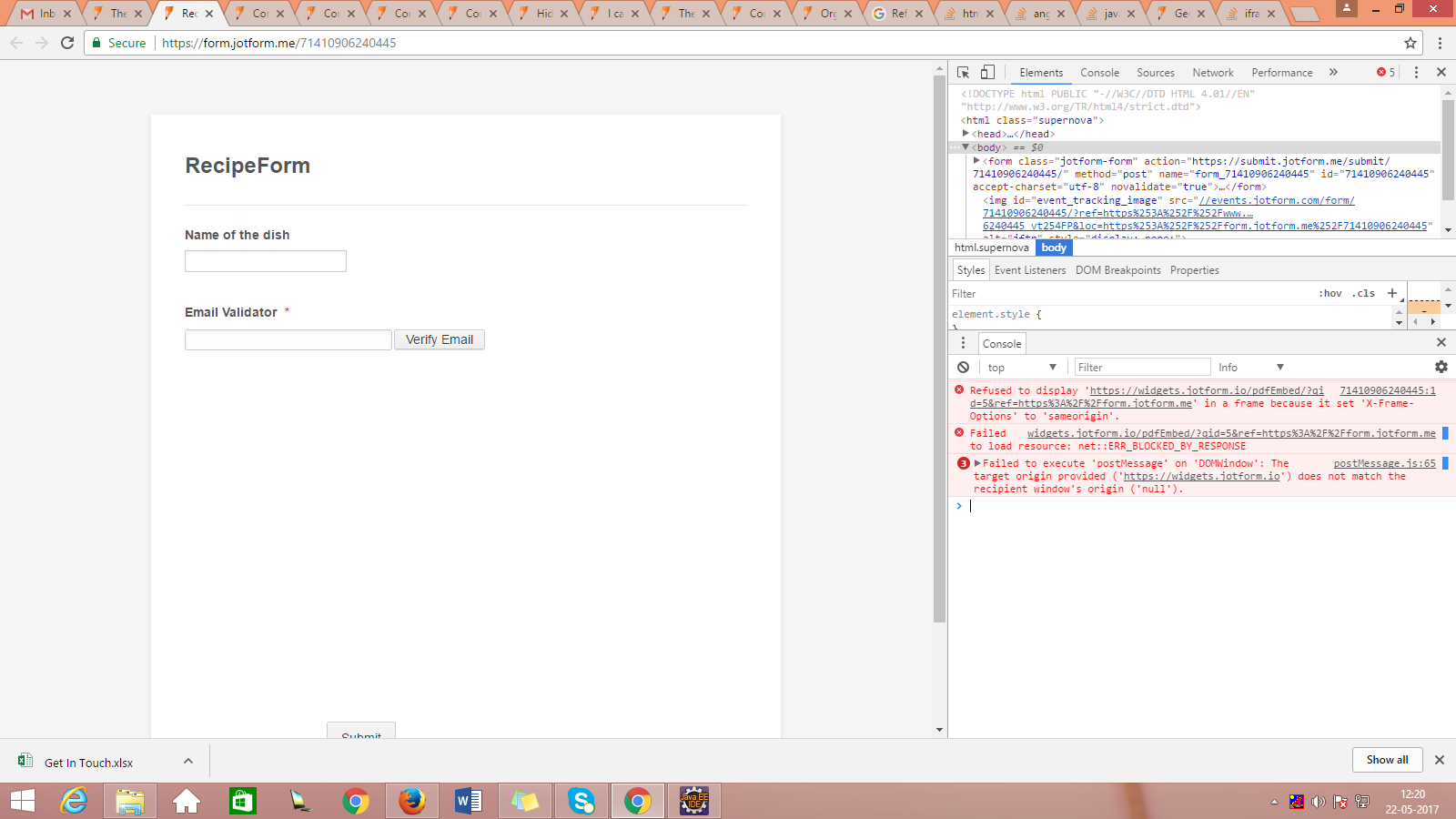
In A Frame Because It Set ‘X-Frame-Options’ To ‘Sameorigin’.
In the world of web development and security, it is essential to have robust measures in place to protect websites and web applications from potential threats. One such security measure is the X-Frame-Options header, which helps prevent clickjacking attacks and ensures the integrity of web content. In this article, we will delve into the concept of X-Frame-Options, specifically focusing on the ‘sameorigin’ setting. We will explore its significance in web security, its role in preventing clickjacking attacks, the importance of the Same-Origin Policy in web browsing, limitations, and alternatives to ‘sameorigin’, as well as the implementation of X-Frame-Options for enhanced web application security.
The Significance of X-Frame-Options in Web Security
X-Frame-Options is a security header that specifies how a web page should be displayed within an iframe. An iframe is an HTML element that allows embedding one website within another. While iframes can be useful for integrating content from different sources, they can also be exploited for malicious purposes such as clickjacking.
Clickjacking, also known as UI redress attack or user interface redress attack, is a technique where an attacker tricks a user into interacting with a webpage or application by disguising it as something else. By utilizing iframes, attackers can overlay legitimate content with malicious content, leading users to unknowingly perform unintended actions, such as sharing personal information or making fraudulent transactions.
To mitigate the risks associated with clickjacking, X-Frame-Options came into existence. The header serves as a defense mechanism by allowing website owners to control how their pages are framed, thereby preventing unauthorized embedding and protecting the integrity of their content.
Examining the Role of ‘sameorigin’ in the X-Frame-Options Header
‘sameorigin’ is one of the options available for the X-Frame-Options header. When set to ‘sameorigin’, it allows the page to be framed only by other pages from the same origin. The origin refers to the combination of the protocol, domain, and port number of a website.
By using ‘sameorigin’, website owners ensure that their content can only be embedded within iframes on their own domain. This setting prevents any external websites from framing their pages, making it challenging for attackers to execute clickjacking attacks. However, it also restricts legitimate use cases where cross-origin framing may be desirable.
Preventing Clickjacking Attacks with ‘sameorigin’ Setting
The ‘sameorigin’ setting in the X-Frame-Options header is an effective measure against clickjacking attacks. By employing this setting, website owners enforce the Same-Origin Policy, which is a fundamental principle of web security.
The Same-Origin Policy restricts the interaction between documents (web pages) from different origins. It ensures that any script running in the context of one page cannot access or manipulate the content of a page from a different origin. This principle plays a crucial role in preventing cross-site scripting (XSS) attacks, data leakage, and clickjacking.
By setting ‘sameorigin’ in the X-Frame-Options header, websites protect their pages from being framed by malicious actors. Only iframes originating from the same domain will be able to display the content, reducing the risk of clickjacking attacks and maintaining the overall security of the web application.
Importance of Same-Origin Policy in Web Browsing
The Same-Origin Policy is a vital aspect of web browsing security. It acts as a boundary that prevents malicious websites from accessing sensitive information or interacting with trusted domains. By enforcing the Same-Origin Policy, web browsers ensure that each website can only interact with resources from the same origin, limiting the potential for data breaches and unauthorized access.
When supported by a proper implementation of the X-Frame-Options header with the ‘sameorigin’ setting, the Same-Origin Policy becomes even more robust. It enhances web browsing security by adding an additional layer of protection against clickjacking attacks and unauthorized embedding of content.
Limitations and Alternatives to ‘sameorigin’ in X-Frame-Options
While the ‘sameorigin’ setting in the X-Frame-Options header provides solid security against clickjacking attacks, it does come with some limitations. One significant limitation is that it completely restricts cross-origin framing, even in situations where it may be necessary or desired.
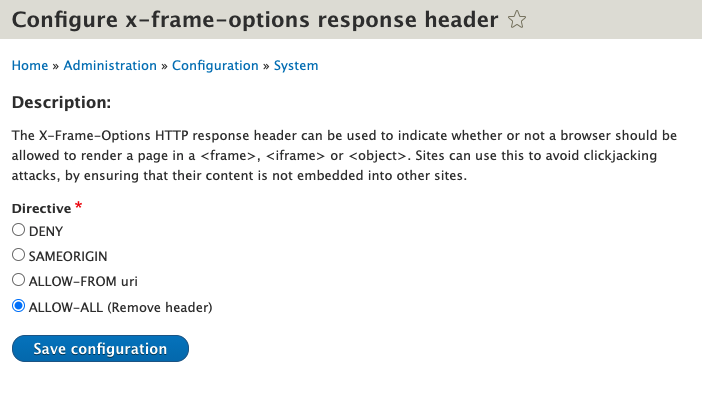
In cases where cross-origin framing is required, alternatives to ‘sameorigin’ can be utilized. These alternatives include the ‘allow-from’ setting or the ‘allow-all’ setting. The ‘allow-from’ setting allows framing from a specific domain, while the ‘allow-all’ setting permits framing from any domain.
However, it is important to note that both alternatives have their own set of risks and should be used cautiously. Allowing framing from a specific domain with the ‘allow-from’ setting requires careful consideration of the security implications, as it may still potentially expose the website to clickjacking attacks if the specified domain becomes compromised. Similarly, the ‘allow-all’ setting should be used sparingly, as it completely opens up the possibility of clickjacking attacks from any domain.
Implementing X-Frame-Options for Enhanced Web Application Security
Implementing X-Frame-Options with the ‘sameorigin’ setting is a relatively straightforward process. It involves adding the header to the HTTP response of a website or web application. The header instructs web browsers to enforce the specified framing policy for the page. The exact implementation steps vary depending on the web server or framework being used.
For example, in Spring Boot, the X-Frame-Options header can be set by including the following line of code:
response.addHeader(“X-Frame-Options”, “SAMEORIGIN”);
In React applications, the X-Frame-Options header can be incorporated by configuring the web server to add the header to the responses.
By correctly implementing X-Frame-Options with the ‘sameorigin’ setting, web developers and administrators can significantly enhance the security of their web applications, protecting against clickjacking attacks and ensuring the integrity of their content.
FAQs:
Q1: What does ‘x-frame-options: sameorigin’ mean?
A1: ‘x-frame-options: sameorigin’ is a setting in the X-Frame-Options header, which specifies that a web page can only be framed by other pages from the same domain.
Q2: How does ‘sameorigin’ prevent clickjacking attacks?
A2: ‘sameorigin’ prevents clickjacking attacks by enforcing the Same-Origin Policy, which restricts the embedding of web content to iframes originating from the same domain, thereby mitigating the risk of unauthorized framing.
Q3: What are the limitations of ‘sameorigin’ in X-Frame-Options?
A3: ‘sameorigin’ completely restricts cross-origin framing, which may be necessary or desired in specific scenarios. Alternatives, such as ‘allow-from’ or ‘allow-all’, can be used to enable cross-origin framing but should be approached with caution due to potential security risks.
Q4: How can X-Frame-Options be implemented in Spring Boot?
A4: The X-Frame-Options header can be set in Spring Boot by adding the line ‘response.addHeader(“X-Frame-Options”, “SAMEORIGIN”);’ to the code, ensuring that the header is included in the HTTP responses of the web application.
Q5: Why is the Same-Origin Policy important in web browsing?
A5: The Same-Origin Policy plays a crucial role in web browsing security as it prevents malicious websites from accessing sensitive information or interacting with trusted domains, thereby protecting users from data breaches and unauthorized access.
Q6: Are there any alternatives to ‘sameorigin’ in X-Frame-Options?
A6: Yes, alternatives to ‘sameorigin’ include the ‘allow-from’ setting, which allows framing from a specific domain, and the ‘allow-all’ setting, which permits framing from any domain. However, both alternatives have associated risks and should be used with caution.
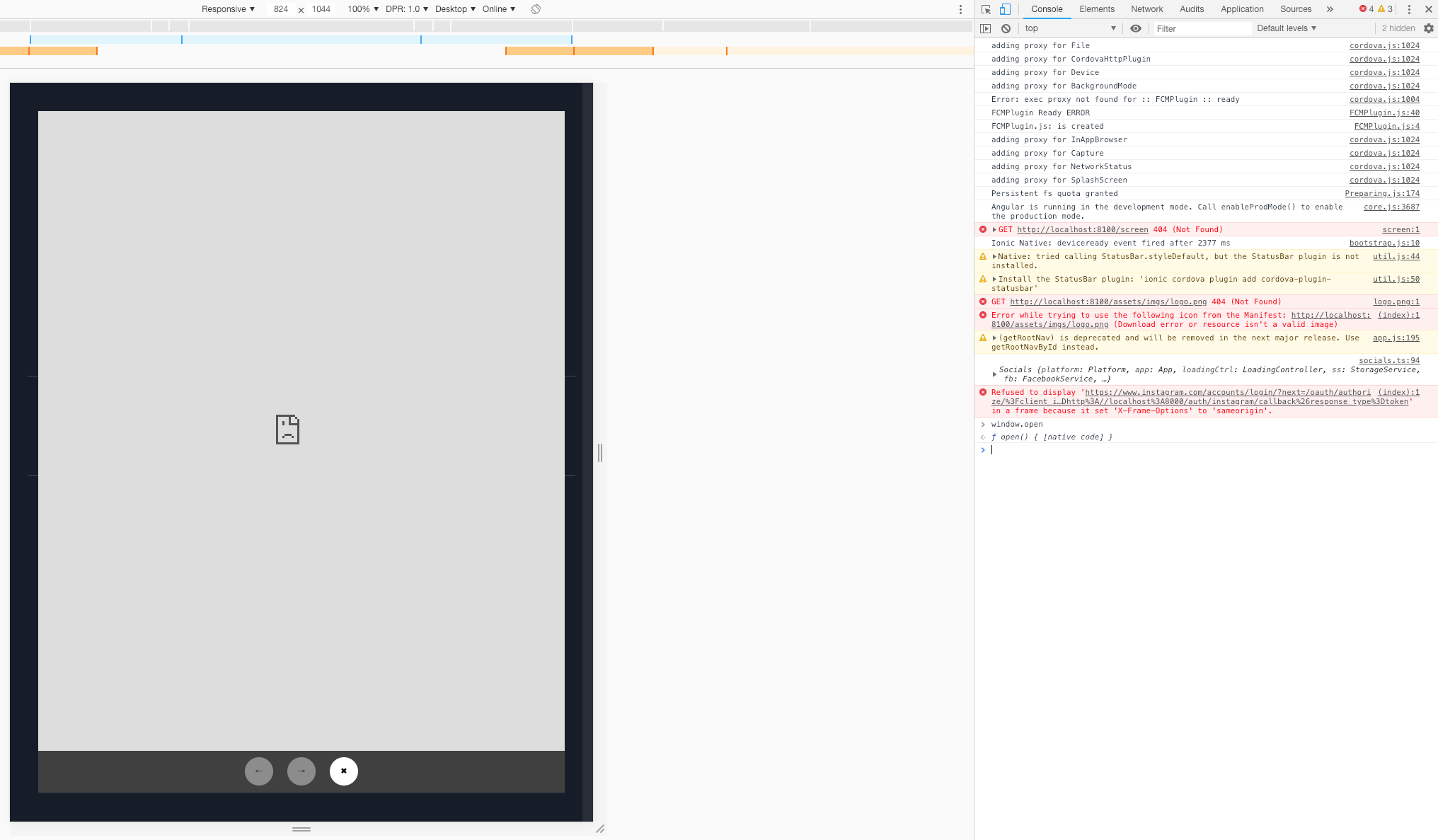
Refused To Display ‘Url’ In A Frame Because It Set ‘X-Frame-Options’ To ‘Sameorigin’
What Is X-Frame-Options To Sameorigin In Html?
In today’s digital age, website security has become paramount. One of the most common vulnerabilities exploited by hackers is known as clickjacking, an attack that tricks users into clicking on something they did not intend to. Fortunately, there is a simple yet effective way to counter this threat – the X-Frame-Options to Sameorigin feature in HTML. In this article, we will delve into the depths of X-Frame-Options, understanding its definition, purpose, implementation, and its impact on web security.
Definition and Purpose:
The X-Frame-Options HTTP response header provides a means to control whether a web page can be displayed inside an iframe. An iframe, short for inline frame, is an HTML element that allows external content to be embedded within a webpage. While iframes have legitimate uses, they also create security risks when misused. X-Frame-Options mitigates this risk by allowing server administrators to specify who can display their website’s content in an iframe.
The Sameorigin directive of X-Frame-Options is one of the three possible configuration values. When this option is set, it restricts the page from being loaded in an iframe on a different domain. In simpler terms, it prevents clickjacking attempts by limiting the website’s display to the same origin or domain. This means that the content can only be embedded within a webpage if it originates from the same domain that the webpage was loaded from.
Implementation and Impact:
Implementing X-Frame-Options to Sameorigin is a straightforward process. It involves adding a simple header to the server’s response to the browser. This header can be sent via the HTTP response or by using a meta tag within the HTML of the webpage. For instance, when implemented in the HTTP response header, it would look like this:
“`
X-Frame-Options: SAMEORIGIN
“`
Alternatively, using the meta tag method:
“`html
“`
Once implemented, the X-Frame-Options to Sameorigin directive immediately enhances website security. It prevents malicious websites from embedding the protected webpage in an iframe and consequently, eliminates the risk of clickjacking. By strictly limiting the page’s display to its own origin, it ensures that user interactions are genuine and intended by the website owner. This measure significantly reduces the possibility of attackers tricking users into taking actions that could compromise their security or privacy.
FAQs:
Q: Why is clickjacking a concern?
A: Clickjacking is a malicious technique designed to deceive users into clicking on invisible or disguised elements placed on top of legitimate website content. This gives attackers the ability to hijack a user’s actions while they remain oblivious to the manipulation. Clickjacking can lead to various nefarious outcomes, such as unintentional form submission, account compromise, or installation of malware.
Q: Are there any drawbacks to implementing X-Frame-Options to Sameorigin?
A: In some cases, the restrictive nature of X-Frame-Options to Sameorigin might interfere with desired functionality of legitimate iframes on a webpage. For example, a website may intentionally embed a trusted third-party widget that becomes restricted by the Sameorigin directive. In such cases, alternative solutions like the Content Security Policy (CSP) might be more appropriate.
Q: Can X-Frame-Options completely prevent clickjacking attacks?
A: While X-Frame-Options provides an essential layer of protection against clickjacking attacks, it is not foolproof. Attackers continually devise new methods to bypass security measures. Therefore, implementing X-Frame-Options should be complemented by other security measures, including regular vulnerability assessments, secure code practices, and ongoing security awareness training.
Q: Is X-Frame-Options supported by all browsers?
A: Most modern browsers support X-Frame-Options. However, it is worth noting that some older browsers may not recognize this header, making the content vulnerable to clickjacking. To ensure maximum protection, it is advisable to combine X-Frame-Options with other security mechanisms and keep browsers updated to the latest versions.
Conclusion:
In conclusion, X-Frame-Options to Sameorigin is a valuable security feature in HTML that helps protect web content from clickjacking attacks. By restricting the display of a website’s content to its own domain, it ensures that user interactions are genuine and not manipulated by malicious entities. However, it is important to note that X-Frame-Options is just one piece of the security puzzle and should be combined with other measures to safeguard websites effectively. Stay informed, stay secure, and protect your online presence.
What Is X-Frame-Options For Iframe?
In the world of web development and security, there are various mechanisms and technologies that are used to protect users and their data from potential threats. One such security measure that is widely used is the X-Frame-Options header for iframes. This header essentially allows website owners to control how their site can be embedded in an iframe on another domain, thus preventing certain types of attacks.
To understand X-Frame-Options, we first need to understand what an iframe is. An iframe, short for inline frame, is an HTML element used to embed another HTML document within the current document. This means that website owners can include content from other websites directly within their own web pages. However, this convenience comes with security risks.
Cross-Site Scripting (XSS) attacks and clickjacking are two major risks associated with iframes. XSS attacks involve injecting malicious scripts into a website, which are then executed by unsuspecting users who visit the infected page. Clickjacking, on the other hand, involves tricking users into clicking on something they didn’t intend to click, by overlaying invisible elements on top of a legitimate website. Both these attacks can be launched through iframes.
This is where X-Frame-Options comes in. The X-Frame-Options header allows website owners to control how their site can be framed within an iframe. There are three possible values for the X-Frame-Options header:
1. DENY: This value tells the browser to deny any framing of the content. In other words, it explicitly prohibits the site from being embedded in any iframe, regardless of the domain. This is the strictest option, ensuring that the site is never embedded within an iframe.
2. SAMEORIGIN: This value allows the site to be embedded in an iframe, but only if the iframe is hosted on the same domain as the parent page. For example, if the parent page is www.example.com, the iframe can only be hosted on www.example.com or any subdomain of example.com. This prevents external sites from embedding the content.
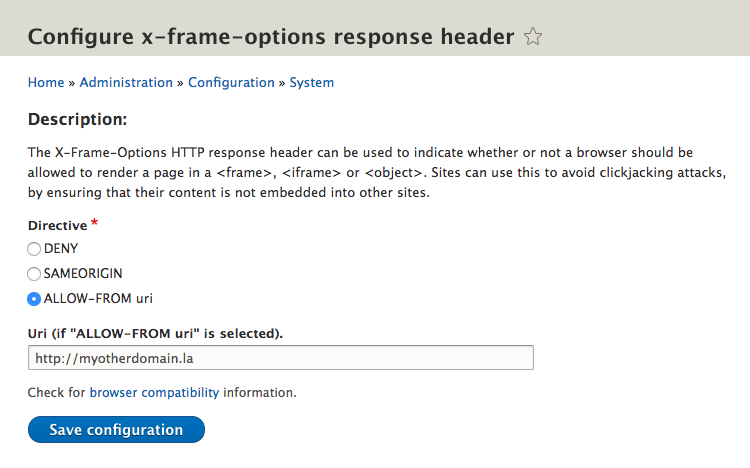
3. ALLOW-FROM URI: This value allows the site to be embedded in an iframe, but only if the iframe is hosted on the specified URI. This allows more flexibility in terms of where the content can be embedded, but it still provides some level of control.
Implementing X-Frame-Options is quite simple. It involves adding the appropriate header to the HTTP response sent by the web server. For example, if a website owner wants to prevent framing of their content from any domain, they would include the header “X-Frame-Options: DENY” in the response. Similarly, if they want to allow framing only from the same domain, they would include the header “X-Frame-Options: SAMEORIGIN”. The header can also be set to “X-Frame-Options: ALLOW-FROM www.example.com” to allow framing from a specific domain.
Frequently Asked Questions (FAQs):
Q: What are the benefits of using X-Frame-Options for iframes?
A: X-Frame-Options provides an added layer of security to prevent XSS attacks and clickjacking. By controlling how a website can be embedded, site owners can reduce the risk of malicious activities and protect their users.
Q: Are there any drawbacks to using X-Frame-Options?
A: One potential drawback is that legitimate uses of iframes, such as embedding content from trusted sources, may also be restricted. For example, a website might want to embed a YouTube video in an iframe, but if X-Frame-Options is set to DENY or SAMEORIGIN, the embedding will be blocked. Therefore, it is important to carefully consider the impact on the functionality of the site before implementing X-Frame-Options.
Q: Can X-Frame-Options completely prevent all iframe-related attacks?
A: While X-Frame-Options can significantly reduce the risk of iframe-related attacks, it is not foolproof. Attackers may find other ways to exploit vulnerabilities and bypass X-Frame-Options. It is important to implement other security measures, such as strong input validation and output encoding, to further enhance the security of a website.
Q: Is X-Frame-Options supported by all browsers?
A: X-Frame-Options is supported by most modern browsers, including Chrome, Firefox, Safari, and Internet Explorer. However, it is always recommended to check the browser compatibility before relying on X-Frame-Options as a security measure.
In conclusion, X-Frame-Options is a valuable security measure for iframes, allowing website owners to control how their content is embedded in iframes on other domains. By setting the appropriate X-Frame-Options header, website owners can prevent XSS attacks and clickjacking, thus protecting their users from potential threats. However, it is essential to carefully consider the impact on functionality and utilize other security measures in conjunction with X-Frame-Options to ensure comprehensive protection.
Keywords searched by users: in a frame because it set ‘x-frame-options’ to ‘sameorigin’. x-frame-options: sameorigin, in a frame because it set ‘x-frame-options’ to ‘deny’., Refused to display https www youtube com in a frame because it set x frame Options’ to ‘SAMEORIGIN, Refused to display ‘url in a frame because it set x frame Options’ to ‘SAMEORIGIN, x-frame-options allow all, X frame-options Spring boot, x-frame-options allow-from, x-frame-options react
Categories: Top 31 In A Frame Because It Set ‘X-Frame-Options’ To ‘Sameorigin’.
See more here: nhanvietluanvan.com
X-Frame-Options: Sameorigin
Introduction:
In today’s interconnected world, websites have become an essential part of our lives. Whether for personal, professional, or entertainment purposes, we rely on them for information, communication, and transactions. However, as websites play an increasingly crucial role, they also become more susceptible to security threats. One such threat is called clickjacking, which can compromise the integrity and security of a website. Fortunately, there are measures that can be implemented to mitigate clickjacking, and one of these is X-Frame-Options: Sameorigin.
Understanding X-Frame-Options: Sameorigin:
X-Frame-Options: Sameorigin is a security mechanism that is implemented in the HTTP response headers of a website. It instructs web browsers on how they should render the website in an iframe or a frame. An iframe is an HTML element that allows external content, such as advertisements or embedded content, to be included within a webpage. While iframes have legitimate purposes, they can also be exploited for clickjacking, a technique in which malicious actors trick users into performing unintended actions by overlaying the legitimate website with a hidden frame containing malicious content.
X-Frame-Options: Sameorigin prevents clickjacking by restricting the rendering of a website in an iframe to only occur when the source of the iframe matches the origin of the website itself. In simpler terms, it ensures that a website can only be framed within its own domain, preventing malicious actors from embedding it within their own websites to deceive users.
Implementing X-Frame-Options: Sameorigin:
Implementing X-Frame-Options: Sameorigin is relatively straightforward. It requires modifying the server’s response headers to include the X-Frame-Options directive. When the web server sends a response to a client’s browser, it can append the X-Frame-Options directive to the response headers with the “sameorigin” value. For example, the header can be set as:
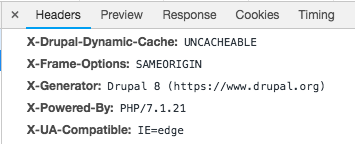
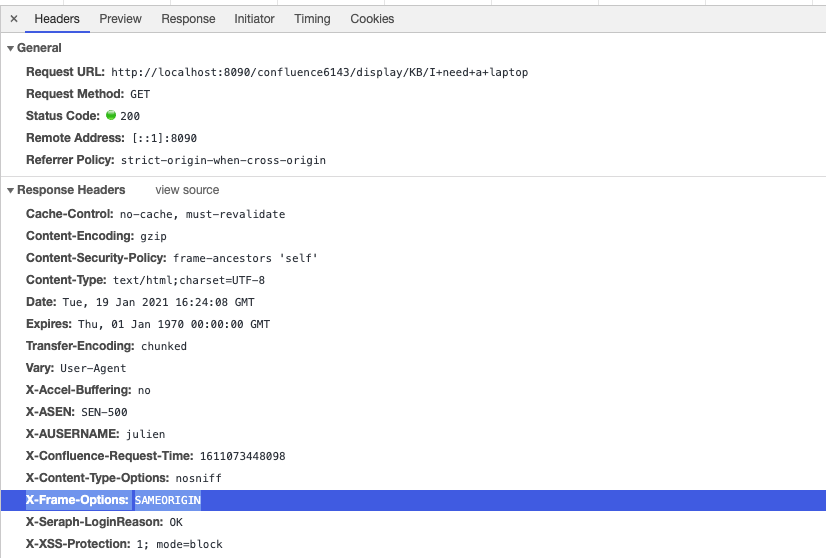
X-Frame-Options: SAMEORIGIN
By including this directive, the website informs the browser that it should only render the page if it is accessed directly from the original source, preventing it from being loaded within an iframe from a different website.
Benefits of X-Frame-Options: Sameorigin:
1. Preventing Clickjacking Attacks: The primary benefit of X-Frame-Options: Sameorigin is its ability to protect websites from clickjacking attacks. By restricting framing to the same origin, it effectively mitigates the risks associated with overlaying legitimate websites with hidden malicious content.
2. Enhanced User Security: With clickjacking attacks neutralized, users can browse websites with increased confidence, as they can be assured that the content they interact with is genuine and coming from a trusted source.
3. Data Protection: Clickjacking attacks can pose serious threats to user privacy and data. By implementing X-Frame-Options: Sameorigin, websites can protect sensitive information from being compromised by preventing any unauthorized access attempts.
FAQs:
Q1. Is implementing X-Frame-Options: Sameorigin sufficient to ensure complete website security?
A1. No, while implementing X-Frame-Options: Sameorigin is an important step in reinforcing website security, it should not be considered a standalone solution. Websites should adopt a multi-layered security approach that includes robust authentication mechanisms, a secure coding practice, regular security audits, and other security headers like Content-Security-Policy (CSP).
Q2. Does X-Frame-Options: Sameorigin have any compatibility issues with certain browsers or older versions?
A2. No, X-Frame-Options: Sameorigin is supported by all major web browsers, including Chrome, Firefox, Safari, and Edge. However, it is essential to note that Internet Explorer uses a different header called X-Frame-Options: DENY, which serves the same purpose as Sameorigin.
Q3. Can X-Frame-Options: Sameorigin impact the functionality of legitimate iframes?
A3. Yes, X-Frame-Options: Sameorigin can restrict the rendering of legitimate iframes, even if they are embedded within the same domain. In such cases, website administrators can opt for alternative approaches like allowing framing through the use of the X-Frame-Options directive with value “allow-from www.example.com,” where “www.example.com” represents the domain allowed to frame the content.
Conclusion:
In a digital landscape where security threats persist, it is crucial for website administrators to proactively protect their users and enhance the overall security posture of their platforms. X-Frame-Options: Sameorigin provides a practical and effective method to combat clickjacking attacks, ensuring that websites are not exploited to deceive users or compromise sensitive information. By implementing this security mechanism, website administrators can safeguard their websites, gain user trust, and create a more secure online environment for everyone.
In A Frame Because It Set ‘X-Frame-Options’ To ‘Deny’.
The digital age has brought about remarkable advancements in technology, transforming the way we interact, communicate, and access information. As the internet continues to evolve, web developers and businesses are tasked with ensuring the security and integrity of their online platforms. One crucial aspect of web security involves setting the ‘X-Frame-Options’ header to ‘deny’ to prevent potential vulnerabilities and protect user data. In this article, we will delve into the world of web security headers, focusing specifically on the significance of ‘X-Frame-Options’ and how it ensures a safer browsing experience.
Understanding Web Security Headers
Web security headers are an essential component of web development, offering an added layer of protection against various threats and attacks. These headers provide instructions to a user’s browser regarding how certain aspects of a web page should be handled. They help guard against cross-site scripting (XSS) attacks, clickjacking, and other malicious activities that could compromise a user’s information.
One critical web security header is ‘X-Frame-Options,’ which dictates whether a website can be loaded within a frame or an iframe on a separate domain. By setting ‘X-Frame-Options’ to ‘deny,’ web developers restrict their web page from being framed, effectively preventing malicious actors from embedding it within their own website. This measure eliminates the risk of clickjacking, where users are tricked into clicking on something unintended due to invisible frames overlaying a legitimate website.
Importance of ‘X-Frame-Options: Deny’
The primary purpose of setting ‘X-Frame-Options’ to ‘deny’ is to protect users from potential security threats. It prevents your website’s content from being framed by other domains, ensuring that visitors can trust the authenticity of your site and interact with its features with confidence. The ‘X-Frame-Options’ header plays a crucial role in fortifying your website’s security, maintaining the integrity of your brand, and safeguarding sensitive user data.
3 Frequently Asked Questions (FAQs) about ‘X-Frame-Options: Deny’
Q: How does setting ‘X-Frame-Options’ to ‘deny’ enhance web security?
A: Setting ‘X-Frame-Options’ to ‘deny’ reinforces web security by inhibiting malicious actors from framing your website. This prevents various attacks, such as clickjacking, where attackers overlay your site with invisible frames to trick users into clicking on unwanted elements.
Q: Are there any downsides to setting ‘X-Frame-Options’ to ‘deny’?
A: While setting ‘X-Frame-Options’ to ‘deny’ is generally beneficial for security, it may restrict legitimate uses of frames or iframes on your website. For example, if your site utilizes embedded content from trusted sources, such as maps or social media plugins, those elements may no longer function correctly.
Q: How can I set ‘X-Frame-Options’ to ‘deny’ on my website?
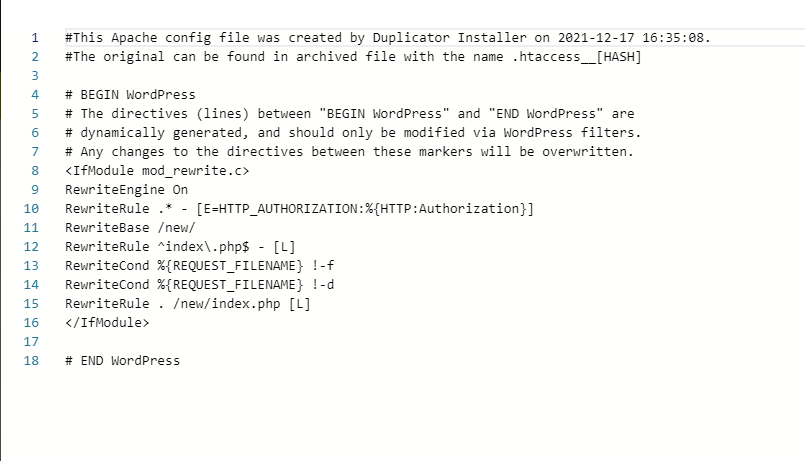
A: The process of setting ‘X-Frame-Options’ to ‘deny’ varies depending on your web server or content management system (CMS). In Apache, you can add the header to your .htaccess file using the following code: Header always append X-Frame-Options DENY. For other platforms, consult relevant documentation or seek assistance from your web hosting provider.
Conclusion
The digital landscape is teeming with threats and vulnerabilities, making it imperative for web developers and businesses to prioritize cybersecurity. By setting ‘X-Frame-Options’ to ‘deny,’ you establish a robust defense mechanism against clickjacking and similar attacks, protecting your website’s integrity and user data. Remember, while implementing security headers is crucial, it is equally important to regularly update and maintain your website’s security measures to adapt to evolving threats and ensure a seamless user experience. Stay informed, stay safe, and prioritize web security for a thriving online presence.
Images related to the topic in a frame because it set ‘x-frame-options’ to ‘sameorigin’.

Found 7 images related to in a frame because it set ‘x-frame-options’ to ‘sameorigin’. theme














![SilenRefresh issue with Google Oauth: Refused to display https://accounts.google[...] in a frame · Issue #364 · manfredsteyer/angular-oauth2-oidc · GitHub Silenrefresh Issue With Google Oauth: Refused To Display Https://Accounts.Google[...] In A Frame · Issue #364 · Manfredsteyer/Angular-Oauth2-Oidc · Github](https://user-images.githubusercontent.com/1517721/41771455-7d808cf0-7615-11e8-835e-84f7cde379e3.png)



















Article link: in a frame because it set ‘x-frame-options’ to ‘sameorigin’..
Learn more about the topic in a frame because it set ‘x-frame-options’ to ‘sameorigin’..
- Refused to display in a frame because it set ‘X-Frame-Options …
- X-Frame-Options – HTTP – MDN Web Docs
- Refused to Display in a Frame Because It Set ‘X-frame …
- Refused to display ‘http://localhost:12345/api/reports/clients …
- X-Frame-Options Set to Deny – Credo Learning Tools
- X-Frame-Options – HTTP – MDN Web Docs
- X-Frame-Options Header Not Set – ScanRepeat
- KB484848: Missing or permissive X-Frame-Options HTTP response …
- How to configure frames with X-Frame-Options header
- Refused to display ‘URL’ in a frame because it set ‘X-Frame …
- Hướng dẫn mở X-Frame-Option trên Apache và Nginx
- Refused to display in a frame because it set X-Frame-Options …
- Error “Refused to display url in a frame because it set ‘X …
See more: nhanvietluanvan.com/luat-hoc