Sudo No Tty Present And No Askpass Program Specified
Possible Causes of “sudo: no tty present and no askpass program specified” Error:
1. Incorrect Configuration of sudoers File:
One possible cause of this error is an incorrect configuration of the sudoers file. The sudoers file is responsible for defining which users can run which commands with sudo. If there are syntax errors or incorrect entries in the sudoers file, it can lead to the mentioned error message.
2. Absence of TTY Device or Misconfiguration:
A TTY (teletypewriter) device is a terminal device that allows user interaction through a command-line interface. If the system does not have a TTY device or if it is misconfigured, it can result in the mentioned error. The absence or misconfiguration of the TTY device prevents the proper execution of the sudo command.
3. Sudo Configuration Issues:
In some cases, the error may occur due to configuration issues with the sudo command itself. This can happen if there are conflicts with other configuration files or if there are discrepancies in the system settings related to sudo.
4. Conflict with PAM Modules or Security Policies:
Pluggable Authentication Modules (PAM) provide a unified interface for user authentication. If there are conflicts between PAM modules or security policies on the system, it can cause the “sudo: no tty present and no askpass program specified” error. These conflicts can arise due to misconfigurations or unsupported configurations.
5. Unavailability of the askpass Program:
The askpass program is responsible for prompting the user for a password when executing sudo commands. If the askpass program is missing, corrupted, or misconfigured, it can result in the mentioned error. The absence of the askpass program prevents the system from acquiring the necessary password input from the user.
6. Insufficient Privileges or Incorrect Sudo Command:
This error may also occur if the user does not have sufficient privileges to run the sudo command or if the syntax of the sudo command itself is incorrect. In such cases, the system denies the execution of the sudo command and displays the error message.
Solutions for the “sudo: no tty present and no askpass program specified” Error:
1. Editing the sudoers File:
To resolve this error, check the sudoers file for any syntax errors or incorrect entries. Make sure that the file is properly configured and that the user running the sudo command is granted the necessary privileges.
2. Checking and Configuring the TTY Device:
If the error is due to an absence or misconfiguration of the TTY device, verify the presence of the device and ensure that it is correctly configured. This may require modifying system settings or updating device drivers.
3. Adjusting Sudo Configuration:
Review the sudo configuration files and settings to ensure that there are no conflicting configurations or discrepancies. Make any necessary adjustments to resolve conflicts and ensure the proper functioning of sudo.
4. Resolving Conflicts with PAM Modules or Security Policies:
If there are conflicts with PAM modules or security policies, review the relevant configuration files and settings. Identify and resolve any conflicting configurations or unsupported policies to eliminate the error.
5. Installing or Verifying the Availability of askpass Program:
Ensure that the askpass program is installed and accessible on the system. If it is missing or misconfigured, reinstall or reconfigure the program. Verify that the system is able to prompt for passwords when executing sudo commands.
6. Verifying Privileges and Correct Syntax for the Sudo Command:
Check the user’s privileges and ensure that they have sufficient permissions to run the sudo command. Additionally, double-check the syntax of the sudo command to ensure that it is correctly formatted.
FAQs:
Q: How can I configure sudo to run without asking for a password?
A: To configure sudo to run without asking for a password, you can add the following line to the sudoers file:
username ALL=(ALL:ALL) NOPASSWD: ALL
Replace ‘username’ with the actual username.
Q: How do I add Jenkins to the sudoers file?
A: To add Jenkins to the sudoers file, run the following command as root:
sudo visudo
Then, add the following line to the sudoers file:
jenkins ALL=(ALL:ALL) NOPASSWD: ALL
Q: How can I run sudo with a password prompt?
A: By default, sudo prompts for a password when executing a command. If you want to run sudo with a password prompt, simply use the sudo command without any additional options or configurations.
Q: What does the error “The input device is not a TTY if you are using mintty, try prefixing the command with ‘winpty'” mean?
A: This error occurs when using the mintty terminal emulator with certain commands that require a TTY device. To resolve the error, you can prefix the command with ‘winpty’ like this:
winpty sudo command
Q: How do I add GitLab Runner to the sudoers file?
A: To add GitLab Runner to the sudoers file, run the following command as root:
sudo visudo
Then, add the following line to the sudoers file:
gitlab-runner ALL=(ALL:ALL) NOPASSWD: ALL
Q: I encountered the error “sudo: not found” when running a Docker command with sudo. How can I fix this?
A: The error indicates that the sudo command is not available in the Docker container. By default, Docker containers do not include the sudo package. You can execute commands as the root user directly or use the Docker command with elevated privileges, depending on your requirements.
Q: How can I run ‘su’ without a password prompt?
A: To run ‘su’ without a password prompt, you can modify the ‘/etc/sudoers’ file and add the following line:
username ALL=(ALL:ALL) NOPASSWD: /bin/su
Replace ‘username’ with your actual username.
Q: Can sudo be used for privilege escalation on Linux systems?
A: Yes, sudo is often used for privilege escalation on Linux systems. It allows authorized users to execute commands with elevated privileges, such as running administrative tasks as the root user. However, it should be used with caution to prevent unauthorized access and potential security breaches.
In conclusion, the error message “sudo: no tty present and no askpass program specified” indicates various possible causes, including incorrect sudoers file configuration, misconfigured TTY device, conflicts with PAM modules or security policies, unavailability of the askpass program, insufficient privileges, or incorrect sudo command syntax. By following the provided solutions and understanding the FAQs, you should be able to troubleshoot and resolve this error effectively. Remember to exercise caution when using sudo and always follow best security practices to ensure the integrity of your system.
Devops \U0026 Sysadmins: Sudo: No Tty Present And No Askpass Program Specified (3 Solutions!!)
Keywords searched by users: sudo no tty present and no askpass program specified Sudo without password, Add jenkins to sudoers, Sudo with password, The input device is not a TTY if you are using mintty, try prefixing the command with ‘winpty, Add gitlab-runner to sudoers, Sudo not found docker, Su without password, Linux privilege escalation using sudo rights
Categories: Top 81 Sudo No Tty Present And No Askpass Program Specified
See more here: nhanvietluanvan.com
Sudo Without Password
Introduction:
In the world of Linux and Unix-like operating systems, sudo (short for “superuser do”) is a powerful command that enables users to execute privileged commands as another user, typically the superuser or root. By default, the sudo command requires users to authenticate themselves by entering their password, which adds an extra layer of security. However, in certain situations, it may be necessary to enable sudo without a password prompt. This article aims to provide a comprehensive guide on the topic, explaining when and how to set up sudo without password, as well as addressing some frequently asked questions.
When to Enable Sudo without Password:
There are a few legitimate scenarios where enabling sudo without a password prompt can be justified. The most common use case is for system administrators who run scripts or automated tasks requiring root access. By bypassing the password prompt, these processes can operate seamlessly without any manual intervention.
It’s important to note that enabling sudo without a password should only be done if you fully understand the implications and trust the users granted this privilege. Improper configuration can lead to severe security vulnerabilities, as malicious actors may exploit the unrestricted access.
Enabling Sudo without Password:
To enable sudo without a password prompt, follow these steps:
1. Open the terminal: Launch the terminal on your Linux or Unix-like system, as sudo configurations require administrative access.
2. Edit the sudoers file: Execute the following command to open the sudoers file in the default text editor (usually nano):
“`shell
sudo visudo
“`
3. Locate the relevant line: Within the sudoers file, find the line that contains the specifications for the user or group you want to enable sudo without password for. It should have a format similar to:
“`shell
%sudo ALL=(ALL:ALL) ALL
“`
4. Modify the line: Add the NOPASSWD tag just before the last word ‘ALL’, ensuring that a whitespace character separates it from the previous entry. The modified line should look like this:
“`shell
%sudo ALL=(ALL:ALL) NOPASSWD: ALL
“`
5. Save and exit: Press Ctrl + X, followed by Y, and then Enter/Return to save the changes and exit the text editor.
6. Test the configuration: Run a command using sudo to ensure that it no longer prompts for a password. For example, executing:
“`shell
sudo ls
“`
If the command runs successfully without requesting a password, then sudo without password has been successfully enabled for the specified user or group.
Frequently Asked Questions (FAQs):
Q1. Can I enable sudo without password for a specific command only?
A1. Yes, it is possible to specify individual commands that can be executed without a password prompt. Replace “ALL” in the sudoers file with the full path of the command you want to allow without a password. For example: `%sudo ALL=(ALL:ALL) NOPASSWD: /bin/ls`
Q2. Can I enable sudo without password for multiple users or groups?
A2. Absolutely! You can grant sudo without password to multiple users or groups by replicating the format mentioned earlier for each user or group.
Q3. How do I revoke sudo without password access for a user or group?
A3. By modifying the sudoers file and removing the NOPASSWD tag from the relevant line, you can revoke sudo without password access. However, caution should be exercised to avoid accidental removal or misconfiguration.
Q4. Are there any security risks associated with enabling sudo without password?
A4. Yes, there are potential security risks when enabling sudo without password. Be cautious when allowing users sudo access without password prompts, as it could lead to unauthorized access or damage caused by malicious activities.
Q5. How can I ensure the security of my Linux system while using sudo without password?
A5. Carefully evaluate the users or groups granted sudo without password access, ensuring they are trustworthy and knowledgeable. Regularly monitor system logs, keep your system up-to-date with security patches, and follow best practices outlined by your Linux distribution.
Conclusion:
Enabling sudo without password can streamline administrative tasks and automation processes. However, it should be used with caution and restricted to trusted users or groups. When granting this privilege, always weigh the security risks against the convenience it provides, and ensure proper monitoring and precautions are in place. By following the guidelines discussed in this comprehensive guide, you can confidently configure sudo without password while maintaining the security of your Linux or Unix-like system.
Add Jenkins To Sudoers
Introduction:
Jenkins is a popular open-source automation server that simplifies the task of building, testing, and deploying software projects. As part of its functionality, Jenkins often needs administrator-level privileges to execute certain commands or scripts that interact with the operating system. By adding Jenkins to the sudoers file, you can grant it the necessary permissions to perform these actions. In this article, we will dive into the details of adding Jenkins to sudoers, exploring the steps involved and addressing frequently asked questions.
Adding Jenkins to sudoers:
To add Jenkins to the sudoers file, follow these steps:
Step 1: Access your terminal or command prompt.
Step 2: Log in as a user with sudo privileges.
Step 3: Open the sudoers file using a text editor. For example, you can use the nano editor with the command:
sudo nano /etc/sudoers
Step 4: Scroll down to the “User privilege specification” section of the file.
Step 5: Add the following line to the file:
jenkins ALL=(ALL) NOPASSWD: ALL
This line allows the user “jenkins” to execute all commands as any user without entering a password prompt. It is vital to ensure that the syntax is correct and that there are no typos, as it may lead to unexpected consequences. Double-check before saving the file.
Step 6: Save the changes and exit the text editor. In nano, press Ctrl+X, then Y, and finally Enter to confirm the changes.
Step 7: Verify the changes by executing a command using sudo with the Jenkins user, for instance:
sudo -u jenkins ls /root
If you can execute this command without being prompted for a password, congratulations, you have successfully added Jenkins to sudoers!
FAQs:
1. Why do I need to add Jenkins to the sudoers file?
By adding Jenkins to the sudoers file, you grant it the necessary permissions to execute administrative commands or scripts via the sudo command. This is crucial for Jenkins to perform tasks such as managing services, accessing system-level resources, or executing specific build or deployment procedures.
2. Can I add Jenkins to sudoers using visudo?
Yes, you can use the visudo command, which is a safer way to edit the sudoers file. By running “sudo visudo” instead of “sudo nano /etc/sudoers,” visudo checks for any syntax errors before saving the file, reducing the risk of breaking sudo functionality.
3. How can I ascertain if Jenkins has sudo privileges?
To verify Jenkins’s sudo privileges, you can create a simple test job in Jenkins that runs a command requiring administrative privileges, such as restarting a service or modifying a system file. If the Jenkins job runs successfully without any password prompts, it indicates that Jenkins has the necessary sudo privileges.
4. Can I add Jenkins to a specific command only?
Yes, you can add Jenkins to the sudoers file for specific commands rather than granting it global superuser privileges for all commands. To do this, modify the sudoers file and specify the command(s) that Jenkins needs to execute with root privileges. For example:
jenkins ALL=(ALL) NOPASSWD: /usr/bin/command1, /usr/bin/command2
With this configuration, Jenkins will have sudo access only for the specified commands, while all other commands will require a password.
5. Are there any security implications of adding Jenkins to sudoers?
Adding Jenkins to the sudoers file does pose some security risks. Since Jenkins operates with elevated privileges, a compromised Jenkins job or a malicious script could potentially cause harm to the system. It is crucial to follow best practices to secure your Jenkins installation, employ strict access controls, and thoroughly review any scripts or commands executed by Jenkins.
Conclusion:
Adding Jenkins to the sudoers file allows you to grant it the necessary permissions to perform administrative tasks smoothly. By following the detailed steps outlined in this article, you can ensure that Jenkins can execute commands with root privileges without requiring a password prompt. However, always exercise caution when configuring sudo access for any user, including Jenkins, and stay vigilant about security practices to minimize potential risks.
Sudo With Password
Introduction:
In the world of Linux and Unix-like operating systems, the sudo command has gained immense popularity as a powerful tool for granting specific users the ability to perform administrative tasks. Sudo, short for “superuser do,” allows designated users to execute commands with the privileges of another user, typically the root user. One crucial aspect of sudo is the use of passwords, which serves as an added layer of security. In this article, we will explore the concept of sudo with password, its advantages, and how it enhances security and privilege management.
Understanding Sudo:
Sudo is a straightforward yet feature-rich command that enables users to execute commands with elevated privileges temporarily. Instead of logging in as the root user, which poses a significant security risk, sudo allows you to perform administrative tasks while maintaining individual user accounts, reducing the likelihood of inadvertent damage to the system.
Advantages of Sudo with Password:
1. Granular Privilege Control: By utilizing sudo, administrators have fine-grained control over the commands users can execute with root privileges. This level of control allows for greater security, as users are restricted to specific tasks and cannot perform unauthorized actions.
2. Traceability: When a command is executed using sudo, a record of the action is logged, detailing which user performed the action and when it was executed. This feature enhances accountability and aids in troubleshooting or auditing activities performed on a system.
3. Reduced Attack Surface: With sudo, you can limit user privileges to only the necessary administrative tasks, reducing the attack surface by minimizing the availability of high-privilege actions. By requiring passwords, you add an additional layer to prevent unauthorized escalation of privileges.
4. Password Expiration and Complexity: Sudo can be configured to adhere to password policies, including password expiration and complexity requirements. This ensures that users regularly update their passwords, mitigating the risk of compromised accounts and granting unauthorized access.
5. Administrator Oversight: The use of passwords in sudo allows administrators to have oversight over privileged actions. Password-based authenticaion, alongside proper logging and monitoring mechanisms, allows administrators to monitor, control, and review actions performed by users with elevated privileges.
Implementing Sudo with Password:
To enable sudo with password protection for users, one should follow these steps:
1. Configure sudoers file: Edit the sudoers file using the visudo command, which ensures proper syntax. Add the line `%sudo ALL=(ALL:ALL) ALL` to grant password-protected sudo access.
2. User assignment: Add users to the sudo group, allowing them to utilize sudo. The appropriate group can be added using the `usermod -aG` command, e.g., `usermod -aG sudo username`.
3. Password verification: By default, sudo requires users to enter their own password to execute commands with elevated privileges. This step ensures that the user is actively authenticated and authorized to perform administrative tasks.
4. Sudo configuration: Sudo can be further configured with options such as password timeout, which specifies for how long the password remains valid, and timestamp_timeout, which determines the period after entering a password within which subsequent sudo commands do not require re-authentication.
Frequently Asked Questions (FAQs):
Q1. Is Sudo the same as logging in as the root user?
A1. No, sudo differs from logging in as the root user. With sudo, users maintain individual accounts and execute privileged commands temporarily, limiting the potential for mistakes or unintended damage.
Q2. Can I use Sudo without entering a password?
A2. While it is technically possible to allow passwordless sudo access, it is strongly discouraged due to security concerns. Requiring a password adds a crucial layer of authentication and access management.
Q3. Can I configure Sudo to prompt for a password only once?
A3. Yes, sudo’s default behavior allows users to execute multiple commands within a configurable timeframe without re-entering their password. The timestamp_timeout option can be customized to meet specific security requirements.
Q4. How can I revoke sudo access for a user?
A4. By removing the user from the sudo group or by modifying the sudoers file, you can revoke sudo access for a particular user.
Q5. Can I restrict sudo access to specific commands?
A5. Yes, sudo allows administrators to precisely control which commands users can execute with elevated privileges. The sudoers file can be edited to limit access to specific commands, directories, or even individual arguments within commands.
Conclusion:
The sudo command, when paired with password authentication, offers administrators a powerful and flexible approach to managing privileges and securing Unix-like systems. By allowing granular control, traceability, and reducing the attack surface, sudo with password enhances both security and the overall management of privileges. Proper configuration and adherence to best practices will help ensure a robust and reliable environment for all users.
Images related to the topic sudo no tty present and no askpass program specified

Found 28 images related to sudo no tty present and no askpass program specified theme
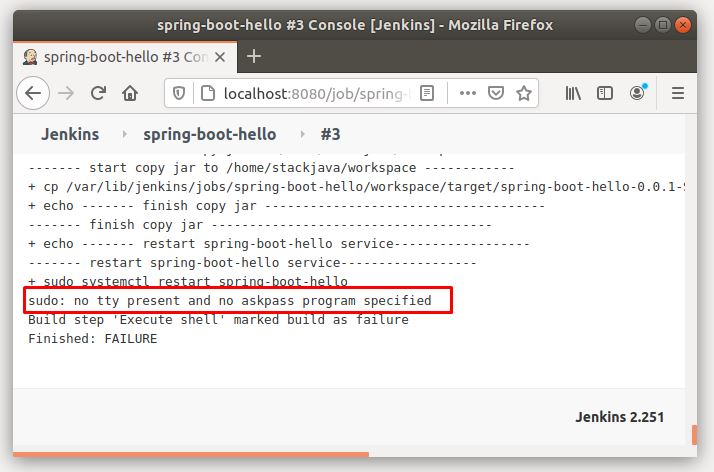

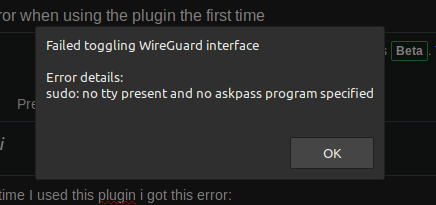





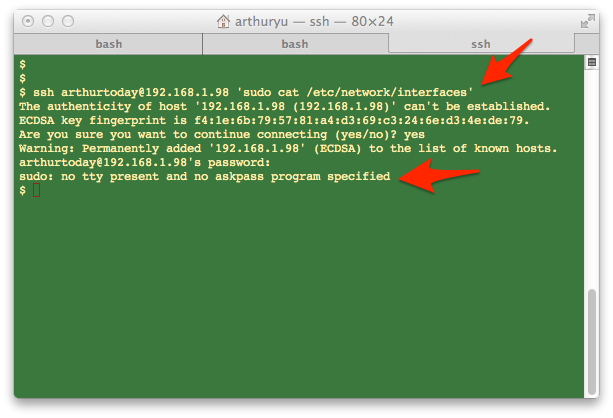
![ERROR] Jenkins Permission denied sudo: no tty present and no askpass program specified Error] Jenkins Permission Denied Sudo: No Tty Present And No Askpass Program Specified](https://images.velog.io/post-images/minholee_93/d079ee20-3e7c-11ea-a9e7-0f7203243739/image.png)

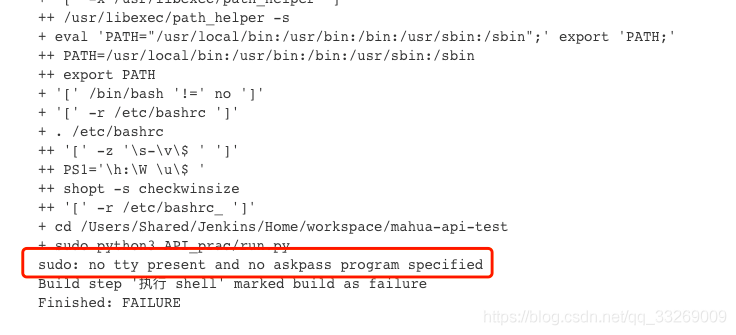
![ERROR] Jenkins Permission denied sudo: no tty present and no askpass program specified Error] Jenkins Permission Denied Sudo: No Tty Present And No Askpass Program Specified](https://images.velog.io/post-images/minholee_93/9de74e30-3e7c-11ea-8364-a532c55080ad/image.png)





Article link: sudo no tty present and no askpass program specified.
Learn more about the topic sudo no tty present and no askpass program specified.
- How to fix ‘sudo: no tty present and no askpass program …
- Linux error ‘sudo: no tty present and no askpass program …
- sudo: no tty present and no askpass program … – Shell Tips!
- “sudo: no tty present and no askpass program specified”.
- Sửa lỗi sudo: no tty present and no askpass program specified
- sudo: no tty present and no askpass program specified
- Sudo: No Tty Present And No Askpass Program Specified
- How to fix the “sudo: no tty present and no askpass program …
- Sudo: No Tty Present and No Askpass … – Position Is Everything
- sorry, you must have a tty to run sudo” (4246335)
See more: https://nhanvietluanvan.com/luat-hoc/