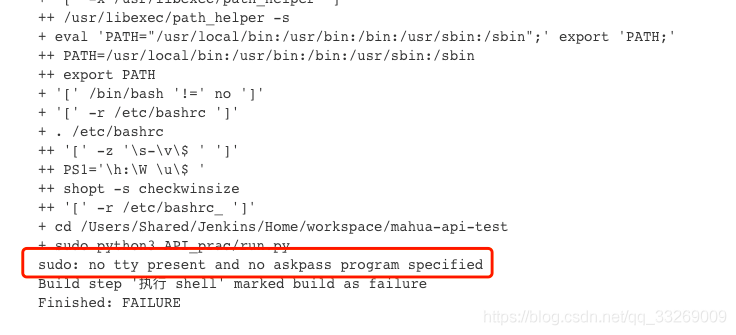
Sudo: No Tty Present And No Askpass Program Specified
When working with the sudo command in Linux, you may come across an error message that says “sudo: no tty present and no askpass program specified.” This error typically occurs when the system cannot find a terminal or input device to read your password from. It can be frustrating, especially if you need to perform administrative tasks using sudo. However, there are several possible causes for this error and corresponding solutions to resolve it.
Possible Causes of the Error:
1. Insufficient Privileges: One common cause of this error is that the user running the sudo command does not have appropriate privileges to execute it. By default, only the root user or users with sudo access are allowed to use this command. If your user account does not have these privileges, you will encounter the error.
2. Misconfigured sudoers File: The sudoers file contains rules and settings that define which users or groups can execute commands with administrative privileges. If this file is not properly configured, it can lead to the mentioned error. It’s important to ensure that the sudoers file is correctly set up to grant necessary privileges to the user encountering the error.
3. Missing or Misconfigured askpass Program: The askpass program is responsible for securely retrieving the user’s password when using sudo. If this program is missing or not properly configured, it can result in the error message. It’s crucial to ensure that the askpass program is available and correctly specified in the system’s configuration.
4. TTY Issues: Sometimes, the error can occur due to discrepancies with the system’s terminal settings or TTY (teletypewriter). If the input device is not recognized as a TTY, it can trigger the error. Therefore, it’s essential to check and resolve any TTY-related issues.
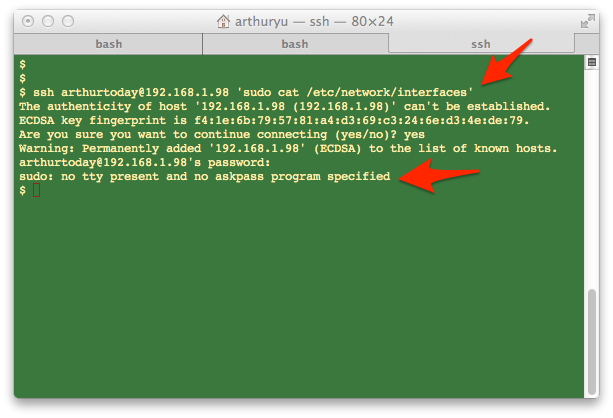
5. Authentication Using SSH Keys: If you are using SSH keys for authentication instead of password-based authentication, it can also trigger the error. In such cases, the system expects a password prompt, but since SSH keys do not require a password, the error is displayed.
Solution 1: Granting Appropriate Privileges
To resolve this error, ensure that your user account has the necessary privileges to use the sudo command. You can do this by either logging in as the root user or adding your account to the sudoers group. Remember that modifying the sudoers file should be done with caution to prevent any security vulnerabilities.
Solution 2: Configuring sudoers File
If the sudoers file is misconfigured, you need to edit it to grant the appropriate privileges to your user account. Use the visudo command, which opens the sudoers file in an editor, to make the necessary changes. Consult the official sudo documentation or seek help from an experienced system administrator to ensure proper configuration.
Solution 3: Enabling the askpass Program
If the askpass program is missing or misconfigured, you should check if it is installed on your system. The name and location of the askpass program may vary depending on your distribution. Once you have located the askpass program, ensure it is properly specified in the sudo configuration file (/etc/sudoers) using the Defaults directive.
Solution 4: Checking for and Fixing TTY Issues
To determine if the error is related to TTY issues, you can try running the command with the ‘winpty’ prefix (e.g., ‘winpty sudo command’) if you are using the mintty terminal in Windows. This can help fix TTY-related problems and allow sudo to work properly.
Solution 5: Using SSH Keys for Authentication
If you are using SSH keys for authentication instead of passwords, you can modify the sudoers file to allow passwordless sudo. Add the following line to the sudoers file using the visudo command:
Replace
Troubleshooting the Error:
Here are some common troubleshooting scenarios related to the error message and their solutions:
1. Sudo without password: If you want to execute sudo commands without entering a password, follow the instructions in Solution 5 above.
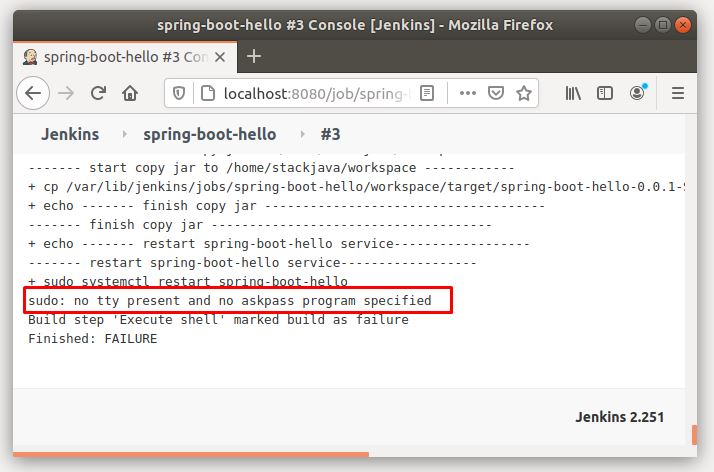
2. Add jenkins to sudoers: To grant Jenkins the necessary sudo privileges, add the following line to the sudoers file using the visudo command:
jenkins ALL=(ALL) NOPASSWD:ALL
This configuration allows the user ‘jenkins’ to execute sudo commands without a password prompt.
3. Sudo with password: If you want to use sudo with a password prompt, ensure that your user account has the appropriate sudo permissions.
4. The input device is not a TTY if you are using mintty, try prefixing the command with ‘winpty’: If you encounter this error while using the mintty terminal in Windows, try using the ‘winpty’ prefix before the sudo command (e.g., ‘winpty sudo command’). This can help resolve TTY-related issues.
5. Add gitlab-runner to sudoers: To grant GitLab Runner sudo privileges, add the following line to the sudoers file using the visudo command:
gitlab-runner ALL=(ALL) NOPASSWD:ALL
This configuration allows the user ‘gitlab-runner’ to execute sudo commands without a password prompt.
6. Sudo not found docker: If you are encountering the error “sudo: not found” while using Docker, it means that the sudo command is not installed in the container. You can either install the sudo package manually or execute commands as the root user using the ‘su’ command.
7. Su without password: If you want to use the ‘su’ command without entering a password, modify the sudoers file to allow passwordless ‘su’ execution. Consult the official sudo documentation or seek help from a knowledgeable system administrator for the specific configuration.
8. Linux privilege escalation using sudo rights: Be cautious when managing sudo privileges as they can lead to privilege escalation vulnerabilities if not properly configured. Always follow security best practices and restrict sudo access to only what is necessary for system administration tasks.
In conclusion, encountering the error message “sudo: no tty present and no askpass program specified” can be frustrating, but with a clear understanding of the possible causes and corresponding solutions, you can successfully resolve this issue. Remember to be cautious when modifying system files and consult official documentation or seek assistance from experienced system administrators if needed.
Devops \U0026 Sysadmins: Sudo: No Tty Present And No Askpass Program Specified (3 Solutions!!)
Keywords searched by users: sudo: no tty present and no askpass program specified Sudo without password, Add jenkins to sudoers, Sudo with password, The input device is not a TTY if you are using mintty, try prefixing the command with ‘winpty, Add gitlab-runner to sudoers, Sudo not found docker, Su without password, Linux privilege escalation using sudo rights
Categories: Top 21 Sudo: No Tty Present And No Askpass Program Specified
See more here: nhanvietluanvan.com
Sudo Without Password
Sudo, a widely used command in Unix-like operating systems, allows users to execute commands with the security privileges of another user. This powerful tool is primarily used to grant limited administrative rights to non-root users for enhanced security. By default, Sudo prompts users to enter their password before executing a command. However, it is also possible to configure Sudo to run commands without prompting for a password. In this article, we will delve into the topic of Sudo without a password, examining the risks, benefits, and best practices when implementing this configuration.
Understanding Sudo Permissions and Advocating for Security
Before exploring the use of Sudo without a password, it is imperative to understand the underlying principle of granting administrative privileges to regular users. By doing so, system administrators can ensure that only trusted individuals have access to high-level operations, mitigating the risk of unauthorized or accidental system modifications. Sudo is designed to enhance security by allowing granular control over these administrative capabilities.
The Risks of Sudo Without Password
Sudo without a password, while offering convenience, poses significant security risks that cannot be overlooked. By eliminating the password prompt, an attacker gaining unauthorized access to a user account automatically obtains unrestricted administrative rights. This can lead to dire consequences such as unauthorized system modifications, data breaches, or even a complete compromise of the entire system. It is critical to understand the consequences of enabling Sudo without a password before implementing it.
Benefits of Sudo Without Password
While we acknowledge the risks, there are scenarios where configuring Sudo without a password can be beneficial. In a specific use case, when running automated scripts or system commands that require administrative privileges, not having to input a password can save time and increase efficiency. Additionally, in controlled environments with strict access controls, where only trusted users have physical or remote access to the system, Sudo without a password can be a useful feature.
Ensuring Secure Implementation
For those scenarios where configuring Sudo without a password is deemed necessary, implementing it securely is of utmost importance. Here are some best practices to consider:
1. Restrict Access: Limit Sudo without a password to specific users or user groups who genuinely require it, ensuring that only trusted individuals have access to this privilege.
2. Regular Auditing: Establish a robust auditing mechanism to closely monitor system activities, keeping track of commands executed without a password. Any suspicious behavior should be investigated promptly.
3. Strong User Authentication: Implement strong user authentication measures, such as multifactor authentication, to mitigate the risks of unauthorized access.
4. Regular Updates and Patches: Keep the system and its software up to date with the latest security patches to prevent potential vulnerabilities from being exploited.
5. Configuration Monitoring: Employ system monitoring and log analysis tools to continuously monitor the Sudo configuration. Unauthorized changes to the configuration should be promptly detected and addressed.
FAQs
1. Is it recommended to enable Sudo without a password?
Enabling Sudo without a password is not recommended in most circumstances due to the significant security risks involved. However, in certain controlled environments with robust access controls, it can be considered.
2. Can Sudo without password increase system vulnerability?
Yes, enabling Sudo without a password increases the system vulnerability since an attacker gaining unauthorized access to a user account automatically obtains unrestricted administrative rights without having to input a password.
3. Are there any alternatives to Sudo without a password?
Alternatives to Sudo without a password include leveraging automation tools, such as Ansible or Puppet, which provide secure ways to execute administrative tasks without requiring manual entry of passwords.
4. How can I balance convenience and security when using Sudo?
To balance convenience and security, it is recommended to evaluate the need for the password-less Sudo configuration on a case-by-case basis. Implement necessary restrictions, strong user authentication, regular auditing, and continuously monitor for any unauthorized changes.
5. Should I regularly review and update Sudo configuration?
Yes, it is crucial to regularly review and update the Sudo configuration to ensure that it aligns with the changing security requirements. Regular updates and patches should be applied to mitigate any potential vulnerabilities.
Conclusion
Enabling Sudo without a password should be approached with caution, only when absolutely necessary, and in controlled environments with robust access controls. Proper evaluation of the risks, combined with strict security measures and ongoing monitoring, can help strike a balance between convenience and security. Overall, it is essential to understand the implications and implement best practices to mitigate the potential risks associated with Sudo without a password. Stay cautious, stay secure!
Add Jenkins To Sudoers
Jenkins is an open-source automation server widely used in the software development community. It offers a variety of plugins and features that enable the automation of tasks such as building, testing, and deploying applications. However, some of these operations may require administrative privileges that normal users do not possess. By adding Jenkins to the sudoers file, we allow it to execute commands with superuser rights, offering a seamless workflow within the Jenkins environment.
To add Jenkins to sudoers, it is crucial to follow specific steps that ensure the process is executed safely and effectively. Here is a detailed guide to adding Jenkins to sudoers:
Step 1: Login as Root User
Firstly, ensure that you have administrative access to the Linux system. Log in as the root user or a user with sudo privileges.
Step 2: Edit sudoers File
To edit the sudoers file, use the visudo command, which safeguards the file against simultaneous edits. Open the terminal and type:
“`
sudo visudo
“`
This will open the sudoers file using the system’s default text editor, usually vi or vim.
Step 3: Locate sudoers Configuration Section
Within the sudoers file, scroll down until you find the section that configures user privileges. It typically begins with a comment stating “User privilege specification.”
Step 4: Add Jenkins User Configuration
Below the aforementioned comment, add the following line to grant specific privileges to Jenkins:
“`
jenkins ALL=(ALL) NOPASSWD: /path/to/your/command
“`
Replace `/path/to/your/command` with the actual path of the command or script that Jenkins needs to execute with administrative privileges.
Step 5: Save and Exit
Save the changes made to the sudoers file and exit the text editor. In vi or vim, press the Esc key, then type `:wq` and hit Enter.
Step 6: Test Configuration
It is crucial to verify if Jenkins can now execute commands with administrative privileges. Restart the Jenkins service using the following command:
“`
sudo systemctl restart jenkins
“`
After the service restarts, run a test build or deployment job that requires elevated privileges to confirm whether the configuration was successful.
Now let’s address some frequently asked questions about adding Jenkins to sudoers:
Q1: What are the potential risks of adding Jenkins to sudoers?
A1: Granting Jenkins administrative privileges can be risky if not managed properly. It is important to ensure that only trusted Jenkins jobs have access to sudo privileges to prevent malicious code execution.
Q2: Can I add Jenkins to sudoers without using visudo?
A2: While it is technically possible to edit the sudoers file directly using a text editor, it is highly recommended to use visudo instead. This command prevents syntactic errors and ensures the integrity of the sudoers file.
Q3: How can I revoke sudo privileges from Jenkins?
A3: To remove Jenkins from the sudoers file, open the sudoers file using visudo and delete the line added during the configuration process. Save the file and exit. Afterward, Jenkins will no longer have administrative privileges.
Q4: Can I grant Jenkins specific command privileges instead of all administrative rights?
A4: Yes, you can specify individual commands or scripts that Jenkins is allowed to execute with sudo privileges. Modify the configuration line in the sudoers file to include the specific command path, granting only the required permissions.
Q5: Will adding Jenkins to sudoers impact the overall system security?
A5: Adding Jenkins to sudoers can present security risks if not carefully managed. Ensure that only necessary privileges are granted and regularly review and monitor Jenkins jobs to prevent unauthorized access or malicious activity.
In conclusion, adding Jenkins to sudoers is a crucial step for enabling smooth integration with Linux systems. By following the outlined steps, you can grant specific administrative privileges to Jenkins, facilitating automated software development and deployment processes. However, it is important to exercise caution and review permissions regularly to maintain system security.
Images related to the topic sudo: no tty present and no askpass program specified

Found 17 images related to sudo: no tty present and no askpass program specified theme











Article link: sudo: no tty present and no askpass program specified.
Learn more about the topic sudo: no tty present and no askpass program specified.
- How to fix ‘sudo: no tty present and no askpass program …
- Linux error ‘sudo: no tty present and no askpass program …
- sudo: no tty present and no askpass program … – Shell Tips!
- “sudo: no tty present and no askpass program specified”.
- Sửa lỗi sudo: no tty present and no askpass program specified
- sudo: no tty present and no askpass program specified
- Sudo: No Tty Present And No Askpass Program Specified
- Sudo: No Tty Present and No Askpass … – Position Is Everything
- sudo: no tty present and no askpass program … – Lightrun
- How to fix the “sudo: no tty present and no askpass program …
See more: https://nhanvietluanvan.com/luat-hoc/