools. Administrators can export logs or use AWS integrations with tools and services such as Amazon CloudWatch and Athena.
Conclusion:
Checking user data logs in Amazon EC2 is imperative for maintaining security, compliance, and adhering to data privacy regulations. By configuring and monitoring CloudTrail, AWS Config, and VPC Flow Logs, administrators can effectively track user activities, detect anomalies, and respond to potential security threats promptly. Regularly reviewing user data logs provides improved visibility into user actions and helps ensure the safety and integrity of critical data stored in EC2.
Aws Cloud Init
Introduction
Amazon Web Services (AWS) offers a wide range of services and features to simplify and streamline the deployment and management of your applications. One such service is AWS CloudInit, a powerful tool designed to enhance the bootstrapping process of Amazon Elastic Compute Cloud (EC2) instances. CloudInit enables users to seamlessly configure new instances during their first boot, saving time and effort in setting up each individual instance manually. In this article, we will explore the capabilities and benefits of AWS CloudInit, its usage scenarios, and frequently asked questions about this useful service.
Understanding AWS CloudInit
AWS CloudInit streamlines the process of initializing EC2 instances by providing a simple, declarative way of customizing them at launch. Traditionally, administrators had to manually intervene in each instance’s initial boot process to configure settings like SSH keys, instance hostname, and user data. With CloudInit, these configurations can be automated and specified using a lightweight scripting language that is both human-readable and machine-parseable.
CloudInit Configuration and User Data
CloudInit leverages User Data, a feature of EC2 instances that enables users to provide custom scripts and run them during the instance’s first boot process. This scripting capability allows users to automate the configuration of their EC2 instances with minimal effort. Users can utilize CloudInit’s extensive list of modules to configure settings such as packages to install, system settings, users and groups, mount points, and even custom scripts for more advanced customizations.
CloudInit configurations are specified as a series of modules or directives in a YAML or cloud-config format, depending on the Linux distribution used. These configurations can be passed to the instance through User Data, enabling them to be executed automatically upon first boot. AWS CloudInit supports various distributions such as Amazon Linux, Ubuntu, CentOS, and more.
Data Sources and Metadata
In addition to User Data, AWS CloudInit also supports different data sources to retrieve metadata about the instance. These data sources include EC2 instance metadata service (IMDS), EC2 instance user data service, and other custom data sources. These data sources provide valuable information such as instance ID, region, availability zone, and public/private IP addresses, which can be dynamically used within CloudInit scripts for enhanced flexibility and automation.
Usage Scenarios
AWS CloudInit offers a wide range of applications for EC2 instance initialization. Some common usage scenarios include:
1. Configuration Management: CloudInit simplifies the process of configuring instances by automating tasks such as package installations, user creation, and file system configuration. This eliminates the need for manual intervention and speeds up the deployment process.
2. Customized Bootstrapping: CloudInit allows for the customization of EC2 instances during the initial boot process. This can include running scripts, modifying package repositories, and installing additional software or utilities.
3. Application Deployment: CloudInit supports the installation and setup of applications on EC2 instances. It can retrieve application packages from various sources and automate the installation process, saving time and effort.
4. Cluster Configuration: CloudInit facilitates the creation of clusters by automatically configuring instances with settings specific to cluster environments. This ensures consistency across instances and simplifies cluster management.
AWS CloudInit FAQs
Q: What operating systems are supported by AWS CloudInit?
A: AWS CloudInit supports a wide range of Linux distributions, including Amazon Linux, Ubuntu, CentOS, Red Hat Enterprise Linux, and others. Windows instances are not natively supported but can be provisioned using EC2Launch.
Q: Can I combine AWS CloudInit with other AWS services?
A: Absolutely! AWS CloudInit is a versatile tool that can be seamlessly integrated with other AWS services. For example, you can use CloudFormation to define your infrastructure and CloudInit to customize your EC2 instances during initialization.
Q: Can AWS CloudInit be used with instance templates or autoscaling groups?
A: Yes, CloudInit configurations can be used with EC2 Launch Templates and launch configurations for EC2 Auto Scaling groups. This allows you to ensure consistent configurations across multiple instances in your infrastructure.
Q: How can I troubleshoot issues with AWS CloudInit?
A: AWS CloudInit logs its activity to various log files on the EC2 instance. You can access these log files to troubleshoot any issues encountered during the bootstrapping process. Additionally, AWS provides detailed documentation and a supportive community forum to assist you.
Conclusion
AWS CloudInit empowers users to automate and customize the initialization process of their EC2 instances, eliminating the need for manual configuration. With its simple yet powerful scripting capabilities, CloudInit simplifies tasks such as package installations, user management, and application deployments. By leveraging CloudInit’s flexibility and integration with other AWS services, users can enhance the efficiency of their infrastructure deployments while reducing operational efforts.
User Data Ec2
Introduction:
User Data is a powerful feature offered by Amazon Web Services (AWS) for its Elastic Compute Cloud (EC2) instances. This feature allows users to run scripts or execute commands on an EC2 instance during its launch. User Data provides immense flexibility to customize and configure instances, making it an essential tool for developers and system administrators. In this article, we will delve into the details of User Data EC2, exploring its functionality, benefits, and common use cases.
Understanding User Data EC2:
User Data EC2 enables users to automate the configuration and customization of newly launched EC2 instances. It allows users to provide scripts or commands that execute sequentially inside the instance at boot time. These scripts can be written in various languages such as Bash, PowerShell, Python, or even in the form of cloud-init directives. User Data scripts can perform tasks such as installing software, configuring system settings, pulling data from external sources, and more.
Benefits of User Data EC2:
1. Automation: User Data EC2 streamlines the instance initialization process by automating repetitive tasks. It eliminates the need for manual configuration, reducing human error and saving valuable time.
2. Scalability: With User Data, setting up multiple EC2 instances becomes effortless. By provisioning instances with identical User Data scripts, you can ensure consistent configurations across the entire fleet.
3. Customization: User Data empowers developers and system administrators to tailor instances to their specific requirements. It allows the installation of software packages, configuration of system settings, and deployment of application code during boot time.
4. Easy Deployment: User Data simplifies the deployment of complex applications by automating the installation and configuration process. This ensures consistent and error-free deployments across different environments.
Common Use Cases of User Data EC2:
1. Application Configuration: User Data scripts can be used to automate the setup and configuration of applications on EC2 instances. From installing web servers and databases to configuring load balancers, User Data makes the process seamless and efficient.
2. Auto-Scaling: User Data plays a crucial role in auto-scaling scenarios. When new instances are launched as part of an auto-scaling group, User Data scripts can dynamically configure these instances to join the application cluster without any manual intervention.
3. Log Collection: User Data scripts can be utilized to specify log collection mechanisms in instances. For example, you can configure instances to automatically send logs to centralized logging services such as Amazon CloudWatch Logs, Elasticsearch, or Splunk.
4. Bootstrapping: User Data is an effective tool for bootstrapping instances with basic configurations needed to join a cluster or network. This includes setting up hostnames, joining Active Directory domains, adjusting firewall rules, and more.
Frequently Asked Questions (FAQs):
Q1. Can User Data be modified after an instance is launched?
Yes, User Data can be modified after the instance’s initial launch. However, the modified User Data will only be executed upon reboot or instance termination and subsequent relaunch.
Q2. Are there any limitations to User Data scripts?
User Data scripts have a size limit of 16 KB for Linux instances and 64 KB for Windows instances. Additionally, script execution time should be within EC2 instance launch timeouts.
Q3. Can User Data scripts be retrieved from within the instance?
Yes, User Data scripts can be accessed from within the instance via the following endpoint: `http://169.254.169.254/latest/user-data/`.
Q4. Can User Data scripts be used to modify existing instances?
No, User Data scripts can only be executed during instance launch. To apply changes to existing instances, you can create an AMI (Amazon Machine Image) with the desired User Data and launch new instances from the updated AMI.
Q5. Are there any security considerations when using User Data EC2?
While User Data scripts themselves do not pose a security risk, it is essential to ensure that the scripts incorporated do not compromise the security of the instances or the environment. AWS recommends avoiding including sensitive information, such as access credentials, within User Data scripts.
Conclusion:
User Data EC2 is a powerful feature that allows users to automate the configuration and customization of EC2 instances during their launch. With its ability to streamline the setup process, User Data saves time, reduces errors, and enhances scalability. By leveraging User Data scripts, developers and system administrators can achieve consistent and efficient deployments of complex applications. With its numerous use cases and benefits, User Data EC2 serves as an indispensable tool for managing and customizing instances in the AWS environment.
Images related to the topic ec2 cloud init logs

Found 21 images related to ec2 cloud init logs theme












Article link: ec2 cloud init logs.
Learn more about the topic ec2 cloud init logs.
- Where is log output from cloud-init stored? – Server Fault
- Troubleshoot using cloud-init – Azure Virtual Machines | Microsoft Learn
- system level logs – AMS Advanced User Guide
- cfn-init vs user-data – Lono
- cloud-init-output.log being overwritten on EC2 instance
- Debugging cloud-init – cloud-init 23.2.1 documentation
- Log your EC2 Linux user data and then ship it to the console …
- Troubleshooting EC2 startup scripts passed as user-data
- ec2-with-cloudwatch-logs.yaml – GitHub Gist
- Bug #1981960 “cloud-init-output.log is increasing its size very …
- How to stream AWS EC2 cloud-init logs to ELK?