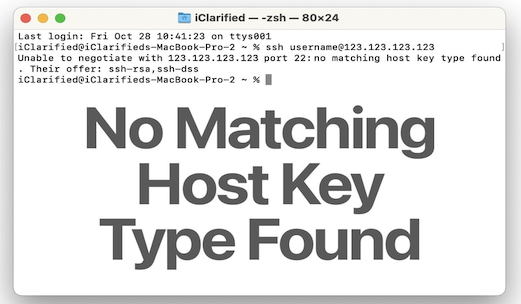
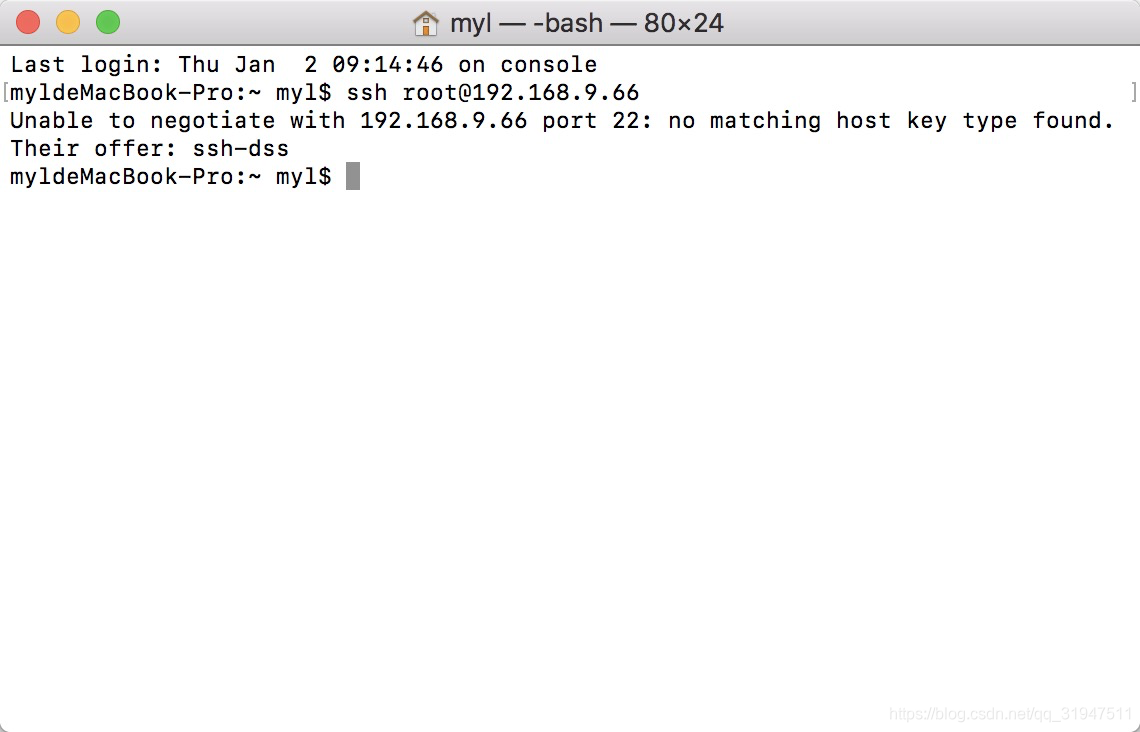
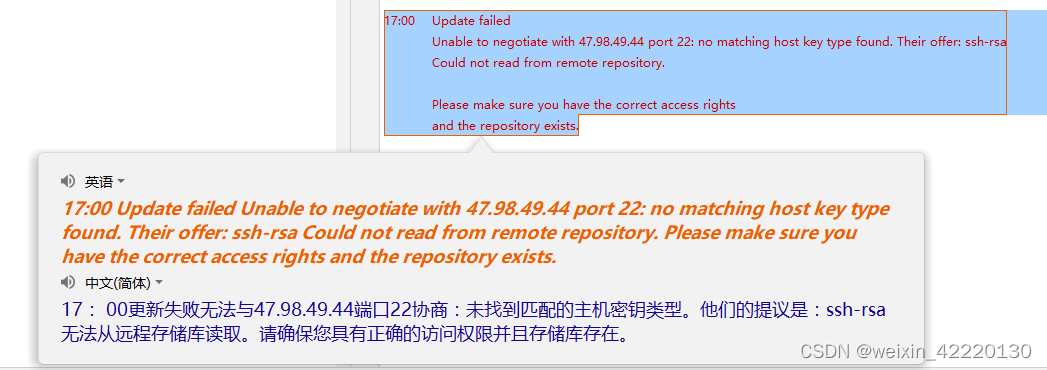
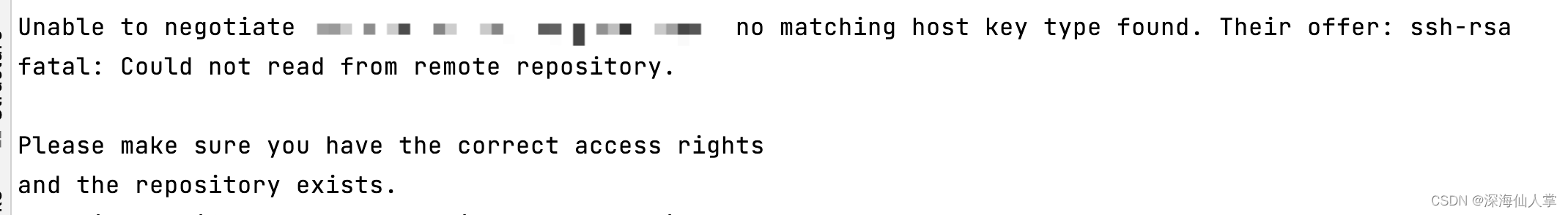
No Matching Host Key Type Found. Their Offer Ssh-Rsa Ssh-Dss
1. Definition and Explanation of “No Matching Host Key Type Found”
The “No Matching Host Key Type Found” error occurs when establishing an SSH (Secure Shell) connection between a client and a server. SSH uses cryptographic keys, known as host keys, for secure communication. The error message indicates that the client and server do not have a matching host key type, leading to the failure of the SSH connection.
2. Understanding SSH and Host Key Types
SSH is a protocol used for secure remote access to systems and secure file transfers. It provides a secure channel by encrypting the entire communication between the client and the server. One of the key components of SSH is the host key, which allows the client to verify the authenticity of the server.
Host keys are generated on the server side and act as a unique fingerprint for each server. When a client connects to a server, it checks the host key to ensure it matches the known key on record. If they match, the connection proceeds; otherwise, it raises the “No Matching Host Key Type Found” error.
3. SSH-RSA: Description, Advantages, and Usage
SSH-RSA (SSH-Rivest-Shamir-Adleman) is a widely used public key algorithm for SSH connections. It utilizes the RSA encryption algorithm for secure key exchange and authentication. RSA offers strong security and is commonly supported by SSH clients and servers.
Advantages of SSH-RSA:
– Widely supported by SSH implementations.
– High security and strong encryption.
– Good performance for most use cases.
– Compatibility with various systems and devices.
Usage of SSH-RSA:
– SSH-RSA is widely used in many SSH environments.
– It can be used for secure remote login and file transfer.
– SSH clients and servers often support SSH-RSA by default.
4. SSH-DSS: Description, Advantages, and Usage
SSH-DSS (SSH-Digital Signature Standard) is another public key algorithm used in SSH connections. It employs the Digital Signature Standard for key exchange and authentication. While SSH-DSS was widely used in the past, it has been deprecated in favor of newer and more secure algorithms.
Advantages of SSH-DSS:
– Wide compatibility with older SSH implementations.
– Suitable for legacy systems that do not support newer algorithms.
Usage of SSH-DSS:
– SSH-DSS is commonly used in older SSH environments.
– It can be used for secure remote access and file transfers.
– However, it is recommended to migrate to stronger algorithms due to security concerns.
5. Common Causes for “No Matching Host Key Type Found” Error
a. Outdated SSH Client/Server: The client or the server involved in the SSH connection may be running an outdated version, which does not support the host key algorithm being used.
b. Mismatched Host Key Types: The client and server have different host key types configured. For example, the client expects an RSA key, but the server only offers a DSS key.
c. Deprecated Algorithms: The server may be using a deprecated host key algorithm that is no longer supported by the client. For instance, if the server uses SSH-DSS, but the client only supports SSH-RSA, the error will occur.
6. Troubleshooting Steps to Resolve “No Matching Host Key Type Found” Error
a. Update SSH Client/Server: Ensure that both the client and server are running the latest versions to support a wider range of host key algorithms.
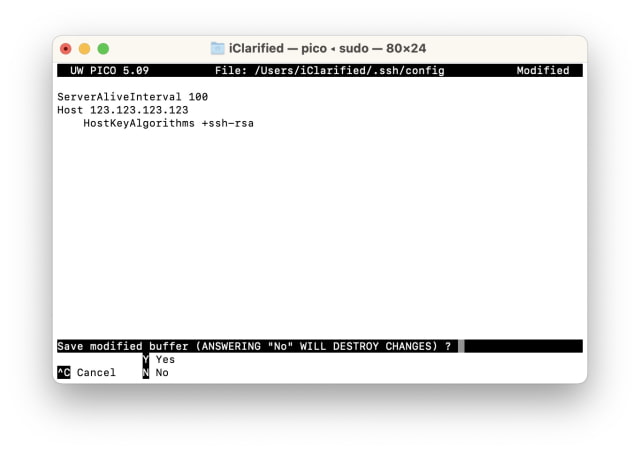
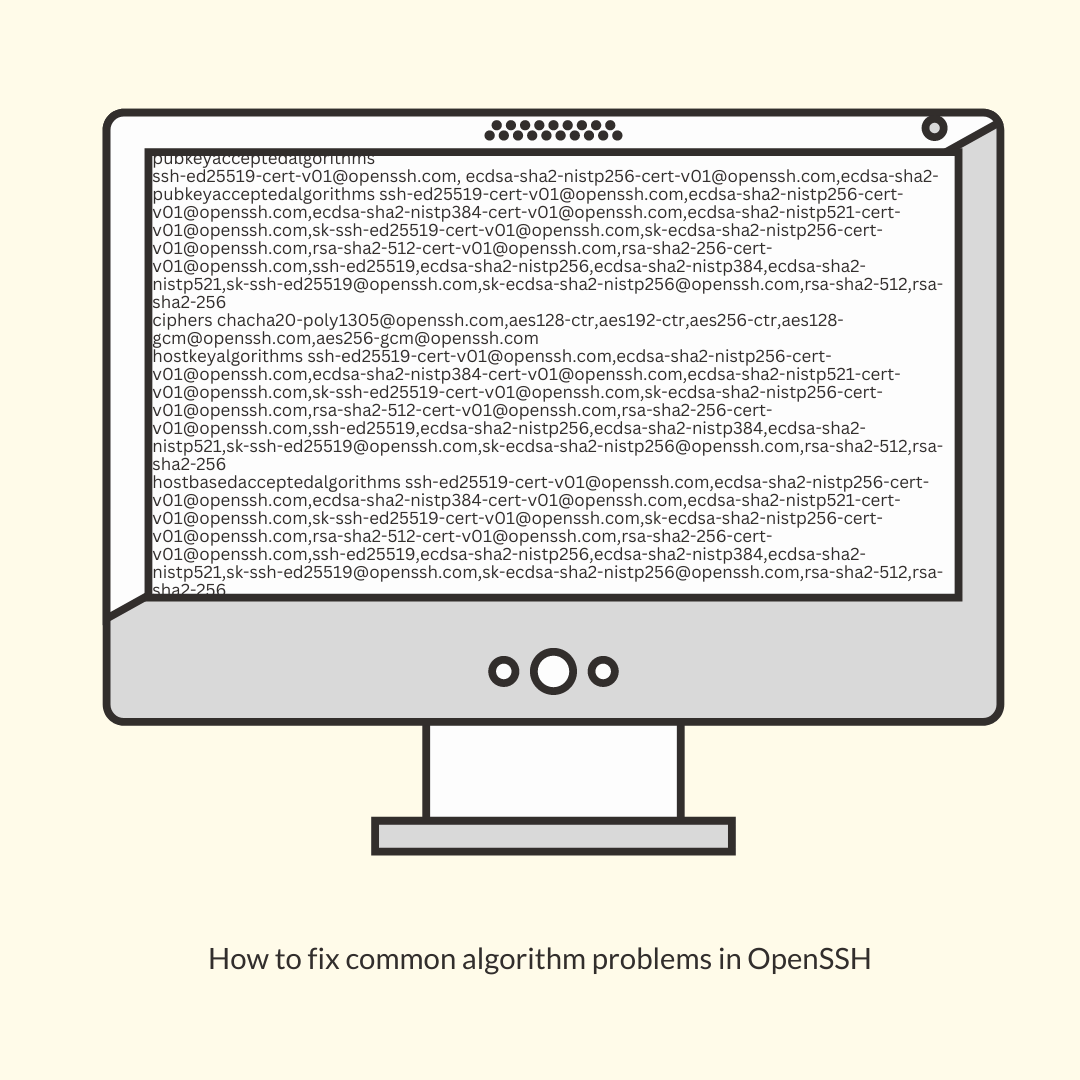
b. Check Host Key Configurations: Verify that the client and server have matching host key types configured. Make necessary changes to match the desired algorithm.
c. Remove Deprecated Algorithms: If you encounter this error due to a deprecated algorithm, consider disabling it on the server or migrating to a stronger algorithm that is supported by the client.
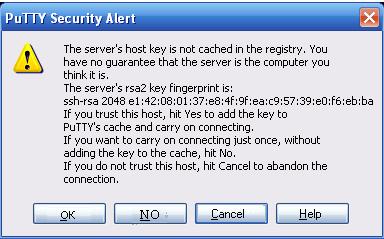
d. Verify Server Identity: Ensure that the server you are connecting to is indeed the intended server and not a malicious one. Cross-check the server’s fingerprint with trusted records.
7. Ensuring Compatibility: Updating SSH Client and Server Configurations
To avoid the “No Matching Host Key Type Found” error, it is important to maintain updated versions of SSH clients and servers. Regularly updating both ends ensures compatibility with the latest host key algorithms and security improvements. It is also recommended to disable or phase out deprecated algorithms to enhance security.
Specific configurations for SSH clients and servers can vary across different operating systems and SSH implementations. Ensure that the desired host key algorithm is supported and enabled in both the client and server configurations.
8. Best Practices for Secure SSH Connections: Key Type Recommendations
To ensure secure SSH connections, it is important to follow best practices when selecting host key algorithms. Here are some recommendations:
– Use SSH-RSA or other modern algorithms such as ECDSA or Ed25519 for host key generation and authentication.
– Avoid using SSH-DSS, as it is deprecated and no longer considered secure.
– Regularly update SSH clients and servers to utilize the latest security enhancements and algorithms.
– Disable or remove deprecated algorithms from SSH server configurations.
– Verify the identity of the server by checking its fingerprint against trusted records.
FAQs
Q1. What is the “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth), permission denied (publickey,gssapi-keyex,gssapi-with-mic)” error?
A1. This error indicates that the SSH client is attempting to authenticate using an SSH-RSA key, but the server has not configured SSH-RSA as an accepted key type. The server may require another key type for authentication.
Q2. What is a host key algorithm?
A2. A host key algorithm is a cryptographic algorithm used to generate a unique fingerprint for an SSH server. It ensures the authenticity and integrity of the server to establish secure SSH connections.
Q3. How can I edit the SSH config file on Windows?
A3. On Windows, open the SSH client’s configuration file using a text editor. The file is typically located at “C:\Users\[Username]\.ssh\config” or “C:\ProgramData\ssh\ssh_config”. Edit the necessary configurations, such as specifying the desired host key algorithm.
Q4. I received a “WARNING: remote host identification has changed” error. What does it mean?
A4. This warning indicates that the SSH client has encountered a different host key for a server than previously recorded. It could indicate a security issue, such as a possible man-in-the-middle attack. Exercise caution and verify the server’s identity before proceeding.
Q5. I am getting a “Permission denied, please try again” error. How can I resolve it?
A5. This error usually occurs when the SSH client fails to authenticate with the server using the provided credentials or key pair. Double-check the authentication credentials, ensure the correct key file is used, and verify that the key is authorized on the server.
Q6. Where can I find the sshd_config file?
A6. The sshd_config file is the SSH server’s configuration file. It is typically located in the “/etc/ssh/” directory on Linux-based systems or in the installation directory on Windows-based systems. Consult the SSH server documentation for the exact location.
Q7. What should I do if I receive the “No Matching Host Key Type Found” error?
A7. Refer to the troubleshooting steps mentioned in this article to resolve the error. Update your SSH client and server, check and configure matching host key types, and ensure compatibility between client and server configurations.
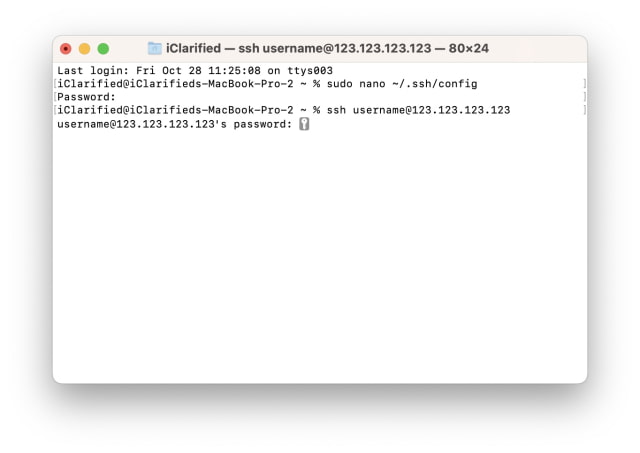
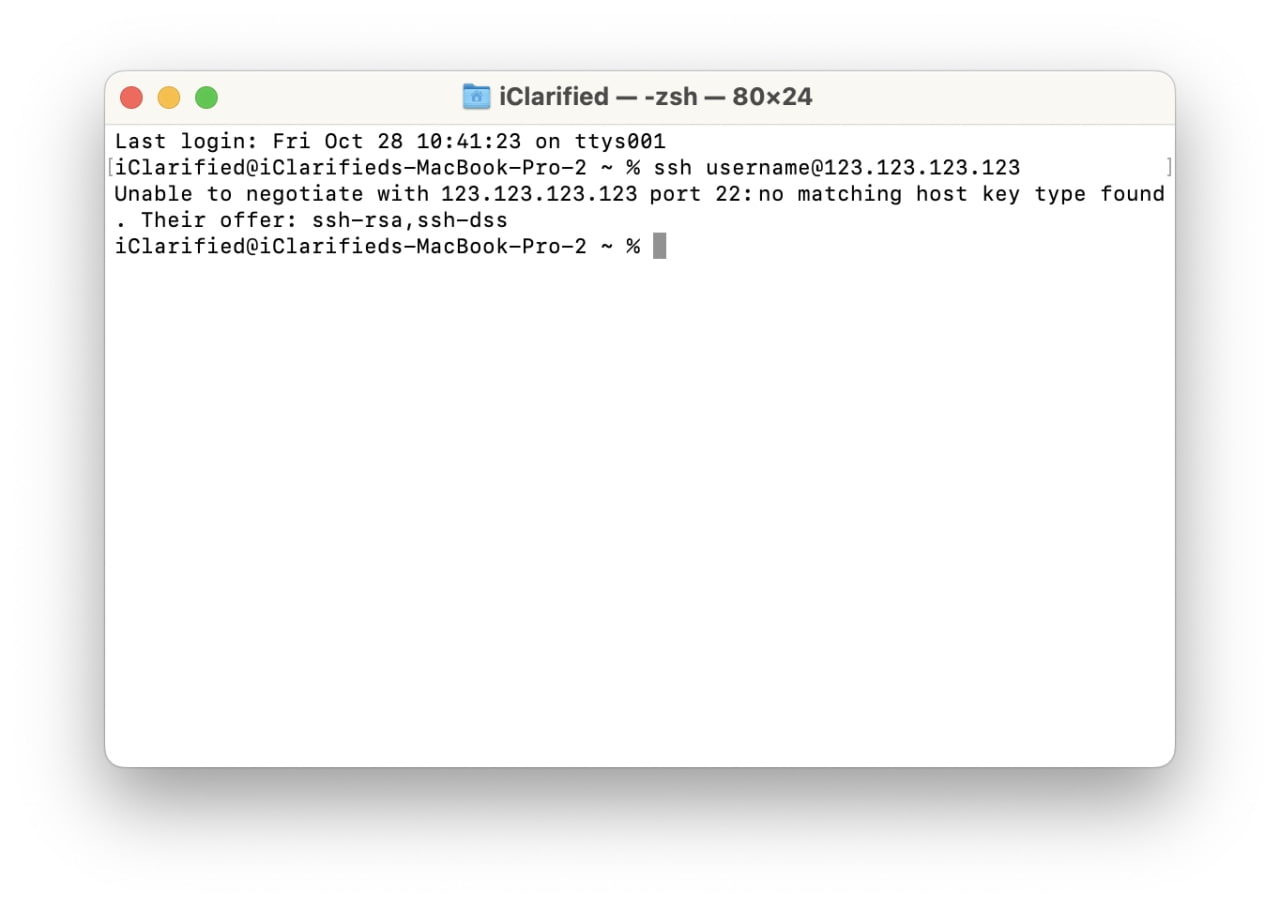
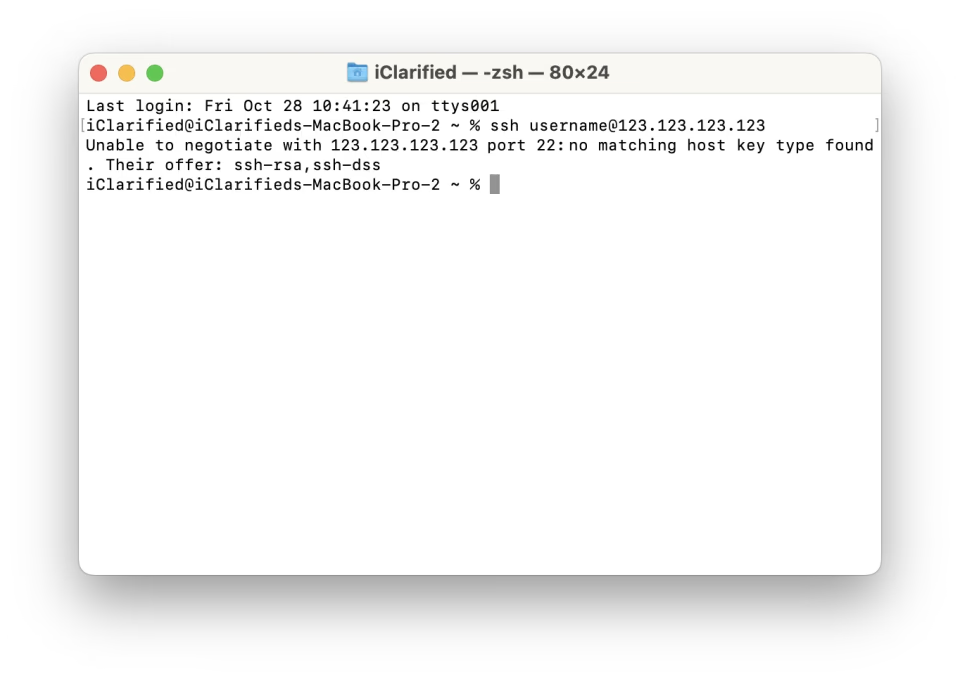
Unable To Negotiate With Ip Port 22: No Matching Host Key Type Found. Their Offer: Ssh-Rsa,Ssh-Dss
What Is Host Key Type Rsa?
In the world of computer security, cryptographic algorithms play a crucial role in safeguarding data and communication. One such algorithm, known as RSA, stands out prominently. RSA, which stands for Rivest-Shamir-Adleman, was invented by three mathematicians in 1977 and has since become one of the most widely used public-key encryption schemes.
Host key type RSA refers to the specific algorithm used to generate public and private key pairs for secure communication in the Secure Shell (SSH) protocol. SSH serves as a secure replacement for protocols like Telnet, Rlogin, and FTP, allowing users to securely access and manage remote servers and devices over an unsecured network.
When a client establishes a connection with an SSH server, host key type RSA is used to authenticate the server’s identity. The server generates a public and private key pair using the RSA algorithm. The public key is stored on the server and distributed to clients, while the private key remains securely stored on the server itself.
How does RSA encryption work?
RSA encryption relies on the mathematical properties of prime numbers and modular arithmetic. Here’s a simplified explanation of how RSA works:
1. Key Generation: The server generates a public key (e, n) and a private key (d, n).
– e is the public exponent, typically a small prime number like 65537.
– n is the product of two large prime numbers, p and q.
– d is the private exponent, and its value is determined using the Extended Euclidean Algorithm.
2. Encryption:
– A client, or sender, obtains the server’s public key (e, n) and encrypts the data using it.
– The client raises the plaintext message to the power of e and takes the remainder when divided by n.
– The resulting ciphertext is sent to the server.
3. Decryption:
– The server, possessing the private key (d, n), decrypts the received ciphertext.
– The server raises the ciphertext to the power of d and takes the remainder when divided by n.
– The original plaintext message is recovered.
4. Authentication:
– To verify the server’s authenticity, the client can use the public key provided by the server to encrypt a random challenge.
– The server, using its private key, decrypts the challenge and sends it back to the client.
– If the challenge matches, the client can trust the server’s identity.
Why is RSA encryption important in SSH?
SSH is designed to provide secure communication over untrusted networks, such as the internet. RSA encryption serves a vital role in ensuring the confidentiality, integrity, and authenticity of the data exchanged between the client and server.
Confidentiality: With RSA encryption, sensitive information sent over the SSH connection remains confidential. Even if intercepted, the encrypted data is practically impossible for attackers to decipher without the server’s private key.
Integrity: RSA ensures that the data transmitted between client and server remains intact. If any modification occurs during transmission, the decrypted data on the receiving end will differ from the original plaintext, indicating potential tampering.
Authentication: Host key type RSA is primarily used to verify the authenticity of the SSH server. By encrypting and decrypting a challenge using the public and private keys, respectively, the client can verify that the server is indeed who it claims to be. This prevents man-in-the-middle attacks where an attacker impersonates the server.
FAQs
1. What other host key types are available in SSH?
Apart from RSA, SSH supports various other host key types, such as DSA (Digital Signature Algorithm), ECDSA (Elliptic Curve Digital Signature Algorithm), and ED25519 (Edwards-curve Digital Signature Algorithm). Each has its own advantages and considerations, but RSA remains the most widely supported and preferred choice.
2. Is RSA encryption considered secure?
RSA encryption is considered secure when implemented with sufficiently large key sizes. The security of RSA relies on the difficulty of factoring large composite numbers into their prime factors. As computational power increases over time, larger key sizes are required to maintain security. Currently, a minimum of 2048-bit RSA keys is recommended for secure communication.
3. Can RSA encryption be used for data encryption in SSH?
While RSA encryption is used for key exchange, session establishment, and server authentication in SSH, it is not used directly for encrypting the data transmitted during the SSH session. Instead, a symmetric encryption algorithm, such as AES (Advanced Encryption Standard), is typically used for bulk data encryption within the established SSH session. This combines the efficiency and security of symmetric encryption with the secure key exchange provided by RSA.
In conclusion, host key type RSA is a crucial aspect of the SSH protocol, providing secure authentication and communication between clients and servers over untrusted networks. Through the use of public and private key pairs, RSA encryption ensures confidentiality, integrity, and authenticity, making it a vital tool in protecting sensitive information for countless users around the world.
What Is Dss In Ssh?
Differential Synchronization System (DSS) in Secure Shell (SSH) is a network protocol used for securely accessing remote systems and transferring data. SSH is widely popular among system administrators and software developers due to its encryption and authentication capabilities. One of the key components of SSH is the use of cryptographic algorithms, including the DSS algorithm, which provides secure communication over insecure networks.
DSS, which stands for Digital Signature Algorithm, is a widely-used asymmetric encryption algorithm. It is based on the mathematically complex problem of integer factorization and provides a high level of security. The DSS algorithm is used in SSH for key exchange and authentication purposes, ensuring that both the client and the server are who they claim to be and preventing unauthorized access.
How does DSS work in SSH?
DSS in SSH primarily operates through the generation and verification of digital signatures. These signatures are used to verify the authenticity and integrity of data sent between the client and the server during the SSH connection. Let’s take a closer look at how DSS works within the SSH protocol:
1. Key Generation: The client and the server each generate their own DSS key pairs, consisting of a private key and a public key. The private key remains securely stored on the respective device, while the public key can be freely shared.
2. Key Exchange: During the SSH handshake, the client and the server exchange their public keys. This step ensures that each party has access to the other’s public key, enabling them to authenticate each other later on.
3. Signature Verification: Once the keys have been exchanged, DSS is used to verify the authenticity of data transferred between the client and the server. When the client sends data to the server, it attaches a digital signature to the data using its private key. The server then uses the client’s public key to verify the signature and ensure its authenticity, thus verifying the client’s identity.
4. Authentication: Similarly, when the server sends data back to the client, it attaches a digital signature using its private key. The client verifies the signature using the server’s public key to authenticate the server’s identity. This authentication process ensures that the communication is secure and that there is no tampering or impersonation.
Frequently Asked Questions (FAQs):
Q1. Why is SSH important for secure remote access?
A1. SSH provides secure encrypted communication between the client and the server, making it essential for remote access to sensitive systems and data. It prevents eavesdropping, data tampering, and unauthorized access.
Q2. How does DSS compare to other encryption algorithms used in SSH?
A2. DSS is one of several encryption algorithms used in SSH, alongside RSA and Elliptic Curve Cryptography (ECC). Each algorithm has its own strengths and weaknesses, but DSS remains a popular choice due to its security and efficiency.
Q3. Can DSS be used for encrypting data in addition to authentication?
A3. No, DSS is primarily used for authentication and digital signature generation. To encrypt the actual data transferred over the SSH connection, symmetric encryption algorithms like AES or 3DES are used.
Q4. Are there any vulnerabilities or weaknesses in using DSS in SSH?
A4. While DSS is generally considered secure, there have been concerns raised about the key sizes used in DSS, particularly ones with a length less than 2048 bits. It is recommended to use longer key sizes to enhance security.
Q5. Can DSS be used in other applications beyond SSH?
A5. Yes, DSS is a widely-used cryptographic algorithm and can be implemented in various applications requiring digital signature generation and authentication, including secure email and code signing.
In conclusion, DSS in SSH plays a vital role in ensuring secure communication and authentication between clients and servers. Through the generation and verification of digital signatures, DSS provides a robust layer of protection against unauthorized access and data tampering. By understanding how DSS operates within the SSH protocol, users can make informed decisions when it comes to securing their remote systems and data.
Keywords searched by users: no matching host key type found. their offer ssh-rsa ssh-dss Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth), permission denied (publickey,gssapi-keyex,gssapi-with-mic)., What is host key algorithm, SSH config file Windows, WARNING: remote host identification has changed, Ssh Permission denied, please try again, Sshd_config, File ssh
Categories: Top 30 No Matching Host Key Type Found. Their Offer Ssh-Rsa Ssh-Dss
See more here: nhanvietluanvan.com
Userauth_Pubkey: Key Type Ssh-Rsa Not In Pubkeyacceptedalgorithms (Preauth)
When it comes to securely accessing remote systems, SSH (Secure Shell) is widely used by system administrators, software developers, and many other professionals. SSH allows users to connect to remote machines over a secure network and perform various tasks, such as remote file transfers, executing commands, and tunneling other protocols.
However, there are instances when SSH connections can encounter issues, and one common error message that users may come across is “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth).” This error can be puzzling for those who are not familiar with the inner workings of SSH and its cryptographic algorithms. In this article, we will dive into the details of this error, explore its causes, and provide solutions to resolve it.
Understanding SSH Public Key Authentication
SSH offers multiple authentication methods, including password-based authentication and public key-based authentication. Public key authentication relies on cryptographic key pairs, consisting of a public key and a private key. The public key is placed on the remote system, while the private key remains on the user’s local machine.
When a user attempts to establish an SSH connection, their client presents their public key to the remote server. The server then checks if the presented public key matches any of the authorized keys stored in its configuration. If a match is found, the user is granted access based on the corresponding private key.
The error message “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth)” indicates that the public key algorithm used by the client is not allowed by the server. The SSH protocol supports multiple public key algorithms, such as RSA, DSA, and ECDSA. The specific algorithm that the server accepts is controlled by the “PubkeyAcceptedAlgorithms” directive in the server’s SSH configuration.
Causes of the Error
1. Outdated Client or Server: One possible reason for encountering this error is that either the client or server software is using outdated versions that do not support the algorithm. To resolve this, ensure that both the client and server components are updated to the latest available versions.
2. Unsupported Algorithm: SSH protocol versions before SSH-2.0 used RSA as the default public key algorithm. However, modern SSH implementations often have “PubkeyAcceptedAlgorithms” configured to prioritize more secure algorithms, such as ECDSA or Ed25519. If the client’s public key is of the RSA type, it may not be accepted by the server if RSA is not included in the allowed algorithms list.
3. Misconfigured Server: The server’s SSH configuration file may have invalid settings or be missing the necessary algorithms in the “PubkeyAcceptedAlgorithms” directive. Double-check the server’s configuration and ensure that it includes the desired public key algorithms.
Resolving the Error
1. Upgrade SSH Components: Ensure that both the client and server SSH components are updated to the latest version. This step is crucial as older software versions may not support the required algorithms.
2. Check Server Configuration: Examine the server’s SSH configuration file, typically located in “/etc/ssh/sshd_config” or a similar location, and look for the “PubkeyAcceptedAlgorithms” directive. Verify that the algorithm corresponding to the key type (e.g., “ssh-rsa” for an RSA key) is listed there. If it is missing or commented out, remove the comment or add the algorithm to the list.
3. Generate a New Key Pair: If the server does not support the client’s key type, one solution is to generate a new key pair on the client side using a supported algorithm (e.g., ECDSA or Ed25519). Then, add the new public key to the server’s authorized keys. This can be done by appending the new public key to the “~/.ssh/authorized_keys” file on the server.
FAQs
Q1. Can I force the server to accept a specific key type?
A1. Yes, you can modify the server’s SSH configuration to include your desired key type in the “PubkeyAcceptedAlgorithms” directive. However, it is recommended to use more secure algorithms like ECDSA or Ed25519.
Q2. What is the most secure public key algorithm for SSH?
A2. While RSA has historically been widely used, newer algorithms like ECDSA and Ed25519 are considered more secure. They offer better performance and stronger security properties compared to RSA.
Q3. I’ve updated the server configuration, but the error persists. What should I do?
A3. After changing the server’s SSH configuration, make sure to restart the SSH service for the changes to take effect. On most systems, you can use the command “sudo systemctl restart ssh” or the equivalent for your distribution.
Q4. Are there any security risks associated with the “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms” error?
A4. This error primarily indicates a configuration issue rather than a security risk. The error typically prevents users from using a specific key type for authentication, but it does not expose vulnerabilities or compromise the SSH connection itself.
In conclusion, the error “Userauth_pubkey: key type ssh-rsa not in PubkeyAcceptedAlgorithms (preauth)” occurs when the SSH server does not accept a specific public key algorithm. By upgrading SSH components, checking and adjusting server configuration, and generating new key pairs when necessary, users can resolve this error and continue securely accessing remote systems via SSH.
Permission Denied (Publickey,Gssapi-Keyex,Gssapi-With-Mic).
In the world of computer security and authentication, the error message “Permission denied (publickey,gssapi-keyex,gssapi-with-mic)” is one that can be rather frustrating for users and system administrators alike. This article aims to provide a comprehensive understanding of this error message, its causes, and possible solutions.
Understanding the Error Message
The error message “Permission denied (publickey,gssapi-keyex,gssapi-with-mic)” indicates that the user attempting to log in to a remote system has been denied access. It typically occurs when using SSH (Secure Shell) to connect to a server or when attempting to execute a command remotely.
The error message itself is comprised of three parts: “publickey,” “gssapi-keyex,” and “gssapi-with-mic.” Each of these represents a different method of authentication that has been attempted but failed to grant access.
1. Publickey: This authentication method uses a pair of cryptographic keys, a public key and a private key. The public key is stored on the remote server and the private key is kept securely by the user. When attempting to log in, the user’s private key is used to prove their identity. If the private key does not match any of the server’s stored public keys, the “Permission denied” error is returned.
2. GSSAPI-keyex: GSSAPI (Generic Security Services Application Programming Interface) is a framework that provides security services for applications. GSSAPI-keyex is a specific method within GSSAPI that involves key exchange. If the GSSAPI-keyex authentication fails, the error message is returned.
3. GSSAPI-with-mic: Similar to GSSAPI-keyex, GSSAPI-with-mic is another method within the GSSAPI framework that involves message integrity checks. If this method fails during the authentication process, the error message is again returned.
Common Causes of the Error
Several factors can contribute to the occurrence of this error message:
1. Incorrect or missing SSH keys: If the user’s private key does not match any of the authenticating server’s public keys, the access will be denied. Double-checking that the correct SSH keys are in use is essential.
2. Misconfigured server settings: The server may have certain SSH configuration settings misconfigured or disabled, which prevents the successful authentication. Checking the server-side configuration files, such as “/etc/ssh/sshd_config,” is important.
3. Network connectivity issues: Problems with network connectivity, such as firewall rules or routing issues, can also lead to the “Permission denied” error. Ensuring that the necessary ports for SSH communication are open and properly configured can help resolve this issue.
Solutions and Troubleshooting Steps
When faced with the “Permission denied (publickey,gssapi-keyex,gssapi-with-mic)” error message, there are several steps you can take to identify and resolve the underlying problem:
1. Verify SSH keys: Ensure that the correct SSH keys are being used for authentication. Verify that the public key associated with your private key is present on the remote server and that it matches your private key.
2. Check SSH configuration settings: Review the server-side SSH configuration file (“/etc/ssh/sshd_config”) and ensure that the required authentication methods (publickey, gssapi-keyex, gssapi-with-mic) are enabled.
3. Verify user permissions: Ensure that the user attempting to log in has the necessary permissions on the remote system. Check the remote server’s user settings and ensure the user is permitted to access the system via SSH.
4. Check network connectivity: Verify that there are no network connectivity issues preventing the SSH connection. Ensure that the necessary ports (typically port 22 for SSH) are open and properly forwarded if connecting through a firewall.
FAQs (Frequently Asked Questions)
Q1. Why am I receiving a “Permission denied (publickey,gssapi-keyex,gssapi-with-mic)” error message?
A1. This error occurs when the SSH authentication process fails due to various reasons, such as incorrect SSH keys, misconfigured SSH server settings, or network connectivity issues.
Q2. How can I fix this error?
A2. To resolve this error, ensure that you are using the correct SSH keys, double-check the SSH server’s configuration settings, verify user permissions, and also check for any network connectivity issues.
Q3. Can I use a different authentication method?
A3. Yes, apart from the methods mentioned in the error message, other authentication methods like password-based authentication can be used. However, it is recommended to use publickey authentication for stronger security.
Q4. What should I do if I have forgotten or lost my SSH private key?
A4. If you have lost your SSH private key, you may need to generate a new key pair and update the remote server’s authorized keys accordingly. Make sure to securely store the new private key to avoid unauthorized access.
Q5. Are there any additional security measures I can take?
A5. Yes, you can enhance security by further hardening the SSH server configuration, such as using key-based authentication only, disallowing root login, implementing two-factor authentication, and regularly updating the SSH server software to patch any security vulnerabilities.
In conclusion, the “Permission denied (publickey,gssapi-keyex,gssapi-with-mic)” error message can be an obstacle while trying to access remote systems via SSH. By understanding the causes and following the troubleshooting steps outlined above, users can work towards resolving the issue and achieving a successful SSH connection.
Images related to the topic no matching host key type found. their offer ssh-rsa ssh-dss

Found 21 images related to no matching host key type found. their offer ssh-rsa ssh-dss theme









![SOLUCIÓN] Port 22: no matching host key type found. Their offer: ssh-dss ✓ - YouTube Solución] Port 22: No Matching Host Key Type Found. Their Offer: Ssh-Dss ✓ - Youtube](https://i.ytimg.com/vi/ncCuk3Dm2pA/mqdefault.jpg)








![Linux|Unix] ssh 접속시 no matching key 해결 방법 Linux|Unix] Ssh 접속시 No Matching Key 해결 방법](https://img1.daumcdn.net/thumb/C176x176/?fname=https://t1.daumcdn.net/cfile/tistory/999EA63359A41D8E11)






Article link: no matching host key type found. their offer ssh-rsa ssh-dss.
Learn more about the topic no matching host key type found. their offer ssh-rsa ssh-dss.
- no matching host key type found. Their offer: ssh-dss
- Unable to negotiate with XX.XXX.XX.XX: no matching host key …
- I get the error “no matching host key type found. Their offer
- How to Fix ‘No Matching Host Key Type Found’ on Mac
- [SOLVED] no matching host key type found. Their offer: ssh …
- SSH No Matching Host Key Type Found – Server Fault
- Unable to negotiate with
port 22: no matching … - What is an SSH Host Key & How are They Configured?
- When used with SSH keys, why are the DSA keys referred to as DSS …
- Generating and using SSH keys for remote host authentication
- Host Key – Glossary | CSRC – NIST Computer Security Resource Center
- Fix for ssh authentication failure “no matching host key type …
- SSH host key verification: a few useful tips – End Point Dev
- Cisco IOS – ‘No matching host key type found’ During SSH
See more: https://nhanvietluanvan.com/luat-hoc/