The Proxy Tunnel Request To Proxy
Understanding Proxy Tunneling
In the world of internet communication and data transfer, proxies play a significant role in enhancing security and privacy. With the increasing prevalence of online threats, it has become crucial to implement measures to protect sensitive information and ensure secure connections. Proxy tunneling is one such mechanism that allows users to request a proxy to establish a secure and encrypted connection between their device and the target server. This article aims to explore the concept of proxy tunneling, its working principles, different methods, protocols used, benefits, considerations, and the process of requesting a proxy.
Defining Proxy Tunneling
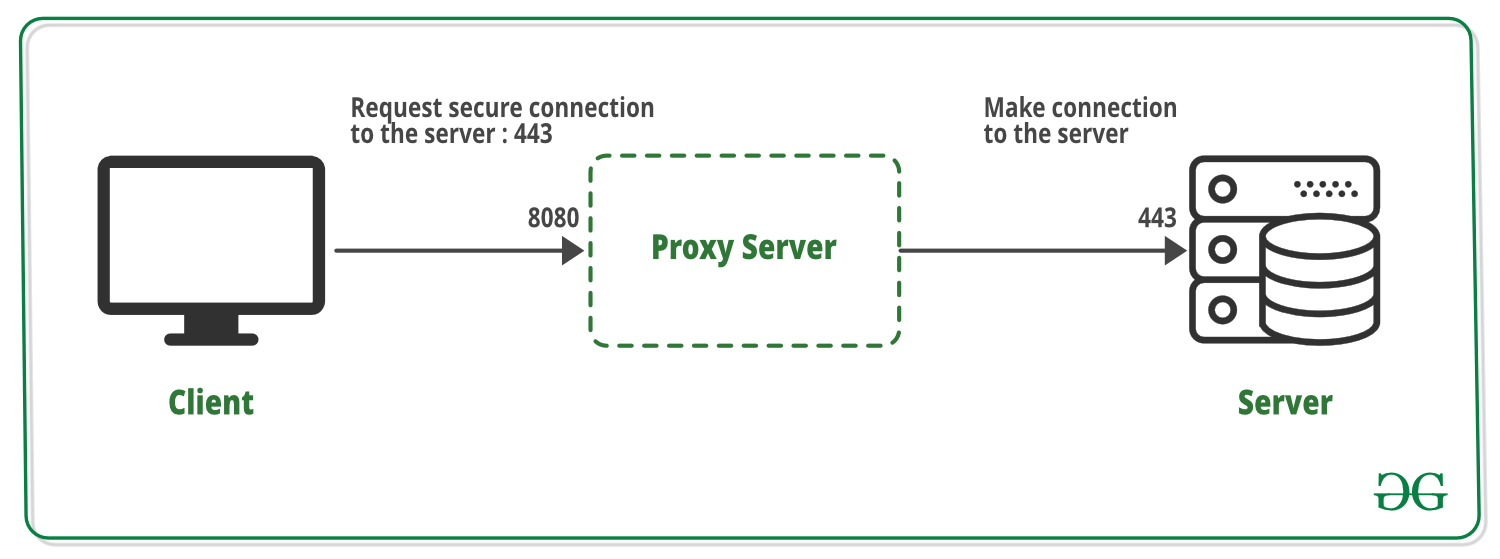
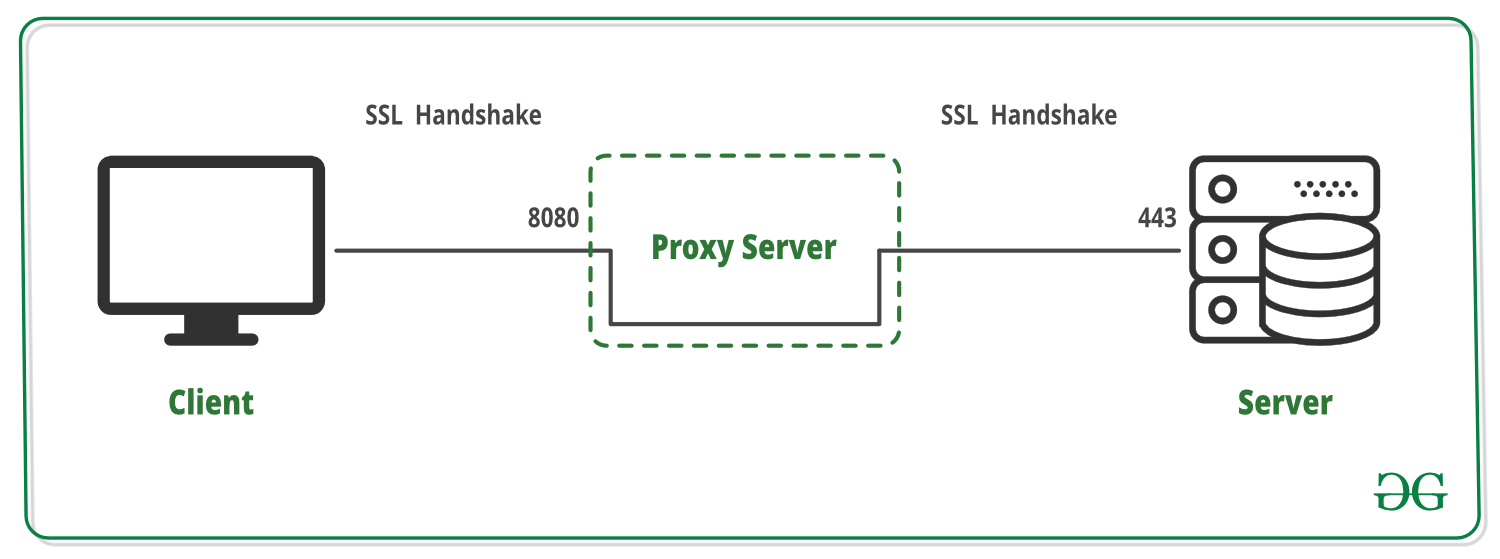
Proxy tunneling refers to the process of encapsulating network protocols within other protocols to create a secure connection between the client and the server through a proxy server. It involves routing the internet traffic through an intermediate server (proxy) that acts as a gateway. The proxy server intercepts the requests from the client, forwards them to the target server, and then returns the response back to the client. The purpose of tunneling is to encrypt the data, hide the client’s IP address, and provide anonymity and security.
The Role of Proxies in Internet Communication
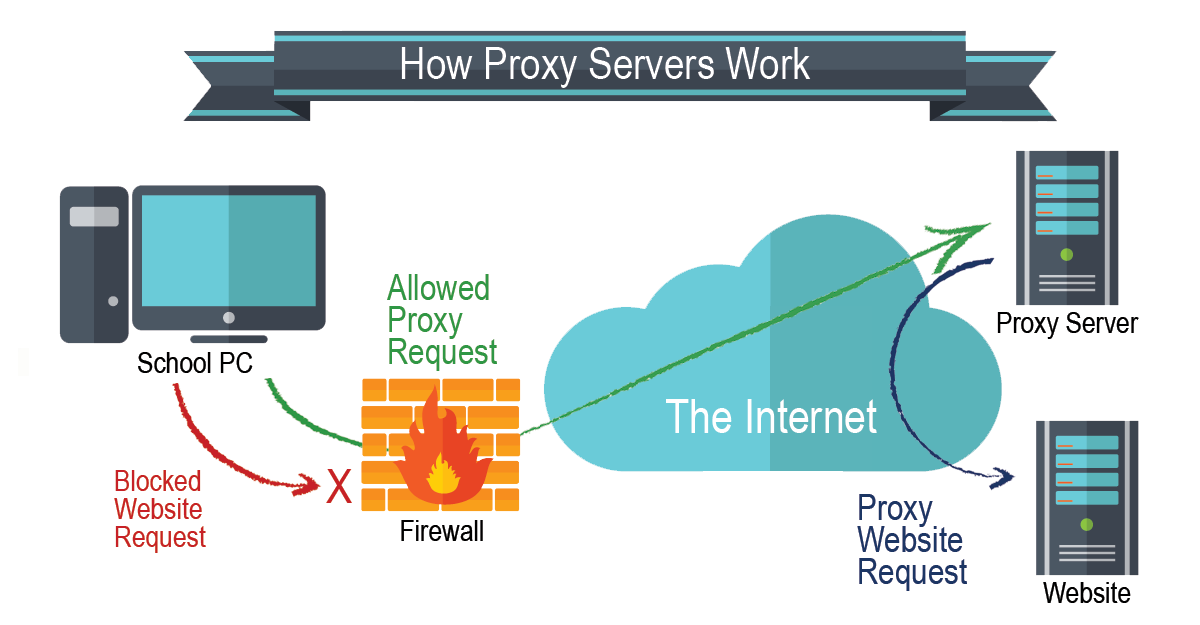
Proxies act as intermediaries between clients and servers, facilitating and controlling internet communication. They can serve multiple purposes such as caching data, filtering content, load balancing, and improving security. By acting as a middleman, proxies can perform various functions to enhance the user experience and protect the client’s identity.
How Proxy Tunneling Works
When a user requests a proxy tunnel, the client establishes a connection with the proxy server. The client then encapsulates its network traffic within a specific protocol supported by the proxy server, creating a tunnel between the two endpoints. This tunnel acts as a secure and encrypted pathway for all subsequent communication between the client and the target server. The proxy server relays the requests to the target server on behalf of the client, ensuring that the client’s identity and data remain hidden and protected.
Different Methods of Proxy Tunneling
Proxy tunneling can be achieved through various methods, each with its own advantages and limitations. The most commonly used methods include:
1. HTTP Tunneling: This method encapsulates the requests within HTTP or HTTPS protocols, allowing them to pass through proxy servers that support these protocols. HTTP tunneling is widely used and operates at the application layer, making it compatible with a wide range of applications.
2. SOCKS Tunneling: SOCKS (Socket Secure) tunneling establishes a secure connection between the client and the server, passing data through a SOCKS proxy server. It works at the transport layer and supports TCP and UDP protocols, making it suitable for applications that require low-level access to the network.
Common Protocols Used for Proxy Tunneling
Proxy tunneling supports different protocols depending on the chosen method. Some of the commonly used protocols include:
1. HTTP/HTTPS: HTTP and HTTPS are widely used for proxy tunneling as they provide compatibility with various applications and web browsers.
2. SOCKS: SOCKS protocols, especially SOCKS5, are commonly used for tunneling TCP and UDP traffic through proxies.
Benefits and Advantages of Proxy Tunneling
Proxy tunneling offers several benefits and advantages in terms of security, privacy, and network management. Here are some prominent advantages:
1. Enhanced Security: Proxy tunneling encrypts the data transmitted between the client and the target server, preventing unauthorized access and eavesdropping. It adds an additional layer of protection to sensitive information.
2. Anonymity and Privacy: By hiding the client’s IP address and routing the traffic through a proxy server, proxy tunneling ensures anonymity and protects the user’s privacy.
3. Access to Restricted Content: Proxy tunneling allows users to bypass regional restrictions and access geo-blocked content by routing their requests through proxy servers located in different regions.
4. Improved Network Performance: Proxies can cache frequently accessed data, reducing the load on servers and improving network performance. This can result in faster response times and reduced bandwidth usage.
Considerations when Requesting a Proxy Tunnel
When requesting a proxy tunnel, there are a few considerations to keep in mind:
1. Compatibility: Ensure that the proxy server and the target server support the desired tunneling method and protocol. Different servers may have different requirements and limitations.
2. Authentication: If the proxy server requires authentication, provide the necessary credentials to establish a successful connection.
3. Network Configuration: Verify that the network configuration allows proxy tunneling and that the necessary ports and protocols are not blocked by firewalls or other security measures.
4. Troubleshooting: In case of any issues or errors, refer to the error codes or error messages to diagnose and troubleshoot the problem. Common error codes include ‘403’, ‘502’, and ‘407’. For example, the proxy tunnel request to proxy failed with status code ‘403’ c#, ‘502’, ‘407’ in UiPath or .NET Core environments.
Conclusion
Proxy tunneling is a powerful mechanism that enables users to establish secure and encrypted connections between their devices and target servers. By encapsulating network protocols within other protocols, proxy tunneling ensures data privacy, security, and anonymity. Understanding the different methods, protocols, and benefits of proxy tunneling is essential for making informed decisions when requesting a proxy tunnel. Remember to consider compatibility, authentication, network configuration, and troubleshooting methods to ensure a successful and secure connection.
FAQs
1. What does the error message ‘Proxy Tunnel Request to Proxy Failed with Status Code ‘403’ C#’ mean?
The error message ‘Proxy Tunnel Request to Proxy Failed with Status Code ‘403’ C#’ indicates that the client’s request to establish a proxy tunnel was rejected due to insufficient permissions or authorization. The client may need to provide valid credentials or adjust the proxy server settings to resolve this error.
2. Why do I receive the error message ‘Proxy Tunnel Request to Proxy Failed with Status Code ‘502’?
The error message ‘Proxy Tunnel Request to Proxy Failed with Status Code ‘502” typically suggests that the proxy server, acting as a gateway, is unable to establish a connection to the target server. This error could be due to network issues, misconfiguration, or server unavailability. Checking the network connectivity and troubleshooting the proxy server configuration could help resolve this error.
3. What does the error message ‘Proxy Tunnel Request to Proxy Failed with Status Code ‘407’ UiPath/.NET Core’ mean?
The error message ‘Proxy Tunnel Request to Proxy Failed with Status Code ‘407’ UiPath/.NET Core’ indicates that the client’s request to establish a proxy tunnel requires authentication. The proxy server is requesting the client to provide valid credentials to access the requested resource. Providing the appropriate authentication credentials should resolve this error.
4. How can I establish a remote proxy for an open tunnel?
To establish a remote proxy for an open tunnel, you need to configure the proxy server to accept incoming connections from the client device. This typically involves configuring the router or firewall to redirect the incoming traffic to the proxy server. Consult the documentation or support resources for your specific proxy server to understand the steps required for remote proxy configuration.
5. What does the error message ‘Proxy Returns HTTP/1.1 407 Proxy Authentication Required’ mean?
The error message ‘Proxy Returns HTTP/1.1 407 Proxy Authentication Required’ indicates that the client’s request to access a resource through the proxy server requires authentication. The proxy server is requesting the client to provide valid credentials before granting access. Make sure to provide the required authentication credentials to resolve this error.
6. Can I use HttpClient with a proxy?
Yes, HttpClient can be used with a proxy by specifying the proxy settings in the HttpClient configuration. The proxy settings include the proxy server’s address, port, and potentially authentication credentials. Review the HttpClient documentation for your programming language or framework to understand the specific methods and properties for configuring a proxy.
How To Make An Ssh Proxy Tunnel
How Does A Proxy Tunnel Work?
In an age where online privacy and security are of utmost importance, understanding how a proxy tunnel works is crucial for individuals and businesses alike. A proxy tunnel serves as an intermediary between a user’s device and the destination server, allowing for enhanced security and anonymity while accessing the internet. In this article, we will delve into the inner workings of a proxy tunnel, discussing its uses, benefits, and the technical aspects that make it function seamlessly.
Understanding the Basics
A proxy tunnel, also known as a tunneling proxy or simply a tunnel, is a method of bypassing firewalls and other network restrictions by encapsulating network protocol data within another protocol. It acts as a bridge between the client device and the internet, forwarding requests and responses back and forth. When a user requests a website, the request is intercepted by the proxy tunnel, which then fetches the information from the destination server and relays it back to the user. This process ensures that the user’s IP address remains hidden, providing an additional layer of privacy.
Encryption and Anonymity
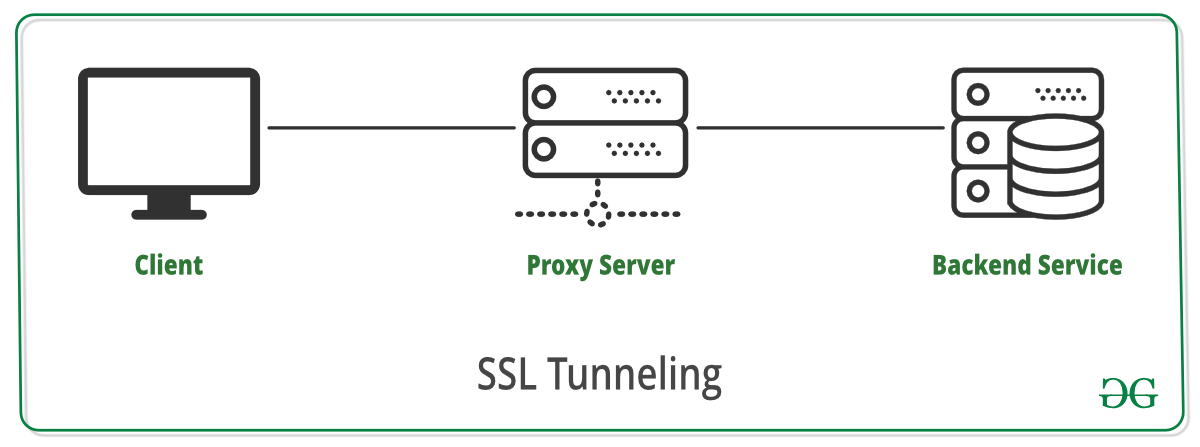
One of the key benefits of utilizing a proxy tunnel is the ability to encrypt online communication. By encapsulating the data within another protocol, such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS), the information is shielded from prying eyes and potential eavesdroppers. This level of encryption ensures that sensitive data, such as usernames, passwords, and financial information, remains secure throughout the transmission process.
Furthermore, a proxy tunnel allows users to remain anonymous while accessing the internet. Instead of directly connecting to a website or service, the user connects to the proxy tunnel, which then serves as a middleman between the client and the destination server. The destination server only sees the IP address of the proxy tunnel, providing an additional layer of anonymity for users concerned about their online privacy.
Types of Proxy Tunnels
There are several types of proxy tunnels that serve various purposes depending on the user’s requirements. Some common types include:
1. HTTP Proxy: The most basic type of proxy tunnel, it provides access to HTTP websites. This is useful for individuals who want to bypass firewall restrictions or access geo-blocked content.
2. SSL Proxy: This type of tunnel adds SSL encryption to the HTTP traffic, ensuring secure browsing and data transmission. It is particularly useful when accessing sensitive information over public Wi-Fi networks.
3. SOCKS Proxy: Unlike HTTP proxies, SOCKS (Socket Secure) proxies support a broader range of protocols, including TCP, UDP, and FTP. They are commonly used for activities such as torrenting, online gaming, and streaming media.
4. Reverse Proxy: This type of tunnel is used to manage and distribute incoming web traffic across multiple servers. It enhances performance, load balancing, and security for websites with high traffic.
Technical Aspects
To better understand how a proxy tunnel functions, let’s explore the technical aspects involved. When a user sends a request through a proxy tunnel, the request is intercepted and encapsulated into a new packet. This packet contains the user’s original request along with additional information, such as the destination server’s IP address and port number.
The encapsulated packet is then transmitted to the proxy server, which acts as the intermediary. The proxy server receives the packet, unpacks it, and relays the request to the destination server. The destination server processes the request and sends the response back to the proxy server, which then forwards it to the user’s device. Throughout this process, the user’s original IP address remains hidden, providing enhanced security and privacy.
In addition to encryption and anonymity, proxy tunnels can offer features such as caching, content filtering, and bandwidth control. These features help optimize network performance and provide a seamless browsing experience for users.
FAQs
1. Why should I use a proxy tunnel?
A proxy tunnel offers enhanced security and privacy by encrypting your online communication and hiding your IP address. It allows you to bypass network restrictions and access geo-blocked content, ensuring a safer and more open internet experience.
2. Can a proxy tunnel slow down my internet connection?
While a proxy tunnel may introduce a slight delay due to the additional processing involved, the impact on internet speed is typically minimal. The actual speed depends on various factors, such as the server’s location, bandwidth capacity, and network congestion.
3. Is using a proxy tunnel legal?
Using a proxy tunnel for legitimate purposes, such as ensuring privacy or bypassing network restrictions, is generally considered legal. However, it is important to comply with local laws and regulations and refrain from illegal activities while using a proxy tunnel.
In conclusion, a proxy tunnel serves as a secure and anonymous intermediary between a user’s device and the destination server. By encapsulating network protocol data within another protocol, a proxy tunnel offers encryption, anonymity, and additional features that enhance online privacy and security. Whether you are concerned about your data’s safety or want to access restricted content, understanding how a proxy tunnel works is essential in today’s digital landscape.
What Is The Difference Between Proxy And Tunnel?
In the world of networking and internet security, the terms proxy and tunnel are often used interchangeably, but they serve distinct purposes and have different implementations. Both proxy and tunnel act as intermediaries between a client device and a server, enabling secure and private communication over public networks. However, there are fundamental differences between the two that users should be aware of to make informed decisions on which solution to deploy based on their specific needs.
Proxy servers:
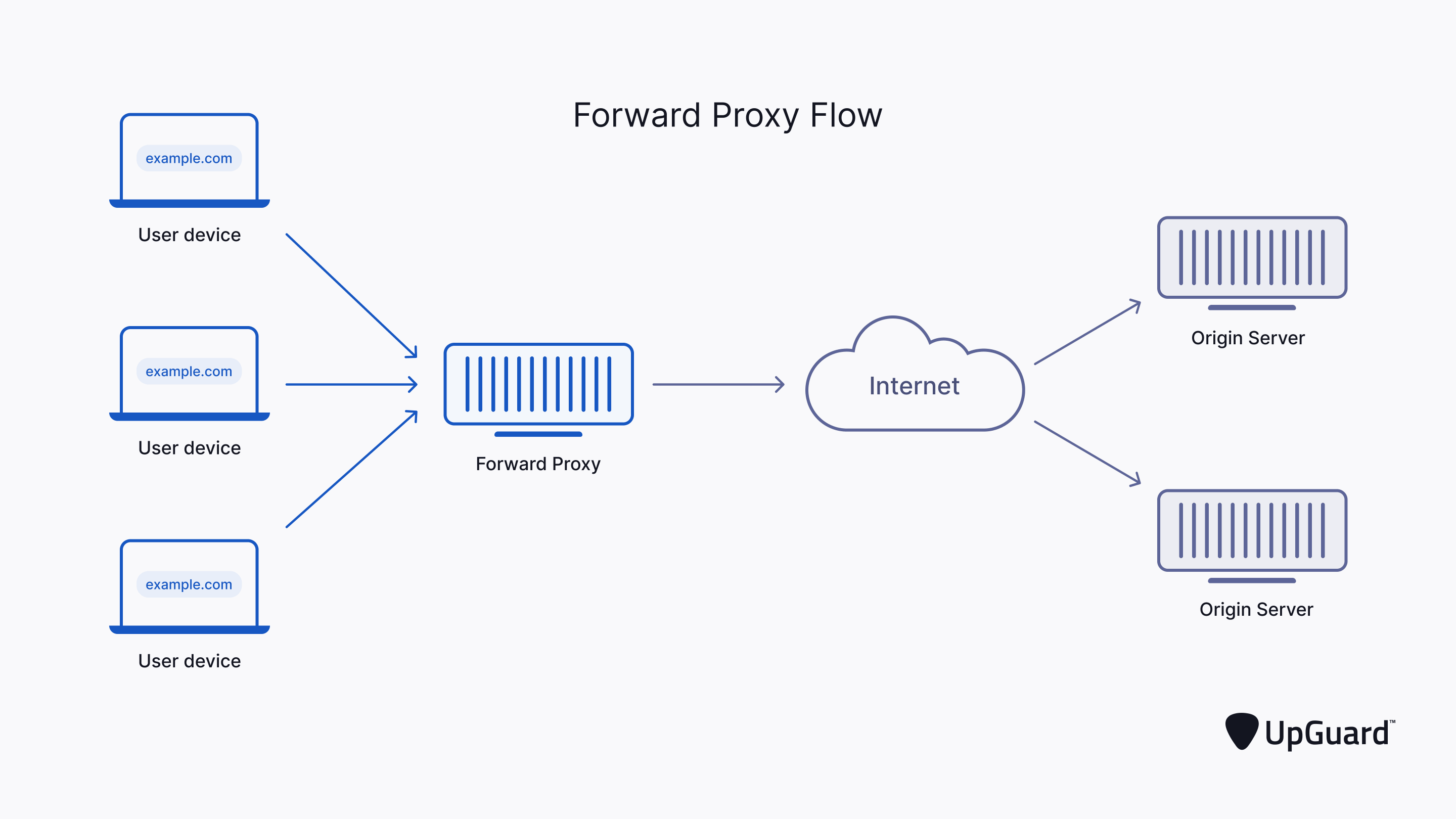
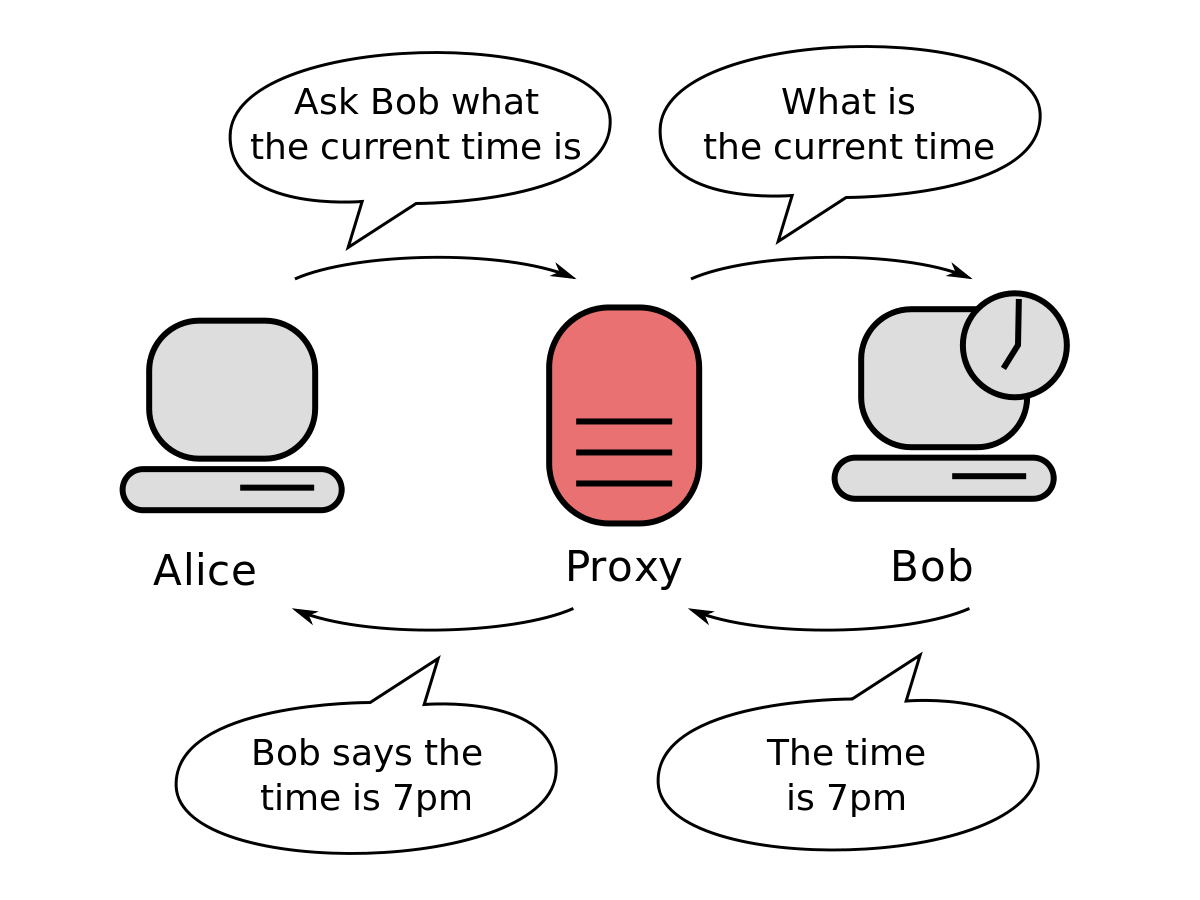
Proxy servers are well-known entities that have been used for decades to improve performance, facilitate caching, and enhance security. Acting as intermediaries between client devices and servers, proxy servers receive requests from client devices seeking resources from a server. Instead of directly forwarding these requests to the server, the proxy server intercepts and processes them on behalf of the client device.
There are several types of proxies available, including forward proxies, reverse proxies, and open proxies. Forward proxies are client-side proxies used to access the internet from within a protected network. They cache web pages and optimize network traffic to improve performance for clients. Reverse proxies, on the other hand, operate on the server-side, usually within the DMZ (demilitarized zone). They handle incoming traffic from external clients, distributing it across multiple servers to balance the load or provide additional security measures.
Proxy servers serve as gatekeepers that shield client devices from direct communication with servers, thus enhancing security by hiding the client’s IP address and other identifying information. Additionally, they can filter and restrict certain types of traffic, such as blocking access to specific websites or censoring content. Proxies can also be configured to provide content filtering or perform deep-packet inspection to analyze network traffic for threats.
Tunnels:
Tunnels, unlike proxies, are not intermediaries but rather secure conduits created between devices across public networks. Tunnels establish end-to-end encrypted connections between devices, enabling secure communication over potentially untrusted networks. These connections can be established using various protocols such as IPsec, SSL/TLS, or SSH.
Tunnels encapsulate the entire packet of data within another protocol, creating a secure “tunnel” that shields the actual data from unauthorized access. This makes it an ideal solution for remote access, where users need to connect securely to a private network from another location or when communicating over public Wi-Fi networks.
One common use of tunnels is Virtual Private Network (VPN) connections. VPNs create a secure tunnel between the user’s device and the VPN provider’s server, encrypting all traffic exchanged between them. This ensures all data, including sensitive information, remains private and protected from potential eavesdroppers. Tunnels are also utilized in Secure Shell (SSH) connections, often used for remote administration.
While proxies are typically used to improve performance, provide caching, and enhance security within a network, tunnels are primarily aimed at securing communications between devices over public networks. Tunnels encrypt traffic from end to end, providing a higher level of confidentiality and protection.
FAQs
1. Which is better, proxy or tunnel?
The choice between a proxy and a tunnel depends on your specific requirements. If you need to enhance security, privacy, and encryption for individual devices or connection points, a tunnel such as a VPN may be more suitable. If you are looking to optimize performance, improve caching, or filter certain types of network traffic, a proxy server might be the better option.
2. Can I use both a proxy and a tunnel simultaneously?
Yes, it is possible to use both a proxy and a tunnel concurrently. For example, you can use a forward proxy to optimize network traffic and cache web pages while establishing a tunnel like a VPN for secure communication between devices.
3. Are tunnels only used for remote access?
While tunnels are commonly used for remote access scenarios, they can also be employed for other purposes. Tunnels can be used to provide secure communication and encryption for device-to-device connections within a network, making them useful for protecting data transmission between servers or other devices.
4. Are tunnels and proxies always secure?
Both tunnels and proxies can enhance security, but the level of security depends on how they are implemented. Tunnels, when properly configured, can provide end-to-end encryption, offering a high level of security. Proxies, on the other hand, can provide enhanced security by acting as intermediaries and hiding IP addresses, but they do not inherently provide encryption.
5. Can tunnels and proxies be used together to maximize security?
Yes, using a tunnel and a proxy together can enhance security. By using a tunnel with end-to-end encryption, you can secure the communication channel between devices, while a proxy can further enhance security by acting as an intermediary to hide IP addresses and perform content filtering.
In conclusion, while proxies and tunnels may seem similar at first glance, they serve different purposes and provide unique benefits. A proxy acts as an intermediary server, optimizing performance and enhancing security within a network, while a tunnel establishes secure connections between devices over public networks, encrypting data for privacy and confidentiality. Understanding the differences between these two concepts enables users to make informed decisions on which solution to implement based on their specific needs.
Keywords searched by users: the proxy tunnel request to proxy the proxy tunnel request to proxy failed with status code ‘403’ c#, the proxy tunnel request to proxy failed with status code ‘502’, the proxy tunnel request to proxy failed with status code ‘407’ uipath, the proxy tunnel request to proxy failed with status code ‘407’ .net core, remote proxy for open tunnel, proxy returns http/1.1 407 proxy authentication required, httpclient proxy, proxy request
Categories: Top 38 The Proxy Tunnel Request To Proxy
See more here: nhanvietluanvan.com
The Proxy Tunnel Request To Proxy Failed With Status Code ‘403’ C#
Introduction
In software development, it is common to encounter various error codes while making requests to a server. One such error that developers often come across is the ‘403 Forbidden’ status code. This error occurs when a request is made to a proxy, but the proxy server denies access to the requested resource. In this article, we will dive deep into understanding this error and explore solutions to overcome it in C#.
Understanding the ‘403 Forbidden’ Status Code
When a client, be it a browser or an application, sends a request to a server through a proxy, the proxy server acts as an intermediary between the client and the server. It evaluates the request and decides whether to proceed with forwarding the request to the destination server or deny access.
The ‘403 Forbidden’ status code indicates that the request was valid, but the server understood it and refused to authorize it. This can happen due to several reasons, such as insufficient permissions, incorrect proxy configurations, or the request being blocked by the server’s security rules.
Dealing with the ‘403 Forbidden’ Error in C#
1. Verify Proxy Server Credentials
One common reason for the ‘403 Forbidden’ error is invalid or missing proxy credentials. Ensure that you have the correct username and password for the proxy server, and make sure to include them in the request headers. For example:
“`
var httpClientHandler = new HttpClientHandler
{
Proxy = new WebProxy(“http://your-proxy-server-url”),
UseProxy = true,
Credentials = new NetworkCredential(“username”, “password”),
};
var httpClient = new HttpClient(httpClientHandler);
“`
2. Check Proxy Server Configuration
The proxy server may have specific configurations that restrict access to certain resources. Review the proxy server’s documentation or contact the administrator to ensure that you are sending the request to the correct URL and port. Incorrect proxy configurations can lead to a ‘403 Forbidden’ error.
3. Review Server-Side Security Rules
The server to which the request is being forwarded may have security rules in place that block requests based on various factors, such as IP address, user-agent, or request headers. Analyze the server’s documentation or engage with the server administrator to understand if any security rules are preventing the request from being authorized.
4. Handle Proxy Authentication Challenges
Sometimes, the proxy server may require additional authentication methods, such as Digest or NTLM. In such cases, you need to handle the proxy authentication challenges appropriately. The HttpClient class in C# provides methods like ‘DefaultProxyCredentials’ or ‘Proxy.Credentials’ to handle specific authentication mechanisms.
5. Change Proxy Server
If all the above steps fail, consider trying a different proxy server. It is possible that the current proxy server is blocking the request for some reason. Switching to another proxy server might resolve the ‘403 Forbidden’ error.
Frequently Asked Questions (FAQs)
Q1. Can I bypass the ‘403 Forbidden’ error without modifying the proxy settings?
A1. In most cases, modifying proxy settings or addressing the authentication requirements is necessary to resolve the ‘403 Forbidden’ error. However, if you are working within an isolated environment, such as local development or a controlled network, you may consider disabling the proxy altogether.
Q2. How can I check if a specific request is being blocked by the proxy server?
A2. You can use tools like Fiddler or Wireshark to intercept and analyze the network traffic. These tools provide insights into the request and response headers, allowing you to identify any proxy-related issues.
Q3. What if I don’t have direct access to the proxy server configuration or credentials?
A3. If you do not have direct access to the proxy server configuration or credentials, reach out to the person responsible for managing the proxy server or contact your network administrator. They should be able to provide you with the necessary details or assist in resolving the issue.
Q4. I’m using a third-party library in my C# project. How can I configure the proxy settings for that library?
A4. Many third-party libraries honor the system’s default proxy settings. Therefore, configuring the proxy settings at the system level should reflect in the library’s behavior. However, if the library provides specific proxy configuration options, refer to its documentation or consult the library’s support community for guidance.
Conclusion
The ‘403 Forbidden’ error is a common issue encountered when working with proxies in C# applications. By understanding the causes behind this error and following the recommended solutions mentioned in this article, you can troubleshoot and resolve the issue effectively. Remember to verify proxy credentials, review server-side configurations, handle authentication challenges appropriately, and consider switching to a different proxy server if necessary.
The Proxy Tunnel Request To Proxy Failed With Status Code ‘502’
Introduction (100 words):
When browsing the internet, encountering a proxy tunnel request failure can be frustrating. If you come across a status code ‘502’ error, it means that the proxy server you attempted to connect with was unable to process your request. This article will delve into the common causes behind a failed proxy tunnel request, explore potential solutions, and address some frequently asked questions to help you understand and troubleshoot this issue effectively.
Understanding a Proxy Tunnel Request Failure (200 words):
A proxy server acts as an intermediary between your device and the websites you visit. It facilitates communication by forwarding your requests and responses, enhancing security and privacy, and improving network performance. However, sometimes the connection between your device and the proxy server is disrupted, leading to a failed proxy tunnel request with a status code ‘502’ error.
The ‘502’ status code, commonly referred to as the “Bad Gateway” error, typically occurs when the proxy server receives an invalid response from the upstream server. In other words, the proxy server attempted to communicate with another server and expected a valid response, but received an invalid or incomplete one instead. This could be due to various factors, including server misconfigurations, network issues, or problems with the upstream server itself.
Causes and Solutions (500 words):
1. Server Misconfigurations:
– Incorrect proxy server settings: Ensure that the proxy server settings (IP address, port, etc.) are configured correctly in your browser or device network settings.
– Improper DNS configuration: Verify that the DNS settings are properly configured on both your device and the proxy server.
– Insufficient timeout settings: Adjust the timeout values to allow sufficient time for the proxy server to establish a connection with the upstream server.
2. Network Connectivity Issues:
– Unstable internet connection: Check your internet connection for stability issues, such as high packet loss or intermittent outages.
– Firewall or antivirus settings: Disable any firewall or antivirus software that might be blocking the connection to the proxy server.
– Network congestion: If you are on a shared network, heavy traffic may hinder the proxy server’s ability to establish a connection. Wait until the network congestion eases or try connecting at a different time.
3. Upstream Server Issues:
– Server downtime or maintenance: The upstream server could be temporarily unavailable due to scheduled maintenance or unexpected downtime. Confirm if the server is operational, and try again later.
– Server overload: If the upstream server is experiencing a high volume of requests, it may struggle to respond to the proxy server’s connection attempt. Allow some time for the server to recover.
– Misconfigured server settings: Contact the administrator of the upstream server to ensure its settings are properly configured to respond to proxy server requests.
FAQs (218 words):
1. Can I bypass a proxy server to avoid 502 errors?
While bypassing a proxy server is possible, it is essential to understand that doing so might compromise your privacy, security, or other benefits that a proxy server provides. If you frequently encounter 502 errors, try troubleshooting the issues mentioned in the article before considering bypassing the proxy server.
2. Does a 502 error always indicate a problem with my network or device?
Not necessarily. A 502 error could be caused by issues on either the client-side (your device or network) or the server-side (proxy server or upstream server). Follow the suggested troubleshooting steps in this article to identify and rectify the problem.
3. Why do 502 errors occur intermittently?
Intermittent 502 errors could be caused by temporary issues, such as network congestion, server overload, or sporadic connectivity problems. Try refreshing the page or waiting a few minutes before attempting again.
4. Why does restarting my device often resolve 502 errors?
Restarting your device clears any temporary glitches or conflicts that might be hindering the proxy server connection. It helps establish a fresh network connection and can potentially resolve the issue.
Conclusion (100 words):
Encountering a “Proxy Tunnel Request to Proxy Failed with Status Code ‘502’” error can be frustrating, but understanding the causes and potential solutions can help alleviate the problem. By following the troubleshooting steps outlined in this article and addressing the frequently asked questions, you can effectively diagnose and resolve issues related to a failed proxy tunnel request, ensuring smoother browsing experiences in the future.
The Proxy Tunnel Request To Proxy Failed With Status Code ‘407’ Uipath
In the world of automation, UiPath has emerged as one of the leading Robotic Process Automation (RPA) platforms, empowering businesses to streamline their operations through the use of software robots. However, like any other technological solution, UiPath may encounter occasional errors that users must troubleshoot to ensure smooth functioning. One such error is the “Proxy Tunnel Request to Proxy Failed with Status Code ‘407’” message, which can disrupt the execution of automation processes. In this article, we will delve into the possible causes of this error and explore the various solutions to rectify it.
Understanding the Error:
When attempting to establish a connection with a proxy server, UiPath may encounter a ‘407’ status code, which indicates that the proxy requires user authentication. This error message is often accompanied by the following error details: “The remote server returned an error (407) Proxy Authentication Required.” Essentially, UiPath is unable to authenticate the user with the proxy server, leading to a failed connection attempt.
Causes of the Error:
Several factors can contribute to the occurrence of the ‘407’ error in UiPath. Let’s take a closer look at each of these possible causes:
1. Proxy Server Configuration: The error can arise if the proxy server is not properly configured or if the provided credentials are incorrect. In such cases, UiPath fails to authenticate the user with the proxy server and returns the ‘407’ status code.
2. Firewall Restrictions: Firewalls are designed to protect a network by regulating the flow of incoming and outgoing traffic. If the firewall settings are excessively strict or misconfigured, they can prevent UiPath from connecting to the proxy server, leading to the ‘407’ error.
3. Incorrect Configuration in UiPath Settings: Incorrectly configured proxy settings within UiPath itself can trigger the ‘407’ error. UiPath relies on accurate proxy server details and user credentials to establish connections, and any discrepancies can result in authentication failure.
4. Internet Connectivity Issues: Limited or intermittent internet connectivity can interfere with the authentication process, as UiPath may struggle to establish a reliable connection with the proxy server. In such cases, the ‘407’ error may arise due to network instability.
Solutions to the Error:
Now that we have explored the potential causes of the ‘407’ error, it’s time to dive into the possible solutions. Here are some approaches you can take to rectify the issue:
1. Verify Proxy Server Configuration: Double-check the proxy server configuration and ensure that the provided credentials are accurate. Consult your network administrator if needed to ensure that the proxy server settings match the ones specified in UiPath.
2. Check Firewall Settings: Review the firewall settings to ensure that they are not excessively restrictive. If necessary, consult with your IT team to modify the firewall rules to allow UiPath’s communication with the proxy server.
3. Configure Proxy Settings in UiPath: Accurately configure the proxy settings within UiPath by navigating to the “Proxy” tab in the “Robot” tray settings. Provide the correct proxy server address, port number, and user credentials to establish a successful connection.
4. Troubleshoot the Internet Connection: Verify that your internet connection is stable and reliable. If necessary, restart your router or switch to a different network connection to eliminate any connectivity issues that may be causing the ‘407’ error.
Frequently Asked Questions:
Q: Can I bypass the proxy server and still use UiPath?
A: While it is possible to bypass the proxy server, it is recommended to consult with your network administrator before doing so. Bypassing a proxy server may compromise network security and violate organizational policies.
Q: Are there any alternative solutions if the error persists?
A: If the ‘407’ error continues to occur despite the above solutions, consider reaching out to UiPath’s support team for further assistance. They will be able to analyze the specific error logs and provide tailored guidance to resolve the issue.
Q: Can the ‘407’ error occur in other RPA platforms?
A: Yes, the ‘407’ error can be encountered in other RPA platforms as well. However, the exact error message and troubleshooting steps may vary depending on the specific automation software being utilized.
Conclusion:
The Proxy Tunnel Request to Proxy Failed with Status Code ‘407’ error in UiPath can disrupt the seamless functioning of automation processes. By understanding the causes and implementing the appropriate solutions, users can rectify this error and ensure uninterrupted automation. Whether it’s verifying proxy server configuration, adjusting firewall settings, or troubleshooting internet connectivity, troubleshooting this error will help users unlock the full potential of UiPath and achieve operational efficiency.
Images related to the topic the proxy tunnel request to proxy

Found 22 images related to the proxy tunnel request to proxy theme

















Article link: the proxy tunnel request to proxy.
Learn more about the topic the proxy tunnel request to proxy.
- HttpClient throws exception with message “The proxy tunnel …
- How to solve the Proxy Server 407 error in .NET.CORE
- Proxy servers and tunneling – HTTP – MDN Web Docs
- HTTP tunnel – Wikipedia
- HTTP tunnel vs HTTP proxy – Stack Overflow
- HTTP Proxy Tunneling – Rafael Gonzaga
- Can’t consume web services via an HTTP proxy server – .NET …
- How To Fix HTTP Error 407 “Proxy Authentication Required”
- Unable to connect through Proxy Tunnel from within Studio
- HttpClient throws an error when sending HTTPS requests via …
- HTTP tunnel – Wikipedia
- Using HTTP Tunnel to Traceroute Through a Proxy With Firewall
See more: nhanvietluanvan.com/luat-hoc