Service Principal Vs Managed Identity
In Microsoft Azure, there are several mechanisms available for managing and securing access to resources, including service principals and managed identities. These two concepts play a crucial role in authenticating and authorizing applications and services to access Azure resources. In this article, we will explore the differences between service principals and managed identities, their benefits and limitations, and how to choose between them.
What is a Service Principal?
A service principal is an identity that represents an application, service, or automated tool and allows it to access Azure resources. It acts as a service account, providing an authentication mechanism for applications to interact with Azure resources. A service principal consists of a unique identifier (application ID or client ID) and a secret or certificate (client secret or key). These credentials are typically used to authenticate the application or service programmatically.
What is a Managed Identity?
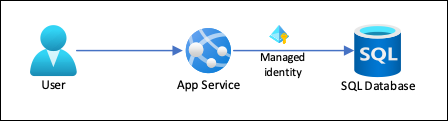
Managed identities, on the other hand, are built-in Azure Active Directory identities that are automatically managed by Azure. They eliminate the need for developers to manage credentials and offer a more secure way to authenticate resources. Managed identities function similarly to service principals but without the need to create and manage the credentials manually. When a managed identity is enabled for a resource such as a virtual machine, Azure assigns the identity and handles the credentials automatically.
Authentication and Authorization with Service Principals
Service principals use Azure Active Directory (AD) for authentication and authorization. The authentication process involves obtaining an access token from Azure AD using the client ID and client secret or certificate. This token is then used for subsequent requests to Azure resources. Service principals can be assigned roles and permissions, allowing fine-grained control over resource access. This level of control is necessary when applications or services require specific access rights to Azure resources.
Authentication and Authorization with Managed Identities
Managed identities leverage Azure AD for authentication and authorization as well. However, the authentication process is simplified with managed identities, as Azure automatically handles the token acquisition and management. When a resource with a managed identity makes a request to Azure resources, Azure AD verifies the identity and grants the appropriate permissions based on the assigned roles. This simplification eliminates the need for managing credentials and reduces the attack surface by removing secrets from the application code or configuration.
Benefits and Limitations of Service Principals
Service principals offer more flexibility and control compared to managed identities. They can be used outside Azure (e.g., in hybrid scenarios), and their credentials can be rotated manually. Service principals also support client credentials and certificate-based authentication, allowing for more diverse authentication scenarios. However, service principals require manual management of credentials, including generating and securely storing secrets or certificates. They also introduce a potential security risk if credentials are compromised.
Benefits and Limitations of Managed Identities
Managed identities provide a simplified authentication and authorization experience. They remove the need for managing credentials, eliminating the risk of secrets or certificates being exposed or mishandled. Managed identities are easily enabled for Azure resources through portal, CLI, or templates. They also support role-based access control (RBAC) for fine-grained authorization. However, managed identities are limited to Azure resources and cannot be used for non-Azure scenarios or services that do not support managed identities.
Choosing between Service Principals and Managed Identities
When deciding between service principals and managed identities, several factors should be considered. If the application or service is solely running within Azure and doesn’t require authentication for non-Azure resources, managed identities offer a simpler and more secure option. Managed identities are recommended for most scenarios, as they reduce the management overhead and improve security. However, if the application needs to access non-Azure resources or requires custom authentication mechanisms, service principals may be a better choice.
In conclusion, both service principals and managed identities play a critical role in authenticating and authorizing access to Azure resources. Service principals offer more flexibility and control but require manual management of credentials. Managed identities provide a simpler and more secure way to authenticate Azure resources, eliminating the need for managing credentials. Carefully consider your requirements and the scope of your application or service to make an informed decision between service principals and managed identities.
FAQs:
Q1: What is an Azure service principal?
A1: An Azure service principal is an identity that represents an application, service, or automated tool and allows it to access Azure resources. It provides an authentication mechanism for applications to interact with Azure resources programmatically.
Q2: What is the difference between managed identity and service principal?
A2: A managed identity is an Azure Active Directory identity that is automatically managed by Azure. It simplifies authentication by handling token acquisition and management. Service principals, on the other hand, provide more flexibility and control but require manual management of credentials.
Q3: What is an Azure service principal ID?
A3: An Azure service principal ID is a unique identifier assigned to a service principal. It is used to authenticate the application or service when interacting with Azure resources.
Q4: What does “Azure service principal là gì” mean?
A4: “Azure service principal là gì” translates to “What is an Azure service principal?” in English. It is a common question in Vietnamese seeking information about service principals in Azure.
Q5: What is AKS managed identity?
A5: AKS managed identity refers to the managed identity feature available in Azure Kubernetes Service (AKS). It allows pods running within AKS clusters to authenticate with Azure resources using managed identities.
Q6: How to create a managed identity in Azure?
A6: Managed identities can be created in Azure through various methods, including the Azure portal, Azure CLI, and Azure Resource Manager templates. The exact steps may vary depending on the chosen method and the specific resource requiring the managed identity.
Q7: What is Az service principal?
A7: “Az service principal” refers to the Azure service principal module in Azure PowerShell. It provides cmdlets for managing service principals and their associated credentials.
Q8: What is the difference between managed identity and service principal in Azure?
A8: The main difference between managed identities and service principals in Azure is the level of automation and management. Managed identities are built-in identities that simplify authentication by handling token acquisition and management automatically. Service principals offer more flexibility and control but require manual management of credentials and tokens.
Keywords: Azure service principal, Managed identity vs service principal, Azure service principal ID, Azure service principal là gì, AKS managed identity, Create managed identity azure, Az service principal, Managed identity Azure, Service principal vs managed identity.
Choosing Right Identity For Azure Services | Managed Identity Vs Service Principal
What Is The Difference Between Service Principal And Managed Identities In Azure?
In the world of cloud computing, Azure has emerged as one of the leading platforms, providing a wide range of services and functionalities to users. Azure offers various identity management options, including service principals and managed identities. Both play a crucial role in securing access to Azure resources, but they have distinct features and use cases. In this article, we will explore the differences between service principal and managed identities in Azure, helping you understand when and why to use each one.
Service Principal:
A service principal is an identity created for a specific application or service in Azure Active Directory (AAD). It is essentially an authentication object that allows the application to authenticate and access Azure resources. Service principals are commonly used in scenarios where you want to grant access to an application rather than an individual user. They are commonly used in service-to-service authentication, connection to Azure DevOps, or when setting up Azure automation tasks.
When creating a service principal, you need to specify a display name, application ID, password or certificate, and the role assignments it will have within Azure resources. The display name is a friendly name that helps identify the service principal, while the application ID is a unique identifier assigned by Azure AD. The password or a certificate is used for authenticating the service principal.
One key advantage of using service principals is that they grant fine-grained access control. You can assign specific roles or permissions to the service principal, ensuring that it only has access to the necessary resources. This helps strengthen the security posture of your Azure infrastructure.
Managed Identity:
Managed identities, on the other hand, provide a simplified way to authenticate and authorize access to Azure resources. They are automatically created within Azure AD and can be associated with Azure resources such as virtual machines, Azure Functions, or App Services. Unlike service principals, managed identities are not user-specific or application-specific. They are tied to the resource instead, simplifying the management process.
To create a managed identity, you need to enable it on the Azure resource. Once enabled, Azure automatically provisions a unique identity for that specific resource. This identity is then used to authenticate and authorize the resource when performing actions against Azure resources.
The primary advantage of using managed identities is that they alleviate the need for developers to handle credentials explicitly. This eliminates the risk of exposing sensitive credentials and simplifies the management process. Furthermore, managed identities can be easily used with Azure resources, as Azure handles most of the authentication process behind the scenes.
FAQs:
Q: When should I use a service principal?
A: Service principals are commonly used in scenarios where you need to authenticate and grant access to an application or service rather than an individual user. They are often used for service-to-service authentication, connecting to Azure DevOps, or when setting up Azure automation tasks.
Q: When should I use a managed identity?
A: Managed identities should be used when authenticating and authorizing Azure resources such as virtual machines, Azure Functions, or App Services. They provide a simplified way to manage identity and access for Azure resources, eliminating the need for developers to explicitly handle credentials.
Q: Can a service principal be used with Azure resources?
A: Yes, service principals can be used with Azure resources. They can be granted access to Azure resources by assigning specific roles or permissions to them. However, managing service principals requires more configuration and administrative effort compared to managed identities.
Q: Can a managed identity be used in service-to-service authentication?
A: Yes, managed identities can be used for service-to-service authentication. When enabled on a resource, the managed identity can authenticate and authorize itself to access other Azure resources without requiring explicit credential handling.
Q: Can a service principal be associated with multiple applications?
A: No, a service principal is specific to a single application or service. If you need to grant access to multiple applications, you will need to create separate service principals for each application.
In conclusion, service principals and managed identities are both important elements of Azure’s identity management framework. Service principals are commonly used for authenticating applications or services, while managed identities provide a simplified way to authenticate and authorize Azure resources. Understanding the differences between the two and their use cases will enable you to make informed decisions when securing your Azure infrastructure.
What Is A Service Principal?
In the realm of identity and access management (IAM), a service principal is an identity used by applications, services, and tools to authenticate and access resources within a system. It is a security principal that represents the application itself rather than an individual user. Service principals are commonly used in cloud computing scenarios and play a vital role in enabling secure communication between services, automating tasks, and managing access to resources.
Service principals are typically created within an Identity Provider (IDP) or Directory Service, such as Azure Active Directory (AAD) in the case of Microsoft Azure, to authenticate and authorize applications to interact with various resources and services. They possess their own set of credentials, often in the form of a client ID and secret or a certificate, which can be used to prove their identity and gain access to protected resources.
The primary purpose of a service principal is to grant permissions and manage access to resources on behalf of the application it represents. By utilizing a service principal, it becomes possible to assign specific roles, such as read/write access, to the application while ensuring that individual users do not have unnecessary access or elevated privileges. This segregation of duties enhances security and helps maintain compliance by following the principle of least privilege.
Service principals are established as first-class entities within an identity system, which means they can be individually managed, assigned roles, and have their credentials rotated as necessary. This makes them ideal for delegation and automation scenarios, as service principals can perform tasks and access resources autonomously without requiring constant human intervention or sharing personal credentials.
Additionally, service principals often integrate seamlessly with other security features and communication protocols, such as OAuth2 and OpenID Connect, to secure the exchange of information between services. They enable applications to acquire access tokens that can be used to authenticate against protected APIs, ensuring secure and authorized interactions.
FAQs:
Q: How is a service principal different from a user account?
A: While a user account represents an individual user and is associated with personal credentials, a service principal represents the application itself. Service principals have their own set of credentials, distinct from any user accounts, ensuring separation of duties and enhancing security.
Q: What are the benefits of using service principals?
A: Service principals offer various benefits, including improved security by following the principle of least privilege, easy management and control of access permissions for applications, automation and delegation capabilities, and seamless integration with other security features and protocols.
Q: How are service principals created?
A: Service principals are typically created within an Identity Provider or Directory Service, such as Azure Active Directory, through administrative interfaces, command-line tools, or APIs provided by the platform. The creation process involves setting up credentials, establishing role assignments, and configuring access permissions.
Q: How are service principals used in cloud computing?
A: In cloud computing, service principals play a crucial role in enabling secure communication between services, automating tasks, and managing access to resources. They allow applications running in the cloud to authenticate and access various resources while maintaining security and compliance.
Q: Can a service principal perform actions on behalf of a user?
A: Yes, service principals can perform actions on behalf of a user, but only if the user has given consent or there is an appropriate role assignment in place. This enables applications to act on user’s behalf to access resources or perform tasks without sharing personal credentials.
Q: Are service principals limited to a specific cloud platform?
A: No, the concept of service principals is not limited to any specific cloud platform. While examples mentioned here predominantly refer to Azure Active Directory, other cloud platforms, such as AWS Identity and Access Management (IAM) or Google Cloud IAM, offer similar functionalities with their own terminology.
In conclusion, service principals are integral to modern identity and access management practices, particularly in cloud computing environments. As dedicated identities for applications and services, they enable secure, permission-based access to resources while allowing for automation, delegation, and easy management. Service principals contribute to the overall security posture of an organization by enforcing the principle of least privilege and providing a controlled means of interaction between applications and resources.
Keywords searched by users: service principal vs managed identity Azure service principal, Managed identity vs service principal, Azure service principal ID, Azure service principal là gì, AKS managed identity, Create managed identity azure, Az service principal, Managed identity Azure
Categories: Top 26 Service Principal Vs Managed Identity
See more here: nhanvietluanvan.com
Azure Service Principal
Introduction to Azure Service Principal
Azure Service Principal is an identity used by applications, services, and automation tools to authenticate and access Azure resources securely. It eliminates the need for using user credentials while granting fine-grained access control to specific resources within an Azure subscription. Service Principal authentication offers a more secure and manageable way of accessing Azure resources compared to using a shared account or individual user credentials.
In this article, we will delve into the concept of Azure Service Principal, its benefits, and how to create and manage it effectively. We will also address frequently asked questions to provide a holistic understanding of this important aspect of Azure.
Benefits of Azure Service Principal
1. Security: Service Principals are distinct, unique identities that can be assigned granular permissions, reducing the attack surface and the risk of unauthorized access. By creating specific identities for each application, organizations can enforce the principle of least privilege more effectively.
2. Automation: Service Principals enable secure automation of various Azure operations by providing non-user-specific credentials. They are commonly used by CI/CD pipelines, deployment scripts, and other automated workflows.
3. No Dependency on User Credentials: By eliminating the dependency on user credentials, Service Principals enhance security and reduce the risk associated with managing shared accounts. Users’ credentials can be rotated independently, ensuring better security posture.
Creating Azure Service Principal
There are different ways to create an Azure Service Principal. The following are two common methods:
1. Azure Portal:
– Sign in to the Azure portal (https://portal.azure.com).
– Navigate to the Azure Active Directory (AD) section.
– Create a new application registration and provide necessary details like name, URL, and other metadata.
– After the application is created, navigate to the “Certificates & Secrets” section to generate a client secret or certificate for authentication purposes.
– Finally, assign appropriate permissions to the Service Principal within Azure resources.
2. Azure CLI:
– Install and configure the Azure CLI on your machine.
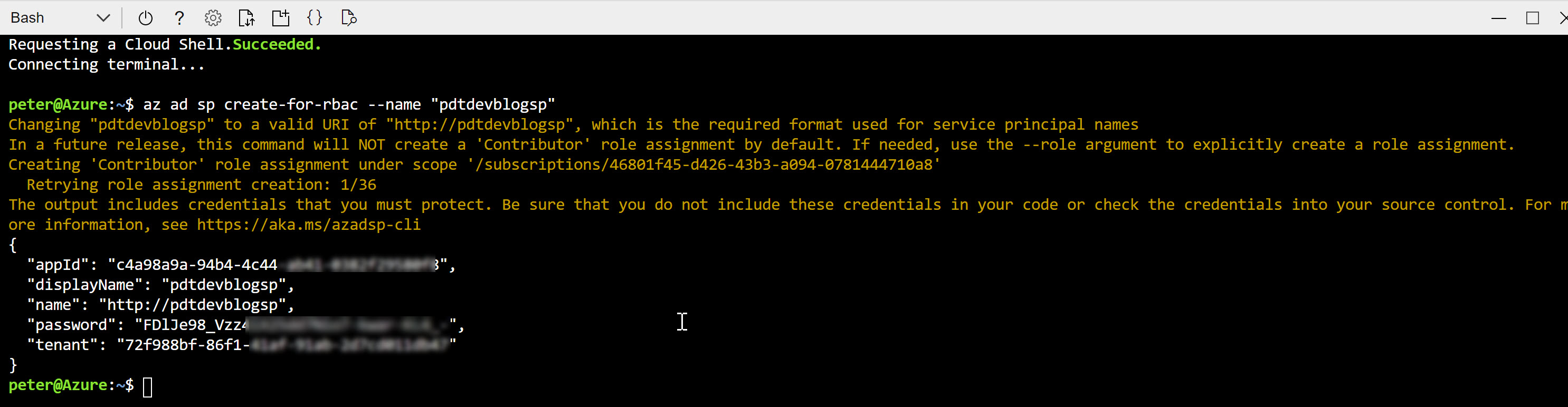
– Use the “az ad sp create-for-rbac” command to create the Service Principal with appropriate default values.
– Customize the Service Principal’s role assignments using the “az role assignment” command, granting specific permissions to your resources.
Managing Azure Service Principal
Once you have created a Service Principal, it becomes essential to manage it effectively. Some key management aspects include:
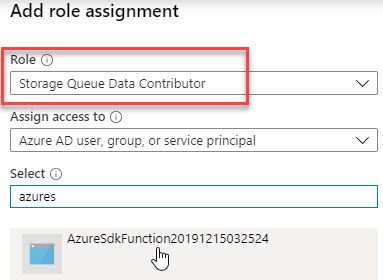
1. Role Assignments: Assigning appropriate roles to the Service Principal ensures that it has the necessary permissions to access required Azure resources. Roles can be assigned at the subscription, resource group, or individual resource level.
2. Secret Rotation: Regularly rotate the client secrets or certificates associated with the Service Principal to maintain a robust security posture. Azure Key Vault can be leveraged to securely store secrets and automate rotation processes.
3. Expiry and Revocation: Review the expiration date of the Service Principal and take necessary actions to ensure uninterrupted access. If the Service Principal is no longer required, revoke it to minimize potential security risks.
Frequently Asked Questions (FAQs):
Q1: What is the difference between a Service Principal and a Microsoft Account?
A: A Service Principal is an identity specific to an application or automation tool, while a Microsoft Account is a user-specific identity used for personal access to Microsoft services. Service Principals offer more control and security when accessing Azure resources programmatically.
Q2: Is it possible to assign roles directly to a Service Principal?
A: Yes, roles can be directly assigned to a Service Principal. By assigning roles at various levels, administrators can control the scope and extent of resource access.
Q3: How can I use a Service Principal in a CI/CD pipeline?
A: Service Principals can be used to authenticate CI/CD pipelines, allowing automated deployments to Azure resources. The pipelines can leverage the Service Principal’s credentials to access the resources securely.
Q4: What are the best practices for managing Service Principals?
A: Some best practices include:
– Regularly review and update permissions assigned to Service Principals.
– Use separate Service Principals for different applications or automation tools.
– Monitor and log activities performed by Service Principals for audit purposes.
– Regularly rotate secrets associated with Service Principals.
Conclusion
Azure Service Principal provides secure and manageable access control to Azure resources by eliminating dependencies on user credentials. Its benefits include enhanced security through fine-grained access control, automation possibilities, and reduced reliance on user accounts. By following best practices and effectively managing Service Principals, organizations can leverage their full potential while maintaining a robust security posture.
Remember, Service Principals are not a replacement for user-based access controls but rather a complementary mechanism for secure, automated, and delegated access to Azure resources.
Managed Identity Vs Service Principal
In the realm of cloud computing, ensuring secure access to various resources and services is of utmost importance. Azure, Microsoft’s cloud platform, provides two main options for managing access to resources – Managed Identity and Service Principal. Understanding the difference between these two concepts is crucial for effectively managing access and maintaining a secure environment. In this article, we will explore Managed Identity and Service Principal, their differences, use cases, and address some frequently asked questions (FAQs) regarding these concepts.
Managed Identity:
Managed Identity is a feature of Azure Active Directory (AD) that simplifies the authentication process for Azure resources. It provides an identity for applications or services running on Azure, eliminating the need to manage credentials manually. Under the hood, Managed Identity leverages Azure AD to obtain tokens that can be used to access Azure resources.
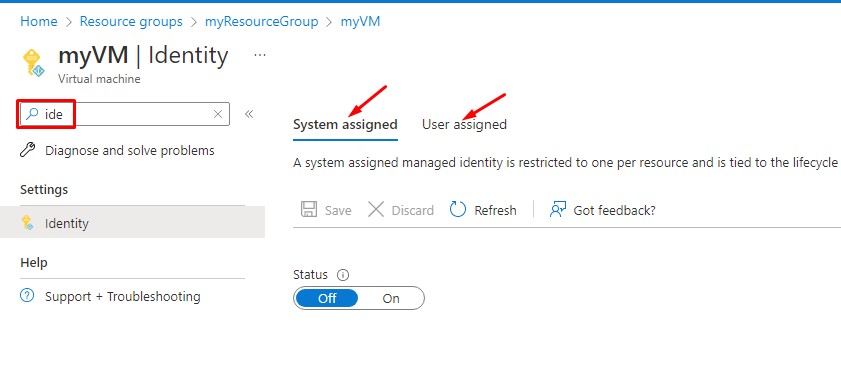
There are two types of Managed Identity in Azure:
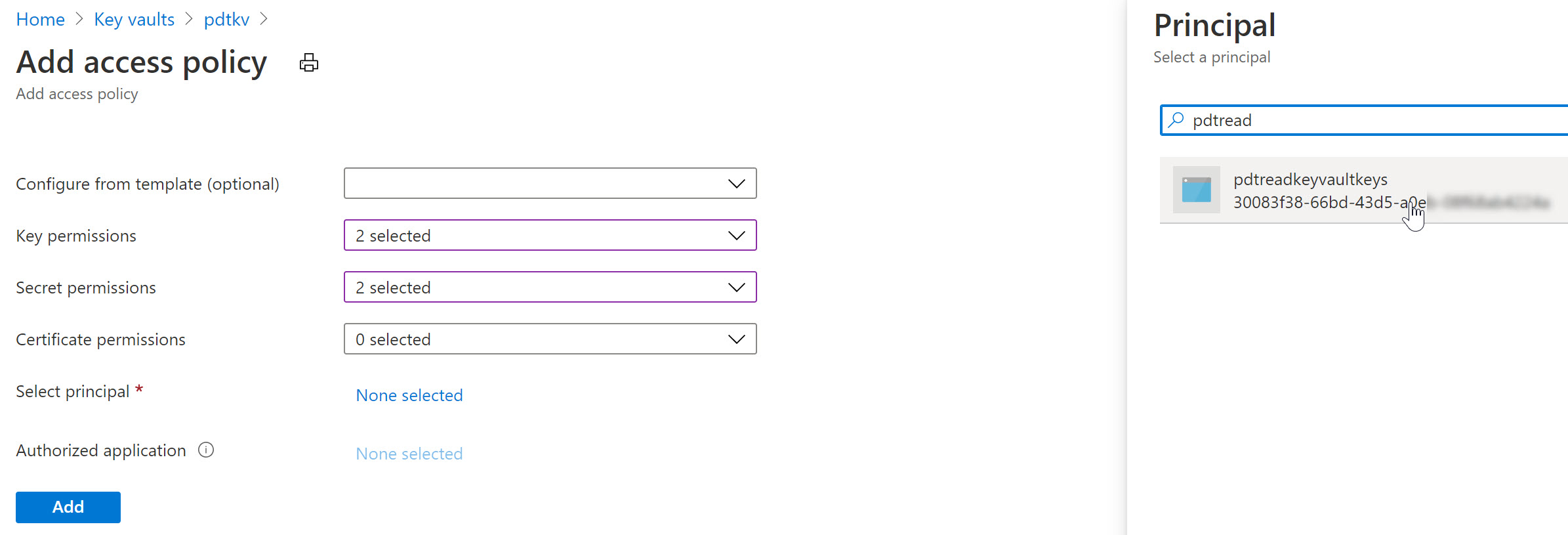
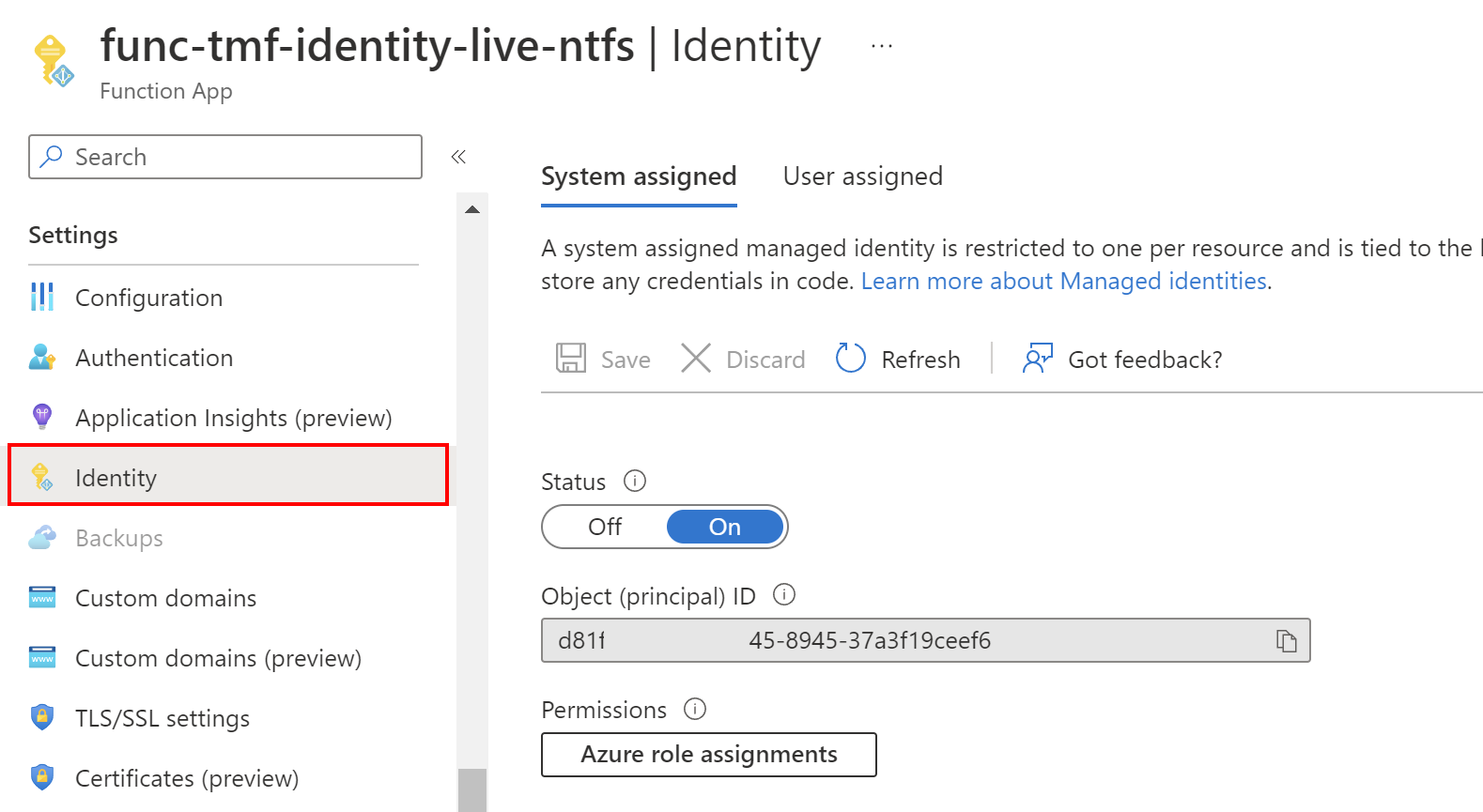
1. System-assigned Managed Identity: This type of Managed Identity is tied to an Azure resource, such as a virtual machine (VM) or an App Service. Once enabled, Azure automatically provisions an identity for that resource, which can then be used to access other Azure resources such as Azure Key Vault or Azure Storage. This eliminates the need for developers to manage credentials and helps ensure better security and governance.
2. User-assigned Managed Identity: Unlike a system-assigned Managed Identity, a user-assigned Managed Identity is created as a standalone Azure resource. It can be assigned to one or more Azure resources, granting them the identity and access management capabilities. This allows for better separation of concerns and more flexibility, as the same identity can be used across multiple resources.
Service Principal:
A Service Principal is also an identity within Azure AD, but it represents an application or a service rather than a resource. It acts as a service account that can authenticate and authorize itself when interacting with various Azure resources.
Service Principals are created explicitly, and they typically represent third-party applications, scripts, and other backend services. They can be assigned specific roles and permissions, allowing them to access and interact with Azure resources such as virtual machines, storage accounts, or APIs.
Comparing Managed Identity and Service Principal:
To better understand the differences between Managed Identity and Service Principal, let’s compare some key aspects:
1. Resource ownership: Managed Identity is directly tied to an Azure resource, whereas Service Principal represents an application or a service.
2. Creation process: Managed Identity is created automatically when using a system-assigned Managed Identity, whereas Service Principals need to be manually created.
3. Visibility and control: Managed Identity requires less manual intervention, as it is created and managed automatically by Azure. On the other hand, Service Principals provide more control and visibility, as they are explicitly created and can be managed independently.
Use Cases:
Managed Identity and Service Principal cater to different use cases and scenarios. Some common use cases for both are as follows:
Managed Identity:
– Accessing Azure Key Vault, Azure Storage, or other Azure resources from within an Azure VM or App Service without storing any credentials.
– Automating resource provisioning and management processes using Azure Resource Manager (ARM) templates or Azure PowerShell/CLI scripts.
– Simplifying authentication and authorization for Azure Functions or Logic Apps.
Service Principal:
– Granting permissions to third-party applications or services to access specific Azure resources.
– Establishing trust between different Azure AD tenants or subscriptions.
– Automating deployments and management tasks using tools like Azure DevOps.
FAQs:
Q1. Can I use both Managed Identity and Service Principal together?
Yes, both Managed Identity and Service Principal can be used together in certain scenarios. For example, you can use a Managed Identity to authenticate and authorize an Azure VM, and then use a Service Principal to access a specific resource within that VM.
Q2. Can I convert a system-assigned Managed Identity to a user-assigned Managed Identity?
Yes, you can convert a system-assigned Managed Identity to a user-assigned Managed Identity. However, the process requires some additional steps and might involve downtime for the associated resource.
Q3. Can I retrieve the credentials associated with a Managed Identity or Service Principal?
No, Managed Identity and Service Principal do not have associated credentials that can be retrieved. They use tokens obtained from Azure AD for authentication and authorization.
Q4. Can Managed Identity or Service Principal be used with applications running outside Azure?
Yes, both Managed Identity and Service Principal can be used with applications running outside Azure. However, additional steps and configurations may be required to establish trust and enable authentication.
In conclusion, Managed Identity and Service Principal are two important concepts in Azure that play a vital role in securing access to resources. Managed Identity simplifies the authentication process for Azure resources, while Service Principal represents applications or services. By understanding their differences, advantages, and use cases, developers and administrators can effectively manage access and maintain a secure environment in Azure.
Images related to the topic service principal vs managed identity

Found 30 images related to service principal vs managed identity theme


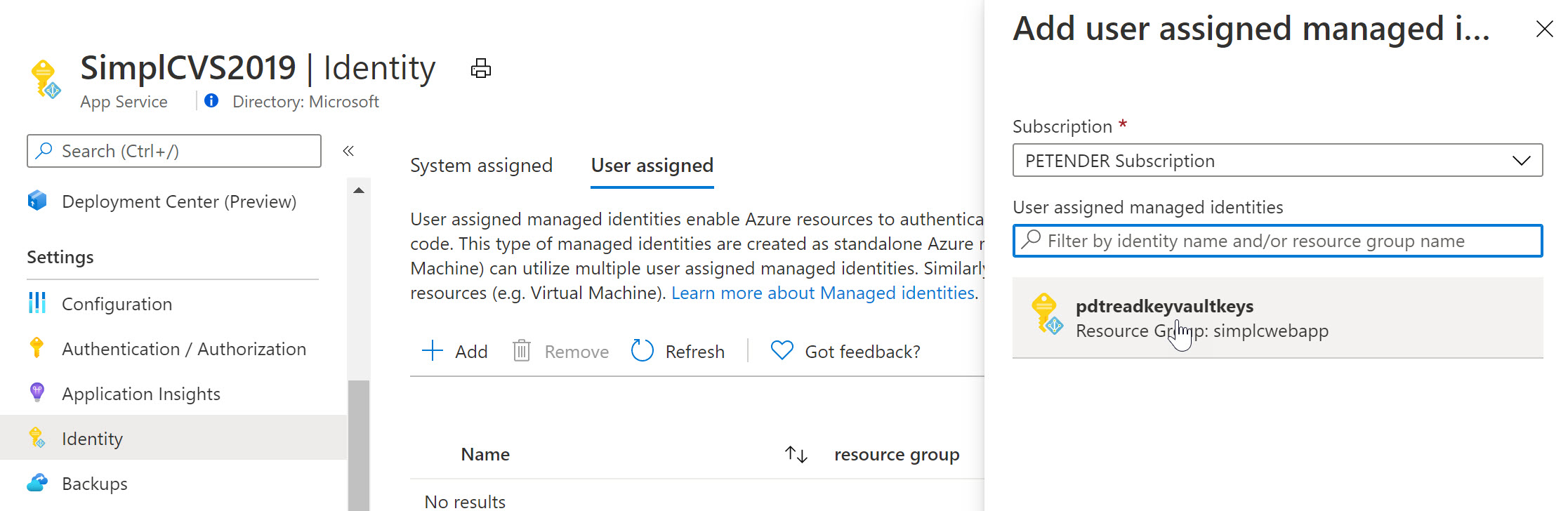

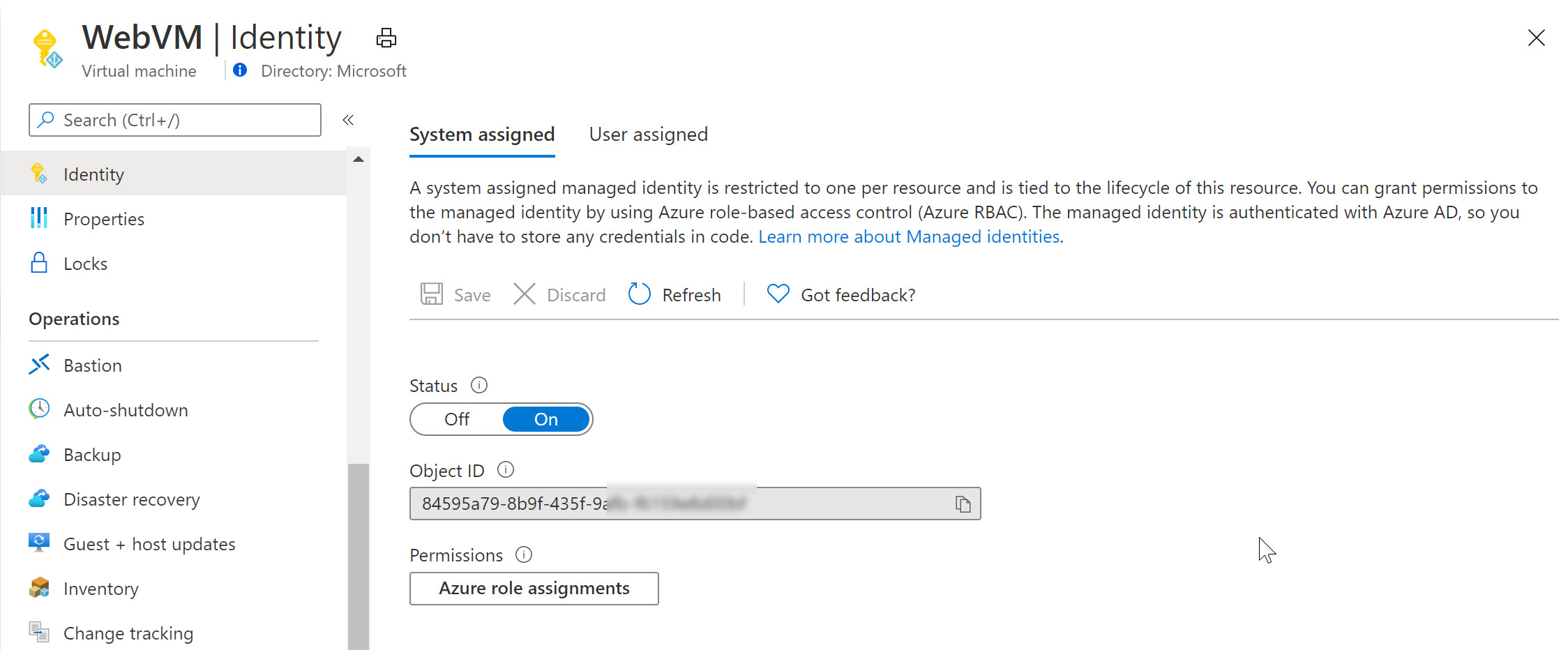



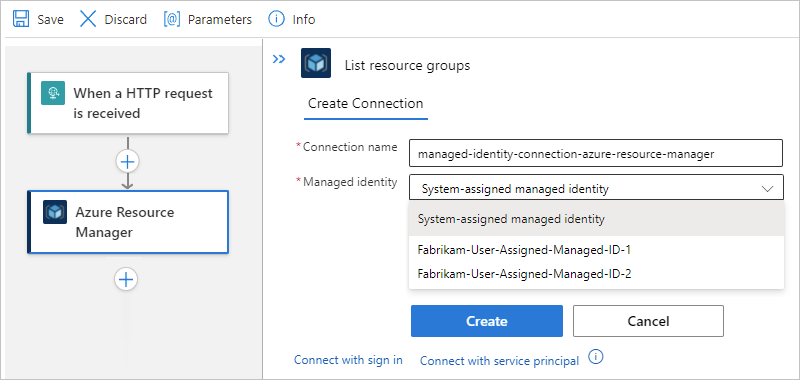




-2x.jpg?width=2480&name=13%20(edited)-2x.jpg)
















Article link: service principal vs managed identity.
Learn more about the topic service principal vs managed identity.
- Azure Managed Identity Vs Azure Service Principal – C# Corner
- Why and how to create Azure service principals – TechTarget
- Securing service principals in Azure Active Directory – Microsoft Entra
- Manage user-assigned managed identities – Microsoft Entra
- Use managed identities on an Azure VM for sign-inV – Microsoft Learn
- Demystifying Service Principals – Managed Identities
- Difference between Service Principal and Managed Identities …
- Why and how to create Azure service principals – TechTarget
- Managed Identities vs Service Principals – when to use what
- Azure – Service Principals v/s Managed Identities – LinkedIn
- Azure Managed Identity vs Service principal
- Difference between Service Principal and Managed Identity in …
- Introducing Service Principal and Managed Identity support on …
- What’s an Azure Service Principal and Managed Identity?
See more: https://nhanvietluanvan.com/luat-hoc/