X509: Certificate Signed By Unknown Authority
In today’s digital age, securing online communications and ensuring the confidentiality and integrity of data have become paramount. X509 certificates play a vital role in establishing trust between parties involved in internet transactions. However, encountering a certificate signed by an unknown authority can raise concerns about the authenticity and security of the connection. In this article, we will explore what an X509 certificate is, why a certificate signed by an unknown authority is a concern, common causes for encountering such a certificate, potential risks and consequences, methods to verify the legitimacy of an X509 certificate, steps to take when encountering one, and best practices to prevent the use of certificates signed by unknown authorities.
What is an X509 certificate?
An X509 certificate is a digital document that confirms the authenticity of a website, application, or server and its associated public key. It follows the X509 standard, which specifies the format and structure for these certificates. X509 certificates are widely used to ensure secure communications through technologies such as SSL/TLS (Secure Sockets Layer/Transport Layer Security) and are essential for establishing trust in online transactions.
Why is a certificate signed by an unknown authority a concern?
A certificate signed by an unknown authority raises concerns because it indicates that the institution or individual issuing the certificate is not recognized or trusted by the client’s system. When a website or server presents an X509 certificate, the client system checks whether the certificate is issued by a trusted authority known as a Certificate Authority (CA). If the certificate is not signed by a recognized CA, it is deemed untrusted, and the connection may be considered insecure.
Common causes for a certificate signed by an unknown authority
1. Self-Signed Certificates: Self-signed certificates are those issued by the owner of the website or server itself rather than a recognized CA. While they provide cryptographic security measures, they lack the trust factor associated with CA-signed certificates.
2. Custom or In-house CAs: Organizations may have their own internal Certificate Authorities to issue certificates for their internal infrastructure. However, if the client’s system does not recognize the CA, it will treat the certificate as being signed by an unknown authority.
3. Expired or Invalid Certificates: Certificates have an expiration date, and if not renewed in time, they become invalid. The client system will reject such certificates as they may no longer guarantee the security of the connection.
Potential risks and consequences of using a certificate signed by an unknown authority
1. Man-in-the-Middle Attacks: When a client accepts a certificate signed by an unknown authority, it opens the possibility of a man-in-the-middle attack. An attacker could intercept and manipulate the communication, posing as the legitimate server, and gain unauthorized access to sensitive information.
2. Data Breaches and Unauthorized Access: Accepting certificates from unknown authorities increases the risk of data breaches, as it undermines the integrity and security of the communication channel. Attackers can exploit this vulnerability to gain unauthorized access to the server or inject malicious code.
3. Loss of Customer Trust: If customers or users detect that a website or application is using certificates from unknown authorities, they may lose trust and choose not to engage in any transactions, potentially impacting the business’s reputation and revenue.
Methods to verify the legitimacy of an X509 certificate
1. Certificate Authority (CA) Verification: Check if the certificate is signed by a trusted and recognized CA. Most operating systems and web browsers have a predefined list of trusted CAs.
2. Certificate Revocation Lists (CRLs) and Online Certificate Status Protocol (OCSP): Verify whether the certificate has been revoked by checking the CRL, which lists certificates that are no longer valid. OCSP provides real-time validation of the certificate’s status.
3. Certificate Transparency (CT) Logs: CT is a publicly auditable framework that logs certificates, making it possible to verify their legitimacy. There are online tools available where you can check if a certificate is logged in CT logs.
Steps to take when encountering a certificate signed by an unknown authority
1. Understand the Risks: Assess the potential risks involved in establishing a connection with a website or server using such a certificate. Determine the sensitivity of the data being exchanged and the importance of the connection.
2. Verify the Certificate: Perform checks to ensure the legitimacy of the certificate. Consult the certificate details and investigate whether it is self-signed, expired, or issued by an unrecognized CA.
3. Contact the Website or Server Owner: Reach out to the administrator or owner of the website or server to clarify the authenticity and security of the certificate. They may provide explanations or alternative methods for secure communication.
Best practices to prevent the use of certificates signed by unknown authorities
1. Use Certificates from Trusted CAs: Obtain certificates from recognized and trusted Certificate Authorities to establish secure connections and gain the confidence of clients and users.
2. Regularly Renew and Update Certificates: Ensure timely renewal and updating of certificates before they expire to avoid potential disruptions in connectivity and prevent the use of expired certificates.
3. Monitor and Respond to Certificate Related Alerts: Implement a monitoring system that alerts administrators of certificate-related issues, such as impending expirations or revoked certificates, and quickly respond to them.
Conclusion
X509 certificates serve as the backbone of secure online communications, establishing trust between parties. However, encountering a certificate signed by an unknown authority raises concerns about the authenticity and security of the connection. It is essential to verify the legitimacy of certificates, use those issued by trusted CAs, and follow best practices to prevent potential risks and consequences. By prioritizing secure communication, organizations can safeguard sensitive data and maintain the trust of their customers and users.
FAQs
Q1. I’m encountering the error “X509: certificate signed by an unknown authority” when trying to pull images in Kubernetes. What should I do?
A1. This error occurs when the Kubernetes cluster encounters a certificate that is not signed by a trusted authority. To resolve this, you can try adding the certificate to the trust store or configuring your Kubernetes cluster to trust the specific CA that signed the certificate.
Q2. When I try to connect to the server, I receive the error “Unable to connect to the server: x509: certificate signed by unknown authority.” How can I solve this issue?
A2. This error usually indicates that the server’s certificate is not recognized by the client’s system. To address this, you can examine the certificate details, verify its legitimacy, and consider adding the certificate’s CA to the trusted authorities of the client system.
Q3. What should I do if I encounter the error “X509: certificate has expired or is not yet valid”?
A3. This error suggests that the certificate’s validity period has either expired or not yet started. To rectify this, ensure that the server presents a valid and up-to-date certificate that falls within its designated validity period.
Q4. What steps can I take to resolve the error “Unable to connect to the server: x509: certificate signed by unknown authority Rancher”?
A4. If you’re encountering this error with Rancher, it means that the Rancher server’s certificate is not recognized as trusted by the client’s system. To resolve this, verify the certificate’s legitimacy, add the certificate’s CA to the trusted authorities, or check if your Rancher installation requires specific configuration steps to establish trust.
Q5. I receive the error “Get https://registry-1.docker.io/v2/: x509: certificate signed by unknown authority.” How do I fix this issue?
A5. This error indicates that the client system does not recognize the certificate authority that signed the Docker registry’s certificate. To resolve this, you can investigate the certificate, verify its status, and consider adding the specific CA to the trusted authorities of the client system.
Q6. What does the error message “Unable to connect to the server: x509: certificate is valid x509: certificate signed by unknown authority” mean?
A6. This error message suggests that while the certificate itself is valid, it was signed by an unrecognized authority. To overcome this, you can take steps to verify the certificate and add the relevant CA to the trusted authorities of the client system.
Generate X.509 Certificates Using Openssl
Keywords searched by users: x509: certificate signed by unknown authority kubernetes pull image x509: certificate signed by unknown authority, Unable to connect to the server: x509: certificate signed by unknown authority, X509 certificate, Tls: failed to verify certificate: x509: certificate signed by unknown authority, X509: certificate has expired or is not yet valid, Unable to connect to the server: x509: certificate signed by unknown authority Rancher, Get https registry-1 docker io v2 x509: certificate signed by unknown authority, Unable to connect to the server: x509: certificate is valid
Categories: Top 88 X509: Certificate Signed By Unknown Authority
See more here: nhanvietluanvan.com
Kubernetes Pull Image X509: Certificate Signed By Unknown Authority
Introduction:
Kubernetes is an open-source container orchestration platform that automates the deployment, scaling, and management of containerized applications. It allows developers to easily deploy and manage applications in a cluster of containers, providing scalability, high availability, and resource efficiency. However, working with Kubernetes can sometimes lead to challenges, such as encountering errors like “x509: certificate signed by unknown authority” when pulling container images. In this article, we will explore the meaning of this error and discuss possible solutions.
Understanding the Error:
When trying to pull a container image from a registry, Kubernetes uses Secure Sockets Layer (SSL) certificates to establish a secure connection between the various components involved. The “x509: certificate signed by unknown authority” error occurs when Kubernetes encounters an SSL certificate that it does not trust or doesn’t recognize the authority that signed it. This could happen due to several reasons, such as expired or self-signed certificates or misconfigured certificate authorities.
Possible Causes and Solutions:
1. Expired Certificates:
Sometimes, SSL certificates have an expiration date, and if the certificate used by the registry has expired, Kubernetes will fail to validate it. To resolve this issue, the certificate needs to be renewed or replaced with a valid one. The renewal process may vary depending on the registry provider, so consult their documentation for detailed instructions.
2. Self-Signed Certificates:
A self-signed certificate is signed by its owner and is not verified by any trusted third-party. By default, Kubernetes only trusts certificates signed by well-known certificate authorities. When using a self-signed certificate, Kubernetes will raise the “x509: certificate signed by unknown authority” error. To resolve this, you need to add the self-signed certificate to the trusted certificate authority list on the nodes running your Kubernetes cluster.
3. Misconfigured Certificate Authorities:
If the SSL certificate used by the registry is signed by a known authority, but Kubernetes fails to recognize it, it could be due to misconfigured certificate authorities on the nodes. Check the certificate chain to ensure that the correct intermediate and root certificates are in place. If any intermediate certificates are missing, Kubernetes won’t be able to verify the SSL certificate and will raise the error.
To fix this, update the trusted certificate store on the nodes with the correct intermediate and root certificates. Consult the official documentation of your operating system or certificate authority for instructions on how to update the certificate authorities.
Frequently Asked Questions (FAQs):
Q1. Why am I getting the “x509: certificate signed by unknown authority” error?
This error occurs when Kubernetes encounters an SSL certificate it doesn’t trust or is signed by an unspecified authority. It can happen due to expired certificates, self-signed certificates, or misconfigured certificate authorities.
Q2. How can I check if my SSL certificate is expired?
You can use the openssl command-line tool to check the expiration date of an SSL certificate. Run the following command:
openssl x509 -enddate -noout -in path/to/certificate.crt
Q3. How do I renew an expired certificate?
To renew a certificate, you need to contact the certificate authority or the person responsible for managing certificates in your organization. Provide them with the necessary details and follow their instructions to renew the certificate.
Q4. Can I disable SSL certificate verification in Kubernetes?
While disabling SSL certificate verification is not recommended in production environments, it is possible in development setups. However, this removes the security benefits of SSL and is strongly discouraged.
Q5. How can I add a self-signed certificate to the trusted certificate authority list?
To add a self-signed certificate to the trusted certificate authority list in Kubernetes, you need to update the trusted certificate store on the nodes running your cluster. The process may vary depending on your operating system, so refer to their documentation for instructions.
Q6. What should I do if the error persists after trying all the solutions?
If the error persists, ensure that you are using the correct certificate, and all the necessary intermediate and root certificates are in place. Check for any typos or misconfigurations in the certificate and its chain. You may also consider seeking help from the support channels of the registry or Kubernetes community for troubleshooting assistance.
Conclusion:
The “x509: certificate signed by unknown authority” error in Kubernetes occurs when an SSL certificate used by a registry is not trusted by Kubernetes. This can be due to expired certificates, self-signed certificates, or misconfigured certificate authorities. By understanding the causes and their respective solutions, you can effectively troubleshoot this error and ensure a smooth process for pulling container images in your Kubernetes cluster. Remember to always follow best practices for SSL certificate management to maintain a secure environment.
Unable To Connect To The Server: X509: Certificate Signed By Unknown Authority
In today’s technology-driven world, connecting to various servers is crucial for many tasks such as accessing websites, sending emails, or running applications. However, occasionally you may encounter an error message that says “Unable to connect to the server: x509: certificate signed by unknown authority.” This error occurs when the server’s SSL/TLS certificate cannot be verified due to being signed by an unknown authority. In this article, we will delve into the reasons behind this error and explore potential solutions for resolving it.
Understanding SSL/TLS Certificates and Authorities
Before we dive into the specifics of the error, let’s first understand what SSL/TLS certificates and certificate authorities are. SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that provide secure communication over a network. SSL/TLS certificates are a crucial component of these protocols, as they verify the authenticity of a server and enable the encryption of data transmitted between the client (your device) and the server.
Certificate authorities (CAs) are trusted third-party organizations responsible for issuing digital certificates. These certificates include information about the server’s identity, such as its domain name, along with the CA’s digital signature to ensure its authenticity. Web browsers and operating systems maintain a list of trusted CAs, allowing them to verify the validity of certificates presented by servers during the SSL/TLS handshake process.
Reasons for the Error: Certificate Signed by Unknown Authority
The error message “Unable to connect to the server: x509: certificate signed by unknown authority” typically appears when the server’s certificate could not be verified against any trusted CA in the client’s certificate store. There are several potential causes for this error:
1. Self-Signed Certificates: Some servers use self-signed certificates, which are certificates signed by the server itself instead of a trusted CA. While self-signed certificates can provide encryption, trust cannot be automatically established by clients, leading to the “unknown authority” error.
2. Outdated or Expired Root Certificates: The client’s device may have outdated or expired root certificates, which are essential for verifying the validity of SSL/TLS certificates. If the root certificate used to sign the server’s certificate is missing or expired, the client won’t be able to establish a trusted connection.
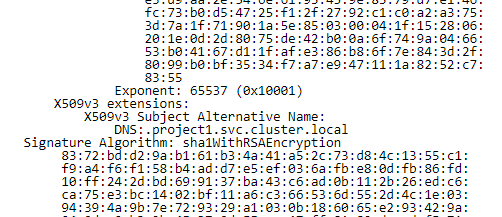
3. Certificate Chain Issues: Sometimes, the server’s certificate may be valid, but it may not present the entire certificate chain required for verification. The certificate chain includes an intermediate CA certificate that links the server’s certificate to a trusted root certificate. If any part of this chain is missing or incorrect, the client will fail to establish a trusted connection.
Resolving the Error: Certificate Signed by Unknown Authority
Now that we understand the causes, let’s explore some potential solutions for resolving the “x509: certificate signed by unknown authority” error:
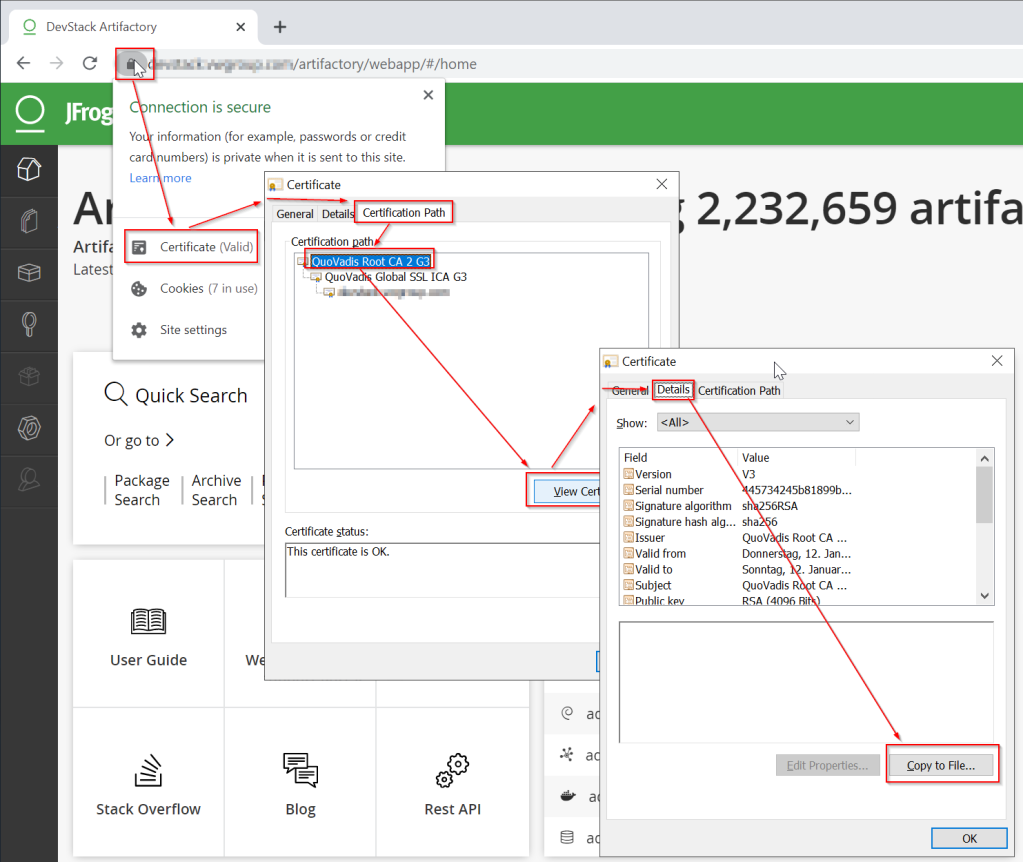
1. Trust Self-Signed Certificates: If you are connecting to a server that uses self-signed certificates, you can manually add the certificate to the trusted certificate store on your device. This allows your client to validate the server’s certificate, thereby establishing a trusted connection.
2. Update Root Certificates: To ensure your device has the latest trusted CA certificates, you can update your operating system or web browser. These updates often include new root certificates and revoke any compromised or expired certificates.
3. Double-Check Certificate Chain: If you are a server administrator, make sure you present the complete certificate chain, including the server’s certificate, any intermediate CA certificates, and the root certificate. Verify the chain’s integrity using tools such as OpenSSL. If any part is missing or incorrect, rectify the issue to establish a trusted connection.
5. Disable TLS Verification (Not Recommended): As a last resort, you can disable TLS verification in your client’s settings. However, this removes the security provided by SSL/TLS, making your connection vulnerable to attacks. This option should only be used in exceptional cases when there are no other alternatives.
FAQs
Q: Why did I receive the “x509: certificate signed by unknown authority” error?
A: This error occurs when the server’s SSL/TLS certificate cannot be verified against any trusted certificate authority in your client’s certificate store.
Q: Can I trust self-signed certificates?
A: While self-signed certificates provide encryption, they cannot establish trust automatically. However, you can manually trust self-signed certificates by adding them to your trusted certificate store.
Q: How do I update root certificates on my device?
A: To update root certificates, you can either update your operating system or web browser. These updates often include new trusted CA certificates.
Q: Can I disable TLS verification to connect to the server?
A: Disabling TLS verification removes the security provided by SSL/TLS, making your connection vulnerable to attacks. It is not recommended unless there are no other alternatives.
In conclusion, the error message “Unable to connect to the server: x509: certificate signed by unknown authority” can occur due to self-signed certificates, outdated root certificates, or issues with the certificate chain. By following the suggested solutions and understanding the implications of each, you can resolve this error and establish a secure and trusted connection to the server.
Images related to the topic x509: certificate signed by unknown authority

Found 33 images related to x509: certificate signed by unknown authority theme

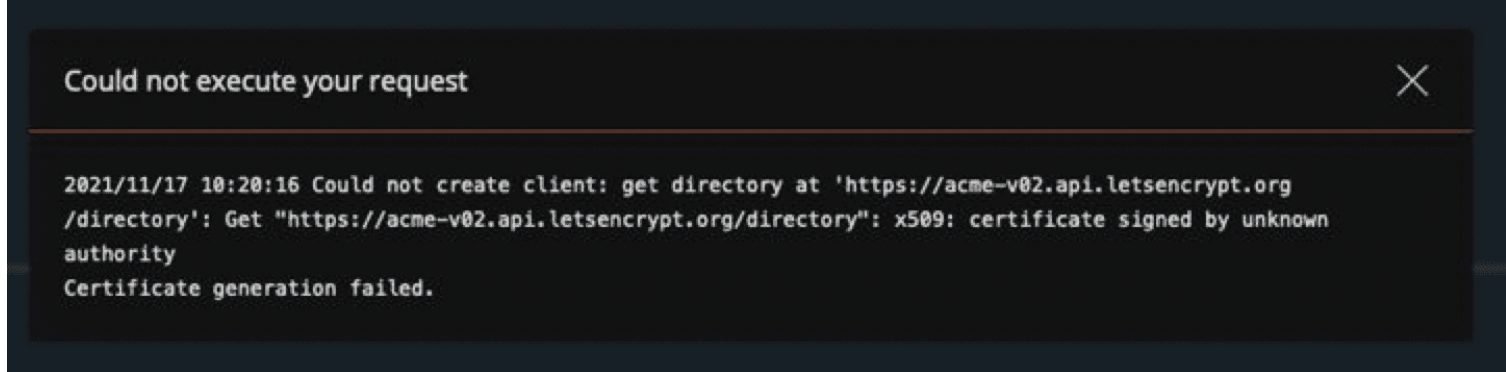







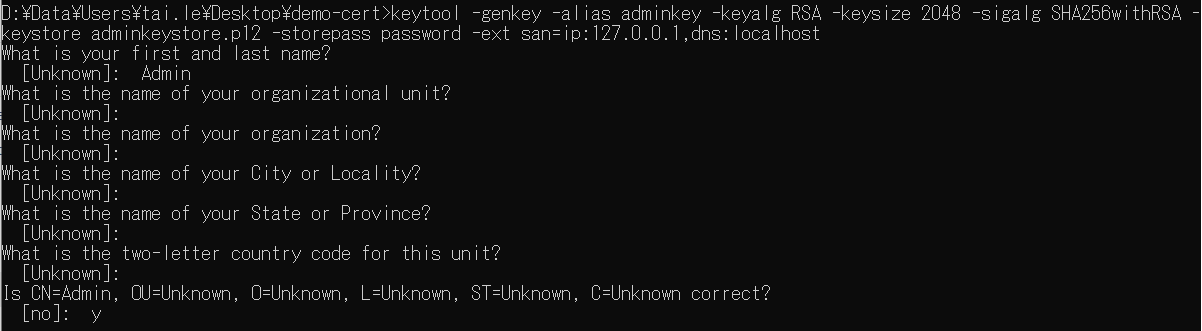












![DirectAdmin] Fix certificate signed by unknown authority Certificate generation failed Directadmin] Fix Certificate Signed By Unknown Authority Certificate Generation Failed](https://www.itcweb.net/Images/Posts/637919379535204104_directadmin-fix-certificate-signed-by-unknown-authority-certificate-generation-failed.jpg)






Article link: x509: certificate signed by unknown authority.
Learn more about the topic x509: certificate signed by unknown authority.
- x.509 certificate là gì? Cách khắc phục lỗi x.509 … – SSL.VN
- “docker pull” certificate signed by unknown authority
- Directamin – x509: certificate signed by unknown authority
- X509 Certificate Signed by Unknown Authority: Causes & Fixes
- ERROR: x509: certificate signed by unknown authority error is …
- How to Fix the “X.509 Certificate Signed by Unknown Authority …
- certificate signed by unknown authority | Bamboo | Atlassian …
- Docker Private Registry: x509: certificate signed by unknown …
See more: https://nhanvietluanvan.com/luat-hoc