X509 Certificate Signed By Unknown Authority
Overview of X509 Certificates
X509 certificates serve as a crucial aspect of secure communication within the realm of computer networks and the internet. These digital certificates are used to verify the authenticity of entities, such as websites, servers, or individuals, in order to establish trust and ensure secure communication. They rely on a Public Key Infrastructure (PKI) model, which involves a hierarchical structure of Certificate Authorities (CAs) to issue, revoke, and manage X509 certificates.
Explanation of Certificate Authorities (CAs)
Certificate Authorities are trusted entities responsible for issuing digital certificates. They play a vital role in validating the identity and authenticity of the entities requesting the certificates. CAs are typically well-known and audited organizations, providing a trusted third-party verification of an entity’s credentials. By signing an X509 certificate with their private key, CAs confirm that the entity possesses the corresponding private key and can be trusted.
Importance of a Valid CA Signature
A valid CA signature on an X509 certificate is crucial to establish trust between entities. When a certificate is signed by a trusted CA, it assures the recipient that the identity of the entity has been verified and the communication is secure. The recipient can verify the certificate’s authenticity by validating the CA’s digital signature using the public key provided by the CA.
Risks Associated with Unknown Authority Signatures
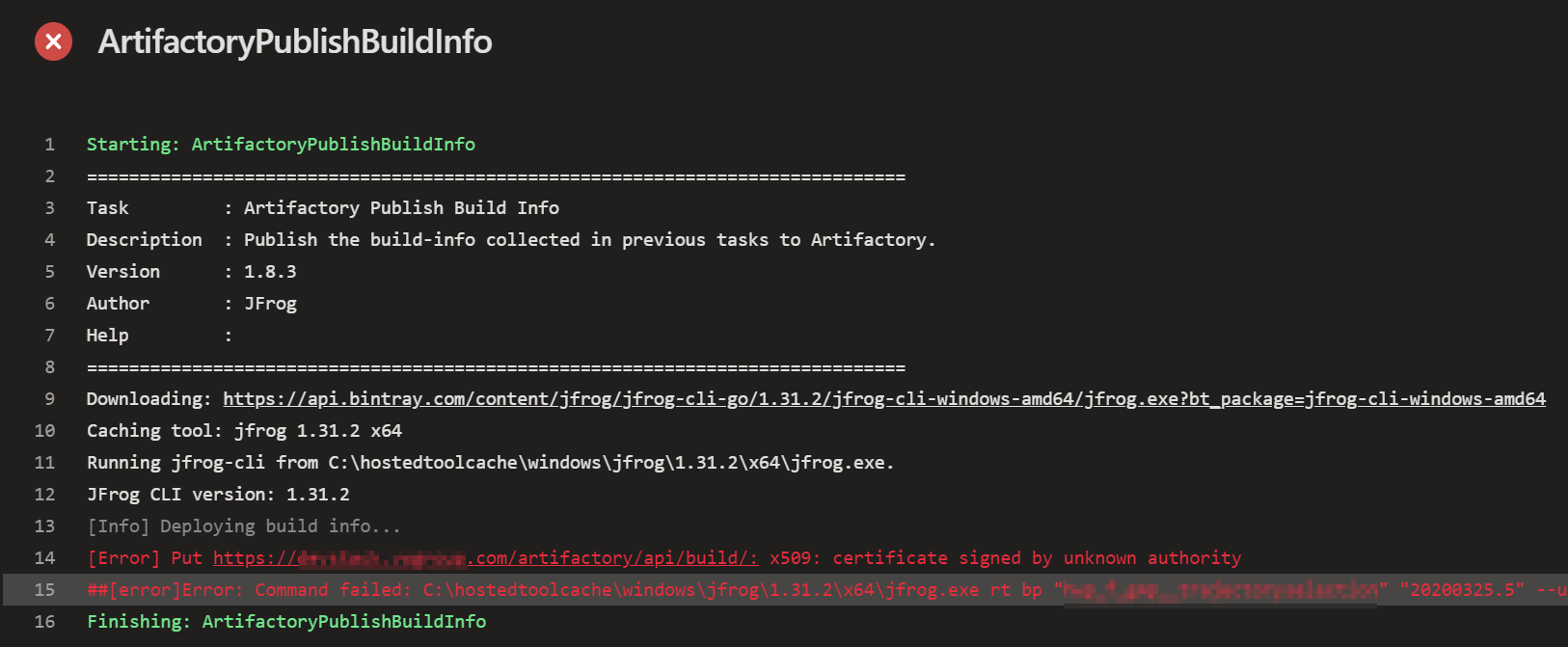
An X509 certificate signed by an unknown authority raises red flags and poses potential risks. It indicates that the certificate’s authenticity cannot be verified through a trusted CA. This situation can occur due to various reasons, ranging from misconfiguration to malicious actions, and it undermines the assurance of secure communication. Ignoring or blindly trusting an X509 certificate signed by an unknown authority puts users at risk of man-in-the-middle attacks, data breaches, or other security vulnerabilities.
How an Unknown Authority Signature Occurs
An unknown authority signature occurs when an X509 certificate is signed by an entity which is not recognized as a trusted CA by the recipient. This happens when the certificate is issued by a CA that is either not part of the recipient’s trusted CA list or is self-signed (signed using the entity’s own private key). The recipient’s software, web browser, or system flags such certificates as potentially untrustworthy unless specific actions are taken to verify their authenticity.
Common Causes of Unknown Authority Signatures
Unknown authority signatures can arise due to several reasons, including:
1. Self-signed certificates: Self-signed certificates are those signed by the entity itself rather than a recognized CA. Although self-signed certificates can be used for internal purposes, they are not considered trusted by publicly accessible systems.
2. Misconfigured or outdated CA lists: Systems maintaining a list of trusted CAs may encounter issues if the list is outdated, incorrectly configured, or lacks the necessary updates. This can result in unrecognized CAs and generate unknown authority signatures.
Potential Implications of Trusting Unknown Authority Signatures
Trusting an X509 certificate signed by an unknown authority has significant implications for security and privacy. It opens the door for potential malicious activities, as the authenticity and trustworthiness of the certificate cannot be adequately verified. An attacker could perform man-in-the-middle attacks, intercept sensitive data, or impersonate a trusted entity, putting the communication at risk.
Steps to Mitigate Risk when Encountering Unknown Authority Signatures
When encountering an X509 certificate signed by an unknown authority, certain steps can be taken to mitigate the associated risks:
1. Do not blindly trust: Exercise caution and do not trust certificates signed by unknown authorities without proper verification. Treat them as potentially untrustworthy.
2. Verify the entity manually: If the situation allows, attempt to verify the entity’s identity through alternative means, such as contacting them directly or cross-referencing with known trusted sources.
3. Investigate the certificate’s chain of trust: Examine the certificate’s chain of trust to determine the authority that signed it. If it can be traced back to a trusted CA, the certificate may still be valid.
Best Practices for Trusted Certificate Management
To maintain a secure environment and reduce the likelihood of encountering X509 certificates signed by unknown authorities, follow these best practices for trusted certificate management:
1. Regularly update and maintain the list of trusted CAs: Keep the list of trusted CAs up to date and ensure that it aligns with industry standards and regulations.
2. Implement certificate revocation checks: Enable certificate revocation checks to identify revoked certificates and prevent their usage within the system.
3. Utilize certificate pinning: Consider implementing certificate pinning, which restricts trust to specific certificates or public keys.
4. Regularly check for certificate expiration: Regularly monitor certificates for expiration dates to avoid encountering expired certificates signed by unknown authorities.
5. Employ certificate transparency logs: Utilize certificate transparency logs to track and investigate certificate issuance, and detect potential anomalies.
FAQs:
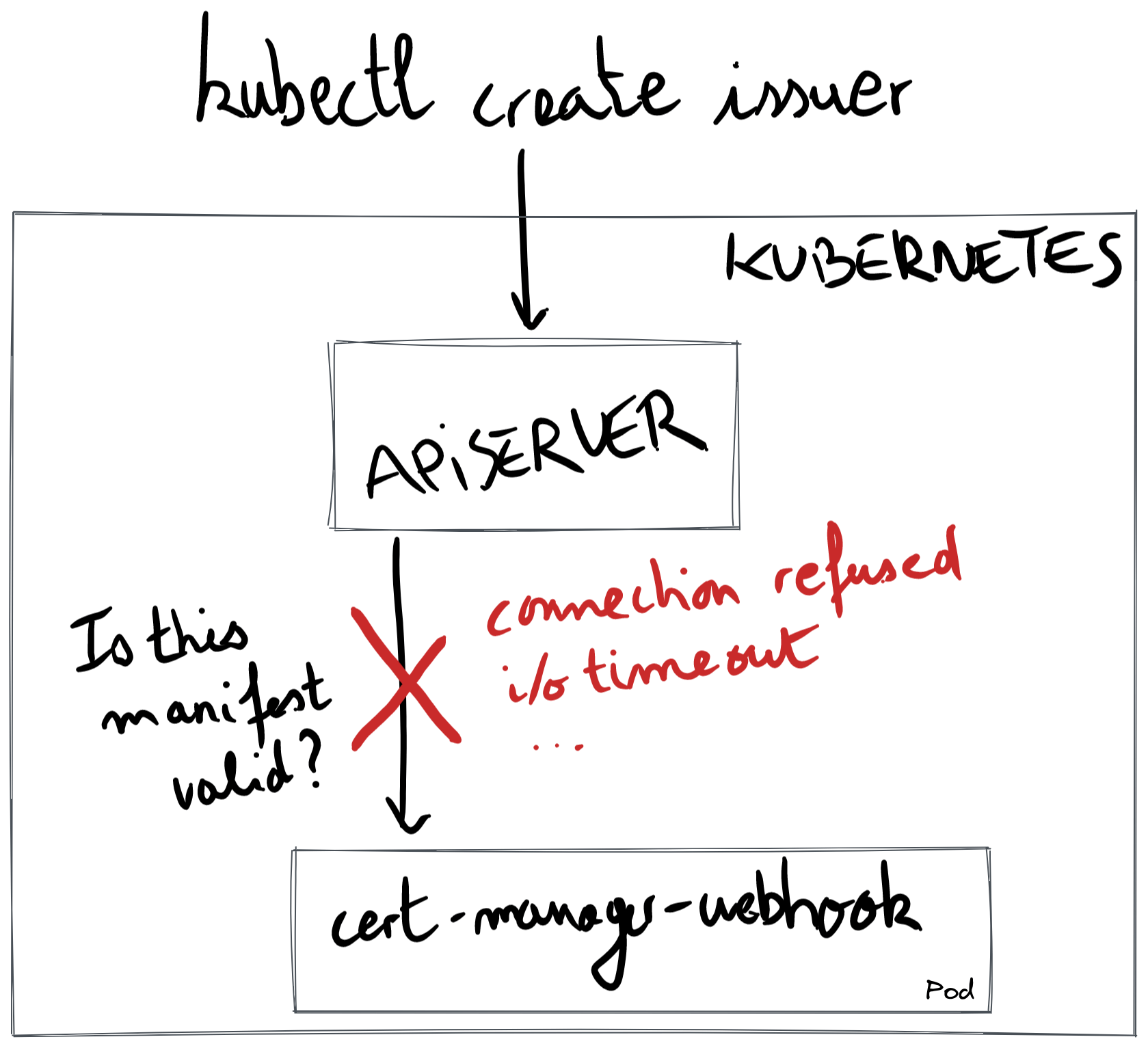
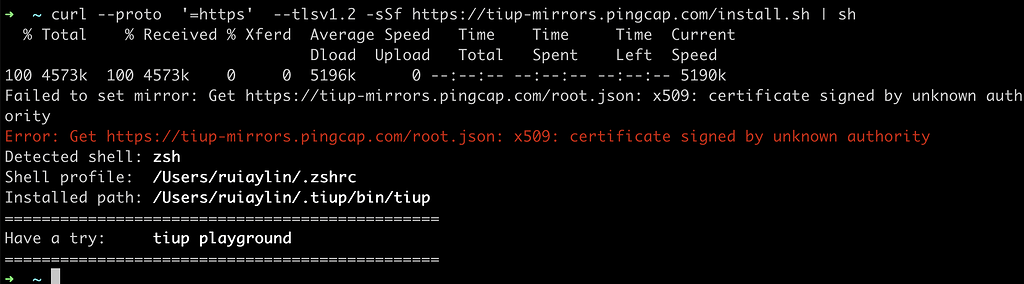
Q: I encountered the error message “kubernetes pull image x509: certificate signed by unknown authority.” What does it mean?
A: This error message suggests that the Kubernetes system encountered an X509 certificate signed by an unknown authority during an attempt to pull an image. It indicates a potential security risk, and further steps should be taken to verify the certificate’s authenticity.
Q: How can I connect to the server when encountering the error “Unable to connect to the server: x509: certificate signed by unknown authority”?
A: When encountering this error, it is essential to verify the certificate chain of trust and ensure the authenticity of the certificate. If possible, consult the server administrator or a trusted expert to assist with resolving the issue.
Q: What should I do if an X509 certificate has expired or is not yet valid?
A: If you encounter an expired or not yet valid X509 certificate, exercise caution and do not trust it. Contact the entity or administrator responsible for the certificate to address the issue promptly.
In conclusion, an X509 certificate signed by an unknown authority poses significant risks to the security and integrity of communication. It is crucial to exercise caution, verify certificates’ authenticity, and follow best practices for trusted certificate management to mitigate these risks effectively. Stay vigilant and prioritize the security of your systems to protect against potential threats associated with unknown authority signatures.
Generate X.509 Certificates Using Openssl
Keywords searched by users: x509 certificate signed by unknown authority kubernetes pull image x509: certificate signed by unknown authority, Unable to connect to the server: x509: certificate signed by unknown authority, X509 certificate, Tls: failed to verify certificate: x509: certificate signed by unknown authority, X509: certificate has expired or is not yet valid, Unable to connect to the server: x509: certificate signed by unknown authority Rancher, Get https registry-1 docker io v2 x509: certificate signed by unknown authority, Unable to connect to the server: x509: certificate is valid
Categories: Top 90 X509 Certificate Signed By Unknown Authority
See more here: nhanvietluanvan.com
Kubernetes Pull Image X509: Certificate Signed By Unknown Authority
Introduction:
Kubernetes is a powerful open-source container orchestration platform that allows developers to automate the deployment, scaling, and management of containerized applications. It simplifies the container management process, making it easier to deploy applications consistently across various environments. However, like any complex system, Kubernetes has its own set of challenges, one of which is the “x509: certificate signed by unknown authority” error when pulling images. In this article, we will delve into the details of this error and explore possible solutions.
Understanding the Error:
When deploying containers on Kubernetes, it is common to pull container images from private or public registries. A registry is a place where container images are stored and can be accessed by Kubernetes to create containers. To ensure the integrity and security of these images, registry servers use SSL/TLS certificates to encrypt the communication between the client (Kubernetes) and the server (registry). These certificates are signed by a recognized certificate authority (CA).
The “x509: certificate signed by unknown authority” error occurs when Kubernetes tries to pull an image from a registry using SSL/TLS encryption, but it cannot verify the authenticity of the certificate presented by the registry server. This happens when the certificate is either self-signed or signed by a CA that Kubernetes does not trust or recognize.
Why does this error occur?
Kubernetes, by default, trusts only a predefined set of certificate authorities to maintain a secure environment. This is to prevent any unauthorized servers from masquerading as legitimate registries and potentially compromising the system’s security. When a certificate signed by an unknown authority is encountered, Kubernetes throws an error to ensure that the image being pulled is from a trusted and secure source.
Possible Solutions:
1. Add a Trusted Certificate Authority:
To resolve this issue, the first approach is to add the root certificate from the unknown authority as a trusted certificate authority in the Kubernetes cluster. This can be done by distributing the CA certificate to all Kubernetes nodes and updating the kubelet configuration to trust this CA. However, this approach may not be feasible or scalable if you are dealing with multiple registry servers or frequently changing certificates.
2. Disable SSL Verification:
Although not recommended for production environments, you can temporarily disable SSL verification to allow Kubernetes to pull the image without checking the certificate authority. This can be achieved by adding the `–insecure-registry` flag to the Docker daemon configuration on each Kubernetes node. However, it is important to note that this solution compromises the security of the communication and should only be used in controlled environments.
3. Use a Trusted Certificate:
Another approach is to replace the unknown certificate with a trusted one. This involves acquiring a certificate from a recognized CA, signing it using their private key, and configuring the registry server to present the new certificate to Kubernetes. This solution ensures secure communication and eliminates the need to modify Kubernetes configurations or compromise the SSL/TLS verification process.
FAQs:
Q: Why should I fix the “x509: certificate signed by unknown authority” error?
A: The error occurs to maintain the integrity and security of container images. Ensuring that the images come from trusted and verified sources reduces the risk of deploying containers with malicious or compromised code.
Q: Can I resolve the error by adding the CA certificate to just one node?
A: No, adding the CA certificate to only one node will not be sufficient. The certificate verification is done at the kubelet level, which is replicated across all nodes in the cluster. Therefore, the CA certificate must be added to every node in the cluster.
Q: Is disabling SSL verification permanently a good solution?
A: No, disabling SSL verification should only be done temporarily and in controlled environments where security risks are appropriately mitigated. In a production environment, it is crucial to maintain the security and integrity of communication between Kubernetes and registry servers.
Q: Can I use a self-signed certificate instead of a certificate issued by a recognized CA?
A: Yes, you can use a self-signed certificate as long as you trust the certificate and are confident it is secure. However, Kubernetes must be configured to trust this self-signed certificate by adding it to the trusted certificate authorities.
Conclusion:
The “x509: certificate signed by unknown authority” error can be a roadblock in pulling container images from registries. However, by understanding the nature of the error and exploring potential solutions, you can overcome this challenge. It is important to prioritize security and ensure that only trusted certificates are used to establish secure communication between Kubernetes and the registry servers.
Unable To Connect To The Server: X509: Certificate Signed By Unknown Authority
In today’s digital age, where online communication plays a vital role, encountering errors while connecting to a server can be frustrating. One such error that users commonly face is “Unable to connect to the server: x509: certificate signed by unknown authority.” This error message indicates a problem with the security certificate of the server, causing the connection to fail. In this article, we will explore what this error means, its causes, and provide solutions to troubleshoot and resolve it.
Understanding the Error:
When you attempt to establish a secure connection to a server, your computer checks the digital certificate associated with that server. This certificate confirms the server’s identity and ensures that the communication between your device and the server is secure. It is issued by a trusted authority, known as a Certificate Authority (CA), to verify the legitimacy of the server.
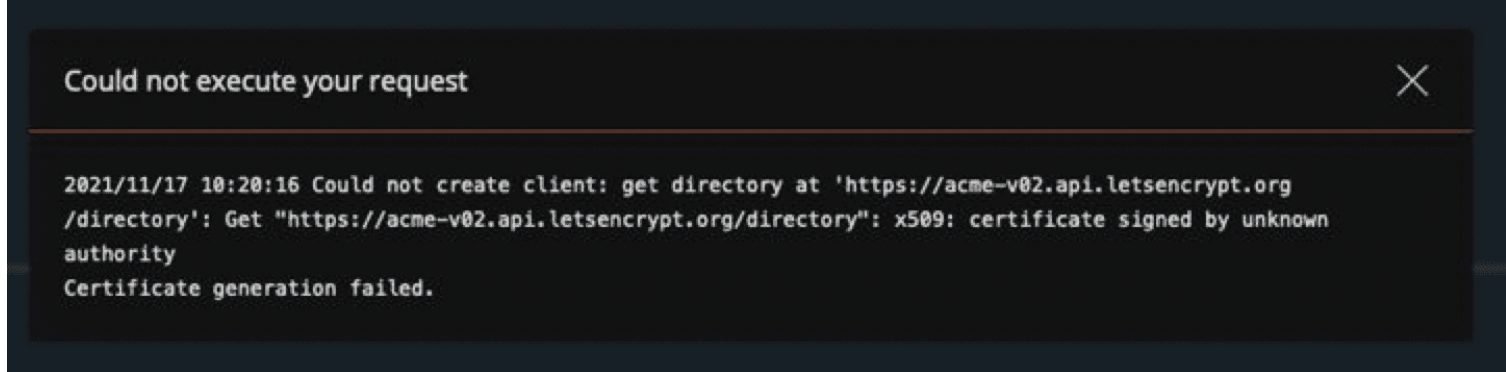
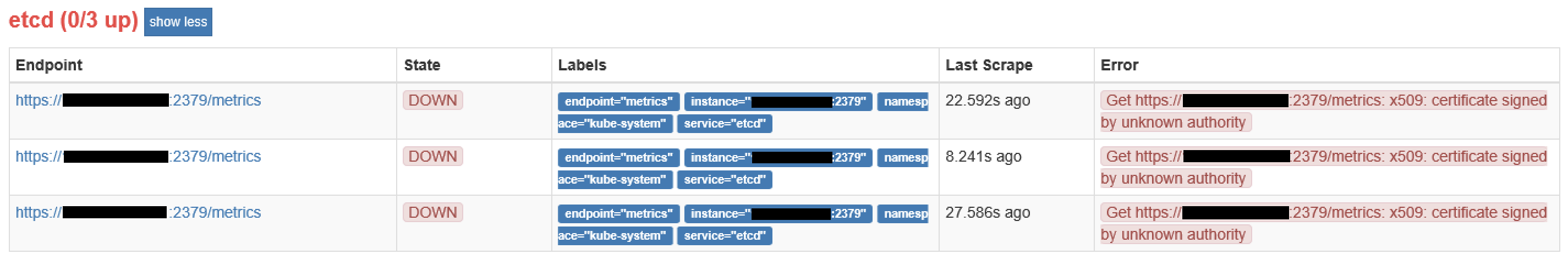
The error message “Unable to connect to the server: x509: certificate signed by unknown authority” indicates that the server’s certificate was not signed by any recognized or trusted CA. This implies that the certificate is self-signed or signed by an authority that your device does not recognize.
Causes of the Error:
Several factors can lead to the occurrence of this error. Let’s discuss some common causes:
1. Self-signed Certificates: Self-signed certificates are created by the server itself, rather than a recognized CA. While they provide encryption, they lack validation from a trusted authority. As a result, when your device attempts to establish a secure connection, it flags the certificate as untrusted and throws the error.
2. Expired or Revoked Certificates: Certificates have an expiration date, and once they expire, they are considered invalid. Similarly, if a certificate is revoked due to a security breach or compromise, it becomes untrusted. In both cases, your device will display the error message to protect you from connecting to potentially insecure servers.
3. Intermediate Certificate Missing: Sometimes, a server’s certificate is part of a chain, where multiple intermediate certificates are used to establish trust between the server’s certificate and the root CA. If any of the intermediate certificates in the chain are missing or not installed, it will result in the error.
4. Misconfigured System Time: Certificates are time-dependent and have a validity period. If your device’s system time is incorrect, it may result in the error, as the certificate provided by the server may appear expired or not yet valid.
Solutions to Resolve the Error:
Now that we understand the potential causes, it’s time to explore various troubleshooting steps to fix the “Unable to connect to the server: x509: certificate signed by unknown authority” error. Here are some solutions:
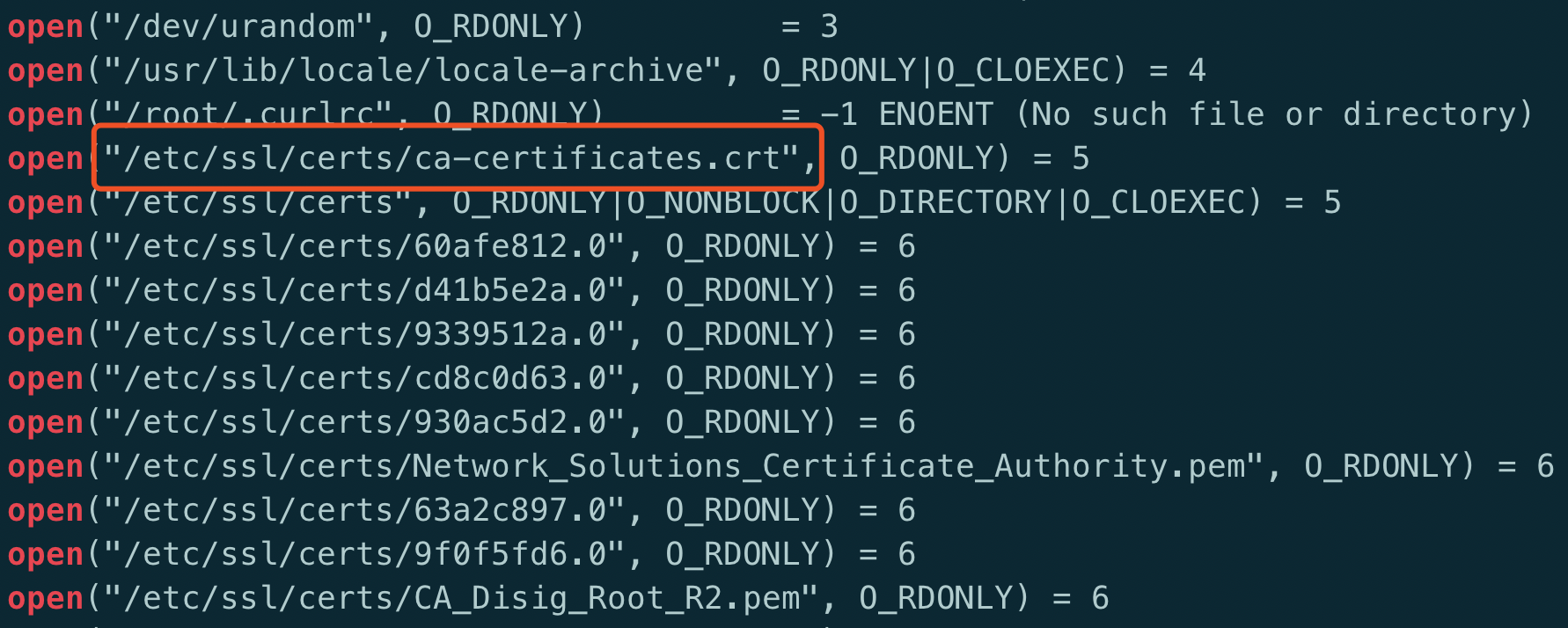
1. Import the Root CA: To establish trust with a self-signed certificate or a certificate signed by an unknown authority, you can manually import the root CA into your device’s trusted certificate store. This will allow your device to recognize and trust the server’s certificate.
2. Verify Certificate Chain: Ensure that the server’s certificate chain is complete and properly configured. Check if the intermediate certificates are provided correctly and, if not, contact the server administrator to get the missing intermediate certificates.
3. Update Operating System and Applications: Keeping your device’s operating system and applications up to date is crucial for security. Updates often include trusted root CA certificates, so updating your system can resolve the issue by adding the missing or outdated certificates.
4. Check System Time Settings: Verify that your device’s system time is accurate. Ensure that it is automatically syncing with a trusted time server. Correcting the system time can resolve the error caused by expired or not yet valid certificates.
FAQs:
Q: Is the “x509: certificate signed by unknown authority” error a serious security concern?
A: While the error signifies a potential security concern, it doesn’t necessarily indicate a direct attack. It primarily highlights a trust issue with the server’s certificate.
Q: Can I bypass this error and still establish a connection?
A: It is possible to bypass this error, but it is strongly recommended not to proceed, as doing so may expose your communication to potential risks or malware attacks.
Q: I’m encountering this error on my web browser. What should I do?
A: Clearing your browser caches and cookies can sometimes resolve the error. Additionally, ensure that your browser is up to date and there are no extensions or plugins interfering with the connection.
Q: Are self-signed certificates always untrustworthy?
A: Self-signed certificates are not inherently untrustworthy, but they lack validation from recognized CAs. Their use is generally limited to internal or testing purposes and is not recommended for public-facing websites.
In conclusion, the “Unable to connect to the server: x509: certificate signed by unknown authority” error occurs when there is an issue with the server’s security certificate. Understanding the error’s causes and implementing the mentioned solutions can help you troubleshoot and resolve the issue, ensuring a secure connection. Always prioritize caution and avoid bypassing the error without taking appropriate security measures.
Images related to the topic x509 certificate signed by unknown authority

Found 42 images related to x509 certificate signed by unknown authority theme


































Article link: x509 certificate signed by unknown authority.
Learn more about the topic x509 certificate signed by unknown authority.
- x.509 certificate là gì? Cách khắc phục lỗi x.509 … – SSL.VN
- “docker pull” certificate signed by unknown authority
- Directamin – x509: certificate signed by unknown authority
- X509 Certificate Signed by Unknown Authority: Causes & Fixes
- ERROR: x509: certificate signed by unknown authority error is …
- How to Fix the “X.509 Certificate Signed by Unknown Authority …
- certificate signed by unknown authority | Bamboo | Atlassian …
- Docker Private Registry: x509: certificate signed by unknown …
See more: https://nhanvietluanvan.com/luat-hoc