In A Frame Because It Set ‘X-Frame-Options’ To ‘Sameorigin’
The ‘x-frame-options’ header is an important HTTP response header that provides security measures against clickjacking attacks by controlling the behavior of web content when it is embedded within an iframe. By setting the ‘x-frame-options’ header, website administrators can dictate whether their content can be framed by external websites or only by pages within the same origin.
This article will explore the different values for the ‘x-frame-options’ header, discuss the implications of setting it to ‘SAMEORIGIN’, and present alternative methods to achieve similar security goals. Additionally, we will provide best practices for implementing the ‘x-frame-options’ header to ensure website security and confidentiality.
What is the ‘x-frame-options’ header?
The ‘x-frame-options’ header is a security measure that allows website administrators to control whether their pages can be embedded within an iframe by external websites. It was introduced to prevent clickjacking attacks, where an attacker tricks users into performing unintended actions by framing legitimate web content within malicious pages.
Different values for ‘x-frame-options’ header
1. ‘SAMEORIGIN’ value of ‘x-frame-options’ header:
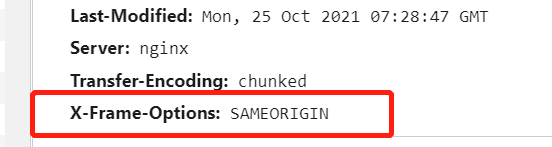
– When the ‘x-frame-options’ header is set to ‘SAMEORIGIN’, it allows the content to be framed only by pages within the same origin. This means that the website can be embedded within an iframe by pages hosted on the same domain or subdomain, but not by pages from a different domain.
2. ‘DENY’ value of ‘x-frame-options’ header:
– The ‘DENY’ value of the ‘x-frame-options’ header prevents any external website from framing the content. This means that the website cannot be embedded within an iframe by any external domain.
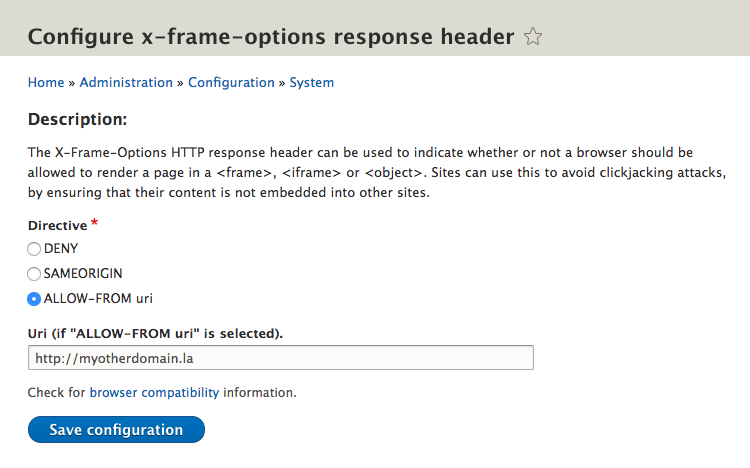
3. ‘ALLOW-FROM’ value of ‘x-frame-options’ header:
– The ‘ALLOW-FROM’ value allows the website to be framed by a specific domain. Administrators can specify the allowed domain in the header, and the content will only be displayable within iframes hosted on that domain.
Implications of setting ‘x-frame-options’ to ‘SAMEORIGIN’
1. Preventing clickjacking attacks:
– By setting the ‘x-frame-options’ header to ‘SAMEORIGIN’, the website administrator ensures that the content cannot be framed by malicious websites. This prevents attackers from tricking users into performing actions on their behalf.
2. Limiting iframe usage to the same origin:
– Setting ‘x-frame-options’ to ‘SAMEORIGIN’ restricts the embedding of content to pages within the same origin. This can be beneficial for websites that want to maintain control over how their content is displayed and ensure a consistent user experience.
3. Ensuring website security and confidentiality:
– By preventing the framing of content by external websites, the ‘SAMEORIGIN’ value of ‘x-frame-options’ helps maintain the security and confidentiality of sensitive information. It reduces the risk of data leaks or unauthorized access to confidential resources.
Alternative methods to ‘x-frame-options’
While ‘x-frame-options’ provides a straightforward way to control framing behavior, there are alternative methods that can achieve similar security goals:
1. Content Security Policy (CSP):
– Content Security Policy is a more comprehensive approach to web security that includes directives to control framing behavior. With CSP, administrators can specify which origins are allowed to frame the content using the ‘frame-ancestors’ directive.
2. Cross-Origin Resource Sharing (CORS):
– CORS is primarily used to manage cross-origin requests, but it can also be utilized to control framing behavior. By configuring the appropriate CORS headers, administrators can specify which domains are permitted to frame the content.
3. Frame ancestors directive in CSP:
– As an extension of CSP, the ‘frame-ancestors’ directive allows administrators to specify which origins are allowed to embed the content within iframes. This provides granular control over framing behavior while maintaining the flexibility of CSP.
Best practices for implementing ‘x-frame-options’ header
To ensure optimal website security and prevent clickjacking attacks, here are some best practices for implementing the ‘x-frame-options’ header:
1. Understand the content and purpose of your website:
– Evaluate the nature of your website and the importance of content framing. Consider whether it is necessary to allow framing by external domains or restrict it to the same origin.
2. Evaluate the necessity of cross-origin framing:
– Determine whether there is a legitimate need for your website to be embedded within iframes hosted on different domains. If not, consider setting ‘x-frame-options’ to ‘SAMEORIGIN’ or ‘DENY’ to enhance security.
3. Implement appropriate ‘x-frame-options’ value:
– Choose the ‘x-frame-options’ value that aligns with your security requirements. Set ‘SAMEORIGIN’ if you only want to allow framing by pages within the same origin, or set ‘DENY’ to prevent framing by any external website.
4. Regularly monitor content and update security measures:
– Stay vigilant and monitor any changes to your website’s content to ensure that security measures, including the ‘x-frame-options’ header, remain effective. Periodically review and update your security configurations as required.
In conclusion, the ‘x-frame-options’ header plays a crucial role in protecting websites against clickjacking attacks and maintaining the security and confidentiality of web content. By properly setting this header and exploring alternative methods such as CSP and CORS, website administrators can ensure a robust security posture while allowing or restricting the embedding of their content within iframes. Stay informed, implement best practices, and regularly review and update security measures to keep your website secure and protected.
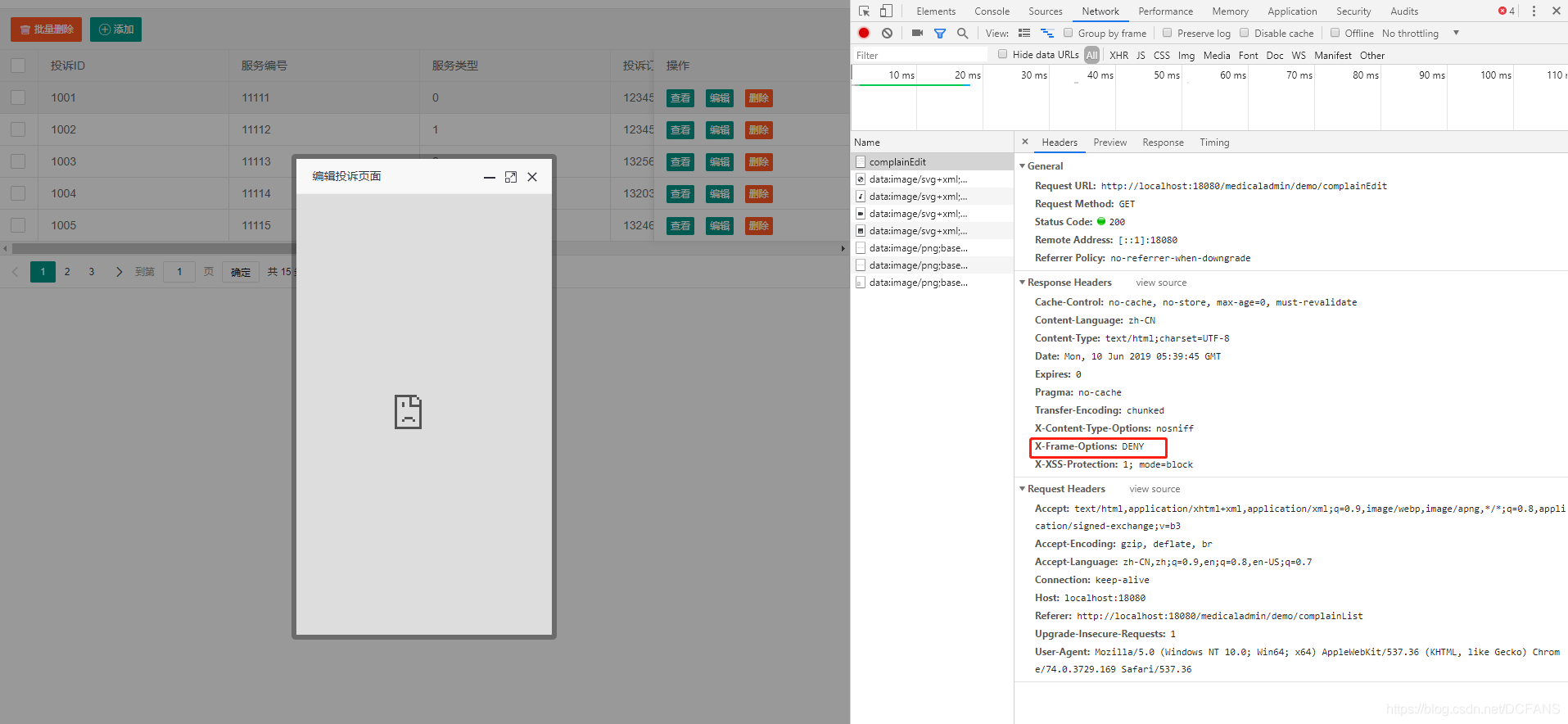
Refused To Display ‘Url’ In A Frame Because It Set ‘X-Frame-Options’ To ‘Sameorigin’
What Is X-Frame-Options To Sameorigin In Html?
In the ever-evolving world of web development and security, developers need to familiarize themselves with various measures and techniques to protect their websites from potential vulnerabilities and attacks. One such technique is implementing the X-Frame-Options header to set a policy on how web browsers should handle framing or embedding the website’s content into another webpage. Specifically, the “X-Frame-Options: sameorigin” directive ensures that the website can only be loaded within a frame on the same origin.
Understanding the Basics:
When a website is embedded or framed within another webpage, it is referred to as “framing” or “embedding.” This allows developers to display content from different sources on a single page, providing a seamless experience for users. However, this convenience comes with security risks, particularly when a malicious website tries to incorporate a trusted site’s content into its own.
The X-Frame-Options header was introduced to mitigate these risks and prevent a potential attack known as “clickjacking” or “UI redress attacks.” Clickjacking occurs when an attacker tricks the user into clicking on a hidden or invisible element on a webpage by overlaying deceptive content with legitimate elements. By implementing the X-Frame-Options header with the “sameorigin” directive, developers can ensure that their website’s content is only framed by pages that originate from the same domain.
Implementation of X-Frame-Options:
To implement X-Frame-Options with the “sameorigin” directive, developers can include the following header in the server-side script:
“`
X-Frame-Options: sameorigin
“`
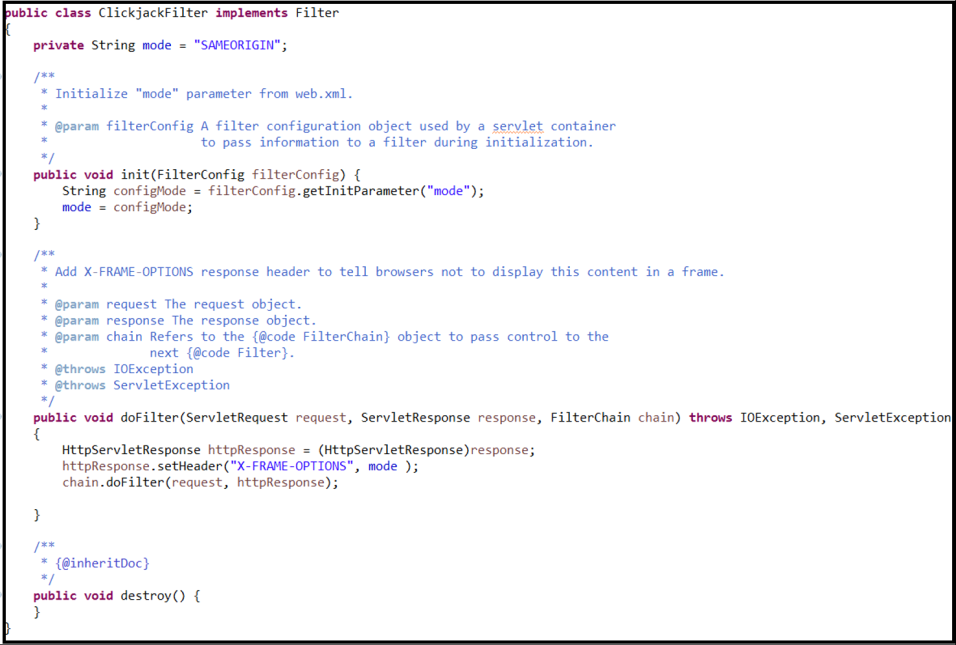
This indicates to the browser that the website can only be framed by pages with the same domain and protects against clickjacking attacks. It is important to note that X-Frame-Options must be included as a server-side header and cannot be set through client-side scripting like JavaScript.
Impact on Different Browsers:
Different browsers interpret the X-Frame-Options header in slightly different ways. Let’s take a look at how some of the popular browsers handle this directive:
1. Internet Explorer (IE): IE supports the X-Frame-Options header and adheres to the “sameorigin” directive. When a website is framed in a different domain, IE displays an error message stating that the webpage cannot be displayed due to security restrictions.
2. Google Chrome: Chrome also supports X-Frame-Options and treats the “sameorigin” directive consistently. If a website is embedded in a different domain, Chrome displays an error page indicating that it refused to display the webpage.
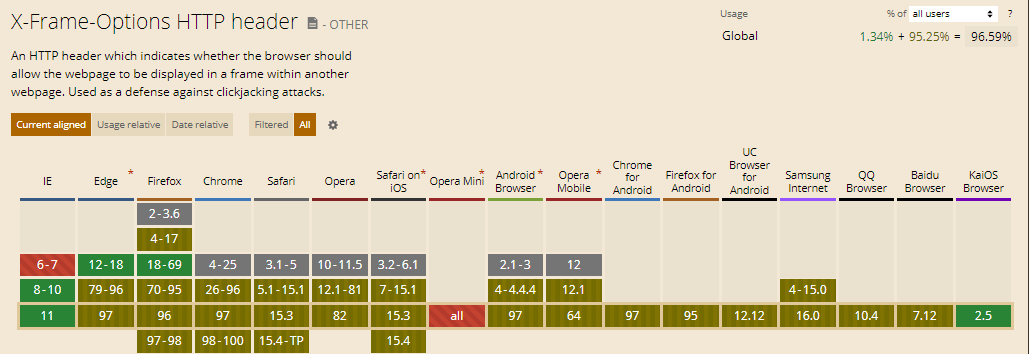
3. Mozilla Firefox: The behavior of Mozilla Firefox depends on the version. In general, newer versions of Firefox recognize and enforce X-Frame-Options. However, older versions have limited or partial support, making it necessary to implement additional security measures to avoid framing vulnerabilities.
4. Safari: Safari introduced support for X-Frame-Options in version 13.1 and later. Similar to other browsers, Safari respects the “sameorigin” directive and prevents the website from being framed by a different domain.
Frequently Asked Questions:
1. Can X-Frame-Options completely prevent clickjacking attacks?
While X-Frame-Options can effectively protect against clickjacking attacks within supported browsers, it is not a foolproof solution. Some modern browsers have started deprecating or moving away from X-Frame-Options and introducing more advanced security techniques like Content Security Policy (CSP) to address clickjacking and other vulnerabilities.
2. Are there any alternatives to X-Frame-Options for preventing clickjacking attacks?
Yes, additional security measures like Content Security Policy (CSP) provide more robust protection against clickjacking and other attacks. CSP allows developers to specify the domains from which the website allows framing. It is highly recommended to use a combination of security headers, including CSP, for a strong defense against clickjacking.
3. Are there any drawbacks to using X-Frame-Options with the “sameorigin” directive?
One potential drawback of using X-Frame-Options with the “sameorigin” directive is that it restricts legitimate framing use cases within the same domain. If a website intends to allow framing by subdomains or external trusted domains, using “sameorigin” may pose limitations. In such cases, alternative measures like CSP should be considered.
4. How can I check if X-Frame-Options is correctly implemented on my website?
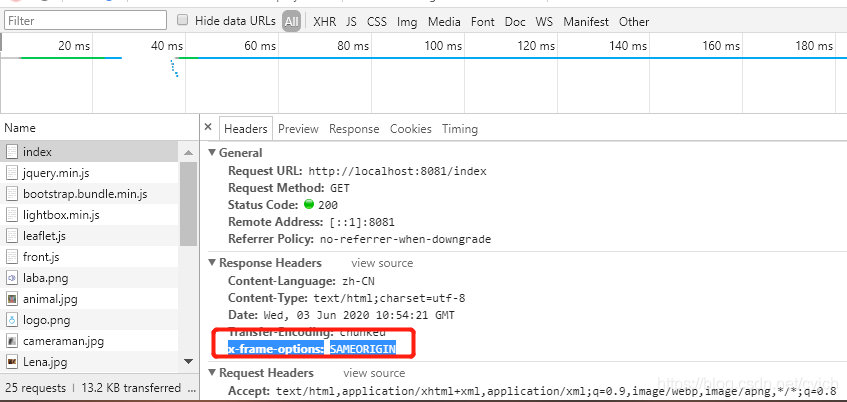
To verify if X-Frame-Options is correctly implemented, you can use browser developer tools or online security testing tools. These tools analyze the response headers and check for the presence of the X-Frame-Options header with the “sameorigin” directive.
Conclusion:
Implementing the X-Frame-Options header with the “sameorigin” directive is a crucial security measure for protecting websites against clickjacking attacks. By controlling the framing behavior, developers can minimize the risk of malicious websites exploiting their content. While X-Frame-Options has been widely adopted, it is important to stay updated with evolving security practices and consider additional measures like CSP to ensure comprehensive protection against emerging threats.
What Is X-Frame-Options For Iframe?
In today’s world, where the internet plays a vital role in our daily lives, ensuring the security of websites and their content is of utmost importance. One essential tool that helps protect websites from malicious attacks is the X-Frame-Options header, specifically designed for iframes. In this article, we will delve into the details of X-Frame-Options for iframes, its significance, its various uses, and its potential pitfalls.
Understanding the Basics
Before diving into the specifics, it is important to understand the concept of iframes. An iframe, short for inline frame, is an HTML element commonly used to embed external content or documents within a webpage. This content can be from the same domain or a different domain altogether. While iframes allow for seamless integration of content from various sources, they can also be abused by cybercriminals to launch attacks on users or their personal information.
Enter X-Frame-Options. This HTTP response header allows website owners to control if and how their pages can be displayed within an iframe. With the help of this header, website administrators can safeguard their websites and protect users from potential threats.
Importance of X-Frame-Options
X-Frame-Options offers several benefits when correctly implemented:
1. Protection from Clickjacking Attacks: Clickjacking is a technique where an attacker tricks a user into clicking on content that is hidden or invisible, thereby performing unintended actions. By implementing X-Frame-Options, website owners can prevent their pages from being loaded in a frame on another website, thus reducing the risk of clickjacking attacks.
2. Preventing Content Scraping: Some websites use iframes to scrape content from other websites without proper permission. By setting X-Frame-Options, website owners can ensure that their web pages cannot be loaded within iframes on other domains, thwarting unauthorized content scraping attempts.
Understanding X-Frame-Options Headers
When it comes to X-Frame-Options, there are three possible values that can be set as the header:
1. DENY: By setting the DENY value for X-Frame-Options, website owners explicitly deny any browser from rendering their page within an iframe. This value ensures the highest level of security by completely blocking the page from being displayed in an iframe on any website.
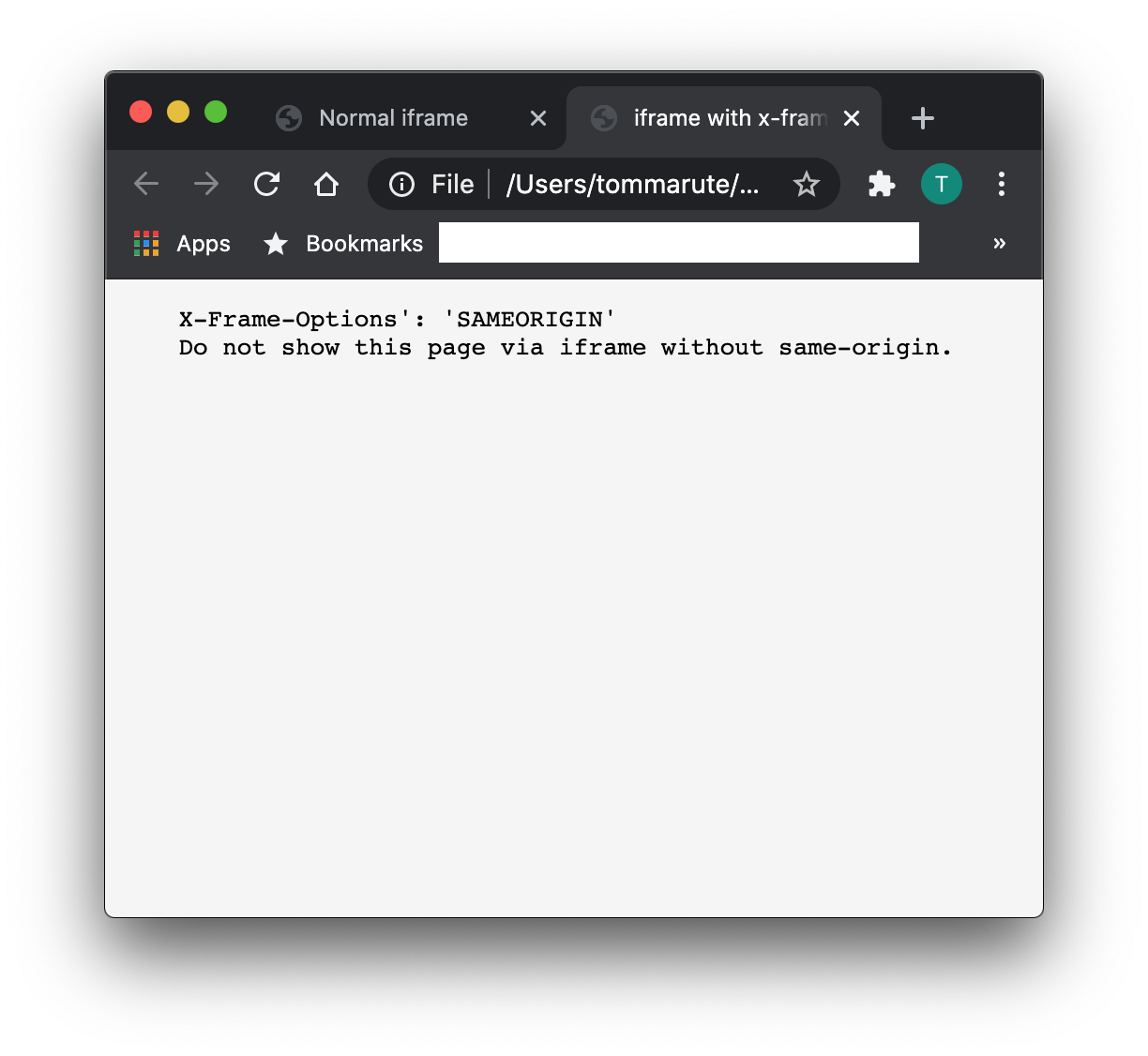
2. SAMEORIGIN: The SAMEORIGIN value permits a webpage to be displayed within an iframe only if the iframe’s parent page belongs to the same origin as the loaded webpage. This value is useful when a website wants to embed its own content on its own pages, but restricts embedding on external websites.
3. ALLOW-FROM uri: This value allows website owners to specify a list of URIs (Uniform Resource Identifiers) which are permitted to display the webpage within an iframe. This approach is generally considered less secure as it relies on the proper configuration of different domains, making it more prone to misconfigurations.
Potential Pitfalls
Though X-Frame-Options provides a useful layer of protection against various attacks, there can be certain downsides to its implementation:
1. Limited Browser Support: X-Frame-Options is supported by most modern browsers, including Google Chrome, Mozilla Firefox, and Microsoft Edge. However, Safari does not support this header, thus rendering its protection ineffective in that particular browser.
2. Complexity in Cross-Domain Embedding: Websites that rely heavily on cross-domain iframes, such as web applications using third-party content, might face difficulties while implementing X-Frame-Options. In these cases, alternative security measures like Content Security Policy (CSP) headers can be considered.
FAQs:
Q1. Are there any alternative headers to X-Frame-Options?
A1. Yes, Content Security Policy (CSP) headers provide an alternative to X-Frame-Options. CSP offers more fine-grained control over content embedding, including iframe restrictions.
Q2. Can I use multiple X-Frame-Options headers on my website?
A2. No, you should only have a single X-Frame-Options header in your website’s response. Multiple headers can lead to unwanted behavior.
Q3. Should I always use the DENY option for X-Frame-Options?
A3. The choice of X-Frame-Options value depends on your website’s requirements. While DENY provides the highest level of security, it may hinder legitimate uses of iframes. Evaluate your needs and choose the appropriate value accordingly.
Q4. Can the X-Frame-Options header prevent all types of clickjacking attacks?
A4. Although X-Frame-Options significantly reduces the risk of clickjacking, it does not provide 100% protection against all possible scenarios. It is recommended to implement additional security measures alongside X-Frame-Options for comprehensive protection.
Conclusion
X-Frame-Options serves as a crucial defense mechanism against clickjacking attacks and unauthorized content scraping. By properly configuring this header, website owners can effectively mitigate potential threats and enhance the security of their webpages. However, it is important to consider the limitations and alternative security measures available to ensure comprehensive protection. Stay vigilant, keep your websites secure, and adopt X-Frame-Options for safer web experiences.
Keywords searched by users: in a frame because it set ‘x-frame-options’ to ‘sameorigin’ x-frame-options: sameorigin, in a frame because it set ‘x-frame-options’ to ‘deny’., Refused to display https www youtube com in a frame because it set x frame Options’ to ‘SAMEORIGIN, Refused to display ‘url in a frame because it set x frame Options’ to ‘SAMEORIGIN, x-frame-options allow all, X frame-options Spring boot, x-frame-options allow-from, x-frame-options react
Categories: Top 49 In A Frame Because It Set ‘X-Frame-Options’ To ‘Sameorigin’
See more here: nhanvietluanvan.com
X-Frame-Options: Sameorigin
As web applications continue to flourish, ensuring their security has become a top priority. One crucial aspect of web security is protecting against clickjacking attacks, where an attacker tricks users into clicking on hidden or disguised elements of a webpage. To mitigate such attacks, the X-Frame-Options header was introduced. This article will delve into X-Frame-Options: Sameorigin, exploring its purpose, implementation, and significance in safeguarding web applications.
Understanding X-Frame-Options
The X-Frame-Options header is a security feature implemented through HTTP response headers. It allows website administrators to specify who is allowed to display their webpage in a frame or iframe. X-Frame-Options provides three options:
1. DENY: This option prevents any webpage from rendering the target webpage in a frame or iframe. It ensures that the webpage cannot be embedded by any external website, offering robust protection against clickjacking attacks.
2. SAMEORIGIN: By choosing this option, website administrators allow the webpage to be displayed in a frame or iframe only if the parent webpage comes from the same origin. An origin represents the combination of a protocol (e.g., HTTP/HTTPS), domain (e.g., example.com), and port (if specified). Therefore, when using X-Frame-Options: SAMEORIGIN, the webpage can only be embedded by another page if it originates from the same domain.
3. ALLOW-FROM uri: This option enables administrators to specify a specific URI (Uniform Resource Identifier) from which the webpage can be embedded. However, support for this option is limited or non-existent in some browsers, making it less commonly used than the other two options.
Implementing X-Frame-Options: Sameorigin
Implementing the X-Frame-Options header with the SAMEORIGIN directive is a straightforward process. Web developers or server administrators need to include the header in their HTTP response. For example, in Apache, the header can be added using the following code:
“`
Header always append X-Frame-Options SAMEORIGIN
“`
Similarly, in Nginx, the following code adds the header:
“`
add_header X-Frame-Options SAMEORIGIN;
“`
Once the header is in place, it signifies to browsers that the webpage should only be displayed in frames or iframes if the parent webpage comes from the same origin. Any attempts to embed the webpage from external sources will be blocked.
Significance in Web Security
X-Frame-Options: SAMEORIGIN plays a vital role in enhancing web security. By limiting the ability to embed a webpage in a frame or iframe from external sources, it prevents attackers from utilizing clickjacking techniques to deceive users into performing unintended actions. Clickjacking attacks can be used to perform various malicious activities, such as initiating transactions, granting unauthorized permissions, or stealing sensitive information without the victim’s knowledge.
Frequently Asked Questions (FAQs)
Q: What is the purpose of X-Frame-Options: SAMEORIGIN?
A: X-Frame-Options: SAMEORIGIN is used to specify that a webpage can only be displayed in a frame or iframe if the parent webpage originates from the same domain.
Q: Are there any limitations to using X-Frame-Options: SAMEORIGIN?
A: While X-Frame-Options: SAMEORIGIN provides effective protection against clickjacking attacks, it does not address other web security vulnerabilities such as cross-site scripting (XSS) or cross-site request forgery (CSRF).
Q: Can X-Frame-Options: SAMEORIGIN be bypassed?
A: In some cases, attackers may attempt to bypass X-Frame-Options: SAMEORIGIN by utilizing other attack vectors, such as opening the target webpage in a new tab or compromising the same domain through other means. However, this risk can be mitigated by employing additional security measures.
Q: How can I test if X-Frame-Options: SAMEORIGIN is in effect on my website?
A: Various online tools are available for testing the presence and effectiveness of the X-Frame-Options header on a webpage. These tools can provide insights into whether the header is being applied correctly.
In conclusion, the X-Frame-Options: Sameorigin header serves as a valuable measure in preventing clickjacking attacks. By restricting the ability to embed a webpage from external sources, it considerably enhances the security of web applications. Implementing X-Frame-Options: SAMEORIGIN is a simple yet effective step towards safeguarding web content and user interactions.
In A Frame Because It Set ‘X-Frame-Options’ To ‘Deny’.
In the world of web development and security, there are numerous measures taken to protect websites and their users from malicious activities. One such measure is the configuration of the ‘X-Frame-Options’ header, which plays a crucial role in preventing clickjacking attacks. By setting ‘X-Frame-Options’ to ‘deny’, websites can efficiently prevent their content from being rendered within a frame or an iframe. This article delves into the concept of ‘X-Frame-Options’ and explores why setting it to ‘deny’ is a recommended security practice.
Understanding ‘X-Frame-Options’:
The ‘X-Frame-Options’ header is an HTTP response header that instructs a browser on how to render a website within a frame or an iframe. It has three possible values: ‘deny’, ‘sameorigin’, and ‘allow-from’. When ‘deny’ is set, the web page cannot be framed under any circumstances. If ‘sameorigin’ is chosen, the page can only be framed by other pages from the same origin, while ‘allow-from’ specifies an origin that can frame the page.
The Importance of ‘Deny’ Setting:
Setting ‘X-Frame-Options’ to ‘deny’ is a recommended security practice for several reasons. Firstly, it helps prevent clickjacking attacks. Clickjacking is a type of attack where an attacker tricks a user into clicking on elements of a different page disguised as harmless content. By rendering the intended website within a frame, the attacker overlays malicious content, creating a deceptive experience for the user. However, when the ‘X-Frame-Options’ header is set to ‘deny’, the attackers cannot frame the website, thus thwarting their malicious intents.
Moreover, by setting ‘X-Frame-Options’ to ‘deny’, website owners ensure that their content is not being misrepresented or misused on other sites. This is particularly important for websites that handle sensitive information, as it prevents unauthorized websites from displaying content that misleads or deceives users. Additionally, the ‘deny’ setting safeguards against various phishing techniques and reduces the risk of users unknowingly interacting with fraudulent websites.
Implementing ‘X-Frame-Options’:
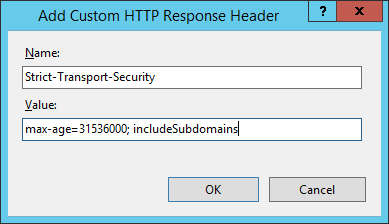
To set the ‘X-Frame-Options’ header to ‘deny’, web developers can include it in the server’s response headers. It can be added through server-side programming or by modifying the server configuration files. Different servers have specific methods of adding headers, so developers should consult the server documentation or reach out to their hosting provider for guidance.
Web developers can also use Content Security Policy (CSP) as an alternative method to mitigate clickjacking. CSP offers more granular control over which origins are allowed to frame a website, providing enhanced security. However, implementing CSP requires careful consideration and thorough testing to ensure compatibility with existing website components.
Frequently Asked Questions (FAQs):
Q1: What happens if a website sets ‘X-Frame-Options’ to ‘deny’?
A1: When ‘X-Frame-Options’ is set to ‘deny’, the web browser will refuse to render the website within a frame, regardless of the context. This prevents clickjacking attacks and safeguards the integrity of the website’s content.
Q2: How does ‘X-Frame-Options’ protect against clickjacking attacks?
A2: Clickjacking attacks rely on rendering a website within a frame or iframe and overlaying malicious content. By setting ‘X-Frame-Options’ to ‘deny’, the website cannot be framed, effectively blocking clickjacking attempts.
Q3: Are there any drawbacks to setting ‘X-Frame-Options’ to ‘deny’?
A3: The ‘deny’ setting can prevent legitimate use cases where a website’s content needs to be rendered within a frame, such as embedding media or widgets. In such cases, developers should choose the ‘sameorigin’ option to ensure the intended usage.
Q4: How can I check if a website sets ‘X-Frame-Options’ to ‘deny’?
A4: To check if a website sets ‘X-Frame-Options’ to ‘deny’, you can inspect the server’s response headers. Using browser developer tools or online header-checking tools, look for the presence of the ‘X-Frame-Options’ header and its value.
Q5: Are there any compatibility issues with setting ‘X-Frame-Options’ to ‘deny’?
A5: ‘X-Frame-Options’ is widely supported by modern browsers and is considered compatible. However, it’s advisable to test the website thoroughly after implementing this setting to ensure there are no unexpected rendering issues.
In conclusion, setting ‘X-Frame-Options’ to ‘deny’ is a crucial security measure to protect websites and users from clickjacking attacks. By implementing this configuration, website owners can prevent their content from being framed within malicious contexts, avoid clickjacking exploits, and maintain the integrity of their site’s reputation and user experience. It is recommended for web developers to embrace this security practice and ensure appropriate safeguards are in place to enhance online safety.
Images related to the topic in a frame because it set ‘x-frame-options’ to ‘sameorigin’

Found 46 images related to in a frame because it set ‘x-frame-options’ to ‘sameorigin’ theme

































Article link: in a frame because it set ‘x-frame-options’ to ‘sameorigin’.
Learn more about the topic in a frame because it set ‘x-frame-options’ to ‘sameorigin’.
- Refused to display in a frame because it set ‘X-Frame-Options …
- X-Frame-Options – HTTP – MDN Web Docs
- Refused to Display in a Frame Because It Set ‘X-frame …
- Refused to display ‘http://localhost:12345/api/reports/clients …
- X-Frame-Options Set to Deny – Credo Learning Tools
- X-Frame-Options – HTTP – MDN Web Docs
- X-Frame-Options Header Not Set – ScanRepeat
- KB484848: Missing or permissive X-Frame-Options HTTP response …
- How to configure frames with X-Frame-Options header
- Refused to display ‘URL’ in a frame because it set ‘X-Frame …
- Hướng dẫn mở X-Frame-Option trên Apache và Nginx
- Refused to display in a frame because it set X-Frame-Options …
- Error “Refused to display url in a frame because it set ‘X …
See more: nhanvietluanvan.com/luat-hoc