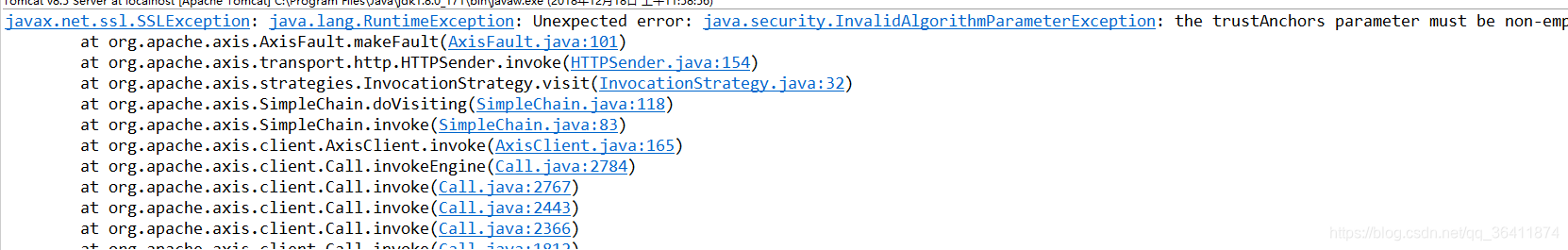
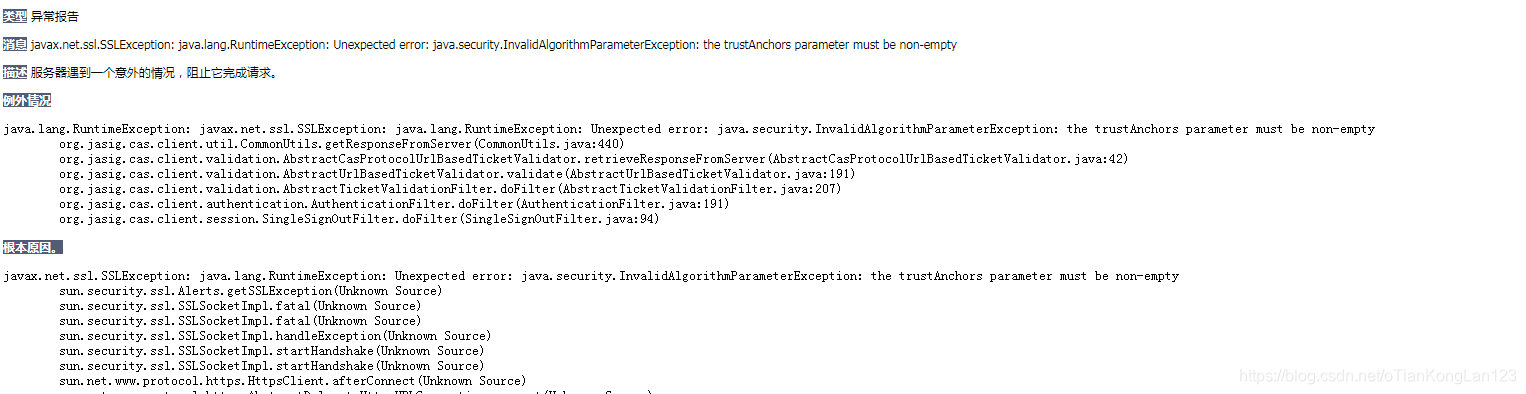
The Trustanchors Parameter Must Be Non-Empty
In the world of network security and authentication, the trustanchors parameter plays a pivotal role in ensuring the integrity and trustworthiness of network communications. It acts as a crucial component in establishing secure connections, verifying digital certificates, and safeguarding sensitive data. The trustanchors parameter must be non-empty, meaning it should include valid and trustworthy sources for trust anchors, to ensure the highest level of security and protection against potential vulnerabilities and risks.
1. Understanding the trustanchors Parameter
Before delving into the significance of a non-empty trustanchors parameter, it is essential to understand what it entails. The trustanchors parameter refers to a set of trusted sources of trust anchors, which are entities that are considered reliable and secure for validating digital certificates and public keys. These trust anchors, also known as root certificates or root authorities, are the foundation of trust within a network system.
2. Significance of a Non-Empty trustanchors Parameter
a. Definition and Role of Trust Anchors
Trust anchors, as mentioned earlier, serve as the ultimate source of trust within a network system. These are the well-established and authoritative entities that have been thoroughly vetted and proven to be trustworthy. When a network system receives a digital certificate, it needs to verify the authenticity and validity of the certificate by tracing it back to a trust anchor. The trustanchors parameter holds the necessary information to carry out this verification process.
b. The Function of the trustanchors Parameter
The trustanchors parameter, when populated with trusted sources of trust anchors, ensures that network systems can verify the legitimacy of certificates and public keys effectively. By having a non-empty trustanchors parameter, network administrators can rely on authenticated and verified certificates, thus establishing secure communication channels.
c. Ensuring Security and Authenticity in Network Communication
A non-empty trustanchors parameter is crucial for maintaining the security and authenticity of network communications. It helps prevent unauthorized access and data breaches by validating certificates and public keys through trusted sources. Without a non-empty trustanchors parameter, network systems are at a higher risk of becoming vulnerable to malicious attacks and unauthorized intrusions.
3. Potential Issues with an Empty trustanchors Parameter
a. Vulnerabilities and Risks of an Empty trustanchors Parameter
An empty trustanchors parameter leaves network systems susceptible to various vulnerabilities and risks. Without a valid and trusted source of trust anchors, it becomes challenging to authenticate certificates and public keys accurately. This creates an environment where malicious actors can intercept and manipulate network communications, leading to potential data breaches, identity theft, and other cyber threats.
b. Importance of Preventing Unauthorized Access and Data Breaches
Unauthorized access and data breaches can have severe consequences for both individuals and organizations. They can result in financial losses, compromised client information, damaged reputation, and even legal implications. By establishing a non-empty trustanchors parameter, network administrators can significantly reduce the risk of such incidents by ensuring the authenticity and integrity of network communications.
c. Impact on Trust and Credibility of Network Systems
The trust and credibility of network systems heavily rely on their ability to provide secure and trustworthy connections. If network systems fail to implement a non-empty trustanchors parameter, users may lose confidence in the system’s ability to protect their information and privacy. This can have a detrimental impact on user adoption, customer satisfaction, and the overall reputation of the network service provider.
d. Compliance with Security Standards and Best Practices
In today’s ever-evolving security landscape, organizations are bound by compliance regulations and industry standards. Many of these regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR), explicitly require the implementation of secure communication protocols with non-empty trustanchors parameters. Failure to comply with these standards can result in severe penalties and legal consequences.
4. Establishing a Non-Empty trustanchors Parameter
a. Identifying Trustworthy Sources for Trust Anchors
Establishing a non-empty trustanchors parameter requires identifying reliable and trustworthy sources for trust anchors. These sources often include reputable certificate authorities and root certificate providers. It is essential to carefully vet these sources and ensure they adhere to industry standards and best practices.
b. Integrating Trust Anchors into Network Configurations
Once trustworthy sources for trust anchors are identified, they need to be integrated into network configurations. This involves updating network settings to include the necessary trustanchors parameter values that point to the validated trust anchor sources. This integration ensures that all network communications are properly authenticated and verified.
c. Regular Updates and Maintenance for Enhanced Security
To maintain the highest level of security, it is crucial to regularly update and maintain the trustanchors parameter. This includes staying updated with the latest root certificates and ensuring that expired or compromised certificates are promptly removed. Regular maintenance ensures that network systems are protected against evolving threats and vulnerabilities.
5. Benefits of a Non-Empty trustanchors Parameter
a. Reliable Verification of Certificates and Public Keys
A non-empty trustanchors parameter enables reliable verification of digital certificates and public keys. This verification process ensures that certificates and keys are authentic, valid, and issued by trusted entities. This reliability is crucial in establishing secure connections and preventing unauthorized access.
b. Mitigating the Risk of Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks are among the most common and dangerous threats to network security. By implementing a non-empty trustanchors parameter, network systems can significantly mitigate the risk of MitM attacks. This is achieved by validating the certificates and keys used in secure communications, making it much more difficult for attackers to intercept and manipulate data.
c. Enhanced Trustworthiness and Authentication of Network Services
A non-empty trustanchors parameter enhances the trustworthiness and authentication of network services. By relying on validated trust anchors, network systems can assure users that their communications are secure and that their data is protected. This, in turn, builds user confidence and fosters trust in the network service provider.
d. Safeguarding Users’ Confidentiality and Privacy
Implementing a non-empty trustanchors parameter plays a vital role in safeguarding users’ confidentiality and privacy. By ensuring the integrity of network communications, sensitive information remains protected from unauthorized access and interception. This protection is essential for maintaining user confidence and meeting regulatory requirements.
6. Implementing the trustanchors Parameter in Practice
a. Examples of Trust Anchors in Different Applications
Trust anchors are used in various applications and systems to establish secure connections. For example, web browsers rely on trust anchors to verify the authenticity of SSL/TLS certificates used in secure website connections. Similarly, email clients use trust anchors to authenticate the sender’s digital signature and ensure the integrity of email communications.
b. Configuring the trustanchors Parameter in Network Settings
Configuring the trustanchors parameter in network settings involves updating the necessary configurations to include the trusted sources of trust anchors. This can be done through the network configuration files or management interfaces provided by the network equipment or software. It is crucial to follow vendor-specific instructions and best practices when configuring the trustanchors parameter.
c. Importance of Documentation and Transparency in Trust Anchor Management
Proper documentation and transparency in trust anchor management are essential for effective implementation and maintenance. Network administrators should maintain clear records of the trust anchor sources, their expiration dates, and any updates or changes made to the trustanchors parameter. This documentation helps with auditing, troubleshooting, and ensuring accountability.
7. Best Practices for Managing the trustanchors Parameter
a. Regular Auditing and Review of Trust Anchors
Regular auditing and review of trust anchors help ensure their continued validity and trustworthiness. Network administrators should periodically evaluate the sources of trust anchors and verify that they align with industry standards and best practices. Any suspicious or untrusted sources should be promptly removed to mitigate potential risks.
b. Ensuring Compatibility and Interoperability with Different Systems
Network administrators should ensure that the trustanchors parameter is compatible and interoperable with different systems and devices within the network. This ensures seamless integration of trust anchor sources and allows for secure communication across the entire network infrastructure.
c. Collaborating with Trusted Certificate Authorities
Collaborating with trusted certificate authorities can greatly assist in managing the trustanchors parameter. Certificate authorities can provide valuable insights and guidance on trustworthy sources of trust anchors and help keep network systems updated with the latest root certificates. Building strong relationships with trusted certificate authorities enhances the security and integrity of network communications.
d. Adequate Training and Awareness Programs for Network Administrators
Network administrators should receive adequate training and awareness programs to stay updated with the latest security practices and technologies related to the trustanchors parameter. This training equips them with the necessary knowledge and skills to effectively manage and maintain trust anchors throughout the network infrastructure.
8. Case Studies and Real-World Examples
a. Instances of Security Breaches Due to an Empty trustanchors Parameter
There have been several instances where organizations have suffered security breaches due to an empty trustanchors parameter. In these cases, attackers were able to manipulate network communications, extract sensitive information, and compromise the integrity of the network system. These incidents highlight the critical importance of implementing a non-empty trustanchors parameter.
b. Successful Implementation of a Non-Empty trustanchors Parameter
On the other hand, organizations that have successfully implemented a non-empty trustanchors parameter have enjoyed enhanced security and trustworthiness in their network communications. They have been able to establish secure connections, validate certificates and public keys accurately, and protect sensitive data from unauthorized access. These success stories emphasize the significant impact of a non-empty trustanchors parameter on network security.
9. Conclusion
In conclusion, the trustanchors parameter must be non-empty to ensure the highest level of security, authentication, and trustworthiness in network communications. By including valid and trustworthy sources for trust anchors, organizations can mitigate vulnerabilities, prevent unauthorized access, and safeguard sensitive data. Implementing and maintaining a non-empty trustanchors parameter should be a top priority for network administrators to adhere to industry standards, best practices, and compliance regulations. When it comes to network security, never underestimate the power of the trustanchors parameter.
Java :Error – Trustanchors Parameter Must Be Non-Empty(5Solution)
Keywords searched by users: the trustanchors parameter must be non-empty
Categories: Top 89 The Trustanchors Parameter Must Be Non-Empty
See more here: nhanvietluanvan.com
Images related to the topic the trustanchors parameter must be non-empty

Found 33 images related to the trustanchors parameter must be non-empty theme









Article link: the trustanchors parameter must be non-empty.
Learn more about the topic the trustanchors parameter must be non-empty.
- Error: “trustAnchors parameter must be non-empty” | Baeldung
- Error – trustAnchors parameter must be non-empty
- Debugging yet another SSL/TLS error: the trustAnchors …
- What to Do When You Encounter the Error: java.lang … – JFrog
- How do I fix: the trustAnchors parameter must be non-empty?
- Error “trustAnchors parameter must be non-empty” in catalina …
- Correcting error “The trustAnchors parameter must be non …
- the trustAnchors parameter must be non-empty
- the trustAnchors parameter must be non-empty” from Studio
- [bitnami/zookeeper] Got error “the trustAnchors parameter …
See more: nhanvietluanvan.com/luat-hoc