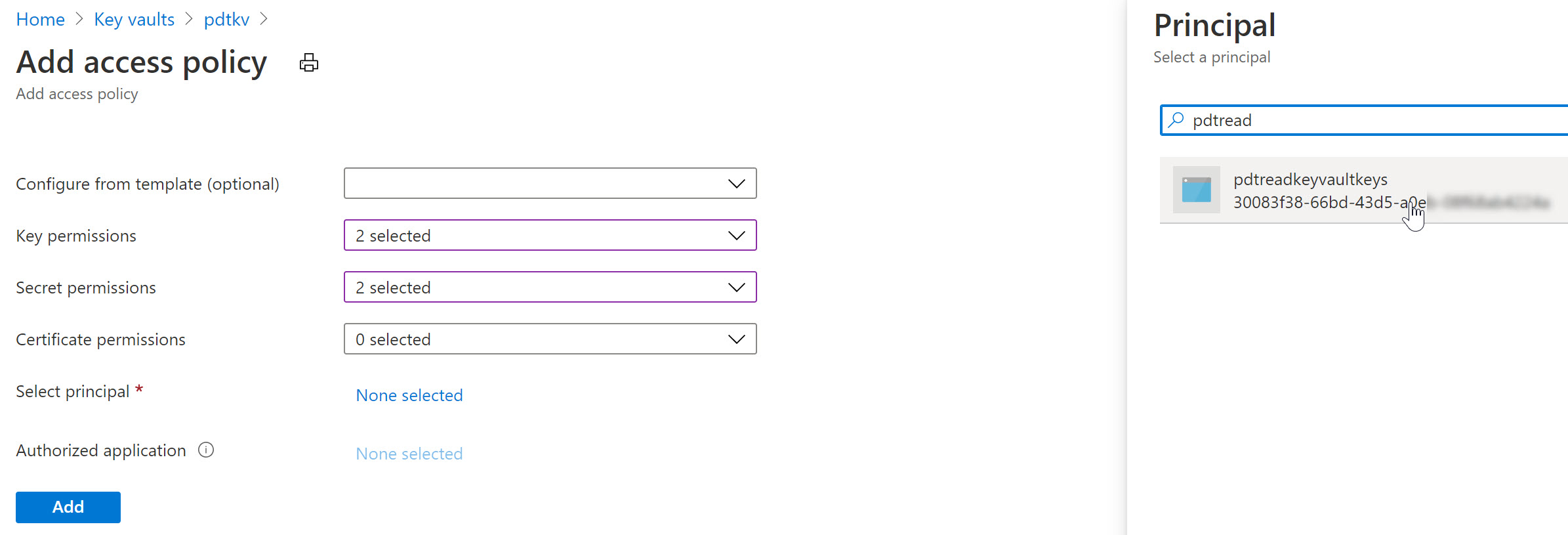
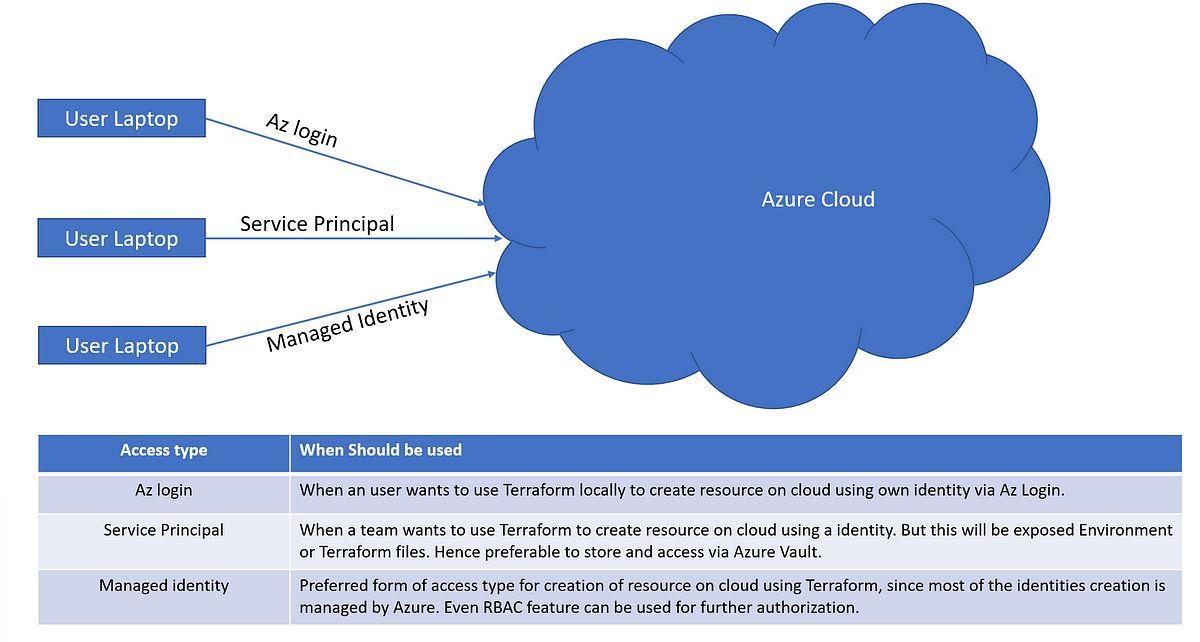
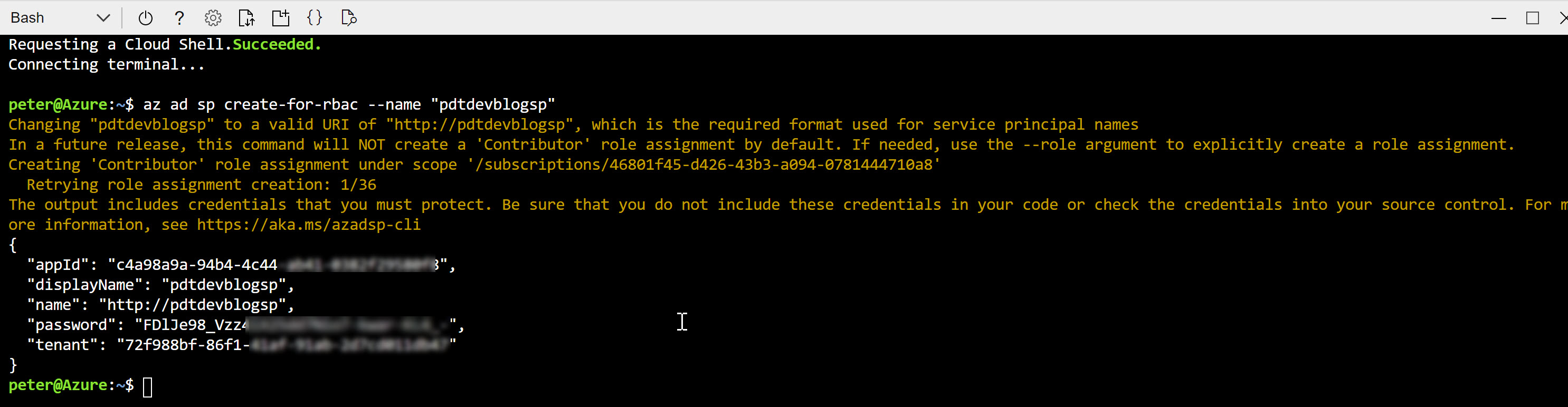
Managed Identity Vs Service Principal
Overview
In the realm of Microsoft Azure, managing identities and authenticating applications and services plays a vital role. Two commonly used methods for this purpose are Managed Identity and Service Principal. Both serve as authentication mechanisms and have their own advantages and use cases. In this article, we will explore the differences, benefits, and best practices when choosing between Managed Identity and Service Principal.
Understanding Managed Identity
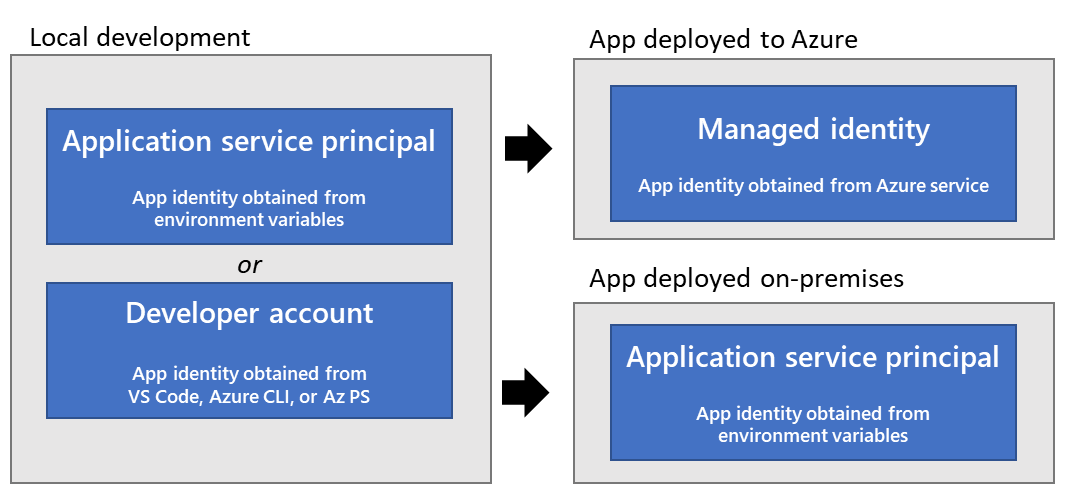
Managed Identity is a feature in Azure that provides an automatically managed identity for Azure services to authenticate with other Azure services. It eliminates the need for developers to manage their own credentials or secrets explicitly within the code or configuration files. Azure automatically handles the lifecycle of the identity, including its creation, rotation, and revocation.
Managed Identity leverages Azure Active Directory (Azure AD), which acts as a trust broker between the identity provider and the Azure service. It uses OAuth 2.0 or OpenID Connect to authenticate and obtain an access token for subsequent service-to-service communication.
Understanding Service Principal
A Service Principal, on the other hand, is a manually created identity in Azure AD that represents an application or an automated process, rather than an individual user. It is similar to a user account but specifically designed for authentication between a service and Azure resources.
To create a Service Principal, you need to register an application in Azure AD and assign it a specific set of permissions. These permissions determine what the application can access in Azure. Once created, the Service Principal is assigned a unique identity and associated secrets, such as a client ID and client secret.
Key Differences between Managed Identity and Service Principal
1. Creation Process: Managed Identity is automatically created by Azure for a specific Azure resource, while Service Principal requires manual registration and configuration.
2. Credentials Management: Managed Identity eliminates the need for developers to handle or store credentials explicitly, whereas Service Principal requires developers to manage the client ID and client secret securely.
3. Scope: Managed Identity is scoped to a specific Azure resource and is only accessible within that resource, whereas Service Principal can be granted access to multiple resources or subscriptions.
4. Lifespan: Managed Identity is tied to the lifecycle of the Azure resource it is associated with, while Service Principal has a separate lifecycle and can exist independently of any specific Azure resource.
Use Cases for Managed Identity
Managed Identity is particularly useful when developing Azure services or applications that require seamless authentication with other Azure resources. It simplifies the authentication process by eliminating the need for explicit credential handling. Use cases for Managed Identity include:
1. Azure Functions: Azure Functions can use Managed Identity to access Azure Key Vault or Azure Storage without the need for explicit credentials.
2. Azure Virtual Machines: Managed Identity can be used by virtual machines to access Azure Resource Manager APIs or Azure Key Vault securely.
3. Azure App Services: Managed Identity allows App Services to authenticate with Azure SQL Database or other Azure services without requiring connection strings or secrets.
Use Cases for Service Principal
Service Principal is more suitable for scenarios that involve third-party applications or services that require access to Azure resources. Some common use cases for Service Principal are:
1. Continuous Integration/Continuous Deployment (CI/CD): Service Principal is often used in CI/CD pipelines to authenticate and interact with Azure resources during the deployment process.
2. Application Registration: Service Principal is used when registering applications that require access to Azure resources, such as Azure Management APIs or Azure Data Lake Storage.
3. Non-Azure Applications: Service Principal can be used to authenticate non-Azure applications or services with Azure resources, enabling secure communication.
Best Practices for Choosing Between Managed Identity and Service Principal
While selecting between Managed Identity and Service Principal, consider the following best practices:
1. Complexity: If you require minimal efforts in managing identities and seamless authentication, Managed Identity is the recommended option. For more fine-grained control or complex scenarios, consider using Service Principal.
2. Single Resource vs Multiple Resources: If the authentication is limited to a single Azure resource, Managed Identity is preferred. If the application requires access to multiple Azure resources, Service Principal offers greater flexibility.
3. Third-Party Integrations: If the application involves third-party integrations or requires access to non-Azure resources, Service Principal is a suitable choice.
4. Security: Ensure that credentials, such as client ID and client secret associated with Service Principal, are managed securely to prevent unauthorized access.
FAQs
1. What is an Azure Service Principal?
Azure Service Principal is a manually created identity in Azure AD that authenticates applications or services with Azure resources. It represents an application or automated process rather than a user.
2. What is the difference between Service Principal and Managed Identity?
Service Principal is manually created and provides greater control and flexibility, whereas Managed Identity is automatically created by Azure and simplifies authentication by leveraging Azure AD.
3. How do I create a Managed Identity in Azure?
Managed Identity is created automatically when you enable it on an Azure resource such as Azure Functions, Virtual Machines, or App Services.
4. What is the purpose of using a Managed Identity in AKS (Azure Kubernetes Service)?
Managed Identity in AKS enables easy and secure access to Azure resources by providing an identity to control permissions and eliminate the need for explicit credentials.
In conclusion, both Managed Identity and Service Principal have their own strengths and use cases in Azure authentication. Understanding the differences and considering the specific requirements of your application or service will help you make the right choice. Whether it’s seamless authentication or fine-grained control, Azure provides the necessary tools to secure and manage identities effectively.
Choosing Right Identity For Azure Services | Managed Identity Vs Service Principal
What Is The Difference Between Azure Service Principal And Managed Identity?
In the world of cloud computing, Microsoft Azure provides a range of services that allow users to build, deploy, and manage applications efficiently. Two important authentication concepts within Azure are service principals and managed identities. While both of them enable secure access to Azure resources, they have distinct differences and use-cases. In this article, we will explore the differences between Azure service principals and managed identities, and shed light on when to use each of them.
Azure Service Principal:
Azure service principal is a security identity used by applications, services, and automated tools to access Azure resources programmatically. In other words, it is a form of a non-human user identity that grants permissions to applications. Service principals allow applications to authenticate using a client ID, client secret, and tenant ID, or a certificate.
Here are a few key points to consider about Azure service principals:
1. Setup and Management: Service principals are created and managed within Azure Active Directory (Azure AD). They can be created manually or through automation. Manual creation involves registering the application and assigning appropriate permissions. Moreover, service principals can be managed using PowerShell, Azure CLI, or programmatically using Azure SDKs.
2. Granular Permissions: With service principals, you can have finer control over the permissions granted to an application. Permissions can be granted at the subscription, resource group, or individual resource level. This enables administrators to grant only the necessary privileges while ensuring the principle of least privilege.
3. Non-Interactive Consent: Service principals can be used in non-interactive scenarios such as scripts or automation tasks. This allows applications to access Azure resources without any user intervention. It is particularly useful when accessing resources on behalf of users within a specific scope.
4. Long-lived Secrets: Service principals can use long-lived secrets like client secrets or certificates for authentication. Client secrets are passwords that need to be managed securely, while certificates provide a more secure authentication method that can be managed through Azure Key Vault.
Managed Identity:
Managed identities in Azure provide an effortless way to authenticate and authorize applications and services without the need for explicit credentials management. Managed identities integrate directly with Azure Active Directory and are automatically managed by Azure. With this approach, Azure itself creates an identity for the application or service and handles its lifecycle.
Here are a few key points to consider about Azure managed identities:
1. Automatic Creation and Lifecycle Management: Managed identities are automatically created and managed by Azure. You don’t need to manually create or configure them. Azure assigns a unique identity to the application or service and handles the rotation and management of its credentials.
2. Simplified Authentication: Using a managed identity, an application or service can acquire credentials without the need to store explicit secrets. No client ID, secret, or certificate is required. This simplifies the authentication process and reduces the risk of secret leakage or management issues.
3. Scope of Access Control: Unlike service principals, managed identities have a limited scope of access control. They are typically tied to a single Azure resource, such as a virtual machine (VM) or an Azure function. This limits the managed identity’s permissions to the specific resource and its associated resource group.
4. Seamless Integration with Azure Services: One of the major advantages of managed identities is their seamless integration with various Azure services. Many Azure services, such as Azure Virtual Machines, Azure Functions, and Azure App Service, support managed identity out of the box. This allows these services to directly acquire the managed identity and access other Azure resources without additional configuration.
FAQs:
Q1. When should I use Azure service principal?
A1. Azure service principals are suitable for scenarios where fine-grained control over permissions is required, and applications need to authenticate programmatically without user interaction. It is well-suited for non-interactive scenarios, such as CI/CD pipelines, automation scripts, or accessing resources on behalf of users.
Q2. When should I use Azure managed identity?
A2. Azure managed identities are recommended when you need a straightforward way to authenticate an application or service without managing explicit secrets. It is the ideal choice for scenarios involving Azure services that offer built-in support for managed identity. Managed identities are particularly useful for virtual machines, Azure functions, and other resources that need secure authentication.
Q3. Can I convert a service principal to a managed identity or vice versa?
A3. No, you cannot directly convert a service principal to a managed identity or vice versa. Both Azure service principals and managed identities have different underlying mechanisms and lifecycles. If you need to switch from one to the other, you will need to create a new identity of the desired type and update your application or service accordingly.
Q4. Is one option more secure than the other?
A4. Both Azure service principals and managed identities offer secure authentication mechanisms. However, managed identities eliminate the need to manage explicit secrets, which reduces the risk of secret leakage or management errors. In general, managed identities provide a more secure and convenient way to authenticate applications and services.
In conclusion, Azure service principals and managed identities are both valuable Azure authentication mechanisms, each with their own strengths and use-cases. Service principals provide fine-grained control over permissions and are suitable for non-interactive scenarios, while managed identities offer an effortless way to authenticate without the need to manage explicit secrets, especially for Azure services with direct support. Understanding the differences between them enables you to choose the right authentication method for your specific requirements and scenarios in Azure.
Is A Managed Identity A Service Principal?
In recent years, managed identities have emerged as a popular approach for providing secure authentication and authorization within cloud-based applications and services. One term that often comes up in discussions about managed identities is the “service principal.” However, there can be confusion about whether a managed identity is the same as a service principal. In this article, we will delve into the intricacies of both concepts, exploring their similarities, differences, and the benefits they bring to the table.
Understanding Managed Identities:
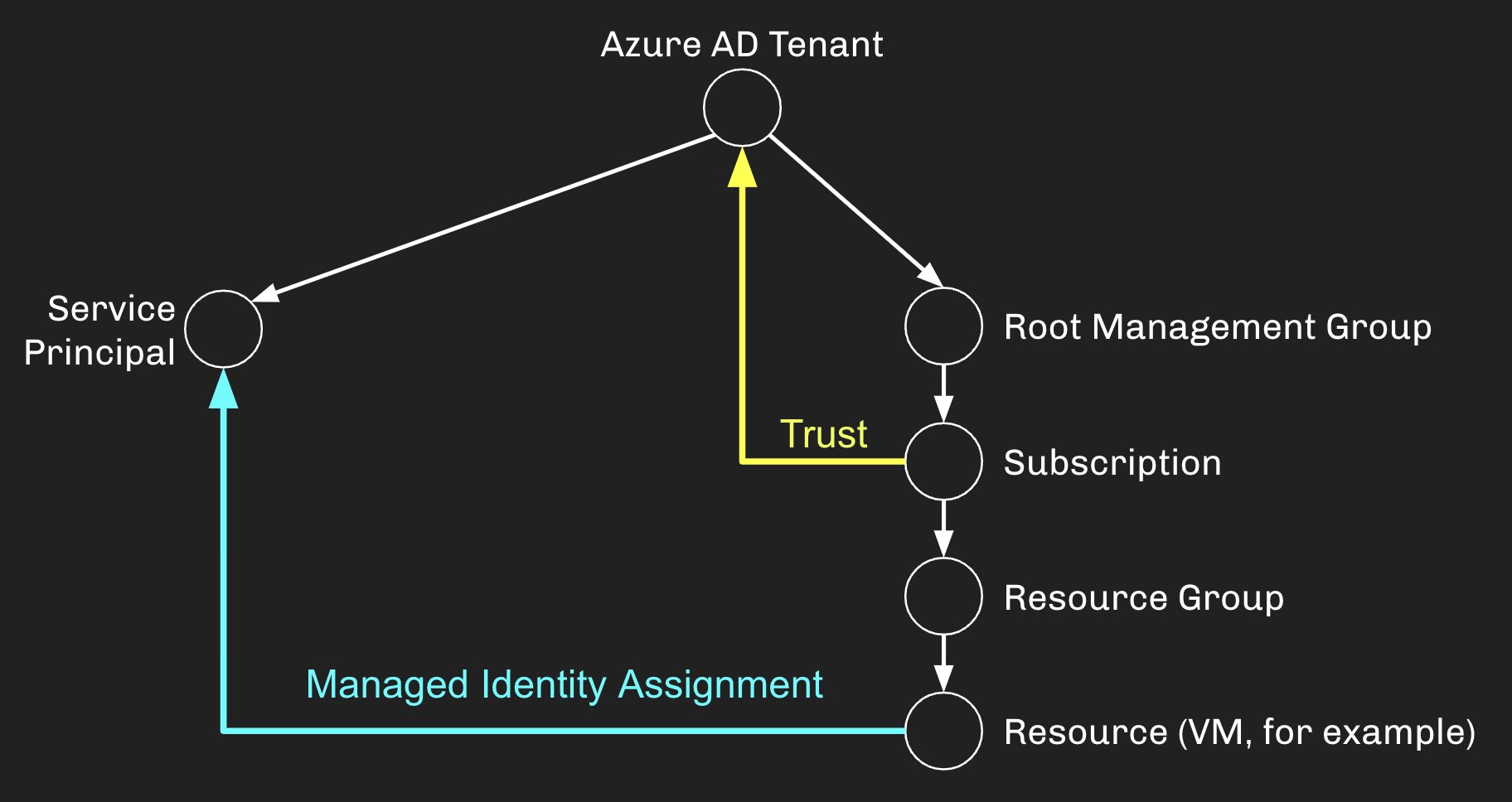
To comprehend the relationship between managed identities and service principals, it is crucial to have a clear understanding of each concept individually. A managed identity refers to an automatically generated identity that is associated with a specific Azure resource. Azure is a cloud computing platform provided by Microsoft. These managed identities enable resources, such as virtual machines or Azure Functions, to authenticate themselves seamlessly to the services they rely on, without requiring explicit authentication credentials.
Managed identities alleviate the need for administrators to manage and secure credentials, reducing the risk of exposure and simplifying the security architecture. These identities work by leveraging the Azure Active Directory (AD) service, which is responsible for issuing and validating tokens that prove an identity’s authenticity.
Exploring Service Principals:
On the other hand, service principals are a concept within the Azure AD that represent non-human identities capable of authenticating against Azure AD. Unlike managed identities, service principals are not automatically generated but must be explicitly created in Azure AD. They are typically used to enable applications and services to interact with Azure resources programmatically or via the Azure command-line interface (CLI). Service principals essentially act as a surrogate identity for the application or service, allowing them to access the resources they require.
Service principals bear similarities to user accounts in Azure AD, but are intended for application-to-application (A2A) or service-to-service (S2S) authentication scenarios, rather than for human users. Service principals have their own object in the Azure AD tenant, complete with their own credentials and permissions.
Relationship Between Managed Identities and Service Principals:
Now that we have a grasp of both concepts, let’s explore the relationship between managed identities and service principals. In simple terms, a managed identity is, in fact, a specific type of service principal. Managed identities are a newer, simpler way to create and manage service principals, specifically designed to simplify the process and enhance security. Therefore, while all managed identities are service principals, not all service principals are managed identities.
By leveraging managed identities, developers can avoid the complexities of manually creating and managing service principals, while still enjoying the benefits of using them. Managed identities automagically handle the creation, regeneration, and subsequent revocation of service principal credentials, simplifying the management overhead and reducing administrative complexities.
The Benefits of Managed Identities:
Managed identities, as a subset of service principals, offer several advantages. Firstly, they eliminate the need to store sensitive authentication credentials within the application or service codebase. This reduces the risk of these credentials being compromised and simplifies the security architecture, as credentials no longer need to be managed, rotated, or revoked. Additionally, managed identities enable seamless integration with Azure resources such as Key Vault, Azure SQL Database, and Azure Storage, without requiring complex manual configuration.
Furthermore, managed identities automatically handle the renewal of expiring tokens issued by Azure AD, ensuring uninterrupted access to resources. This automatic renewal saves developers from having to implement token refresh mechanisms and enhances the application’s reliability.
FAQs:
Q: Can a managed identity be used outside of Azure resources?
A: Managed identities are designed specifically for use within Azure resources. However, various libraries and SDKs provide integrations that allow developers to utilize managed identities outside of Azure to interact with Azure resources.
Q: Can I assign multiple managed identities to a single Azure resource?
A: No, each Azure resource can have only one managed identity associated with it. If multiple resources require access to the same Azure resource, they each need their own managed identity.
Q: Can I delete a managed identity?
A: Yes, managed identities can be deleted. Deleting a managed identity revokes its credentials and removes its association with the Azure resource it was created for.
Q: Are managed identities available in all Azure regions?
A: Managed identities are available in most Azure regions, but it is recommended to consult the Azure documentation for the latest region coverage.
In conclusion, while managed identities and service principals are closely related concepts, they are not entirely interchangeable. Managed identities are a simplified way of managing service principals, designed to enhance security and reduce complexities. By leveraging managed identities, developers can reap the benefits of service principals without the need for manual creation and management. These identities provide a secure and seamless way to authenticate and authorize Azure resources, ensuring reliable and hassle-free communication within cloud-based applications and services.
Keywords searched by users: managed identity vs service principal Azure service principal, Service principal vs managed identity, Azure service principal là gì, Azure service principal ID, Az service principal, Create managed identity azure, AKS managed identity, Managed identity Azure
Categories: Top 29 Managed Identity Vs Service Principal
See more here: nhanvietluanvan.com
Azure Service Principal
In the world of cloud computing, Microsoft Azure has established itself as one of the leading platforms, offering a wide range of services to meet the needs of modern businesses. One crucial aspect of Azure is the concept of a service principal, which plays a vital role in securing and managing access to Azure resources. In this article, we will dive deep into the world of Azure service principals, exploring what they are, why they are important, and how they can be used effectively.
What is an Azure Service Principal?
In simple terms, an Azure service principal is a unique identity created for use with applications, services, or automation tools to access specific Azure resources. It is similar to a user identity (or principal) within Azure Active Directory (AD) but is intended for non-human entities, such as applications or automated scripts.
Why are Azure Service Principals Important?
Azure service principals are important for several reasons. First and foremost, they provide a secure way to access Azure resources, as they are assigned specific roles and permissions. By utilizing service principals, organizations can ensure that only authorized applications or tools have access to their resources, minimizing the risk of unauthorized access.
Furthermore, service principals enable seamless automation and integration with Azure resources. They allow applications or scripts to authenticate themselves and acquire the necessary access tokens without requiring any user intervention. This eliminates the need to hard code or store sensitive credentials within an application.
How to Create an Azure Service Principal?
Creating an Azure service principal is a straightforward process. There are various methods available, including Azure portal, Azure CLI, PowerShell, and Azure DevOps. Let’s explore the steps involved in creating a service principal using the Azure portal:
1. Navigate to the Azure portal (portal.azure.com) and sign in with your Azure credentials.
2. Open the Azure Active Directory blade and select “App registrations”.
3. Click on “New registration” to create a new application registration.
4. Provide a name for your application, select the appropriate account type, and specify the redirect URI (optional).
5. Once the registration is complete, note down the “Application (client) ID” and “Directory (tenant) ID”. These are the unique identifiers associated with your service principal.
6. To grant the necessary permissions to your service principal, open the “API permissions” tab and click on “Add a permission”. Choose the required permissions based on your application’s needs.
7. After granting the permissions, click on “Certificates & secrets” to create a client secret. This secret will be used to authenticate your service principal.
8. Finally, note down the value of the client secret, as it will be required while authenticating your service principal.
FAQs:
Q: What is the difference between a service principal and an application?
A: While an application registration represents the application itself, a service principal is the specific instance or identity created for that application to access Azure resources. An application registration can have multiple service principals associated with it, enabling better management and control.
Q: Can a service principal access resources across multiple Azure subscriptions?
A: Yes, a service principal can be granted access to resources across multiple Azure subscriptions. However, the necessary permissions must be configured at the subscription level to allow access.
Q: How can I use a service principal in my application code?
A: To utilize a service principal in your application code, you can leverage Azure SDKs or Azure Active Directory authentication libraries. These libraries provide easy-to-use methods for authentication and acquiring access tokens using the credentials of your service principal.
Q: Can I assign custom roles and permissions to a service principal?
A: Yes, service principals can be assigned custom roles and permissions to grant fine-grained access control. This allows organizations to tailor the access rights based on their specific requirements.
Q: How can I rotate the client secret for a service principal?
A: To rotate the client secret for a service principal, navigate to the “Certificates & secrets” section of your application registration in the Azure portal. Click on “New client secret” to generate a new secret, and update your application code with the new secret value.
In conclusion, Azure service principals are an indispensable tool for securing and managing access to Azure resources. By creating and utilizing service principals effectively, organizations can enhance the security of their applications, automate processes, and integrate seamlessly with Azure. Understanding the concept, creation process, and best practices surrounding Azure service principals is crucial for anyone working with Azure resources.
Service Principal Vs Managed Identity
Introduction
In modern cloud environments, securing access to resources and applications is of paramount importance. Two popular approaches to accomplish this in Microsoft Azure are Service Principal and Managed Identity. Although both provide secure authentication and authorization mechanisms, they are different in terms of their usage scenarios and functionality. In this article, we will delve deeper into the concepts of Service Principal and Managed Identity, highlighting their similarities, differences, and use cases.
Service Principal: An Overview
A Service Principal is essentially a non-human identity used by applications or services to authenticate and interact with various resources within Azure. It acts as a representative for an application or a service, allowing it to authenticate and request access to Azure resources. Service Principals are typically used in scenarios where applications need to access Azure resources programmatically, without the need for user intervention.
To create a Service Principal, administrators can use the Azure portal, Azure CLI, or Azure PowerShell. Once created, Service Principals are assigned specific roles and permissions to control their access to resources. These roles can be customized to restrict or grant specific privileges, ensuring granular control over the application’s actions. Service Principals can also be used to authenticate applications across different tenants, making them highly versatile.
Managed Identity: An Overview
Managed Identity, on the other hand, is an Azure Active Directory (Azure AD) feature that provides an easier and more streamlined method of managing identities within Azure. Unlike Service Principals, Managed Identity is automatically created and managed by Azure itself. It simplifies the process of authenticating and securely accessing Azure resources, reducing the need for explicit credential management.
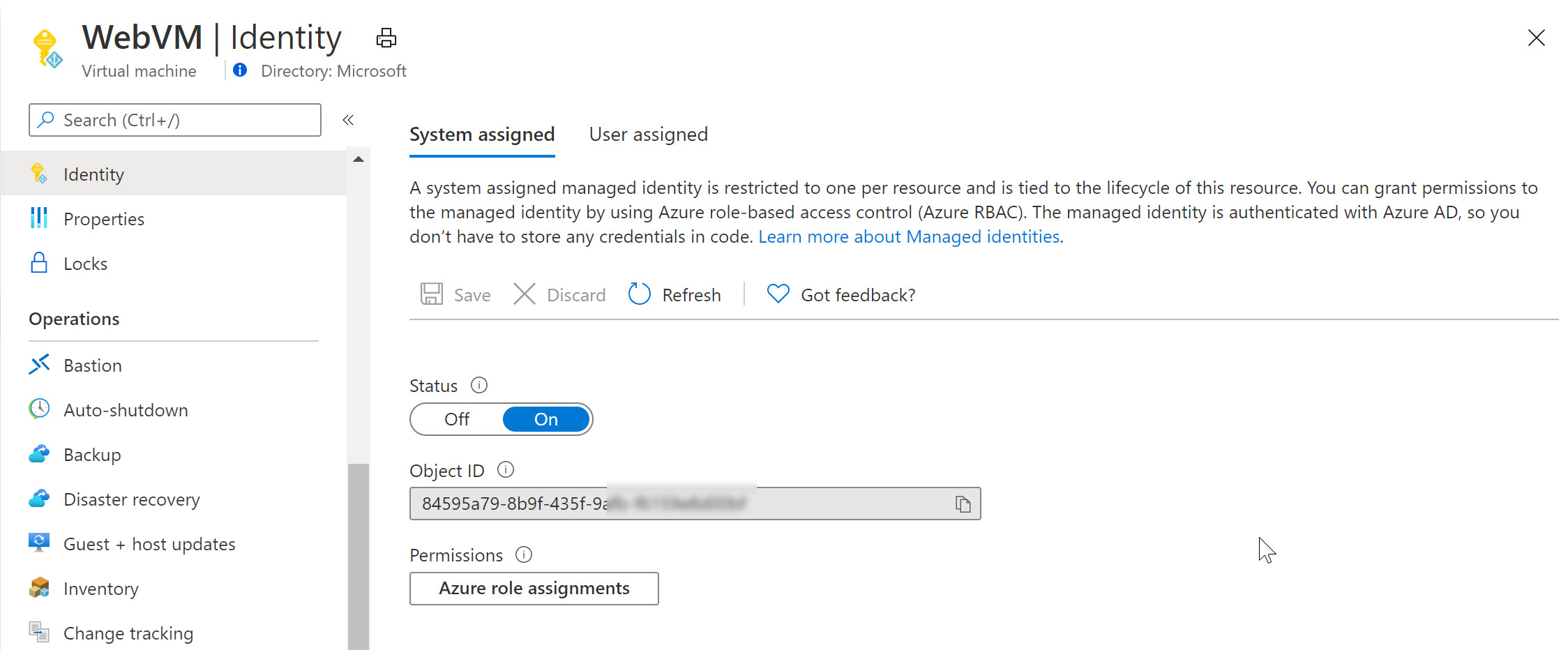
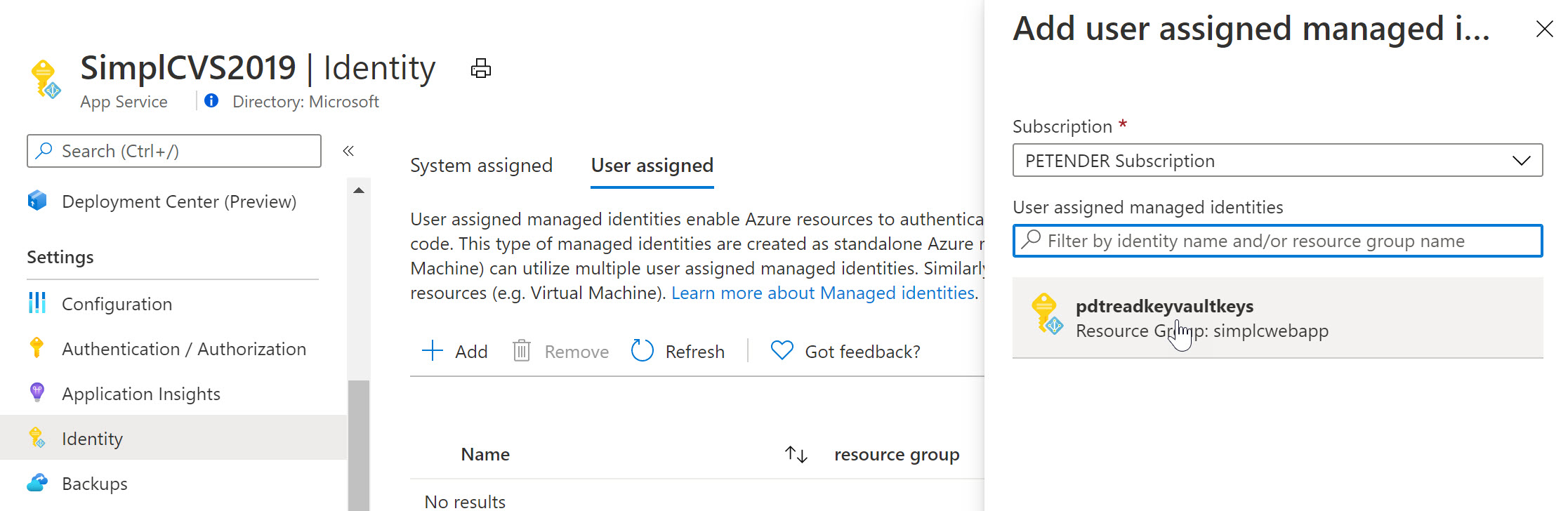
There are two types of Managed Identity available in Azure: System-assigned and User-assigned Managed Identities. A System-assigned Managed Identity is enabled directly on an Azure resource, such as a virtual machine or an Azure function. On the other hand, a User-assigned Managed Identity is created as a standalone Azure AD object and can be assigned to multiple Azure resources.
Comparison and Use Cases
While both Service Principal and Managed Identity provide secure access, there are distinct differences in their functionality and common use cases.
1. Creation Process:
Service Principals require explicit creation by an administrator, which involves manually specifying the application’s details and credentials. On the contrary, Managed Identity eliminates the need for manual creation, as Azure automatically handles the process.
2. Credential Management:
Service Principals rely on a combination of a client ID, client secret, and tenant ID to authenticate and access resources. These credentials must be explicitly managed and protected. In contrast, Managed Identity leverages Azure AD for authentication, eliminating the need to handle explicit credentials. In this case, Azure handles the rotation and management of the underlying credentials.
3. Scoping:
Service Principals are often scoped to a single application or service, providing a more focused identifier for authentication purposes. Managed Identities, particularly User-assigned ones, can be shared across multiple resources, allowing for centralized management and reduced administrative effort.
4. Use Cases:
Service Principals are commonly used in scenarios where applications require programmatic access to Azure resources. For example, an application that needs to provision or manage Azure resources during its runtime would benefit from using a Service Principal. Managed Identity, on the other hand, is typically recommended for applications running within Azure, as it removes explicit credential management and provides a more secure authentication method.
FAQs
1. Can Service Principals and Managed Identities be used interchangeably?
While Service Principals and Managed Identities share the same underlying goal of providing secure access to Azure resources, they differ in their creation process, credential management, and scoping. Thus, they are not interchangeable, and the choice between them should depend on the specific requirements and use case of your application.
2. Can a Managed Identity be converted to a Service Principal?
No, a Managed Identity cannot be converted to a Service Principal. However, a Service Principal can be created for an existing Managed Identity, allowing the application to have multiple authentication options.
3. Can I specify custom roles and permissions for a Managed Identity?
Yes, you can assign custom roles and permissions to a Managed Identity. This enables granular control over the actions the application or service can take within Azure.
4. Can Managed Identities be used outside Azure?
Managed Identities are primarily designed for Azure resources and cannot be used directly outside the Azure ecosystem. However, Azure AD supports various identity federation protocols, such as OAuth and OpenID Connect, which can enable authentication across multiple systems.
Conclusion
In summary, Service Principals and Managed Identities are two vital authentication and authorization mechanisms in Azure. While Service Principals provide more flexibility and customization options, Managed Identity offers a streamlined approach by eliminating the need for explicit credential management. By understanding the differences and use cases of each, organizations can choose the right identity management solution that aligns with their application and security requirements, ensuring secure and efficient access to Azure resources.
Images related to the topic managed identity vs service principal

Found 11 images related to managed identity vs service principal theme
















-2x.jpg?width=2480&name=13%20(edited)-2x.jpg)
















Article link: managed identity vs service principal.
Learn more about the topic managed identity vs service principal.
- Azure Managed Identity Vs Azure Service Principal – C# Corner
- Why and how to create Azure service principals – TechTarget
- Use Azure Active Directory service principals & managed identities
- Manage user-assigned managed identities – Microsoft Entra
- Securing service principals in Azure Active Directory – Microsoft Entra
- Demystifying Service Principals – Managed Identities
- Difference between Service Principal and Managed Identities …
- Why and how to create Azure service principals – TechTarget
- Managed Identities vs Service Principals – when to use what
- Azure – Service Principals v/s Managed Identities – LinkedIn
- Azure Managed Identity vs Service principal
- Difference between Service Principal and Managed Identity in …
- What’s an Azure Service Principal and Managed Identity?
- Azure Service Principals and Azure Managed Identities
See more: https://nhanvietluanvan.com/luat-hoc